7.2. Understanding Cryptographic Algorithms
Cryptographic algorithms are used to encode a message from its unencrypted or clear-text state into an encrypted message. The three primary methods of encoding messages are hashing, using symmetric algorithms, and using asymmetric algorithms. The following sections discuss these methods and some of the standards in which they're used.
7.2.1. The Science of Hashing
As we mentioned earlier, hashing is the process of converting a message, or data, into a numeric value. The numeric value that a hashing process creates is referred to as a hash total or value. Hashing functions are considered either one way or two way.
A one-way hash doesn't allow a message to be decoded back to the original value. A two-way hash allows a message to be reconstructed from the hash. Most hashing functions are one way. Two primary standards exist that use the hashing process for encryption:
Secure Hash Algorithm
The Secure Hash Algorithm (SHA) was designed to ensure the integrity of a message. The SHA is a one-way hash that provides a hash value that can be used with an encryption protocol. This algorithm produces a 160-bit hash value. SHA has been updated; the new standard is SHA-1.
Message Digest Algorithm
The Message Digest Algorithm (MD) also creates a hash value and uses a one-way hash. The hash value is used to help maintain integrity. There are several versions of MD; the most common are MD5, MD4, and MD2.
NOTE
Message digests are discussed in detail later in this chapter. The primary thing to know about a message digest is that it's nothing more than text expressed as a single string of digits.
MD5 is the newest version of the algorithm. It produces a 128-bit hash, but the algorithm is more complex than its predecessors and offers greater security.
NOTE
Both SHA-1 and MD5 are good hashing algorithms. The primary difference between the two is speed; MD5 is faster to process than SHA.
LANMAN
Prior to the release of Windows NT, Microsoft's operating systems used the LANMAN protocol for authentication. While functioning only as an authentication protocol, LANMAN used LM Hash and two DES keys. It was replaced by the NT LAN Manager (NTLM) with the release of Windows NT.
NTLM
Microsoft replaced the LANMAN protocol with NTLM (NT LAN Manager) with the release of Windows NT. NTLM uses MD4/MD5 hashing algorithms. Several versions of this protocol exist (NTLMv1, NTLMv2), and it is still in widespread use despite the fact that Microsoft has pointed to Kerberos as being its preferred authentication protocol. While LANMAN and NTLM both employ hashing, they are/were used primarily for the purpose of authentication.
7.2.2. Working with Symmetric Algorithms
Symmetric algorithms require both ends of an encrypted message to have the same key and processing algorithms. Symmetric algorithms generate a secret key that must be protected. A symmetric key—sometimes referred to as a secret key or private key—is a key that isn't disclosed to people who aren't authorized to use the encryption system. The disclosure of a private key breaches the security of the encryption system. If a key is lost or stolen, the entire process is breached. These types of systems are common, but the keys require special handling. Figure 7.4 illustrates a symmetric encryption system; in this example, the keys are the same on each end.
Figure 7.4. Symmetric encryption system

Typically, a new key isn't sent across the encrypted channel (if the current key has been compromised, the new key may also be compromised). Keys are sent using an out-of-band method: by letter, by courier, or by some other method. This approach may be cumbersome, and it may leave the key subject to human error or social engineering exploitation.
The other disadvantage of a symmetric algorithm is that each person who uses the encryption algorithm must have the key. If you want 50 people to access the same messages, all 50 people must have the key. As you can imagine, it's difficult for 50 people to keep a secret. On the other hand, if you want to communicate with 50 different people in private, you need to know who uses which key. This information can be hard to keep straight—you might spend all your time trying to remember who uses which key.
Encryption methods usually use either a block or stream cipher. As the name implies, with a block cipher the algorithm works on chunks of data—encrypting one and then moving to the next. With a stream cipher, the data is encrypted a bit, or byte, at a time.
Several successful encryption systems use symmetric algorithms. A strong algorithm can be difficult to break. Here are some of the common standards that use symmetric algorithms:
Data Encryption Standard
The Data Encryption Standard (DES) has been used since the mid-1970s. It was the primary standard used in government and industry until it was replaced by AES. It's a strong and efficient algorithm based on a 56-bit key. (Strong refers to the fact that it's hard to break.) A recent study showed that a very powerful system could break the algorithm in about two days. DES has several modes that offer security and integrity. However, it has become a little dated as a result of advances in computer technology, and it's being replaced. For its time, it was one of the best standards available.
Advanced Encryption Standard
Advanced Encryption Standard (AES) has replaced DES as the current standard, and it uses the Rijndael algorithm. It was developed by Joan Daemen and Vincent Rijmen. AES is now the current product used by U.S. governmental agencies. It supports key sizes of 128, 192, and 256 bits, with 128 bits being the default.
NOTE
For more information about Rijndael (AES), see its website at http://csrc.nist.gov/encryption/aes/rijndael/.
AES256
AES256 (also often written as AES-256) uses 256 bits instead of 128. This qualifies for U.S. government classification as Top Secret.
