Once you have a good inventory of the I/O devices on the network and have identified what kind of unapproved devices you might find, you must enumerate which operating systems (and versions) are in use throughout the organization.
It used to be that you would find only one type of operating system on a network. With the advent of mobile computing, Internet business, and corporate mergers, networks have become more complex and diverse. Typical computer examinations must adapt to the fast-changing and diverse world in which computer forensic science examiners work. Before you can begin a forensic investigation, you must be familiar with various operating systems you might encounter.
Commonly Encountered Operating Systems
operating system
Acts as a director and interpreter between the user and all the software and hardware on the computer.
Not only do various operating systems exist, but each operating system has multiple versions, such as server and workstation, and new releases. How you handle and extract information from a computer running Linux will be very different from how you handle and extract information from a Windows computer.
Windows
Although you probably won’t find it in use anymore, Microsoft’s first attempt at a graphical operating system was Microsoft Windows 1 in 1985. Many subsequent versions of Microsoft Windows have been released. Table 2-1 highlights a few of the better-known versions of Windows that you might encounter on older systems.
In 1995, Microsoft introduced Windows 95, which was a significant improvement over Windows 3.x and was Microsoft’s first truly consumer-oriented graphical operating system for PCs. Windows NT came into its own with Windows NT 4: It was released in 1996 and became quite popular in the late 1990s. Then, along came Windows 98, followed by Windows 2000 and Windows Me (Millennium Edition). In 2001, Windows XP made its appearance, followed by Windows Server 2003. In 2006, Windows Vista was released, and two years later Windows Server 2008 came on the scene. Microsoft’s latest release for workstations is Windows 7, and Windows Server 2008 R2 (Release 2) for servers. The most common Microsoft systems you will encounter are Windows XP, Windows Vista, and Windows 7.
Table 2-1: Early Windows Graphical Operating Systems
| Version | Release date | Description |
| Windows 1 | 1985 | Microsoft’s first attempt at a graphical operating system |
| Windows 3.1 | 1992 | Used in the early 1990s prior to creation of Windows 95 |
| Windows 3.11 | 1993 | Used in early 1990s prior to creation of Windows 95 |
| Windows for Workgroups 3.11 | 1994 | Allowed resource sharing between users without aid of a central authentication server |
| Windows NT | 1994 | NT stands for New Technology. It was specifically designed for the corporate environment and intended for use on high-powered servers and workstations |
| Windows 95 | 1995 | Popular in late 1990s; more than a million copies were sold in the first four days after it was released |
UNIX/Linux
The UNIX operating system was originally created at AT&T’s Bell Laboratories and licensed freely to most universities and research facilities. UNIX was designed to allow a number of programmers to simultaneously access a single computer and share its resources. The operating system coordinates the use of the computer’s resources, and it controls all of the commands from all of the keyboards and all of the data being generated. It permits each user to work as if he or she were the only person working on the computer.
Bell Labs distributed the operating system in its source language form. By the end of the1970s, dozens of different versions of UNIX were available. The success of the UNIX operating system has led to many technologies that are part of the IT environment today. Although UNIX is often installed on mainframes, versions of UNIX have found their way into the PC world. Some of the different versions available are BSD, HP-UX, SCO, IBX AIX, Sun Solaris, and Digital.
open source
Code that the code creator makes available under a license that permits end users to freely redistribute, make modifications of, and create derivative works of the source code.
Linux is a UNIX-like operating system that was written by Linus Torvalds in 1991. Originally named Freax, it was hosted on the Minix operating system. Linux is an open source operating system, whichmeans that its source code is readily and freely available online, and that users can either purchase commercial distributions at low cost, or “roll their own” at no cost, if they prefer.
Ready availability has allowed thousands of people to contribute patches, fixes, and improvements. Installing Linux has become easier as the versions and products have evolved. The earlier versions were all text-based and, frequently, hardware support had to be compiled into the kernel. Newer versions have graphical-based installations, making the process much less complicated. Various versions of Linux are available. Some of the more popular ones are Mandrake, SuSE, Caldera, MkLinux, Debian, Slackware, and Red Hat. You will probably encounter Red Hat most often.
Macintosh and Mac OS
Apple introduced the Macintosh line of personal computers in 1984. The first Macintosh, or Mac for short, had 128 KB of memory and a unique design. The monitor and floppy disk drive were built into the same cabinet that housed its main circuitry. In 1994, Apple introduced the PowerMac. In 1998, the third generation of Macs was born with the release of the iMac.
