Deploying Server-side E-mail Content Filters and Scanners
Introduction
We looked briefly at content filtering in Chapter 9 during our discussion on securing Microsoft Exchange Server. In this chapter, we will focus more intently on scanning e-mails and attachments for questionable content. We will talk about the different ways in which filtering is done, what is looked for during the filtering process, and what is done with the e-mail once it’s filtered. We will also look at the types of attachments that can be scanned and filtered, such as document, ActiveX, and Java files.
Many organizations employ firewalls and Internet proxies to protect access to their networks. However, they are still exposed to attack from viruses, spam, mail bombs, and other inappropriate content that can come through the door within e-mail. Without some type of content-filtering application to scan e-mail, corporations are wide open to productivity-robbing attacks from advertisers, malicious virus programmers, and pornography promoters.
Some e-mail servers are built with content filters. However, one of the more popular messaging platforms, Microsoft Exchange Server, does not come bundled with a content filter. In fact, most of our illustrations in this chapter will involve Exchange Server and the more popular third-party software packages used with it. Content scanning isn’t done only at e-mail servers and e-mail gateways—it can also be done at firewalls. We will examine content filtering and scanning software that work at firewalls as well.
Overview of Content Filtering
In most cases, virus-infected, unsolicited, or otherwise inappropriate e-mail comes with some telltale identifiers in the subject or in the message. Content filtering is a method that can be used to isolate and identify keywords that signal the presence of these types of e-mails. Content filtering deals with what information is allowed into a network, unlike firewalls, which are concerned with who is allowed into the network. Corporations must work to not only protect against outside hackers breaking into secure networks (access control), they must work to protect the information that comes into the network via e-mail (content control). This is done through content filtering.
Content filtering is a matter of network and business integrity. Content filtering will protect a corporation’s network from infection from e-mailborne viruses, network congestion from system misuse, as well as loss of network service from spam and spoof attacks. Loss of information, lost productivity, exposure to legal liability and confidentiality breaches, as well as a reduction in damage to reputation through misuse of company e-mail should all be the result of an effective content-filtering software implementation.
When using a content-filtering tool, all e-mail is filtered at the server before it reaches the intended recipient. E-mail can be filtered based on sender, subject, excessive file size, prohibited content, profanities, corrupted data, pornography, or racist or hate e-mails. One of the leading content-filtering tools currently on the market is MIMEsweeper by Content Technologies. MIMEsweeper uses a technique called lexical scanning to read all e-mail.
Content filtering works at the application layer of the Open System Interconnection (OSI) model. The content of e-mail entering or leaving a network is not legible until the data that comprises it is interpreted through some sort of interface; the application layer is responsible for providing a user or application interface for system and network processes. This is usually done at the mail server application.
A content-filtering product works with a compiled database of keywords that represent a content security risk. When an external e-mail is received, corporations using content-scanning products can reject e-mail that contains words or phrases that have been compiled in the database, by directing the e-mails to a quarantine zone. Once in the quarantine zone, the e-mail can be further dissected to determine the safety and/or validity of the e-mail and its contents. If it is determined that the e-mail is safe, then it is passed on to the intended recipient; if the e-mail is determined to be a security threat or in violation of corporate policy, the e-mail is discarded.
Content filtering is widely used as a security measure to protect corporations against secure information being revealed, lawsuits, racist and pornographic material, as well as hate mail—but an additional benefit to content filtering is the ability to help protect against virus attacks. When content-filtering software is deployed on a Simple Mail Transfer Protocol (SMTP) mail server, for example, virus attacks can be minimized. Such software uses a keyword search to determine if an attachment containing VBScript commands are contained within the e-mail. If such an attachment is found, the e-mail will be sent directly to quarantine to determine content and further navigation. Figure 11.1 illustrates one typical path that an e-mail message would follow when entering into a network that uses content-filtering software.
1. An e-mail message is received from the host mail system.
2. The e-mail message is broken down into component parts, such as header, body, and attachments. The header is examined for sender and recipients along with other key values that have been previously determined by the system e-mail administrator. The body and attachments are recursively disassembled until the data is in raw form.
3. Upon breakdown of the body and attachments to raw form, the data is examined to determine the presence of any security threat, content control, and/or virus attack.
4. If a security threat, content control, and/or virus attack are present, the determination is made for the disposal of the e-mail message.
5. Once the e-mail message has been disposed of, the threat no longer exists.
As we mentioned, the body and attachments of e-mails are broken down to raw form. This breakdown, also called recursive container disassembly, or recursion, provides for high-speed and efficient e-mail breakdown, optimizing a corporation’s success rate at removing e-mail with inappropriate content before it ever reaches the intranet. Recursion is critical in content security. Recursion separates raw data in the protocol layers (headers, encoding, and compression) from the body and attachments contained within e-mail. Once data has been broken down to a more simple state, content-analysis tools offer the best chance of success. This includes any third-party anti-virus tool that is currently on the market. Once the body and attachments have been broken down, the data is scrutinized for content. VBScript and Java commands are easily detected at this level. Information from the compiled database can be used to pull out an e-mail and send it to the quarantine area. E-mails may also be rejected due to macro, worm, or Trojan horse viruses detected once recursion occurred.
System administrators are able to assign numerous quarantine areas. The quarantine areas can be assigned based on file size, sender name, subject, compiled database keywords, encrypted messages, recursive breakdown with virus present, or even junk e-mail. Once the e-mails have reached quarantine, they are dealt with, in most cases, in a predefined manner. In some cases, it is the system administrator’s responsibility to determine further action. Protocol for handling inappropriate content may have been established depending on what a particular IT department determines to be best practice. In most cases, all e-mail received in quarantine is disposed of without further hesitation. Content-filtering software can be configured to add legal disclaimers, automatically archive e-mail, or generate information messages. These messages can be sent to the intended recipient within the network to advise of quarantined e-mail, or a log file can be created to assist in adding further information to the compiled database for future use.
