8
IoT Sensors: Security in Network Forensics
D. Karthika
Department of Computer Science, SDNB Vaishnav College for Women, Chennai, Tamil Nadu, India
Abstract
IoT forensics is a branch of digital forensics which deals with IoT-related cybercrimes. It includes investigation of connected devices, sensors, and the data stored on all possible platforms. The motive is to identify, collect, analyze, and present digital evidence collected from various mediums in a cybercrime incident. There is no specific method of IoT forensics that can be broadly used so identifying valuable sources is a major challenge. IoT forensics requires a multi-faceted approach where evidence can be collected from various sources. These include variance of the IoT devices, data present across multiple devices and platforms, and data that can be updated, modified, or lost. Data is stored on cloud or a different geography for data to be retrieved. This chapter focuses on with ever evolving IoT devices that there will always be a need for unique, intelligent, and adaptable techniques to investigate IoT-related crimes. Forensics experts will have to develop skill sets to deal with the variety and complexity of IoT devices to keep up with this evolution. There are high possibilities the data on cloud can be altered which would result to an investigation failure. Cybercrime keeps evolving and getting bolder by the day. No matter the challenges one faces, there is always a unique solution to complex problems.
Keywords: Cloud computing, Internet of Things (IoT), networks, sensors, forensics
8.1 Introduction
The Internet of Things (IoT) is having a significant impact on organizations, customers, business innovation device owners, and foundation administrators. The push to make all electronics “smart” is fueling a frenzy of opportunity for digital hoodlums, country state on-screen actors, and security scientists. According to a security expert, the track record in cybersecurity is terrible. The IoT is a quickly expanding field of technology and gadgets that might endanger the economy, partnerships, commercial exchanges, individual security, and wellness.
While the development is mechanical, distinct people have ever-present human inspirations and inclinations to try, intentionally or inadvertently, to misuse those advancements. They confirmed that they are on the approach of experiencing a security nightmare. What does this mean exactly? For one reason, IoT innovation is outpacing IoT security knowledge and awareness. New physical and digital frameworks, gadgets, and connections that were unimaginable 5 years ago are rapidly straining human morality to its limit. Consider a comparable topic that allows us to draw parallels: bioethics and the new, uncommon hereditary building talents that people now possess [1]. They may now be able to produce novel traits in animals and humans by spontaneously mixing DNA from carefully sequenced nucleotide sequences. Just because they can do something does not imply that they should do it all the time. The fact that they can connect to another device does not indicate that they should. That is exactly what the IoT is doing. The necessity to reconcile all the fantastic, confident forecasts about humanity’s future with the truth that human intellect and conduct have consistently and will continue to miss the mark when it comes to idealistic aims. There will always be blatant and hidden criminals; regular individuals who become embroiled in conspiracies, financial disasters, and extortion; tragedies; and profiteers and con artists ready to damage and profit from others’ pessimism. To put it another way, a few people will always be driven to break in and take gadgets and frameworks for the same reason that a burglar would always be motivated to break into a house and grab the most expensive belongings.
8.2 Cybersecurity Versus IoT Security and Cyber-Physical Systems
It is not common to associate IoT security with cybersecurity, yet it is a combination of both. Small data, servers, organizational structures, and record security are only a few of the components of IT. Internet-linked key frameworks may also be monitored and overseen by the government in an instant or suitable manner. Also known as digital important structures, this item has become a crucial distinction between IoT and cybersecurity. Unless otherwise specified, cybersecurity typically ignores the physical and security components of the equipment device, as well as any essential international communications it may have. Unlike most other technologies, the IoT has a unique security need that extends to actual devices and equipment that begin and receive data in the real world. Physical and basic components make up the IoT. In addition to being physical objects, a substantial percentage of IoT devices may represent security risks [2]. Such contraptions can, therefore, cause bodily harm, property destruction, and death.
