6.1. Understanding Physical and Network Security
Physical security measures prevent your systems from being accessed in unauthorized ways, primarily by preventing an unauthorized user from physically touching a system or device. Most networked systems have developed high levels of sophistication and security from outside intruders. However, these systems are generally vulnerable to internal attacks, sabotage, and misuse. If an intruder has physical access to your systems, you should never consider them to be secure.
The following sections discuss the aspects of physical security that affect your environment, including access controls, social engineering, and the environment.
6.1.1. Implementing Access Control
Access control is a critical part of physical security. Systems must operate in controlled environments in order to be secure. These environments must be, as much as possible, safe from intrusion. Computer system consoles can be a vital point of vulnerability because many administrative functions can be accomplished from the system console. These consoles, as well as the systems themselves, must be protected from physical access. Two areas that help make a system secure are physical barriers and biometrics, both of which are discussed in the following sections.
6.1.1.1. Physical Barriers
A key aspect of access control involves physical barriers. The objective of a physical barrier is to prevent access to computers and network systems. The most effective physical barrier implementations require that more than one physical barrier be crossed to gain access. This type of approach is called a multiple barrier system.
Ideally, your systems should have a minimum of three physical barriers. The first barrier is the external entrance to the building, referred to as a perimeter, which is protected by burglar alarms, external walls, surveillance, and so on. The second barrier is the entrance to the computer center, which is behind a locked door, and could rely upon such items as ID badges, fobs, or keys to gain access. The third barrier is the entrance to the computer room itself. Each of these entrances can be individually secured, monitored, and protected with alarm systems. Figure 6.1 illustrates this concept.
Figure 6.1. The three-layer security model

Although these three barriers won't always stop intruders, they will potentially slow them down enough that law enforcement can respond before an intrusion is fully developed. Once inside, a truly secure site should be dependent upon a physical token for access to the actual network resources.
NOTE
Physical tokens are anything that a user must have on them to access network resources and are often associated with devices that enable the user to generate a one-time password authenticating their identity. SecurID, from RSA, is one of the best known examples of a physical token, and information on it can be found at http://www.rsa.com/node.aspx?id=1156.
NOTE
No matter how secure you think your system is, you'll never be able to stop everyone. But your goal is to stop those who are less than fanatic and slow down the ones who are. As an analogy, the front door of your home may contain a lock and a deadbolt. This minimal security is enough to convince most burglars to try somewhere less secure. A fanatic who is bent on entering your home, however, could always take a chain saw or similar tool to the door.
High-security installations use a type of intermediate access-control mechanism called a mantrap (also occasionally written as man-trap). Mantraps require visual identification, as well as authentication, to gain access. A mantrap makes it difficult for a facility to be accessed in number because it allows only one or two people into the facility at a time. It's usually designed to physically contain an unauthorized, potentially hostile person until authorities arrive. Figure 6.2 illustrates a mantrap. Notice in this case that the visual verification is accomplished using a security guard. A properly developed mantrap includes bulletproof glass, high-strength doors, and locks. In high-security and military environments, an armed guard, as well as video surveillance, would be placed at the mantrap. After you're inside the facility, additional security and authentication may be required for further entrance.
Figure 6.2. A mantrap in action

NOTE
Some mantraps even include scales to weigh the person. While the weight can be used to help identify a person, often the scales are used to make certain no one is sneaking in. If the weight of the scale appears too high, an officer can check to make sure two people haven't crowded in and are attempting to quickly bypass security.
The following sections discuss perimeter security, the establishment of security zones, and partitioning.
6.1.1.1.1. Perimeter Security
Perimeter security, whether physical or technological, is the first line of defense in your security model. In the case of a physical security issue, the intent is to prevent unauthorized access to resources inside a building or facility.
The network equivalent of physical perimeter security is intended to accomplish for a network what perimeter security does for a building. How do you keep unauthorized intruders from gaining access to systems and information in the network through the network?
