After you make a verified copy of original media, you’re ready to begin analysis. The tools discussed in the following sections can perform many forensic functions. Your choice of tools depends on specific investigative needs. The following sections include common software and hardware tools and cover their capabilities.
As with disk imaging tools, your choice of tools to use depends on the following:
- Operating system(s) supported
- User interface preferences
- Budget
- Functionality/capabilities
- Vendor loyalty
Software Suites
Several companies specialize in developing and providing forensic tools. These companies produce software and/or hardware with diverse functionality. Some suites of forensic software are tightly integrated and have mature user interfaces. Other forensic suites are little more than collections of useful utilities. Consider the following tools and try out the ones you like. Your final choice of forensic tools should enable you to perform the examinations you will encounter. Although bells and whistles are nice, it’s more important to get the tools you really need.
EnCase
Guidance Software produces the EnCase product line. EnCase was originally developed for law enforcement personnel to carry out investigations. This product line has grown to support commercial incident response teams as well.
The general concept of a case is central to the EnCase product. The first action you take is to create a case file. All subsequent activities (see Figure 8-19, Figure 8-20, and Figure 8-21) relate to a case.
Figure 8-19: EnCase interface
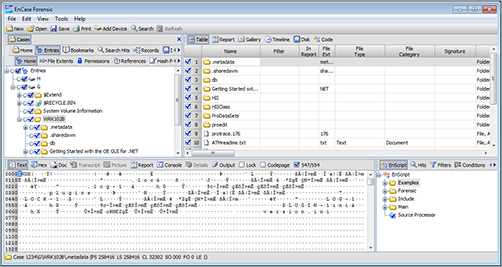
Figure 8-20: Using EnCase to search for keywords
Figure 8-21: Viewing IP addresses with EnCase
EnCase is an integrated Windows-based GUI tool suite. Even though the EnCase functionality is impressive, you are likely to need other utilities at some point. Fully integrated solutions can increase productivity, but don’t hesitate to use another tool when you need it.
Here are just a few features of EnCase:
- Snapshot enables investigators to capture volatile information including:
- RAM contents
- Running programs
- Open files and ports
- Organizes results into case files and manages case documents
- Helps maintain the chain of custody
- Provides tools for incident response teams to respond to emerging threats
- Supports real-time and postmortem examinations
EnCase provides the functionality to acquire and examine many types of evidence. The organization around a case provides the structure to keep information in order. Overall, EnCase is one of the premium suites of software you definitely should evaluate when selecting forensic tools. For more information on EnCase, visit the Web site at www.guidancesoftware.com.
Forensic Toolkit (FTK)
Another forensic suite that provides an integrated user interface is AccessData’s Forensic Toolkit (FTK) (Figure 8-22). FTK runs in Windows operating systems and provides a powerful tool set to acquire and examine electronic media.
Figure 8-22: FTK Evidence Processing options
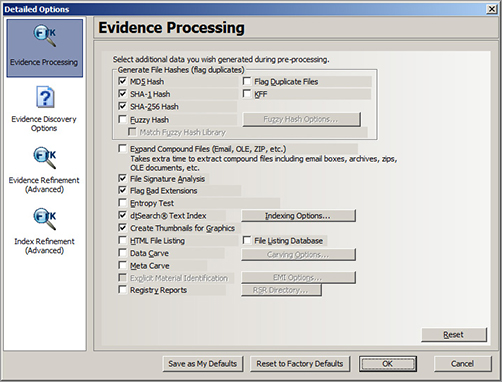
As discussed in “Disk Imaging and Validation,” earlier in this chapter, FTK contains a disk imaging tool. This imaging tool provides one or more copies of primary evidence for analysis.
FTK provides an easy-to-use file viewer that recognizes nearly 300 types of files. It also provides full text indexing powered by dtSearch (we cover dtSearch features later in this chapter in the “Miscellaneous Software Tools” section). FTK’s integrated file viewer and search capabilities enable it to find evidence on most devices.
FTK works with media images created by several imaging utilities, including:
- FTK
- EnCase
- SMART
- dd
Search capabilities include e-mail and archive file analysis. FTK also enables users to quickly examine files in many different formats. Results are organized by case and presented in a case content summary. For more information on FTK, visit the AccessData Web site at www.accessdata.com.
The Sleuth Kit (TSK)
The Sleuth Kit (TSK) is a popular, free, open source forensic software suite. TSK is a collection of command-line tools that provides media management and forensic analysis functionality.
