Client-Side Anti-Virus Applications
Introduction
At first, viruses were just annoying, then they started to corrupt the hard disk, and now they are stealing personal information. So what’s next? One thing is sure: between the time this book is written and the time you are reading it, new malicious attacks will have surfaced. Fending off these attacks is difficult, because you’re shooting at moving targets.
The three most serious types of attacks come through e-mail and/or the attachments sent with them, by surfing the Internet, and via security holes or bugs in software. Anti-virus applications help prevent the first two types of attacks.
This chapter will discuss the installation, configuration, and maintenance of the three most popular anti-virus applications for the PC, focusing in particular on the way these applications work with e-mail clients.
Although many people believe that the use of an anti-virus application should be mandatory, there are a lot of PCs that do not use any form of virus protection. If such a PC were not connected to the Internet, were not used for e-mail, did not have software of unknown origin installed, and did not come in contact with diskettes or recordable CD-ROMs, virus protection might be unnecessary—but that would not be a realistic use of a PC. In this regard, the infamous “Love Letter” attack shows that two things are incontrovertible:
![]() Anti-virus applications are not an overall safeguard.
Anti-virus applications are not an overall safeguard.
![]() A virus or malicious code can quickly affect a large number of PCs.
A virus or malicious code can quickly affect a large number of PCs.
The first step in choosing an anti-virus application is to determine how quickly the company updates its application to detect new viruses and threats. In the case of the Love Letter virus, the three applications described in this chapter had a fix within a week. It is essential to remember that most anti-virus applications can detect only known viruses and malicious code—new methods of attack are always hard to detect. Therefore, virus inoculate application is a more accurate term than antivirus application. Even the heuristic algorithms (which detect viruses by their behavior and the way the code is built) can only intercept variations of known viruses and files that look or act like a virus (including macros). Nevertheless, anti-virus companies such as Symantec, Network Associates, and Trend Micro learn about viruses and malicious code today and use this knowledge for even better virus protection tomorrow.
Table 5.1 is an overview of functionalities incorporated in the three e-mail anti-virus applications discussed in this chapter.
McAfee VirusScan 5
With VirusScan 5, McAfee put the last version of their popular anti-virus application on the retail shelves. Network Associates Incorporated is ending a long history of this well-known and heavily-used anti-virus application. Future McAfee anti-virus applications will only be available online, through McAfee.com Clinic, at VirusScan Online.
Availability of VirusScan
The traditional McAfee applications are still bundled as McAfee VirusScan 5. Although the version of the VirusScan engine is the same as VirusScan 4, additional features have been added (e-mail scan, download scan, and Internet filter). The new user interface, McAfee VirusScan Central, is similar to the McAfee Office User Interface. As shown in Table 5.2, McAfee maintains its traditional VirusScan software only on the Windows 9x platforms. Because VirusScan v4.x and v5.x use the same DAT files, both versions protect against the latest viruses and malicious code. However, version 4 scans only for viruses; it is not maintained or further developed. VirusScan v3.x has been fully discontinued and should be upgraded to version 5 or VirusScan Online. For Windows 2000 Professional, only VirusScan Online is available, although VirusScan for Windows NT can be used.
Updates of Virus Definition Files
McAfee will issue a new virus definition file (DAT file) every four to six weeks. The DAT file can be manually downloaded (for evaluation copies) or automatically downloaded and installed with SecureCast (if it’s a licensed copy). If a new threat surfaces, McAfee will try to issue a scan engine update/fix as soon as possible. VirusScan also gives a warning if the DAT files are out of date (older than one month).
The version number of a DAT file is <scan engine version>.<DAT sequence number>. At the time of this writing, the latest version of the DAT file is 4.0.4087.
Installation of VirusScan 5
The McAfee VirusScan setup application installs the application and lets you configure it at the same time. All VirusScan functionalities are useful, so it makes sense to activate them right away. The first dialog screen asks you to choose which kind of installation is needed; you should go for the complete installation.
The next dialog screen (see Figure 5.1) introduces the first of several wizards that are part of the installation and configuration process, called the Safe & Sound Setup (see the “Safe & Sound” sidebar).
The lower half of the screen gives you the option to run an update of the VirusScan engine and DAT files, and to create a rescue diskette. Both options should be regarded as mandatory. The first option is mandatory because between the time in which the VirusScan CD-ROM is burned and the time it’s installed, many new viruses will have surfaced, so at installation date the VirusScan software is already out of date. The second option, creating a rescue diskette, is also prudent. The chance that you will need it is slim, but if a virus blocks access to the hard disk, the rescue diskette may be the only way to regain access to it, so have a few diskettes ready during installation.
Next, the setup gives you the option to automatically insert a weekly VirusScan schedule for all local drives. You should check this option, so you won’t forget to activate it on a regular basis. After installation, you can add or modify different types of scheduling by using the McAfee VirusScan Scheduler. The next option is to execute a scan at the time the PC starts up. There’s no reason you shouldn’t check this option, since the sooner the system starts scanning for viruses, the fewer the chances for damage through a virus. And you should remember that a new(er) version of an anti-virus application can catch viruses that were previously present, but that were not recognized by the earlier anti-virus application.
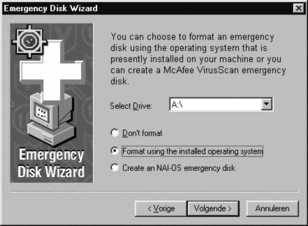
After this, the Installer program will install the VirusScan application. Before it completes, it will run a few wizards, depending on the options checked earlier. The first one is SecureCast Online (ECEngine.exe, which will call MUpdate.exe), to update the VirusScan DAT files. Before this is done, you will be prompted to register the VirusScan license. The second wizard is the Emergency Disk Creation Wizard (Edisk32.exe). The wizard prompts you for the way you want the diskette to be formatted and gives you three options (see Figure 5.2). If the drives in your PC are the FAT type (this is always the case for Windows 95, and can be when running Windows 98, especially when you have upgraded Windows 95 to Windows 98), you should go for the third option, Create an NAI-OS Emergency Disk. This is a “clean-cut” DOS version that is used to create a dedicated Emergency Disk. However, if you also have FAT32 drives, which will be the case if you installed Windows 98 Second Edition directly on your PC (or you bought it with Win98 SE), it’s best to use the second option and let the diskettes be newly formatted with the operating system.
Installation of VirusScan 4 for NT
Installation of VirusScan 4 is as straightforward as version 5, only what’s going on under the hood is totally different. Even the functions that are installed are different. This has to do with the possibilities offered by Windows NT 4 Workstation. VirusScan runs with three processes in the background:
The application can be managed via the VirusScan NT AntiVirus Console (mcconsol.exe). If you go to the VirusScan On-Access Monitor properties, you will see that it can scan on inbound (incoming) and outbound (outgoing) files. This means that every file entering or leaving the PC will be checked for viruses, including e-mail attachments and files downloaded from the Internet.
