Business Building Blocks
Keywords
VDML; Capability unit; SOA; CBA; CBA infrastructure; Service unit
A fundamental requirement for agility is the ability to configure existing components with minimal addition or adaptation to meet changing business needs. This requirement is addressed by VDM through the definition of sharable capability methods that can be individually modified or improved and integrated in multiple contexts to deliver related but diverse products or services. We define these business-oriented design concepts and relationships as a capability-based architecture (CBA).
The CBA is based on a service-oriented architecture (SOA)—the building blocks are integrated as services, but the CBA builds on the information technology of SOA to include the elements of business design that are addressed by VDML—collaborations, activities, deliverable flows, personnel, resources, values, and so on. From a business perspective, the services of CBA are collaborations—people and machines working together for a shared purpose. A business is a network of collaborations.
A capability method is a collaboration that specifies the activities and roles that provide a specific application of a capability as a service. A product is produced by a value stream which is a network of capability methods that delivers value to a customer or internal recipient. Capability methods are sharable services, and thus each capability method may participate in multiple value streams.
Capability methods are bundled into capability units. A capability unit is an organization unit that manages the capability methods along with the shared personnel and other resources that are applied by the capability methods. The capability unit may be responsible for a more general capability—such as machine maintenance, order management, warehouse management, field services, and product assembly—supported by the capability methods. A capability unit is implemented as a service unit at an operational level. A service unit implements the capability methods of the capability unit as business processes along with other administrative and supporting capabilities that maintain, adapt, and improve the capability unit implementation.
Management of resources by a capability unit results in sharing of resources for all of the value streams served by the capability methods of that capability unit. This sharing achieves economies of scale and other benefits from the elimination of duplication.
In this chapter, we will first expand on the characteristics of a CBA and its relationship to the more detailed operational business design. We will then focus on multiple aspects of value stream modeling. Next, we will consider issues related to management of capability units and expand on the requirements of operational business design. Finally, we will describe key components of the supporting information technology infrastructure.
Capability-Based Architecture
A CBA is the basis for design of all business aspects of the agile enterprise, including administrative services and business management. However, of primary concern is the design of the business to deliver products and services and the ability to quickly adapt to new market demands and opportunities. Consequently, our focus will be on the impact of CBA on lines of business and delivery of products and services to external customers.
In the following sections, we will discuss further the aspects of a CBA, particularly capability methods, capability units, value streams, and the operational implementation.
Capability Methods
A capability method is a collaboration that specifies the roles, activities, and deliverable flows to provide a particular service. This includes engaging other capability methods as supporting services. In general, a capability method receives deliverables from a requesting collaboration as input to its service and returns results. A capability method may also send and receive deliverables with other collaborations through stores.
Capability methods may have different degrees of structure, ranging from unstructured to fully structured with an activity network. The degree of structure depends on the level of detail in the model and the repeatability of the activities in the collaboration.
Many capability methods delegate to other capability methods. For example, a capability method can define the overall activities to produce a product. Such a capability method is then not generic but is specific to the product. The activities of that capability method, for the most part, will delegate to other capability methods where some may still be specific to the product while others may be generic, shared by other product lines. There may be multiple levels of capability methods delegating to other capability methods. At each level, a capability method should be limited in scope to confine its activities to a particular capability and delegate to other capability methods where a different capability is required, usually involving different personnel or key assets. The most elementary capabilities are the most sharable and stable.
Capability Units
A capability unit is an organization unit that is responsible for a bundle of capability methods and associated personnel, resources, facilities, and information that together provide various applications of a more general capability. A capability unit is depicted in Fig. 3.1 to include a bundle of capability methods and assets. Each of the capability methods provides a specific application of the capability.

A capability unit presents capability offers that identify the capability methods that the capability unit supports. There may be multiple capability units (organizations) that have some of the same capability offers. Consequently, when an activity requires a capability for delegation, one or more capability offers identify capability methods and associated capability units to provide the needed capability. The selected capability unit fills the activity role to provide the capability method along with the personnel and resources that are required.
Capability units are important because a capability usually involves some key assets that can support multiple capability methods. A capability unit implementation will also include additional services that support management and control of the bundle of capability methods. A capability unit is implemented as a service unit at the operational level of design detail, discussed later.
For example, consider a shoe-repair shop as a capability unit. It has skilled shoe-repair persons, machines, materials, and ways to track the repairs of individual deliverables (shoes). There are several different capability methods for repair of stitching, replacement of heels, replacement of soles, and refinishing. Each of these services will utilize some or all of the shoe-repair shop assets. There will also be ancillary services such as cancellation of an order and change of an order. Additional support services based on other capabilities (that may be outsourced) will be used by the repair shop for accounting, purchasing, payroll, and marketing.
Note that a capability unit may manage all of the associated capability methods and all of the assets used by its capability methods, or it may manage some of the assets and delegate management of capability methods and some resources to suborganizations. In such a case, the parent and subunit relationships will align with the enterprise management hierarchy discussed in Chapter 10.
Capability Library
In a VDML capability library, capabilities are classified in a taxonomy. The nodes of the taxonomy are capability categories and capability definitions. The capability definitions for capability methods are leaves of the taxonomy tree. The capability library also contains capability definitions that identify capability units. A capability method definition can be associated with more than one capability unit, and a capability unit definition may identify multiple organization units that manage the general capability.
The capability taxonomy is not the same as the enterprise management hierarchy, and it is not the delegation tree of capability methods delegating to other capability methods. It provides a classification structure that brings similar capabilities together, and supports identification of existing methods that may meet a business need.
Value Stream
Collaborations can define roles, activities, and flows of deliverables. Deliverables flow between activities within a collaboration, and they flow between collaborations via delegation and stores. Capability methods provide sharable services that may be engaged in different contexts, and they may engage other capability methods as services. The network of collaborations (primarily capability methods) and their activity networks that deliver a particular product or service are called a value stream. A value stream is distinguished from a value chain by the level of detail that includes activities, deliverable flows, integration of shared capabilities, and value contributions.
