The variety of operating systems, application programs, and storage methods available today means that when it comes to looking for evidence there are a multitude of places to look. Digital evidence can be found in numerous sources, including stored data, applications used to create data, and the computer system that produced the activity. Systems can be huge and complex, and they can change rapidly. Data can be hidden in many different locations and formats. After you find such data, you may have to process it to make it readable by people.
connector
The part of a cable that plugs into a port or interface to connect devices. Male connectors are identified by exposed pins. Female connectors are identified by holes into which the male connector can be inserted.
In recent years, manufacturers have developed branded forensic workstations that provide external native connectors for a variety of media, such as Serial ATA (SATA), SCSI (Small Computer System Interface), flash media, and the older IDE (Integrated Drive Electronics) drives. SATA hard drives are more commonly used by individuals, while SCSI hard drives are more likely to be found in a corporate environment.) As a forensic investigator, you will encounter and work with many different types of media. You may also encounter connectors that hook up FireWire to SATA, SCSI, or IDE, and that hook up USB to SATA, SCSI, or IDE. A forensic investigator will determine what media the suspect has been using to store data and will have a variety of connectors on hand to aid the investigation.
The general discovery process is the same whether you are working with a SATA, SCSI, or IDE drive. You should adapt your techniques to suit the hardware you encounter.
To begin the discovery process for a drive, copy the image file onto your forensic workstation and then process it using one or several different forensic tools such as FTK, Encase, or ProDiscover.
Network Activity Files
Let’s use an example case that involves the Internet and pictures. During your career as a forensic investigator, you may be called upon to investigate situations where an employee has illegally accessed and downloaded pictures of proprietary designs from a competitor’s internal Web site and then used these designs in his or her own work.
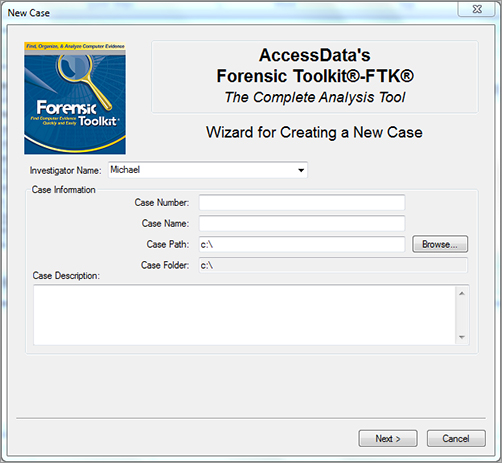
After the forensic image has been added to your forensic computer, open your forensic software and start a case. Figure 6-1 shows the New Case Wizard from the AccessData Forensic Toolkit (FTK).
Figure 6-1: AccessData’s Forensic Toolkit New Case Wizard
When a user logs on to a Windows XP, Vista, or Windows 7 system for the first time, a directory structure is created to hold that individual user’s files and settings. This structure is called the profile. The profile creates a directory that has the same name as the user, along with various other folders and files.
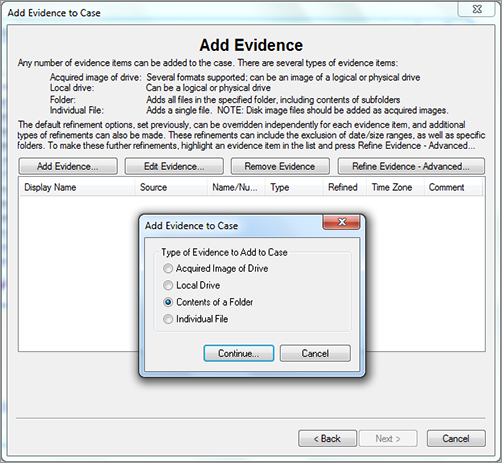
Because this case involves searching for images that were downloaded from the Internet, the forensic investigation can begin by adding the entire image of the suspect computer to the FTK case. The image can then be preprocessed and evidence from the entire hard drive reviewed. Evidence from the folders where these files may be stored can be added to the case, as illustrated in Figure 6-2.