There was no one, static set of meta-safety rules that applied to all devices and hosts at the time. Every IoT device must have a completely engaging application, and there must be a set of frameworks in which IoT devices may be used. Even though IoT devices come in a variety of shapes and sizes, they all have the following characteristics: Possibility of directly or indirectly transmitting data through the internet in the device’s medium or state, manipulates or displays anything tangible, such as the segment itself, or a rapid association with a factor. A physical device might be an IoT device if it has sophisticated interfaces to connect to the Internet as shown in Figure 8.1. So, the health of an IoT device depends on its use, the physical strategy it employs, and the conditions it is subjected, and the affectability of the frameworks with which the device interacts.
Figure 8.1 IoT sensors over business objectives.
Consider the IoT to be a superset of the cycle, as the cycle will be incorporated into the IoT merely by its web connectedness. A cycle is first and foremost a well-designed system that promotes safety, security, and usability. Developing business IoT deployments should learn from the cycle’s rigorous rigor.
8.3 The IoT of the Future and the Need to Secure
We are always inventing new techniques for dealing with large-scale challenges, even as today’s IoT technologies continue to push the boundaries by establishing new connections between things, systems, and people use of absorbent, a new material, opens a world of IoT possibilities.
8.3.1 The Future—Cognitive Systems and the IoT
Gadgets along with computers, should not anything be said about cutting-edge new research on the verge of computerization, even though the IoT is poised for rapid growth in the next years? To what degree will the protection of the IoT today affect the future? Our understanding of the future of the IoT is greatly enhanced by intellectual frameworks and research.
Transmission of prepared material via information transports, IP systems, and even the Internet is made possible by an advanced transformation of cerebrum detected signals (by pneumoencephalography). BMI-related psychological study suggests that certain smart gadgets in the future will be inquisitive about whether they are guided by a person or another form of cerebrum. On the other hand, humans may be rendered hyper-aware by feeding their thoughts data from sensors located hundreds of kilometers away. To control the automaton, the pilot would use his hands in place of a joystick. Using just concept signals (controls) and input (feeling) given through an interchanges interface, all essential flying maneuvers and alterations are achievable. Let us imagine that a computational framework communicates the airplane’s piton tube velocity via a computer to the pilot’s BMI interface. The pilot “feels" the speed as if it were a wind on his skin. This may not be as far off as it looks.
As an example, consider the sort of IoT security that is necessary in psychological frameworks where the items are human brains and dynamic physical structures. Authenticating a human mind to a gadget or a device to the cerebral cortex is a difficult task. The BMI has a role to play in fostering untrustworthiness. When signs are mocked, destroyed, or their accessibility and timeliness are restricted, what would happen? It is easy to see that the IoT’s apparent benefits pale in comparison to the implications of such future frameworks for mankind. They are all the same in terms of threats and hazards.
8.4 Security Engineering for IoT Development
Brains are generating new cognitive capabilities to deal with difficulties on a massive scale while IoT enhancements are testing individual boundaries by building new connections between things, frameworks, and individuals. Today’s fast-paced technology industry prioritizes market-driven features over security design. As a result, toxic programmers have a wide range of opportunities to abuse the system. Evidence that cannot be denied and the evolution of utilitarian corporate requirements in an ideal work environment are part of a systematic strategy. Before they are made, tested, and transmitted, these requirements have been tried, developed, and resolved into engineering. This is how a cascade model that is faultless and error-free may work. Businesses will build IoT devices and frameworks that utilize a range of inventive techniques, because the world is not flawless.
Businesses and organizations of all sizes, both small and large, would rely heavily on the ostensible security of their suppliers’ technology and programming. The following issues will be covered in this part as they pertain to IoT security building [3]. A safe IoT upgrading method is essential. Include security in the design process from the start. Consistency Consciousness Investigating IoT security frameworks already exist. Security policies and procedures are created. In order to support the IoT, security solutions and administrations must be chosen. Choosing a safe advancement strategy is not easy because there are few alternatives. A new layer is being revealed in the region today.
8.5 Building Security Into Design and Development
Ethical development of IoT products and platforms is the focus of this chapter. This guidance applies whether you are developing a single IoT item or coordinating and transmitting many IoT devices into a project framework. This must be done by focusing on accumulating risks on purpose, following security standards to the end, and maintaining a strong focus on data protection.
