CHAPTER TEN
Cyber Forensics
Investigative Smart Practices
IT IS IMPORTANT TO SPEND just a moment before proceeding, to discuss the difference, albeit potentially subtle, between “smart” and “best” or even “good” practices.
“Best” or even “good” practices are typically grounded in data, analytical analysis, baselines, perceptions, and practices supported by the actions or results of primarily a single company that catches the eye of an industry, which in turn is then joined by other organizations mimicking or adopting these practices over time, inevitably resulting in the establishment of a “best practice.” There seems to be something circular or maybe even incestuous about best practices.
In Chapter 10, the concept of Investigative Smart Practices is introduced. These Investigative Smart Practices are embedded within the sequential “steps” taken during a cyber forensic investigative process.
Smart practices underline the fact that any practice worth such special attention, while also utilizing data and analytical analysis, ought usually to capture the inventiveness required to go beyond “following the pack” to applying independent, logical thought to approaching and solving problems. This means that actions are taken because they are the smartest decisions to make, and steps to take, not simply because others have done so. Smart practices are also defensible on their own and do not rely on “group” approval or acceptance.
Smart practices are employed to help overcome obstacles to innovation. As technology advances and morphs almost daily, the technical challenges and investigative scenarios faced by a cyber forensic investigator will require the implementation and use of smart practices in order to determine a best course of action for the case at hand, which may be a completely different approach or set of actions for the next case. Nonetheless, following a process is integral to the successful investigation of any case.
Remember from the ongoing case: Ronelle Sawyer is investigating whether Jose McCarthy has potentially engaged in the unlawful distribution of his organization’s intellectual property to a competitor, Janice Witcome, managing director of the XYZ Company. Ronelle works for a Fortune 500 company named ABC Inc. Ronelle’s employer is global, extremely large, and departmentalized. These departments are “siloed” such that each performs a single task and only that task. There are procedures, processes, and guidelines for each and every activity, including cyber forensics.
It is important that Ronelle, as a cyber forensic investigator, follow a defined forensic process. If anything, an investigator should follow those processes set forth by the standard forensic practices adopted by the investigator’s organization, department, or agency.
Whatever the forensic process followed, it needs to be followed from the very inception of the investigation, case, or incident all the way to the logical conclusion of the case, investigation, or incident, which can possibly even require the forensic investigator to appear as an expert witness in a court of law.
A reminder: As you read through this chapter, you will encounter words that have been italicized. These words represent key concepts and are more fully defined by a working definition, which is included within a glossary at the end of the book. Should you desire an explanation of any italicized word, please refer to this glossary.
This process, the Investigative Smart Practices, however, need not detail exactly every step-by-step procedure of a cyber forensic investigation, as this could be an exercise in futility; there are so many different directions in which an investigation can evolve, and attempting to follow a specific investigative template or to fit every investigation into the same investigative approach could have disastrous outcomes. Additionally, such procedures would quickly become dated as new investigative technologies are sure to develop.
During the course of our coverage of basic cyber forensic concepts in the previous chapters we occasionally joined Ronelle during her investigation. The actual investigation is only one piece of this investigative process. It may be the piece that pays the bills; however, there are other components to the investigative process that are as equally important. These other pieces may not entail finding the preverbal “needle in the haystack” or the “smoking gun,” yet they are equally as important. Why? Any one of the steps done incorrectly, carelessly, or skipped could thwart and invalidate the entire investigation, regardless of the eventual investigative findings.
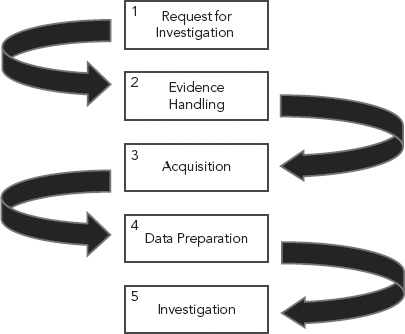
In general, the cyber forensic investigative process is likely to incorporate a combination of the following initial steps (see Figure 10.1). These Investigative Smart Practices, however, are not necessarily meant to be followed sequentially, nor are they mutually exclusive. As stated, each investigation should be evaluated and processed on its own merits and the steps taken throughout the investigation should be those that ensure an organization or department’s cyber forensic investigation procedures are clearly followed, and that there can be no question as to the completeness of the process followed or the accuracy of the evidence collected.
FIGURE 10.1 Generalized Investigation Process Flow
Each forensic case should be considered unique, as each can span the spectrum and diversity of topics: divorce, murder, child molestation, intellectual property theft, employer/employee issues, sexual harassment, cyber extortion, industrial espionage, and the list goes on (it is nearly infinite).
It can be a divorce case based on claims of sexual harassment by an employee. Or perhaps a disgruntled worker steals a copy of his or her employer’s strategic marketing plan and offers it for sale to a competitor, or a child makes a new online friend who later turns out to be an adult with previous convictions for solicitation of a minor. Some cases may include more than a single topic; for example, the case may involve an employer investigating an employee’s theft of intellectual property and industrial espionage, as is the case with Ronelle’s investigation. The possibilities are boundless.
To add to the broad range of investigation types there is also a broad range of investigative practices. Cyber forensic investigators work in all areas and at all levels within society: federal, state, municipal, within law enforcement, at independent small business, and global corporations. Each of these areas is bounded by differing rules, regulations, laws, and procedures. Cyber forensic investigators will face differing hurdles depending upon the organization, state, and even country in which they work.
It is important to remember that forensic investigators are bound by procedures. If an organization has developed written step-by-step procedures, then the organization’s investigators are required to follow those steps. The success or failure of a case can be highly dependent upon assuring that the forensic investigator has followed a specific set of written procedures. A savvy lawyer can make an opposing side’s forensic investigators look foolish. One could easily imagine the cross-examination dialogue: “If you don’t even follow your own procedures how can we be certain you followed existing, required Federal procedures?” In some cases, not following your own written procedures may be comparable to not following the law. Be prepared to follow written forensic procedures.
The process by which procedures can be formulated will be dependent upon the individual organization, taking into consideration any laws that supersede and enjoin the organization to follow these laws. However, there are some general steps or smart practices, guidelines, which should take place and be part of a well-organized cyber forensic investigation. Be advised, these steps may not occur sequentially; some may occur concurrently with other steps, or throughout the entire process.
These Investigative Smart Practices are not the rule but rather suggested smart practices. There may be a situation or an organization that requires additional steps, combines steps, or rearranges the steps shown in Figure 10.1 to a degree; however, skipping a single step or steps or not performing specific steps can lead to potential disaster.
FORENSIC INVESTIGATIVE SMART PRACTICES
Objective: To determine both the validity of the investigative request and to establish the investigative scope.