When content-filtering software is used, e-mail liability is reduced. Recently there has been a surge of lawsuits involving large corporations and former employees over the use of e-mail. In January 2000, Nissan Corporation was involved in a lawsuit involving employees who had been fired for sending inappropriate e-mails via company e-mail. The verdict was favorable to Nissan for two reasons, the first being that Nissan had a policy in place that strictly forbade the use of company computer systems for non-company related business. Nissan demonstrated a duty of care in an attempt to reduce unacceptable employee activity, thereby minimizing the company’s own liability. The second reason was that part of Nissan’s company IT policy was to perform content filtering. Because Nissan took the time to ensure that employees did not have to tolerate questionable material via e-mail, they were able to detect such e-mails being sent through their corporate e-mail system, and were able to dismiss employees, based on the content-filtering findings and the policy that Nissan had in place.
Frequently, insurance companies see an organization’s attempt to secure its infrastructure and property as a blessing because it lowers liability. We can imagine that in the Nissan case, the established security policy is what allowed both Nissan and its insurers to breathe a sigh of relief. Content filtering is more than just censoring e-mails and noting what URLs are accessed by employees; content filtering essentially affords people the opportunity to use the Internet as well as an intranet without worrying about unwanted negative material, while at the same time minimizing the legal liability to corporations. Policy-based content security depends on a corporation establishing an acceptable e-mail and Web usage policy, then educating employees on the policy, and enforcing the policy with a desirable software solution. It is an organization’s legal responsibility to protect itself and its employees from undesirable e-mails. In order to accomplish this, organizations need to have content-filtering software in place.
Corporations have an easier view of the type of e-mail that is being received into and out of the network. This affords obvious benefits to every company:
![]() At the lowest level, content filtering protects against unwanted e-mails being distributed to employees from external sources.
At the lowest level, content filtering protects against unwanted e-mails being distributed to employees from external sources.
![]() Junk e-mail is minimized, almost to the point of non-existence, which reduces slow response time within the intranet.
Junk e-mail is minimized, almost to the point of non-existence, which reduces slow response time within the intranet.
![]() Content filtering allows e-mails to be sent to quarantine based on sender, subject, and file size.
Content filtering allows e-mails to be sent to quarantine based on sender, subject, and file size.
![]() Content filtering uses recursive breakdown to protect against embedded virus attacks.
Content filtering uses recursive breakdown to protect against embedded virus attacks.
![]() Content filtering protects against secure company information being sent out via company e-mail. The same compiled database of keywords may be used to filter outgoing e-mail for company-sensitive information.
Content filtering protects against secure company information being sent out via company e-mail. The same compiled database of keywords may be used to filter outgoing e-mail for company-sensitive information.
It is important to note that content filtering can be used not only for e-mail applications but can also be used in Web-based applications within corporations as well. The most obvious method is to prevent certain Web sites from being accessed through the company intranet. A compiled database of keywords is listed, and any sites searched under those words are not accessible. Keyword lists are most often used in the case of pornographic Web sites as well as hate Web sites. Content filtering can be taken to an even more invasive level, by using packet sniffers. Packet sniffers are programs that monitor network activity and produce reports for network administrators that provide such detailed information as what, where, when, how, and by whom data is being transferred to and from the Internet.
As we can see, content filtering is a necessary component for e-mail security. Because suspicious e-mail is usually revealed within either the header or body, it is easy to filter out unwanted e-mail. Further use of recursive breakdown helps to severely minimize virus attacks by finding embedded VBScript controls and Java applets within attachments and additional body material of e-mails.
Filtering by Sender
The easiest, most obvious way to filter e-mail is by looking at the sender of the e-mail. Usually, the sender is visible in the header of the e-mail. The sender field of the e-mail is one of the default items that content-filtering software is designed to look at. It is already possible, in most enterprise e-mail server software, to create a list of senders and e-mail domains that are rejected from exchanging e-mail. Content-filtering software goes a little further in that its filters can adapt to new senders and log their identities for future reference without an administrator having to manually input additions to the list on the mail server.
Some senders try to be clever and disguise their identities by using spoofing tricks to make it seem that the e-mail is actually coming from someone or someplace else. Sometimes the sender field is blank to the human reader or it may appear the e-mail message is coming from the recipients themselves. However, content-filtering and attachment-scanning software installed at the server can see through these tricks by filtering and breaking down the e-mail header to raw data, which reveals hidden information about the source of the e-mail. So even if the e-mail was relayed through multiple SMTP servers on the Internet, this can be seen once the header containing the sender information is broken down.
Furthermore, if the sender cannot be revealed, scanning the body of the e-mail or the attachments for suspicious content would be the next step that the software would take. Once discovered, questionable e-mail would be blocked or eliminated.
Filtering by Receiver
Filtering by receiver gets to one of the fundamental reasons for content-filtering software and brings the comprehensiveness of content filtering to the forefront. Filtering by receiver not only looks at e-mail entering the organization, but, more important in some cases, it handles e-mail leaving the organization. Employees of an organization might be forwarding sensitive information to outside parties that may jeopardize an organization’s entire business process. They may also be sending confidential information to co-workers. It is also quite possible that virus developers that want to avoid detection may use their workplace e-mail accounts to launch virus attacks over the Internet.
Software that detects a trend in who gets what information within and outside an organization can be truly helpful in securing an enterprise’s corporate messaging infrastructure. Frequent recipients of certain e-mail can be logged and the content of the e-mail can be more closely examined to ensure that sensitive or confidential material is sent to appropriately authorized individuals.
Subject Headings and Message Body
Usually, it is easy for an e-mail recipient to recognize what a particular e-mail is about by simply looking at the subject heading of the e-mail. However, the proliferation of Internet ads, chain letters, and unsolicited e-mail or spam that is transmitted on a daily basis makes it a little difficult at times to decipher exactly what the contents of an e-mail hold—many of these e-mails have subject headers that don’t match the actual message in the body of the e-mail. Messages that appear to be legitimate are received and opened daily by unaware end-users only to discover that the e-mail is actually an advertisement. For users with free Web-based e-mail accounts, visiting certain sites that register their e-mail addresses often seems to open up the floodgates of unsolicited e-mail. One can only guess at the great opportunity that exists for viruses, and other malicious applications to propagate through this medium.
Content-filtering software that can search through the subject headings and body text of e-mails goes a long way in protecting end-users, especially from the types of threats and distractions that drain productivity. Most of the junk mail sent and received over the Internet uses the same keywords and sentence structure, which makes it easy to weed them out once the body is examined. These keywords, as mentioned before, are matched up against a database of keywords to look for in the content filtering software. Some of the less savvy unsolicited mailers will be picked out as soon as the header is read.