As a product developer or framework designer, it is easy to say that security must be considered from the start. But what does that entail? Construction teams have carefully assessed methods to enhance security from inception to end, based on this information. This aspect is missing from many of today’s fast-paced coordinated improvement initiatives. It takes money and effort to achieve this level of rigor when businesses analyze the methods and equipment, they will utilize to fulfill their security goals. To be sure, the cost of these activities is small compared to the cost of having your product or business at the top of news feeds, taking a beating online or getting fined by an administration controller for net negligence that resulted in a major trade-off.
When you begin a change of events or reconciliation project, one of your first responsibilities is to determine your advancement philosophy and determine how to update it into a more security-conscious one. This section outlines a few suggestions for you to consider. When extras help both the item and framework groups, they are considered extras.
8.6 Security in Agile Developments
A development strategy that incorporates security must be considered from the start in order to ensure that all security, health, and protection requirements are considered and met during the events and updates of an IoT device or framework (by a framework, the mean an assortment of IoT gadgets, applications, and administrations that are incorporated to help a business work). A templated approach to development can be beneficial to any project type [4].
Dexterous methods will be used to develop many IoT products and frameworks, allowing for fast configuration, creation, and deployment of highlight sets. When it comes to the security mix, the statement lays out numerous requirements as the deadline nears: Produce functioning code on a frequent basis (typically within a month or two), with the preference being for shorter periods. In order to progress, it is essential to have working programming. The tight development deadlines associated with agile initiatives are at the heart of the problems that must be addressed in order to provide a coordinated and safe development process. Various security requirements must be satisfied before an object can be considered safe. Addressing these demands in a short development cycle is difficult. An increased focus on security also hinders communication of utilitarian customer tales in event of an unexpected change of circumstances.
Securing needs requires the same technique and thinking as other non-functional criteria such as unshakable quality, execution, adaptable comfort, movability, and accessibility. Client stories, according to some, must contain nonfunctional demands as part of the notion of doneness. Transformation of all security (and nonfunctional) requirements into imperatives does not scale effectively when the development team is working with a significant number of security requirements. In particular, the technique emphasizes the management of security needs and offers suggestions for arranging requirements in a way that reduces pressure on the development team during each cycle. Security criteria One-Time, Every Sprint, and Bucket guide Microsoft’s approach. Each Sprint requirement is unique to each run and is assessed during run planning. The criteria are suitable for the safe execution of an undertaking and other needs that must be met from the beginning, for example, developing secure coding rules that can be followed during events and developing a list of suggested programs for non-traditional segments/libraries. Basic needs are those that can be carried out and satisfied throughout a project. By categorizing these requirements into basins, organizations may choose whether to include them in their planning.
8.7 Focusing on the IoT Device in Operation
Merchant goods as a service contribution, in which users pay for a set of benefits each month, are a fascinating aspect of the IoT. Costly clinical imaging frameworks are an example. Customers can rent IoT equipment, which is then tracked for billing reasons.
It is possible for customers to create and record changes in their IoT devices by connecting them to seller’s cloud platform, which is connected to the seller’s cloud infrastructure. Some of these items are periodically outsourced to an ODM that specializes in IoT. The OEM then incorporates these operational costs into the master supplier agreement between the two firms (MSA). The administration of IoT devices can also be assisted by some carriers, if this is done in the client’s domain [5].
Solid development activities (DevOps) strategies and time are essential for operational IoT frameworks, given the need of integrating them into client operational frameworks, as well as the requirement to support robust and varied back-end foundations. DevOps combines agile development techniques such as Scrum or Kanban with a strong focus on activities.
8.8 Cryptographic Fundamentals for IoT Security Engineering
Individuals that create consumer or industrial IoT goods or incorporate IoT communications into their companies are the target audience of this chapter. Cryptographic security in IoT deployments and implementations is laid out for readers in this book. This section deviates from the rest of the book’s focus on practical applications and recommendations to cover some of the more difficult underlying principles connected with applied cryptography and cryptographic implementations. Although many cryptographic implementation mistakes and deployment vulnerabilities are still being used by even security-conscious IT companies today, the authors believed it was necessary to share this history. Because of this, several previously uninterested sectors (such as manufacturers of household appliances) have begun connecting their goods to the internet and integrating IoT features into their products. Meanwhile, they commit several errors that might put their consumers at risk.