In the physical environment, perimeter security is accomplished using locks, doors, surveillance systems, and alarm systems. This isn't functionally any different from a network, which uses border routers, intrusion detection systems, and firewalls to prevent unauthorized access. Figure 6.3 illustrates the systems used to prevent network intrusion.
Few security systems can be implemented that don't have weaknesses or vulnerabilities. A determined intruder can, with patience, overcome most security systems. The task may not be easy, and it may require careful planning and study; however, a determined adversary can usually figure out a way.
Figure 6.3. Network perimeter defense

If you want to deter intruders from breaking into your building, you can install improved door locks, coded alarm systems, and magnetic contacts on doors and windows. Remember that you can't always keep an intruder out of your building; however, you can make an intrusion riskier and more likely to be discovered if it happens.
|
Real World Scenario: Circumventing SecurityRecently, a small business noticed that the level of network traffic seemed to be very high in the late evening and early morning. The business couldn't find a network-related reason why this was happening. Upon investigation, the security consultant found that a part-time employee had established a multiuser game server in his office. The game server was set to turn on after 10:00 p.m. and turn off at 5:30 a.m. This server was hidden under a desk, and it supported around 30 local game players. The part-time employee didn't have a key to the building, so an investigation was conducted to determine how he gained access to the building after hours. The building had electronic locks on its outside entrances, and a pass card was needed to open the doors. However, the door locks were designed to automatically unlock when someone was leaving the building. The investigation discovered that the employee and a friend had figured out a way to slide a piece of cardboard under one of the external doors, which activated the door mechanisms and unlocked the doors. The intruders took advantage of this weakness in the doors to gain access after hours without using a passcard and then used the server to play games in his office. |
6.1.1.1.2. Security Zones
A security zone is an area in a building where access is individually monitored and controlled. A large network, such as a large physical plant, can have many areas that require restricted access. In a building, floors, sections of floors, and even offices can be broken down into smaller areas. These smaller zones are referred to as security zones. In the physical environment, each floor is broken into separate zones. An alarm system that identifies a zone of intrusion can inform security personnel about an intruder's location in the building; zone notification tells them where to begin looking when they enter the premises.
The concept of security zones is as old as security itself. Most burglar alarms allow the creation of individual zones within a building or residence; these zones are treated separately. When you go to bed, for example, the alarm shouldn't monitor the bedroom for movement because it's perfectly acceptable there.
Real World Scenario: Security Zones in the Physical EnvironmentAs a security administrator, you'll need to evaluate your workplace and think of physical zones that should exist in terms of different types of individuals who might be present. If your workplace is already divided into zones, forget that this has been done and start from scratch. Answer the following questions:
You should evaluate your environment routinely to make certain the zones that exist within your security plan are still relevant. Always start from scratch and pretend that no zones exist; then verify that the zones that do exist are the same as those you've created from this exercise. |
The networking equivalent of a security zone is a network security zone. They perform the same function. If you divide a network into smaller sections, each zone can have its own security considerations and measures—just like a physical security zone. Figure 6.4 illustrates a larger network being broken down into three smaller zones. Notice that the first zone also contains a smaller zone where high-security information is stored. This arrangement allows layers of security to be built around sensitive information. The division of the network is accomplished by implementing virtual LANs (VLANs) and instituting demilitarized zones (DMZs), both of which are discussed in Chapter 1, "General Security Concepts."
6.1.1.1.3. Partitioning
Partitioning a network is functionally the same as partitioning a building. In a building, walls exist to direct pedestrian flow, provide access control, and separate functional areas. This process allows information and property to be kept under physical lock and key.
Figure 6.4. Network security zones

|
Hallways in an office building are usually built differently from internal office space. Hallways are usually more flame resistant, and they're referred to as fire corridors. These corridors allow people in the building to escape in the event of a fire. Fire corridor walls go from the floor to the ceiling, whereas internal walls can stop before they reach the ceiling (most office buildings have a false ceiling in them to hold lighting, wiring, and plumbing).
