In general, encryption provides:
Confidentiality Assurance that only authorized users can view messages
Integrity Assurance that only authorized users can change messages
Authentication Assurance that users are who they claim to be
Nonrepudiation Assurance that a message originated from the stated source
To a forensic investigator, the most common exposure to encryption occurs when confronted with encrypted files. Encryption is becoming more common for hiding file contents. Though there are other valuable uses for cryptography, such as securing communication transmissions and authenticating the originator of a message, they are beyond the scope of this discussion.
As a forensic investigator, you must understand cryptography basics and how you should react when you encounter encrypted files.
Usually you’ll recognize encrypted files when an attempt to open a file with a known extension fails. For example, you might attempt to open an encrypted Microsoft Word document in Microsoft Word, but you receive an error message instead. The text of the error message tells you that you need a converter to read the file. In other words, Microsoft Word doesn’t recognize the contents of the encrypted file.
Another sign of encrypted files is a collection of meaningless filenames. Many encryption utilities change filenames to hide the meaning and type of the file.
There are two main types of encryption algorithms. (An algorithm is the detailed sequence of steps necessary to accomplish a task.) Each type has strengths and weaknesses, but they both serve the same function.
Private key algorithms use the same value to encrypt and decrypt the original text. Private key algorithms are sometimes referred to as symmetric key algorithms because the same key is used to encrypt and decrypt files.
Public key algorithms (also known as asymmetric key algorithms) use one value to encrypt the text and another value to decrypt it. One implementation is to use public and private key pairs.
Transposition cipher
An encryption method in which the positions of plaintext characters are shifted by a defined number of places to produce ciphertext. Ciphertext created with a transposition cipher is a permutation of the plaintext.
Encryption algorithms transform an original message, called plaintext, into an encrypted message, called ciphertext. The algorithm also generally provides a method for reversing the process by translating the ciphertext back into the original plaintext message. We looked at the Caesar cipher, which is a substitution cipher, in the previous “Encryption Basics” section. Another type of cipher is a transposition cipher. For example, suppose you want to send a message to a particular recipient that no one else can read. You choose a block transposition cipher to change the order of the letters in the original message. First, write the original message in a block with a specific number of columns. Next, you create the ciphertext by reading down each column.
Our plaintext message is:
I would like to meet with you in private at pier 42 tonight at midnight.
Using a block width of 10, you rewrite the message:
iwouldlike
tomeetwith
youinpriva
teatpier42
tonightatm
idnightxxx
You can add specific characters to make the message fill up the last row.
Next, construct the ciphertext by reading down the columns.
Our encrypted message is:
ityttiwooeodomuannueitiilenpggdtpihhlwrettiiiraxktv4txeha2mx
All you have to do to decrypt the message is to rewrite it in a block and read the message across the rows. The key to the process is knowing that the original block used 10 columns. Once you know the number of columns in the original block, simply divide the length of the ciphertext, 60, by the number of columns, 10. This tells you there are six rows in the original plaintext block. Write the ciphertext in columns using six rows and you can read the original message.
encryption key
A code that enables the user to encrypt or decrypt information when combined with a cipher or algorithm.
All algorithms use some type of value to translate the plaintext to ciphertext. Each algorithm performs steps using the supplied value to encrypt the data. The special value that the algorithm uses is the encryption key. Some encryption algorithms use a single key, while others use more than one. The Caesar cipher uses a single key value. The key value tells how many positions to add to the plaintext character to encrypt and the number to subtract from the ciphertext character to decrypt. As long as the sender and receiver both use the same algorithm and key, the process works.
Private, or Symmetric, Key Algorithms
private key algorithm
An encryption algorithm that uses the same key to encrypt and decrypt. Also known as symmetric key algorithm.
The easiest type of encryption to understand and use is the private key algorithm, also referred to as a symmetric key algorithm. It is symmetric because the decrypt function is a simple reversal of the encrypt function. In other words, it looks the same on both sides. (See Figure 7-1.)
