Tackling Intruders in Wireless Mesh Networks
CONTENTS
7.1 WMN Intrusion Tackling Schemes: Background
7.1.1 WMN Architecture and Related Background
7.1.2 A Different Perspective of Tackling Intrusion in WMNs
7.1.3 Status of IDSs and IPSs for WMNs
7.1.4 Current Status of Achievements and Our Motivation
7.2 Tackling an Intruder with a Tricky Trap
7.2.1 Considered Setting: Network Characteristics and Security Model
7.2.2 PaS Model: The Idea Behind It
7.2.3 Initiating Competition by Using Game Theory
7.2.3.2 Marking the Intruder and Making a Decision
7.3.2 Marking the Intruder Considering Various Cases
7.4 Applicability and Future Network Vision
7.5 Wireless IDPS: Features and Differences to Know
7.5.1 Wireless IDPS Security Capabilities
7.5.2 Wireless IDPS Limitations
7.6 Potential Research Fields and Concluding Remarks
This chapter presents a different approach to tackling intruders in wireless mesh networks (WMNs). The traditional approach of intruder detection and prevention suggests purging out intruders immediately after their detection. In our work, we take a different approach and only purge an intruder when it is marked as a direct threat to the network’s operation. Our intrusion tackling model is termed the pay-and-stay (PaS) model and it allows a rogue node to stay in the network only at the expense of doing some traffic-forwarding tasks in the network. Failing to carry out the required tasks of packet forwarding disqualifies the node permanently, and eventually that rogue entity is purged out. Alongside presenting our approach, we briefly discuss other available literature, essential knowledge on wireless networks, intrusion detection and prevention, and status of intrusion-related works for WMNs.
7.1 WMN Intrusion Tackling Schemes: Background
WMNs [1,2] have recently become a very popular front of research. However, as a type of wireless network, they have several weaknesses that are usually associated with any kind of wireless technology. Unlike their wired counterparts, owing to the use of wireless communications, secure authentication with access control and various security issues are very crucial in such networks to ensure proper service to the legitimate users while also preventing a variety of attacks. Most security threats are posed by illegitimate entities that enter or intrude into the network perimeter, commonly termed as intruders. Sometimes, a legitimate node could also be compromised in some way so that an attacker-intended task for a security breach could be performed. In this chapter we also term any such kind of rogue node or entity as an intruder. So, the main objective of this work is to identify any kind of intrusion in a WMN and tackle it in a meticulous manner so that a wide range of security attacks may be deterred and the benefiting network. As we go through the chapter, we will explain the concepts and motivations behind our approach of dealing with this issue.
7.1.1 WMN Architecture and Related Background
The mesh architecture of a wireless network concentrates on the emerging market requirements for building networks that are highly scalable and cost effective. However, WMNs lack efficient security guarantees in various protocol layers [3,4]. There are a number of factors that come into consideration. First, all communications go through the shared wireless nodes in WMNs that make the physical security vulnerable. Second, the mesh nodes are often mobile, and move in different directions and often change the topology of the network. Finally, since all communications are transmitted via wireless nodes, any malicious node can provide misleading topology updates that could spread out over the whole network topology [5,6]. All these points make it difficult to ensure a proper level of security. However, it is desireable to achieve at least some kind of agreed-upon standard for a particular application scenario by identifying the rogue entities within the network. That is why we believe detecting the rogue node (intruder, thus an intrusion event) and tackling the intruder skilfully can keep away different kinds of attacks and keep the network healthy for its proper operation.
7.1.2 A Different Perspective of Tackling Intrusion in WMNs
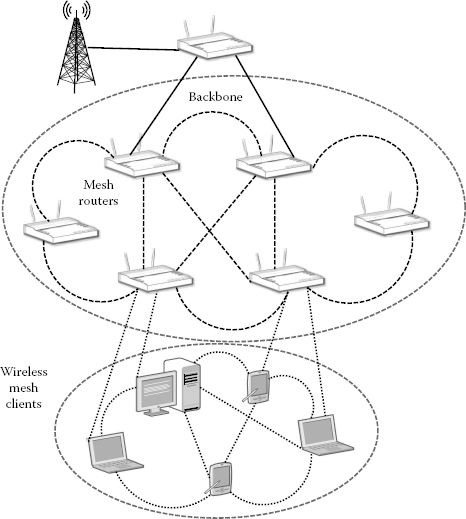
WMNs consist of mesh routers and mesh clients, where mesh routers form the backbone of the network that provides network access to both the mesh and conventional clients. Mesh clients can connect (see Figure 7.1) either to a backbone or among each other. Hence, the mesh client can access the network through the mesh router in a multi-hop manner. Therefore, any malicious node or intruder can attack the network in the forms of black hole attack, grey hole attack, Sybil attack and so on [1,5]. In all these attacks, the routing packets are deliberately misled towards wrong destinations or network entities. Once the malicious node (here, we will call it an intruder) has control over the packet after getting it in its trap, the packet could be modified, fabricated, dropped or forwarded (arbitrarily), all of which are considered major obstacles for secure and guaranteed routing in WMNs. Our idea is that in such an attack scenario, we will allow the node to operate but for its actions, it needs to pay at a high scale so that it is deterred from doing further mischief. We call our approach the PaS model of intruder tackling as the intruder needs to pay for its stay once it sets itself within the network. We will illustrate how we achieve our goal in the later sections. It should be noted here that we focus on the modelling of intruder/intrusion detection and its efficient tackling; hence, other issues such as physical layer issues, transmission and channel or signal-related issues, core routing issues, cryptographic and key management issues and so on are out of the scope of this work.
FIGURE 7.1
Hybrid wireless mesh network.
7.1.3 Status of IDSs and IPSs for WMNs
Both fields of intrusion detection systems (IDSs) and intrusion prevention systems (IPSs) are insufficiently researched in the case of WMNs. As these types of networks have a mesh backbone that could have devices with a proper amounts of resources and considerably high energy supplies, the usual intrusion detection and prevention mechanisms could often be applied on the basic structure/backbone. However, the problem arises when we want to tackle intrusions in the end-user level (mesh clients or fringe portion). Figure 7.1 shows the typical structure of a WMN, where we show the mesh clients in the network.
The mesh clients could consist of different types of devices ranging from laptops to mobile phones; even a wireless sensor networks (WSNs) could be at the mesh network end as mesh clients. Any effective intrusion tackling mechanism for WSN could be difficult to implement on the sensors because of their lack of proper resources; this matter is treated as a separate research issue, because it is out of the scope of this work. For other types of mesh clients, some kind of intrusion tackling mechanism can be employed. Our work mainly focuses on this area, where a different approach of tackling intrusion could end up being beneficial for the network by allowing an intruder to stay in the network rather than instantly purging it out once it is caught or marked. This matter will be discussed further in the chapter.
7.1.4 Current Status of Achievements and Our Motivation
Until today, the works on intrusion in WMN have been very scarce. Often, the proposed approaches do not offer good solutions to the problem but rather put some kind of scratchy overview. There are a few other works that should also be mentioned because they provide important information and ideas related to the field. Hence, in this section, we present the notable past works that especially focus on this topic and also some other works that are somewhat related to our approach.
