13
Fingerprint Image Identification System: An Asset for Security of Bank Lockers
Mahendra, Apoorva, Shyam, Pavan and Harpreet Bedi*
SEEE, Lovely Professional University, Punjab, India
Abstract
In the discipline of biometric authentication, fingerprints are the most widely prescribed biometric feature for individual identification and verification. The implementation of a based method to fingerprint recognition and verification of the fingerprint image collected at the bank is presented in this chapter. The fingerprint-based bank locker system is a step forward from the traditional key-operated bank locker system. Thefts who are aware of this can now quickly copy and make keys. Furthermore, the keys must be handled with care and may be misplaced due to carelessness. A fingerprint-based bank locker scheme, on the other hand, is here to solve these problems.
Keywords: Biometric fingerprint sensor, bank locker security system
13.1 Introduction
Security is a major concern, and in today’s hectic and competitive environment, people are unable to notice ways to manually secure their sensitive personal belongings. Instead, one discovers an alternative that can provide maximum protection while remaining globalized.
Individuals may readily access their information at any time in today’s global network society [1], and from any place, there is also the possibility that others may be able to access similar information at the same time and from the same location. This technology, which can differentiate between existing users and fraudsters, is now catching everyone’s attention due to the possibility of personal identity being exposed. The fingerprint-based bank locker system is safe as well as simple to use and maintain. You will not have to deal with keys, and you would not have to worry about losing them [2]. The machine reads the person’s fingerprints with a fingerprint sensor and then stores the recorded fingerprints against bank locker records or in a separate record or cloud dedicated to fingerprints. If current prints match, then microcontroller receives a signal which displays the data on the LCD monitor. For approved customers, the controller also tells the motor driver to open the bank locker door. Customers who are not allowed to open locker doors will be denied access [3].
Passwords, which are four-digit PIN numbers and identification cards, are currently used for private authentication. Identities and data filled are frequently estimated, whereas cards are frequently stolen. Biometric identification technology, which recognizes individuals based on their specific biological details, is gaining traction as a solution to these issues [4].
Biometrics is described as the process of recognizing and identifying a physiological or behavioral characteristic that is unique to an individual. Biometric identification entails storing a database of the microcontroller receives a signal from the account holder’s physical characteristics or actions (habits) and comparing them to someone Others may attempt to somehow get access to the account to evaluate if the request is real [5]. Fujitsu has specialized in biometric recognition technology such as fingerprints, ears, and voiceprints.
Many methods are still in the development and estimation stages. Among the available biometric characteristics, fingerprints prove to be one of the simplest, with a low mismatch ratio, high security accuracy, and dependability [6]. This scenario for working in a bank locker involves locks and keys (Figure 13.1). We cannot say that we are providing adequate protection for our lockers because of this. We are using two separate technologies, embedded systems, and biometrics, to provide perfect protection and make our work easier [7]. Microcontrollers or optical signal processors are used as computing cores in embedded systems (DSP). The most important trait, though, is being committed to completing a particular mission.
Fingerprints are one-of-a-kind and unlike everyone else and using them will increase security. This protection system can be used by people who are illiterate. The user spends less time operating this tool.
For engineering purposes, Arduino is very common these days. Arduino can also be used for coding work because it allows us to add software programming and run our programs.
The motor that is used which allows to rotate or precise angular or linear position, speed, and acceleration control.
A 16 × 2 LCD is a liquid crystal display module that produces a visible display. It shows 16 characters per line, and there are two lines in total, so it shows 32 characters at once.
For the power supply, we used a Step-Down Transformer that has been controlled to 12 V.
Block Diagram