The VDML model of a value stream includes the network of value contributions of activities to support value proposition(s) for the end product of the value stream. The value stream is thus the key structure for design and analysis of the work to deliver a product or service. An enterprise typically will have multiple value streams to deliver products or services to customers as well as multiple value streams to deliver products or services to internal recipients.
In a CBA, capability methods will be shared by multiple value streams. The capability library supports identification of the same or similar capabilities for potential consolidation. For development of a new or changing value stream, the capability library supports identification of capability methods to provide needed capabilities.
As a value stream is analyzed or a new value stream is developed, new capability methods may be added to the capability library. A capability method will be associated with a capability unit as the organization responsible for management of the capability method and associated assets. Alignment of capability methods with capability units and the capability unit position in the management hierarchy may be refined later to optimize sharing of assets and improvements.
Modeling Value Streams
VDML represents the configuration of multiple value streams using shared capabilities. The values delivered by each value stream can be traced to the capabilities that contribute to each value. The values contributed by each capability can be traced to its activities and any capabilities that it engages. From a VDM value proposition perspective, the enterprise is a network of value streams, each receiving values from its participating capabilities.
From an enterprise perspective, there are value streams delivering products or services to customers and others delivering products or services to internal consumers. The existence of a distinct value stream will depend on differences in the associated line of business, the character of the product or service, and the characterization of a unit of production.
The value chain of a line of business or product line will define major stages in the delivery of a product or service starting with product and market research and product development and potentially ending with customer field support services. The focus of a value chain is the general sequence of major operating stages that lead to delivery of value to an end customer. The stages are decomposed, potentially to several levels, to identify key capabilities affecting customer value. A value chain is used as the basis for definition of stages of a product lifecycle in Chapter 9.
A value stream, as used here, is more detailed and robust in the specification of a network of capabilities. It includes the flow of deliverables, the roles of participating people and organizations, the activities of participants, and the value contributions of activities. The entire value chain for a product or service could be modeled as a single value stream, but it is more appropriate and more manageable to define separate value streams for each of the primary value chain stages, particularly when the rate of production is significantly different. Value propositions should be developed for each of these value streams.
For example, product development has a long lifecycle as compared to a production process, and it contributes distinct values. The same value stream model for product development may be applied to the development of multiple products, so it is useful to consider this effectively as a supplier to the production process. At the same time, delivery of a new product specification is different from delivery of revisions to an existing product, so it may be appropriate for revisions to be modeled as different value streams although they may share many of the same capabilities. In addition, product development may have different value streams for different types of products. In any case, the value contributions of a product development value stream can feed a production value stream and ultimately impact the value proposition for an end customer.
A customer may receive a product that is a package of two or more relatively independent products like a set of furniture or appliances. In such cases, each of the products may have a value stream and value proposition with a composite value proposition defined for the package received by the consumer.
Implementation and management of a CBA requires modeling and transformation of existing processes and responsibilities. For an existing, silo-based enterprise, the production value streams for a line of business are likely intertwined in a large, complex process. The value stream will have embedded variations for the differences between the products or services of that line of business. In another LOB, there may be separate processes for each product or service with duplicated capabilities.
CBA requires identification of distinct capabilities, consolidation of equivalent capabilities for sharing, and the composition of value streams, using shared capabilities.
In this section, we will discuss approaches to development of a value stream model in VDML. We will focus on a single value stream as delivering a product or service to an end customer, but the approach is fundamentally the same for any value stream. Generally, analysis for an enterprise will start with a mainstream production operation that delivers end-customer value as a potential source of significant business value. As the enterprise agility matures, the scope of analysis will expand to include additional value streams, such as product development, and support services.
We will start by considering two complementary approaches to development of a value stream activity model: (1) top-down and (2) bottom-up. We will then consider identification and consolidation of sharable capabilities, followed by refinements to deliverable flows. Then, we describe development of the associated value contribution network. Finally, we will consider modeling the value stream in electronic commerce.
Top-Down Analysis
Top down analysis starts with the selection of a value stream and develops successive levels of detail. This may be based on an existing value chain model, or an industry framework, or both. We will consider each of these.
Value Chain Basis
Fig. 3.2A illustrates a conventional form of a hypothetical value chain used in strategic planning for an established, made-to-order product. This value chain depicts broad capabilities and an implied transition through those capabilities to deliver customer value. Each of the high-level capabilities is broken into supporting capabilities.