Network partitioning accomplishes the same function for a network as physical partitioning does for a building. Buildings have physical walls, whereas network partitioning involves the creation of private networks within larger networks. Partitions can be isolated from each other using routers and firewalls.
Therefore, while the network systems are all connected using wire, the functional view is that of many smaller networks. Figure 6.5 shows a partitioned network. It's important to realize that unless a physical device (such as a router) separates these partitioned networks, all the signals are shared across the wire. This device accomplishes the same function as a hallway or locked door—from a purely physical perspective.
NOTE
Partitioning and security zones are essentially interchangeable. Typically, partitioning is more narrowly focused than zones, but this need not always be the case. In a typical installation, a zone would encompass one floor, while a partition would include one room.
Figure 6.5. Network partitioning separating networks from each other in a larger network

6.1.1.2. Biometrics
Biometric systems use some kind of unique biological trait to identify a person, such as fingerprints, patterns on the retina, and handprints. Some of the devices that are used are hand scanners, retinal scanners, and, potentially, DNA scanners, which can be used as part of the access control mechanisms. These devices should be coupled into security-oriented computer systems that record all access attempts. They should also be under surveillance in order to prevent individuals from bypassing them.
These technologies are becoming more reliable, and they will become widely used over the next few years. Many laptops sold now have a fingerprint reader built in. The costs associated with these technologies have fallen drastically in recent years.
6.1.2. Understanding Social Engineering
Social engineering is the process by which intruders gain access to your facilities, your network, and even to your employees by exploiting the generally trusting nature of people. A social engineering attack may come from someone posing as a vendor or as e-mail from a (supposedly) traveling executive who indicates that they have forgotten how to log on to the network or how to get into the building over the weekend. It's often difficult to determine whether the individual is legitimate or has nefarious intentions.
NOTE
Occasionally, social engineering is also referred to as wetware. This term is used because it is a form of hacking that does not require software or hardware but rather the gray matter of the brain.
Social engineering attacks can develop subtly. They're also hard to detect. Let's look at some classic social engineering attacks:
Someone enters your building wearing a white lab jacket with a logo on it. He also has a toolkit. He approaches the receptionist and identifies himself as a copier repairman from a major local copier company. He indicates that he's here to do preventive service on your copier. In most cases, the receptionist will let him pass and tell him where the copier is. Once the "technician" is out of sight, the receptionist probably won't give him a second thought. Your organization has just been the victim of a social engineering attack. The attacker has now penetrated your first and possibly even your second layer of security. In many offices, including security-oriented offices, this individual would have access to the entire organization and would be able to pass freely anywhere he wanted. This attack didn't take any particular talent or skill other than the ability to look like a copier repairman. Impersonation can go a long way in allowing access to a building or network.
The next example is a true situation; it happened at a high-security government installation. Access to the facility required passing through a series of manned checkpoints. Professionally trained and competent security personnel manned these checkpoints. An employee decided to play a joke on the security department: He took an old employee badge, cut his picture out of it, and pasted in a picture of Mickey Mouse. He was able to gain access to the facility for two weeks before he was caught.
Social engineering attacks like these are easy to accomplish in most organizations. Even if your organization uses biometric devices, magnetic card strips, or other electronic measures, social engineering attacks are still relatively simple. A favorite method of gaining entry to electronically locked systems is to follow someone through the door they just unlocked, a process known as tailgating. Many people don't think twice about this event—it happens all the time.
NOTE
Famed hacker Kevin Mitnick wrote a book called The Art of Deception: Controlling the Human Element of Security (Wiley Publishing, Inc., 2002), in which 14 of the 16 chapters are devoted to social engineering scenarios that have been played out. If nothing else, the fact that one of the most notorious hackers known—who could write on any security subject he wants—chose to write a book on social engineering should emphasize the importance of the topic to you.
