

Solution examples and design methodology
IBM FileNet Content Manager (P8 Content Manager) can be used for the implementation of a large spectrum of applications that vary from small departmental systems to large enterprise systems running in a complex environment and integrating with several other systems. In this chapter, we describe common P8 Content Manager solutions, each illustrating P8 Content Manager’s features and capabilities. In addition, we introduce the design methodology that guides you from the Enterprise Content Manager (ECM) strategy definition through deployment and administration planning. The methodology is used as the structure for the remaining chapters of the book.
We describe the following topics:
– Policy document management process
– Invoice archiving
– Email archiving
– Insurance claim processing
– Social Enterprise Content Management
2.1 P8 Content Manager sample solutions
In this section, we present five common P8 Content Manager sample solutions:
•Policy document creation
•Insurance claim processing
•SAP invoice archiving
•Email archiving
•Training material development
Each solution demonstrates how you can implement P8 Content Manager to solve enterprise content management challenges using a different approach.
The following different approaches are available for the implementation of an ECM system:
•Simple stand-alone content management application
•ECM system integrated with the line of business (LOB) application
•Archiving solutions
•Social ECM solutions
Typically, a mix of the approaches is used in organizations based on the needs to meet the business requirements and challenges.
The policy document creation sample solution demonstrates a simple document management solution with check-in check-out capabilities and security. The insurance claim processing sample solution demonstrates the integration and record management capabilities of P8 platform. The SAP invoice archiving solution demonstrates the SAP archiving and high availability capabilities of P8 platform and intelligent document recognition (ICR). The Email archiving solution demonstrates the archiving and compliance capabilities of the P8 platform. The social ECM sample solution demonstrates the social features of the P8 platform.
|
Note: The solutions we present here are simplified versions. In actual installations, the solutions are often more sophisticated than what we describe here. We simplify the scenarios and their solutions for ease of reading and understanding. The important point from this section is to get an idea of what P8 Content Manager can do to help solve your business problems.
|
2.1.1 Policy document creation
In the first P8 Content Manager solution, a team of authors, reviewers, and managers is responsible for updating policy documents. Those documents define the organization guidelines. Goals must be rigidly reviewed, and all workers must always have access to the current policy information. The following flow is for the events of this use case:
1. The author creates a new document for revision and assigns a minor version number on the documents.
2. The reviewers and authors collaborated in this document and adding minor versions of the document.
3. The approver approves the final revision of the document and checks in the document as a major version.
4. The major version is available now to all users based on their permissions and security is applied to the document as the final approved version of the document.
This P8 Content Manager solution is implemented with the following features:
•Content versioning, including major and minor versions
•Document access controlled by role-based permissions and dependency on document lifecycle status
•Check-in and check-out capability
Figure 2-1 illustrates the implemented document revision and approval process using P8 Content Manager.
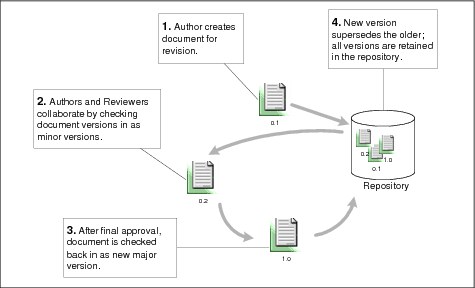
Figure 2-1 Document revision and approval process
Solution description
This solution uses P8 Content Manager features without additional programming. In the design, policy documents are stored in the repository where they are available to all users for reference.
Each policy document goes through a document lifecycle with multiple states. In this implementation, the states are minor and major versions. A minor version is a draft document; a major version is a completed document that has been approved and released. A security policy is implemented to define the security that applies to documents in the major version state and those in the minor version state. Minor versions can only be viewed and modified by authors, reviewers, and approvers. They are invisible to general users. All users can view major versions, but only authors, reviewers, and managers can modify them.
For simplification and to reflect the majority of actual solutions, this sample solution does not include document retention. When implementing a document revision solution for your environment, you must address your document retention requirements and include them in your solution implementation as necessary.
2.1.2 Processing insurance claims
In this sample P8 Content Manager solution from the insurance industry, the company policy governs how claims are processed. The main system of records for this solution is the insurance company claim processing system and the P8 Content Manager is used as the content repository together with the IBM Enterprise Records for compliance.