TSK has a few features that deserve separate mention. TSK supports Mac partitions and analyzes files from Mac file systems. It also runs on Mac OS X. TSK can analyze volatile data on running systems.
The core TSK toolkit contains five different types of tools.
- File System Tools
File System Layer The fsstat tool reports file system details, including inode Numbers (file system data structures that contain file information), block or cluster ranges, and super block details for UNIX-based systems. For FAT file systems, fsstat provides an abbreviated FAT table listing.
File Name Layer The ffind and fls tools report allocated, unallocated, and deleted filenames.
Meta Data Layer The icat, ifind, ils, and istat tools report on file metadata (file details) stored in file systems.
Data Unit Layer The blkcat, blkls, blkstat, and blkcalc tools report file content information and statistics.
File System Journal The jcat and jls tools report journal information and statistics.
- Volume System Tools
The mmls, mmstat, and mmcat tools provide information on the layout of disks or other media.
- Image File Tools
The img_stat, and img_cat tools provide details and content information for image files.
- Disk Tools
The disk_sreset, and disk_stat tools detect and remove an HPA on an ATA disk.
- Other Tools
hfind The hfind tool looks up hash values.
mactime This tool uses fls and ils output to create timelines of file activity, such as create, access and write activity.
sorter This tool sorts files based on file type.
sigfing This tool searches for a binary value in a file, starting at a specific offset location.
For more information on TSK, visit the TSK Web site at www.sleuthkit.org.
ProDiscover
Technology Pathways provides two different versions of the ProDiscover tool suite: Forensics and Incident Response (IR), depending on your particular forensic needs. (ProDiscover IR is shown in Figure 8-23 and Figure 8-24.) Both ProDiscover products run in Windows with an integrated GUI.
Figure 8-23: Using ProDiscover IR to add comments to a file
Figure 8-24: Search results in ProDiscover IR
Here are some notable ProDiscover features:
- Allows live system examination
- Identifies Trojan horse programs and other software intended to compromise system security
- Utilizes a remote agent that allows centralized examination and monitoring, along with encrypted network communication to secure analysis data
- Creates a bit stream copy of an entire suspect disk, including hidden HPA sections, to keep original evidence safe
- Ensures integrity of acquired images using MD5 or SHA-1 hashes
- Supports FAT12, FAT16, FAT32, all NTFS versions, Linux ext2/ext3, and Sun Solaris UFS file systems
- Generates reports in eXtensible Markup Language (XML)
ProDiscover provides functionality similar to other full-featured forensic software suites listed in this section.
Technology Pathways also offers a free version of ProDiscover Basic. ProDiscover Basic is a complete GUI-based computer forensic software package. It include the ability to image, preserve, analyze, and report on evidence found on a computer disk drive. This version is freeware and may be used and shared free of charge.
Take a look at the full product line for more details on specific features. To learn more about ProDiscover, visit the Technology Pathways Web site at www.techpathways.com.
SIFT
The SANS Investigative Forensic Toolkit (SIFT) is a collection of open source (and freely available) forensic utilities. SANS originally developed SIFT as a toolkit for students in the SANS Computer Forensic Investigations and Incident Response course. The students liked the toolkit so much that word spread and SANS decided to repackage and release it to the public.
SIFT is available either as a VMware virtual machine or as an ISO image to create a bootable CD. It provides the ability to examine disks and images created using other forensic software. This toolkit allows users to examine the following file systems:
- Windows (FAT, VFAT, NTFS)
- Mac (HFS)
- Solaris (UFS)
- Linux (ext2/ext3)
SIFT tools support the following evidence image formats:
- Raw (dd)
- Expert Witness (E01)
- Advanced Forensic Format (AFF)
SIFT includes these individual tools:
- The Sleuth Kit (TSK file system analysis)
- Log2timeline (generates timelines)
- Ssdeep and md5deep (generates hashes)
- Foremost/Scalpel (file carving)
- Wireshark (network analysis) (http://www.wireshark.org/) (See Figure 8-25.)
Figure 8-25: Wireshark Network Analyzer
- Vinetto (thumbs.db analysis)
- Pasco (Internet Explorer history analysis)
- Rifiuti (examines Recycle Bin)
- Volatility Framework (memory forensics)
- DFLabs (GUI front end for TSK)
- Autopsy (GUI front end for TSK)
- PyFLAG (log and disk analysis)
- Guymager (GUI imager for evidence acquisition)
Figure 8-26: Guymager open source forensic manager
SANS also provides users with documentation (including a series of “how-to” tutorials) on using SIFT in a forensic investigation. For more information on SIFT, visit the SANS Web site at https://computer-forensics2.sans.org/community/downloads/.