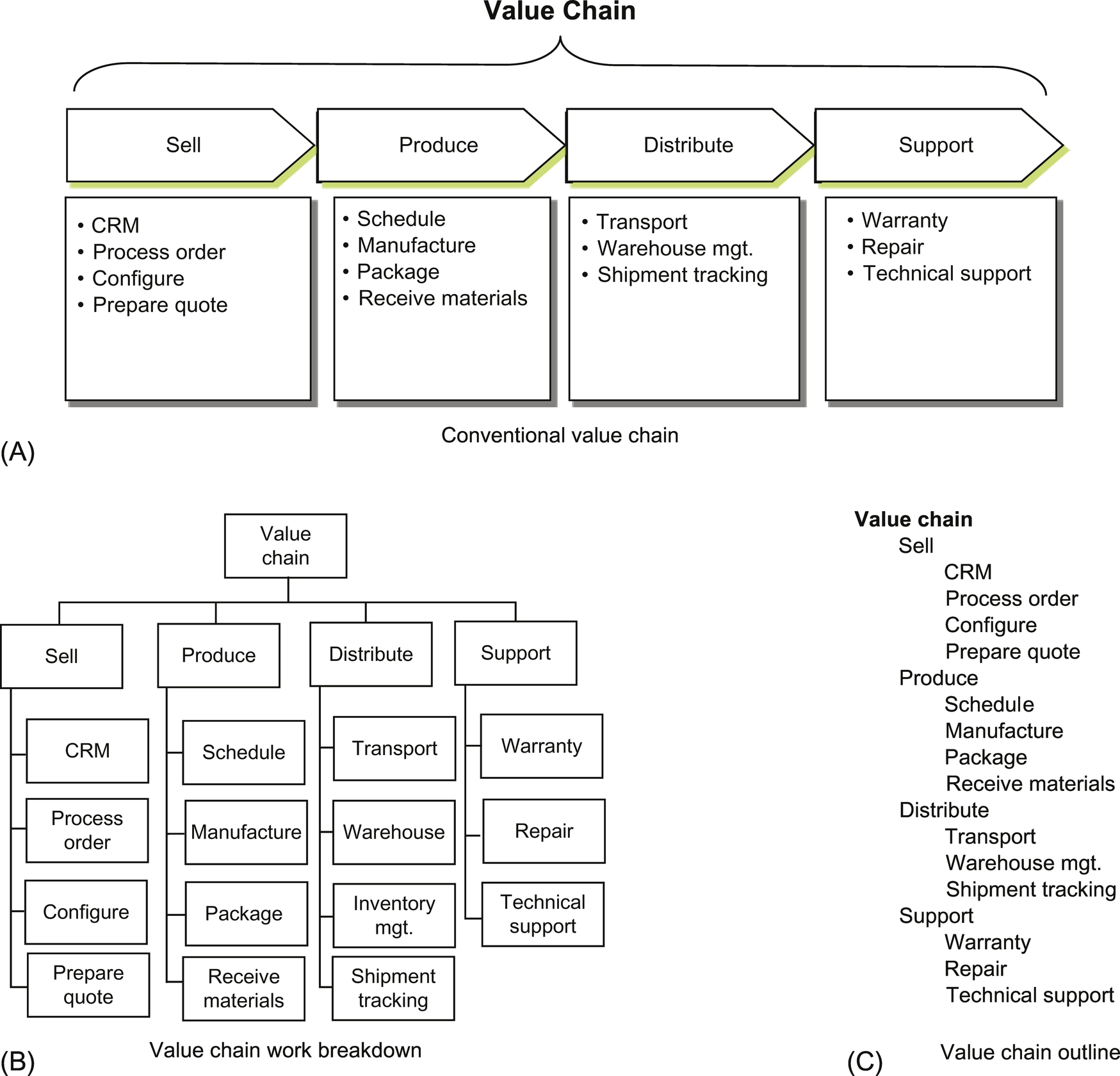
A value chain analysis focuses on the contributions of value for the end customer. This example business begins with sales and proceeds through product production, distribution, and support. The customer support capability functions somewhat independently, occurring when there is a reason for some action in the field. Consequently, it is appropriate to model this as a separate value stream. The value chain decomposition is sometimes described as a process model, but it is at most a high-level abstraction of the processes that actually deliver customer value. A value chain is not intended to be a process model but rather an abstraction of the flow of value contributions. Nevertheless, at times it is helpful to think in terms of a process breakdown to help identify the required capabilities.
It may be useful to use alternative forms for the value chain decomposition. The conventional value chain model is equivalent to a work breakdown structure, as depicted in Fig. 3.2B. Fig. 3.2C illustrates the same model in the form of an outline. The outline form is often a more convenient way to capture additional levels of detail, since it is easier to expand multiple levels. Regardless of the form, a conventional value chain model, if available, is a useful starting point for analysis.
The decomposition of the value chain identifies potential capabilities that may be implemented as sharable services. On further analysis, we may find that there are additional capabilities at each level that are less crucial but nevertheless necessary. The addition of deliverable flows will help identify the need for additional capabilities.
Starting from a value chain perspective helps focus on what the product line does rather than who does it. This helps ensure that the definition of capabilities is driven by the business of the enterprise and avoids repackaging the same old way of doing business. As capabilities are identified, they should be defined in the VDML capability library. As the number of capabilities increases, it is useful to start using the capability categories to group similar or related capabilities together and to start identifying capabilities that could be consolidated.
Industry Frameworks
Industry frameworks provide another approach to top-down analysis. Industry frameworks provide prototypical designs of enterprises in a particular industry, based on a consensus of industry representatives. The frameworks tend to define characteristic breakdowns of functionality and business processes that may align with capabilities. They may provide more detail and objectivity than a business-specific value chain. Of course, each enterprise may be different due to individual circumstances or manner of doing business, and these differences may be a basis for achieving competitive advantage in certain markets.
One advantage of an industry framework is that the capabilities will tend to align with implementations of capabilities in commercial enterprise applications and outsourcing services. Use of an industry framework does not mean that a well-defined conventional value chain should be abandoned; instead, together they define more insight for the definition of shared capabilities.
An industry framework may include an enterprise data model. The role of a consistent, enterprise logical data model is discussed in Chapter 6. Use of a framework data model should be strongly considered early in the development of a CBA for a particular enterprise, for two reasons. First, development of a good enterprise logical data model is a very large and time-consuming undertaking that will delay the CBA transformation and exceed the cost of acquiring a model. Second, the framework data model is more likely to be consistent with commercial software systems and outsourcing services as well as industry standards, so data exchanged between services have fewer data transformation problems.
The enhanced Telecom Operations Map (eTOM, http://www.tmforum.org/browse.aspx?catID=1648) from the Tele Management Forum (TMF), illustrated in Fig. 3.3, is one widely recognized industry framework. It is described as a business process framework but is similar to a capability map. It represents the processes of a typical telecommunications service provider. The TMF has defined a companion enterprise data model called shared information and data (SID, https://www.tmforum.org/information-framework-sid/) that supports the enterprise logical data model requirement discussed in Chapter 6.