As an administrator, one of your responsibilities is to educate users on how to avoid falling prey to social engineering attacks. They should know the security procedures that are in place and follow them to a tee. You should also have a high level of confidence that the correct procedures are in place, and one of the best ways to obtain that confidence is to check your users on occasion.
Preventing social engineering attacks involves more than just training on how to detect and prevent them. It also involves making sure people stay alert. One form of social engineering is known as shoulder surfing and involves nothing more than watching someone when they enter their sensitive data. They can see you entering a password, typing in a credit card number, or entering any other pertinent information. The best defense against this type of attack is simply to survey your environment before entering personal data.
Social engineering is easy to do, even with all of today's technology at our disposal. Education is the one key that can help.
Don't overlook the most common personal motivator of all: greed. It may surprise you, but people can be bribed to give away information. If someone gives out the keys, you won't necessarily know it has occurred. Those keys can be literal—as in the keys to the back door—or figurative—the keys to decrypt messages.
NOTE
The movie and book The Falcon and the Snowman detailed the accounts of two young men, Christopher Boyce and Daulton Lee, who sold sensitive United States codes to the Russians for several years. The damage they did to U.S. security efforts was incalculable. In another case, U.S. Navy Petty Officer John Walker sold electronic key sets to the Russians that gave them access to communications between the U.S. Navy and the nuclear submarine fleet in the Atlantic. Later, he sold information and keys on ground forces in Vietnam. His actions cost the U.S. Army countless lives. During the height of his activities, he recruited family members and others to gather this information for him. In each of these cases, money was the motivating factor that led them to commit these crimes.
It is often a comforting thought to think that we cannot be bought. We look to our morals and standards and think that we are above being bribed. The truth of the matter, though, is that almost everyone has a price. Your price may be so high that for all practical purposes you don't have a price that anyone in the market would pay, but can the same be said for the other administrators in your company?
Social engineering can have a hugely damaging effect on a security system, as the previous note illustrates. Always remember that a social engineering attack can occur over the phone, by e-mail, or by a visit. The intent is to acquire access information, such as user IDs and passwords.
6.1.3. Scanning the Environment
The environment in which your business operates is bigger than the mere physical facility that houses your computers and employees. It also includes wireless cells, physical locations, shielding, and fire suppression. The following sections discuss these four areas to help you prepare for the exam.
6.1.3.1. Wireless Cells
The advent of wireless technology has created a wealth of solutions and problems for security professionals. The ability to use small, low-powered devices, such as cell phones, makes this technology attractive for mobile workers. Manufacturers now make smart phones that can also act as PDAs. Adapters are available for most PC systems that allow them connection to cell phones. New cell sites are being added internationally, and the coverage area of cell phones is increasing exponentially.
The technology is based upon small, low-powered transmitters located strategically throughout a coverage area. A cell provider is given approximately 800 separate frequencies to use in a coverage area. The frequencies are then broken down into roughly 56 channels in a single cell. Figure 6.6 shows this coverage scheme.
Figure 6.6. A cell system in a metropolitan area

The individual cells have a high level of computer intelligence, and they hand off conversations to each other automatically. Cell phones in the United States operate in the 824MHz to 894MHz range. The Federal Communications Commission (FCC) requires police scanners to bypass these frequencies in the United States; most other countries don't require this frequency blocking in communications equipment.
|
NOTE
It's a federal crime to monitor or eavesdrop on cell phone frequencies, though there are exceptions, as with the Patriot Act.
Cell phones use analog as well as digital transmission capabilities. The analog cell systems allow approximately 60 simultaneous conversations to occur in a single cell. Digital technology expands that to about 180 simultaneous conversations. New applications, which will allow for cell-based banking and other transactions, are being added to cell technology.