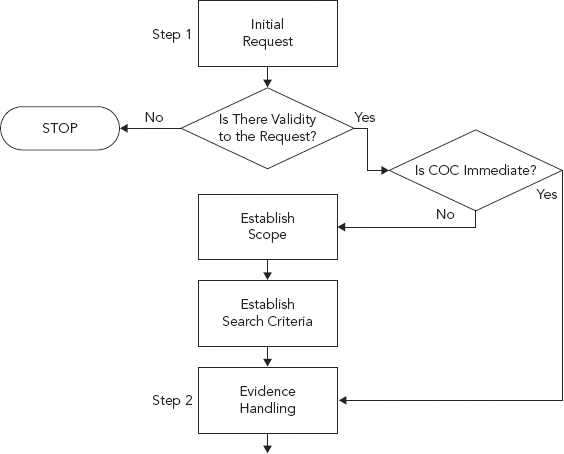
Step 1: The Initial Contact, the Request
In order for there to be an investigation someone needs to come forward and make a request (see Figure 10.2). Usually there are two opposing parties or sides, the requester and the target or subject. The subject is the person who is being investigated. Depending upon the case it may be a spouse, co-worker, contractor, or someone in a foreign country that has written some malicious code. The subject could be labeled “suspect” but naming him/her as such may be presumptuous or lead to subjectivity.
FIGURE 10.2 Step 1: The Initial Contact, the Request
Usually there is some “document of request,” establishing a basis or justification to conduct the investigation. Examples of specific documents that would possibly form the basis for launching an investigation include, but are not limited to, the following:
- Letter of Engagement
- Contract
- Official (Corporate) Request
- Subpoena
- Search Warrant
- Court Order
If there is justification for a specific complaint or reason to investigate, there should also be rules, laws, company policies, procedures, or baselines upon which the investigation request was filed. Again, the specific type of document necessary to begin a forensic investigation will depend upon the type of organization and perhaps the type of case.
For example, before a forensic practice in a large corporate environment can begin an investigation, an approval form submitted via the Legal department or Human Resources department may be required. Law enforcement may require a subpoena or search warrant before an investigation may take place. A small independent forensic practice may require a letter of engagement or contract, from a client, before beginning an investigation.
On the other hand, the requester (for example, executive management, a business partner, spouse, or an aggrieved third party) may require the independent cyber forensic investigator to sign a nondisclosure agreement (NDA), as he or she will no doubt be made privy to proprietary information. Each of these forensic scenarios is completely different and requires unique handling.
It is here that the legitimacy and scope of the investigation is determined. A judge may determine the legitimacy of a law enforcement investigation by issuing a search warrant, but this isn’t so for an internal corporate investigation. The rules or guidelines for a corporate investigation may not require such stringent controls; perhaps a simple request form approved by the Legal department.
However, the cyber forensic investigator should have advice of legal counsel prior to proceeding with an investigation involving accessing an individual’s personal items. In the United States, for example, evidence collection and examination must not violate (as of the writing of this text) the following:
- Fourth Amendment
- Privacy Protection Act
- Electronic Communications Privacy Act
Warrantless workplace searches by private employers rarely violate the Fourth Amendment. So long as the employer is not acting as an instrument or agent of the U.S. Government at the time of the search, and the search is a private search, the Fourth Amendment would not apply (see Skinner v. Railway Labor Executives’ Ass’n, 489 U.S. 602, 614 [1989]).
The cyber forensic investigator will encounter other unique challenges as well. Does the requester own the system and have the authority to request a forensic investigation? In a divorce does the system requiring investigation belong to the requester’s spouse? If so, the forensic investigator may be in violation of privacy laws by performing such an investigation without authority, authorization, court order, etc., and thereby breaking the law. The scope or legitimacy may not always be in the hands of the cyber forensic investigator.
Some additional items that should be addressed prior to beginning a cyber forensic investigation include:
1. Determine whether it is feasible to continue with the investigation based upon information gathered, legitimacy and/or credibility of the complaint, exposure to the organization, and so on.
2. Benefits and/or risks involved in pursuing an investigation.
3. Liabilities and/or risks in not pursuing the investigation.
4. Obligation(s) to pursue (ethical/moral).
5. Are sufficient resources available to successfully carry out the investigation?
It is imperative for the cyber forensic investigator to be provided with the scope of the investigation from management, law enforcement, and so on, or to develop the scope of the investigation based upon the initial evidence presented, violation of law, etc. This may involve an initial meeting in which the requester seeking the cyber forensic investigation provides the forensic investigator with specific parameters of the investigation, the breadth and depth of the intended investigative areas, search criteria, applicable law, etc., thus establishing the scope of the investigation.
At a minimum the search criteria may include several components:
1. Keywords associated with the case being investigated (personnel names, company project code names, competitor names, phrases, etc.).
2. Dates or date ranges during which the act under investigation is reported to have taken place.
3. File types (.docx, .doc, .xls, .pdf, .nef, .tif,.png, .jpg, .wav, .mp4, etc.) associated with the case being investigated.
Some investigators may be strictly bound by this criterion and others may not. Some investigation requests may be general enough such that a broad date range and general file types is all that may be required. A child molestation case performed by law enforcement may not request certain file types, as the investigator may be interested in reviewing any files on the subject’s seized hardware.
All data regardless of type may be fair game be it video, images, emails, Internet artifacts, or chat transcripts. On the other hand, some cases, involving subpoenas for example, may be strictly bound by exact criterion, such as time and date ranges. Going beyond a certain time or date period would be a violation of the court order (i.e., the subpoena). Again, each case or situation is unique.
In a corporate setting, in which the systems, applications on those systems, and the data all belong exclusively to the organization, there may be more flexibility regarding the investigative process. The organization does however need to advise its employees that the systems belong to the organization as does all its contents and data (notification laws vary in the United States by state; thus, it is important to verify which laws your organization may be required to comply with). An organization will usually present this notification banner to the employee, as a pop-up screen right before login so that the employee has to confirm knowledge of the organization’s ownership of the systems and all data on those systems, and accept this condition, in order to successfully log on. This acknowledgment and acceptance by the employee give the organization the right to do whatever it wants to do with their digital property.
This being the case, corporate requests can be (and usually are) as broad and generic as needed (see Figure 10.3).