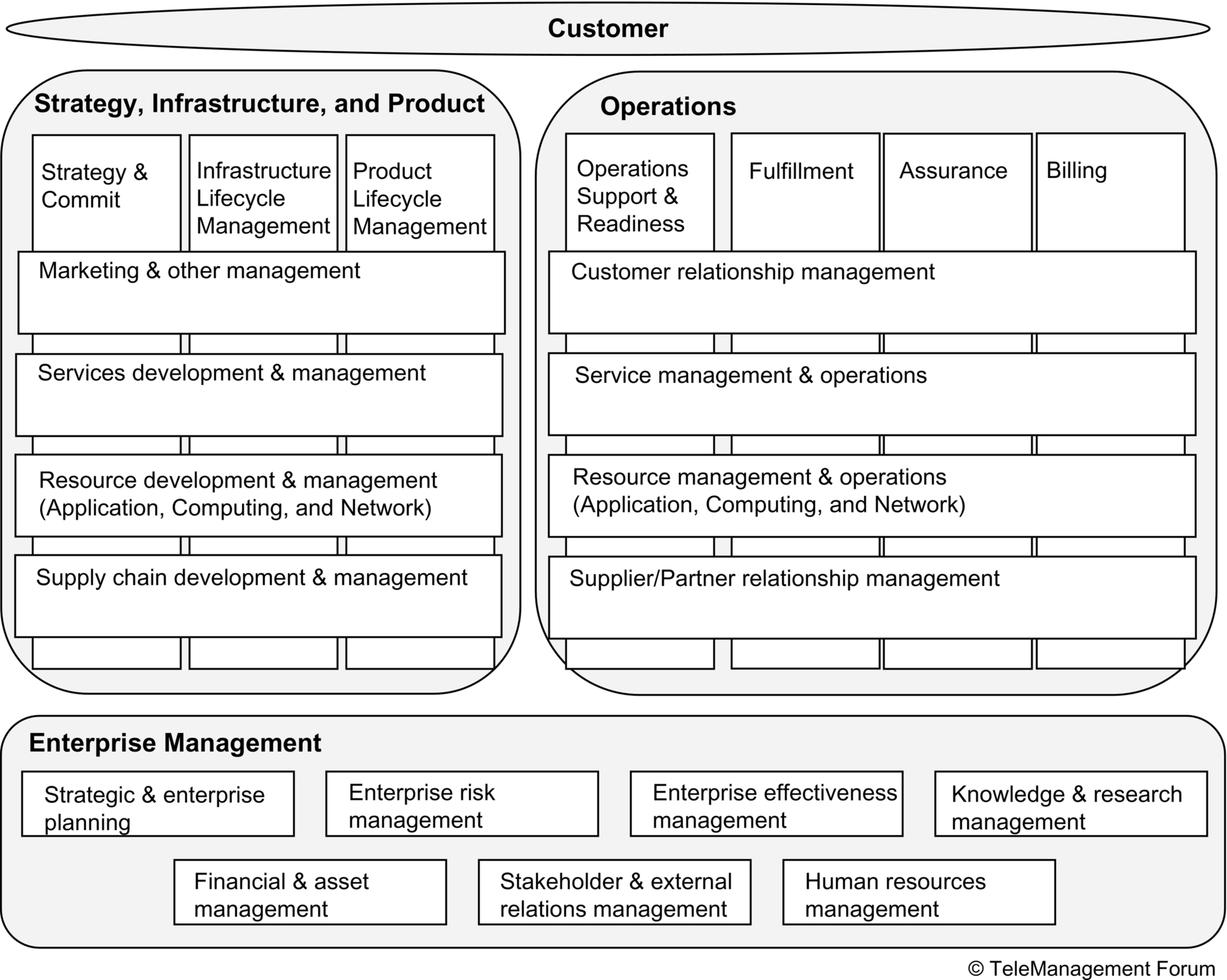
Fig. 3.3 illustrates the eTOM framework at the enterprise level. There are three major process categories: (1) operations; (2) strategy, infrastructure, and product; and (3) enterprise management. These are described as level-zero processes.
The operations category reflects the primary business operations. The strategy, infrastructure, and product segment defines processes for changes to the business; that aspect of agile enterprise architecture is addressed in Chapter 9. The processes in enterprise management are typically viewed as support services—those processes that are part of managing the enterprise, such as finance and human resources, but are not a direct part of delivering customer value.
The operations and the strategy, infrastructure, and product categories of Fig. 3.3 are each divided by vertical and horizontal partitions described as level 1 processes. The vertical partitions reflect functional capabilities. The horizontal partitions reflect primary enterprise objectives that cut across the functional capabilities. For example, customer relationship management (CRM) is an enterprise objective that requires participation and support from each of the functional capabilities. These objectives are optimized operationally in the operations segment and optimized from a business change perspective in the strategy, infrastructure, and product segment.