A second major difference is the Alert Manager. This difference will become apparent as you attempt to configure the Alert Manager. It has been set up with the assumption that Windows NT Workstation will be used in large networked environments. If you’re running NT Workstation on a standalone PC, you won’t use most options for the Alert Manager.
Configuration of VirusScan 5
As soon as VirusScan 5 is active, you can manage all tasks with McAfee VirusScan Central (see Figure 5.3) or by the separate programs. The configuration of VirusScan described here will focus only on the parts related to protecting the e-mail clients.
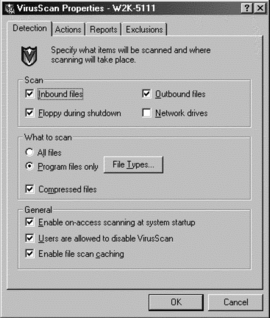
Choose Options | Vshield Properties … (or VsConfig.exe) and the Vshield Properties window will show. After choosing “E-Mail Scan,” the properties windows look like Figure 5.4.
The leftmost shortcut list of the properties window shows the three other main functionalities (modules) of VirusScan 5:
![]() System Scan Scans selected files in memory and on disk
System Scan Scans selected files in memory and on disk
![]() Download Scan Scans selected files, also e-mails, and downloads from the Internet
Download Scan Scans selected files, also e-mails, and downloads from the Internet
![]() Internet Scan Filters malicious ActiveX and Java applets and filters configured URLs
Internet Scan Filters malicious ActiveX and Java applets and filters configured URLs
The E-Mail Scan option has, like the other three functionalities, a tab strip with four options:
![]() Detection What should be scanned on access, and how, shown in Figure 5.4
Detection What should be scanned on access, and how, shown in Figure 5.4
![]() Action What to do with an infected e-mail attachment after it has been detected
Action What to do with an infected e-mail attachment after it has been detected
![]() Alert Whom to alert that an infected attachment has been detected, and how
Alert Whom to alert that an infected attachment has been detected, and how
![]() Report What and where to log the activities of e-mail scanning
Report What and where to log the activities of e-mail scanning
The Detection tab indicates that VirusScan can scan two types of mail clients. The first mail client uses MAPI (Messaging Application Program Interface), like Microsoft Exchange, MS Outlook, and Lotus cc:Mail v8 (lower versions of cc:Mail are not MAPI-compatible). The virus-scanning program accesses the active e-mail box through the MAPI interface, so the mail folders on the mail server can be checked. Actually, this doesn’t even require a MAPI-based e-mail-client, because it can directly hook into the interface. Only the client is used to set up the connection with the mail server and the proper account, and triggers the scanning program to be activated. Before the user opens an e-mail, the body and all attachments will be scanned. McAfee calls this on-access scanning. VirusScan also adds a scanning program to the Extra-menu (EmalScan.dll). With the scanning program, the user can scan e-mail, attachments, and folders manually (on-demand).
The second type is the Internet e-mail client, also called a POP3 client (Post Office Protocol version 3). Examples of POP3 clients are MS Outlook Express, Qualcomm Eudora for Windows, and Netscape Messenger. With POP3, your e-mails are downloaded from the mail server (probably located at an Internet service provider (ISP) on the Internet). Your e-mails will be scanned (using Webscanx.exe) like any other file that is downloaded from the Internet—that’s why the option states “Requires Download Scan.” However, if Download Scan is configured to scan all files, it will also scan the files opened by the e-mail client. Every time an Outlook Express folder, which is actually a DBX file, is opened, it will be scanned by the Download Scan. This takes place regardless of the fact that the property window states “Folder: All incoming mail” because this folder and the attachment are related only to the MS Exchange (MAPI) part.
I recommend that you select the option to scan “All attachments” because relying on file extensions is not safe enough. If you were to use the option “Program files only” you’d end up scanning all files, since this requires defining a long list of extensions.
When enabling the scanning of POP3-based e-mail clients, you also need to enable the scanning of files that are downloaded from the Internet. If you scan all files from the Internet, the chance of your system getting infected with viruses is greatly reduced. The drawback is that it takes time, slowing down the effective speed of the Internet connection, unless you have a Pentium III 600Mhz system with at least an Integrated Services Digital Network (ISDN) connection. However, if you are a user who downloads a lot from the Internet or a system administrator who is confronted with this kind of user, the slowdown is a good trade-off for the decreased chance of infection.
You should also enable the Java and ActiveX filter, so VirusScan 5 will scan malicious Java applets and ActiveX controls; this will slow down the Internet access, however, remember that e-mails can contain not only HTML code, but also JavaScript which is rich in opportunities for someone who wants to plant malicious code in other systems. Although you expect less experienced users to run into problems as they roam the Internet, the truth is that no one is excluded from devious attacks. See Chapter 6 for in-depth coverage of JavaScript attacks.
An interesting example of virus infection occurred during the Yugoslavian crisis when NATO developed a virus that was able to download files from a PC it had infected. This virus was sent by e-mail to users in the Yugoslavian government in an effort to retrieve information from their computers. However, the virus wound up on computers in NATO offices and started downloading files from NATO PCs.
Use all functionalities that are offered by an anti-virus application like VirusScan 5. If there is a substantial slowdown in Internet access, however, choose the option “Program files only.” The default extensions list is fairly complete. In the case of filtering Java and ActiveX, don’t take any chances—keep filtering enabled.
Let VirusScan also check compressed files (for example, .zip files), since the System Scan will not scan all compressed files. VirusScan scans only the most well-known compression programs during e-mail and download scans. For programs like ARJ and ARC, you must use the VirusScan command-line scan utility (scan32.exe).
In the Action tab, you can select the appropriate action to be taken at the moment a virus or malicious code is detected. If you’re using VirusScan for personal or home use, select “Prompt for user action.” This is the only option that makes you aware of a virus. For network/office
environments the option “Move infected files to folder” is the most effective. Deleting the file removes the proof of a virus. Cleaning may fail and should directly be followed up. The option “Continue” should never be used—the longer the virus or malicious code stays in one of your attachments, the greater the chance it will do some serious harm.
The third tab is Alert. For personal or home use, you can consider letting VirusScan automatically send a reply mail, notifying the sender that you were sent an infected e-mail/attachment. In a network/office environment, the option to alert a system administrator should be activated—first, because the fact that you or someone else got an infected attachment means that the virus protection on the mail server is leaking (see Chapter 12 for more information on server-side scanning). Second, the system administrator must directly check to determine whether the virus has spread to more mail accounts.
The last tab, Report, is used for selecting logging options. By logging as much information as possible, you can periodically check the status of VirusScan. This is something that you shouldn’t forget to do. What often happens, as I’ve experienced myself, is that a program (like an anti-virus application) may seem to be working on the surface but when you check the logs, errors are reported.