The following flow of events is for the sample insurance claim processing solution:
1. A new claim is opened in the Claim Management application and the claim ID is communicated to the customer.
2. The claim management application will invoke a service in the ECM repository, populate all claim-related metadata, including claim ID, propagating the proper retention policy based on the claim type.
3. The claim-related documents arrive from different sources and may include electronic documents, email, electronic forms, and paper documents.
4. Paper documents will be converted to an electronic format and send for processing.
5. Using Datacap optical character recognition (OCR)/intelligent document recognition (ICR) capabilities, the claim number will be extracted from the electronic document and the documents will be stored in the ECM system. If the claim number cannot be found in the electronic documents, an exception process will be initiated through the ECM system to the Claim Management system.
6. After the document is filed into FileNet Content Manager, a corresponding record object will be created and placed under the IBM Enterprise Records record folder where retention will be aggregated on the claim records folder.
7. A task will be created within the Claim Management application triggered by the document release in the repository.
8. The integration between the Claim Processing application and IBM ECM will allow users to access, view, load, and link the documents to the claim case throughout the Claim Processing lifecycle, according to their established permissions. Also, the ECM system using the Content Federation will present content from other repositories, such as policy documents to the authorized users.
9. The document metadata is updated from the Claim Management application as the claim moves through the process.
10. The claim close event from the Claim Management application will trigger a service request to ECM to start the retention process.
11. After the claim case record and all associated documents will be ready for disposition, the service request will be sent to the Claim Processing application to automatically dispose of structured data in the same time as unstructured content.
This P8 Content Manager solution is implemented with the following features and components:
•Document scanning and character recognition
•Integration with LOB application
•Active content event actions
•Records management
•Content Federation Services
Figure 2-2 illustrates the implemented insurance claim processing solution using P8 Content Manager.
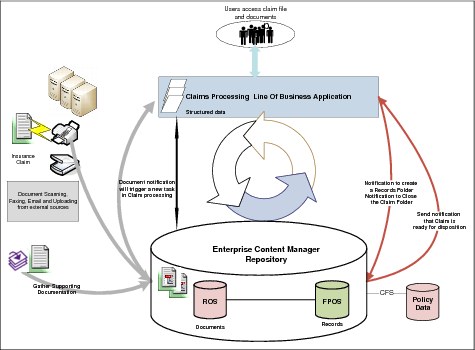
Figure 2-2 Insurance claim processing
Solution description
In this solution, the active content is the insurance claims. The content is moved through a business process in a series of steps implemented in the LOB application (claim processing application).
From the claim processing application, a records folder is opened in the ECM system for each new claim. IBM Datacap converts the paper documents received from the client to electronic documents and stores them into the ECM repository. Datacap also extracts the metadata from the documents using ICR and automatically indexes the documents without user interaction. A record is declared for the documents that are stored in the ECM repository and the retention period is set based on the business requirements. The LOB application utilizes the features of the ECM system through the integration capabilities of the P8 Content Manager. The documents can be retrieved and viewed from different sources that are transparent to the business user.
2.1.3 Archiving SAP invoices
This is a cross-industry sample P8 Content Manager solution. Large organizations have to process a large volume of paper-based invoices. They have to place them in a system to track and control invoice processing.
A major challenge is the large volume of information that must be processed, indexed, and stored. Another challenge is the requirement for fast response and high availability necessary for the accounting department. To address these challenges, the solution includes load-balanced server farms to achieve high ingestion and response rates.
The flow of events for this sample solution follows:
1. Upon invoice arrival, the paper invoices are scanned using IBM Datacap.
2. Data from the invoice is extracted using IBM Datacap OCR/ICR capabilities.
3. Extracted data is verified against the SAP system. If data cannot be verified, an exception handling process is launched.
4. The invoice is created in the SAP system.
5. Invoice images are stored in the P8 Content Manager indexed with the invoice information and linked to the SAP transaction.
6. An invoice’s documents can be retrieved and viewed directly from the SAP system
7. Authorized users can search for the invoices using IBM Content Navigator and view the invoice images, as well as directly use SAP to view invoices associated with the transaction record.
This P8 Content Manager solution is implemented with the following features and components:
•IBM Datacap
•IBM Content Collector for SAP
•P8 Content Manager security
•P8 Content Manager server farm
•High performance search operation (load balancer)
•Scalability
Figure 2-3 on page 24 illustrates the implemented invoice processing solution using P8 Content Manager.