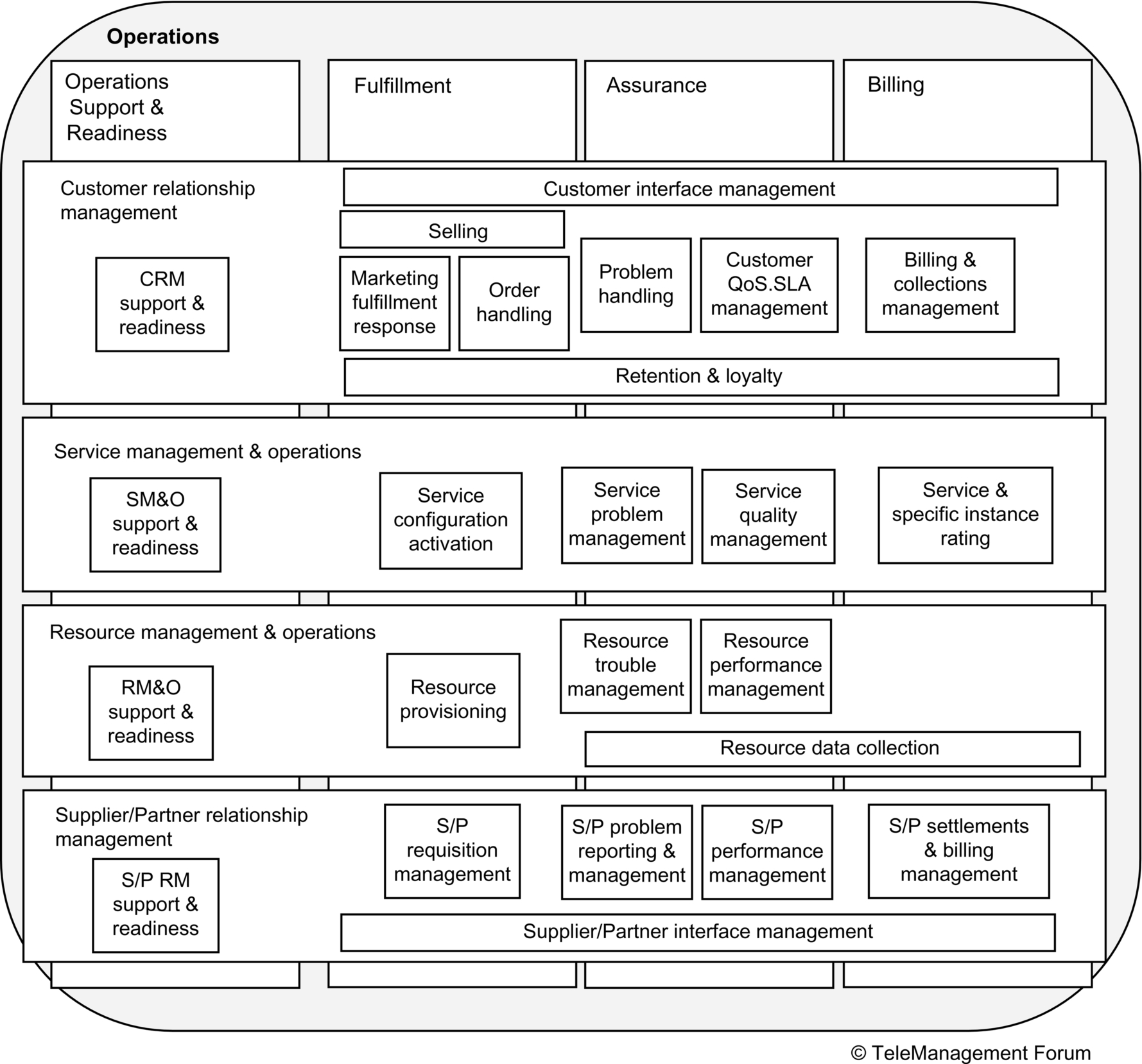
Fig. 3.4 shows more detail for the operations processes. These level 2 processes are shown at the intersections of the vertical and horizontal level 1 processes; each is in both a horizontal and a vertical level 1 process within the eTOM specification. Each of these level 2 processes is further detailed in subprocesses. Note that some level 2 processes span level 1 processes; these are effectively shared capabilities that may represent either shared work management service units or capabilities that can be further broken down to define shared operational capability units. A similar breakdown is defined for the strategy, infrastructure, and product level 1 processes. More detailed breakdowns also exist for the enterprise management processes. eTOM process models provide additional insights on capability requirements and the contexts in which they are used.
Value Stream Decomposition
As a first step in developing the detail of a value stream, a delegation tree should be developed based on the value chain and/or industry framework. Each node in the delegation tree is a potential capability method containing an activity network where certain activities delegate to the next lower level of capability methods.
Fig. 3.5 illustrates a delegation tree in which the solid-line arrows represent the request-response relationships from capability methods requesting services to those providing services. The dotted line represents the value stream—the sequence of execution of the capability methods as they contribute value toward the end product. This is a simplified portrayal, since a value stream usually will have branches that are executed concurrently, like tributaries to a river.
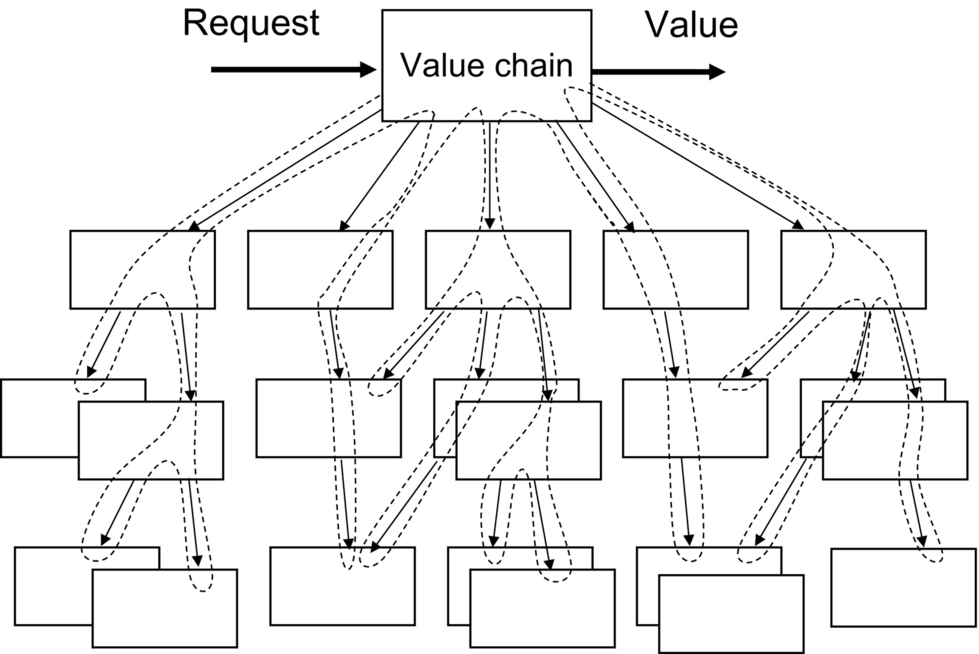
Note that some of the capability methods are engaged more than once in the same value stream. The context in which they are engaged will likely affect the measurements of values contributed. If the value stream activities are sequential, then the time from the request to the delivery of customer value is the sum of the times it takes each capability method to contribute its value. The cost of the product or service will be the sum of the costs of executing each capability method.