Global System for Mobile Communications (GSM), the newest standard for cell systems, offers encryption. GSM works in conjunction with a Subscriber Identification Module (SIM), allowing users to change phones. The SIM is a removable card that can be moved from one phone to another. Unfortunately, U.S. and European cell standards aren't interchangeable, although many manufacturers are now selling dual-mode phones.
Many people believe that cell phones are untraceable and that you can't determine the location of a cellular user. This isn't the case. When a cell phone is turned on, it immediately identifies itself to the cell that is closest to it. The cell systems can triangulate a cell user to within a few feet. This can be done even if the phone isn't in use but is merely turned on. The point of origin can be determined in only a few moments because the process is largely computerized.
Real World Scenario: Securing Your Wireless DevicesYou've become increasingly concerned about secure access to your network using wireless devices. Many managers and other employees use wireless personal digital assistants (PDAs) to communicate when they're away from the office. What can you do to secure these devices? You may want to implement a wireless security protocol (such as Wireless Transport Layer Security [WTLS] or Elliptic Curve Cryptography [ECC]) in these devices and in your network. Doing so would allow communications to occur between wireless users and your network. |
6.1.3.2. Physical Location
The location of your computer facility is critical to its security. Computer facilities must be placed in a location that is physically possible to secure. Additionally, the location must have the proper capabilities to manage temperature, humidity, and other environmental factors necessary to the health of your computer systems. The following sections look at environmental and power systems.
6.1.3.2.1. Environmental Systems
Many computer systems require temperature and humidity control for reliable service. The larger servers, communications equipment, and drive arrays generate considerable amounts of heat; this is especially true of mainframe and older minicomputers. An environmental system for this type of equipment is a significant expense beyond the actual computer system costs. Fortunately, newer systems operate in a wider temperature range. Most new systems are designed to operate in an office environment.
If the computer systems you're responsible for require special environmental considerations, you'll need to establish cooling and humidity control. Ideally, systems are located in the middle of the building, and they're ducted separately from the rest of the HVAC system. It's a common practice for modern buildings to use a zone-based air conditioning environment, which allows the environmental plant to be turned off when the building isn't occupied. A computer room will typically require full-time environmental control.
NOTE
Environmental systems should be monitored to prevent the computer center's humidity level from dropping below 50 percent. Electrostatic damage is likely to occur when humidity levels get too low.
Humidity control prevents the buildup of static electricity in the environment. If the humidity drops much below 50 percent, electronic components are extremely vulnerable to damage from electrostatic shock. Most environmental systems also regulate humidity; however, a malfunctioning system can cause the humidity to be almost entirely extracted from a room. Make sure that environmental systems are regularly serviced.
Environmental concerns also include considerations about water and flood damage as well as fire suppression. Computer rooms should have fire and moisture detectors. Most office buildings have water pipes and other moisture-carrying systems in the ceiling. If a water pipe bursts (which is common in minor earthquakes), the computer room could become flooded. Water and electricity don't mix. Moisture monitors would automatically kill power in a computer room if moisture were detected.
Fire, no matter how small, can cause damage to computer systems. Apart from the high heat, which can melt or warp plastics and metals, the smoke from the fire can permeate the computers. Smoke particles are large enough to lodge under the read/write head of a hard disk, thereby causing data loss. In addition, the fire-suppression systems in most buildings consist of water under pressure, and the water damage from putting out even a small fire could wipe out an entire data center.
|
NOTE
Fire suppression is discussed further in this chapter in the section by the same name, "Fire Suppression."
6.1.3.2.2. Power Systems
Computer systems are susceptible to power and interference problems. A computer requires a steady input of AC power to produce reliable DC voltage for its electronic systems. Power systems are designed to operate in a wide band of power characteristics; they help keep the electrical service constant, and they ensure smooth operations.
NOTE
Major fluctuations in AC power can contribute to a condition known as chip creep. With creep, unsoldered chips slowly work their way loose and out of a socket over time.