Figure 6-2: Adding evidence to a case in FTK
cache
Space on a hard disk used to improve performance speed by storing recently accessed data so that future requests for that data can be served faster locally.
temporary Internet files
Copies of all HTML, GIF, JPG, and other files associated with the sites a user has visited on the Internet.
Before a browser downloads a web page, it looks in the Temporary Internet Files folder to see if the information is already stored there. This increases the speed at which the page will load. Web browsers cache web pages that the user visited recently. This cached data is referred to as a temporary Internet file, and it is stored in a folder on the user’s hard drive. All of the HTML pages and images are stored on the computer for a certain amount of time, and they are deleted when the temporary Internet file reaches a certain size.
Trojan horse program
In computers, a type of program or code that appears to be legitimate or harmless, but contains malicious or harmful instructions that may allow unauthorized users access to the victim’s computer system.
Sometimes, while a user is viewing web pages, files can be written to the user’s hard disk without the user’s knowledge. For example, many sites contain Trojan horse programs that automatically download objectionable material (files) to a user’s computer without the user’s knowledge.
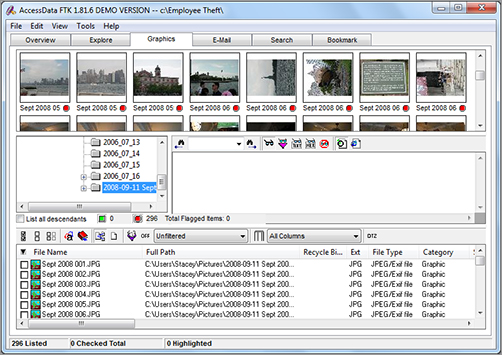
When working with web pages, it’s important to keep in mind that a web page is not usually a single graphics file. A web page is a collection of multiple photos and graphics files that are displayed together as a single web page. Forensic investigators see each element that makes up a web page. This can be very important when reviewing graphics information, because the investigator needs to put the evidence into context. The user may have visited a single web page, yet the forensic application may show dozens and dozens of photographs in the Internet History. An untrained person might think the user had downloaded dozens of individual photos, yet the truth is only a single web page was visited.
Figure 6-3 shows how the information in the Temporary Internet Files folder can be viewed using forensic software.
Figure 6-3: FTK displaying information found in the Temporary Internet Files folder
Information found in the Temporary Internet Files folder could have been unintentionally downloaded by the suspect. For example, some courts have determined that the existence of files automatically stored in a cache is not sufficient to convict a defendant of possessing or procuring child pornography. Other circumstances need to be evaluated to distinguish between unintentional and intentional acts. Such evaluations should consider the history of the files, their origin and use, and the control that the defendant had over the files.
In Firefox for Windows, the directory storing temporary Internet files is called Cache and is found in the following location: C:Documents and SettingsusernameApplication DataMozillaFirefoxProfilesrandom_characters.defaultCache
In the path above, username is the Windows username of the suspect computer. random_characters is a series of random characters. The Application Data folder is hidden by default. To view this folder, go to Tools Folder Options, select the View tab, and then mark ‘‘Show Hidden Files And Folders’’ before proceeding.
In Internet Explorer, the location for temporary Internet files varies depending on the version of Windows used on the system. For Windows 7 or Windows Vista, the Temporary Internet Files directory resides in: C:UsersusernameAppDataLocalMicrosoftWindowsTemporary Internet Filesor C:UsersusernameAppDataLocalMicrosoftWindowsTemporary Internet FilesLow
Note that on PCs, Temporary Internet Files may be located on hard drivers other than the C drive. Forensic investigators should search all drives for Temporary Internet Files.
For systems that use Windows XP or Windows 2000, the Temporary Internet Files directory is located in: C:Documents and SettingsusernameLocal SettingsTemporary Internet Files
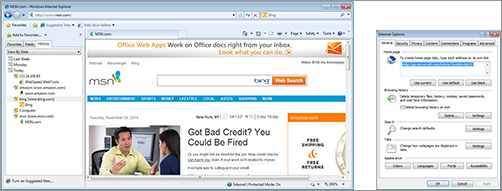
Forensic investigators may also find evidence in the browser’s History folder. The History folder contains a list of links to web pages that the user visited. Figure 6-4 shows an example of data contained in the History folder. It also shows why this file may contain little or no data. The Internet Options dialog box in Internet Explorer includes Browsing history settings. The user can specify how long the list of visited Web sites should be kept. The default setting is generally 20 days. Computer users can change this setting to a shorter period, or set the browser to erase the entire history when the browser is closed.