It is useful to develop a delegation tree in an outline form as suggested by Fig. 3.2C. Text can be added below each of the capability name headings to describe the capability, along with the required input deliverable(s) and expected output deliverable(s).
The next step is to develop activity networks for the capability methods. This is detail that would be difficult to manage in the outline form of the delegation tree, so, at this point, we should start building the value stream model in VDML.
It is useful but not essential that the capability definitions in the value stream outline be transferred to the VDML capability library. An initial taxonomy should be developed using capability categories. This will help identify potentially shared capabilities which can then be identified by the same name in the different contexts in which they are used. The capabilities of capability methods must be leaves in the taxonomy tree. If convenient, related capability method definitions can be grouped under capability unit definitions. Note that the capability taxonomy is not the same as the delegation hierarchy.
Initial detail of the activity network for each capability method can then be developed based on the deliverables. Starting with the output deliverable of the value stream, work backward to identify the last activity of the top-level capability method that produces the end product. That activity must either be performed by a person or application/machine, or it must delegate to a supporting capability method. The output of a delegating activity becomes the output of the engaged capability method, and the input to the delegating activity must be the input to the engaged capability method.
Note that the name of a delegating activity depicts what is done from the perspective of the containing capability method. This may or may not be the name of the capability method that is engaged by that activity.
As deliverable flows are identified, the business items that flow as deliverables can be identified and posted in the VDML business item library. Note that a sequence of activities that incrementally add value to a business item can be represented as having the same business item as inputs and outputs rather than creating unique names for the business item in each deliverable flow. Sometimes it will be necessary to add an activity to create a deliverable that is needed as input to another activity.
An activity can only be performed by an individual performer or collaboration. If the activity requires multiple people, then the activity must engage a separate capability method with roles for the multiple participants.
Bottom-Up Analysis
Bottom-up analysis complements top-down analysis by examining the activities of actual business processes to discover activity networks and capability methods.
Traditional businesses usually have few shared capabilities as part of the delivery processes, and thus the capabilities are embedded and not identified in the processes. As a starting point, the work necessary to deliver a product or service is essentially the same whether the model is a traditional, product-line silo, or a value stream. The difference is the composition of a CBA value stream from sharable capability methods. Additional differences may emerge as the value stream is refined.
The top-down analysis should identify candidate value streams and existing processes that perform equivalent work. These processes are then the subjects of bottom-up analysis. The top-down and bottom-up analyses will eventually overlap and be reconciled to produce a more robust model.
This section uses a hypothetical example to illustrate how an analysis can use a spreadsheet to capture information about a current process segment with embedded capabilities and transform that process segment to a segment of a value stream that engages a sharable capability method.
Activity Data Capture
An analyst will start at the end of a process and trace the deliverable flows back through the string of activities and deliverable flows that produce the end product. The analyst should consider the purpose of the model and decide which inputs are of interest in a management-level model of the value stream. Then the analyst must determine if any alternative output deliverable flows are of interest and, if so, trace the output deliverable flows forward to develop the full activity network. Fig. 3.6 illustrates a resulting activity network segment arranged in approximate chronological sequence. Full chronological sequence is not useful where there are concurrent flows. It is most useful to keep together activities that occur in sequence.
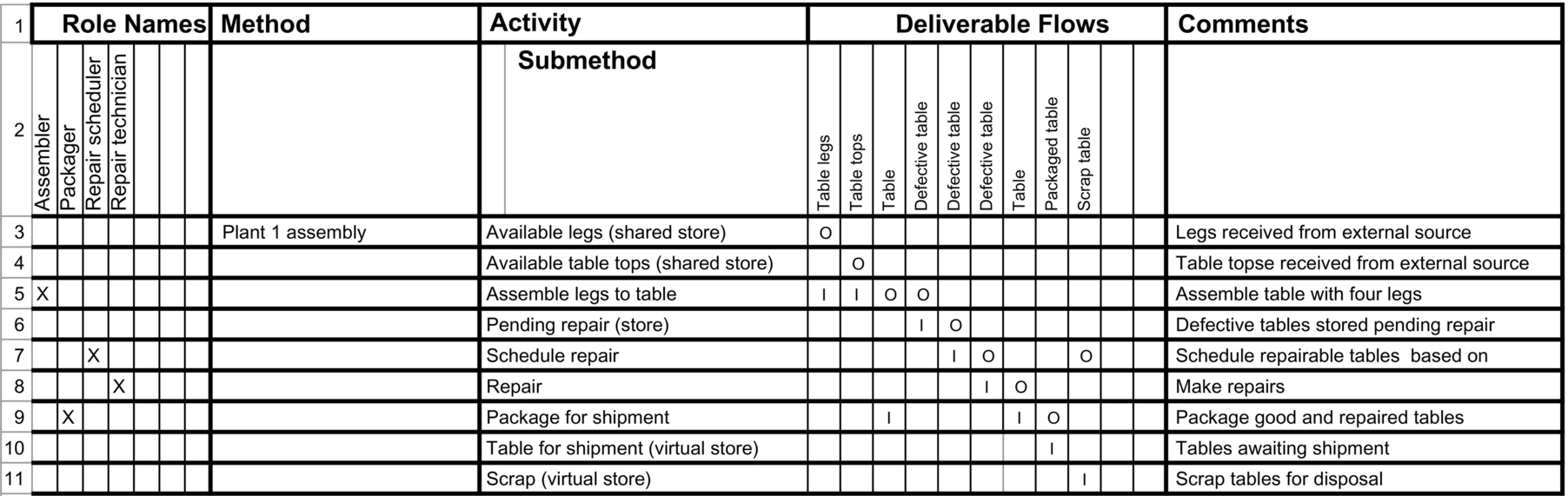
Note that a value stream in the VDML model does not represent the flow of individual units of production but represents the paths of deliverables as fractions of production. As a result, gateways in an operational process will be represented as the flows of percentages of production in VDML. In VDML, variations in production rates are buffered by stores, and repeated execution (iteration) will be represented either as a capability method engaged for each iteration or activity value contributions that represent repeated performance of the activity (or group of activities). We will illustrate the analysis with a hypothetical process in which table legs are assembled to table tops and some defective tables are repaired.