Configuration of VirusScan 4 for NT
Configuring VirusScan 4 for NT is easy. As described earlier, VirusScan 4 for NT runs with three services, one of which (mcshield.exe) is in fact for scanning all input/output (I/O) from disk and network. This will include all e-mail messages and attachments. As Figure 5.5 shows, scanning involves inbound files (files entering the system through, for example, a modem, a network, or a diskette) and outbound files (files that are leaving the system, such as e-mails, files written to a network drive, or downloadable files). This type of scanning is based on access. That’s why you shouldn’t be scanning network drives, because it’s time consuming and should be a task for the fileserver. If you’re using McAfee products, the fileserver should be running NetShield.
Also, be selective with the files you are scanning on access. Before you know it, scanning all files will take up a fair amount of processor capacity. It makes sense to select the option “Enable file scan caching.” Although this will use extra memory, it speeds up scanning. The Properties Sheets Actions and Reports are similar to the ones described for VirusScan 5. However, from the Exclusions sheet you are able to exclude files from being scanned. Ensure for yourself that excluding a file does not decrease the chance of catching a virus.
McAfee VirusScan Links
McAfeeVirusScan updates of the virus definition files: http://download.mcafee.com/updates/updates.asp
McAfee AntiVirus Center (contains a large amount of information on viruses): www.mcafee.com/anti-virus
McAfee VirusScan 5 download (no longer available on the McAfee Web site, but still downloadable from ZDNet): ftp://zdftp.zdnet.com/pub/private/sWIIB/utilities/security/scan32.exe
McAfee VirusScan 4 for NT download: www.nai.com/asp_set/buy_try/try/products_evals.asp
Norton AntiVirus 2000
Norton AntiVirus has a long history. Like many Norton utility programs, it was regarded as essential way back in the MS-DOS times. After some dwindling success during the Windows 95 years, Symantec took over Norton and turned it in a different direction. One of the products that came out of this acquisition is Norton AntiVirus 2000.
Availability of Norton AntiVirus 2000
Symantec took the Norton utilities and built them into a number of Norton 2000 packages collected under the name Norton SystemsWorks. One of these packages is Norton AntiVirus 2000. The actual version of Norton AntiVirus is 6.0. Symantec still supports the older Norton AntiVirus versions 4 and 5 (see Table 5.4 for supported versions).
Table 5.4
Supported Versions of Norton AntiVirus
| Norton AntiVirus | Version |
| AntiVirus for Windows 3.x | 4.0 |
| AntiVirus for Windows 9x | 6.00.03 |
| AntiVirus for Windows NT workstation | 6.00.03 |
| AntiVirus for Windows 2000 Professional | 6.00.03 |
| AntiVirus for Macintosh | 6.0 |
All versions can use the same virus definition files, thereby guaranteeing that everyone using Norton AntiVirus can make use of the latest virus detection. Norton AntiVirus 2000 (v6) determines the platform it is being installed on and then makes a platform-dependent installation. Symantec will try to maintain the support for as many Windows platforms as possible. The Norton AntiVirus 2001 application will support Windows 9x, Millenium (Me), 2000, and NT.
Updates of Norton AntiVirus 2000 Definition Files
Symantec releases a new definition file every week for newly detected viruses that will not be intercepted by the current version of the Norton AntiVirus definition files. There are two ways of obtaining a newer definition file. First, by downloading it from the Symantec Web site (the offline method if you want to upgrade manually). Second, by a scheduled or on-demand download through Symantec LiveUpdate, the automatic update function for a great number of Symantec products. LiveUpdate will search for an available Symantec download site, check if a newer version of the AntiVirus definition file is available (or if an update of Norton AntiVirus is available, for that matter), and download and install it. An advantage of LiveUpdate is that it will download only the changes since the last update. These incremental files are called micro definitions (MicroDefs).
Every time an update is applied, the new files are put in a new directory (see the section, “Configuration of Norton AntiVirus 2000”). The name of the directory is the same as the version of the virus definition files. The format is <date>.<sequence number>, with YYYYMMDD as the format of the date and 999 the format for the sequence number. The sequence number is related to the build with the same date; in most cases this will be 001.
Installation of Norton AntiVirus 2000
The installation of Norton AntiVirus 2000, like VirusScan, is straightforward. During installation, a number of options are presented (here also it is prudent that you check all options and do a full installation). Norton AntiVirus also allows you to disable these options after installation, but making them active during installation is prudent.
The installation of Norton AntiVirus is the same for all Window platforms, as far as functionality is concerned. Of course, under the hood of Norton AntiVirus, the installation is platform-dependent.
One of the first windows gives you three installation options:
1. Enable Auto-protect at startup. This means that Norton AntiVirus is loaded and enabled (Navapw32.exe) during the Windows startup. If not checked, it’s still loaded, but disabled.
2. Add a weekly scan task to the (Norton Program) Scheduler. Windows 95 uses its own scheduler program (nsched32.exe). The other operating systems use the Windows Task Scheduler. You can add additional tasks through the main program (Navw32.exe or NMain.exe, in the Symantec shared directory that is used through the Desktop shortcut of AntiVirus 2000).
3. Scan at startup. For Windows 9x this means that a command line is added to autoexec.bat:
@C:PROGRA∼1NORTON∼1NAVDX.EXE /Startup
This is an MS-DOS 16-bit application that does a virus scan on all parts of the operating system that could be harboring viruses (such as memory and boot records) and unloads itself before Windows9x is loaded. Unless you do not like putting commands in the autoexec.bat, add this scan for safety before the Windows operating system is loaded.
The next window in the installation process targets the installation of e-mail virus scanning (see Figure 5.6). At the top, you are also able to enable or disable e-mail protection. The Norton installation program has already checked which accounts of POP3 e-mail clients are present on your system; these are displayed in a list within the window.
Accounts on IMAP- or HTTP-based e-mail clients are not identified, and you must configure these manually after installation. Virus protection can be enabled per e-mail client account. The third option in the window allows you to select the response upon the discovery of an infected attachment. Here also, you should always let the application ask you what action should be taken. This is the only way the presence of a virus becomes apparent to you.
When enabling e-mail protection, it is important to understand that Norton AntiVirus makes changes to your e-mail account before it is able to scan the mails for viruses (this is explained in the next section, “Configuration of Norton AntiVirus 2000”). The installer does give you a notice of these changes, but if you are not aware of what they mean, it is a surprise to find out what happened. Now Norton Installer will install AntiVirus 2000, followed by running the registration wizard. At the end, the user is prompted for three options:
1. Run LiveUpdate after installation. You should do this to get the latest updates of Norton AntiVirus definition files and applications. Remember that LiveUpdate will download and install the new virus definition files and subsequently reboot the PC.