RADAR is a reputation-based scheme for detecting anomalous nodes in the WMNs pre-sented in Ref. [7]. The authors use the concept of reputation to characterise and quantify the mesh node’s behaviour and status in terms of some performance metrics. The RADAR architecture shows how the reputation of network nodes is maintained. Reputation management is defined as a feedback process that involves the monitoring and tracking of a mesh node’s performance and reviewing evaluation reports from the witnesses. A trust network construction algorithm is also presented and the performance is measured by taking into account some critical parameters such as false positive, decision accuracy, response latency and detection overhead. The idea of using reputation is not very different from those that are used in the available literature in other fields, but the way the authors formed their algorithm and architecture for WMNs has been proven to be effective for some scenarios.
Ref. [8] describes an architecture of asymmetric, distributed and cooperative IDSs for WMNs. In this work, the authors mention the notion of the selfish behaviour of the suspected intruder. They use a double-mode mechanism in the detection model for judging the troubling behaviour: (a) the frequency of the node’s seizing channel behaviour during the active time of the node and (b) the continuous sampling results of the node’s backoff value. Alongside presenting the idea in mathematical form, the authors analysed the whole scheme in terms of throughput ratios and detection delays.
The idea of Ref. [9] is to note down various types of basic information about intrusion detection in WMNs and to propose an IDS architecture. This work, however, is very elementary and the authors also note that they put forward an initial design of a modular architecture for intrusion detection, highlighting how it addresses their identified challenges. Ref. [10] presents an IDS software prototype over a wireless mesh network testbed. The authors implement the idea and the evaluations are presented in a limited range. However, this work is incomplete because there are many unanswered questions, such as what to do with a distributed or large-scale WMN, what to do to ensure real-time analysis and detection of anomalous nodes, and so on.
OpenLIDS is a lightweight IDS for WMNs presented in Ref. [11]. This work shows an analysis of a typical wireless mesh networking device performing common intrusion detection tasks. The authors examine the participating nodes’ ability to perform intrusion detection. The experimental study shows that commonly used deep packet inspection approaches are unreliable on typical hardware. So, the authors implement a set of lightweight anomaly detection mechanisms as part of an IDS, called OpenLIDS. They also show that, even with the limited hardware resources of a mesh device, it can detect current malware behaviour in an efficient way.
Ref. [12] presents a very simple model of intrusion detection in WMNs. This work is questionable as the contribution is limited to a vague work-flow diagram with insufficiently done analysis. However, from the objective mentioned in the work, it is understood that the authors targeted designing only a framework without going into any details of the operations. Ref. [13] presents an idea of using a finite-state machine to model intrusion detection in WMNs. By simulation studies, the authors show that under a flooding-combined attacks, the IDS shows a high false alarm rate due to the side effect of flooding on the attacker’s neighbours. Hence, the dummy node used in the approach needs more design features to record more information about the monitored node. This work is flawed and a convincing result is yet to be achieved.
In Ref. [14], the authors present a framework for intrusion detection in IEEE 802.11 WMNs. Some intrusion detection agent structures are shown. The concept is mainly shown in the form of some diagrams and where different components work in a cooperative manner. However, the idea appears to have been not thought out very well and somewhat naive. The work presents the primary components (or agents) that should be installed in mesh routers and mesh nodes. The detection of intrusion could be made and an action database could be used for making decisions about any detected intruder. No detailed analysis is presented in the work and it basically touches the surface of the problem.
As is evident from the above-mentioned works on IDSs in WMNs, very few countable papers have been published so far on this topic. Again, none of the above works talked about intrusion tackling or utilising the intruder for the network’s benefit before purging it out. Hence, we have come up with the idea of intrusion tackling with the PaS model. While the proposal section outlines the details of the model, there are more related works that inspired or influenced our way of thinking to build up the basic mathematical and theoretical intrusion tackling model.
In Ref. [3], the authors propose an algorithm to specifically defend against security attacks in WMNs where the algorithm makes use of a counter threshold to find the threshold value. This threshold value is compared with the actual number of data packets delivered. If the actual number of data packet is less than the threshold value, then the route is declared to contain malicious node(s), which implies that packet loss is always due to the malicious node(s). Therefore, the path will be excluded from route selection. However, packet loss may occur due to other factors such as mobility and battery power. If we keep excluding the route by assuming that the poor performance routes contain malicious nodes, then we may end up with few or no routes for communications at the end. This method may work on specific settings but is not efficient to encounter security attacks in dynamic topologies of WMNs.
The authors in Ref. [15] advocate using a protocol for carrying authentication for network access (PANA) to authenticate the wireless clients. The PANA model also provides the cryptographic materials necessary to create an encrypted tunnel with the associated remote access router. However, the authentication procedure presented in the paper is tedious and resource consuming. Although the framework talks about protecting the confidentiality of exchanged information and the overall approach is analysed, it has not been tested in a detailed manner that could convince the readers about its efficiency in practical implementation cases.
The authors in Ref. [16] propose a framework of a non-cooperative zero-sum game between genuine and malicious mesh routers and use mathematical tools and models for their approach. This game model solves the problem of grey hole attacks where the malicious node drops a subset of packets that it receives. The game has a source node as the target and a malicious node as the attacker; each competes with the other for limited resources and each node gains depending on its own strategy and that of the other. The attacker benefits from dropping packets and the target gains from forwarding the packets successfully. Our approach adopts a similar game-theoretic model as a part of the total solution. However, the difference is that we circumvent the flaws of this paper’s idea by using our own mathematical model and by choosing appropriate parameter values. As an example, Ref. [16] takes 50% of the packet arrival rate to send buffer based on which the gains of both nodes vary. Therefore, it may be impractical because, in reality, higher packet arrival rates are expected to minimise packet delays and a large number of nodes should be involved in communications in any WMN.
A novel algorithm named channel-aware detection (CAD) has been adopted in the work presented in Ref. [17]. The authors use two different strategies to detect the grey hole attacks. Their approach detects a potential victim mesh node (i.e. which can be attacked) by hop-by-hop loss observation and traffic overhearing. A comparative performance analysis has been shown to detect and isolate the selective forwarding attackers [25] in multi-hop network scenarios. The probability of misdetection or false alarm is analysed and a design is proposed to limit these to a certain threshold. However, the approach is complicated, focuses on a narrow set of attacks, and is applicable only in some restrictive scenarios. This work basically focuses on the communication and signalling aspects in the physical layer but is related to our work in the sense that some of the ideological concepts helped us in the formulation of our approach, which we will discuss later.
Attention has been devoted to investigating the use of cryptographic techniques to secure the information transmitted through the wireless network. Some other preliminary solutions have been addressed in ad hoc sensors WMNs to prevent different types of malicious attacks [18, 19, 20].
Now that we have presented some background knowledge, in the next section, we present our proposed model.
7.2 Tackling an Intruder with a Tricky Trap
It should be noted before going any further that our security model is for intrusion tackling or intrusion handling, instead of direct intrusion detection or intrusion prevention in WMNs. The background knowledge noted so far could be useful while explaining our approach to handling the issue. We also clarify some terms in the later sections to explain our position in a better way and to differentiate among the terminologies.
