In this section, you’ll look at some sample analysis reports. Most of them are taken from the various software programs described in Chapter 8. The samples show different sections of the reports. In addition to these reports, you can find two sample reports and case summaries in Appendix A of the Forensic Examination of Digital Evidence: A Guide for Law Enforcement document by the National Institute of Justice at www.ncjrs.org/pdffiles1/nij/199408.pdf.
The following sample report starts with a case brief explaining the particulars of the incident.
Sample Report for Copyright Piracy Case
On June 1, 2009, a concerned citizen contacted the police department regarding possible copyright piracy. He explained that he searched the Internet seeking to purchase Acme Accounting accounting and finance software. He purchased that software from a Web site called Knockoff.com that advertised it as “authentic,” but he was unable to register the software he purchased.
When the police department contacted Acme Accounting, they were informed that several other buyers also complained they were also unable to register Acme Accounting software purchased from the same Web site. The case arose from a 14-month investigation led by U.S. Immigration and Customs Enforcement working with the Department of Justice Computer Crimes and Intellectual Property Section.
The investigation was conducted by the Bureau of Immigration and Customs Enforcement. After making an undercover purchase of software from the Web site through the Customs Cyber Center, the agents obtained a warrant to search the suspect’s residence for computers and materials used in making counterfeit software and other evidence related to the theft charges. The agents submitted a desktop computer to the computer forensic laboratory for analysis.
Now let’s move on to the objective of the case. As you follow along, note some of the particulars of the case, such as:
- Computer type
- Operating system
- Offenses committed with the computer
- Case agent
- Where the exam took place
- Tools used
Objective
Determine if the suspect used the desktop computer as an instrument in the crime of copyright infringement and/or as a repository of data related to those crimes.
- Computer type: Compaq Deskpro desktop computer
- Operating system: Microsoft Windows XP
- Offenses: Criminal copyright infringement
- Case agent: Customs Cyber Center investigator, D. Brown
- Where examination took place: Computer Forensic Laboratory
- Tools/Software used: AccessData’s Forensic Toolkit (FTK) and Password Recovery Toolkit
Initial Assessment
This section of the report gives an initial assessment of the case. It establishes proper documents were provided, the goals of the examination were set, and that the case was assigned.
1. The initial documentation provided by the investigator was reviewed. This review determined that:
a. Legal authority was established by a search warrant obtained specifically for the examination of the computer in a laboratory setting.
b. Chain of custody was properly documented on the appropriate departmental forms.
c. The request for service and a detailed summary explained the investigation, provided keyword lists, and provided information about the suspect, the counterfeit software, and the Internet web address.
2. The computer forensic investigator met with the case agent and discussed the investigative avenues and potential evidence being sought in the forensic examination.
3. Evidence intake was documented:
a. The computer was marked and photographed.
b. A file was created and the case information was entered into the laboratory database.
c. The computer was properly stored in the laboratory’s property room.
4. The case was assigned to a computer forensic investigator.
Disk Imaging
The next section of the report documents the analysis. It explains how the evidence was assessed, how the drive was imaged, and how the data was analyzed.
1. The desktop computer was examined and photographed.
a. The computer cover was removed and the hardware was examined and documented.
b. The computer was booted to the BIOS setup screen. The BIOS information was documented, and the system time was compared to a trusted time source and documented. The boot sequence was checked and documented. (Figure 9-3 shows an example of the BIOS setup screen.)
Figure 9-3: BIOS setup screen showing system time
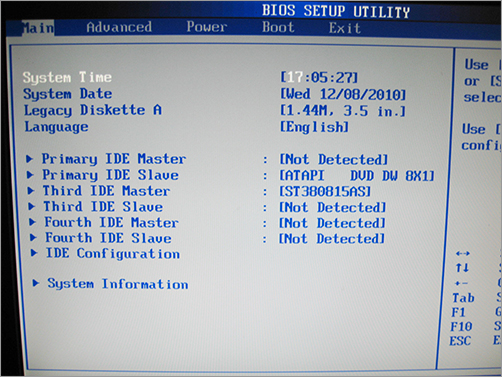
c. The desktop computer was powered off without making any changes to the BIOS.
2. Access Data’s FTK Imager was used to create an evidence file containing the image of the desktop computer’s hard drive.
a. The hard drive was removed from the suspect computer.
b. A hardware write blocker, Intelligent Computer Solutions’ Super DriveLock (http://www.ics-iq.com/), was connected to the forensic computer.
c. The hard drive which was removed from the suspect computer was then plugged into Super DriveLock.
d. Access Data’s FTK Imager was used to make a forensic dd image of the suspect hard drive.
e. A MD5 hash was created of both the suspect hard drive and the dd image and the results compared to validate that the dd image was an exact duplicate of the original hard drive. (The validated dd image is sometimes referred to as the “golden” image.)