2. Create a rescue disk set. The Norton Rescue Disk (Rescue32.exe in Program FilesNorton Rescue) is an extensive utility that can create a set of diskettes (default 5) containing all essential Norton AntiVirus files, Registry files, and other files the user wants on the rescue diskettes. It is important that the boot diskette be able to access all local drives. Depending on the drive type (FAT, FAT32, NTFS, or even HPFS), the operating system that boots from diskette must be able to access all available drives. It can also make rescue tapes using the IOMEGA Zip or Jaz drive.
3. Scan for viruses after startup. Because a new anti-virus program can detect more viruses, it’s always safe to start with a full scan after installation or update.
This completes the installation, and after rebooting, Norton AntiVirus 2000 is operational. As the system is booted again, a shortcut to Norton AntiVirus 2000 (C:…Symantec SharedNMain.exe /dat:C:Program FilesNorton AntiVirusswplugin.nsi) becomes available on the desktop. The /dat: switch is absolutely necessary to let it work. The NSI file (Norton Systemworks Integrator) takes care that the Norton Main program loads all the right executables.
The Task tray contains one or two new icons, Norton AntiVirus 2000 Auto-Protect (Navapw32.exe) and Norton AntiVirus Scheduler (Nsched32.exe if it is running on Windows 95). If you activated E-mail Protection, then Poproxy.exe will be running in the background. No other Norton AntiVirus 2000 processes are running in the background on the Win9x platforms. On the Windows NT/2000 platforms, the following are running:
Configuration of Norton AntiVirus 2000
You can maintain all configuration options from the main application of Norton AntiVirus 2000 (NMnmain.exe, or Navw32.exe for that matter; see Figure 5.7). The directory Program FilesCommon FilesSymantec Shared holds the directory VirusDefs, where the virus definition files are residing. With every update that is applied, a new directory is created with the latest complete set of definition files. This makes it easy for the advanced user to go back to an earlier version (see the sidebar, “About AntiVirus 2000 Settings”).
The other AntiVirus 2000 files are located in Program FilesNorton AntiVirus (the installation directory). AntiVirus uses the Registry to save all setup settings, and program options are placed in configuration files (with DAT extensions).
Norton AntiVirus 2000 holds the unique and identifying data of the boot records in the file Navsysr.dat (in the Windows NT version this function is
not available), located in the directory Ncdtree (default). This important data can be regarded as the fingerprints of the file. During each scan of the boot, it compares the current fingerprint with the recorded one. If a fingerprint differs, and a virus is presumed, Norton AntiVirus alerts you. This technique is called inoculating. (In prior releases of Norton AntiVirus, it was also possible to inoculate other files on your PC. However, AntiVirus 2000 has made this function no longer available; the advanced scanning techniques incorporated in AntiVirus 2000 makes inoculation of viruses embedded in files obsolete.) Because boot records and system files should not change, inoculation is a good way to detect embedded viruses.
The rest of this section will focus on the Norton AntiVirus 2000 configuration for protecting e-mail clients.
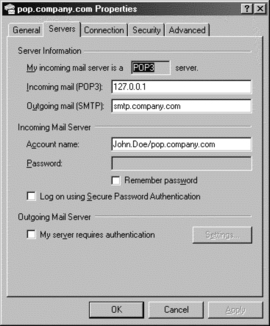
Norton AntiVirus 2000 enables its scanning for viruses on e-mails by modifying the e-mail client account’s server settings (see Figure 5.8). The POP3 server name is replaced by the address 127.0.0.1 (also known as localhost or loopback) and the original server address is added to the account name. If you were to look at the processes running on your machine, there would be one called poproxy.exe (in this section called the POP-proxy). This process listens for e-mail communication (authentication and downloading of e-mails) on this IP address. As the name of the program suggests, the POP-proxy is a go-between, preventing the POP mail server from having direct contact with your e-mail client.
The moment you check for new mail, using AntiVirus 2000 E-mail Protection, your (POP3-based) e-mail client contacts the POP server—in this case, the mail server address is 127.0.0.1:110 (110 is the default port on the mail server for POP communication being your own computer). If you had checked “Remember Password” for your account, authentication would be transparent to you; otherwise, you get a window (see Figure 5.9) prompting you to enter the password. If you were not aware of the change AntiVirus made to your e-mail account, you will be by now (it’s stating that the server is 127.0.0.1). If both account name and password are available to the e-mail client, it tries to find the POP mail server. The POP-proxy will emulate the POP communication that normally takes place with the actual mail server and replies to the call of the e-mail client. Now that the connection has been made, the authentication takes place. The e-mail client passes the account name and password to the POP mail server, in this case the POP-proxy.
In this example (see Figure 5.8) the account name is John.Doe/pop.company.com. POP-proxy splits this account name between the actual account name (John.Doe) and the POP mail server name (pop.company.com). With this information, it now connects to the mail server (pop.company.com), pretending to be the e-mail client, and performs the authentication. Presuming the password is correct, the authentication is successful and a connection is established over which the e-mails can be downloaded. The e-mail client will now start to check if there are e-mails available, and if so, fetch them from the mail server. The POP-proxy forwards the requests to the POP mail server. The mail server will send available messages. POP-proxy will not forward the e-mails directly. Instead, it reads the complete message, including all attachments, and checks for possible viruses. If no virus is detected, the complete message is forwarded to your e-mail client. After all messages are transferred, the e-mail client closes the connection with the POP-proxy and POP-proxy disconnects from the POP mail server. Only after the connection is fully terminated between the POP-proxy and the POP mail server, does POP-proxy fully terminate its connection with the e-mail client. Remember that Poproxy.exe scans for viruses only on incoming mail; outgoing mail bypasses POP-proxy and the e-mail client sends it straight to the SMTP mail server (in this example, smtp.company.com). The POP-proxy also assumes that a connection between client and server exists. It does not set up a dial-in connection—that is up to the e-mail client or it must be done manually.
This solution is pretty straightforward, however it is invasive, meaning that it changes personalized settings and not systems settings. Norton AntiVirus Auto-Protect (Navapw32.exe) and McAfee VirusScan 5 do the latter. A problem that may occur, related to the way TCP/IP is set up on your system, becomes apparent when your e-mail client gives the message: Unable to find host. It is not easy to explain here how to solve it—the cause of the problem lies in the fact that communication between e-mail client and POP-proxy is not functioning. It could be that the POP-proxy is not connected through the default (110) port. Another possibility is that changes may have been made to the hosts or lmhosts files, whereby 127.0.0.1 points to some other host. Or the system assumes the address is not local and uses the default gateway to find the host.
I know it hardly sounds realistic, but I have seen stranger things. Most of the time, an experienced user is able to solve it. I have installed AntiVirus on different machines and have had this problem on one (running Windows 95)—honestly, under other circumstances, the machine gave me a hard time with TCP/IP name resolving. At first I thought I was the only one that could not get POP-proxy to work, but looking at the technical support pages of Qualcomm’s Eudora, I stumbled upon someone asking about the same problem. The answer was far from the quality you would expect from a company like Qualcomm: they said that the best thing to do was to disable AntiVirus E-mail Protecting (as if we hadn’t thought of that!).