The core concept of our approach is that all the intruders in a network are always harmful for the network. In fact, sometimes, there are ways to obtain benefit out of it or utilise it for the network’s welfare or for its own benefit. Keeping this tricky fact in mind, we take a different approach to tackle an intrusion.
7.2.1 Considered Setting: Network Characteristics and Security Model
We assume a hybrid wireless mesh network where different types of devices could form the fringe part or could play the roles of mesh clients. A network model is shown in Figure 7.1. From the figure, it can be seen that any node in the fringe parts could come and go, that is, they may be mobile, which allows a newcomer or even an intruder to try its luck in the network. As we have noted before that even if a node within the legitimate mesh clients acts as an attacker, in our case, we consider it as an intruder; that is, it has lost the legitimacy to stay in the network as a legal participant and is seen as a suspicious entity that has caused an intrusion (illegitimate incursion) within the network perimeter. We assume that standard security components (i.e., cryptographic keys for data confidentiality, security measures, etc.) and other basic intrusion detection mechanisms are present within the network. The basic intrusion detection agents could be installed in any node in the network. Hence, our mechanisms start working after an intrusion is detected or some node is suspected of being an intruder. To capture the whole idea in a single sentence, We are interested in dealing with the intruder if it is suspected to be such, after it has caused an intrusion rather than purging it out directly from the network. By ‘standard security components’ we mean the cryptographic parameters, keys and other security mechanisms that are used in a device that participates in a given network. (The reader is encouraged to go through the basic terms and preliminaries mentioned in Section 7.2 for a recap.)
7.2.2 PaS Model: The Idea Behind It
Once a node in the network is suspected to be an intruder (by any of the standard components installed in the legitimate devices), our model is employed to force the intruder to work for the network. If it works for the network, we see little problem in allowing the node to stay in the network. That is because the routing packets and exchanged data within the network would be protected by other cryptographic measures in place as noted in the previous section. Instead of taking a straight negative decision to defuse it, we give it enough tasks to perform for forwarding any possible network packet to the next hops or to the intended destinations.
If the node is an intruder unwilling to participate in the forwarding process of the packets, we decide finally that the node is not suitable for staying in the network and must be purged out. Otherwise, by putting pressure on it to forward a huge number of packets, we save the network’s other resources. Each forwarding takes energy for wireless transmission; hence, if an intruder happily does the network’s legitimate nodes’ job, we drain its energy or make it pay for its survival/stay in the network. If the node drops the packets randomly or selectively, we catch this with our enforced mechanisms and mark it as a selective forwarder or we charge it for causing selective forwarding. To employ this policy, the intrusion tackling agent is installed on each legitimate mesh entity (mesh router or mesh clients).
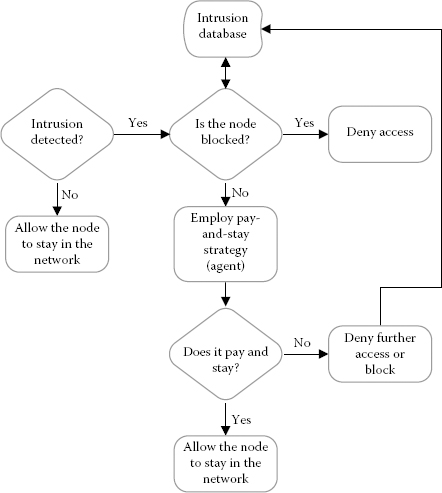
Figure 7.2 shows an operational diagram of a PaS intrusion tackling model. The intrusion database can be stored in any of the devices with a good amount of storage space or could be partially maintained by each node, that is, each node acts as the intruder tackler for its surrounding nodes. For primary intrusion detection, as noted earlier, any standard scheme could be utilised. Because of the structural dimensions of WMNs, such a strategy is possible, whereas for WSNs or other wireless ad hoc networks, such a strategy may not be used. As shown in the figure, our model gets activated after the IDS does its part; we deal with what to do after the intrusion, not before the intrusion. The core goal is to maximise or save the utilisation of network resources by putting the burden of packet transmissions on a rogue entity. In case the rogue entity refuses to pay or render the service, we purge it out from the networks, and thus this is an effort of delicately handling an intruder in a wireless mesh network setting.
FIGURE 7.2
Operational diagram of our intrusion tackling model.
The texts below explain how we achieve this PaS strategy for intrusion tackling. There are mainly two phases in our approach. The first phase is a game theory-based PaS model and the second phase is marking the intruder and taking a decision (that is also a part of the intrusion tackling model). The following sections illustrate our approach in detail.
7.2.3 Initiating Competition by Using Game Theory
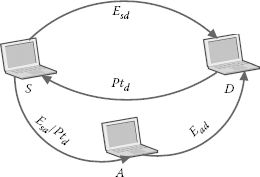
Game theory [21] can be defined as a statistical model to analyse the interaction between a group of players who act strategically. Figure 7.3 introduces a usual attack model where there are two players involved, namely, Player_1, which is the source node S, and Player_2, which is the malicious/attacker (in our case, intruder) intermediate node A. Let D be the destination node and N be the finite set of all players. We limit our game to a non-cooperative, incomplete information, and a zero-sum game model [22], where one player wins and the other player loses. Our target is that the intruder should spend more resources in doing wrong with any packet than that are used by the target node to forward packet to the destination. That means the intruder eventually has to pay heavily for its illegal staying within the network. It should be noted that we use the terms intruder and attacker interchangeably throughout the rest of the chapter.
FIGURE 7.3
A diagram showing node S sending packet (directly and via node A) to the destination node D.
Before presenting the mathematical model of our approach, in Table 7.1, we note the critical notations used in this chapter for ease of reading and to identify of various items at a glance.
Let Pi be the probability to defend the ith node in the network. We assume that vi is an intermediate node and vi–1 and vi+1 are the upstream and downstream nodes, respectively. The total probability of defending all N nodes is . The energy spent for utility cost is .
The remaining energy is , where . Our objective is that the energy that needs to be spent by the intruder to cause trouble in packet flow or forwarding must be more than the energy spent by the victim (which is sending or receiving the packets).
The energy of the sender to send via the attacker could be noted by the equation , where α is a constant. The success of the attack depends on the value of α. If α > 1, the attack succeeds. If α = 1, the energy spent by the attacker equals that of the target. When α = 0, the attacker cannot attack, and α < 1 means that the attacker cannot drop any packet.
Basic Notations and Their Meanings
Notation |
Meaning |
Pi |
Probability to defend the ith node in the network |
vi |
Intermediate node |
vi−1 |
Upstream node |
vi+1 |
Downstream node |
μ |
Packet arrival rate |
Esd |
Energy spent for utility cost |
Er |
Remaining energy |
α |
A constant |
pa |
Probability of transmitting packets via Player_2 |
pd |
Probability of direct transmission of packets |
qf |
Forwarding probability |
qd |
Probability of dropping the packet |
Pt |
Points received |
The state of the game is (m, n), where m is the sending buffer of Player_1 and n is the dropping buffer of Player_2. If one packet is present in the sending buffer of m of Player_1, then m will take a value of 1 and n can take a value 0 or d, depending on whether any packet is dropped or not. We also denote μ as the probability that a new packet arrives at the sending buffer of Player_1. There are four possible states of the game: k1 = (0,0), k2 = (0,d), k3 = (1,0), k4 = (1,d). Therefore, the transition probabilities from one state to another state are calculated as follows:
When (m = 1)
(7.1) |
When (m = 0)
(7.2) |
where μ is the arrival rate of packets in the sent buffer and x is the joint strategy.