The following products solve most electrical line problems:
Surge protectors
Surge protectors protect electrical components from momentary or instantaneous increases (called spikes) in a power line. Most surge protectors shunt a voltage spike to ground through the use of small devices called metal oxide varistors (MOVs). Large-scale surge protectors are usually found in building power supplies or at power-feed points in the building. Portable surge protectors can be purchased as part of an extension cord or power strip. If subsequent surges occur, the surge protector may not prevent them from being passed through the line to the computer system. Surge protectors are passive devices, and they accomplish no purpose until a surge occurs.
Power conditioners
Power conditioners are active devices that effectively isolate and regulate voltage in a building. They monitor the power in the building and clean it up. Power conditioners usually include filters, surge suppressors, and temporary voltage regulation. They can also activate backup power supplies. Power conditioners can be part of the overall building power scheme; it's also common to see them dedicated strictly to computer rooms.
Backup power
Backup power is generally used in situations where continuous power is needed in the event of a power loss. These types of systems are usually designed for either short-term, as in the case of a battery backup system, or long-term uses, as in an uninterruptible power supply (UPS). UPS systems generally use batteries to provide short-term power. Longer-term backup power comes from power generators that frequently have their own power-loss-sensing circuitry. Power generators kick in if a power loss is detected, and they provide power until disabled. The generators require a short amount of time to start providing power, and the battery backup systems provide time for the generators to come online. Most generator systems don't automatically turn off when power is restored to a building—they're turned off manually. This is necessary because it's common for several false starts to occur before power is restored from the power grid.
Most power generators are either gas or diesel operated, and they require preventive maintenance on a regular basis. These systems aren't much use if they don't start when needed or they fail because no oil is in the motor. Newer systems are becoming available that are based on fuel cell technology; they will probably be very reliable and require less maintenance.
6.1.3.3. Shielding
Shielding refers to the process of preventing electronic emissions from your computer systems from being used to gather intelligence and to preventing outside electronic emissions from disrupting your information-processing abilities. In a fixed facility, such as a computer center, surrounding the computer room with a Faraday cage can provide electronic shielding. A Faraday cage usually consists of an electrically conductive wire mesh or other conductor woven into a "cage" that surrounds a room. The conductor is then grounded. Because of this cage, few electromagnetic signals can either enter or leave the room, thereby reducing the ability to eavesdrop on a computer conversation. In order to verify the functionality of the cage, radio frequency (RF) emissions from the room are tested with special measuring devices.
The following section discusses the problems of electromagnetic and radio frequency interference.
6.1.3.3.1. Electromagnetic Interference and Radio Frequency Interference
Electromagnetic interference (EMI) and radio frequency interference (RFI) are two additional environmental considerations. Motors, lights, and other types of electromechanical objects cause EMI, which can cause circuit overload, spikes, or electrical component failure. Making sure that all signal lines are properly shielded and grounded can minimize EMI. Devices that generate EMI should be as physically distant from cabling as is feasible because this type of energy tends to dissipate quickly with distance.
Figure 6.7 shows a motor generating EMI. In this example, the data cable next to the motor is picking up the EMI. This causes the signal to deteriorate, and it might eventually cause the line to be unusable. The gray area in the illustration is representative of the interference generated by the motor.
RFI is the by product of electrical processes, similar to EMI. The major difference is that RFI is usually projected across a radio spectrum. Motors with defective brushes can generate RFI, as can a number of other devices. If RF levels become too high, it can cause the receivers in wireless units to become deaf. This process is called desensitizing, and it occurs because of the volume of RF energy present. This can occur even if the signals are on different frequencies.
Figure 6.8 demonstrates the desensitizing process occurring with a wireless access portal (WAP). The only solutions in this situation would be to move the devices farther apart or to turn off the RFI generator.
