The main purpose of computer forensics is the proper identification and collection of computer evidence. It is both an art and a science. Computer evidence shares common characteristics with, but also differs from, conventional legal evidence. Forensic examiners need to understand the specifics of computer evidence so that they can properly collect it for later use.
Incidents and Computer Evidence
Computers may be involved in security violations in one of two ways. First, a computer can be used in the commission of crimes or violations of policy. Second, a computer can be the target for an attack. In the first situation, one or more computers are used to perform an inappropriate action. Such actions might be illegal (for example, fraud or identity theft) or simply disallowed under an organization’s security policy (for example, participating in online auctions on company time).
Regardless of whether an action is a crime, any violation or intended violation of security policy is called a security incident. A company’s security policy should outline an appropriate response for each type of incident. As covered in Chapter 2, “Preparation—What to Do Before You Start,” most incidents that do not constitute crimes generally require only internal investigation. An organization’s incident response team (IRT) normally carries out internal investigations. The IRT is specially trained to identify and collect evidence to document and categorize incidents. This team must also be cognizant when incidents are crimes and require law enforcement involvement.
In general, an incident response team deals with incidents where one or more computers serve as the target for an attack. Criminal investigations are frequently conducted to address the type of incident where a computer is used as a tool in committing a crime. In both situations, the computer forensic analysis produces evidence of activity carried out during an incident.
computer evidence
Any computer hardware, software, or data that can be used to prove one or more of the five Ws and the H for a security incident—namely, who, what, when, where, why, and how.
To investigate an incident properly and build a case that allows you to take action against a perpetrator, you’ll need evidence to provide proof of the attacker’s identity and actions. Computer evidence consists of files, along with their contents, that remain behind after an incident has occurred. In some cases, the files themselves—such as pictures or executable files—can provide evidence of an incident. In other cases, the contents of files such as logs or protocol traces provide necessary proof. Recognizing and identifying hardware, software, and data you can use is the first step in the evidence collection process.
Types of Evidence
Four basic types of evidence can be used in a court of law:
- Real evidence
- Documentary evidence
- Testimonial evidence
- Demonstrative evidence
Computer evidence generally falls into the first two categories.
Before you start looking for evidence, understand that most successful cases are based on several types of evidence. As you conduct an investigation, be aware of what types of evidence you can gather. Although computer forensics tends to focus on one or two types, a complete investigation should address all types of evidence available. In the following sections, we look more closely at each of these four types of evidence.
Real Evidence
real evidence
Any physical objects you can bring into court. Real evidence can be touched, held, or otherwise observed directly.
The type of evidence most people already know about is real evidence. Real evidence is anything you can carry into a courtroom and place on a table in front of a jury. In effect, real evidence speaks for itself. It includes physical objects that relate to a case.
Of the four types of evidence, real evidence is the most tangible and easiest to understand. When presenting a case to a jury, real evidence can make a case seem more concrete. You may be asked to present real evidence, even when the most compelling evidence is not physical evidence at all.
Remember that most courtroom participants are not technically savvy. Consequently, any piece of pertinent tangible physical evidence will help a case. Without real evidence, in fact, a case may be perceived as weak or circumstantial.
In a murder trial, the case’s real evidence might include the murder weapon. In the context of computer forensics, the actual computer used to commit a crime could be introduced as real evidence. If a suspect’s fingerprints are found on that computer’s keyboard, real evidence can be offered to prove that the suspect uses that machine. A hard drive from a suspect’s computer or a mobile device might also constitute real evidence.
hard evidence
Real evidence conclusively associated with a suspect or activity.
Sometimes real evidence that conclusively relates to a suspect (such as fingerprints or DNA) is called hard evidence.
Hot Java, Cold Jury
Cool Beans, Hot Java versus James T. Kirkpatrick is a fictitious case we’ll use to illustrate the importance of real evidence. Kirkpatrick was charged with launching spam campaigns from a public terminal in the Cool Beans, Hot Java coffee shop. The Cool Beans network administrator provided ample proof that Kirkpatrick was in the shop during the alleged spam activity. Cool Beans provided security camera images of Kirkpatrick and accompanying computer access logs showing activity consistent with spam floods. Any technical person had to agree this case was a slam dunk.
However, the jury acquitted Kirkpatrick owing to the lack of compelling evidence. When questioned, jurors said that they found it difficult to convict a man based on little more than printed reports and pictures showing him in the shop. They wanted concrete evidence. Perhaps the actual computer Kirkpatrick used would have helped to convince the jury, or a network diagram showing how IP addresses are assigned, could have helped the jury make the jump from the virtual to the physical world.
Never overlook potential evidence when conducting an investigation. Other types of evidence may involve or refer to real evidence. For example, it is very common to use log file contents when arguing a case. The process of establishing the credibility and authenticity of such data is often easier when you start with the physical disk drive and/or computer from which you extracted the log file. In this example, real evidence supports the log file data and helps make proof more tangible.