Early versions of the Macintosh operating system were called System x.x, where x.x was the version number. With the release of Mac OS 8, however, Apple dropped the word “System.” Now the versions are simply known as Mac OS with a version number. The most current version is OS X (so called because X is the Roman numeral for 10), based on the UNIX BSD operating system. Macs are popular for high-end users and graphic or drawing applications, such as CAD. You might encounter Mac OS 8, 9, and X.
Other Operating Systems
The first operating system used on the earliest IBM PCs was called the Disk Operating System (DOS). Microsoft’s version of DOS is the most common one and is called MS-DOS. Those of you who have been around the computing environment for a while might remember that IBM Corporation also produced a DOS product called PC-DOS. If you run into a DOS machine, you probably won’t find a mouse and you certainly won’t find a colorful screen. To run a DOS operating system, you issue commands at a prompt on the screen.
Freespire, formerly called Linspire (and originally, Lindows), is a full-featured operating system like Microsoft Windows 7 or Apple Mac OS. It runs Windows applications on top of Linux so they appear as they would in a native Windows environment. Various virtual machine environments are also available for Windows, Linux, UNIX, and Mac OS. These environments permit various different guest operating systems to run on top of those host OSes as well.
Mobile device operating systems (smartphones and such) are not as complex as those for PCs. Mobile devices run a variety of operating systems that include 3Com’s Palm OS, Symbian, Google Android, Microsoft Windows Mobile, or iPhone OS (iOS). Windows Mobile (version 7 is now shipping) is a Microsoft product that supports color displays, graphics, Word, Excel, and built-in MP3 players or MPEG movie players. Other mobile OS offerings likewise support a broad range of screen resolutions, dynamic input areas, improved network communication, and Bluetooth. Of these, Google Android appears to be grabbing ever-increasing mind and market share.
Know Your Local File Systems
file system
An operating system’s method for organizing, managing, and accessing files through logical structures on a hard drive.
File systems enable an operating system to find files requested from a hard disk. The file system keeps a table of contents of the files on the disk. When a file is requested, the table of contents is searched to locate and access the file.
cluster
Also referred to as an allocation unit, a unit of disk space that’s allocated for files and directories.
To understand this better, let’s take a quick look at hard disks. The hard disk on which an operating system is installed is broken into large pieces called clusters or allocation units. Each cluster contains a number of sectors. A disk partition contains those sectors. Without additional support, each partition would be one large unit of data. Operating systems add a directory structure to assign names to each file and manage the free space available to create new files. The directory structure and method for organizing a partition is called a file system.
Different file systems reflect different operating system requirements. Some work better on small machines; others work better on large servers. The same hard disk can have partitions with file systems belonging to DOS, Windows, or Linux. When more than one file system type is installed on a hard drive, this is called a multiboot or dual-boot configuration.
FAT/NTFS
File Allocation Table (FAT)
A simple file system used by DOS, but supported by later Microsoft (and other) operating systems. The FAT resides at the beginning of a disk partition and acts as a table of contents for stored data.
A file system keeps a table of contents (TOC) of files on a drive. When a file is requested, that TOC is searched to locate and access the file. One common file system is File Allocation Table (FAT). Each cluster has an entry in the FAT that describes how it is used. The operating system uses FAT entries to chain together clusters that form files.
In the 1970s, PC file systems were designed to support floppy disks. Hard disk support came later. DOS uses the FAT file system, which is also supported by all other DOS- and Windows-based operating systems. Early versions of DOS used FAT12. The FAT system for later versions of DOS and older versions of Windows 95 is called FAT16. It is simple, reliable, and uses little storage. The FAT is stored at the beginning of the partition to act as the table of contents. To protect the partition, two copies of the FAT are kept in the event that one becomes damaged. The FAT structure doesn’t have a lot of organization; files are given the first open location on the disk.
Virtual FAT (VFAT)
Also called FAT32, an enhanced version of the FAT file system that allows for names longer than the 8.3 convention and uses smaller allocation units on the disk.
Virtual FAT (VFAT) or FAT32, is an enhanced version of the FAT file system. It’s available in Windows 95 and early versions of Windows NT. It allows files to have longer names than the 8.3 convention adopted by DOS. FAT32 also accommodates the use of smaller allocation units on a disk. The 8.3 convention is the original FAT file naming system, in which filenames could be up to eight characters long and files had three character extensions, or less, such as .txt, .doc, .ext, .bat, .bin, and so forth.
extended FAT (exFAT)
Sometimes (and incorrectly) called FAT64, this extended version of the FAT file system was developed to keep FAT working with the kinds of large hard disks (1 TB and larger) now so widely installed in modern desktop and notebook PCs.
