Appendix Forensic Investigations, ABC Inc.
Ronelle Sawyer
June 12, 2009
Forensic Report
Case # 000029
Distribution List
| Group, Contact Name | Location | Title/Department/Business Unit |
| Legal | ABC Inc. Headquarters | Security Operations |
| HR | ABC Inc. Headquarters | Security Operations |
DOCUMENT RELEASE AND CONFIDENTIALITY
This document is proprietary and confidential and has been released only to the persons listed above. It may not be distributed outside the organization without written approval from ABC Inc. Legal department.
1 EXECUTIVE SUMMARY
On April 1, 2009, ABC Inc. Legal department contacted the ABC Inc. Forensic Investigations department regarding the cyber forensic examination of a hard drive belonging to Jose McCarthy. There were suspicions that McCarthy was attempting to sell intellectual property belonging to ABC Inc. to a competitor, XYZ Company. The hard drive used by McCarthy was forensically examined to determine if there were any indications of intellectual property theft.
After careful cyber forensic analysis of McCarthy’s hard drive a letter was found showing intent to sell proprietary information.
2 FORENSIC ACQUISITION
2.1 Custody and Storage
On April 6, 2009 Ronelle Sawyer, cyber forensic investigator with ABC Inc., received McCarthy’s hard drive for analysis. Ronelle Sawyer performed Chain of Custody with Legal and took possession of the evidence (see the following graphic). Evidence was locked in a security vault until acquisition was performed.
2.2 Forensic Equipment (Hardware, Software, Adapters, etc.) Overview:
Forensic Workstation—Dell Precision T7500 Workstation:
- Windows 7 Professional—64-bit
- CPU—Quad Core Intel Xeon Processor X5687, 3.60GHz,12M L3, 6.4GT/s
- RAM—12GB, DDR3 RDIMM Memory
- Hard Drive(s)—10,000 RPM Seagate 1 TB SATA drives, RAID 5
Forensic Software:
- Guidance Software’s EnCase Forensic v.7.2
- Access Data’s FTK v. 3
Other:
- Image Masster Solo-4 Forensic
- Digital Intelligence Ultrablock write blocker
- Evidence duplication—200 GB sanitized Seagate Hard Disk Drive
- Type—Barracuda ATA (IDE)
- Model Number—ST360078
- Serial Number—67DF9R30
2.3 Evidence (Original Evidence) Hard Drive Overview
- 80GB Hard Disk Drive
- Manufacturer—Seagate
- Type—Barracuda ATA V (IDE)
Chain of Custody Form
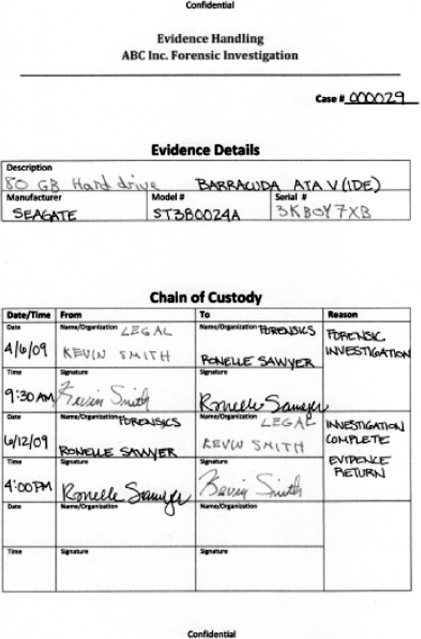
- Model Number—ST380024A
- Serial Number—3KB0Y7XB
- MD5 Hash—59a34105247fb3a26e4bc411fea32eb4
2.4 Acquisition and Verification
On April 7, 2009 Ronelle Sawyer, using Image Masster’s Solo-4, performed a hash analysis of the evidence hard drive, as described in Section 2.3, which resulted in the following MD5 hash value: 59a34105247fb3a26e4bc411 fea32eb4.
After obtaining the hash value Ronelle obtained a bit-for-bit forensic image of the evidence hard drive using the Solo-4.
The forensic image was captured to a sanitized drive, described in Section 2.2. After this acquisition both the original evidence and the new bit for bit image were both hashed. All MD5 hash values obtained were identical: 59a34105247fb3a26e4bc411fea32eb4.
Upon confirmation of image integrity, Ronelle returned the original evidence drive to the secured forensic evidence vault.
Ronelle created a duplicate drive as the forensic lab’s working evidence. Ronelle then connected the duplicate drive to a forensic workstation (described in Section 2.2) via a Digital Intelligence write blocker. Using EnCase Forensic edition 7.2, Ronelle re-acquired the duplicate working copy hard drive in EnCase image file format.
Ronelle divided an 80 GB file into multiple smaller 2 GB pieces for ease of transport, naming these new forensic image files “JoseMcCarthy.EO1” through “JoseMcCarthy.EO40.” Using EnCase, Ronelle hashed the new image and verified the hash match. All future analysis for this case was performed from this image.
Ronelle performed the following preprocessing using EnCase and FTK:
- Opened cases in EnCase and FTK—imported Evidence files “JoseMcCarthy.EOx.”
- Hash verification—match.
- Mounted image within EnCase and FTK.
- Verified the system’s time and data, which were compared to an external time source synchronized to the U.S. atomic clock—system’s time was found to be within five seconds of the actual time.
- Recovered deleted items.
- Verified file types.
- Indexed files.
3 FORENSIC ANALYSIS
Search Criteria:
- Date Range: May 10, 2008–March 26, 2009
- Keywords:
- Janice
- Witcome
- XYZ
- File Types: Any
Searching for criteria above provided two identical documents in separate locations:
1. C:WINDOWSsystem32SoftwareDistributionSetupServiceStartupwups2.dll7.0.6000.374systemm32.dll
2. D:Incriminating Evidence.doc
The text contained in both documents was identical and has been copied here for quick reference:
Hello Janice
I’m looking forward to continuing negotiations. The information I am willing to provide you with will save XYZ Company years of research and development. I feel 100,000 U.S. dollars is a small price to pay for such a large return. Please reconsider as I think this will be mutually beneficial.
Thanks Jose
In uncovering these documents two irregularities were identified:
1. The file named systemm32.dll, located in the system 32 folder created on Friday, February 06, 2009, was actually an MS Word document. Why or how this Word document was stored in the System32 directory and named with a DLL extension cannot be ascertained.
2. The second file, named Incriminating Evidence.doc, was located in a partition that was deleted. This file also was created on Friday, February 06, 2009. Why this partition was deleted cannot be ascertained.
4. CONCLUSION
Two files containing the same text were identified on the hard drive assigned to Jose McCarthy matching the criteria provided. Both files show the same create dates. One file named systemm32.dll, located in the system 32 folder and created on Friday, February 06, 2009, was actually an MS Word document. The second file, named Incriminating Evidence.doc, was located in a partition that was deleted. This file also was created on Friday, February 06, 2009.