In the spreadsheet of Fig. 3.6, the first group of columns identifies role names that are associated with activities. The role of each activity is indicated by an “X” in the intersection of the role column and the activity row. Note that role names need only be unique within a process/capability method. Some roles may be identified as appropriate in multiple methods and should be given the same names. It will likely be necessary to consider the general issue of role names later in the VDML role definition library or an equivalent table may be developed in a spreadsheet, organized in a taxonomy.
The second major column is for method/process names. At this stage of analysis, there is only a segment of one process being considered. Some rows will be added in the next step of analysis.
The third major group of two columns has “Activity” overlapping with “Submethod.” At this stage only the activity caption is relevant. Each of the detail rows contains an activity or store name.
The fourth major group of columns is labeled “Deliverable Flows.” The name in each column is the name of a business item that flows from a source to a destination activity. There may be multiple deliverable flow columns with the same name indicating a flow of the same business item. The source activity is designated by an “O” for output, and the destination activity is designated by an “I” for input. So in one deliverable flow column, the source and destination activities are designated as output and input. The last column is for comments.
In the detail of the example, the first two activities are identified as shared stores. This means that the inputs to these stores come from other processes, presumably owned and operated by other organizations. Where inputs are directed to these stores, the stores appear as virtual stores because the actual stores are in the process we are analyzing. Stores are usually owned by the recipient as an input buffer.
Note that the activities in rows 6–8 deal with repairs, and row 11 deals with the tables that are scrapped. The good table output of row 5 is an assembled table that goes directly to “Package for shipment” in row 9. The defective tables (second output) go to the activity of row 6, which is a store, holding defective tables for repair. A store is appropriate since the production rate for good tables is much higher than the repair rate, and defective tables will occur at random times.
The final outputs of this process also go to stores: the tables for shipment and the tables for scrap disposition. Note that these are designated as virtual stores. This means that they represent stores that exist elsewhere, presumably owned by the organizations responsible for processing shipments and disposition of scrap.
Process Transformation
Fig. 3.7 illustrates the above example, transformed to create a repair service as a potentially sharable capability method. Rows 6–8 have been moved to the bottom of the spreadsheet, separated by a double line and given a method name of “Repair Service.” In their place (between rows 5 and 9) is a submethod call to “Repair Service.” The call has input designated “D1” for “delegation,” and outputs designated “R1” and “R2” for the results for the repaired and scrapped tables.
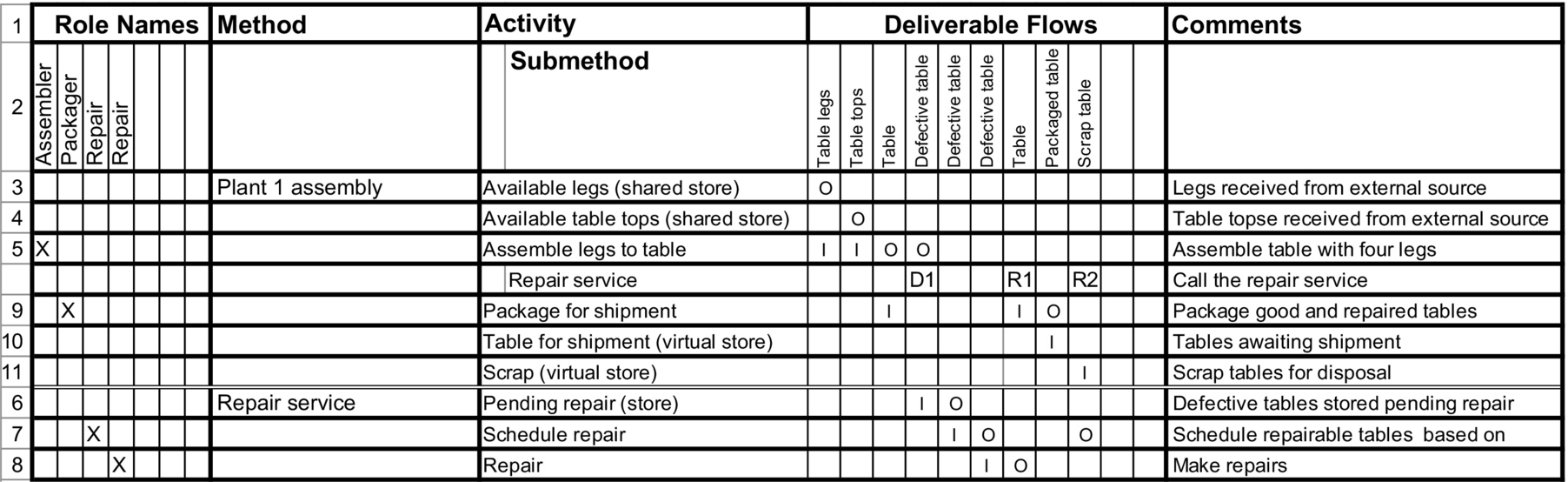
In the Repair Service method, line 6 has an input of “I1” to correspond to the delegated input, “D1,” and lines 7 and 8 have outputs O2 and O1, respectively, corresponding to the results of R2 and R1 of the above call.
The numbering of inputs and outputs is necessary so that the Repair method can be called by other processes without the deliverable flow columns of the call being aligned with the input and output columns of the Repair method. Each caller will refer to the input “D1” and the outputs “R1” and “R2.” In this way sharable capabilities can be pulled out of larger processes and engaged in multiple contexts.