For example, assume that the current state of the system is (1,0). Player_1 (i.e., S) has a packet in its sent buffer. It uses two strategies: transmit the packet directly or transmit via A. If S transmits the packet directly to D, then the states are (0,0) or (1,0) with probability pd. Otherwise, it transmits packets via Player_2 (i.e., A) with probability pa. A either drops the packet or forwards it to D. If it drops, then the states become (0,d) or (1,d). If A forwards the packet, then the next states will be (0,0) or (1,0). Note that A is the potential intruder in this case.
The strategy set for Player_1 is S1 = {s1, s2}, meaning that Player_1 forwards the packet either directly to destination D (s1) or via A (s2). Mixed strategies (denoted as x) that correspond to S1 are πs (s1, s2) = (pd, pa), where pd + pa = 1. The strategy set of Player 2 is A2 = (a1, a2). Mixed strategies corresponding to the action of A2 are πa (a1, a2) = (qf, qd), where qf + qd = 1. Here, qd is the probability of dropping the packet. Hence, (πs, πa) = (pd, pa, qf, qd).
The destination D gives some points to source S for the transmitted packet. When the source node S sends the packet through the path S → D, node S receives some points of Ptd from D. When S transmits packets via A, it receives points of Ptd from D and it gives A some points, Ptsa. If S does not receive any point from D for the transmitted packet, it means that the packet did not reach D successfully. Each packet transmission from node vi to node vi+1 causes an energy-spending Evi vi+1. Therefore, depending on the energy spent and points received by the source and attacker, the nodes S and A will remain with the following net utility:
(7.3) |
If (–Ptsa – Esa) < (Ptd – Esd) < (Ptd – Ptsa – Esa) the utility of S will decrease if A drops the packet compared to the utility it receives when a packet reaches D:
(7.4) |
where β is the profit earned by node A. If (Ptsa – Ead) < (Ptsa + β), the utility earned from dropping the packet is higher than the utility received from S for transmitting the packet. However, the utility can be calculated from the following equations based on the probability of dropping and forwarding the packets:
(7.5) |
and
(7.6) |
7.2.3.2 Marking the Intruder and Making a Decision
In this section, we describe a multi-hop acknowledgement (ACK)-based algorithm to detect malicious node(s) doing a selective forwarding attack. Owing to the structure of WMNs, it is possible to use this method. We know that a selective forwarding attack is one of the most dangerous attacks because the packets are dropped randomly, which may contain sensitive data. In this algorithm, multiple nodes need to be selected as ACK points in WMNs. This means that those mesh nodes are responsible for sending an ACK packet after receiving a packet from a source node or the nearest intermediate source nodes. We assume that the WMNs are operating under an ideal channel quality and the majority of the mesh routers are behaving normally. We consider that the packet loss appears only due to malicious activity from an intruder. Moreover, since there may be multiple existing routes from a source mesh node to a destination mesh node and a source node may receive multiple route replies of each of its route requests, we encourage the source node to keep a record of each route for future references. It should be noted here that dealing with physical layer or channel-level matters are out of the scope of this work as we focus on the theoretical framework and mathematical model of the operational concept.
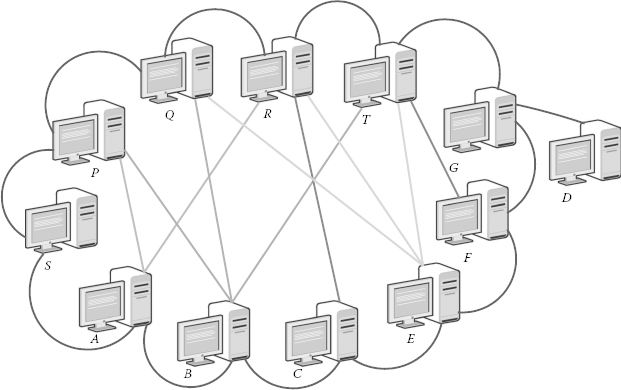
In Figure 7.4, we show the structure of a wireless mesh network where S is the source node and D the destination node. We assume N to be the total number of mesh nodes in the forwarding path. M is the number of malicious nodes among N. Let X be the normal-behaving nodes between each of the two malicious nodes and Y be the number of ACK points in the forwarding path. We consider Z as the percentage of randomly selected check points.
FIGURE 7.4
Multi-hop acknowledgement.
When the source node S sends a route request, it receives several route replies. Let us consider that S chooses the route SABCEFG → D, where E is the malicious node. We are considering two selected ACK points (i.e., Y = 2), namely, B and F.B and F will acknowledge back after they receive the packets from the source mesh nodes. Therefore, the following possibilities may occur if:
Scenario 1: One of the nodes is malicious in the forwarding path.
Scenario 2: One or more nodes are malicious in the forwarding path.
Scenario 3: Both the ACK points B and F are malicious.
Scenario 4: Either B or F is malicious.
This algorithm uses two approaches: hop-by-hop loss observation and traffic overhearing to detect the malicious node on the path of data flow. More specifically, we assume vi to be an intermediate node and vi–1 and vi+1 to be the upstream and downstream nodes, respectively. vi+1 receives a packet from vi–1; then it updates itself with the packet count history and with the corresponding packet sequence number, it buffers the link layer ACK that it receives for each packet, and then forwards it to vi–1 (i.e., downstream node). We denote ws as the total number of packets that are successfully sent–received by the source S to destination D.nvi→vi+1 is the number of packets received successfully by vi+1 (i.e., this is the number of successfully received packets from any intermediate node to its downstream node).
Two operations are performed when the mesh router forwards a packet to the downstream node as explained in this paragraph. When each packet is relayed to the downstream traffic, the mesh router or upstream node buffers ACK and overhears the downstream traffic to check whether it (downstream node) forwarded or tampered with the packet. The upstream node observes these two operations and then makes a simple analysis of the scenario.
The downstream node maintains two parameters. They are (a) probability of ACK that we denote as PAck and (b) probability of no acknowledgement (NACK), PNAck. The probability of ACK (PAck) is computed as PAck = 1 – PNAck and the probability of NACK is computed as PNAck = (nt + nd)/nf, where nt is the number of tampered packets, nd is the number of dropped packets, and nf is the number of total forwarded packets.