Overview of Attachment Scanning
As discussed in the Content Filtering section, attachment scanning is necessary for protection against e-mail and Web attacks on corporate IT infrastructures. Most newly created viruses appear embedded in the body or as an attachment. For third-party virus-protection software to have the greatest chance of success, the attachments must be broken down and scanned. Using current scanning software, e-mail attachments can be scanned in a matter of seconds, causing no delay of delivery for secure e-mails. Of course, all employees should use basic e-mail common sense. The following steps should be made known to all employees when dealing with e-mails with attachments:
![]() Do not open an attachment from an unknown source.
Do not open an attachment from an unknown source.
![]() Do not open any files attached to e-mail unless you know what the file is. Even a file from a friend or family member could pose a virus threat to the network.
Do not open any files attached to e-mail unless you know what the file is. Even a file from a friend or family member could pose a virus threat to the network.
![]() Do not open any files contained in e-mail if the subject line is questionable.
Do not open any files contained in e-mail if the subject line is questionable.
![]() Delete any chain e-mails and junk e-mail.
Delete any chain e-mails and junk e-mail.
![]() Do not download any files from strangers.
Do not download any files from strangers.
![]() Use caution when downloading files from the Internet.
Use caution when downloading files from the Internet.
![]() Ensure that end-users update their anti-virus software regularly.
Ensure that end-users update their anti-virus software regularly.
Following these standard policies will help aid any company’s best effort to minimize virus attacks.
When attachment scanning is performed, e-mail is received into the network, and is immediately scanned based on a standard protocol. One standard protocol could be that all e-mails received with attachments must be scanned. This protocol should be in effect within all organizations, as attachments are the greatest source of virus attacks within a network. The attachment is decoded and decompressed if necessary. The attachment is scanned for viruses (see Figure 11.2). If the attachment is clean, the e-mail is sent directly to the intended recipient. If a virus is detected, the e-mail is either moved to quarantine or destroyed. Standard protocol can be used to notify the intended recipient that a virus-infected e-mail was received and to contact the original sender for a clean attachment.
When attachment scanning is performed on e-mails being received from outside the company network, it is a much cleaner, quicker solution to a potential virus problem. As stated above, any e-mail with attachments is scanned and further delivery of e-mail is halted if a virus has been detected. If that same virus-infected e-mail is received from within the network and a virus is present, the original sender’s machine must be scanned and anti-virus software must be updated. It is likely that a virus attack will spread more quickly from internal sources than from an outside source.
Obviously, stopping e-mail attachments from being sent is not a feasible solution, but those same e-mail attachments are a critical success factor in securing your company’s network from virus attacks. This can seem like a daunting task, since no company has control over who sends e-mail messages into the network (although content-filtering software can be used to eliminate e-mail messages from known unwanted sources). However, when you consider that sharing messages between customers and vendors is a necessary part of today’s business activity, there is no doubt that working with e-mail attachments has to be made a safe practice.
The major concern was once about executable programs that were attached to e-mails. That is no longer the case, because macro viruses are now the number one source of virus attacks, and the number one method for these attacks is via e-mail.
Attachment-scanning software is available as a front-end tool to recursively break down any embedded e-mail attachments and to dissect them for possible virus infection. When using scanning software, a company is afforded a better opportunity to secure its network against virus attacks, thus saving company dollars. Any attachments that are found to be questionable are moved to a quarantine area and dealt with from that area, securing the network from virus infections, or other inappropriate content from incoming e-mails. Virus-infected or inappropriate e-mails can be deleted directly from the quarantine area, sending a message to the intended recipient advising them to contact the original sender for a clean attachment.
Content filtering and attachment scanning are used in conjunction in most scenarios. Hand in hand, these components help to secure the network from all possible attacks, virus as well as unwanted junk e-mail, hate e-mail and other types of e-mail that can cause legal issues for companies. Protection needs to occur at two primary levels: at the desktop level, with each employee having updated anti-virus software running on his/her machine and at the server level with content filtering and attachment scanning software running to protect against e-mail attacks. Having both levels secured will help to alleviate the threat of e-mail attack.
Attachment Size
Most Word documents and Excel spreadsheets exchanged between endusers as e-mail attachments are only a few kilobytes in size. For this reason, attachment-scanning software can raise flags and perform predefined operations on e-mails with attachments that exceed a certain size.
Large amounts of data leaving or entering an enterprise network as attachments to e-mail could be a regular occurrence for some organizations, but it could also mean that someone is sending data out of, or into, the company. The data leaving might be sensitive company information, or a newly created virus. The data entering the network may be an e-mail bomb designed to flood the network and crash e-mail servers or cause a broadcast storm in the network, bringing network traffic to a grinding halt.
Attachment Type (Visual Basic, Java, ActiveX)
E-mail attachments exist in many forms and file types. The advent of macro viruses, worms, and Trojan horses raised the awareness of Internet security experts, and in fact took Internet security to a whole new level. The concept that documents sent via e-mail as attachments may not simply hold the information contained in the text, but may also carry packages that alter or destroy application and computer system function, fueled the anti-virus and e-mail scanning software industry. Now there are potential new threats presented by technology such as Microsoft’s ActiveX and Sun Microsystems Java.
ActiveX and Java were originally conceived for the purpose of making the Web browsing experience less flat and two-dimensional and more dynamic, attractive, and exciting. ActiveX and Java are the technologies responsible for the animation and interactivity we enjoy on the World Wide Web today. In fact, developers already incorporate Java and ActiveX capabilities in the form of Web browser plug-ins. There are other applications besides Web site animation provided by the enhanced capability of ActiveX and Java. The power of these two programming environments is more than evident, even in this early stage of their lives. Skilled programmers are already manipulating this power in the effort to create more sophisticated virus threats.
In order for Java applets and ActiveX controls to work, either for or against us, they must gain access to our hard drives. Considering how much time we as a culture spend on the Internet, it is not unusual to download an ActiveX control or a Java applet hidden in a file or other program. ActiveX controls and Java applets are capable of reading and deleting files, accessing RAM, and traversing a network by hopping from computer to computer. What is more dangerous about ActiveX controls and Java applets is that they are created in such a way that they do not require intentional input or action from an unsuspecting end-user. They virtually run themselves once granted access to a hard disk.