Figure 7-1: Symmetric key algorithm
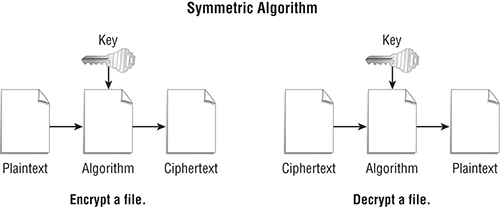
This type of algorithm is simple, fast, and a frequent choice for encrypting data. The key and the algorithm are all that is required to decrypt the file. (Sounds simple doesn’t it? And it is, if you have the key and algorithm.) Although this type of algorithm is common for encrypting files, it can be more difficult to use for message encryption. The problem is managing the encryption key. The key is required to decrypt a file or message. Plus, you have to find a way to get the key to the recipient in a secure manner.
If someone is eavesdropping on all communication between you and your intended recipient, then he or she will likely intercept the encryption key as well as any encrypted data. With the key, they will be able to decrypt files at will. For the purposes of computer forensics, you will more likely find symmetric algorithm–encrypted files on media. The simple reason for this is that symmetric algorithms are fast and easy to use. Because you have only a single key, you don’t need to specifically generate keys and then keep up with multiple values. That means you need the single key.

Don’t assume that computer investigators only deal with file encryption using symmetric keys. You will encounter various types of encryption and algorithms. Encryption is a discipline in itself. This section just highlights those issues you are most likely to encounter.
Key discovery is similar to password discovery. Forensic investigators need to find, deduce, or crack the encryption to get to the key. The biggest difference between cracking passwords and cracking encryption keys is that cracking encryption keys is usually much harder and takes far longer. The simple explanation is that the plaintext for a password is generally limited to a couple dozen characters. The plaintext for a file could be gigabytes. Cracking the encryption key takes substantially longer than cracking a password.
Many well-known symmetric encryption algorithms exist. Here are a few of the more common ones forensic investigators are likely to encounter:
- Data Encryption Standard (DES)
- First published in 1977
- Adopted by the U.S. government standard for all data communications
- Uses 56-bit key (plus eight parity bits)
- Old and weak by today’s standards
- Triple DES (3DES)
- More secure than DES
- Uses three separate DES encryption cycles
- Blowfish
- Stronger alternative to DES
- Key size can vary from 32 bits to 448 bits
- Advanced Encryption Standard (AES)
- The latest, strongest standard adopted by the U.S. government after an exhaustive competition among algorithms designs developed by leading world experts in cryptography
- Based on the Rijndael cipher
- Key sizes are 128, 192, or 256 bits
- Serpent
- Came in second place in the AES competition
- Similar block sizes and key sizes to AES
- Twofish
- Related to the Blowfish algorithm
- One of the five finalists in the AES competition
Advanced Encryption Standard (AES) competition
Sponsored by the National Institute for Standards and Technology (NIST), the AES competition was for an encryption standard to replace DES. The competition began in 1997 and culminated with the announcement in 2000 that the winner of the Advanced Encryption Standard was the Rijndael cipher.
Each algorithm in the previous list can effectively encrypt files. For more security, use a newer algorithm and a secure key. Research some of the common encrypt/decrypt utilities and compare the algorithms they support.
Public, or Asymmetric, Key Algorithms
public key algorithm
An encryption algorithm that uses one key to encrypt plaintext and another key to decrypt ciphertext. Also called asymmetric algorithm.
The other type of encryption algorithm is the public key algorithm. This type of algorithm is also called asymmetric because the decrypt process differs from the encrypt process. An asymmetric encryption algorithm addresses the issue of key distribution by requiring two keys to complete the encrypt-decrypt process.
passcode
A character string used to authenticate a user ID to perform some function, such as encryption key management.
The process starts with key generation. The software that encrypts plaintext will also have a utility to generate keys. When asked, the user supplies a passcode and the utility uses the passcode to generate a private key and a public key. This is called a key pair. Private keys are meant to be secret and should not be disclosed to anyone. On the other hand, public keys can be distributed to anyone. The encryption algorithm uses the private key to encrypt plaintext and the public key to decrypt resulting ciphertext. (See Figure 7-2.)
Figure 7-2: Asymmetric algorithm
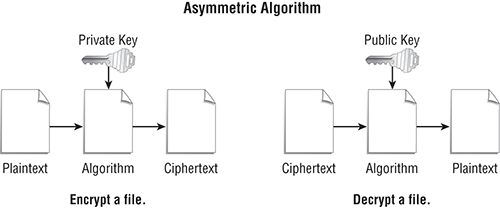
The resulting process allows you to encrypt data with your private key. Anyone who has the public key can decrypt the file or message. This process lets anyone verify that a file or message originated from a specific person. If you can decrypt a file with Fred’s public key, Fred had to encrypt it with his private key. Although this is great for sending messages and verifying the sender’s identity, it doesn’t add much value if all you want to do is encrypt some files.