We introduce two packets, PROBE packet and PROBE_ACK, to detect the malicious routers. The PROBE packet is used by source node S with every ws data packet to the destination node D. When the source node S sends the PROBE packet through the path, each node in the path marks the PROBE packet with the detection parameters and this is termed packet marking. A PROBE packet sent to the destination by the source node is also marked by it (i.e., S) with the number of packets that will be transmitted to a particular destination node. When the PROBE packet is passed along the path, each node vi attaches a mark of its opinion to the downstream node (vi+1). The opinion is calculated by observing the downstream node’s behaviour by the transmitter node. The opinion of the downstream node is calculated as follows:
• If (PNAck > tm), it means malicious behaviour
• If (PNAck < tm), it means normal behaviour
where tm is the monitoring threshold which carries values between 0 and 1. As the PROBE packet is passed through the path, the node also appends the behaviour parameter to the PROBE packet. The behaviour parameter represents the observation of node vi+1 about the behaviour of the upstream node vi. The behaviour of the node is calculated by determining the loss rate of the packets over the link vi to vi+1. It is calculated by the following formulae:
• If (Lvi→vi+1 > tl), malicious behaviour is detected
• If (Lvi→vi+1 < tl), normal behaviour is detected
where (Lvi→vi+1 = 1 – (nvi→vi+1/nvi–1→vi)) is the loss rate of the link that is observed by the node vi+1. tl is the loss rate threshold that can take any value between 0 and 1. The algorithm will detect the malicious behaviour with higher probability with the lower values of tl and tm.
For the game-theoretic model analysis, we substitute the values for the required energy to transmit packets from S to D either directly or via A and the points earned by source S and A are as follows: Esd = 0.6, Esa = Ead = 0.05, Ptd = 1 and Ptsa = 0.3. We assume that the packet arrival rate μ to send the buffer is quite fast; μ = 0.8 and β = 0.2.
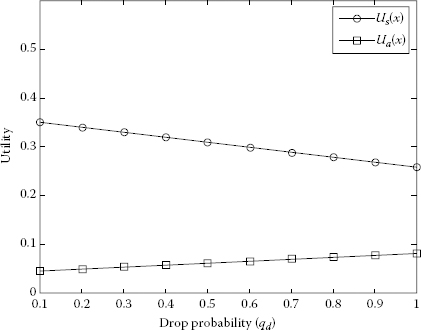
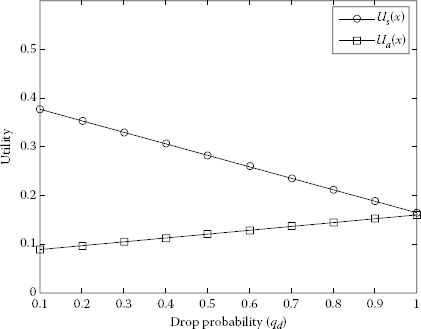
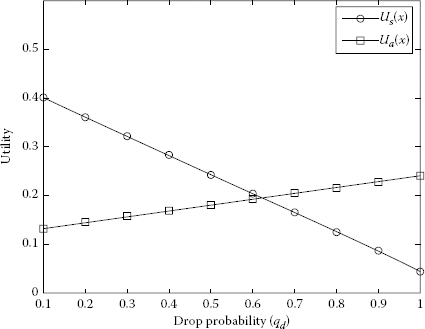
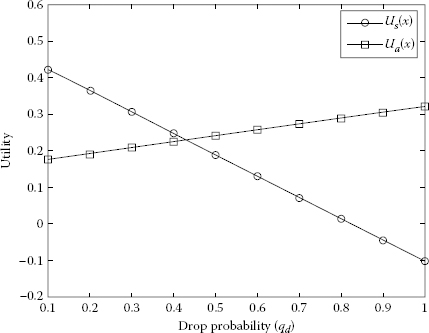
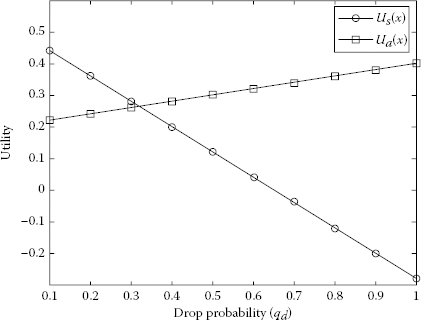
Using Equations 7.5 and 7.6, we obtained the utility of Player 1 and Player 2. We represented Figures 7.5 through 7.9 of utilities S and A as a function of drop probability using MATLAB® [23]. The packet dropping probability is chosen between 0 and 1. It is observable from Figures 7.5 through 7.9 that the utility of S is decreasing and the utility of A is increasing with the increase of dropping probability.
FIGURE 7.5
Increasing the utilities of A and decreasing the utilities of S with respect to different drop probabilities of qd when pd = 0.8 and pa = 0.2.
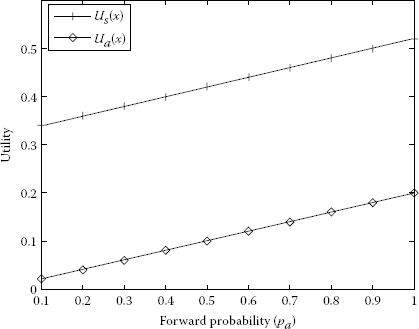
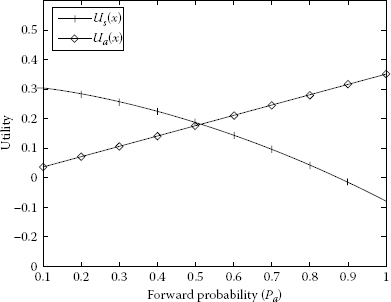
Player 2 reaches the maximum utility when source S transfers all the packets via A with the highest dropping probability. It can be seen from Figure 7.9 where pa = 1 and qd = 1 that the maximum utility of Ua = 0.4. On the other hand, for qd = 1, Player 1 has its maximum utility Us = 0.256 when the probability of sending packets directly to D increases. The maximum utility of S is shown in Figure 7.5 where pd = 0.8 and qd = 0.1. Figures 7.10 through 7.14 represent the utility of S and A as a function of forward probability to A, pa. The forward probability is chosen between 0 and 1.
FIGURE 7.6
Increasing the utilities of A and decreasing the utilities of S with respect to different drop probabilities of qd when pd = 0.6 and pa = 0.4.
FIGURE 7.7
Increasing the utilities of A and decreasing the utilities of S with respect to different drop probabilities of qd when pd = 0.4 and pa = 0.6.