Figure 6.7. Electromagnetic interference (EMI) pickup in a data cable

Figure 6.8. RF desensitization occurring as a result of cellular phone interference

Real World Scenario: Project TEMPESTTEMPEST is the name of a project commenced by the U.S. government in the late 1950s. TEMPEST was concerned with reducing electronic noise from devices that would divulge intelligence about systems and information. This program has become a standard for computer systems certification. TEMPEST shielding protection means that a computer system doesn't emit any significant amounts of EMI or RFI. For a device to be approved as a TEMPEST, it must undergo extensive testing, done to exacting standards that the U.S. government dictates. Today, control zones and white noise are used to accomplish the shielding. TEMPEST-certified equipment frequently costs twice as much as non-TEMPEST equipment. |
6.1.3.4. Fire Suppression
Fire suppression is a key consideration in computer-center design. Fire suppression is the act of actually extinguishing a fire versus preventing one. Two primary types of fire-suppression systems are in use: fire extinguishers and fixed systems.
6.1.3.4.1. Fire Extinguishers
Fire extinguishers are portable systems. The selection and use of fire extinguishers is critical. Four primary types of fire extinguishers are available, classified by the types of fires they put out: A, B, C, and D. Table 6.1 describes the four types of fires and the capabilities of various extinguishers.
| Type | Use | Retardant Composition |
|---|---|---|
| A | Wood and paper | Largely water or chemical |
| B | Flammable liquids | Fire-retardant chemicals |
| C | Electrical | Nonconductive chemicals |
| D | Flammable metals | Varies, type specific |
Several multipurpose types of extinguishers combine extinguisher capabilities in a single bottle. The more common multipurpose extinguishers are A-B, B-C, and ABC.
The recommended procedure for using a fire extinguisher is called the PASS method: Pull, Aim, Squeeze, and Sweep. Fire extinguishers usually operate for only a few seconds—if you use one, make sure you don't fixate on a single spot. Most fire extinguishers have a limited effective range of from three to eight feet.
NOTE
A major concern with electrical fires is that they can reoccur quickly if the voltage isn't removed. Make sure you remove voltage from systems when a fire occurs.
Most fire extinguishers require an annual inspection. This is a favorite area of citation by fire inspectors. You can contract with services to do this on a regular basis: They will inspect or replace your fire extinguishers according to a scheduled agreement.
6.1.3.4.2. Fixed Systems
Fixed systems are usually part of the building systems. The most common fixed systems combine fire detectors with fire-suppression systems, where the detectors usually trigger either because of a rapid temperature change or because of excessive smoke. The fire-suppression system uses either water sprinklers or fire-suppressing gas. Water systems work with overhead nozzles, as illustrated in Figure 6.9. These systems are the most common method in modern buildings. Water systems are reliable and relatively inexpensive and require little maintenance.
Figure 6.9. Water-based fire-suppression system
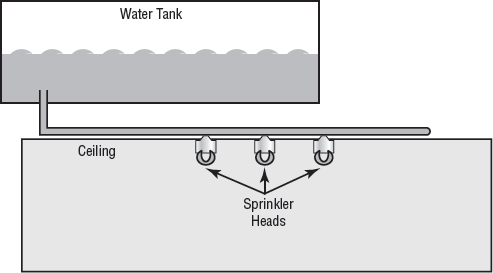
The one drawback to water-based systems is that they cause extreme damage to energized electrical equipment such as computers. These systems can be tied into relays that terminate power to computer systems before they release water into the building.
Gas-based systems were originally designed to use carbon dioxide and later Halon gas. Halon gas isn't used anymore because it damages the ozone layer; environmentally acceptable substitutes are now available. The principle of a gas system is that it displaces the oxygen in the room, thereby removing this necessary component of a fire.
|
The major drawback to gas-based systems is that they require sealed environments to operate. Special ventilation systems are usually installed in gas systems to limit air circulation when the gas is released. Gas systems are also expensive, and they're usually only implemented in computer rooms or other areas where water would cause damage to technology or other intellectual property.