Triple-DES
Triple-DES (3DES) is a technological upgrade of DES. 3DES is still used, even though AES is the preferred choice for government applications. 3DES is considerably harder to break than many other systems, and it's more secure than DES.
CAST
CAST is an algorithm developed by Carlisle Adams and Stafford Tavares (hence the name). It's used in some products offered by Microsoft and IBM. CAST uses a 40-bit to 128-bit key, and it's very fast and efficient.
Rivest's Cipher
RC is an encryption family produced by RSA laboratories. RC stands for Rivest's Cipher or Ron's Code. (Ron Rivest is the author of this algorithm.) The current levels are RC5 and RC6. RC5 uses a key size of up to 2,048 bits. It's considered to be a strong system.
Blowfish
Blowfish is an encryption system produced by Counterpane Systems that performs a 64-bit block cipher at very fast speeds. It is a symmetric block cipher than can use variable-length keys. The original author was Bruce Schneier; he next created Twofish, which performs a similar function on 128-bit blocks.
International Data Encryption Algorithm
International Data Encryption Algorithm (IDEA) was developed by a Swiss consortium. It's an algorithm that uses a 128-bit key. This product is similar in speed and capability to DES, but it's more secure. IDEA is used in Pretty Good Privacy (PGP), a public domain encryption system used by many for e-mail. Currently, ASCOM AG holds the right to market IDEA.
7.2.3. Working with Asymmetric Algorithms
Asymmetric algorithms use two keys to encrypt and decrypt data. These asymmetric keys are referred to as the public key and the private key. The public key can be used by the sender to encrypt a message, and the private key can be used by the receiver to decrypt the message. As you may recall, symmetrical systems require the key to be private between the two parties. With asymmetric systems, each circuit has one key.
The public key may be truly public or it may be a secret between the two parties. The private key is kept private and is known only by the owner (receiver). If someone wants to send you an encrypted message, they can use your public key to encrypt the message and then send you the message. You can use your private key to decrypt the message. One of the keys is always kept private. If both keys become available to a third party, the encryption system won't protect the privacy of the message.
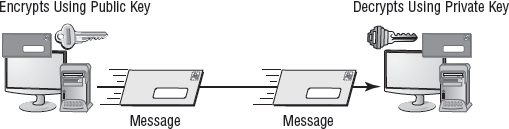
Perhaps the best way to think about this system is that it's similar to a safe deposit box. Two keys are needed: The box owner keeps the public key, and the bank retains the second, or private, key. In order to open the box, both keys must be used simultaneously. Figure 7.5 illustrates the two-key method. Notice that in the encryption process, Key 1 is used to encrypt the message and Key 2 is used to decrypt it. In this way, it's harder to break the code unless both the public and private keys are known.
Figure 7.5. A two-key system in use
NOTE
Two-key systems are referred to as Public Key Cryptography (PKC). Don't confuse this with Public Key Infrastructure (PKI), which uses PKC as a part of the process.
The algorithms used in this two-key process are complicated, and several volumes would be needed to explain them thoroughly. In this book, I'll focus primarily on how the two-key process is used. It's implemented in systems such as Public Key Infrastructure (PKI), which is discussed in more detail later in this chapter.
Four popular asymmetric systems are in use today:
RSA
RSA is named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman. The RSA algorithm is an early public-key encryption system that uses large integer numbers as the basis of the process. It's widely implemented, and it has become a de facto standard. RSA works for both encryption and digital signatures, which are discussed later in the chapter. RSA is used in many environments, including Secure Sockets Layer (SSL).
Diffie-Hellman
Dr. W. Diffie and Dr. M. E. Hellman conceptualized the Diffie-Hellman key exchange. They are considered the founders of the public/private key concept; their original work envisioned splitting the key into two parts. This algorithm is used primarily to send keys across public networks. The process isn't used to encrypt or decrypt messages; it's used merely for the transmission of keys in a secure manner.
Elliptic Curve Cryptography
Elliptic Curve Cryptography (ECC) provides similar functionality to RSA. ECC is being implemented in smaller, less-intelligent devices such as cell phones and wireless devices. It's smaller than RSA and requires less computing power. ECC encryption systems are based on the idea of using points on a curve to define the public/private key pair. This process is less mathematically intensive than processes such as RSA.
Palm, Motorola, Cisco, and others have implemented, or are implementing, the ECC system for security. Palm handhelds can now form secure connections to applications running on other systems using wireless or other means. Motorola recently released its new development system for the next generation of cellular phones; this system implements ECC and other protocols as an integral part of the toolkit. You can expect that ECC will be commonly implemented in cellular devices in the near future.
El Gamal
El Gamal is an algorithm used for transmitting digital signatures and key exchanges. The method is based on calculating logarithms. The process used is similar to the Diffie-Hellman key exchange and is based on the characteristics of logarithmic numbers and calculations. The El Gamal algorithm was first published in 1985. The Digital Signature Algorithm (DSA) is based on El Gamal.

 Watch for the Weakest Link
Watch for the Weakest Link