An in-depth examination of how cryptography is used to secure IoT communication and messaging protocols is presented along with recommendations for further cryptographic protections at different levels of the technological stack.
8.8.1 Types and Uses of Cryptographic Primitives in the IoT
It is amazing to see how quickly items are being sold as service contributions, where consumers pay a monthly subscription fee for certain privileges. Costly clinical imaging frameworks are an example. Renting out IoT devices to clients and tracking its usage for billing purposes distinguishes this firm [6].
It is possible for customers to create and record changes in their IoT devices by connecting them to seller’s cloud platform, which is connected to the seller’s cloud infrastructure. An ODM that works with the IoT framework may outsource such components from time to time. When most people think about cryptography, encryption comes to mind. It is well known that information is “mixed” to keep unauthorized parties from understanding it. All the IA goals stated above are partially or totally met by genuine cryptography. The use of cryptographic natives to achieve a larger, more sophisticated security purpose should only be done by security experts who understand applied cryptography and convention design. Security objectives may not be met due to even the tiniest error, which can lead to expensive vulnerabilities. The number of ways to weaken cryptographic security is greater than the number of ways to do business.
Cryptographic crude sorts fall into the accompanying classifications:
- • Encryption using symmetry (and decoding).
- • Asymmetric hashing is a type of hashing that is performed on a pair of marks created with digital technology.
- • Symmetric: MAC is used to verify and legitimize information from its beginning.
- • Asymmetric cryptography employs elliptic bend (EC) and number factorization (IFC). As a starting point for validation, these, like non-denial, give respectability, personality, and expertise.
- • A random number’s age: Most of the cryptography’s assumption requires large quantities generated from high-entropy sources.
The use of cryptography in separation is uncommon at best. As opposed to this, it provides the fundamental security characteristics required by upper-layer communication and other protocol standards. Examples include Bluetooth, ZigBee, SSL/TLS, and other conventions (for instance, how to deal with a bombed message uprightness check).
Conditional charges are under the master supplier agreement between the two companies (MSA). Many IoT service providers, however, provide secondary administrations to their IoT device services. Operational IoT frameworks demand robust development tasks (DevOps) strategies and time due to their reach into client operational frameworks and the requirement to support powerful and adaptable back-end foundations. It is a combination of coordinated improvement efforts based on Scrum or Kanban with a strong task-focused approach to software development and operations.
8.8.1.1 Encryption and Decryption
Encryption is the most well-known cryptographic service; it is used to jumble or disguise data so that unauthorized parties cannot read or comprehend it. In other words, it is employed to secure information from eavesdroppers while enabling only the intended recipients to interpret it [7].
In Figure 8.2, cryptography methods are accessible on both an asymmetric and symmetric basis (explained shortly). To cipher—encrypt, the encryption method requires a cryptographic key and unprotected data. This ensures that no one can listen in on the conversation. When the data is needed, it is decoded by the receiving party using a special key. Unencrypted data is called plaintext; encrypted data is known as ciphertext. If the information is encrypted before it reaches IoT device B, the listener is at risk. A related topic is where encoding happens throughout the communication stack, and what protocol is utilized, based on the capabilities of the endpoints involved in communication. To protect communications, engineers were obliged to decide on which encryption method they would use, depending on the threat model they used. Considering that many encrypted protocols function solely point-to-point and must travel via several gateways, some of which are obviously hazardous, this is a high-risk industry.

Figure 8.2 Encryption and decryption process.
To prevent data loss, sessions and apps must be encrypted from the beginning to the conclusion. Among the most prominent instances are the electricity sector and the vulnerable SCADA protocols employed there. One of the most popular safety upgrades is the construction of secure communication gateways (where recently extra encoding is performed). Others use end-to-end secured protocols to tunnel unsecure protocols through a secure tunnel. In system security designs, each encoding security technique should be taken into consideration, noting where plain-text data is stored (in storage or transit) and where it must be reincarnated (encrypted) into cipher-text. End-to-end encryption should be recommended wherever practicable. To put it another way, a secure-by-default posture must be reinforced all the time.