FIGURE 10.3 Step 1: Request for Investigation
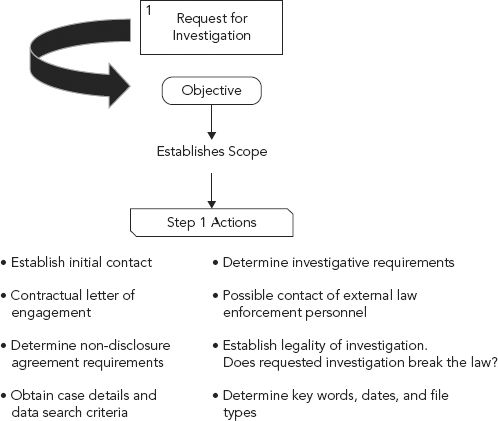
In our ongoing investigation conducted by Ronelle into the activities of employee Jose McCarthy, company procedure states that all investigation requests be routed first through the firm’s Legal department. The Legal department decides on the legitimacy of the investigation, and whether to proceed forward or not. The Legal department also decides the scope of the investigation but, being that they do not perform the actual investigation, at times, the specific search criteria necessary for an efficient investigation may not be obtained in such a manner that would best aid Ronelle in her investigations (e.g., the Legal department will likely lack the technical aptitude to ask the best cyber forensic questions).
Senior management within ABC Inc. decided that their initial concerns were warranted and decided to request a full cyber forensic investigation. Procedure dictates HR and Legal approvals. Request was submitted and approved by both departments. The case was then sent down to ABC Inc.’s forensic department and assigned to cyber forensic investigator Ronelle Sawyer as lead investigator.
After further discussions with senior management Ronelle obtained more details involving the case and was able to outline the following investigation scope criteria:
Scope of Investigation
Date Range—Time period: from employee Jose McCarthy’s start date to his termination date—May 10, 2008, to March 26, 2009.
Keywords—“Janice,” “Witcome,” and “XYZ.” Note: Keywords were not actually supplied with the request but Ronelle was able to create a keyword list from the details provided by management at ABC, Jose’s direct manager, and from ABC’s general counsel.
File Types—Documents: word processing and spreadsheets. Ronelle met further with the Legal department to ask if there were specific file types she should focus on, as this information was not initially provided by ABC management and in many cases may be omitted. File types could also be ANY and ALL; once again, each case is different.
The objective in this step is to determine the scope of the investigation. The scope or boundaries begin with determining if the case is legitimate. If it is determined that the case is not legitimate, violates no laws, has no merit, or is not supported by management, then the need or reason for an investigation must be re-examined, as no scope for the investigation has been determined.
This step can be, and depending on the case particulars, may be required to be, shared with others throughout the organization (e.g., Human Resources, IT Security, Operations) or externally to the organization (law enforcement). Ronelle’s Legal department determined, based upon the preliminary evidence provided, that the initial case against Jose McCarthy had merit and was legitimate, thus clearing the way to begin the full cyber forensic investigation.
Step 2: Evidence Handling
Objective: To preserve the integrity of the evidence; and being able to prove the integrity of the evidence, in a court of law.
It is at this step of the investigative process that the evidence (typically digital but may also be hard copy) is actually handed off to the cyber forensic investigator. The evidence-handling step occurs continuously while the evidence is in the cyber forensic investigator’s possession. Initially it involves the taking possession of evidence, perhaps taking photographs of the evidence, documenting the condition of the evidence, and taking note of any preexisting damage or peculiar markings. Most, if not all, of the cyber forensic investigator’s interaction with the evidence can fall under the evidence-handling step. The specific focus of evidence handling, as presented here, is the movement of evidence, typically physical in nature versus electronic (see Figure 10.4).
FIGURE 10.4 Step 2: Evidence Handling
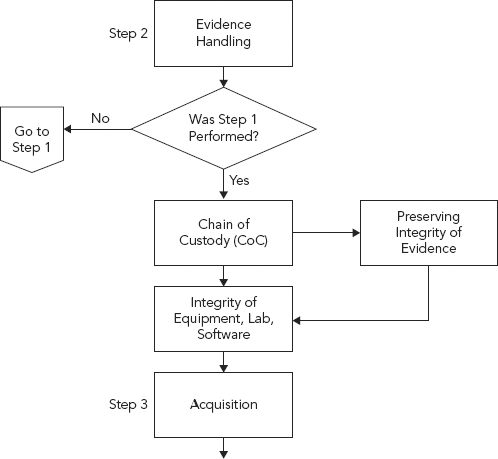
Law enforcement is perhaps most obliged, due to specific requirements and legal compliances, to follow stringent evidence handling procedures. For example, some cyber forensic investigators in a corporate environment may skip photographing and documenting irregular markings on hard drives contained within their environment, where this may be a standard procedure by law enforcement professionals.
The cases presented to law enforcement are at times more serious in nature and tend to be criminal versus those cases that may typically arise within a corporate environment. The consequences of mishandling evidence in a criminal investigation are perhaps higher, so therefore the requirements for controls are higher. A general accepted principle in cyber forensics is it is better to be overly cautious; document every step, photograph every piece, take many notes, and so on, rather than being less diligent and failing to document a potentially critical piece of evidence.
Evidence handling is ongoing and occurs throughout the investigation. It includes how the evidence is stored when not being used and how the evidence is handled when being used. Evidence handling can also include the handling of a cyber forensic investigator’s equipment and tools. These tools include anything that will connect to, attach to, or otherwise interact with the evidence, software, or hardware. For example, an improperly maintained hardware write blocker could possibly short the circuit board on an evidence hard drive. The mishandling of such tools may lead to potential damage or destruction of evidence.
Any equipment the cyber forensic investigator uses to conduct an investigation on the evidence needs to be documented; this includes hardware, software, and connecting media. This equipment should be properly maintained and in working order. Names, versions, upgrades, models, and any other relevant information pertaining to the equipment used (hardware and software) can be considered important and therefore documented per case. As months and perhaps years pass after an investigation, it may not be easy to recall which version of software was used for an investigation.
Later stages of evidence handling, as the case winds down and concludes, may involve returning the evidence to the original owner, if allowed by law. Whenever possession of evidence changes hands, be it upon receipt or return, the chain of custody must be upheld.
The chain of custody is the evidence handling procedure that tracks the evidence as it changes possession. Chain of custody usually takes the shape of a form or document of some sort. A form is usually involved because the signatures of those receiving and those relinquishing the evidence are required.
A chain of custody form will usually contain some of the following fields:
- Case number or assignment
- Date
- Time
- Serial/model numbers
- Description fields
- Location
Chain of custody forms take on many appearances. In some cases a form may be broken down into two separate parts:
1. Item description—describes the articles being transferred. This will include serial and model numbers, make, and descriptions (see Figure 10.5).
2. Signatures—Custody transfer—this piece includes the date and time of transfer and the signature of the releaser and the signature of the receiver (see Figure 10.6).