The extended FAT (exFAT) file system is an enhanced version of VFAT/FAT32. This file system is available in Windows Vista SP1, Windows 7, and Windows Server 2008 (and for embedded devices on Windows Embedded Compact 6.0—often referred to as Windows CE or Windows Embedded CE—and newer versions). It supports disk partitions of up to 64 zettabytes (ZB); 512 TB is the current recommended maximum. Individual files can be as large as 16 Exabytes, but are also subject to the 512 TB partition limit (or smaller). The exFAT file system also supports nearly 2.8 million files per directory (up from 65,535 in FAT32), and improved free space allocation and delete performance.
New Technology File System (NTFS)
A file system supported by Windows NT and higher-level Windows operating systems, including Windows Server 2000, 2003, and 2008, and Windows XP, Vista, and 7.
The New Technology File System (NTFS) was developed expressly for versions of Windows NT and Windows 2000. Windows NT supports NTFS 4 and Windows 2000 and higher support NTFS 5. Windows Vista and Windows Server 2008 and higher support NTFS 6. Only Windows NT and higher Windows operating systems can use data on an NTFS volume. NTFS organizes files into directories, which are then sorted. It also keeps track of transactions against the file system, making it a recoverable file system. The following graphic shows a copy of the file structure on a Windows 7 computer.
Figure 2-7: Windows folder hierarchy structure is laid out clearly in this treemap listing from WinDirStat.
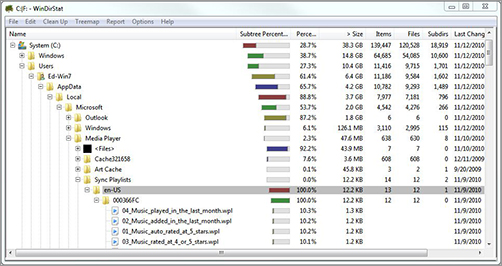
Notice the lines on the left side of the screen. Those lines indicate how many directories deep you are. In modern Windows versions file structures can go 20 or more levels deep.
Various UNIX/Linux File Systems
UNIX has been around for decades, making it the oldest of all file systems used on PC hardware. Also, UNIX file systems probably differ the most from other file systems used on PCs. The UNIX file system is organized as a hierarchy of directories starting from a single directory called root, which is represented by a slash (/).
UNIX looks at all disks and storage devices as part of one file system. Likewise, all Linux files are in one tree; there is no concept of drives such as A, B, C, and D. Storage devices are linked to the directory structure. In other words, a floppy disk may be accessed at /mnt/floppy and a CD-ROM on /cdrom. Any subdirectories that are created use the storage space assigned to their parent directory—unless they are assigned their own storage space. Filenames are case sensitive, so TEST and test are two different files.
The Linux operating system supports multiple and different file systems. To enable upper levels of the OS core to deal with these file systems, Linux defines an intermediary layer, known as the Virtual File System (VFS). Just as in UNIX, there are no drive letters in Linux. Instead, Linux creates a virtual file system, which makes all files on all devices appear to exist on one device. In Linux, as with UNIX, there is one root directory, and every file you can access is located under it.
Second/Third Extended Filesystems (ext2/ext3)
State-based filesystems used by the Linux operating system.
Second/Third Extended Filesystems (ext2/ext3) are state-based file systems. This means the file system maintains state for all open files in memory—in other words, all open files have corresponding entries in data structures in memory.
Beginning with Red Hat Linux 7.2, the default file system changed from the ext2 format to the journaling ext3 file system. The ext3 file system is an enhanced version of the ext2 file system. It keeps logs and checkpoints for all transactions so that a file system check is no longer necessary after an unclean system shutdown. This way, if a system crashes, it can restore the file system using those logs.
Network File System (NFS)
Provides remote access to shared file systems across networks. The primary function of NFS is to mount directories to other computers. These directories can then be accessed as though they were local.
The Network File System (NFS) was originally developed at Sun Microsystems in the 1980s to create a file system for diskless clients (networked computers with no local storage devices that rely upon servers for all their storage needs). NFS provides network access to shared file systems. The primary function of NFS is to mount directories to other computers. These directories can then be accessed as though they were local. This works the same way that mapped drives work in Microsoft networking.
Other File Systems
We’ve covered several file systems in this chapter; however, there are many other file systems available that are outside the scope of this book. The section “Tales from the Trenches: A Preparation War Story” presented earlier in this chapter warns that you can’t always anticipate every possible contingency before you head into the field. We must also recognize that we can’t arm you with information on every conceivable topic, nor every specific file system.