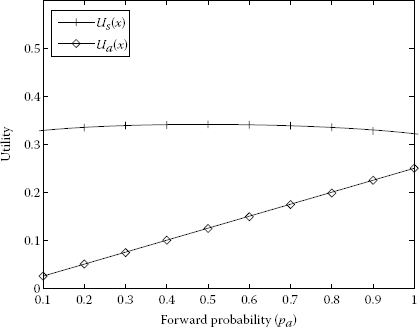
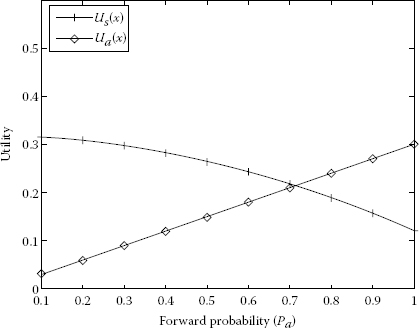
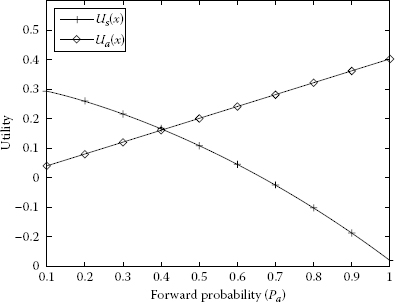
The forward probabilities are qf = 1 and qf = 0.75 and the drop probabilities are qd = 0 and qd = 0.25 in Figures 7.10 and 7.11. It is clear that in Figure 7.10 the utilities of S and A are increasing. The maximum utility of S is 0.5 and the maximum utility of A is 0.2. In Figures 7.11 through 7.14, the utility of S is decreasing overall (with a slight bent increase and going down in Figure 7.11) and the utility of A is increasing and the maximum utility of A is 0.4; the forward probabilities are qf = 0.75, qf = 0.5, qf = 0.25 and qf = 0 and the drop probabilities are qd = 0.25, qd = 0.5, qd = 0.75 and qd = 1.
FIGURE 7.8
Increasing the utilities of A and decreasing the utilities of S with respect to different drop probabilities of qd when pd = 0.2 and pa = 0.8.
FIGURE 7.9
Increasing the utilities of A and decreasing the utilities of S with respect to different drop probabilities of qd when pd = 0 and pa = 1.
7.3.2 Marking the Intruder Considering Various Cases
In the malicious behaviour detection phase, the following possible cases may occur when the upstream and downstream nodes are combined to detect malicious activities:
FIGURE 7.10
Increase of utilities S and A as a function of pb with respect to qf = 1 and qd = 0.
FIGURE 7.11
Increase of utilities S and A as a function of pb with respect to qd = 0.75 and qf = 0.25.
FIGURE 7.12
Increase of utility A and decrease of utility S as a function of pb with respect to qf = 0.5 and qd = 0.5.
Case 1: If PNAckvi→vi–1 > tm and Lvi→vi+1 > tl. The node vi, either drops or tampers with the packets. The probability of NACK is greater than the monitoring threshold tm. The node vi–1, the upstream node, will observe node vi, on whether it drops the packets or tampers with it. Node vi–1 will increase nd, which is the number of dropped packets, and also nt, which is the number of tampered packets. The downstream node, vi+1 will observe if loss rate is greater than the threshold t, the loss rate threshold. The upstream and downstream will observe if node vi, is misbehaving.
FIGURE 7.13
Increase of utility A and decrease of utility S as a function of pb with respect to qf = 0.25 and qd = 0.75.
FIGURE 7.14
Increase of utility A and decrease of utility S as a function of pb with respect to qf = 0 and qd = 1.
Case 2: If PNAckvi→vi–1 < tm and Lvi→vi+1 > tl. In this case, the monitoring threshold is greater than the probability of NACK from node vi–1 to vi. The node vi is behaving normally. If the observed loss rate of the link from vi to vi+1 is greater than the loss rate threshold, node vi is misbehaving. According to the upstream node, node vi is normal but on the other hand, the downstream node can detect if node vi is misbehaving. To overcome this problem, we need to verify link layer ACKs that are received by the upstream node vi–1 for each packet that is forwarded successfully by the node, vi.
Case 3: If PNAckvi→vi–1 > tm and Lvi→vi+1 < tl. In this case, the upstream node vi–1 has a greater probability of NACK and is greater than the monitoring threshold tm. In this case, there is a misbehaving activity at the node vi. On the other hand, the observed loss rate link from vi to vi+1 is lower than tl which is the loss rate threshold. According to the upstream node vi–1, the node vi is misbehaving and the downstream node will consider node vi as normal. To overcome this issue, the upstream node can detect the misbehaving node vi by observing false information in the PROBE packet.
Case 4: If PNAckvi→vi–1 < tm and Lvi→vi+1 < tl. The downstream and the upstream nodes do not detect any misbehaving node.
7.4 Applicability and Future Network Vision
Our intrusion tackling model is designed to protect the network from a wide range of security attacks that target the routing mechanisms of the network. The basic IDS mechanisms employed on the devices could notify a suspected intruder and when our model gets activated to handle the case, we ensure the proficiency in dealing with it to use the apparent negative entity for a positive purpose. Only when it is proven to be a serious threat to the network, we retract its permission to participate in the network. The preliminary IDS mechanism acts as the primary defence against intrusion activity and our mechanism acts as the final line of defence against malicious intrusion. The behavioural analysis, to mark the intruder, sets the solid defence strategy to make our model effective in practical scenarios. Owing to the features of WMN with the required amount of resources, this model works fine and proves to be effective, whereas for other wireless networks such as WSN, mobile ad hoc network (MANET) and vehicular ad hoc network (VANET), this model is not directly applicable.
From the higher-level view, however, all the above-mentioned wireless technologies fall under the category of wireless self-organising networks or ad hoc networks. Hence, putting all of them under an umbrella term, we could fit them in various future networking technologies such as pervasive or ubiquitous computing, Internet of things (IoT), future Internet, cloud computing and so on [24]. It is expected that WMN as a wireless network technology will blend well within these emerging technologies and concepts. If it is so, then the basic principle of the PaS model could be applied in various scenarios. Even if the exact model may not be applied, it is possible to think of giving the intruder some waiver to stay in any of the future networks so that when it does more good than evil, the network in an intelligent manner utilises its capacities rather than alienates it without giving it a chance. In fact, a concept such as pervasive computing would allow thousands of computation-enabled devices to work together in a blended environment where it would be extremely difficult to mark any entity as a clear intruder or an unwanted node. This is because all those good and bad entities together would form a pervasive or ubiquitous environment with a complete mixture of human life and various device technologies. Likewise, other future or next-generation computing and network technologies will have various applicable scenarios considering the PaS model’s core idea.
7.5 Wireless IDPS: Features and Differences to Know
Intrusion detection and prevention system (IDPS) is basically the combination of detection and prevention mechanisms [26]. Before ending this chapter, we feel that it is necessary for the readers to have some idea about various IDPS technologies commonly used for wireless networking. As our mechanism does not fall under any clear category, we referred to our approach as intruder tackling because we let the intruder stay in the network even after finding it out, which is conflicting to any IDS, IPS or IDPS’s main objective. The idea behind putting this section here is to clarify these terminologies further so that the readers will be able to make proper distinctions among these mechanisms.
A wireless IDPS monitors wireless network traffic and analyses wireless networking protocols to identify malicious behaviour. However, it cannot identify suspicious activity in the application or higher-layer network protocols (e.g., TCP, UDP) that the wireless network traffic is transferring. It is most commonly deployed within the range of an organisation’s wireless network to monitor it, but it can also be deployed to locations where unauthorised wireless networking could be occurring.
Owing to the transmission methods, wireless network attacks differ from those on wired networks. However, the basic components involved in a wireless IDPS are the same as the network-based IDPS: consoles, database servers, management servers and sensors. A wireless IDPS monitors the network by sampling the traffic. There are two frequency bands to monitor (2.4 and 5 GHz), and each band includes many channels. A sensor (here, we mean any kind of sensing mechanism) is used to monitor one channel at a time and it can switch to other channels as needed.