X-Ways Forensics
X-Ways Forensics, from X-Ways Software Technology AG, is a collection of forensic tools that assist in examining media images. Compared to other forensic suites in this section, it’s a little more lightweight. However, it does provide several forensic tools that include some large package features at a very reasonable price.
Some of the main X-Ways features include:
- Case management
- Automatic activity logging
- Automated reports in HyperText Markup Language (HTML)
- A display of existing and deleted files, sorted by file type category
- Gallery view for graphics
- Skin color detection helps in isolating pictures that may contain pornography
- File extension/file type mismatches detection
- EnCase media image support (read)
This list only covers a few of the many features of X-Ways. For more information on this product, visit the X-Ways Software Technology Web site at http://www.x-ways.net/forensics/.
Miscellaneous Software Tools
In addition to drive imaging software and complete forensic software suites, there are many targeted tools and utilities that are of value to computer forensic investigators. No matter how many features your forensic suite of choice may have, your investigation might have specific needs that require other special tools.
The following sections cover a few special-purpose tools. As with previous sections, consider each of these tools and choose the best ones for your forensic needs.
DriveSpy
DriveSpy was introduced earlier in the “Disk Imaging and Validation Tools” section. It’s included here as well to remind you that DriveSpy does a lot more than just duplicate drives. For instance, you can:
- Select files based on name, extension, or attributes
- View the sectors and clusters in built-in hex viewers.
- Search a partition or drive for specific text strings
DriveSpy provides basic command-line functionality that is portable enough to carry on a single floppy disk and use at the scene of a forensic investigation. After an image of a drive is created, DriveSpy also assists you in examining image content.
For pricing and more information, visit the Digital Intelligence, Inc. Web site at http://www.digitalintelligence.com/software/disoftware/drivespy/.
dtSearch
After you create an image of suspect media, you’ll need to search it for possible evidence. The dtSearch product line, from dtSearch Corporation, provides solutions that enable you to search terabytes of text in a short time. Although not strictly a forensic tool, dtSearch (Figure 8-27) supports a highly necessary forensic function.
Figure 8-27: dtSearch
The dtSearch products offer the following features:
- Over 25 search options, including indexed, unindexed, field content searching for supported file types, and full-text search options
- Convert results to HTML, XML, or PDF, with search results highlighted (exposes the search results context)
- Support for distributed searching for high performance
The dtSearch product line includes several different products for different forensic investigative needs, including:
dtSearch Desktop Searches stand-alone machines
dtSearch Network Searches across networks
dtSearch Spider Extends a local search to a remote Web site
dtSearch Web Supports instant text searching for online documents
dtSearch Publish Publishes an instant searchable database on CD/DVD
dtSearch Engine Empowers developers to add dtSearch’s functionality to applications
For a forensic examiner, the Desktop and Network products provide the capability to find possible evidence on multiple machines. For more detailed product information, visit the dtSearch Corporation Web site at www.dtsearch.com.
NetAnalysis
NetAnalysis, from Digital Detective, is a software utility that recovers and then analyzes Internet browser artifacts. NetAnalysis (Figure 8-28) empowers investigators to search and analyze browser history from suspect computers. Even if a user deletes all browser history, NetAnalysis can still recover much of that deleted content and reconstruct past actions.
Figure 8-28: NetAnalysis
NetAnalysis enables investigators to reconstruct visited Web sites from locally cached data. It can read several standard forensic image formats, including images generated by EnCase. The Auto Investigate function helps investigators save time by automatically identifying suspicious Web sites that may contain specific content, such as child pornography. It also analyzes search terms, user IDs, and passwords it finds on the suspect computer.
NetAnalysis helps investigators recover and identify the most valuable information to an investigation. Using NetAnalysis to find questionable browsing activity is much easier than performing a manual analysis. NetAnalysis also allows users to develop standard key terms and queries to share and use with other investigations.
For more detailed product information, visit the Digital Detective Web site at http://www.digital-detective.co.uk/netanalysis.asp.
Quick View Plus File Viewer
Quick View Plus, from Avantstar, is a general-purpose file viewer. Quick View Plus (Figure 8-29) allows you to view files in over 300 formats. Quick View Plus also allows you to view parts of files and print them or cut and paste into your own applications.
Figure 8-29: Quick View Plus file viewer
From a forensic perspective, Quick View Plus provides examiners the ability to search many types of files for text strings and view the results in the context of the original file.
Find more details on Quick View Plus by visiting the Avantstar Web site at www.avantstar.com.