The most common type of encryption you will run into during evidence analysis is file encryption. For that reason, we focus on symmetric key algorithms.
Steganography
Both symmetric and asymmetric encryption algorithms share one common trait: Encrypted files can be recognized by examining their contents. The fact that a file has encrypted content draws attention to its value. A forensic investigator may want to decrypt a file just because it contains encrypted content and, therefore, probably contains some data of value or other evidence.
Encrypt It All!
If you are going to use encryption, then it’s generally a good practice to encrypt everything to avoid drawing attention to particular encrypted files. As an analogy, if every letter mailed was written on a post card, and you suddenly found a post card placed inside of an envelope, you’d want to know why. Placing the post card in an envelope would draw attention to the fact that something might be hidden in that message. The same is true for encrypting files. If forensic investigators find encrypted files when all other files are unencrypted, they’ll want to know what the user is hiding in the encrypted file.
There is another approach. Steganography is the practice of hiding one message in another, larger message. The original message, or file, becomes the carrier and the hidden message is the payload. Large pictures and sound files make good carriers because the payload can be inserted without changing the original file in an obvious way. Steganographic utilities insert payload bytes into the carrier by slightly changing bytes in the carrier file. If the original data in the carrier separates the changed bytes by wide enough margin, changes are unnoticeable. If you change every 100th pixel in a picture by a single shade of color, the resulting picture appears almost identical to the original.
Steganography allows users to embed desired data into seemingly innocent files and messages. A secret message embedded in a picture file can be sent via e-mail as an attachment and raise no suspicion. Or better yet, the user can simply post the picture on a Web site and there won’t be a direct connection between the user and the person they are communicating with. The ease with which anyone can obtain steganographic utilities makes covert data communication and storage easy.

Keeping Secrets
Intelligence experts suspect that the terrorists who planned and carried out the attacks on New York and Washington, D.C. on September 11, 2001, may have used steganography to communicate with one another. Investigators suspected the terrorists of embedding messages in digital pictures and then e-mailing the pictures (and embedded messages) as attachments to normal e-mail messages. The messages looked like common e-mails with attached pictures. The pictures could have been anything. Nothing was there to provide a clue that the pictures held secret messages. That is the power of steganography.
Detecting steganography is difficult. It can be detected only by noticing the changes to the carrier file or using statistical analysis to detect an anomaly. Detecting changes to the carrier file requires a noticeable difference that you can see or hear. Statistical analysis depends less on human perception because it compares the frequency distribution of colors of a picture with the expected frequency distribution of colors for the file. For audio carrier files, a statistical analysis utility would use sound patterns instead of colors.
Another method for detecting steganography is finding steganographic utilities on a suspect machine. Although the mere presence of such software doesn’t prove steganography is in use, it certainly provides motivation to look harder for carrier files with embedded messages. Few people go to the trouble of acquiring and installing steganographic utilities without using them.
Here are a few steganographic utilities that you might encounter in your career as a forensic investigator. Look at several of these for more information about and examples of how steganography works:
- Puff (http://members.fortunecity.it/blackvisionit/PUFFV200.HTM)
The freeware Puff steganography tool runs in Microsoft Windows and handles many carrier file types.
- Invisible Secrets (www.invisiblesecrets.com)
Invisible Secrets is a full-featured commercial Microsoft Windows application that makes it easy to hide data in several different types of carrier files.
- PhilTools Image Steganography (http://philtools.com/image_steganography/)
PhilTools is a Web site that allows users to submit an image file and a message. The web site hides the message in the image and returns the new image to the user. Hidden messages can also be extracted from a carrier image at this site.
Remember that the appeal of steganography is that its very nature masks the existence of the message. Forensic investigators can look at a suspect drive and easily overlook embedded data if they aren’t careful. Look for utilities that create steganographic files. Also, look for files that would make good carriers. If the circumstantial evidence points to hidden data, chances are steganography is in use.
Next, let’s examine the quality of encryption by considering key length and key management.