8.8.1.2 Symmetric Encryption
Simply said, symmetric encryption implies that both the sender (scrambled) and the recipient (unscrambled) utilize the same cryptographic key. The calculation, which can encode or decode depending on the mode, is a reversible activity, as seen in Figure 8.3.

Figure 8.3 Symmetric encryption.
Several standards utilize an alternate symmetric key for each movement heading. Device A, for example, might encode to Device B in this manner by utilizing key X. Key X attends both meetings. The key Y, which is shared by both groups, may be used in the other direction (from B to A).
In addition to the cryptographic key and information processed by the figure, an introduction vector (IV) is periodically asked to help certain figure modes (clarified in a second). Figure modes are essentially various ways for bootstrapping the figure to work on successive chunks (obstructs) of plain-content and figure content information beyond the fundamental figure. The electronic codebook (ECB) is the fundamental figure, which works on a single square of plain-content or figures message at a time. Because repeated squares of indistinguishable plain content will have an indistinguishable figure content structure, jumbled information will be rendered impotent against catastrophic traffic inquiry, the ECB mode figure is employed without anyone else on occasion. There is no need for an IV in ECB mode; all that is necessary is the symmetric key and information to act with. In the former ECB, square figures may have worked in square tying modes and stream/counter modes, which were examined directly.
8.8.1.3 Asymmetric Encryption
Asymmetric cryptography essentially implies that two separate, paired keys, one public, and the other person, are used to encrypt and decode, respectively in Figure 8.4. IoT device A ciphers to IoT device B using IoT device B’s public key in the image below. Device B, on the other hand, encrypts data for device A using device A’s public key. Personal keys for each device must be always kept secret, or else anybody or whatever with them will be able to decrypt and consider the data.
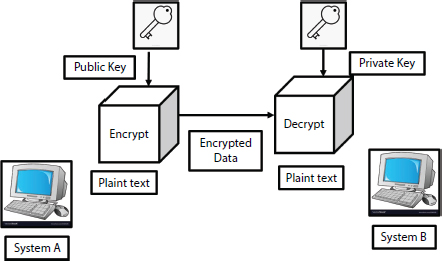
Figure 8.4 Asymmetric encryption.
The most widely used asymmetric encryption technique nowadays is RSA (Rivest, Shamir, Adelman). It is an integer factorization algorithm that can encrypt and decode small amounts of data. The advantage of this method is that the traffic can only be decoded by one birthday party that possesses the corresponding RSA private key.
The drawback of uneven encryption (RSA) is that it can only encrypt up to the modulus length in question (1,024 bits, 2048 bits, and so on). Because of this issue, the most common use of RSA public key encryption is to encrypt and communicate other small keys (typically symmetric) or random values used as predecessors to cryptographic keys. Larger RSA modulus sizes (for better computational resilience against attack) are currently promoted with the aid of NIST.
8.8.1.4 Hashes
Cryptographic hashes are designed to represent a big message at random with a small, unique fingerprint. They can be used in several security tasks (the hash). They require the following qualities: They keep any information about the hashed data secret (this is named resistance to first pre-image attacks) They prevent two messages with completely different hash from sharing the same hash. They generate pricing that looks to be entirely arbitrary (hash).
8.8.1.5 Digital Signatures
A digital signature is a cryptographic feature that offers trustworthiness, validation, data beginning, and, in certain circumstances, non-renunciation security. They are intended to be unique to the underwriter, the person or device in charge of marking the message and who holds the marking key, like a hand-scribbled mark. The author of the mark in the accompanying graph may now accompany the message (now known as the marked message), allowing anybody with the necessary key to do the opposite of mark activity, known as signature check [8].