ThumbsPlus File Viewer
ThumbsPlus File Viewer, from Cerious Software Inc., is a general-purpose file viewer and editor. It allows you to view files in many formats. A good file-viewing tool makes browsing through several graphics files far easier. ThumbsPlus (Figure 8-30) makes it easy to collect and browse most common graphic formats.
Figure 8-30: ThumbsPlus Pro
You can find many more details on ThumbsPlus by visiting the Cerious Web site at http://www.cerious.com/featuresv7.shtml.
Paraben Tools
Paraben Corporation provides a wide array of forensic tools. The Forensic Replicator was introduced earlier. In this section, you’ll learn about three additional Paraben tools. At the end of the Paraben Tools section, be certain to follow the link to learn about other forensic tools offered by Paraben.
Device Seizure
Paraben’s Device Seizure (Figure 8-31 and Figure 8-32) is a software tool that enables investigators to acquire and analyze data from over 2,400 different mobile devices. This includes mobile phones, PDAs, and GPS devices. Paraben also sells hardware accessories that work with Device Seizure to allow you to physically connect to all supported mobile devices.
Figure 8-31: Paraben’s Device Seizure Welcome Wizard
Figure 8-32: Paraben’s Device Seizure main screen
Device Seizure acquires and organizes a large amount of mobile data, including:
- Active and deleted text messages
- Phonebook entries from memory and the SIM card
- Call history with call details
- PDA common information (calendar, to-do list, etc.)
- File system contents
- GPS information
- E-mail information
Device Seizure can also translate GPS coordinates into Google Earth data. This makes it easy to present evidence in a form that anyone can easily see and understand. Paraben designed Device Seizure to be a solid forensic tool for mobile device investigations.
Chat Stick
Paraben provides several consumer products for home and corporate use, such as the Chat Stick. The Chat Stick is a USB thumb drive that comes preloaded with software.
Using the Chat Stick is easy. Simply insert the Chat Stick in a USB port on a target computer. The Chat Stick software automatically launches and lets you search for chat logs from most popular instant message (IM) software, including:
- Yahoo
- MSN
- ICQ
- Trillian
- Skype
- Hello
- Miranda
Chat Stick identifies chat logs and copies these logs to the USB thumb drive. From there, Chat Stick software (Figure 8-33) allows users to view and create reports on all IM conversations.
Figure 8-33: Paraben’s Chat Stick software
Chat stick makes it easy for parents to check up on IM activities on home computers. Businesses also use Chat Stick to ensure their employees uphold their acceptable use policies for computer equipment at work.
Paraben Porn Stick
Paraben’s Porn Stick is another consumer product distributed on a USB thumb drive. The Porn Stick contains preloaded software that searches a target computer for suspicious images—specifically pornography.
As with the Chat Stick, the Porn Stick software automatically launches when the thumb drive is plugged into a USB port. Users can search one or more drives on the target computer for suspicious images.
The Porn Stick stores thumbnails of suspicious images on the USB thumb drive. Images can be previewed once the scan is finished. To make the process more palatable, the Porn Stick blurs image thumbnails. You can select any image and use the mouse pointer to see a small portion of the unblurred image (see Figure 8-34). This feature makes it difficult to “accidentally” view objectionable material.
Figure 8-34: Detection results from Paraben’s Porn Stick software
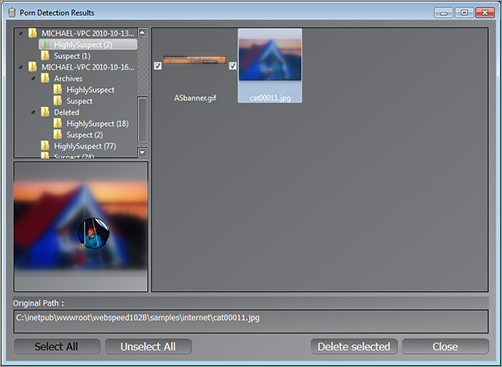
The Porn Stick is a consumer product that home and business users typically purchase. As with the Chat Stick, parents can use it at home and businesses can use it in the office to check for acceptable use policy violations.
For more information on any Paraben products, visit their Web site at www.paraben.com.