Figure 13.1 Block diagram.
13.1.1 Design Analysis
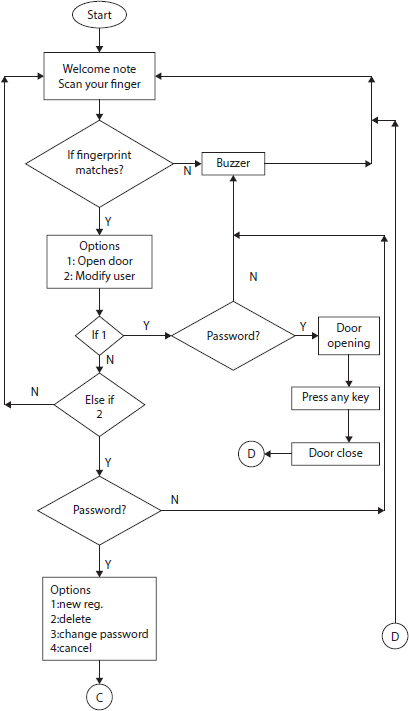
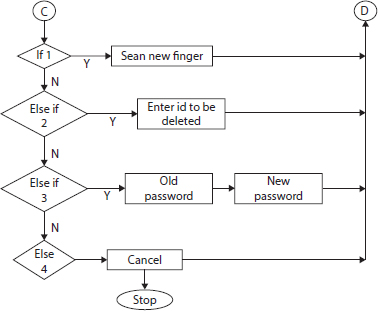
In an automated fingerprint recognition scheme, image enhancement and minutiae matching are two crucial stages (Figure 13.2). Fingerprint identification depends on the impression left by minute ridge formations or patterns on the fingertips to identify people. Nobody’s ridge pattern composition is the same, and no one’s pattern varies over time [8].
Feature extraction for a high-quality fingerprint is much faster, more precise, and reliable than for a lower-quality fingerprint [9]. Skin conditions (e.g., damp or dry, cuts, and bruises), sensor noise, non-uniform contact with the sensor surface, and generally poor-quality fingerprint images all degrade fingerprint quality (e.g., those of the elderly and laborers).
Isolated areas of distinct and continuous ridge detail may appear in a single finger impression, but there is insufficient detail to make an exclusion or identity inference, as shown in Table 13.1. If the areas between these areas can be clarified in a way that maintains the ridges’ continuity, then a significant opinion that would not have been possible otherwise can be created.
13.2 Result and Discussion
A false match occurs when images from two different fingers match, and a false non-match occurs when images from the same finger do not match. As a result, a successful fingerprint matching system’s main goal is to reduce each of these errors as shown in Figure 13.3. However, since both error rates are inversely related, they cannot be minimized at the same time. Another significant design consideration is the fingerprint recognition system’s protection, as well as the fingerprint template database security. Unauthorized access to or disclosure of fingerprint template data from such databases poses a significant security and privacy risk, as shown in Figure 13.4. This biometric bank locker system has many advantages over conventional locking systems, making it indispensable. This locker device is very user-friendly.
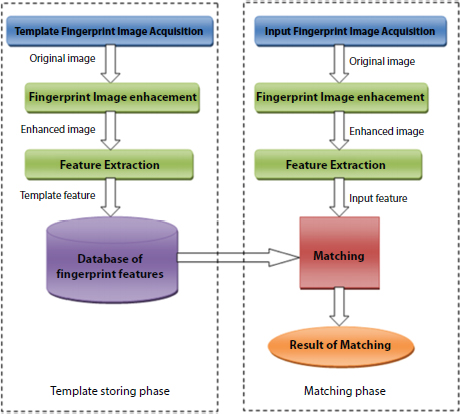
Figure 13.2 Fingerprint pattern recognition.
13.3 Conclusion
Authentication of fingerprints has been practiced for over a century. However, thanks to the advancement of automated fingerprint recognition systems, its use has only recently become widespread and mainstream. We have developed a biometric-based locker that provides a high level of protection. The locker will be inaccessible to any registered person.
Table 13.1 The physical state, liveness detection, and resolution of current fingerprint sensors.
| Technology | Outer physics | Flexible physics | Liveness detection | Resolution [R] | Limitations |
| Optical | Solid | No | No | R < −600 dpi and 1,000 dpi possible | Optical focusing and alignment mechanism size |
| Capacitive | Solid | No | No | R < 600 dpi | ESD protection, poor performance for damaged and dry skin |
| Thermal | Solid | No | No | R < 600 dpi | Environment-dependent, need training, more power consumption |
| Pressure (piezo electric) | Solid | No | No | R < 600 dpi | Less sensitive, protective layer reduces the quality of images |
| Radio frequency | Solid | No | Possible | R < 600 dpi | Low accuracy with dry fingers |
| Ultrasonic | Solid | No | Possible | R < 600 dpi | large size, cost, more time, 10 acquire images |
| Micro-Electro- Mechanical Systems | Solid | Possible | No | R < 600 dpi | Not particularly for fingerprint sensing |

Figure 13.3 Working of the circuit.

Figure 13.4 Finger print do not matched.
We use fingerprints because replication of a fingerprint is impossible to verify. The system is reasonable and straightforward to use. This technique is often mounted anywhere, where you would like high degree of security. This locker system is extremely reliable and safe. The paper also provides a description of the various steps involved in developing fingerprint-based individual identification.
13.4 Future Scope
For well over a century, people have been researching fingerprint authentication. Due to the advancement of automated fingerprint recognition systems, its use has only recently become widespread and popular. Biometric systems will be used in bikes for antitheft systems; this biometric system can be used in bike locking and to start the bike’s engine to provide an improvement in car biometric systems are often implemented, which is a great idea for starting the car and running it so that only the car’s owner can drive it. Retina scanners are often used in place of fingerprint scanners.
References
1. Takeda, M. and Uchida, S., Finger Image Identification Method for Personal Verification, IEEE, CH2898-5/90/0000/0761$01, 1990.
2. Afsar, F.A., Arif, M., Hussain, M., Fingerprint Identification and Verification System using Minutiae Matching. National Conference on Emerging Technologies, 2004.
3. Ratha, N.K., Karu, K., Chen, S., Jain, A.K., “A real-time matching system for large fingerprint databases,”. IEEE Trans. Pattern Anal. Mach. Intell., 18, 8, 779–813, Aug.1996.
4. Jain, A.K. and Hong, L., “Online fingerprint verification,”. IEEE Trans. Pattern Anal. Mach. Intell., 19, 4, 302–341, Apr.1997.
5. Kumar, A. and Zhang, D., “Combining fingerprint, palmprint and hand-shape for user authentication”, in: Pattern Recognition, ICPR 2006. 18th International Conference on, vol. 4, IEEE, pp. 549–552, 2006.
6. Zhao, F. and Tang, X., Preprocessing and post processing for skeleton-based fingerprint minutiae extraction. Pattern Recognit., 40, 2007, 1270–1281, 2007.
7. Ruili, J. and Jing, F., “VC5509 A Based Fingerprint Identification Preprocessing System,”. International Conference on Signal Processing, pp. 2859–2863, 2008.
8. Yun, E.K. and Cho, S.B., “Adaptive Fingerprint Image Enhancement with Fingerprint Image Quality Analysis,”. International Conference of Image and Vision Computing, pp. 101–110, 2006.
9. Dhameliy, M. D., and Chaudhar, J. P., A Multimodal Biometric Recognition System Based on Fusion of Palmprint and Fingerprint. International Journal of Engineering Trends and Technology (IJETT). V4(5):1908–1911, May 2013.
* Corresponding author: [email protected]