Anyhow, if disabling Norton AntiVirus 2000 seems the only solution, remember that the manually configured e-mail account must be reset manually. This is also the case if you decide to uninstall AntiVirus 2000. The uninstall process inverts only the changes made on the automatically configured e-mail clients.
In most cases POP-proxy will work, but it is good practice to check and test the functioning of your e-mail client (as should be the case for all changes made to your system).
On the whole, the number of configuration options for e-mail protection is very limited. If you go to the Options button on the Norton AntiVirus console, and choose “E-mail Protection,” a window similar to Figure 5.10 is shown. This is used to enable or disable AntiVirus 2000 e-mail protection. If you check “Enable e-mail protection” (recommended), you can subsequently check the e-mail accounts you want to be protected by AntiVirus 2000 Poproxy.exe. Of course you can disable it again at another stage. During both actions, the e-mail clients must not be active, because this would prevent AntiVirus from making the account changes.
For the Action option, you must make the choice as to how AntiVirus 2000 should respond to an attachment. As stated earlier, the “Ask me what to do” choice (recommended) is the best, as this is the only way to find out that a virus/malicious code has been detected. No additional alerts are implemented in the Windows 9x of AntiVirus. Although AntiVirus 2000 under Windows NT has the same options, only a special alert service (NAV Alert) runs in the background. In a networked environment, you should consider using the Corporate or Enterprise version of Norton AntiVirus 6; they are far more suitable and maintainable.
When using the Windows NT/2000 version, running the NAV Alert Service offers you more possibilities for alerting others, for example system administrators, through mail and management software.
The E-mail Protection Advanced sheet (see Figure 5.11) gives an additional four options. These and the Action option are saved in the Registry from where Poproxy.exe reads them.
1. Display tray icon when processing e-mail. This option is self-explanatory. For testing purposes it can be handy to have some signal that POP-proxy is working.
2. Display the logo screen when scanning e-mail. The option is also self-explanatory. (Personally it escapes me who but Symantec benefits from this option. I presume you would, like me, prefer that the e-mail client periodically check for new mail in the background, without being bothered by a logo screen while you’re working in another application.)
3. Temporarily disable e-mail protection. With this option, you can disable the e-mail protection without unloading Poproxy.exe and restoring the account settings. POP-proxy is still the go-between, but now without checking for viruses and malicious code. You should only use this if you are experiencing problems with downloading trusted e-mails (for example if has a very large attachment). Remember to activate it afterwards, else you run without virus protection. If you do not have any of the two display options active, you have no way of knowing if Poproxy.exe is not scanning for viruses.
4. Protect against timeouts when scanning e-mail (recommended). When Poproxy.exe is downloading an e-mail with one or more large attachments, the e-mail client could time out on the server, because POP-proxy is not sending anything to the client. Remember that POP-proxy will pass attachments only after it has fully downloaded and scanned for viruses/malicious code. By checking this option (the default), POP-proxy will periodically send something to the e-mail client (so-called keepalive packets). There is no reason for keeping this option checked.
Norton AntiVirus Links
Norton AntiVirus virus definition file updates: www.symantec.com/avcenter/defs.download.html
Norton AntiVirus Research Center: www.symantec.com/avcenter/index.html
Norton AntiVirus 2000 Service & Support (NAV 2000): www.symantec.com/techsupp/custom/mysupport.cgi?miniver=nav2000&x=32&y=11 www.symantec.com/techsupp/nav
Norton AntiVirus 2000 (trial version): www.symantecstore.com/Pages/TBYB/index.html
Trend Micro PC-cillin 2000
Trend Micro is a company with the sole focus of building security software. Trend Micro PC-cillin 2000 is the latest PC-based anti-virus application that profits from the knowledge built up within Trend Micro over the more than ten years that this company has existed.
Availability of Trend Micro PC-cillin 2000
Trend Micro has a comprehensive set of content security products with PC-cillin. PC-cillin 2000 is not the actual version number. In fact, Trend Micro uses two version numbers—one for the program and one for the scan engine. PC-cillin is version 7.5x and the scan engine is 5.17. The latest update of both can be found on the Trend Micro Web site (see the section, “Trend Micro PC-cillin Links”).
If you use the automatic update function, it checks for the latest version of both the program and virus definition files (which Trend Micro calls the Pattern file). See Table 5.5 for supported versions.
Table 5.5
Supported Versions of Trend Micro PC-cillin
| Trend Micro PC-cillin | Version |
| PC-cillin for Windows 3.x | n/a |
| PC-cillin for Windows 9x | 7.51.0 |
| PC-cillin for Windows NT workstation | 7.51.0 |
| PC-cillin for Windows 2000 Professional | 7.51.0 |
Trend Micro supports earlier versions of PC-cillin, as long as they are used with the latest version of the scan engine. Trend Micro, like Symantec (Norton) and Network Associates Inc (McAfee), is dedicated to providing the latest virus scanners and scanning functions—you should make use of it.
Updates of PC-cillin Virus Definition Files
Trend Micro releases a new version of the virus pattern (VP) file every week (usually Tuesday, as stated on their Web site). Like the other two anti-virus applications, you can get the latest version of the latest VP file, first by going to the Web site and downloading the file, called LPTxxx.ZIP (xxx stands for the pattern number). Second, by using ActiveUpdate, which downloads the latest version of the VP file automatically (scheduled or on-demand). However, ActiveUpdate has an interesting feature—it does an incremental update. Only the changes to the current VP file that you are using are downloaded, and then incorporated into the existing file, making the latest version. If you update weekly, this means you need to download only about a fraction of the actual size.
Every time an update is applied, a new file is created in the installation directory of PC-cillin 2000 (by default, C:Program FilesTrend PC-cillin 2000). The name of the file is LPT$VPN.<pattern number>. The pattern number is a three-digit number.
Installation of Trend Micro PC-cillin 2000
Trend Micro PC-cillin 2000 is the third anti-virus application covered in this chapter, so the installation process will look very familiar to you. The beginning of the installation process, however, is slightly different. It starts off with a full virus scan of the local drives. After that, you are asked to supply the license/serial number of your PC-cillin 2000 copy. If you fail to supply one, it installs PC-cillin as a trial version. After installation, you can always upgrade to a full version through the registration option (Support|Registration). If you already registered a trial version, you are asked if you want to change the version information. When you answer “Yes,” a registration window will pop up. This window holds the “Upgrade to Full Version” button that enables you to provide the serial number.