FIGURE 10.5 Chain of Custody Form (Part 1)
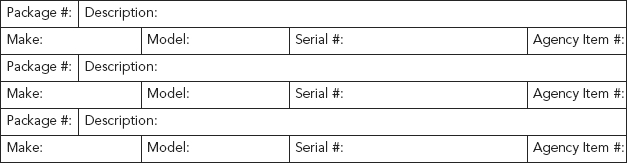
FIGURE 10.6 Chain of Custody Form (Part 2)
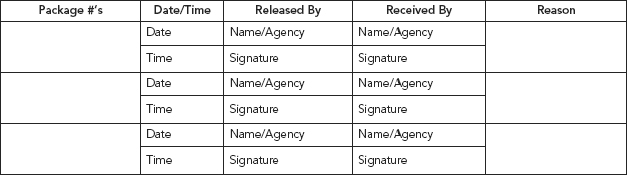
The key objective of evidence handling is ensuring that data is not altered, manipulated, or changed in any way from its originally acquired form, thus the preservation and tracking of the evidence.
Be advised: As explained previously, evidence handling does not necessarily follow the initial request, sequentially. These steps may occur simultaneously, or in some cases chain of custody or the handling of the evidence could occur first. In cases where law enforcement is called to the scene of a crime, these professionals may have to handle and collect evidence well before being directed by the courts as to what needs to be done with the evidence.
The important thing to remember is that chain of custody needs to occur before, during, and after the transfer of any evidence. Beginning an initial chain of custody process should not occur after the evidence has been examined, as being able to prove who has had access to the evidence will allow for accountability over the integrity of the evidence. This accountability is an essential step in preserving evidence (see Figure 10.7).
FIGURE 10.7 Step 2: Evidence Handling
Ronelle received the evidence, in the form of an 80GB hard drive from her Legal department. It was hand delivered in a sealed container. Upon receipt, Ronelle opened the container and found the hard drive and chain of custody form. The form has been filled out and is awaiting Ronelle’s signature.
Ronelle dated the form, signed her name in the recipient field, and copied it. Ronelle kept the original (for internal records keeping and to verify the audit trail and chain of custody “trail”) and returned the copy to the sender for their records. (See Figure 10.8.)
FIGURE 10.8 Step 2: Chain of Custody Form—Signature Field
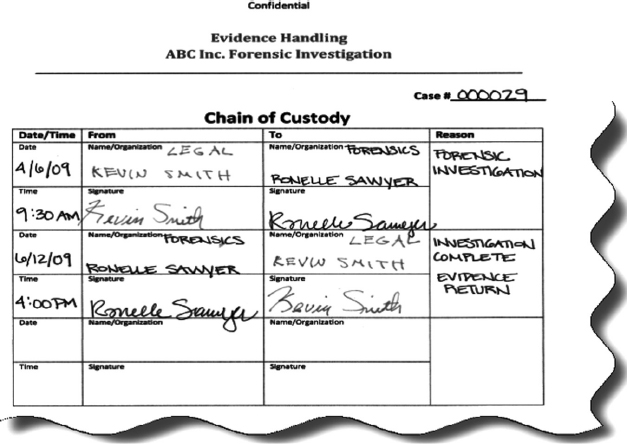
The Legal department filled out the “From” section of the chain of custody document along with a brief description and the serial number of the hard drive; however, the rest of the form was left blank. This is not unusual, as most first responders who are initially responsible for gathering evidence may not have the technical background to go beyond basic macro identification details and may find this a bit too detailed.
Ronelle confirmed that the serial number matched the chain of custody form and the hard drive that was in the container and proceeded to fill out the remaining lines of the custody transfer document, such as the hard drive model and details to describe and identify the hard drive, in the description field. (See Figure 10.9.)
FIGURE 10.9 Step 2: Chain of Custody Form—Evidence Details

After completing the chain of custody documents Ronelle secured the evidence (the hard drive) by sealing it in its container and locking it in a forensic vault, within the forensic lab.
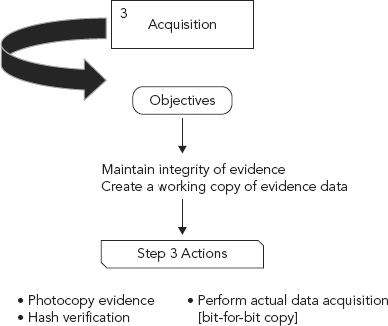
Step 3: Acquisition of Evidence
Objective: Obtain a forensically sound image and preserve the integrity of the original evidence.
The acquisition of evidence generally refers to the imaging of the evidence in a forensically sound manner. A forensically sound manner is one in which the evidence is not altered. Nothing is written, altered, changed, or otherwise modified on the piece of evidence (see Figures 10.10 and 10.11).
FIGURE 10.10 Step 3: Acquisition Process
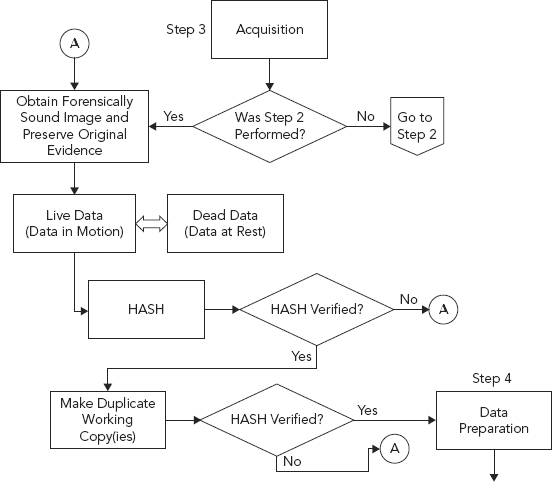
FIGURE 10.11 Step 3: Acquisition Objectives
The acquisition of evidence can, in theory, fall under the previous evidence handling section. Most if not all of the cyber forensic investigator’s interaction with the evidence can fall under evidence handling. As mentioned previously, the evidence handling section discussed the physical movement of evidence and the handing off of evidence, which is the action requiring chain of custody. This line does get blurry.
Consider the case of a live network acquisition. A live network acquisition is one in which an investigator may need to connect to the network of an organization and acquire a system remotely, thereby never actually taking physical possession of the system. However, something needs to be considered, there is a “handing off” of evidence that is occurring, albeit done remotely. In this case, the evidence acquisition and handling would occur simultaneously. Nevertheless, even though these two activities may occur simultaneously, they are still separate activities worth separating for discussion.
In the example of a network acquisition, the evidence handling process would imply that the cyber forensic investigator obtain and carry out proper chain of custody through the acquisition of an accurate IP address to which to connect to the network. The acquisition “action” would then entail using forensically sound network acquisition software to acquire the system (collect the digital evidence).
Evidence
It is perhaps important to stop for a moment in our discussion of the investigative process to address the various types of evidence which an investigator may encounter
According to the Federal Rules of Evidence, there are three classifications or types of evidence:
1. Original. An “original” of a writing or recording is the writing or recording itself or any counterpart intended to have the same effect by a person executing or issuing it. An “original” of a photograph includes the negative or any print there from. If data are stored in a computer or similar device, any printout or other output readable by sight, shown to reflect the data accurately, is an “original.”