3. After the dd or “golden” image was validated, steps were taken to preserve and safeguard this image and return the original suspect computer.
a. The hard drive was returned to the suspect computer, and then returned to the proper legal authorities. (As a forensic investigator, you’ll keep the golden image you created, along with any subsequent images to conduct your investigation. You’ll return the original suspect computer to legal authorities.)
b. The golden image was replicated, and the new image was validated by doing an MD5 hash and comparing the results to ensure it was an exact duplicate.
c. The golden image was then returned to the forensic laboratory safe and locked up.
4. Now there were two copies of the original suspect hard drive—the golden image, which was locked up in the safe, and the second authenticated image, which became the working copy. Now, the investigators were ready to begin the analysis of the image.
Analysis
This section of the report describes the evidence and the steps taken to process the evidence.
1. A laboratory computer was prepared by the investigator using licensed copies of Windows XP, AccessData’s FTK version 1.43, and WinHex version 10.45 SR-2.
2. The FTK evidence files from the desktop computer were copied to the laboratory computer’s hard drive.
3. A new FTK case file was opened, and the suspect computer’s evidence files were examined using FTK.
a. Deleted files were recovered by FTK.
b. File data, including filenames, dates and times, physical and logical size, and complete path, were recorded.
c. Keyword text searches were conducted based on information provided by the investigator. All hits were reviewed.
d. Graphics files were opened and viewed.
e. HTML files were opened and viewed.
f. Data files were opened and viewed; four password-protected and encrypted files were located.
g. Unallocated space and slack space were searched.
h. Files of interest were copied from the FTK evidence file to a compact disk.
4. Unallocated clusters were copied from the FTK evidence file to a clean hard drive, which had been wiped to U.S. National Institutes of Science and Technology (NIST) Special Publication 800-88: Guidelines for Media Sanitization, which can be found at http://csrc.nist.gov/publications/nistpubs/800-88/NISTSP800-88_rev1.pdf.
5. FTK was then used to carve images from unallocated space.
6. The carved images were extracted from FTK, opened, and viewed.
7. WinHex was used to verify the results obtained. A total of 3,592 images were extracted.
8. AccessData’s Password Recovery Toolkit works directly with FTK. (The FTK notifies you that files are encrypted.) The encrypted files were imported into the Password Recovery Toolkit from the FTK, and passwords were recovered for the password-protected files.
9. Once the passwords were cracked, the files were imported back into the FTK and reprocessed.
10. The files were opened using the passwords and viewed.
Findings
This section summarizes the findings that are valuable to the investigation.
The analysis of the desktop computer recovered 265 files of evidentiary value or investigative interest. The recovered files included:
1. Ninety document files including documents containing the suspect’s name and personal information. Text in the files included names of customers who had purchased the software, their methods of payment, and shipping information. In addition, text that described the counterfeit software and pricing structure was found.
2. Fifty-seven graphics files, including high-resolution image files of software labels and packaging materials, certificates of authenticity, registration cards, and copies of checks made out to Knockoff. Most graphics were scanned.
3. Eighty-three HTML files, including Hotmail and Yahoo e-mail inquiries about the software and e-mails between the suspect and customers (including the concerned citizen who reported his inability to register the software he had purchased).
4. Thirty-one graphics files carved from unallocated space depicting copies of checks.
5. Four password-protected and encrypted files.
a. Microsoft Word 2000 document containing a list of personal information about several individuals including names, addresses, dates of birth, credit card numbers and expiration dates, and other information. Password: [gotya].
b. Microsoft Word 2000 document containing information on how to crack the license for the Acme software products. Password: [crack].
c. Microsoft Excel spreadsheet containing the dates and dollar amounts of payments made through PayPal and eBay. Password: [money].
d. Microsoft Excel spreadsheet containing a list of various software products and their licensing key numbers. Password: [moremoney].
Supporting Documentation
This section contains the most detailed information. It describes how investigators arrived at the conclusions in the findings sections. It includes documents and tables that outline all the steps taken to meet the investigation’s objective. The section begins with details about the media analyzed and then moves on to subsections showing string searches and log file analysis.
Figure 9-4 is the file overview. It summarizes the number of items included in the case.