We should mention that most of the wireless LANs (WLANs) use the Institute of Electrical and Electronics Engineers (IEEE) 802.11 family of WLAN standards [24]. IEEE 802.11 WLANs have two main architectural components:
• A station, which is a wireless end-point device (e.g., laptop computer, personal digital assistant).
• An access point, which logically connects stations with an organisation’s wired network infrastructure or other network.
Some WLANs also use wireless switches, which act as intermediaries between access points and the wired network. A network based on stations and access points is configured in infrastructure mode; a network that does not use an access point, in which stations connect directly to each other, is configured in an ad hoc mode. Nearly all organisational WLANs use the infrastructure mode. Each access point in a WLAN has a name assigned to it called a service set identifier (SSID). The SSID allows stations to distinguish one WLAN from another.
Wireless sensors have several available forms. A dedicated sensor is usually passive, performing wireless IDPS functions but not passing traffic from the source to the destination. Dedicated sensors may be designed for fixed or mobile deployment, with mobile sensors used primarily for auditing and incident handling purposes (e.g., to locate rogue wireless devices). Sensor software is also available bundled with access points and wireless switches. Some vendors also have host-based wireless IDPS sensor software that can be installed on stations, such as laptops. The sensor software detects station misconfigurations and attacks within the range of the stations. The sensor software may also be able to enforce security policies on the stations, such as limiting access to wireless interfaces.
If an organisation uses WLANs, it most often deploys wireless sensors to monitor the radio-frequency range of the organisation’s WLANs, which often include mobile components such as laptops and personal digital assistants. Many organisations also use sensors to monitor areas of their facilities where there should be no WLAN activity, as well as channels and bands that the organisation’s WLANs should not use, as a way of detecting rogue devices.
7.5.1 Wireless IDPS Security Capabilities
The main advantages of wireless IDPSs include detection of attacks, misconfigurations and policy violations at the WLAN protocol level, primarily examining IEEE 802.11 protocol communication. The major limitation of a wireless IDPS is that it does not examine communications at higher levels (e.g., IP addresses, application payloads). Some products perform only simple signature-based detection, whereas others use a combination of signature-based, anomaly-based and stateful protocol analysis detection techniques. Most of the types of events commonly detected by wireless IDPS sensors include unauthorised WLANs and WLAN devices and poorly secured WLAN devices (e.g., misconfigured WLAN settings). Additionally, the wireless IDPSs can detect unusual WLAN usage patterns, which could indicate a device compromise or unauthorised use of the WLAN, and the use of wireless network scanners. Other types of attacks such as denial of service (DoS) conditions, including logical attacks (e.g., overloading access points with large numbers of messages) and physical attacks (e.g., emitting electromagnetic energy on the WLAN’s frequencies to make the WLAN unusable), can also be detected by wireless IDPSs. Some wireless IDPSs can also detect a WLAN device that attempts to spoof the identity of another device.
Another significant advantage is that most wireless IDPS sensors can identify the physical location of a wireless device by using triangulation—estimating the device’s approximate distance from multiple sensors from the strength of the device’s signal received by each sensor, then calculating the physical location at which the device would be, the estimated distance from each sensor. Handheld IDPS sensors can also be used to pinpoint a device’s location, particularly if fixed sensors do not offer triangulation capabilities or if the device is moving.
Wireless IDPS overcomes the other types of IDPS by providing more accurate prevention; this is largely due to its narrow focus. Anomaly-based detection methods often generate high false positives, especially if the threshold values are not properly maintained. Although many alerts based on benign activities might occur, such as another organisation’s WLAN being within the range of the organisation’s WLANs, these alerts are not truly false positives because they are accurately detecting an unknown WLAN.
Some tuning and customisation are required for the wireless IDPS technologies to improve their detection accuracy. The main effort required in the wireless IDPS is in specifying which WLANs, access points and stations are authorised, and in entering the policy characteristics into the wireless IDPS software. As wireless IDPSs examine only wireless network protocols and not the higher-level protocols (e.g., applications), generally there is not a large number of alert types, and consequently not many customisations or tunings are available.
Wireless IDPS sensors provide two types of intrusion prevention capabilities:
• Some sensors can terminate connections through the air, typically by sending messages to the end points telling them to dissociate the current session and then refusing to permit a new connection to be established.
• Another prevention method is for a sensor to instruct a switch on the wired network to block network activity involving a particular device on the basis of the device’s media access control (MAC) address or switch port. However, this technique is only effective for blocking the device’s communications on the wired network, not on the wireless network.
An important consideration when choosing prevention capabilities is the effect that prevention actions can have on sensor monitoring. For example, if a sensor is transmitting signals to terminate connections, it may not be able to perform channel scanning to monitor other communications until it has completed the prevention action. To mitigate this, some sensors have two radios—one for monitoring and detection, and another for performing prevention actions.
7.5.2 Wireless IDPS Limitations
The wireless IDPSs offer great detection capabilities against authorised activities, but there are some significant limitations. The use of evasion techniques is considered as one of the limitations of some wireless IDPS sensors, particularly against sensor channel scanning schemes. One example is performing attacks in very short bursts on channels that are not currently being monitored. An attacker could also launch attacks on two channels at the same time. If the sensor detects the first attack, it cannot detect the second attack unless it scans away from the channel of the first attack.
Wireless IDPS sensors (physical devices) are also vulnerable to attack. The same DoS attacks (both logical and physical) that attempt to disrupt WLANs can also disrupt sensor functions. Additionally, sensors are often particularly vulnerable to physical attacks because they are usually located in hallways, conference rooms and other open areas. Some sensors have antitamper features, which are designed to look like fire alarms that can reduce the possibility of being physically attacked. All sensors are vulnerable to physical attacks such as jamming that disrupts radio-frequency transmissions; there is no defence against such attacks other than to establish a physical perimeter around the facility so that the attackers cannot get close enough to the WLAN to jam it.
We should mention that the wireless IDPSs cannot detect certain types of attacks against wireless networks. An attacker can passively monitor wireless traffic, which is not detectable by wireless IDPSs. If weak security methods are used, for example, wired equivalent privacy (WEP), the attacker can then carry out offline processing of the collected traffic to find the encryption key used to provide security for the wireless traffic. With this key, the attacker can decrypt the traffic that was already collected, as well as any other traffic collected from the same WLAN. As the wireless IDPSs cannot detect certain types of attacks against wireless networks, it cannot fully compensate for the use of insecure wireless networking protocols.
We hope that, from this discussion, it is clear that there are some basic differences between the IDPS technologies of general wireless networking and that of the wireless mesh network.
7.6 Potential Research Fields and Concluding Remarks
This chapter’s main focus was to present an intrusion tackling model for WMNs with the idea of utilising the resources of an intruder before taking a final decision of removing it from the network. This approach proves to be useful for WMN and other schemes dealing with intrusion detection or intrusion prevention could be employed side by side. In that case, better protection could be achieved to limit the number of false positives. Also, if applied as the only intrusion tackling module, other security schemes dealing with various types of attacks could work well alongside this mechanism. If the intruders’ resources are used for the network and strong cryptographic mechanisms protect the network packets, this model can prove to be one of the best solutions to deal with WMN intrusion. As future works, the idea could be extended to find out a more efficient solution to tackle a huge number of colluding intruders who might make packet drop seemingly a natural event. As none of the previous works dealt with intrusion in this way, this work opens a new frontier to the researchers to work on intrusion tackling rather than direct exclusion by detection or prevention. New models could be developed in this area and numerous ways could be thought of based on the findings presented in this work.