2. Duplicate. A “duplicate” is a counterpart produced by the same impression as the original, or from the same matrix, or by means of photography, including enlargements and miniatures, or by mechanical or electronic re-recording, or by chemical reproduction, or by other equivalent techniques which accurately reproduces the original.
3. Best evidence. The best evidence rule is a common law rule of evidence which can be traced back at least as far as the eighteenth century. In Omychund v. Barker (1745) 1 Atk, 21, 49; 26 ER 15, 33, Lord Harwicke stated that no evidence was admissible unless it was “the best that the nature of the case will allow.” The general rule is that secondary evidence, such as a copy or facsimile, will be not admissible if an original document exists, and is not unavailable due to destruction or other circumstances indicating unavailability.1
Generally, “Best Evidence” states that evidence is best in its most original state. This being the case, it is the cyber forensic investigator’s responsibility and priority to keep whatever evidence received in its original (original to the investigator) state. The evidence the cyber forensic investigator received could be a copy of original evidence, but as far as the investigator is concerned the evidence (even though it is a copy and not the original) received is the best evidence. Any changes or alterations to this evidence could have disastrous consequences and may result in the inability to submit in court any of the evidence collected during the investigation. Such a limitation or inability could result in the dismissal of the case and a failure to prosecute a guilty party.
In order to preserve this best evidence it is important that every action taken during the investigative process on will do absolutely nothing to destroy, manipulate, change or alter that evidence in any way. The importance of this cannot be overstated. In step with this mantra, it is also important therefore to be prepared to prove, if required, the integrity of the work in a court of law. Therefore, it is almost equally as critical to document all of the individual steps taken in ensuring the preservation of evidence throughout the investigative process.
In essence, the two main components of evidence acquisition are ultimately preserving evidence and documenting the steps ensuring that preservation.
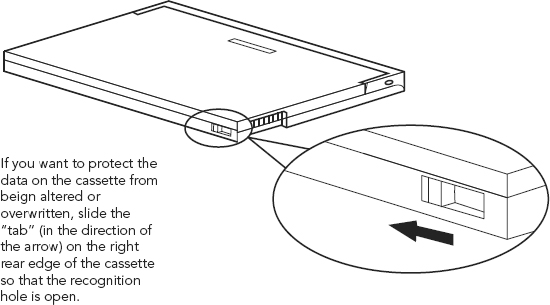
When acquiring evidence it is imperative to use a write blocker. Hardware write blockers are preferred over software write blockers, but each has its appropriate application of use. Write blockers, while allowing data to be copied off of a device, at the same time prevent anything to be written to the device. Remember old cassette tapes? You could push in the top tab and prevent overwriting songs contained on the cassette. (See Figure 10.12.)
FIGURE 10.12 Write Protecting a Cassette
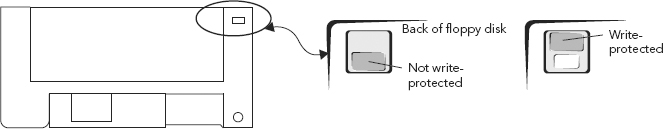
Floppy disks had something similar, but the lock could be switched on or off, allowing for data to be altered on floppy if one changed his/her mind. (See Figure 10.13.) Nonwritable CDs and DVDs are write blocked.
FIGURE 10.13 Write-Protect “Switch” on a Floppy Disk
All these are examples of hardware write blockers. In the forensic field there are many other types of write blockers. At the core of these devices is usually an adapter, which on one end plugs into a source and on the other plugs into a target. (See Figure 10.14.)
FIGURE 10.14 Laptop to IDE Hard Drive Adapter

The source is the evidence (in our case example, Jose McCarthy’s hard drive) and the target is where the evidence will be copied to (a sanitized drive).
It is also imperative to acquire bit-for-bit copies or images whenever possible. It is important to understand the difference between a bit-for-bit image versus just a copy. Aside from the possibility of altering evidence, a large amount of evidence would be skipped or missed by just copying folders off a system or making a logical copy. A bit-for-bit image allows for all of the data contained within the drive to be captured, including the unallocated space, slack space, file system structure, and so on. A bit-for-bit is, as the name implies, the copying of every single bit, verbatim, and transplanting each bit onto the target. It is not a logical copy but a physical copy, a bit-for-bit copy.
Cyber forensics will not always be performed upon a hard drive; as mentioned, there are network acquisitions to contend with as well as cell phones/PDA acquisitions, etc. Bit-for-bit copies are not always feasible or in some cases possible. On a corporate file server for example, each employee may be allocated space for saving work files; this space is sometimes referred to as a Home Directory. It is a user’s personal (for business uses) space on the corporate network. An acquisition of a server containing hundreds of employee’s Home Directories may not be warranted.
A logical acquisition of only the specified subject’s Home Directory may be the best alternative for acquiring this evidence. The same can be true for corporate email. Many corporate email servers, such as Exchange and Domino (used for Microsoft Outlook and Lotus Notes respectively) bundle their data into large files called PST and NSFs. These file types may be found and residing across enterprise email systems. It may not be necessary to image all the servers or the array. Imaging the single file in such a case may suffice. It may be acceptable to mount these files (refer to Chapter 5 for our discussion of mounting files) and image just the components pertaining to the subject under investigation.
Hashing
A hash is usually a mathematical function or algorithm that converts a variable-sized set of data into an invariable, completely random data set. The resulting hash data length is dependent upon the hash type and its intended function. In forensics, uniqueness and distinctiveness is critical, so hash lengths of 128 bits and 256 bits are not uncommon to ensure evidence uniqueness.
Hashes are usually displayed in HEX. Each hexadecimal character can encode 4 bits of binary data. (For a refresher of HEX, refer to Chapter 3.) So, a HEX value of 64 characters is equivalent to 256 binary bits. Likewise, a 128 HEX value would represent a 512-bit hash. Although, currently in cyber forensics, a 128-bit hash is sufficient for establishing uniqueness of data.
The uniqueness of hash values is important in cyber forensics such that no two pieces of evidence are identical. Consider fingerprints as an analogy; every person on the planet has unique fingerprints. Matching fingerprints in a crime scene to those of a specific individual would be inconsequential if fingerprints were not unique; 256-bit hash values allow for 2256 unique values. (For a refresher on bits and possible values associated with bits review Chapter 1.)
In cyber forensics this uniqueness of the hash values will also ensure evidence integrity. To ensure evidence integrity, before the evidence is acquired it is first hashed. The evidence is then acquired and that evidence is hashed a second time. The hash values between the evidence pre-acquisition and post-acquisition need to be identical to ensure evidence integrity.
Any change to the evidence after taking the original hash will cause any subsequent hash to be completely different. Recall hashes are completely random when created, so any alteration of data regardless of scope, amount, or importance of the change will generate a completely new random hash. Any change in the data will completely alter the algorithmic outcome (i.e., the hash value).