Figure 6-4: Internet Explorer History list and Internet Options Browsing history settings
cookie
Small text file placed on a computer’s hard drive as users browse Web sites. Each cookie file contains a unique number that identifies users to the Web site’s computers upon the user’s return to the site.
The Cookies folder is similar to the History folder. It holds cookies—information stored by Internet sites that were visited by the user. A number of utilities work with forensic software to display the contents of a cookie in an easily readable format. One such utility is DCode, which you can download from http://www.digital-detective.co.uk/downloads.asp.
Flash cookies (also called Local Shared Objects, or LSOs) are files placed on your computer by a Flash plugin. These cookies are stored in central system folders and are protected from deletion. Cookie deletion settings in the browser don’t affect LSOs. LSOs are used like standard browser cookies. The primary differences are that Flash cookies hold 25 times more data than standard browser cookies and never expire. Flash cookies are easily identifiable by their .sol file extension. The default storage location for LSO files is operating system-dependent. LSO files may be stored at: UsersusernameAppDataRoamingMacromediaFlash Player#SharedObjects.
Unfortunately, conventional forensic software used to analyze Internet history may not find these files, and the forensic investigator may have to dig deeper to recover Flash cookie data. Once recovered, you can parse .sol files into a more readable form using the SharedObject Reader plugin, which can be downloaded from http://code.google.com/. From this web page, search for “SharedObject Reader” to locate the plugin.
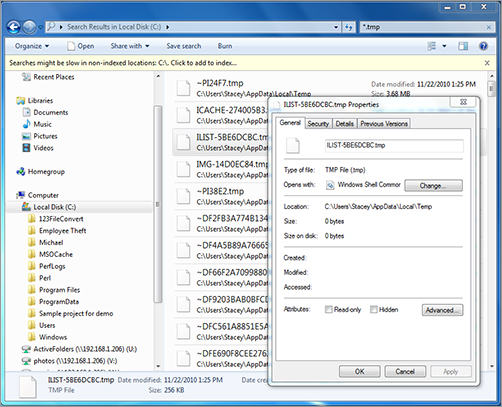
Many applications create temporary files when the application is installed and when a file is created. These files are supposed to be deleted after installation is finished or when a document is closed—but sometimes this doesn’t happen. For example, each time you create a document in Microsoft Word, the software creates a temporary file (with a .tmp extension) like those shown in Figure 6-5. The Properties dialog box indicates that the tmp7201.tmp file was created on September 09, 2010. Temporary files may provide useful evidence.
Figure 6-5: Temporary file listing and properties
If, during your examination of the computer, you find no history files, temporary Internet files, or temporary files in the expected folders, the data has likely been stored somewhere else, so you’ll need to dig deeper to uncover any hidden evidence.
Some additional file types that you may want to look for during a forensic investigation include:
- Files in strange locations
- Files with strange names
- Files that start with a period (.) and contain spaces
- Files that have changed recently
MAC time
Set of time stamps associated with a file. The time stamps describe the last time the file was modified (mtime), accessed (atime), and created (ctime).
MAC time attributes are extremely useful to the forensic investigator and assist in investigating and understanding system behavior, as well as following user activity with regard to a certain file. These time attributes are attached to any file or directory in UNIX, Windows, and other file systems. Microsoft, depending on the version of the operating system, calls these time attributes LastWriteTime, LastAccessTime, and CreationTime, or Created, Modified, and Accessed, as shown in Figure 6-5.
Various other available tools provide similar types of information. For example, you can use X-Ways Trace (available from X-Ways Software Technology AG at http://www.x-ways.net/trace/) to analyze a drive to locate information about Internet-related files. Such tools can be useful in gathering evidence regarding sites visited, last date visited, and cache filenames.