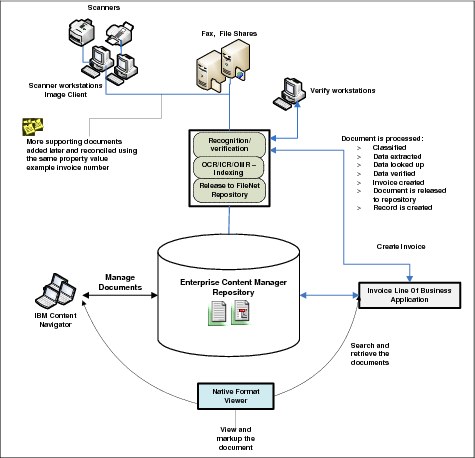
Figure 2-3 SAP archiving solution
Solution description
This solution utilizes the following P8 Content Manager components and capabilities: IBM Datacap Invoice Capture, IBM Content Collector for SAP, and server farms.
IBM Datacap for Invoice Capture
IBM Datacap for Invoice Capture is a solution for accounts payable automation. Extract invoice data using OCR to reduce manual data entry. Apply advanced validation database lookups, calculations, and checksum to verify accurate data recognition. It stores the data and document to IBM Content Manager.
IBM Content Collector for SAP
IBM Content Collector for SAP integrates Filenet Content Manager with the SAP system. It improves the efficiency of SAP business processes by linking content to SAP transactions. It supports both SAP Archivelink and SAP Netweaver Information Lifecycle management protocols.
Server farms
For applications with high-volume loads, P8 Content Manager can be configured as a server farm. A server farm employs multiple servers to multiply processing power. In this solution, three P8 Content Manager servers are deployed to spread the document processing load across three separate P8 Content Manager servers. A load balancer spreads the incoming load evenly so that even a high ingestion rate, the load does not overload a single server. In a similar fashion, searches and document retrieval requests are managed by a load balancer on the call center side.
Server farms can also be configured in highly available configurations. Refer to Chapter 3, “System architecture” on page 37 for more details.
2.1.4 Email capture for compliance
This solution addresses recent industry concerns about legal discovery of email messages. It uses IBM Content Collector for Email and P8 Content Manager to capture emails directly from email server journals.
This P8 Content Manager solution is implemented with the following features and components:
•IBM Content Collector for Email with rule-based automation
•IBM Enterprise Records
Figure 2-4 on page 26 illustrates the implemented email capture for compliance solution using P8 Content Manager.
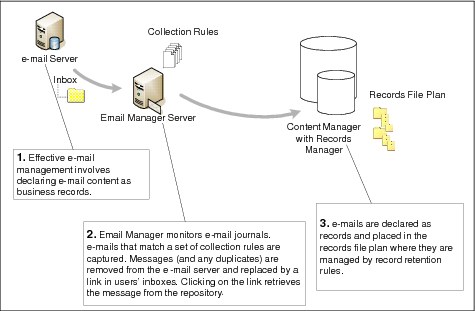
Figure 2-4 Email capture for compliance
Solution description
This solution uses IBM Content Collector to monitor an Exchange Server Journal (IBM Lotus Notes® and other email systems are also supported). The journal contains a copy of all incoming and outgoing messages. IBM Content Collector for Email monitors the journal and searches for messages that meet a set of conditions or rules. Common conditions include:
•Messages that contain particular keywords
•Messages to or from a particular set of addresses
•Messages that pertain to compliance issues raised by the legal department
Messages that meet the set of conditions or rules are treated this way:
•The message is captured and added to P8 Content Manager.
•Duplicates of the message (if the message was sent to multiple recipients) are identified. Only one copy is added to the repository.
•Selected messages based on business rules (for example, emails to a specific address or containing a combination of keywords on the subject or mail body) are classified and declared as an official record subject to legal retention rules.
•In the user’s mailbox, the message is replaced by a stub. When the user clicks the stub, the message is retrieved from the repository and displayed in Outlook as expected.
•When the records retention period expires, the content is destroyed with no ability to restore it.
2.1.5 Knowledge management through collaboration
In this sample solution, an organization needs to develop and manage the internal training material. They need a solution to provide relevant training information to users according to their job description function and preferences. Organization employees need to collaborate over the training material by starting discussions following updates of a training material and rate the training material. The flow of the events for this use case follows:
•Authors create training material that might include documents, videos, and audio and stores it in Content Manager.
•Training material becomes available in a Lotus Connections community for the subject matter experts’ (SME) review.