Currently, the most commonly accepted legal (read court tried and tested) HASH used is either MD5 (128-bit hash) or SHA-1 (160-bit hash). Once the original evidence has been forensically imaged and hashes verified, the original evidence should be properly stored following smart evidence handling procedures. The originally acquired evidence should not be used in the detailed investigation and e-discovery process. Only copies of the evidence, once verified by hashing, should be used, while the originally acquired evidence is locked away.
There are a variety of different tools which allow for forensic imaging, some are free and others quite expensive. All forensic tools will usually provide for bit-for-bit imaging and will usually contain a built-in hash verification routine. There is forensic hardware specifically made for forensic imaging, such as Image MaSSter’s Solo. There are forensic software suites (software packages with multiple functionality), which allow for imaging as well as other related forensic activities such as HEX editors, drive and file mounting, searching, indexing, parsing, and many other tasks. Examples of such forensic suites include Guidance Software’s EnCase and Access Data’s FTK.
Ronelle received the evidence drive from her Legal department. She followed proper chain of custody procedures and stored the evidence drive in her department’s evidence vault. As time permitted Ronelle went to the vault to retrieve the evidence, completed the chain of custody procedure by signing out the evidence, and brought the evidence to her forensic machine. Ronelle acquired her evidence using EnCase Enterprise and ImageMasster’s write blocker (see Figure 10.15).
FIGURE 10.15 Image MASSter Write Blocker

Ronelle opened a new case file in EnCase and connected the evidence drive to her forensic acquisition system via the write blocker. EnCase was able to identify the physical media (i.e., the actual drive removed from Jose’s work machine) and mount the drive. An MD5 hash verification of the entire evidence disk was performed, returning the hash value 59a34105247fb3a26e4bc411fea32eb4.
Ronelle used Encase functions to perform a full physical disk acquisition. After the acquisition process completed successfully, without any errors, (according to the EnCase software routine), Ronelle performed another hash verification of the acquired data. The hash values of the original evidence and the forensic image created via Encase matched: 59a34105247fb3a26e 4bc411fea32eb4.
Ronelle then returned the original evidence to the vault and again followed the established chain of custody procedures by checking the evidence back into the vault and recording this on the chain of custody document. Ronelle now has an exact copy of the entire physical disk, which she obtained without altering the original evidence.
Step 4: Data Preparation
Objective: Prepare and identify data for analysis and investigation (see Figures 10.16 and 10.17).
FIGURE 10.16 Step 4: Data Preparation
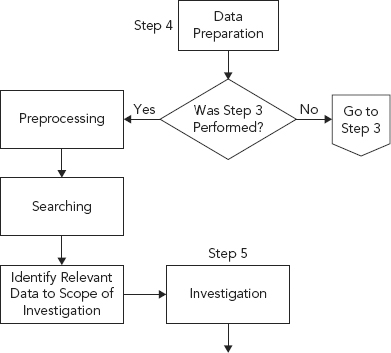
FIGURE 10.17 Step 4: Data Preparation Objectives

Data preparation can be broken down into two types:
1. Preprocessing
2. Searching
Preprocessing
Preprocessing involves those steps that prepare the evidence before the evidence is searched. Searching the evidence, on the other hand, brings about results, which then need to be investigated.
Mounting
The mounting of the filing systems (see Chapter 5) contained within a piece of evidence is necessary so that the data structure can be viewed, so that the organization of the data can be made apparent. Without mounting the evidence, the simple task of finding a file can be very complex and tedious. Imagine having to manually identify the partition type and then manually carving out each and every file by going through each and every byte of the file system. Tedious is an understatement.
Forensic tools (as well as other tools, i.e., operating systems) can quickly mount a drive and its file system, presenting the data in a relatively intuitive manner. Also, more complex files need to be “mounted.” ZIP files and other file formats require mounting in order to be readable and therefore searchable.
Recover Deleted Files
Recovery of deleted items involves recovering files from unallocated space. Typically, the tools that recover these files look for file headers and footers, thereby requiring a file to be entirely intact. Recall from Chapter 4 that when a file is deleted it is first sent to the deleted items folder. Then, when a file is deleted from the deleted items its space is thereby made available, or unallocated. The file is not moved or magically erased; its space is only made available for some other file to be written to. Until this space is overwritten the data contained within the file is still resident on the drive.
Remember, only the entry in the file system is altered such that retrieval by the operating system is not possible. However, the file system entry is not part of the actual file. The file may be deleted and floating somewhere in unallocated space yet still be completely intact. Forensic tools can locate, identify, and restore these files. Certainly some of the metadata that would normally be seen with a saved file will be missing, but the file itself may be in pristine condition. A file can be partially overwritten and not recoverable in its entirety, however, pieces of that file can still be found and used as evidence.
Verifying
Verifying data ensures the data is what it claims to be. As already discussed, there is the evidence verification process achieved by hash matches; but, here verification implies attempting to uncover a deliberate concealment of evidence. Verifying file types is of great importance as a suspect can quickly and easily rename a file.
For example, is a word document (e.g., .docx) really a word document, or is it an image? Recall from Chapter 4 we discussed files and how files are defined in the file header. Another tedious task for a human would be to go through each and every file checking headers for accuracy. Compounded with having to manually extract or carve out each file, as explained previously, a cyber forensic examination would never end. This file verification function is a functionality contained in most cyber forensic software packages at it is imperative for evidence pre-processing.
Verification also implies verifying if perhaps a partition on a hard drive was deleted. Again, this may be an attempt at concealment. Examining the Master Boot Record (MBR) and Volume Boot Records (VBR) would reveal the presence of any additional partitions, which may not be mounted by the operating system. For a refresher on MBR see Chapter 5 and for VBR see Chapter 8. Forensic software automates this manual task, allowing for a quicker identification of potentially missing partitions.
Indexing
Some forensic tools can index the data contained within a piece of evidence. Essentially, indexing organizes all the data in a “database,” which allows for quick search results. Just as Google quickly responds with search results, so too will forensic tools when data is indexed. Google has indexed much of the Internet (websites), allowing for quick search results. If it wasn’t for this indexing Google would have to start searching each and every site every time a request was made. The initial indexing, sometimes called crawling, takes some time but the benefits once indexed may be worthwhile. Some time is sacrificed on the front end for some quick searching on the back end.
Searching
Searching essentially involves refining the original evidence into a smaller subset of data which then can be investigated. Searching can be broad in meaning to encompass a wide scope of data, such as data between date ranges or specific file types. It can also imply the actual searching for more exact criteria, such as a keyword. Indexing greatly improves the efficiency of searching when an exact or precise target, perhaps a keyword, is involved.