This is why content filtering and attachment scanning are essential for a secure network today. If we can stop the malicious code from entering our networks, we can prevent it from spreading through our organization. Server-based solutions that protect organizations from possible infiltration by Java and ActiveX should be implemented as best practice, since traditional access control security methods cannot even begin to combat the threat that ActiveX and Java could present.
McAfee GroupShield
McAfee GroupShield is one of the more commonly used groupware server virus-protection packages. GroupShield works on the principle that traditional file-level anti-virus software cannot scan within the proprietary databases of most e-mail server systems. GroupShield comes in different types to suit the particular file format of the e-mail server it is intended for (for example, Lotus Domino Server and Microsoft Exchange Server).
GroupShield allows us to scan individual mailboxes for viruses on the server as well as personal and off-line folders (as in the case of GroupShield for MS Exchange).
Installation of GroupShield
We will now perform an installation of McAfee GroupShield for Microsoft Exchange Server 5.5.
1. Click the Start button and select Run.
2. Click the Browse button and find the Setup.exe file
3. Click the OK button to start the installation. The installation splash screen should appear as shown in Figure 11.3.
4. Click the Next button until the Server setup screen appears as shown in Figure 11.4. Enter the server name and the installation path for GroupShield and click Next.
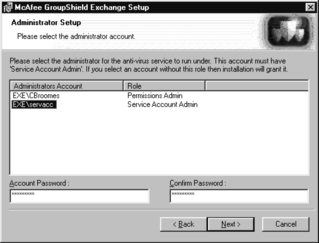
5. At the Administrator Setup screen, add the Exchange Server service account and enter the password (see Figure 11.5). Click Next.
6. GroupShield then needs us to define the type of quarantine medium and the location of quarantined e-mails/attachments as shown in Figure 11.6. Click Next.
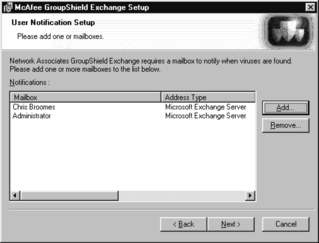
7. GroupShield needs to be able to notify administrators whenever it encounters a virus. The User Notification Setup screen, shown in Figure 11.7, displays the administrators to be notified when viruses are detected.
8. GroupShield then suggests we schedule a one-time scan to establish that the server is currently free of viruses (see Figure 11.8). Select a date and time and click Next.
9. GroupShield finally displays all selected options for installation (see Figure 11.9). Click Next to confirm options and begin installation.
Configuration
GroupShield configuration is done mainly in the Microsoft Exchange component that is installed on the Exchange server. However, the Outbreak Manager component also requires configuration via the creation and application of rules. Let’s look at GroupShield configuration in Exchange.
The GroupShield component can be accessed by first selecting the server in the Exchange Administrator console (see Figure 11.10).
The component has ten tabs, each containing configuration for a different aspect of GroupShield functionality. The first tab, the Administration tab, contains settings for the GroupShield administrators Exchange mailbox and the quarantine database or directory (see Figure 11.11). There is also a denial of service attack protection setting to regulate scanning of attachments (see the Attacks section later in this chapter for a description of denial of service attacks). Attachments that take too long to scan will consume too much of GroupShield’s scanning engine’s resources and render it unable to scan any other attachments; GroupShield service for scanning any other attachments is denied.
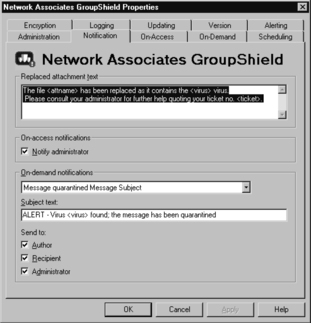
The Notification tab specifies whether to send an alert to the administrator, the sender, and the intended recipient of a message. The notification messages are categorized into on-access notification (viruses detected by automatic protection of e-mail), and on-demand (virus detected in e-mail during manual scan). The types of notification messages can be specified and customized (see Figure 11.12).
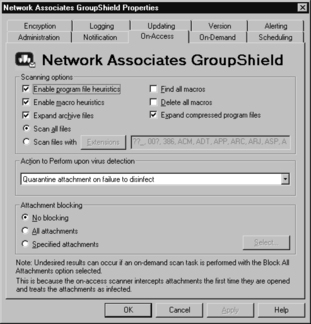
The On-Access tab configures scanning options and how to respond to infected e-mail once detected; how to handle attachments upon e-mail access is also controlled on this screen. On-Access scanning works once email is opened. Figure 11.13 displays the best settings for this feature. (Special attention should be paid to the note at the bottom of the Attachment blocking section.)
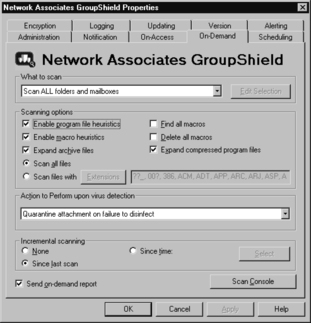
The settings on the On-Demand tab are almost identical to the On-Access tab, as you can see in Figure 11.14. Since on-demand scanning is used on e-mail that has already been accepted into the system, the Attachment blocking settings are replaced here by the incremental scanning settings.
The Scheduling tab is simply there to allow administrators to schedule scanning and update tasks. Scans should be scheduled for a time period of least mail server activity, such as middle of the night.
The encryption tells GroupShield how to treat encrypted e-mail during on-demand scanning (see Figure 11.15). GroupShield can be set to trust all encrypted e-mail, trust only those mailboxes that are listed, or trust no encrypted e-mail and quarantine them all. GroupShield’s scanning engine cannot scan encrypted attachments so it is recommended that we select the quarantine option for encrypted messages to ensure the safety of our mailboxes. GroupShield’s On-Access scanning settings can be set to trust mailboxes that employ Network Associates’ PGP mail encryption software.
The Logging tab sets the depth of event logging for GroupShield. Figure 11.16 displays the Logging tab with the event and component activities that can be logged. These events are displayed using the McAfee Log Manager. The maximum number of events that can be logged can be specified. The Logging tab even allows us to log this activity in the NT Event Log.