This work was supported by Networking and Distributed Computing Laboratory (NDC Lab), KICT, IIUM. Al-Sakib Khan Pathan is the corresponding author.
1. Pathan, A.-S.K., Security of Self-Organizing Networks: MANET, WSN, WMN, VANET. ISBN: 978-1-4398-1919-7, Auerbach Publications, CRC Press, Taylor & Francis Group, USA, 2010.
2. Bruno, R., Conti, M. and Gregori, E., Mesh networks: Commodity multihop ad hoc networks, IEEE Communications Magazine, 43(3), 2005, 123–131.
3. Shila, D.M. and Anjali, T., Defending selective forwarding attacks in WMNs, IEEE International Conference on Electro/Information Technology 2008 (EIT’08), Iowa, USA, 18–20 May 2008, pp. 96–101.
4. Wireless mesh networks and applications in the alarm industry. WhitePaper, AES Corporation, 2007, available at: http://www.aes-intellinet.com/documents/AESINT-WhitePaper.pdf (last accessed 9 January 2012).
5. Akyildiz, I.F. and Wang, X., A survey on wireless mesh networks, IEEE Communications Magazine, 43(9), 2005, S23–S30.
6. Deng, H., Li, W. and Agrawal, D.P., Routing security in wireless ad hoc networks, IEEE Communication Magazine, 40(10), October 2002, 70–75.
7. Zhang, Z., Nait-Abdesselam, F., Ho, P.-H. and Lin, X., RADAR: A reputation-based scheme for detecting anomalous nodes in wireless mesh networks, IEEE Wireless Communications and Networking Conference, 2008 (WCNC 2008), Las Vegas, NV, USA, 2008, pp. 2621–2626.
8. Li, H., Xu, M. and Li, Y., The research of frame and key technologies for intrusion detection system in IEEE 802.11-based wireless mesh networks, International Conference on Complex, Intelligent and Software Intensive Systems, 2008 (CISIS 2008), Barcelona, 4–7 March 2008, pp. 455–460.
9. Makaroff, D., Smith, P., Race, N.J.P. and Hutchison, D., Intrusion detection systems for community wireless mesh networks, 5th IEEE International Conference on Mobile Ad Hoc and Sensor Systems, 2008 (MASS 2008), Atlanta, GA, USA, 2008, pp. 610–616.
10. Wang, X., Wong, J.S., Stanley, F. and Basu, S., Cross layer based anomaly detection in wireless mesh networks, 9th Annual International Symposium on Applications and the Internet, 2009 (SAINT’09), Bellevue, WA, 20–24 July 2009, pp. 9–15.
11. Hugelshofer, F., Smith, P., Hutchison, D. and Race, N.J.P. OpenLIDS: A lightweight intrusion detection system for wireless mesh networks, Proceedings of the 15th Annual International Conference on Mobile Computing and Networking (MobiCom’09), New York, NY, USA, 2009, DOI: 10.1145/1614320.1614355.
12. Yang, Y., Zeng, P., Yang, X. and Huang, Y., Efficient intrusion detection system model in wireless mesh network, 2nd International Conference on Networks Security Wireless Communications and Trusted Computing (NSWCTC 2010), 24–25 April 2010, Wuhan, China, pp. 393–396.
13. Wang, Z., Chen, J., Liu, N., Yi, P. and Zou, Y., An intrusion detection system approach for wireless mesh networks based on finite state machine, Draft available at: http://www.cs.ucla.edu/~wangzy/inestablishment/resource/IDS_draft.pdf (last accessed: 24 March 2012).
14. Khan, S., Loo, K.-K. and Din, Z.U., Framework for intrusion detection in IEEE 802.11 wireless mesh networks, The International Arab Journal of Information Technology, 7(4), October 2010, 435–440.
15. Cheikhrouhou, O., Laurent-Maknavicius, M. and Chaouchi, H., Security architecture in a multihop mesh network, 5th Conference on Safety and Architectures Networks (SAR 2006), Seignosse, Landes, France, June 2006, pp. 1–10.
16. Shila, D.M. and Anjali, T., A game theoretic approach to gray hole attacks in wireless mesh networks, in Proceedings of the IEEE MILCOM, San Diego, CA, 16–19 November 2008, pp. 1–7.
17. Shila, D.M., Cheng, Y. and Anjali, T., Channel-aware detection of gray hole attacks in wireless mesh networks, Proceedings of IEEE Globecom 2009, 30 November–4 December, Honolulu, HI, USA, 2009, pp. 1–6.
18. Parno, B., Perrig A. and Gligor, V., Distributed detection of node replication attacks in sensor networks, Proceedings of the 2005 IEEE Symposium on Security and Privacy (S&P’05), 8–11 May 2005, pp. 49–63.
19. Sanzgiri, K., Dahill, B., Levine, B.N., Shields, C. and Belding-Royer, E.M., A secure routing protocol for ad hoc networks, Proceedings of the 10th IEEE International Conference on Network Protocols (ICNP’02), 12–15 November 2002, Paris, France, pp. 78–87.
20. Salem, N.B. and Hubaux, J.P., Securing wireless mesh networks, IEEE Wireless Communication, 13(2), April 2006, pp. 50–55.
21. Srivastava, V., Neel, J., MacKenzie, A.B., Menon, R., DaSilva, L.A., Hicks, J.E., Reed, J.H. and Gilles, R.P., Using game theory to analyze wireless ad hoc networks, IEEE Communications Surveys & Tutorials, 7(4), 2005, 46–56.
22. Javidi, M.M. and Aliahmadipour, L., Game theory approaches for improving intrusion detection in MANETs, Scientific Research and Essays, 6(31), December 2011, 6535–6539.
23. MATLAB. URL: http://www.mathworks.com/products/matlab/ [last accessed: 11 May, 2013].
24. Kindy, D.A. and Pathan, A.-S.K., A walk through SQL injection: Vulnerabilities, attacks, and countermeasures in current and future networks, in Building Next-Generation Converged Networks: Theory and Practice, ISBN: 9781466507616, CRC Press, Taylor & Francis Group, USA, 2013.
25. Khanam, S., Saleem, H.Y. and Pathan, A.-S.K., An efficient detection model of selective forwarding attacks in wireless mesh networks, Proceedings of IDCS 2012, 21–23 November 2012, Wu Yi Shan, Fujian, China, Lecture Notes in Computer Science (LNCS), Vol. 7646, Springer-Verlag 2012, pp. 1–14, 2012.
26. Mohammed, M. and Pathan, A.-S.K., Automatic Defense against Zero-Day Polymorphic Worms in Communication Networks. ISBN 9781466557277, CRC Press, Taylor & Francis Group, USA, 2013.