Activity Log Files
A device’s log files contain the primary records of a user’s activities on a system or network and can provide valuable information to the forensic investigator. For example, authentication logs document accounts related to a particular event, along with the IP address of the authenticated user. These files also contain date and time stamps, username, and the IP address where the request originated. Application logs may also yield valuable evidence to the forensic investigation because they record the time, date, and application identifier. When an application is used, it produces a text file on the desktop system containing the application identifier, the date and time the application was started, and how long the application was in use.
Operating systems logs may also reveal vital evidence. Logs from operating systems document system related events, such as types of devices used, errors, reboots, and much, much more. As a forensic investigator, you’ll want to analyze operating system logs to identify patterns of activity along with any unusual patterns or events. Network device logs, such as firewall and router logs, should also be examined as a part of any forensic investigation. These logs may provide vital information or evidence about the user’s activities on the network. The information gathered from network device logs can also be used to support the evidence gathered from logs provided by other systems.
One of the most important pieces of information that a log file may reveal is how an attacker entered a network and the source of illicit activities. For example, log files from servers and Windows security event logs on domain controllers can attribute activities to a specific user account.
E-mail Headers
e-mail header
Data at the beginning of an electronic message that contains information about the message.
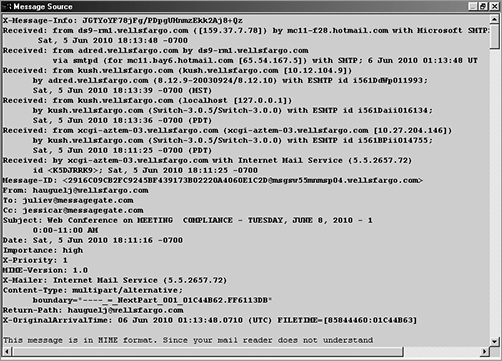
E-mail headers are another source that forensic investigators should examine during the investigative process. Consider the following example. Several employees in a company report that they received e-mail messages from the support team requesting information to update a database. The e-mail instructs the user to send his logon and password information back to the sender. Because IT staff would never request such information from users, you suspect this is an attempt by an intruder to gain sensitive information. In this instance, one of the first items you may want to look at is the e-mail header. Figure 6-6 shows an example of an e-mail header.
Figure 6-6: E-mail header
IP address
A unique identifier for a computer or device on a TCP/IP network.
The e-mail header shows the path the message took from its first communication point of origin until it reached the recipient. The first point is the IP address of the e-mail sender as assigned by his or her Internet service provider (ISP). Analyzing an e-mail header can provide valuable information to the forensic investigator regarding the source of the illicit request. In the following sections, we’ll analyze the lines in the e-mail header to illustrate how to read and interpret this data.
protocol
A set of rules and conventions that govern how computers exchange information over a network medium.
Before communication can begin, a software or device driver must be installed on the computer and a common method of communication or protocol determined. In simple terms, a protocol is the language that computers use to talk to each other. For example, if I speak and understand only English and you speak and understand only French, communication isn’t going to be very effective because neither of us knows what the other is saying or how to effectively talk to each other. The same holds true for computers.
Transmission Control Protocol/Internet Protocol (TCP/IP) network
A network that uses the TCP/IP protocol.
Computers need addresses and protocols to communicate. An IP address is an identifier for a computer or device on a TCP/IP network. Networks using the TCP/IP protocol route messages based on the IP address of the destination.
IP addresses come in two kinds: IPv4 and IPv6 (older and newer versions of the same TCP/IP protocol). An IPv4 address is 32 bits, or 4 bytes, long and is a decimal number between 0 and 255, which is expressed as four octets in dotted decimal notation. For example, 192.00.132.25 is a valid IPv4 address. An IPv6 address is 128 bits, or 16 bytes, long represented using 16 hexadecimal digits (numbers 0 through 9, and letters A through E or a through e). FE80:3043:3B5B:B0D9:B388 is a valid IPv6 address.
packet
Unit of information routed between an origin and a destination. A file is divided into efficient-size packets for transmission.
router
Device (or software) that determines the next network point to which a packet should be forwarded on the way to its destination.