As a result, the verifiers should not trust the information or its source if the mark confirmation technique fails. Derivative marks, which are deviant in nature, and private keys that are typically not shared (and should never be disclosed) make them a valuable means of doing both substance and information verification, guaranteeing the respectability of information, and offering non-revocation capabilities. The following are examples of basic twisted advanced mark calculations:
- • RSA
- • DSA (digital signature algorithm)
- • Elliptic curve DSA (ECDSA)
It is impossible for any organization to deny signing a message since digital signatures are produced using a single, private (unshared) key. As a result, the signature could only have come from the entity’s private key. An array of cryptographic protocols employs asymmetric digital signatures. Examples include SSL/TLS/IPSEC/S/MIME networks, ZigBee networks, Connected Vehicle Systems (IEEE 1609.2), and many more.
8.8.1.6 Symmetric (MACS)
It is also possible to produce marks using symmetric cryptography. In the case of asymmetrical digital marks, D. MAC is a term that is occasionally used to describe symmetric marks. Because MACs are created using an asymmetric computation method, the same key is utilized to generate and validate them. MAC is often used to refer to both the computation and the final mark, thus keep that in mind when using the word [9].
This code is often generated by hash work or a symmetric figure in various scenarios. To protect both sender and receiver, MAC keys are utilized (as indicated in the adjacent outline) (verifier). Considering the possibility that the symmetric keys used to create MACs are shared, MACs generally do not claim to provide personality-based substance validation (nor can non-revocation be guaranteed), but they do provide enough check of cause (especially in momentary exchanges) to qualify as information starting point confirmation.
8.8.1.7 Random Number Generation
Numerical unpredictability is essential to cryptography since it is utilized in the creation of many cryptographic variables, including keys. While it is tough to compute or replicate huge, unexpected amounts (such as animal power), extremely deterministic quantities are not. They can be classed as either deterministic or non-deterministic RNGs (random number generators). As the name suggests, deterministic models are calculation-based and will consistently produce the same response for a single set of input data sources. Non-deterministic methodologies, alternatively, the RNG, generate arbitrary data, usually from relatively uncommon physical events such as circuit turbulence and other low-inclination sources (even semi-arbitrary hinders happening in working frameworks). It is no surprise that RNGs are among the most delicate components of a cryptographic device, given their effect on key security and sources.
Subverting a cryptographic device’s RNG so that you can see the cryptographic keys it generates invalidates the device’s security. It is a device that produces random data that may be used for a variety of applications including cryptographic keys, introduction vectors, padding, and more. They require seeds that must be very random and come from sources with high entropy levels in order to work properly. In the event of a seed or entropy source tradeoff, the RNG’s yields will suffer, and cryptography will suffer as a result. This leads to data manipulation, mockery of encounters or even more terrible acts.
IoT RNGs must be seeded with high entropy sources, and the entropy sources must be completely protected from disclosure, alteration, or any other form of control, in order to be effective. The random clamor features of electrical circuits, for example, vary with temperature; therefore, it is sensible to set temperature boundaries from time to time and legitimately halt entropy gathering capacities that depend on circuit commotion when temperature limits are surpassed. In smart cards (for example, credit/charge swap chip cards), this component regulates the chip’s temperature in order to avoid attacks on RNG.
During the design phase, a device’s entropy quality should be assessed. There should be consideration given to the min-entropy characteristics, and the IoT setup should be flexible enough to avoid the NDRNG from being stuck and contributing to the RNG in a similar way. When developing the cryptographic architecture for an IoT device, it is important to have top-tier random number generation capabilities, even though it is not a commercial concern. RNG state, RNG data sources and RNG outputs are covered in this section, as well as extraordinary entropy production and entropy state insurance.
8.8.1.8 Cipher Suites
Combining one or more of the computing types to accomplish the most essential security features is the most enjoyable aspect of applied cryptography. In some communication protocols, these rule groupings are referred to as cipher suites. Depending on the current standard, a figure suite offers the specific structure of computations, possible key lengths, and applications for each.
8.9 Cloud Security for the IoT
A brief summary is provided in this section on cloud management and IoT’s security. By using cloud administrations and security best practices, companies may work together and govern IoT enterprises that span several authorities and jurisdictions. AWS, Cisco (Fog Computing), and Microsoft Azure components were examined for their cloud and security contributions [10].