Filtering may differentiate itself from searching in that it is usually broader in scope, perhaps applying to data falling into a subset. For example, data falling into a certain date range, or all data of a certain file type. Culling is the process of collecting the refined data that is relevant to the investigation. It differs from filtering in that culling usually invokes an eDiscovery effort. It is the collecting of data pertaining to a certain individual or case.
It all still involves refining evidence into a smaller subset. Instead of searching all data within an organization only the data which pertains to the case needs to be searched. For example, searching only the subject’s profile involved in the incident instead of all users’ profiles contained on a server, or perhaps removing data not within scope (e.g., removing executables from a subset).
Searching also applies to finding those pieces of evidence in unallocated space that are no longer part of a file. Much of a file can be overwritten, but sometimes ASCII text, including remnants of sentences or paragraphs, may be recoverable. However you decide to define these terms, in the end, all actions involve the searching for evidence.
Ronelle now has her image in EnCase. She has already verified her image, so she now begins the evidence processing step of the investigation. Ronelle has mounted the image successfully and is able to view the file structure contained on the drive. This implies that the Master File Table (MFT) has not been altered.
Jose McCarthy, in an effort to conceal his actions, created two partitions on his 80 GB hard drive; one in which he used for day-to-day activity and a second he used to store his personal data. When confronted with the possibility of criminal prosecution he quickly deleted the second partition, therefore making it “invisible” to the operating system.
From the hard drive label (Figure 10.18), Ronelle was able to clearly see that the hard drive is 80 GB, but how would she be able to identify the size of the partition? How would she be able to account for all 80 GB of data?
FIGURE 10.18 Hard Drive Label

If the second partition is not identified she may miss a lot of evidence—in this case, all the essential evidence.
As a cyber forensic investigator, Ronelle, by protocol, examined the partition table and noticed the partition of 60 GB. The starting and ending point of that single partition was quickly determined. Without the use of forensic tools, if Ronelle did not have a working knowledge of the specifics and functioning of the Partition Table, how would our investigator be able to explain the missing 20 GB? Identifying the end of the first partition will be helpful to Ronelle in locating the starting point of the deleted partition. Review Chapter 7 for a refresher in identifying partitions.
Finally, the deleted partition was recovered and all those data associated with the second partition was retrieved, accessed, and analyzed. Ronelle has also recovered all deleted files. She verified all file types and then indexed all the contents of the drive.
In our IP theft case, Ronelle Sawyer is investigating whether Jose McCarthy has potentially engaged in the unlawful distribution of his organization’s intellectual property to a competitor, Janice Witcome, Managing Director of the XYZ Company.
Ronelle is faced with examining millions of pieces of potential evidential data residing on Jose’s hard drive, looking for the proverbial needle in the haystack. Ronelle has filtered all the data from Jose’s hard drive to reveal only data that has been created or modified within the scope of the investigation, and the date range (May 10, 2008–March 26, 2009) of the investigation. From the remaining data Ronelle then searched those data for specific keywords related to the case under investigation, namely, “Janice,” “Whitcome,” and “XYZ.”
Step 5: Investigation
Objective: Finding the data that matches the search criteria.
Investigation is the step within the process that finds the data matching the criteria identified in the investigation request. It is this piece that ultimately finds the proverbial smoking gun. Sure, chain of custody done improperly can destroy a case, but without this evidence there might not be a case (see Figures 10.19 and 10.20).
FIGURE 10.19 Step 5: Investigation
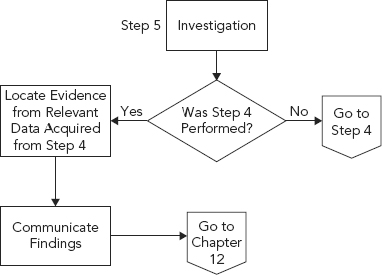
FIGURE 10.20 Step 5: Investigation Objectives
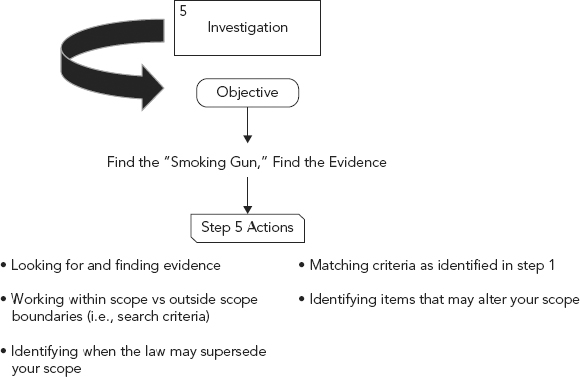
Investigations are case specific and ultimately there are infinite avenues from which cases may evolve. Each and every case is different and it may not be necessary to uncover all of the evidence in all of the cases which come across an investigator’s desk; however, in some cases, every single stone may need to be overturned.
Ronelle’s filtering and searching has returned two documents: “Systemm32.dll” (see Figure 10.21) and a second document named “incriminating evidence.doc.” Recall from Chapter 4 that Ronelle identified a file named “Systemm32.dll” (see Figures 4.10, 4.12, and 4.13), which was actually the incriminating document renamed by Jose in an attempt to conceal his activity.
FIGURE 10.21 Systemm32.dll and incriminating evidence.doc
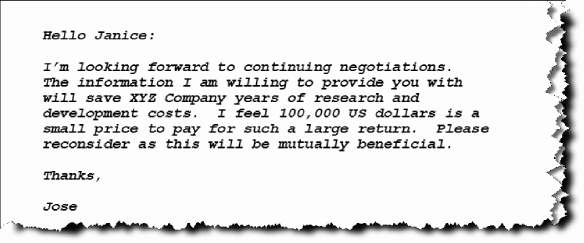
The second document named “incriminating evidence.doc” was located in the second 20 GB deleted partition. The document name, “incriminating evidence,” was created solely for the purpose of this text-based case, as naming a document in such an obvious manner would simplify the computer forensics process as well as being outright illogical.
This document appears to contain the evidence that Ronelle’s Legal department is seeking.
Let’s examine the letter from Jose McCarthy via a HEX editor, shown in Figure 10.22.
FIGURE 10.22 The Letter from Jose McCarthy Shown via a HEX Editor
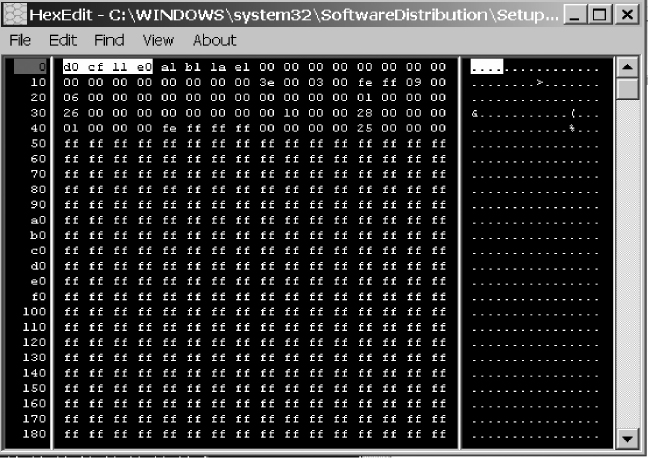
We can easily see the document file signature, d0 cf 11 e0 (Figure 10.22), which identifies this document as a Word document. So even if this document were to be renamed with a .dll extension, reviewing via the HEX editor would have easily identified this document as a Word document.