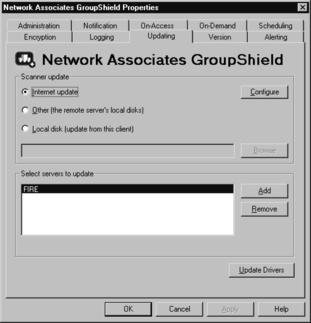
The Updating tab shown in Figure 11.17 lets us specify where we want to receive GroupShield anti-virus and program updates. We can download updates from the Internet, from another server on our network, or from a file on the server’s own disks. Not only can we specify where to get updates, we can select which servers to update.
The Version tab displays the versions of the different components of the GroupShield Exchange software. The server software, scanning engine, the virus definition file versions, and the date of the scanning driver are displayed.
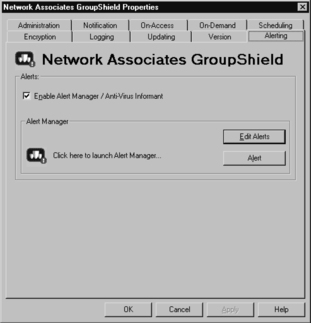
McAfee Alert Manager is the component that allows administrators to be notified of the outcome of virus-scanning operations immediately after the operation is complete or when a virus is found. The Alerting tab, shown in Figure 11.18, allows us to activate or deactivate Alert Manager and to customize alert messages. We can also launch the Alert Manager from this tab.
Specific Settings
The first setting to specify is the denial of service timeout setting. As we mentioned earlier, if GroupShield spends too much time trying to scan a particular attachment, its scanning services are unavailable to other e-mail with attachments. E-mail messages without attachments can be read while other attachments are being scanned. We want a good balance between giving GroupShield enough time to scan each attachment without locking up the system. The default time-out value is 60 minutes, with a maximum time-out value of 2,880 minutes. If scanning of any attachment exceeds the specified setting, then the e-mail attachment is sent to quarantine. As we can see, selecting the right setting for denial of service timeout is critical for maintaining efficient e-mail traffic flow. If the setting allows for too great a period of time, any other e-mail that is received during that time period will not be scanned. If the setting is for too short a time, then e-mails may be sent to quarantine unnecessarily. We should always be sure to adjust the time-out to achieve the right balance for our network.
Trend Micro ScanMail for Exchange Server
ScanMail for Microsoft Exchange Server has enjoyed widespread use since its first appearance on the market in 1997. This package is said by some to be complicated to install. We will now look at how to perform an installation of ScanMail 3.5 on our Exchange server.
Installation of ScanMail
The ScanMail installation program is quite robust, allowing us to install ScanMail on several servers remotely, while also being quite straightforward and easy to perform as we will see in this installation. Administrator permissions are required to install ScanMail.
Double-click the setup icon to start the installation program. The Welcome screen appears as shown in Figure 11.19. Click Next.
Select the server you wish to install ScanMail on from the list shown in Figure 11.20. Click Next.
Enter the account and password of a domain administrator with Exchange server administrator permissions. This will serve as the logon account. Usually this is the same as the Exchange server service account (see Figure 11.21). Click Logon.
Select the ScanMail components you wish to install as shown in Figure 11.22. Click Next.
ScanMail installs the selected components and begins to function.
Configuration
Once installed, ScanMail should be configured to suit an administrator’s specific requirements for security on the network. Configuration of ScanMail is done in quite a few different areas of the application. Let’s walk through some basic configuration for ScanMail to protect against virus-infected attachments.
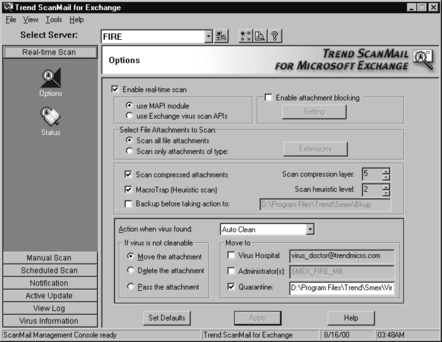
The first options that need to be configured in ScanMail are the realtime scanning options (see Figure 11.23). The real-time scanning options tell ScanMail what to scan, how to scan (whether to use the Exchange anti-virus Application Programming Interface, or API), and how to handle any virus-infected files.
Figure 11.23 shows that ScanMail is using Exchange’s API for scanning. The options can be set so that all attachments on the server are scanned, including compressed attachments and macro traps. Once a virus is found, the options determine whether the attachment should be quarantined, deleted, or allowed to enter. Levels of compressed file scanning and intelligent (heuristic) scanning can also be defined in the settings. In the event of a virus outbreak, the attachment blocking feature allows us to block certain file types that we can specify from entering the e-mail system entirely. Therefore, they don’t have to be scanned.
The Manual Scan and Scheduled Scan options are identical to the realtime scanning options, except that they require user intervention to be carried out.
Specific Settings
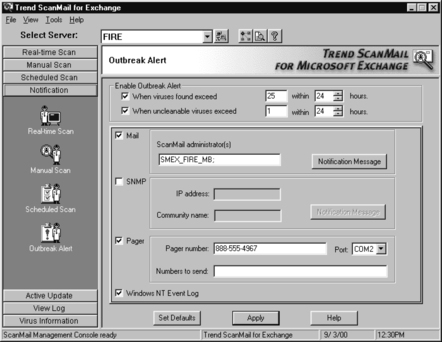
Some of the settings that allow ScanMail to stand apart from the competition are not scanning-related. The Notification options cover real-time scanning and scheduled scanning, manual scans, and virus outbreaks. Figure 11.24 displays the Notification options screen.
This screen allows us to alert the sender, the recipient, and the administrator in the event of a virus being detected. We can even set notifications to write an event in the Event Log. The notifications options during Realtime Scan, Manual Scan, and Scheduled Scan are identical. Outbreak Alert notifications, however, differ significantly from the other three event notifications. A virus outbreak has to exist for a significant period of time before it’s detected. Outbreak Alert notification settings specify how the administrator is contacted in the event of a virus outbreak. Outbreak Alert notification settings also define a threshold for what is considered a virus outbreak. Once the threshold is reached or exceeded, the alert notification procedure is triggered. Figure 11.25 displays the settings for notification.