Figure 9-4: File overview showing number of items in case
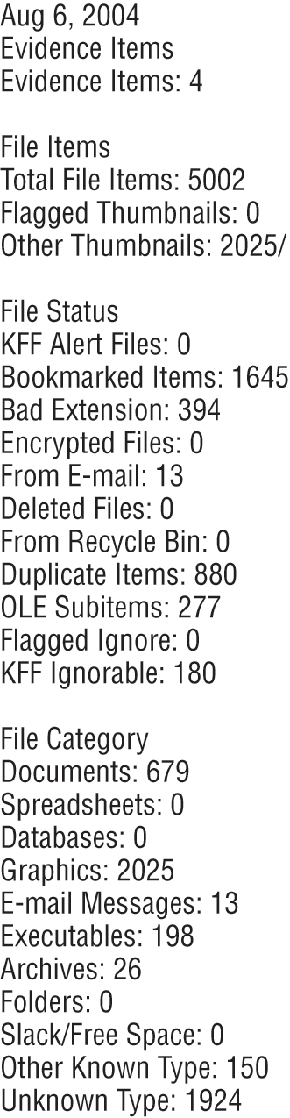
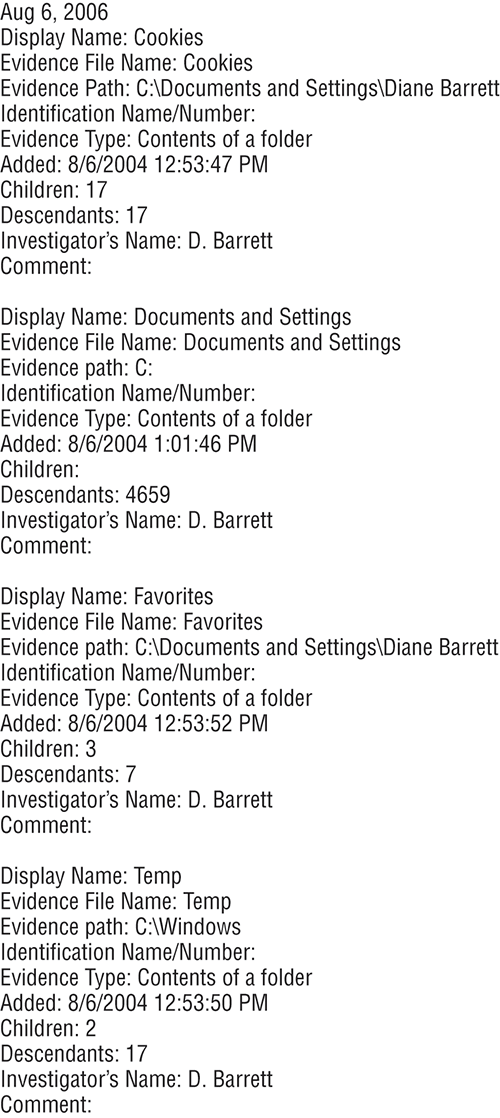
Figure 9-5 is a sampling of the evidence list. These are some of the items that should be included in the supporting documentation part of the report.
Figure 9-5: Sampling evidence list
As you can see from this sample report, the sections outlined are the starting point for your reports. From here the forensic investigator must formulate a report that is understandable to a judge and jury.
Additional Report Subsections
Often, forensic reports include additional subsections, especially if a case is extensive or contains data from many devices and computers. If a report becomes too long, include a table of contents so that everything stays organized in logical fashion. The audience can scan it and get a better idea of the purpose of the report.
Some additional subsections might include:
- If you are investigating an intrusion, include a methodology section on attacks to help the audience understand how attacks are conducted or how the particular attack in the case took place.
- If the case involves an employee illegally accessing confidential information on a vendor Web site, a section on Internet activity could be added to show the browsing history and Internet activity of the employee. This section could also be used to show the download of malicious tools or evidence erase programs.
- When an employee illegally accesses confidential information on a vendor Web site, a user applications section is usually included. The applications section should include a list of all installed applications such as “hacker tools” or malicious software and a description of what they do.
- Sometimes a final summary and/or conclusion may be included with a report.
In the copyright piracy case described in the previous section, “Sample Report for Copyright Piracy Case,” the final summary and conclusion might look like the following.
Summary
Based on the information revealed by the computer analysis, several new avenues of investigation were opened. By contacting the victims listed in the password-protected Microsoft Word document, investigators learned that the victims all purchased software from the suspect through either his Web site or his direct mail. The Hotmail and Yahoo e-mail messages found on the suspect’s computer provided information on additional victims. The password-protected Microsoft Excel spreadsheet containing the dates and dollar amounts of payments made through PayPal and eBay documented that the suspect had sold 2,578 illegal copies of Acme software with a retail value of $750,250.00.

In the case we just examined, the suspect eventually pled guilty and was sentenced to 5 years in prison. Since the report is prepared before the case goes to trial, obviously information on the final disposition of the case would not be included in the report.
Follow-Up Reports
Information regarding the disposition of the case can be included in follow-up reports. Forensic investigators usually issue an Initial Report documenting findings. Supplemental Reports may also be issued as new evidence is discovered and documented.
Recommendations
Instead of a summary or conclusion, you might add a Recommendations section to your report. This can be especially helpful if the case probably won’t end up in court—for example, when the company doesn’t want to prosecute and just wants to know how to reduce its risk in the future.
Glossaries and Appendixes
Use a glossary to define technical terms that the average person might not understand. You might also want to include an appendix for detailed information that would interrupt the flow if it were included in the report proper. When investigating accounting fraud, you will frequently come across large spreadsheets. These sheets are hard to print in a format that is easily viewable. In instances such as this, you will want to attach an electronic appendix.