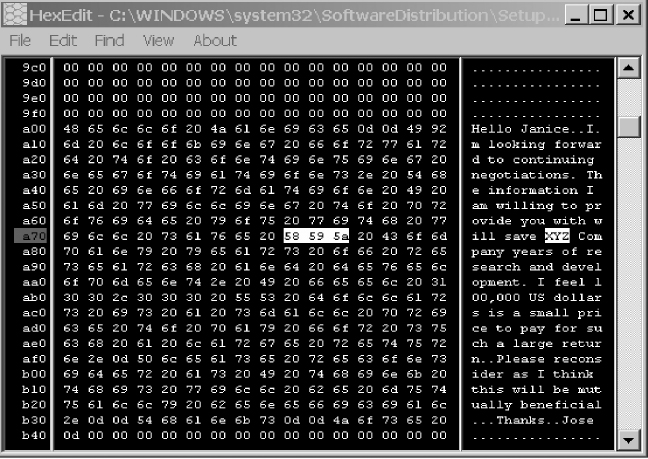
Two of Ronelle’s keywords (“XYZ” [indentified by HEX 58595a] and “Janice”) where identified in the document retrieved from Jose McCarthy’s hard drive (see Figure 10.23). This shows the importance of setting up keywords in such a manner that will ensnare as many real hits as possible. For example, the keyword “Janice Witcome” would not result in a “hit” on the document just reviewed. Understanding human behavior is an important skill when conducting an investigation; as in Ronelle’s case, people usually interact on a first name basis.
FIGURE 10.23 Identification of Search Word Key Terms
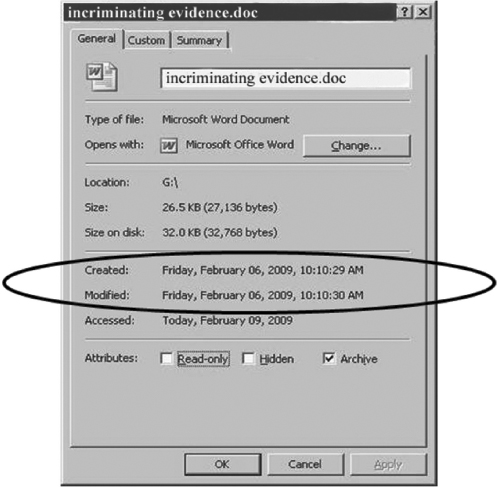
Ronelle made a startling discovery when examining this document. She noticed some inconsistencies with the document’s modified date/time (see Figure 10.24). The created time of “incriminating evidence.doc,” as seen by the document properties and viewed via MS Word, do not match the created time of the document when viewed via the filing system metadata. The MS Word document properties can be viewed by right clicking on the document and selecting properties.
FIGURE 10.24 Inconsistencies with the Document Modified Date/Time
The “created time” metadata pulled from the file system shows a create time of 10:10:28. The forensic tool Ronelle is using displays this data. She is unsure how it is being derived and if it is accurate. Ronelle is able to extract the data from the directory entry of the file system as seen in Figure 10.25.
FIGURE 10.25 Extract of the Data from the Directory Entry of the File System
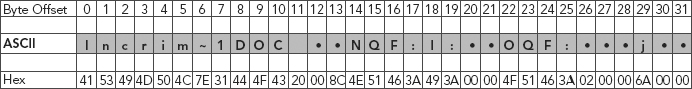
Ronelle understands that such an entry is not an NTFS entry but a FAT entry, and is unsure as to why there is a discrepancy.
Time is an important concept in forensics for more than one reason. As with most topics in forensics, an entire book can be written just on the single concept of time and the relevance of time in an overall investigation.
Stepping back from Ronelle’s investigation, time and the role time plays in a cyber forensic investigation will be discussed in Chapter 11. The time discrepancy issue discussed will be further examined to determine why or how this can happen, with a focus on answering the question, “is a hundredth of a second discrepancy important or relevant in a forensic investigation?”
Understanding why this discrepancy exists could be the difference between successfully presenting a case versus looking incompetent during a deposition, or worse, as a testifying expert in court.
In Chapter 10, we introduced Investigative Smart Practices in a general format to fit most types of forensic organizations and most types of cases. An exact line-by-line instruction set for running a complete cyber forensic investigation is logically impossible to present, as each organization performing a cyber forensic investigation will have their own approaches, procedures, policies, and methods, some dictated by law, others by internal preferences and protocols.
An investigation run by law enforcement, for example, into child pornography versus an internal corporate investigation into the theft of intellectual property may eventually find the evidence necessary to prosecute the guilty; however, the approaches, steps taken, and processes to that end may be entirely different and be supported by completely different protocols and documentation.
It is wise to note that just as peculiar as the differences are between organizations, so too are the differences between cases.
The following Investigative Smart Practices are meant to be broad in scope and used as guidelines:
- Step 1: Initial Contact/Request. The validity and scope of the investigative request is established. This function may be performed by someone outside the cyber forensics field. For example, this can be determined by a judge via a court order or perhaps via the HR department within a large organization.
- Step 2: Evidence Handling. The integrity of the evidence is preserved throughout the entirety of the case. This process occurs each and every time the evidence is handled. Preserving the integrity of the evidence is vital, as is being able to prove the integrity of the evidence in a court of law.
- Step 3: Acquisition of Evidence. This step involves obtaining a forensically sound image of the original evidence. Acquisition of evidence can certainly fall under Step 2, Evidence Handling; however, this step focuses more precisely on the acquisition of the evidence versus the handling of the evidence during acquisition.
- Step 4: Data Preparation. Preparing and identifying data for analysis and investigation. This is the “analyzing” of all data to ensure a valid and complete search. This includes mounting complex files, verifying file types, recovering deleted items, and anything else which would prepare the data for final investigation (Step 5).
- Step 5: Investigation. Focuses on finding those data that match specified search criteria. This step tends to be a little more subjective than the others, being that the investigator may need to examine the search results, discard false positives, and identify the critical piece(s) of evidence, which typically is not conveniently named “incriminating evidence.doc.”
As is the case with evidence hash values, each case is unique. It is this uniqueness that makes cyber forensics such a challenging field.