Next, you are given an Options window (see Figure 5.12) that is made up of three parts. The first is Internet Protection, which has three options:
1. Parental Web Filtering This option gives you the opportunity to prevent access to certain Web sites.
2. Malicious Object Protection This option allows you to prevent the downloading of known malicious Java or ActiveX applets. You should certainly keep this option checked. If you check this and/or the previous option, PC-cillin will activate Webtrap.exe (under Windows NT it is called WebTrapNT.exe) in the background.
3. POP3 Scan The name says it all. You can enable virus/malicious code scanning on your POP3 e-mail accounts. If you check this option, PC-cillin will activate Pop3trap.exe in the background. Pop3trap works the same way as Norton AntiVirus Poproxy.exe (under Windows NT called Pop3Trap.exe), except that it changes all accounts at once, and the POP mail server is replaced with localhost instead of 127.0.0.1.
The second part, Active Desktop, is not enabled but it can be activated after installation. I would leave it as is. In the third and last part, you can allow PC-cillin to do an automatic update of the pattern file and program/scan engine file. You should check this option, as explained earlier in our discussion of the other anti-virus applications.
Next, the installation program gives you the opportunity to provide the information needed if the update program can only access the update files through a proxy server. If you work from home, this will in most cases be transparent, so you can skip this option and continue the installation process. If you are installing PC-cillin in a networked office environment, it is very likely that Internet access passes through a proxy server. In this case, you need to complete the proxy server information (IP address/port and possible username/password to access the proxy server). If you are not familiar with this type of information, contact the system or network administrator.
The next step of the installation process is the creation of emergency rescue disks. You are given two options:
I advise you to create a rescue disk set, especially if you do not have one already. The pattern disk option is not meant as a first-time option. This option should be used only after an update of the virus pattern file, so you have an up-to-date rescue disk. If you choose to postpone the creation of the rescue disk set, you can create it later with the rescue utility (Rescue.exe, Start | Programs | Trend PC-cillin 2000 | Create Rescue Disk).
After installing PC-cillin, the ActiveUpdate program is started, preceded with the registration process. (You need to register to be able to use ActiveUpdate. Even if you are using the trial version, registering is possible without any limitations.) You will need to do a reboot afterwards, to let PC-cillin pick up the updated pattern file.
When the system is rebooted, a shortcut is created on the desktop. If you have the Quick Launch Toolbar activited, a PC-cillin icon will also appear. In the Task bar, you’ll see the icon of the PC-cillin Real-time Scan (pcciomon.exe for Windows 9x and pntiomon.exe for Windows NT).
PC-cillin 2000 performs a virus scan of memory, boot records, and system files at the startup of the PC. On the Windows 9x platforms, this is done by placing the following command line in the AUTOEXEC.BAT:
C:PROGRA∼1TRENDP∼1PCSCAN.EXE C: C:WINDOWSCOMMAND /NS /WIN95
(C: and C:WINDOWSCOMMAND are the directories to be scanned; /NS means No Subdirectries; /WIN95 indicates that the operating system is Windows 9x).
Configuration of Trend Micro PC-cillin 2000
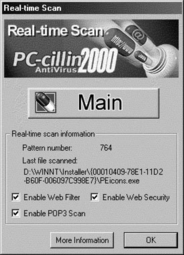
As mentioned earlier, PC-Cillin 2000 runs three processes in the background of your system. These can easily be enabled/disabled via the window that appears upon double-clicking the PC-cillin Real-time Scan in the Task Tray (see Figure 5.13). From this window you can (de)activate the three main Internet Protection scanning functions (run by two processes), Enable Web Filter, Enable POP3 Scan, and Enable Web Security. From this window, you can also start the main/console program (Pccmain.exe; see Figure 5.14). The More Information button gives you access to version numbers and the pattern file number.
Checking one of these functions activates it. The related processes are already in memory, but are informed to take action (or, in the case of unchecking the option, deactivate the action). In the case of Enable POP3 Scan, PC-cillin must also modify all the POP3 e-mail accounts. You should be aware that the e-mail client is not running at the moment you activate/deactivate POP3 scanning—this prevents PC-cillin from modifying the server information of the accounts.
When you start the PC-cillin 2000 main program, through the Main button in the Real-time Scan window (see Figure 5.13)—or the shortcut on the desktop, or the icon on the Quick Launch bar—a window is shown, similar to the one in Figure 5.14. The Properties frame is the largest, and the left-hand bar (similar to the Outlook bar) contains six main functions. However, no Mail Scan is present here. To access the Mail Scan properties (shown in Figure 5.14) you must use the menu bar (Options| Mail Scan). This properties sheet is divided into two parts:
1. Manual Scan for Outlook PC-cillin 2000 scans only local Outlook folders (i.e., not Outlook Express); on-demand scanning is provided for Outlook (95, 97, 98, and 2000), not real-time, so you need to use the Scan Wizard to do a manual scan.
2. Real-time Scan for POP3 The Real-time Scan scans for viruses/malicious code during the download of e-mails from a POP3 mail server.
As you perform a manual scan on Outlook, the on-demand scanner program opens the Outlook folders, accesses all mails, and opens and decodes all attachments. The manual scan program does not scan for viruses and malicious code. This is done by the real-time scan process, which scans every file that gets accessed. So the manual scan program, in a way, breaks the Outlook up into a series of files that can be scanned separately. Remember that you cannot scan Outlook Express folders with the manual scan for Outlook function. If a virus or malicious code is found in an e-mail attachment, action is taken as specified in the properties sheet. You can choose from the following:
![]() Clean This will try to remove the virus/malicious code from the attachment.
Clean This will try to remove the virus/malicious code from the attachment.
Because you are given only these options, “Clean” is the most appropriate one. PC-cillin 2000 will give a virus notice, so you are aware that it detected something. It will also inform you if the virus/malicious code has beeen cleared.
The second action you can select determines what to do if a virus/malicious code cannot be removed from the attachment. You are advised to use the “Pass” option, but notice what the exact attachment is. As soon as the scanning is over, you should quarantine the infected file. Use “Delete” only if no other option is available to get rid of the virus.
You can scan Outlook folders by selecting the Scan function in the left bar of the main program and then select Scan Wizard (or, using the main menu, File | Scan | Scan Wizard). Now choose the last option of the list, “What do you want to scan,” and PC-cillin will take care of the rest.
In the lower part of the Mail Scan properties window (Figure 5.14), you can select the action to be taken if a virus/malicious is detected during the download of an e-mail attachment from a POP2 mail server. This is the same process as with the scanning of Outlook folders. You see the checkbox options “Splash” and “Start POP3 Scan” in the frame, “Action when virus is found.” These are not related to the “Action when virus is found” option and it would have made more sense if they were placed in a separate frame. The functions of these two options are as follows:
![]() Splash If checked, a PC-cillin logo is shown for a few seconds every time the real-time POP3 scan starts, indicating that it is doing its job.