Assume you have been asked to investigate a spammer. Because of the nature and volume of e-mails sent, local law enforcement has been called in to investigate and they have called on you to help out. You arrive on the scene to begin your investigation.
Before you touch anything, look around the scene and take pictures of everything. Digital pictures are inexpensive, but can be valuable later. As you work through the investigation, you’ll frequently want to refer back to images of the crime scene as you originally found it. As an added bonus, it’s not uncommon to find additional evidence in original pictures after extracting digital evidence from a suspect’s machine.
After you photograph everything, start identifying all of the potentially pertinent real evidence that you have permission to search or seize. Notice that the suspect’s computer has both a scanner and a mobile device cradle attached. That tells you to look for the mobile device and scanner source or target data. Mobile devices can be valuable sources for documentary evidence (which we discuss in the next section). Most people who use mobile devices store lots of personal data on them. Find the mobile device and make sure it has power. If you are authorized to seize a mobile device, be sure to take its power supply as well.
After looking for and securing the mobile device, look for any source documents (for example, printed hard copies) the suspect might have scanned. Also look for CD/DVD-ROMs the suspect may have used to store scanned images. Next, examine the physical computer and surrounding area for other signs of evidence. You should look for such items as:
- Handwritten notes. Even technically savvy people use notes. In fact, because handwritten notes are not stored on a computer, many people consider them to be more “secure.”
- Any peripheral device that is, or can be, connected to the computer. This could include:
- Storage devices
- Communication devices
- Input/output devices
- All removable media, such as:
- Optical media (write-once or rewritable CDs, DVDs, or Blu-ray Discs)
- Removable disks (floppies, ZIP disks, and so forth)
- USB Flash Drives (UFDs) and other USB drives, plus eSATA or FireWire drives
- Tapes and other magnetic media
This list is not exhaustive. It is simply a teaser to start you thinking about real evidence.
Looking for physical evidence is easy. Use your eyes and your brain. Look hard at the scene and think about how any physical device or object might provide evidence you need to prove your case, whether such evidence will be presented in a court of law or appear in an incident report.
After you acquire all the real evidence you can collect, it’s time to consider other types of evidence that might be available. These types of evidence—documentary, testimonial, and demonstrative—are covered in the following sections.
Documentary Evidence
documentary evidence
Written evidence, such as printed reports or data in log files. Such evidence cannot stand on its own and must be authenticated.
Much of the evidence you are likely to use in proving a case will be written documentation. Such evidence includes log files, database files, and incident-specific files and reports that supply information about what occurred. All evidence in written form, including computer-based file data, is called documentary evidence. All documentary evidence must be authenticated. Because anyone can create an arbitrary data file with specific content, you must prove that documentary evidence was collected appropriately and that the data it contains proves some fact.
Authenticating documentary evidence can be quite complex when you’re trying to convince nontechnical jurors (or judges) that the contents of a file conclusively prove an attacker performed some specific action. Opposing attorneys are likely to attack the method of authenticating documentary evidence as well as the evidence itself. We have all heard of hard evidence thrown out of court because it was collected illegally. Computer evidence can be even more difficult to collect properly. We will cover admissibility in the section titled “Admissibility of Evidence in a Court of Law” later in this chapter.
Best Evidence Rule
best evidence rule
Whenever a document is presented as evidence, you must introduce the original document if at all possible. A copy may only be introduced if the original is not available.
In addition to basic rules that govern all computer evidence, you must consider one additional rule. Whenever you introduce documentary evidence, you must introduce an original document, not a copy. This is called the best evidence rule. The purpose of this rule is to protect evidence from tampering. If an original document is required, there is less opportunity for modification to occur during some copy operation. Of course, you’ll have to convince the judge and jury that the document you bring into court is actually the original.
As you progress through an investigation, you will use utilities and tools to explore the contents of the computer and storage media. All files and file contents that support your case are considered documentary evidence. This is where you’ll find the bulk of your evidence for many investigations.
Remember, most of your documentary evidence will come directly from items on the real evidence list (such as computers or mobile devices). Some documentary evidence will be supplied by third parties, such as access logs from an Internet service provider (ISP), but most will come from your own investigative activities.
You’ll constantly be reminded to document each and every step in your investigation. Always document. There will be a test! Rest assured that if you testify in court, you’ll be asked to justify your investigation and any and all actions you took to extract evidence.
After you get a handle on the physical evidence, you can start looking at the physical media’s content for digital evidence. How do you look for digital evidence? You will use a collection of forensic tools to search for documentary evidence. Some of these tools are as simple as file listings or viewers, while others have been developed specifically for forensic investigations. Chapter 8, “Common Forensic Tools,” covers frequently used forensic tools and their uses in an investigation. Until Chapter 8, we refer to tools designed to examine file system contents as forensic tools.
