In the first section of this chapter, we explored the types of evidence you can look for on a computer. What happens when you can’t find any evidence but you know it’s there? Chances are it’s either hidden, or somewhere in the trace evidence. (We cover trace evidence in the next section.)
Metadata
metadata
Data component that describes other data. In other words, it’s data about data.
There are various types of hidden evidence, starting with document metadata. Virtually all applications produce some type of evidence that ordinary users don’t know about. For example, as a Microsoft Word document is written and changed, changes are normally tracked. To view this information, simply click the file and then choose Properties (see Figure 6-11).
Figure 6-11: Metadata for a Microsoft Word document
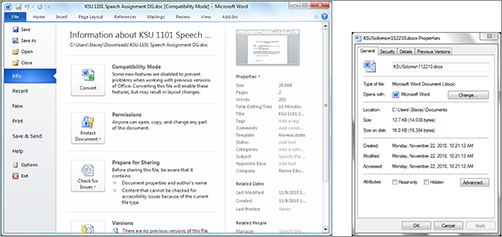
The information in the Properties dialog box can be especially useful to a forensic investigator. For example, let’s say you are dealing with a situation in which a system was compromised and intellectual property was stolen. If a criminal is unsophisticated, you could very well end up with a good lead just by looking at the properties of the new documents. Metadata can be found in most Word, Excel, and PowerPoint documents. However, because metadata has become a known issue, there are ways to delete it. Microsoft released a tool that removes personal or hidden data that might not be immediately apparent when you view a document in a Microsoft Office XP or 2003 application. This tool is called rhdtool.exe, and resides at http://www.microsoft.com/downloads/. Note that this add-in is not compatible with 2007 and 2010 Office systems. The Document Inspector feature in the 2007 and 2010 Office systems replaces this add-in.
Although some metadata is readily accessible through the user interface in each Microsoft Office program, other metadata is accessible only through extraordinary means (for example, opening a document in a low-level, binary file editor such as HexEditor).
Metadata Tips
A criminal might try to hide information by backdating a document created in Microsoft Word—setting the system clock back and then saving the document. Upon a closer look, a forensic investigator can easily uncover the truth. When looking at file directory details, watch for discrepancies between the creation or modified date shown in Windows and time/date stamps in the metadata. For example, Windows might show a Last Modified Date of March 18, 2008, while metadata embedded in the document itself may show a later date. The metadata might also show a different author.
Metadata also tracks total editing time for each document. When a document is surreptitiously backdated, total editing time indicated can be unusually high and indicate that a document was edited for months or even years instead of the hours or days you would normally expect to see. Unusually high editing time is a red flag to a forensic investigator, and may indicate that a document has been tampered with or is a forgery.
Steganography
steganography
Process of passing information in a manner that hides the existence of one message inside another file or message.
The next method for hiding data we look at is steganography. Steganography is a special kind of cryptography that makes the presence of secret data undetectable. It encrypts an original plaintext message into a digital file. The least significant bit of each byte in the image or other data is replaced with bits from the secret message. Such a message can be hidden in a sound file, a graphics file, or in unused spaces on a hard disk. Someone who saves pornography to a hard disk may choose to hide evidence using this method. In some instances, steganography can be used as a means for covert communication among terrorists. Three of the more popular steganography programs include Hide and Seek, Stealth (both of which run on Windows-based systems), and Steganographic File System (SFS), which works on UNIX file systems.
HTML Documents
You can readily view all the code for a web page simply by opening a web page and choosing the View Source option from the View menu on the toolbar (or right-click anywhere on the web page and choose View Source). Figure 6-12 shows the source code for http://www.msn.com/index.html.
Figure 6-12: Source code for the home page on www.msn.com
Most web pages are written in HTML. Figure 6-12 gives you an idea how easy it would be to hide messages or data in web page coding. For example, say a perpetrator was stealing company secrets and wanted to allow a competitor company to access them. The perpetrator could set up his or her own Web site and hide the information in the source code. The competitor could then easily retrieve that information.