Because of its routing ability, TCP/IP is the standard protocol of choice for most networks. TCP/IP breaks data into smaller units called packets. Devices called routers then pass the packets across the networks by reading the headers to determine if each packet belongs to the router’s network or if it should be passed on to another network. This is similar to sending a letter, where the zip code indicates the letter’s final destination. For example, when a person sends a letter from California to New York, the letter may be transported to various post offices before it actually arrives in New York. If the zip code on the letter does not match the zip code for the area in which it arrives, the letter is forwarded on until it reaches its final destination.
UDP datagram
A message sent using the User Datagram Protocol (UDP), a network protocol used on the Internet. UDP allows applications to send datagrams to other hosts on an Internet Protocol (IP) network without requiring prior communications to set up special transmission channels or data paths.
As a forensic investigator, you should also be familiar with e-mail and web protocols other than TCP/IP. Each part of the TCP/IP protocol suite contains important information for investigators. For example, within a network, an investigator can map an IP address to the Media Access Control (MAC) address. The MAC address identifies a specific piece of hardware, such as an individual network card. Criminals can use special software to change the MAC address of hardware to pretend to send or receive messages using a fake address (or the real address of some other hardware). Also, criminals can use low-level custom code to send messages over different paths and in different sequences (for example using UDP datagrams) that are reassembled at the recipient’s end. A working knowledge of the TCP/IP stack and various protocols is required for a forensic investigator to be able to intercept and reassemble this type of message. Following is a list of the most common web protocols that you’re likely to encounter.
Domain Name Service (DNS) resolves the names that users type into a web browser to their proper network addresses. DNS is most commonly used by applications to translate domain names of hosts to IP addresses.
File Transfer Protocol (FTP) performs basic interactive file transfers between hosts, allowing files to be uploaded and downloaded.
Simple Mail Transfer Protocol (SMTP) supports basic message delivery services between mail servers.
Post Office Protocol (POP) is used to retrieve e-mail from a mail server. It downloads the messages to the client, where they are then stored.
Internet Message Access Protocol (IMAP) allows e-mail to be accessed from computers at various locations (for example, home, office, while traveling, and so forth) without the need to transfer messages or files back and forth between computers.
HyperText Transfer Protocol (HTTP) is a low-overhead web browser service protocol that supports the transport of files containing text and graphics.
Multimedia Internet Message Extensions (MIME) is a type of communications protocol that supports binary, audio, and video data transmission.
The above information is a lot to absorb but it’s necessary to understand for an investigator to make sense of the e-mail header (Figure 6-7).
Figure 6-7: E-mail header
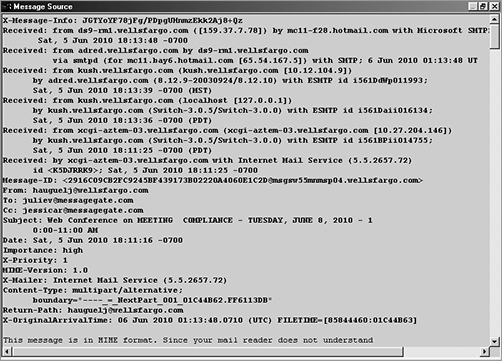
When a user sends an e-mail message, the message is transmitted to a forwarding server or an ISP’s mail server. The mail server adds a Received: field to the header of the e-mail message. The message will then be passed through additional mail servers before reaching its final destination. As the message is transferred from server to server, each mail server adds its own Received: field to the message header on top of the one from the last server. The e-mail message shown in Figure 6-7 has six Received: fields, meaning that it passed through six e-mail servers before reaching the recipient.