If you come across another file system that we don’t mention here, remember that the Internet can be your biggest friend and ally. Other file systems we know about (and mentioned in the previous version of this book) include BFS (the BeOS File System designed for an alternative Power PC and PC operating system in the mid-1990s) and HPFS (the High Performance File System native to OS/2).
Indeed, other file systems abound, including the distributed Andrew File System (AFS), the Common Internet File System (CIFS), and even mainframe holdovers like the Hierarchical File System (or HFS). For less common file systems, you can use your favorite Internet search engine to learn more, or even to search for specific forensic tools if you should need them to capture and preserve data.
Maintain Tools and Procedures for Each Operating System and File System
The challenge for computer forensic scientists is to develop methods and techniques that provide valid and reliable results while preserving evidence and preventing harm to information. You need to have procedures and tools in place so that you can more easily collect the evidence you need.
What happens if a system is set up to log every event imaginable? The system’s hard drive space will fill up, and someone will have to weed through all the collected information to figure out which events really can help an investigation. Having good procedures in place and conducting proper maintenance of your tools will help make the forensic process run more smoothly.
Preinstalled Tools Make Forensics Easier
For computer forensic science to be effective, it must be driven by information discovered during an investigation. Many systems currently include 500 GB or higher capacity hard disks. From a practical standpoint, it may be impossible to examine every file stored on a seized computer system. It could be equally difficult for law enforcement personnel to sort through, read, and comprehend the amount of information contained within files on today’s huge systems. So, we’ll take a look at some tools that can help you with this seemingly arduous task.
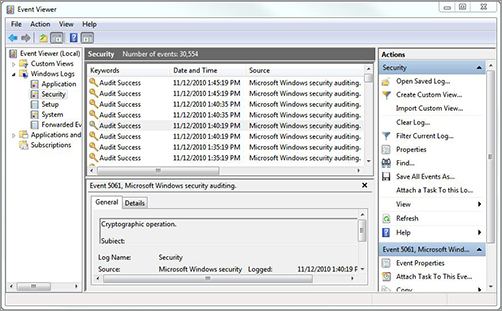
Eventually, you will work with a forensic toolkit. For now, let’s look at the tools that are already installed on most operating systems. These are tools that you can readily take advantage of and use. All operating systems come with the ability to log events. Because Windows 7 is a popular operating system these days, we’ll look at how it logs events. Event Viewer allows you to audit certain events. Event Viewer maintains three log files: one for system processes, one for security information, and one for applications. Figure 2-8 was captured on a Windows 7 computer. In Windows Server 2003 and 2008 versions, you will also find directory services, DNS server, and file replication logs, among many others.
Figure 2-8: The Windows 7 Event Viewer provides ready access to Windows audit logs and logged event detail.
Auditing Users and File Access
auditing
The process of tracking who’s logging in and accessing what files.
Auditing is the process of tracking users and their actions on a network and its component systems. You should audit access use and rights changes to prevent unauthorized or unintentional access by a guest or restricted user account. This will stymie unauthorized access to sensitive or protected resources. How much you should audit depends on how much information you want to store. Keep in mind that auditing should be a clear-cut activity built around equally transparent goals and policies.
When deciding what to audit, first identify potential resources at risk within your networking environment. These resources might typically include sensitive files, financial applications, and personnel files. After those resources are identified, set up an audit policy using operating system tools. It can be useful to monitor successful as well as failed access attempts. Failure events allow you to identify attempts at unauthorized access; successful events can reveal accidental or intentional (but unwanted) escalations of access rights.
Each operating system has its own methods to track and log access. Auditing is resource intensive and can easily add an additional 25 percent load to any server. Make time to view your logs. Log files can’t help protect against a system compromise if an intrusion recorded in your logs isn’t read for six months. Most operating systems produce log files in text file format, but viewing data graphically is much easier than interpreting text. If possible, import your log files into some type of database or log analysis tool.
Auditing can be as simple or as complex as you want to make it. Regardless of the auditing plan you devise, be consistent.
Tracking Incoming and Outgoing Computer Access
Most operating systems also include built-in utilities for tracking the address of a computer and tracing the route it takes to get to a destination on the Internet. Producing and recording such information can be quite important when internal users are engaging in malicious activity. With the advent of business-to-business activities, using tracking utilities is also a good way to know when employees are accessing the sites of business partners.
This section discussed tools that are already in place to track information traveling across a network. After you obtain this information, how can you use it? Can you accuse an employee of hacking based on the information that you have gathered? Such questions fall under the scope of knowing your legal limits, so let’s move on and see what you can and cannot do with the information you gather, assemble, or produce as you conduct an investigation.