Hiding Documents by Changing Names, Properties, or Locations
Most operating systems allow users to hide files based on extensions. Using this feature is as simple as changing the properties of a directory to Hidden on the General tab in the properties in Windows. An untrained eye might never see system files or even the extensions associated with files if the user chose to hide them.
You can hide UNIX directories by putting them in existing directories that have many files, such as in the /dev directory on a UNIX implementation, or by making a directory that starts with three dots (...) instead of the normal single or double dot. To superficially hide files on a UNIX computer, put one dot in front of the file (for example, .myfile). This prevents the file from showing up in the output of a file listing. To see all hidden files, use the ls command with the -a parameter, like this: ls -a.
Hidden Disk Partitions
multiboot system
System that can boot, or start, and then run more than one operating system (though only one at a time).
Data can be concealed in hidden disk partitions. We’ll use the example of a multiboot system, in which, essentially, one operating system is hidden from another. One of our laptops (Computer A) is set up for dual booting (two operating systems). It can boot to either Windows Vista or SuSE Linux. When you view the system in Windows, the Linux partition doesn’t show up, mainly because Windows doesn’t understand the Linux file system. So, Windows acts as though the Linux system isn’t there. If a bootloader is set up to recognize the other operating system, you are given a choice of which operating system to use after a computer boots. This lets you know that more than one operating system is installed. However, some operating systems allow you to choose which operating system to boot to without user interaction. Simply choose the default operating system to boot when you do the setup. For example, another one of our computers (Computer B) dual boots either Windows 7 or Windows Server 2008. An ordinary user would not know that Windows Server 2008 is installed because we configured the system not to display the operating systems at boot time. This is another example where an untrained person might have no idea that hidden data exists. So, we can store files on the Windows 7 drive while booted to Windows Server 2008, and hide the directory so other users have no clue the files are even there. In this instance, the evidence you may be looking for as a forensic investigator could be stored partially on one partition and partially on another partition. If space allows, users seeking to hide could actually install more than two operating systems.
Covert Channels and Other Hiding Places
covert channel
Method whereby an entity receives information in an unauthorized and obscure manner.
Several other methods, such as covert channels, can be used to hide data. A tool such as Loki can transmit valuable data in seemingly normal network traffic. Loki is a Trojan horse that looks like a stream of pings but instead provides a back door to the computer on which the client is installed. After the client is installed, it allows communication to occur without being controlled by a security mechanism.
Suspects can also hide data in white space in documents, behind graphics in documents, and in host protected areas (HPAs) on drives. These areas on a hard drive are created specifically to allow manufacturers to hide diagnostic and recovery tools, but computer savvy people can use them to hide data as well.

Tales from the Trenches: Hidden Evidence
While many technical methods exist for hiding data (examples include steganography, encryption, and digital watermarking), some cases that you work will involve data that was hidden using techniques so simple that any average Microsoft Office user could use them.
I once worked on a case involving two coworkers who transferred information to each other by embedding short messages at the end of Word documents. They changed the color of the text to white so that the message was white text on a white background and remained invisible to anyone who saw the document.
Another simple technique is to use a nonstandard font to write a Word document. The person receiving the document knows which font is needed to view the text and has that font loaded on their computer. Anyone without that font would see only “garbage” on their screen when they viewed the document.
This last technique was used by an illegal drug supplier. He took a photograph of a handwritten sign that contained the instructions and location of how and where a drug transaction was to take place. The drug dealer hoped that anyone monitoring or “sniffing” his network traffic would be unable to “read” the message. A forensic examiner using the search functionality in any forensic utility would not see the message. The examiner would have to use the graphics function in the tool to see such a message.
These and many other techniques for finding hidden data are taught in various computer forensic courses. For additional information about this type of training, please visit Neil’s Web site at http://www.trcglobal.com.