Reading the header from the bottom up, the information on the bottom line starts with an X. This entry is added by the sender’s mail server, which records the time (in coordinated universal time, or UTC) the message was received by the mail server from the sender: 06 Jun 2010 01:13:40.0710 (UTC). Moving up in the header, the next X entry shows Internet Mail Service and an ID (5.5.2657.72). This information indicates that the sender’s mail server uses Internet Mail Service and assigned a unique ID to the message. The Received: entry, found several lines above, shows when the next server in the relay received the message. As you follow the information up through the message header, you can trace the path the message traveled through the mail servers (in this case, at wellsfargo.com). The entry at the top was inserted by the last server in the relay before the message was delivered to its destination.
This header comes from Microsoft Outlook 2010. To view header information:
1. Open the e-mail (the e-mail opens on the message tab).
2. Click on the File tab.
3. Click on Properties.
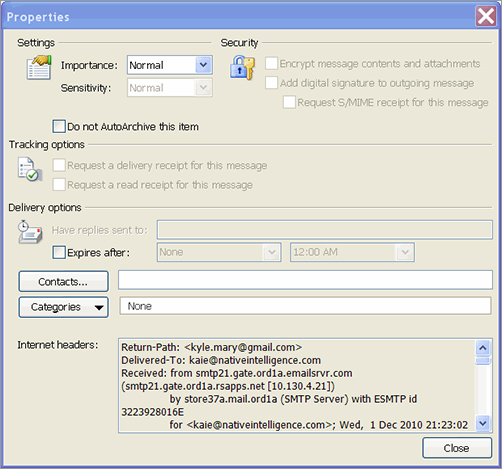
You should now see the header as shown in Figure 6-8. (Note: the process may be different depending on which version of Microsoft Outlook you’re using.)
Figure 6-8: Microsoft Outlook E-mail message Properties dialog box
E-mail addresses and messages are stored in a file within the mail program’s folder. These types of files usually have a .pst or .pab extension. Depending on your e-mail software, the steps may vary on how to expose the e-mail header. The following link offers instructions for some of the more popular programs: http://www.spamcop.net/fom-serve/cache/19.html
Deleted Files
The Recycle Bin, present in Windows operating systems, is another place where forensic investigators may find useful data. Many users do not realize that files sent to the Recycle Bin are not automatically deleted. In reality, the Recycle Bin acts as a halfway house for deleted files, so that files can be undeleted by a user upon demand. The Recycle Bin includes information such as the original location of files before they were deleted and date and time of deletion. When the Recycle Bin is emptied, this information record is deleted along with the other files. Forensic investigators may still be able to recover a deleted file’s contents if they have not been overwritten.
Many people mistakenly believe that when they delete something from their computers, they actually erase all the information in the file. This is not necessarily true. When a file is deleted, the first character of the filename is changed to a hex E5. Chapter 2, “Preparation—What to Do Before You Start,” discusses file systems and explains that a file system keeps a table of contents of the files on the disk. When a file is requested, the table of contents is searched to locate and access the file. When a user deletes a file, the actual file is still there, but the table of contents ignores it. The Davory data recovery utility is a great tool that allows forensic investigators to recover deleted files from a drive (see Figure 6-9). The Davory data recovery is available for download from X-Ways Software Technology AG at http://www.x-ways.net/davory/.
Figure 6-9: Davory data recovery
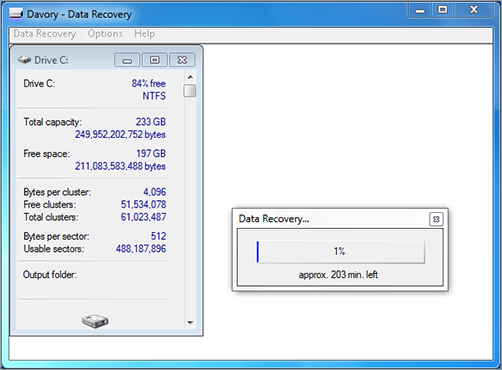
As you can see, the Davory utility recovered 3,905 files that were supposedly deleted. This example illustrates that with a little careful digging, you can find information about a file (and sometimes even the file itself), even when that file has been deleted or moved.
Remember, the data in deleted files isn’t actually erased from the disk. When a file is deleted, the operating system deletes the pointers to the file and shows the space occupied by the file’s data as available, but the data is still there, until other files begin to overwrite it.