Splash If checked, a PC-cillin logo is shown for a few seconds every time the real-time POP3 scan starts, indicating that it is doing its job.
![]() Start POP3 scan This option is exactly the same as checking the “Enable POP3 scan” option in the Real-time Scan window (see Figure 5.12). In fact, these are linked.
Start POP3 scan This option is exactly the same as checking the “Enable POP3 scan” option in the Real-time Scan window (see Figure 5.12). In fact, these are linked.
As you see, there is not a lot to configure to let PC-cillin do its work. Personally, I think it’s unfortunate that a few options are not included in this program: an Action option of “Quarantine” would be appropriate, and extended Alert and Security options. This shows that PC-cillin 2000 is meant to be a single-user PC AV application. If you want these options for a networked environment, you should consider a corporate solution of Trend Micro.
A corporate solution (like Trend Micro OfficeScan Corporate Edition with Trend Virus Control System) or enterprise solution (like Norton AntiVirus Enterprise Solution 4.0) enables you to battle viruses effectively in large networks. Even with a small number of PCs to manage, a corporate anti-virus solution has a number of advantages. However, if you have to manage over 100 PCs, it’s vital that you have a corporate/enterprise solution, if only to prevent you from spending all day keeping PCs virus-free. The first important benefit is the single point of administration. From a single workstation you can monitor and manage the anti-virus application on all systems, using an anti-virus management console application. From within a Windows NT or Netware domain all client PCs can be accessed. To communicate between the management workstation and a client PC, the PCs must run a special communication agent. Through this agent, the management console can not only query the anti-virus status of the PC, but also update/upgrade the anti-virus application and virus definition files. From the server from which the updates/upgrades take place, a central quarantine can be set up, along with other centralized functions, accessible to all client PCs. The result of such a solution is that management efforts can be reduced significantly. There are additional functionalities that come with the corporate/enterprise anti-virus solution:
![]() Automated deployment of version upgrade or replacement of a version
Automated deployment of version upgrade or replacement of a version
![]() Unattended updates of virus definition files (for example, overnight)
Unattended updates of virus definition files (for example, overnight)
![]() Centralized alert and dispatch of virus detection
Centralized alert and dispatch of virus detection
![]() Centralized configuration of the anti-virus application, through one or more anti-virus policies (a PC is linked to a specific policy and every change to a policy can be distributed with a single mouse-click)
Centralized configuration of the anti-virus application, through one or more anti-virus policies (a PC is linked to a specific policy and every change to a policy can be distributed with a single mouse-click)
![]() Centralized management console can manage different versions of the anti-virus application across different platforms (or operating systems)
Centralized management console can manage different versions of the anti-virus application across different platforms (or operating systems)
![]() Prevention of configuration changes by users
Prevention of configuration changes by users
![]() System-wide report of anti-virus statistics and analysis
System-wide report of anti-virus statistics and analysis
Although the benefits of a corporate/enterprise solution are already clear, its ultimate benefit becomes apparent when you must apply a fix for a high-risk virus (like the “Love Letter” or Melissa viruses). It would be a matter of hours to get all PCs updated, instead of days, and your daily operations that keep your network virus-free can be reduced to a matter of minutes.
Trend PC-cillin 2000 Configuration Settings
PC-cillin 2000 differs from the other two anti-virus applications in this chapter in the way it stores its configuration settings. The most significant difference is that PC-cillin 2000 for Windows 9x does not use the Registry to store any settings at all. Only the registration of PC-cillin 2000 as an installed application is recorded in the Registry. For the other settings, one configuration file (Pcc2k95.ini, for Windows 9x) is used, located in the C:Windows directory. For PC-cillin 2000 for Windows NT the configuration settings file is called PCC2kNT.ini and is located in the C:Winnt directory. However, all settings are also recorded in the Registry.
There is no clear reason why the configuration settings file is located in the Windows directory. The practice of placing files in this location stems back to the Windows 3x operating system. However, most current applications commonly place configuration files in the applications installation directory. The configuration files used by ActiveUpdate (Version.ini and Server.ini) are placed in the installation directory, so it is not clear why the Pcc2k95.ini is not here too. As a home user or system administrator you should be aware of the location of the configuration file. If you want to move it to another directory, be sure this directory is in the PATH variable, or else PC-cillin will be unable to locate the configuration file. Also, if you upgrade your system and place the new Windows version in another directory, you should move the configuration file.
PC-cillin 2000 does not provide any security feature that prohibits users from changing the options. By removing the Pccmain.exe from the system you only remove the user interface from the system. This does not prohibit the user from making changes to the configuration file. As you can see in the following excerpt of the Pcc2k95.ini file with the relevant e-mail scanning components, it can be easily interpreted.
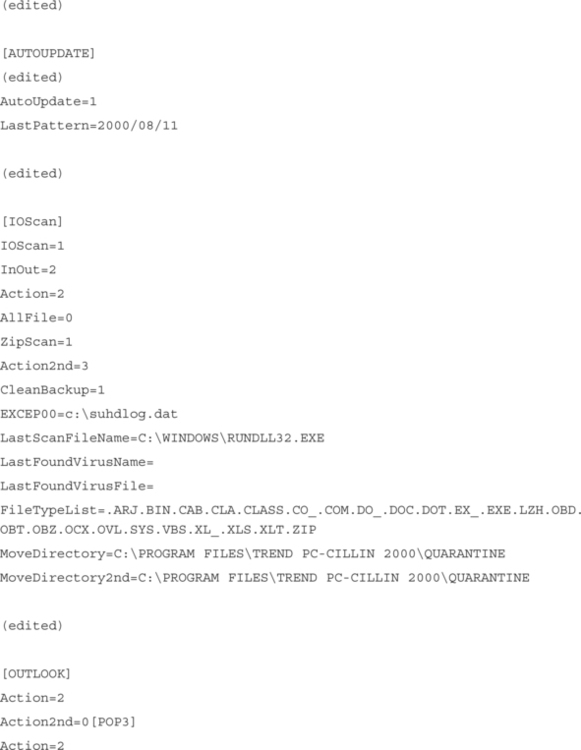

Not only configuration settings are recorded, but also runtime (operational) information, like LastScanFileName=C:WINDOWSRUNDLL32.EXE.
The [RESUME] part is used by PC-Cillin to find the appropriate pattern file. Changing the value will result in the program not finding the pattern file or using a different one.
Under [POP3] the keywords correspond to:
| Action=1 | Action when virus found: clean |
| Action2nd=1 | Action on uncleanable files: delete |
| Splash= 0 | Splash |
| ONOFF= 0 | Start POP 3 Scan / enable POP3 Scan |
It’s nothing fancy, but it’s highly maintainable, even without the Pccmain.exe program. Remember that all PC-cillin 2000 programs/utilities use this configuration setting, so be careful when changing this file manually, in case you have to remove the PC-cillin main program to prevent people from using it.