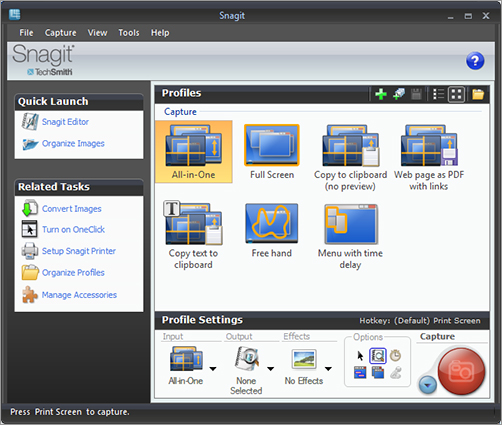
Snagit
Snagit, from TechSmith Corporation, is a full-featured tool designed to capture and manage screenshots. Sometimes, the best way to document the state of evidence is to save an image from the screen. Snagit (Figure 8-35) makes it easy to take screenshots using over 40 different methods. You can record any aspect of what’s on a computer monitor.
Figure 8-35: Snagit
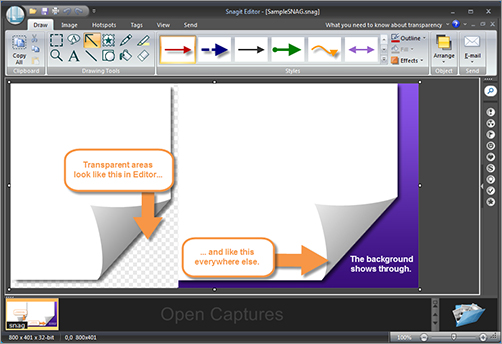
Once you take a screenshot, Snagit allows you to edit it (see Figure 8-36) and add features to highlight specific areas on that image. Snagit also helps in sharing, cataloging, and storing screenshot images. Snagit can help to simplify any investigation.
Figure 8-36: Snagit Editor
For more information on Snagit, visit the TechSmith Web site at http://www.techsmith.com/snagit/.
Hardware
Up to this point, we’ve ignored the requirement that all software tools must run on hardware of some type. Although forensic tools run on general-purpose machines, using dedicated computers for forensic investigations is often advisable. Using dedicated hardware decreases the possibility of accidental contamination by nonforensic applications.
Although actual evidence contamination cannot occur on the original evidence when analyzing an image of the original, other applications might affect the evidence image copy you are examining. Your forensic machine probably has special-purpose hardware elements such as a disk-write blocker, keystroke logger, or multiple format disk controllers.
Because forensic examination computers tend to support special-purpose hardware and software, several companies offer hardware devices and complete computer systems built from the ground up to serve as forensic hardware devices. Some of these systems can be expensive, but if you need a prebuilt forensic hardware platform, the cost is probably justified. Carefully consider your needs based on:
- Where will you analyze media?
- At the scene
- In the lab
- How often do you use forensic software?
- What type of operating system and hardware must you analyze?
- Will the evidence you collect be presented in a court of law?
Answers to these questions will help you to decide whether you need special-purpose forensic hardware and what features you need. The following sections describe the products offered by some forensic hardware providers.
Cellebrite
Cellebrite produces a line of forensic hardware for use in mobile device forensics. Their Universal Forensic Extraction Device (UFED) enables forensic investigators to extract information from more than 3,600 mobile devices, including phones and GPS units. UFED is used by militaries, law enforcement agencies, governments, and intelligence agencies around the world to extract information from mobile devices during investigations.
UFED comes in multiple versions to support user-specific requirements. The UFED system includes over 100 different connectors that allow investigators to attach any type of mobile device. UFED software supports many features investigators need, including:
- Extract existing and deleted phone data
- Call history
- Text messages
- Contacts
- Images
- Geotags
- Search, reconstruct, and analyze phone data
- Integrate GPS information with Google Maps and Google Earth
For more information on Cellebrite UFED products, visit the Web site at http://www.cellebrite.com/forensic-products.html.
ICS Solo 4
Intelligent Computer Solutions (ICS) specializes in data duplication hardware. They produce a line of forensic acquisition products for both field and lab use. Their forensic products use high-speed hardware and hardware write blockers to duplicate evidence media. Instead of using software tools to create images of evidence media, ICS provides hardware to accomplish the same task. The tool also has the ability to capture video played on Web sites.
The main advantage to using hardware data acquisition is increased speed. ICS products transfer data at rates up to 18 GB/min. That is far faster than any software image acquisition. ICS products, such as the ICS Solo-4 (Figure 8-37), provide a convenient method to extract images from a suspect computer, even without removing its hard drive(s).
Figure 8-37: Image MASSter Solo-4 from ICS
Photograph Courtesy of Intelligent Computer Solutions, Inc., 2010

For more information on the ICS line of forensic acquisition products, visit the ICS Web site at www.ics-iq.com.