Additional ScanMail Offerings
ScanMail comes in four different flavors to support the four most prevalent messaging platforms. ScanMail supports Lotus Domino and cc:Mail, HP OpenMail, and Microsoft Exchange. ScanMail for Lotus Domino supports real-time scanning during replication and at message reception at the mail router. ScanMail for cc:Mail supports scanning of LAN-based and mobile cc:Mail users as well as the cc:Mail DB6 and DB8 Post Office databases. ScanMail for HP OpenMail supports improved real-time scanning and cleaning of virus-infected e-mail at the service router. All these versions of ScanMail now provide remote monitoring capabilities through a Web browser. The addition of this feature, among others, and ScanMail’s support for the leading e-mail applications mentioned earlier have enabled it to remain a major player in the market.
ScanMail’s creators have added a new component that allows administrators to incorporate content filtering and spam blocking based on user-defined rules, as well as to protect the system from viruses. The ScanMail eManager plug-in for Microsoft Exchange allows for real-time management of inbound and outbound e-mail based on the content of the header, body, and any attachments contain therein.
ScanMail eManager incorporates a spam filter that relies on rules, defined by the administrator, on how to handle inbound e-mail based on the information contained within the header. The mail domain, the sender, and the contents of the subject field, for example, can be examined to determine whether the incoming e-mail should be accepted or rejected.
The eManager content filter uses rules that apply to the body of e-mail and attachments, searching for questionable keywords and rejecting or blocking any e-mail that contains them. The eManager content filter uses a customizable word list to store its keywords. Administrators can edit the word list and add or delete keywords at their discretion to block whatever types of e-mails they wish. The default rules cover quite a wide range of scenarios from pornography to Web greeting cards. The word list influences the scope of the scenarios and vice versa. Incoming e-mail is dissected and scanned using the rules and any content matching entries in the word list is noted and the e-mail containing them is, in most cases, quarantined or deleted.
Spam and content filtering both occur on the server as messages are received into the Exchange server, but before the message is written to the Exchange Information Store database. The end-user never even knows that dangerous e-mail was sent to them.
Content Technologies’ MAILsweeper for Exchange 5.5
MAILsweeper for Exchange 5.5 is a true content-filtering/blocking application designed specifically to rid the Microsoft Exchange Server messaging platform from resource-robbing content. MAILsweeper is a service that comes as part of Content Technologies’ MIMEsweeper content filtering package and works along with any command-line virus protection available for Windows NT and Exchange to provide more comprehensive protection for Exchange Server.
Installation of MAILsweeper
The MAILsweeper installation requires that our server run Windows NT Server 4.0 and at least Exchange Server 4.0 with the latest service pack. Let’s step through the installation of MAILsweeper 3.25 on our NT 4.0 Server with Exchange 5.5 SP3.
Double-click the setup icon to begin the installation. The screen shown in Figure 11.26 should appear. Click Next.
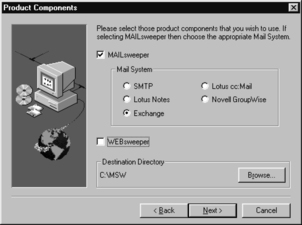
Click Next to accept the defaults for the next screen. Select MAILsweeper and Exchange on the Product Components screen as shown in Figure 11.27. Click Next.
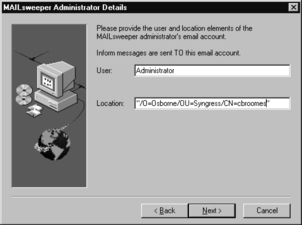
Enter the company name, NT Domain, and administrator e-mail account in the Administrator Details screen (see Figure 11.28). Click Next.
Select any of the command-line anti-virus tools displayed in Figure 11.29. Click Next.
Once all the installation options are selected, they are displayed on the Installation Ready screen as shown in Figure 11.30.
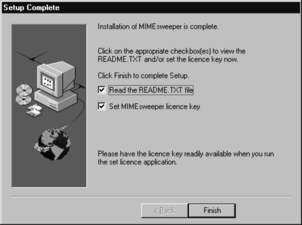
At the end of the installation, the license program is launched (see Figure 11.31).
Configuration
Configuration of MAILsweeper after installation is not usually necessary. However, we can change its settings by editing the configuration files that MAILsweeper uses (see Figure 11.32). MAILsweeper relies on five text-based configuration files to determine its functionality. The files are the Logging configuration, Mail configuration, Packaging configuration, Post Office configuration, and Validator configuration.
Specific Settings
MAILsweeper can be configured to work with SNMP as well as the command-line anti-virus utilities listed in the setup. The SNMP settings available in the SNMPTrapConfig section as shown in Figure 11.32, allow us to configure an SNMP community for sending messages about MAILsweeper status. We can use SNMP in conjunction with MAILsweeper to monitor scanning and alert administrators when inappropriate content and e-mail are detected.
Firewall and E-mail Content Scanning
Most organizations with an Internet presence use firewalls to protect the company from Internet-based attacks or intrusions. Firewalls are hardware or software devices that filter access into and out of networks based on some form of authentication. In other words, firewalls determine who gets in and out and who doesn’t. However, that is as far as most firewalls go. What if someone who has legitimate access into and out of an enterprise network is sending or receiving potentially dangerous information that might be harmful to the organization?
To combat this threat, some network security vendors create modules that work in conjunction with firewalls, by determining what gets in and out of a network rather than who. The next section introduces two popular software firewall packages on the market today.
Content Technologies’ MIMEsweeper for CheckPoint’s Firewall-1
Content Technologies’ MIMEsweeper for CheckPoint’s FireWall-1 is intended to extend the basic access-control functionality of previous versions by adding content control to the firewall. Everyone can agree the best place to stop viruses, unsolicited mail, and other inappropriate e-mail, besides at the server, is at the entry point to the network in general.
CheckPoint has incorporated a feature known as Content Vectoring Protocol into FireWall-1, which enables it to forward data that it lets through the firewall to MIMEsweeper for further validation. MIMEsweeper breaks the data down into identifiable components and scans each component for viruses and other inappropriate content. Figure 11.33 illustrates the synergy between the two applications as they work on data entering a network.