Trend Micro PC-cillin 2000 Links
Trend PC-cillin 2000 Virus Pattern file update: www.antivirus.com/pc-cillin/pattern.asp
www.antivirus.com/pc-cillin/support.htm
Trend PC-cillin Virus Information Center:
www.antivirus.com/pc-cillin/vinfo/
Summary
Because the e-mail client is so vulnerable to viruses and malicious code, the use of a client-side anti-virus application is absolutely crucial. In this chapter we discussed the three most popular anti-virus applications: McAfee VirusScan 5, Norton AntiVirus 2000, and Trend Micro PC-cillin 2000. One of the most important factors in choosing one of these applications is how updates to the applications are provided.
McAfee VirusScan 5 has the ability to scan for viruses in e-mails when using MAPI-based or POP3-based e-mail clients. It can scan for viruses while downloading files from the Internet, block malicious Java applets and ActiveX controls, as well as restricting access to specific Web sites. Trend Micro PC-cillin 2000 has these same functionalities, only it cannot real-time scan MAPI-based e-mail clients, and it uses a POP3 proxy to scan the e-mails. Norton AntiVirus 2000 uses the same technique to scan for viruses in e-mails, but lacks the functionality for explicitly scanning for malicious Java applets and ActiveX controls and blocking access to specific Web sites.
On the whole, the three are highly comparable and are the top choices of all available anti-virus applications. They can all efficiently scan all POP3 traffic, guarding us from taking in viruses using the Internet’s most popular application. None of the three is preferable above the others—just try them and then make your own choice!
FAQs
In general, there are no absolute arguments for choosing a specific antivirus application. The three AV applications described in this chapter are equal in functionalities (see Table 5.1). If you need one for your home PC or on a few business PCs, try all three using trial versions, and choose the one you are most comfortable with. In networked environments, centralized maintainability and deployment is very important. Both Norton and Trend Micro have Corporate/Enterprise versions of their AV applications. Another important point in choosing a particular AV application is if it can protect the mail system (or e-mail client, for that matter) from downloading infected e-mails or attachments. If you use a MAPI-based e-mail client (like Outlook 9x/2000), Norton AntiVirus and Trend PC-cillin cannot deliver realtime scanning of the e-mail client.
The simple answer is “as often as possible.” If you use an automatic update option, you can schedule it daily. If you do not use an automatic update, you can check weekly if the company’s Web site provides updates. Or subscribe to their newsletter (the three programs discussed in this chapter have newsletters), so you get a mailing with new virus information, including information on new updates. A rule of thumb is to update the virus definition files at least twice a month. Knowing that, on average, 300 new viruses are detected monthly, waiting longer than that to apply an update significantly increases the chance of being confronted with an active virus/malicious code on your PC.
You can get a false virus alert (also called false positive) if files are changed on an operating system (OS) level. This happens when you install an application on your PC, run an upgrade of your OS, or apply an OS service pack. False positives are not harmful as long as they do not abort the installation process. So, always ignore a virus alert during an installation, unless you have serious doubt that this is not a false alarm. However, the best thing you can do is disable the AV application, do the installation, followed by a manual full system AV scan. If no virus is detected, reboot your system and you are safeguarded from any virus (extremely rare situations excluded).
Yes, at least initially. It is vital that you conduct a full scan at first. A full scan will result in a significant loss of performance, but you can then do partial scans of recently updated files at regular periods. That way, you can be reasonably sure your system is virus-free, while not causing a significant slowdown. However, if you have a Pentium III PC with Ultra DMA-66/100 and 128 MB of internal memory, then you can scan every file for viruses on-access. On-access scanning, also called real-time scanning, means that every time a file is accessed, it is scanned for viruses, even if you accessed and scanned that file minutes before. There is no reason not to do it—it’s better to be safe than sorry!
Yes, normally the anti-virus application will uninstall without a hitch, but you must perform a reboot after the uninstall. After the reboot the anti-virus application is effectively removed from your system. However, a 100 percent uninstall is never achieved, meaning that the empty installation directory is still present, for example in shared directories (underProgram FilesCommon)—especially if the uninstall queried you in removing shared files and you replied No. And the Registry can still contain references for the anti-virus application. This will not hurt the operation of your system. There are special utilities that can clear unused keys out of the Registry (for example, within the McAfee Clinic service). Inexperienced users are urged not to get into the Registry to remove the keys manually. One wrong delete can bring your system down.
Am I safeguarded from ever having my PC infected with a virus when I use the latest anti-virus application?
No guarantees are ever handed out, as we saw when the Love Letter Visual Basic script raged over the Internet. But then again, having car insurance does not mean that you never get into a car accident. With every new version of an AV application, the heuristic scanning algorithms become much better, decreasing the chance of your PC becoming infected with an unknown virus.
Yes, although the number of viruses that attack Linux is currently small, there are already anti-virus scanners that work on Linux. Since the number of Linux-based systems is increasing rapidly, it can be expected that the number of Linux viruses will also increase. The system can also be penetrated by Windows-based viruses that can access Linux volumes. Here are a few anti-virus applications that are available for Linux:
F-Secure for Anti-Virus version 4.x: www.f-secure.com/download-purchase
VirusScan for UNIX-Linux Version 4.7: www.nai.com/asp_set/buy_try/try/products_evals.asp
Norton AntiVirus 2000 (with the latest update, Norton AntiVirus can scan volumes with the ELF format)
AmaViS Virus Scanner (A Mail Virus Scanner): http://aachalon.de/AMaViS
AntiViral Toolkit Pro: www.avp.com
McAfee VirusScan Validate 3.0.0: www.mcafeemall.com
Although every virus is malicious code, the term is mostly used to refer to programs that are sent with HTML (Web) pages. These can be Java applets (written in the Java language), ActiveX controls (mostly written in Visual Basic), or JavaScript/VB script code within a Web page. In normal circumstances, they are used to enhance the functionalities of the Web page, but can also perform other actions, such as sending files from your PC to a rogue server on the Internet. And since your e-mail client can receive HTML pages as e-mail, malicious code can get into your system as part of an e-mail.
No, there is a distinct difference between Windows 9x and Windows NT/2000 that affects the working of the anti-virus application. Windows 9x with its FAT(32) volumes incorporates little security, so the anti-virus application can access files and devices with ease. However, Windows NT/2000 is a far more complex operating system and incorporates a high level of security in its system and NTFS/HPFS drives. The anti-virus application must operate as a service that runs on the system using the system account, to be able to access all files and devices. Because the anti-virus program needs to hook into the system, it uses several dynamic link library (DLL) files that differ from operating system to operating system. Although an NT-based anti-virus application may run on Windows 2000, it will probably not work effectively. Check with the software producer if you need a specific version for an operating system. Nevertheless, the virus scanner part of the application will be the same for all operating systems, since the intelligence of a virus scanner is platform-independent.