Security for IoT components that demand huge amounts of data is closely tied to the cloud and cloud security. On the agenda will be IoT data archive and disclosure frameworks along with best practices for these administrations’ assurance. IoT features in the cloud need determining whether elements of security are under the client or cloud provider’s purview. Topics covered in this section include:
Section 8.3 focuses on the cloud as it relates to and benefits IoT. As a result of IoT, they will also find new cloud-related requirements. On the way, they will identify and analyze IoT-related security threats both within and outside of the cloud, as well as cloud-based security policies, and look at additional contributions to this sector.
- • Examining IoT contributions from cloud service providers (CSPs): They will investigate a couple of CSPs as well as their product/security-as-a-service management. The environment cloud computing is exemplified by Cisco’s Fog Computing, Amazon’s AWS, and Microsoft’s Azure.
- • Controls for cloud IoT security: An examination of the cloud’s security capabilities to develop a solid IoT venture security plan.
- • Creating a successful, all-encompassing IoT cloud security design: This section combines and matches available cloud security contributions to build a successful, all-encompassing IoT cloud security design.
- • New cloud-enabled IoT calculation subheadings: Again, we are moving on from the cloud security debate to quickly investigate new processing standards that the cloud is keen to provide.
8.9.1 Asset/Record Organization
The capacity to track assets and inventory is one of the most critical components of a secure IoT. Device characteristics are included in this category. For corporate asset/inventory management, the cloud is a suitable solution, as it provides a view of all devices that have been registered and permitted to function inside the organization’s limits.
8.9.2 Service Provisioning, Billing, and Entitlement Management
The fact that many IoT device suppliers would provide their products as a free bonus to consumers makes this a very interesting use case. Device operations need to be authorized (or denied) and payments depending on use must be set up. In addition to camera and sensor observing services (such as Drop Cam cloud recording), wearable observing, and following services (such as Fit Bit gadget administrations), there are a variety of additional services available.
8.9.3 Real-Rime Monitoring
Real-time monitoring is possible with cloud apps installed in the backend of mission-critical capabilities such as crisis management, mechanical control, and manufacturing. It is becoming more commonplace for businesses to move to the cloud their mechanical control framework, mechanical observation, and other capacities in an effort to cut operational costs, improve data accessibility, and open up existing B2B and B2C administrations when feasible.
8.9.4 Sensor Coordination
Automated benefits agreements are made possible by machine-to-machine interactions. Over time, workflows will become more automated, removing individuals from the exchange circle in the meanwhile. Cloud computing will be crucial to the success of these automated procedures. Examples of cloud services that IoT devices can use to acquire the most current data, limitations, or information will be developed in the future.
8.9.5 Customer Intelligence and Marketing
One of the most important aspects of the IoT is the ability to customize displays for individual users. An IoT cloud that is primarily focused on smart devices and reference points has been created by salesforce. It is built on the cloud and is a contemporary, real-time event motor. Clients can use this framework to send salespeople warnings or notifications based on their activity. The notion of crisp neighborhood alerts is a good example. Customers are detected when they pass through a company or retail area using a few sensors at these occasions. Their purchase history, tastes, and other variables are examined once they have been identified, and material is given to them that is specifically customized to them. A hostile actor might utilize the following instrument or file against a client, which is interesting from a security perspective.
Another type of IoT customer insight is improvements in vitality proficiency that benefit the environment. Household appliances, for example, can transmit consumption data to cloud-based back-end frameworks as part of a smart framework approach. Device utilization can be balanced based on demand and cost. IoT devices and consumers can adapt to data from IoT devices, such as time and frequency of use, energy spent on the device, and current electrical display estimation, by changing use patterns to save energy expenditures and reduce environmental impact.