So, what are you looking for? Use forensic tools to look for any file or file contents that show what a suspect did while using the computer. This can include many types of log files and other activity files. For example, WS_FTP is a common File Transfer Protocol (FTP) client. When you use it to transfer files, the program lists all activity in a file named wsftp.log. Look for instances of this file. You’ll be surprised how often people leave such audit trails lying around.
Here’s a list of some of the steps you’ll want to take while looking for documentary evidence:
- Catalog all programs installed on the target system.
- Harvest all audit and activity log files you can find that use default file-names. (To discover the default names for audit and log files, you might have to research each identified program. The program’s web page is one place to start.)
- Examine operating system and application configuration files for recorded use of nonstandard audit or activity log filenames.
- Search for any files created as a result of using any identified program.
As with real evidence, experience will guide you in identifying and extracting documentary evidence. Be creative and persistent!
Testimonial Evidence
testimonial evidence
Evidence consisting of witness testimony, either in verbal or written form. Testimonial evidence may be presented in person by a witness in a court or in the form of a recorded deposition.
The testimony of a witness, either in verbal or written form, is called testimonial evidence. The most common form of testimonial evidence familiar to the general public is direct witness testimony in the courtroom. A witness is first sworn in, and then he or she presents testimony that directly relates knowledge of an incident. Testimonial evidence does not include opinions, just direct recollection from the witness.
A second common form of testimonial evidence is testimony delivered during a deposition. As with live testimony, during a deposition, the witness delivers testimony under oath. All testimony, as it is delivered, is recorded by a court reporter. A record of a deposition can be entered into evidence just like the testimony of a live witness in court. Each type of testimony has its advantages, but a deposition can often be taken much sooner, when events are fresh in a witness’s mind.
You’ll often need to use testimonial evidence to support and augment other types of evidence. For example, you may have a system administrator testify that your server keeps logs of all user accesses and has done so for the last two years. This testimony helps to validate the documentary evidence of access log contents taken from that server’s hard disk drive (physical evidence).
When you first looked at the e-mail spammer scene in the fictitious Cool Beans, Hot Java versus James T. Kirkpatrick case, you contacted every possible witness, right? When investigating an incident, you’ll want to talk with each person who has physical access to the suspect’s computer, or who has substantive contact with that suspect. Interviewing witnesses is a task best left to law enforcement when dealing with criminal matters, but you should include their testimony in your investigation. Quite often, witness testimony provides extra information that leads you to additional documentary or physical evidence.
A witness could give you clues to hiding places for key storage media, or to the suspect’s computer usage habits. If you have reason to believe a suspect carried out illegal activities during lunch, for example, this can help you limit the initial amount of data you must examine. Work with whoever is interviewing witnesses to get your questions presented. Those answers can save you a lot of work!
Demonstrative Evidence
demonstrative evidence
Evidence that illustrates or helps to explain other evidence. Usually demonstrative evidence consists of some kind of visual aid.
Many types of computer evidence make sense to technical people but seem completely foreign to less technical folks. For judges and juries to understand the finer points of a case, it is often necessary to use visual aids and other illustrations to help explain some of the more technical details in the evidence. Any evidence that helps to explain, illustrate, or re-create other evidence is called demonstrative evidence. Demonstrative evidence does not stand on its own as do other types of evidence. It exists only to augment other evidence.
Let’s assume you want to use a web server log file to show how an attacker exploited a new vulnerability. That attack crashed the server and caused substantial loss of business while the system was down. You can use charts, flowcharts, and other visual aids to help explain how web servers work in a way that is easy to understand. Demonstrative evidence is often essential to successful use of other types of evidence.
In many cases, you’ll be called upon to explain highly technical concepts to nontechnical people. For example, in our e-mail spammer case, you’d have to explain what a spammer does. Although most people have heard of spam, not many understand how it originates and spreads. Further, you’d have to explain why it’s so difficult to catch the originator of those messages, and why spam causes problems in the first place. It is always a good idea to start with the basics. Show how normal e-mail works and how a spammer causes problems by using excessive network bandwidth. Several illustrations are likely to help get this information across.
For example, you might want to start at the beginning. Building a complex technical argument from the ground up requires some basic education and background. Figure 3-1 is an illustration you might use to show how e-mail works.
Figure 3-1: Demonstrative evidence helps explain how e-mail works.
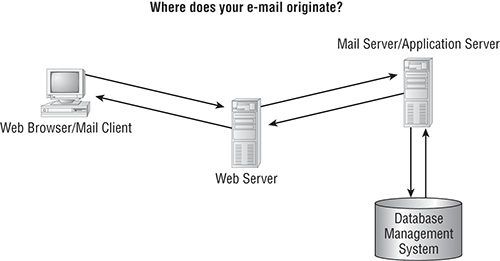
Developing the right visual aids normally comes after the bulk of other evidence has already been collected. Remember, demonstrative evidence is used to explain or demonstrate other evidence. Use it to make your points clear to a judge and jury.
Now that we have looked at the different types of evidence, let’s see how you can obtain evidence legally.