Data from the Internet enters the network and is first met by FireWall-1, which checks the authority of the sender of the data. If the data is not coming from an approved source, it is rejected. Approved data is passed on to MIMEsweeper, which breaks down and scans the data for inappropriate content. If MIMEsweeper approves the content, it is sent back to FireWall-1 with instructions to allow it onto the LAN. If the content is not approved, it is also sent back to FireWall-1, but this time with instructions to discard the data.
MIMEsweeper, in conjunction with FireWall-1, provides the following security benefits to an organizations network:
1. Prevents viruses and macros from entering or leaving the network.
2. Prevents unauthorized transmission of sensitive or confidential materials into and out of the organization.
3. Prevents downloading or uploading of harmful ActiveX scripts, Java applets, and other executable files.
4. Denies access to questionable content (for example, hate and pornography Web sites).
Axent Raptor Firewall
Axent Technologies Inc.’s Raptor Firewall is a more advanced software-based firewall than Firewall-1. It incorporates all the standard firewall attributes (for example, access lists and authentication), and it also includes its own content filtering and blocking components, without needing another third-party solution to be installed along with it. Some standard features of Raptor Firewall include:
![]() Enhanced list of built-in application-proxies, including the popular protocols that allow it to be integrated seamlessly with Microsoft networking products.
Enhanced list of built-in application-proxies, including the popular protocols that allow it to be integrated seamlessly with Microsoft networking products.
![]() Automatic port blocking to protect services running on the firewall.
Automatic port blocking to protect services running on the firewall.
![]() Anti-spam functionality built into the SMTP proxy.
Anti-spam functionality built into the SMTP proxy.
![]() Secure virtual private networking (VPN) access to authorized users.
Secure virtual private networking (VPN) access to authorized users.
Raptor Firewall works by not routing any network traffic from external sources unless the traffic is recognized as authorized. In fact, it hides network routes from external sources. This non-routing of traffic is the default state for Raptor. Even if Raptor fails, no unauthorized traffic is routed, because Raptor works to grant access based on administrator-configurable rules or policies rather than by denying access.
Most hackers will attempt their attack on a target at the application level. E-mail is the most logical place for such attacks to take place. Raptor Firewall uses application-level access controls to prevent these attacks, by scanning and filtering e-mail content for better control. When Raptor Firewall works at the application level, it also allows for the use of dedicated security proxies, to examine the entire data stream for every connection attempt. This is a significant advantage over packet filtering, which works at a lower level in the protocol stack. In effect, Raptor Firewall protects networks from a variety of traditional denial of service attacks, spoofing, and network snooping, as well as new attacks, such as malicious Java applets.
Raptor Firewall provides efficient protection against e-mail and other SMTP-based attacks. Through the use of wizards, administrators can successfully relay mail from their external SMTP servers to internal mail servers without compromising the location or security of the internal mail server. Furthermore, unauthorized SMTP relay from spam senders can be prevented by an editable list of senders to block.
Not only is Raptor Firewall efficient at denying access, it is also excellent at providing authorized access through its address redirection capabilities. Raptor Firewall can service an authorized Internet request by accepting the request from the host at an external address and transparently relaying the request to an internal host and then relaying the response back to the Internet host without the Internet host detecting that the request was serviced by an internal protected server.
Axent Technologies’ Raptor Firewall proves to be a formidable and robust security package. In addition to the numerous useful features that are provided, it is easily configurable via wizards and easy-to-use interfaces.
Attack Detection and System Scanning
Attack detection and system scanning are an integral part of network security. Administrators need to know who is attempting to break into their networks, and how to protect against such attacks. However, the perfect solution cannot always be found. This may be either a result of not having the appropriate staff or tools to get the job done, or a result of the inability to keep pace with the newest hacker technologies. In these cases it may be more prudent to employ the services of third-party service providers who specialize in network security.
Attacks
You may recall the attacks made on such sites as Yahoo!, eBay, Buy.com, Amazon, and others, which rendered these sites useless. The type of attack that these particular sites (and many others) fell prey to is known as a denial of service (DoS) attack. A denial of service attack happens when an attacker crashes a host or service so that it cannot communicate properly with the rest of the network. A denial of service attack can take on one of three forms:
![]() A host can be completely crashed by causing a kernel panic (in Linux and other UNIX boxes) or with the blue screen of death (BSOD) (Windows 98 and NT boxes). To recover from this attack, a user would have to reboot the system.
A host can be completely crashed by causing a kernel panic (in Linux and other UNIX boxes) or with the blue screen of death (BSOD) (Windows 98 and NT boxes). To recover from this attack, a user would have to reboot the system.
![]() A denial of service attack can be more selective, and disable one of its services, such as a host’s Web server or the ability to use a network interface card (NIC).
A denial of service attack can be more selective, and disable one of its services, such as a host’s Web server or the ability to use a network interface card (NIC).
![]() The third way for a denial of service attack to occur is for the attack to target elements of the network other than a specific host. In this instance, it is possible to target the network’s bandwidth, and clog it with bogus network requests. As you know, a network’s bandwidth is its connection to the Internet. By clogging it with an overwhelming volume of requests, an attacker can use all of a network’s available bandwidth, rendering it useless.
The third way for a denial of service attack to occur is for the attack to target elements of the network other than a specific host. In this instance, it is possible to target the network’s bandwidth, and clog it with bogus network requests. As you know, a network’s bandwidth is its connection to the Internet. By clogging it with an overwhelming volume of requests, an attacker can use all of a network’s available bandwidth, rendering it useless.
One additional type of DoS attack that you should be aware of is the distributed denial of service (DDoS) attack. This attack consists of distributing the attack across several hosts. The DDoS is usually coordinated among numerous individuals, and it is difficult to trace the attack’s origin. This particular type of attack needs four key elements to be successful: the attacker, a master node, one or more daemon nodes, and a victim.
With the distributed denial of service attack, the host does not communicate directly with the victim. Instead, the host is the administrator of a network that is made up of master and daemon nodes. The attacker has the ability to control one (or many) master nodes, and master nodes have the ability to control several (up to dozens) of daemon nodes. Those daemon nodes are then directed at the victim. The end result is a barrage of data, causing the targeted host to crash.