8.9.6 Information Sharing
As a result of the IoT, multiple parties can exchange data. An implanted rehabilitation device, for example, may communicate data to a therapeutic office, which may then transmit that data to a protection provider. Depending on the circumstances, the data might be stored with additional patient information. Cloud-based data exchange and interoperability services are required for effective IoT analytics. Wot.io focuses on middleware-layer information trade administrations for horde information sellers’ sources and sinks because to the variations in IoT equipment stages, administrations, and information structures. Many IoT applications and accompanying protocols employ the publish/subscribe paradigm, which lends itself well to middleware systems that can translate between the different information languages. The availability of such services is essential for the development of information-based B2B, B2I, and B2C solutions.
8.9.7 Message Transport/Broadcast
A large-scale IoT message exchange administration may be built on top of the cloud because of its centralization, flexibility, and adaptability. This is because many cloud administrations utilize a combination of protocols like as HTTP and MQTT that may be used to broadcast and disseminate data as well as subscribe to and move it in several ways (centrally or at the organized edge). While there are a few exceptions, the security options given by cloud-based platforms need less cybersecurity professionals and can reduce on-premises security costs. VMs and systems in cloud-based IaaS administrations are more likely to be linked constantly and securely by default, leading in security scale economies that benefit client organizations, according to the study. First, this post will examine IoT commerce goods and features now available in the cloud, before diving into IoT cloud security.
8.10 Conclusion
Because of the characteristics of WSN devices and the needs of applications, low-power remote communications are utilized, and the functionalities supported must be carefully balanced against the restricted assets during application transfer. Even though numerous studies on security instruments for WSN situations currently exist, our objective is to examine how security may be treated as an empowering figure of the integration of low-power WSN with the Web, within the framework of its commitment to the IoT. The great promise of IoT brings with it a host of new challenges. This chapter focuses on security problems, among other challenges, and because IoT is built on the Web, security issues from the Web will also surface in IoT. The representation here clearly focuses on the security of the Web of Things in several scenarios. The extensive usage of the framework has exacerbated the security issues associated with the Web of Things (IoT).
References
1. Jing, Q., Vasilakos, A.V., Wan, J. et al., Security of the Internet of Things: perspectives and challenges. Wirel. Netw., 20, 2481–2501, 2014.
2. Zhao, K. and Ge, L., “A Survey on the Internet of Things Security”. 2013 Ninth International Conference on Computational Intelligence and Security, Leshan, pp. 663–667, 2013.
3. Deebak, B.D. and Al-Turjman, F., “A hybrid secure routing and monitoring mechanism in IoT-based wireless sensor networks”. Ad Hoc Netw., 97, 102022, 2020.
4. Santos-González, I., Rivero-García, A., Burmester, M., Munilla, J., Caballero-Gil, P., “Secure lightweight password authenticated key exchange for heterogeneous wireless sensor networks”. Inf. Syst., 88, 101423, 2020.
5. Wang, G., Lee, B., Ahn, J., Cho, G., “A UAV-assisted CH election framework for secure data collection in wireless sensor networks”. Future Gener. Comp. Sy., 102, 152–162, 2020.
6. Jha, S.K., Panigrahi, N., Gupta, A., “Security Threats for Time Synchronization Protocols in the Internet of Things”, in: Principles of Internet of Things (IoT) Ecosystem: Insight Paradigm, pp. 495–517, Springer, Cham, 2020.
7. Aakanksha, T. and Gupta, B.B., “Secure Timestamp-Based Mutual Authentication Protocol for IoT Devices Using RFID Tags”. Int. J. Semant. Web Inf. Syst. (IJSWIS), 16, 3, 20–34, 2020.
8. Julie Golden, E. and Harold Robinson, Y., “Security and Privacy Issues in Wireless Sensor Networks”, in: IoT and Analytics for Agriculture, pp. 187–210, Springer, Singapore, 2020.
9. Siddiqui, S.T., Alam, S., Ahmad, R., Shuaib, M., “Security Threats, Attacks, and Possible Countermeasures in Internet of Things”, in: Advances in Data and Information Sciences, pp. 35–46, Springer, Singapore, 2020.
10. Das, S.K., Samanta, S., Dey, N., Kumar, R., Design Frameworks for Wireless Networks, Springer Nature Singapore Pte Ltd., Springer, 2020.
Email: [email protected]