•SMEs that are participating in that community are collaborating over the material where they can put comments, add tags, and provide feedback over the content.
•After the training material is finalized, the content becomes available to user communities that require training.
•In that community, users can add comments and view activity streams, download counts, and recommendation counts.
Figure 2-5 on page 28 illustrates the implemented knowledge management through a collaboration solution using P8 Content Manager.
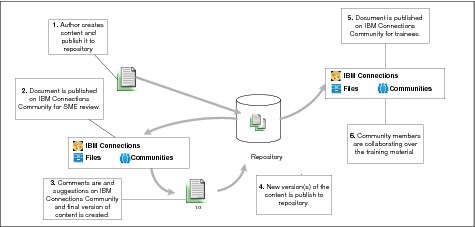
Figure 2-5 Knowledge management through collaboration
Solution description
In this solution, the content that is managed is the training material of the organization. Training material can include documents, presentations, video, and audio. Content authors and SMEs need to collaborate during material preparation. Trainees need to follow the training material, put in comments, and view activity streams, recommendations, and the number of downloads.
In the first step, content is stored in Content Manager along with metadata and is available through the IBM Connections community for review by the SMEs. Using IBM Connections, a SME can add comments, put in recommendations, monitor the activity steam over the content, and upload new versions in the Content Manager repository. When the review process is completed, the finalized content is available on the user community.
Using IBM Connections, a trainee can view new content, add tags, comments, and recommendations, and follow the content. Content Manager provides activity feeds, recommendation counts, download counts, and tag searching, enabling users to locate training content and find relevant content in their social network.
2.2 Design methodology
In the previous section, we present four common P8 Content Manager solutions implemented at client sites. In this section, we introduce the methodology for creating the solution designs to help you with your implementation process.
From our experience, successful design and implementation follow a well-thought-out, repeatable process. Enterprise content management projects are complex, involving the installation, configuration, and customization of a mixture of hardware, software, network resources, content analysis, and process policy. The projects often cross organizational boundaries and involve teams from the IT department, legal department, Quality Assurance department, and others. An organized approach is necessary for a successful implementation.
We outline the recommended design methodology that has been used by many IBM Enterprise Content Management architects in the field and has been applied successfully in many client situations.
The process starts with a top-down approach:
1. Define the ECM strategy.
2. Define the requirements.
3. Create a functional design document from the requirements.
4. Design the systems architecture.
5. Design the P8 Content Manager repository.
6. Design the document security model.
7. Build applications and user interfaces.
8. Create the system and application testing plan.
9. Create a deployment plan.
10. Plan for administration and maintenance.
The remaining chapters of this book address the concepts and recommendations for each step in the methodology. When you design a P8 Content Manager solution, we recommend following the chapters in the book and using our suggestions and recommendations to meet your design challenges.
2.2.1 Defining ECM strategy
The main purpose of an ECM strategy is to establish the decision making principles and standards for the use of content as a business resource. To develop an ECM strategy, a thorough understanding of the business and the underlying information needs, how to structure the information resources to support those needs, and how to manage and maintain the architecture is required.
ECM strategy definition is a critical step in the process of the development of an ECM system. Typically, in the ECM strategy definition phase, you need to define the high-level requirements of the organization for the ECM system and lay out a plan for the successful adoption of the ECM system by the organization. The ECM strategy defines the organization’s vision for the ECM system and consolidates the different departments’ requirements and directions.
The ECM strategy will establish a common picture of the ECM future that clarifies the business units’ directions, aligns actions to the correct directions, and coordinates various initiatives. The organization needs to have a clear understanding and establish an ECM vision to pursue core ECM elements and any adding advanced capabilities.
In our experience, the following elements of the ECM strategy are key:
•ECM standards
•Security standards
•Content taxonomy and classification
•Content inventory
•Change management plan for the adoption of the ECM system
ECM requires a change and people management approach that will support every business group and requires a managed business process change and large-scale adoption of the technical solutions. The fundamental challenge of rolling out an ECM system is that it requires the active involvement and participation of all users.
Effective ECM strategy eliminates information silos, enables the foundational ECM elements, such as the enforcement of the information governance and support for business requirements, and enables the integration and automation of business processes.
2.2.2 Requirements analysis
The first setp is to gather and analyze the requirements for the development of an ECM system. From our experience, ECM systems evolve and grow according to the organizational needs and business challenges. So, the requirements gathering is an iterative process. It is important to start the requirements gathering as early as possible and aligning those requirements with the ECM strategy. If you miss a critical requirement, the entire system might be flawed. It is important to gather input from all groups that will be involved in using, building, testing, training, or operating the system.