Attempts at Password Cracking
As a forensic investigator, you should know what to look for when a system has been hacked. Let’s examine a scenario that involves password cracking to access systems.

Passwords are used for many purposes. Many users don’t create complex passwords, or have trouble remembering more than one. Thus, many users create one easy-to-remember password and use it for everything.
brute force attack
An attack that systematically tries every conceivable combination until a password is found, or until all possible combinations have been exhausted.
Often, an attacker captures the password file before cracking it. On a computer running early Windows versions, passwords are stored in a file with a .pwl extension and one is created automatically for each user. On a computer running Windows XP, Vista, Windows Server 2003, or Windows Server 2008, the password file is stored in a database called the Security Accounts Manager (SAM). On a Windows 7 computer, the password file is stored in the Credentials Manager. A popular way of obtaining passwords is to use a method called a brute force attack. Several programs use this method to obtain passwords. Some of the popular brute force programs include L0phtCrack, Crack, and John the Ripper. If you search the Internet for password-cracking tools, you might be amazed at how much information you can find. So, where do you find evidence on a computer that’s been hacked or otherwise compromised? The log files are always a great place to start a forensic examination.
All operating systems come with the ability to audit and log events. In Figure 6-10, a Windows computer has been set up to log successful and failed attempts at logons.
Figure 6-10: Event Properties dialog box for a Logon Failure attempt
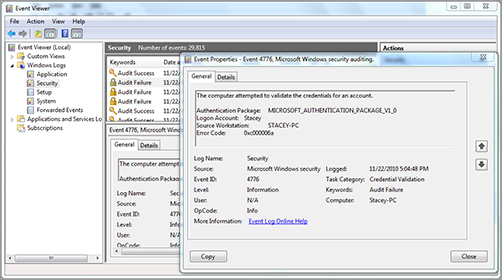
By examining the log, you can clearly observe that there were several failed attempts to log on an administrator made within one minute. As a forensic investigator, seeing this many failed attempts in such a short time period should alert you that someone could be trying to crack the password. Administrators frequently set the lockout threshold at three to five failed attempts. At the threshold point, the account locks and will thwart further attempts to crack it.

Password-cracking programs have legitimate uses. For example, when a network administrator suddenly quits, is fired, or dies, a password-cracking program can allow an authorized person access to the Administrator account.
In addition to those named above, there are several other logs you can review to aid your investigation and find evidence of a computer’s activity. On older Windows operating systems, most of these logs are stored in the C:WindowsSecurityLogs directory. On Windows Vista and Windows 7 computers, the logs are stored in the c:WindowsLogs directory. In Linux, the security logs are located in the /Var/Log/ directory. This directory contains a record of all root access allowed and all denied access. Other logs are stored in /Var/Adm/Syslog, /Var/Admmessages, and /Var/Adm/Kernel.
Log files also reside on routers and intrusion prevention and detection systems, so you should be prepared to examine all of these files as a part of a forensic investigation. Telltale signs often appear in logs, offering strong indications that something is amiss. When you are examining security logs to trace an attempt to crack the Administrator password, look for long entries of random characters, password changes, and repeated occurrences of three dots (...). These are all suspicious items and should raise a flag to forensic investigators to dig deeper. Look through all log files to make sure you understand what has happened to a system.
port scanner
Program that attempts to connect to a list of computer ports or a range of IP addresses.
Often perpetrators use tools such as port scanners to find open ports on a system and then upload a remote access program to take control of that system. The longer they remain undetected, the longer a hijacked system can be used as a conduit. When this happens, you may find evidence of illicit activity in the log files.
As a forensic investigator, you should educate yourself about recent exploit scripts and newly discovered vulnerabilities. Remaining current helps you identify popular means of attack. Become familiar with how systems work, what services are running, when log entries are created, and what those log entries represent. Evidence is frequently found in these files, so you’ll use them often during your career.
In forensics, we’re also concerned with how to crack passwords that a user placed on a system or documents on a system (e.g., a password-protected Word document). This topic is covered in Chapter 7, “Passwords and Encryption.”