As you can imagine, such attacks cause corporations to lose hundreds of thousands of dollars. When the means of revenue of any given corporation, such as eBay or Buy.com, is Internet traffic (e-commerce), shutting that Internet site down for a day results in an enormous loss in revenue. However, to the attacker, this type of attack offers several key benefits. Using the distributed denial of service, one single attacker can use literally hundreds of systems to attack a victim. There are few organizations that are prepared to deal with that kind of Internet traffic. Most companies would fall victim to such an attack. Even the strongest of networks is not protected. This type of attack makes it very difficult, if not impossible, to trace back the attack to the originator.
The DDOS attack represents not only potential lost income for an organization, but it could be a precursor to another serious problem. The DDoS attack could be a precursor to an attack that would place highly sensitive company documents in places where unauthorized users can find the information readily available to them. There have been instances when a DoS attack was the first step in a well-developed plan to infiltrate a company’s network and obtain secure data. It is highly recommended that as a follow-up to this chapter you research software that is used for DDoS attacks. There are numerous packages that are readily available to be downloaded from the Internet. The majority of the software packages used for DDoS attacks contain the master and daemon components discussed throughout this section.
DoS attacks are not new. As you may remember, the Melissa Virus, the Love Letter virus, and many other viruses caused a denial of service. These virus attacks also had one other element in common with the more widely known DoS attacks (Yahoo!, eBay, etc.)—all of these attacks were completed using the same method. One host directly communicates with another and is able to crash the victim by sending data the victim cannot handle.
DDoS attacks are becoming more and more common in the current technical environment, for numerous reasons. The ease of installing most operating systems (OSs) and applications bears some responsibility for network attacks. Most OSs imply that they will auto-configure, when in actuality they use default settings, making it easy for an attack to occur. In most instances, networks are based on a single OS and/or hardware platform. The single OS and/or hardware platform solution makes it easier to maintain an organization’s network, but it also makes the organization more vulnerable to attacks. An additional factor contributing to DDoS attacks becoming more common is increasingly complex software (complexity can lead to source code problems that are easy for hackers to exploit). Many software manufacturers release software prior to full life cycle testing, which is another easy target for hackers to use to break down source code and infiltrate. Add inexperienced users as well as overburdened IT professionals, and you have the makings for a mess.
Real-time, Third-party Services
An alternate solution for IT departments who deploy virus-protection and network-security measures is to use real-time third-party security service providers. The network security industry has developed to the point where there are companies that specialize in various areas of network security, such as content control, access control, or virus protection. We will examine the services offered by two leading providers, Evinci and Securify.
Evinci
We have examined in detail various methods and tools to protect our messaging infrastructures from attack by viruses, spam, and other inappropriate e-mail content. However, we do not necessarily have to implement these measures ourselves. An easier (and sometimes less costly) way of securing enterprise networks is through the use of third-party service providers. With all of the different types of attacks that can happen to an organization from an external source, via the Internet, having your current security evaluated by a third party may be a cost-effective business decision. If you are doing business over the Internet, you need to do everything possible to ensure that your security is air-tight. One third-party service provider is Evinci, Inc. (www.evinci.com). Evinci’s area of focus is providing security to customers who conduct business over the Internet. They provide network and Internet security protection, through an assessment process that is designed to determine the actual level of security currently available within your organization. Through a five-step methodology that includes assessment, planning, implementation, education, and maintenance solutions, Evinci is able to determine an organization’s Internet security needs and work proactively against Internet security attacks.
Securify
Securify’s primary business concern, much like Evinci, is security services. Securify (www.securify.com) works with e-commerce businesses to ensure the security and integrity of the network, maintaining the balance between control, ease of accessing information, and privacy. Securify performs product evaluations for potential and existing clients.
For an Internet security solution, Securify offers a Public Key Infrastructure (PKI) service. PKI is one of the cryptography methods developed to protect data exchanged between computer systems, and is described in detail in Chapter 1.
When working with an organization to develop a security solution, Securify assesses the applications, if any, which would most benefit from a PKI solution, and develops scalable certificate policies, practices, and procedures.
Securify offers an Internet security resource center called Packet Storm (www.packetstorm.securify.com). Updated hourly, Packet Storm is one of the most current databases of security information; it provides information on network assessment, vulnerability analysis, review of code, security research, and incident response. Packet Storm provides an Assessment area, where users can find exploits and tools that give them a better idea of what their own systems vulnerabilities are. The site also provides a Defense area, which is a resource for monitoring and security tools. A large portion of the Packet Storm database is dedicated to Papers—this section of the database contains documentation that is helpful for finding answers to usability questions. In addition, their magazine section includes information that has appeared in electronic publications. It’s an extensive and useful data center for information gathering. The site is packed with useful information, and I recommend that you take a look at it.
Summary
The threats to organizations on the Internet are becoming more deadly and sophisticated on almost a daily basis. There is always some new virus or new variant of the last highly destructive virus that needs to be combated and neutralized. In this chapter we examined various methods of securing our enterprise networks against Internet-based attacks. We discussed the latest phenomenon of ActiveX and Java viruses. We evaluated popular anti-virus, content-filtering, and attachment-scanning software by installing such products as Trend Micro’s ScanMail, McAfee’s GroupShield, and Content Technologies’ MIMEsweeper/MAILsweeper. We configured them to work on Microsoft Exchange Server 5.5 SP3, our messaging platform of choice, as well as on the leading software-based firewall, Checkpoint’s FireWall-1. We also briefly discussed methods of securing our networks through the use of software-based firewalls and third-party service providers.
Best practices dictate that the ideal place to defend against attack is at the entry point to the LAN—firewalls, routers, and servers. In this chapter we covered methods for doing it ourselves and suggested third-party vendors we would use to secure our networks for us. E-mail protection and network security have taken a more aggressive place in the business and technology arena. As the Internet continues to become more accessible to everyone, we must be careful to always implement security that matches the depth of the threats to private networks.
FAQs
How do I know whether implementing server-side content filtering and attachment scanning is financially feasible?
When you factor in the cost of lost productivity, extra hours spent by your IT staff evaluating the scope of the problem and determining the correct solution, not to mention the actual cost of information leaked or lost to attacks on your network, it should not be hard to determine whether implementing a solution saves money in the long run.