For each iteration of requirements gathering, create a requirements document. As a milestone goal, create and review this document and obtain the appropriate sign-offs on the document.
A requirements document needs to include the following information:
•Functional requirements - What must the system accomplish?
•Non-functional requirements - To what must the system adhere?
•Hardware - What standards or limitations apply to hardware specifications?
•Software - What standards apply to software specifications?
•Security - What are the security requirements for the system?
•Retention - What are the retention requirements for the system?
•Usability - What ease of use standards apply?
•Performance - What levels of response times are required?
•Continuity - What service levels are expected?
•Documentation - What training and documentation are required?
Typically, requirements gathering is an iterative process. You will start with the functional design, revisit the requirements, complete the requirements analysis, and then revisit the functional design. This process continues until you feel confident that all known requirements have been identified and addressed.
The enterprise content management illustration in Figure 2-6 helps in structuring the discussion among the various people involved in understanding what functionality the solution requires to solve specific business problems.
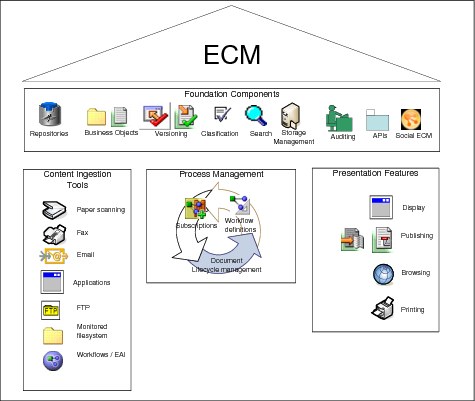
Figure 2-6 A simple input and output diagram to assess functional requirements
For example, based on Figure 2-6 on page 31, you can discuss the following points to help you gather functional requirements:
•How will content be ingested? Options might be paper scanning, fax, email, other applications, FTP, monitored file system, or workflows.
•What are the content and workflow management requirements? Considerations can be indexing, validation, the addition of document management, security, binding of documents, usage of entry templates, and check-in and check-out features.
•What are your presentation and delivery management requirements? Consider content-based search, publishing, and browsing requirements; printing needs; display needs; Simple Mail Transfer Protocol (SMTP) sends; and the requirement for the usage of search templates.
•What indexing terms will be used to identify and retrieve information?
•What interfaces are required with existing systems to move information between systems?
•What is the lifecycle of the document and how does it fit as part of the business process?
•How will auditing requirements be satisfied?
•How will security or information confidentiality requirements be met?
•How will the information be searched across the enterprise?
•What is the minimum required to describe the metadata?
•How long will the documents need to be stored in the system?
•Who will be responsible for the destruction of the documents?
•What type of storage will be required?
Working from the requirements analysis to a functional design is probably one of the biggest challenges in your project. This activity requires extensive experience and solid knowledge of the P8 Content Manager product. We address this topic in more detail in Chapter 13, “IBM FileNet Content Manager solutions” on page 427.
As you read through each chapter of this book, remember that each chapter provides many of the best practices for a number of scenarios but in a generalized way. Use these best practices and recommendations within the context of the actual functional requirements for your solution; do not apply them as is.
2.2.3 Functional design
A functional design shows the components of the systems and describes how each component handles information objects. The functional design needs to match the user requirements and be presented to the project team for review.
Functional design will define the overall solution architecture, such as taxonomy, and the folder and data structure design. A solution model is created to support sample use cases. Analysis and design are crucial in the whole development cycle. Any mistake in the design phase can be expensive to solve in a later stage.
As mentioned in 2.2.2, “Requirements analysis” on page 30, the functional design step is often part of an iterative solution design process. Chapter 13, “IBM FileNet Content Manager solutions” on page 427 covers this topic in more detail.
2.2.4 System architecture design
The system architecture design (sometimes called a logical design) lays out the setup of the hardware and software components. The system architecture is a blueprint for system infrastructure construction. A logical design shows servers (both hardware and software), network connections, storage units, and database instances. When creating your system architecture design, consider the following elements:
•Server topology
•Network (LAN and WAN) topology
•Scalability and continuity
•Virtualization
•Shared infrastructure
•Capacity planning
•Performance
Although system architecture can be derived from nonfunctional requirements, it can be influenced by the functional requirements. Often, system architecture is dependent on certain decisions made in the functional design.
During this phase, the major architectural decisions must be documented. Architectural decisions are significant because they might directly or indirectly determine whether a system meets its nonfunctional requirements, such as software quality attributes. Harmonizing the architectural decision-capturing process simplifies reusing and learning from architectural decisions made on previous projects. Architectural decisions need to be identified, made, and enforced systematically.
For more information regarding system architecture, business continuity, and capacity planning, refer to the following chapters:
2.2.5 Repository design
The repository design is the key design step in a P8 Content Manager project. It specifies the number, type, and structure of the solution repositories. It defines the object classes that will be stored in the repositories, including the metadata, folder storage, security descriptors, and retention requirements for each type of content object.
The repository design typically is tightly linked to the functional design. It affects and is affected by the security design. The repository design must be carefully synchronized with the application and security design.
For more details, refer to Chapter 4, “Repository design” on page 81.
2.2.6 Security model design
You can enforce security through repository design and application design. A dependency exists between application security constraints and the security mechanisms applied on the repository. P8 Content Manager offers a rich set of options for developing a security model. Our suggestion is to utilize the repository security features as much as possible.
ECM Security Framework controls access to the information from the initial classification through to disposition, covering all aspects of information lifecycle management, and simplifies and speeds up ECM planning and execution.
Determine which users and groups will have access and the levels of access that these users and groups will have. Create these users and groups in the authentication provider if they do not exist there.
The security model for ECM needs to be clearly defined and it needs to be understood that security access for documents that are transitory records might differ from the documents that will become business records.
The Security Framework needs to address the principles for security and user roles mapping between different ECM modules. For more details, refer to Chapter 5, “Security” on page 151.
2.2.7 Application design
Application design is mainly derived from the functional design and must be synchronized with the repository and security design. The application design includes user interfaces and custom software components. The design presents the details of application features and functionality and specifies the application programming interface (API) that developers will use to construct the application.
ECM solution design needs to support reusability by creating or using existing shared components. For more details, refer to Chapter 6, “Application design” on page 191.
2.2.8 Test planning
Testing is a required step before the deployment of an ECM solution to the production environment. There are many types of tests that a solution has to pass in order to be a successful one.
The most common types of tests are:
•User Acceptance Tests (UAT)
•Regression tests
•Performance tests and load tests
•Backup and recovery tests
User acceptance tests verify that the system meets the functional requirements described in the functional design document.
Regression tests verify that the functionality of the solution is not affected after the implementation of new features or the resolution of a defect. It is important to have a full set of regression tests for the ECM solutions and we suggest that those tests are automated.
Performance and load tests verify the system responsiveness and stability under a defined workload. It is a best practice to develop performance tests and execute them before any major release is put on the production environment.
Backup and recovery tests verify that the system can be successfully recovered in case of disaster. You need to perform at least one recovery test a year to verify that your backup and recovery plan is still valid.
2.2.9 Deployment
Deployment is defined as the methodology to move a designed solution from development to production. When planning for deployment, issues related to release management, change management, testing, and the steps for the actual move need to be considered. It is important to plan for deployment as early as possible, especially at development time, to address many of the challenges that might arise in this area.
For more details, refer to Chapter 9, “Deployment” on page 271. Also, refer to Chapter 11, “Upgrade and migration” on page 371 for upgrade and migration information.
2.2.10 Maintenance planning
Maintenance is related to operational aspects, such as system monitoring, backup and restore, and other tasks. Capacity planning might also be considered as part of your maintenance planning activity.
It is a best practice to have four environments where one of the environments, User Acceptance Testing (UAT), is a replica of the production environment. The replica includes version, configuration, topology, and data to ensure that the applications and any upgrades are sufficiently tested before being deployed to production.
For more details, refer to Chapter 10, “System administration and maintenance” on page 315. Also, refer to Chapter 12, “Troubleshooting” on page 387 for troubleshooting information.
2.3 Conclusion
In this chapter, we introduced five typical use cases where Content Manager can be used. Those use cases are simplified and the actual use cases are much more complicated. The purpose of those examples is to make a quick introduction of Content Manager features and capabilities. The detailed solution building blocks and how they are used for the implementation of those use cases are described in Chapter 13, “IBM FileNet Content Manager solutions” on page 427.
We also described the proposed methodology for the implementation of an ECM system using Content Manager. That methodology is used as a structure for the rest of the book.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