Each major process can be modeled with a spreadsheet. As subsequent processes are analyzed, opportunities may be recognized for using some of the already-defined sharable methods. Note that there can be additional levels of delegation, for example, if the Repair method was substantial, it might have sharable submethods pulled out as well.
This approach separates the activities and shared methods from the responsible organizations. This can be important for taking internal politics out of the restructuring analysis. Later, the organization structure for management of shared capabilities can be considered with a better understanding of the scope of sharing and the similarities of sharable capabilities.
Capability Reconciliation and Consolidation
Based on this spreadsheet-based analysis, capability methods can be defined in the VDML model. The capability methods from this bottom-up analysis of actual processes should overlap with the top-down analysis of capability methods. The capability names and deliverable flows of business items will help reconcile these two perspectives.
The capability library must be refined to provide appropriate classifications using capability categories. This will help identify capability methods that are similar. In some cases, a capability identified in the top-down analysis will be the same capability method identified differently in the bottom-up analysis. The details of the two must be reconciled to define one capability method with an appropriate name.
Capability methods that are classified as similar must be analyzed to determine if they should be consolidated as one shared capability method. Those that cannot be consolidated but share core elements should be evaluated as different services of the same capability unit. Note that it is possible that the same capability unit and associated capability methods could be provided by multiple organization units if required by considerations such as data residency (import/export regulations) and access constraints.
This consolidation achieves two important objectives: (1) it identifies multiple contexts in which a shared service unit can be applied and (2) it reduces the explosion of detail, since the detail of a consolidated service unit needs be expanded only once.
It may be necessary to modify the definition of some capability methods to consolidate them as shared services. In some cases, calling collaborations may need to be modified to provide a more appropriate scope or objective for a capability method so that a capability method can satisfy the needs of multiple, delegating activities.
Deliverable Flow Refinements
At this stage, we will focus on refinements to the deliverable flows starting with planning percentages, considering synchronous versus asynchronous interactions and modes of process optimization.
Production Planning Percentages
When a capability method has more than one output, a planning percentage must be assigned to each output. If they are alternative outputs, then the percentages should add to 100%. If they are concurrent outputs, then both percentages should be 100%. In rare cases, the outputs may be alternatives part of the time and concurrent part of the time, resulting in a total greater than 100%. These percentages may be different in different scenarios when they depend on product mix or random occurrences such as defects.
The statistical measurements associated with elements of a collaboration method are based on a single unit of production, and the cumulative value measurements can be affected by these percentages. In particular, planning percentages are a concern when deliverable flows branch or merge. For example, when flows have a concurrent branch, the cumulative cost of production should be allocated to the branches. When alternative flows are merged, the cumulative cost should be the weighted average share of the cumulative costs based on the planning percentages of the incoming flows.
At this stage, values can be assigned for testing purposes and to indicate the relationships between multiple outputs.
Synchronous Exchange
At this stage of analysis, most of the links between capability methods have defaulted to synchronous delegations.
A synchronous exchange is a simple request-response. The requester's action is suspended pending a response from the recipient. In VDML, this is represented as delegation by an activity to engage a capability method as a service. Only capability methods can be engaged in this mode.
Fig. 3.8A depicts a synchronous flow (for illustration only). The dashed boxes depict capability methods. Activity A engages capability method N. In capability method N, activities B and C are performed and a result is returned to activity A.

Delegation enables the capability method to be engaged in different contexts with different inputs where the activity network does not depend on the source of the request. The measurements of the capability method will be dependent on the input and thus the context in which it is engaged. These measurements will be reflected in the value contributions associated with the response. The measurements of an engaged capability method are based on a unit of production of the engaged method. The measurements returned from the delegation are then adjusted by the calling activity to reflect the share of production of that context that is delegated to the engaged method.
Asynchronous Exchange
Not all interactions are synchronous. An asynchronous exchange occurs when a source activity sends a deliverable but does not wait for a response.
In VDML, a virtual store in the sending collaboration receives the deliverable flow, and the corresponding, shared (real) store in the receiving collaboration provides the deliverable to a receiving activity. The effects of this deliverable flow may be realized in a result received by the sender at a later time. This mode can be applied by any collaboration, not just a capability method.
The value measurements associated with a deliverable in a store must be factored into the measurements for the receiving collaboration. Essentially, each business item in the store can be viewed as a unit of production from the source collaboration, so the adjustment to measurements will be based on the number of business items from the store that represent a unit of production in the receiving collaboration. For example, tires may be delivered to a store to supply an automobile production line. Each tire is a source unit of production. However, since four tires are required for each automobile, four tires are a unit of production of the receiving collaboration. This will require adjustment of incoming value measurements.
An asynchronous exchange is depicted in Fig. 3.8B. Activity A in capability method M sends a deliverable to the virtual representation of store X. The deliverable is received by the shared (real) store X in capability method N where it can be accepted by activity B at a later time. The result may or may not be returned to method M or some other method later in the value stream via a similar link with another store.
A deliverable may be sent to and received by a store because (1) it is assumed that the receiver may not take immediate action and may be receiving similar deliverables from other sources, (2) the production rates of the source and recipient are different, (3) there are multiple sources or multiple consumers of the deliverables, or (4) the receiver should be free to determine and change how it will process the deliverable, and a shared store is a way of isolating the sender process(es) from the receiver process(es).
Generally, the shared store will be owned by the receiver. However, a shared store can receive deliverables from multiple sources and supply deliverables on demand to multiple recipients. The store should be owned by a common parent organization in the receiving management hierarchy.
A difference in production rate may also occur when the sender or receiver (or both) is operating in a batch mode. It may also occur when multiple units being received are used for each unit of the receiver's production, or only some of the units received are used by the receiver's production.
A service can be engaged asynchronously for a request-response exchange by agreement between the requester and provider. A deliverable can be sent to the provider's input store, and the provider later sends a response to the requestor's input store. However, at an operational level, this requires that the request carries the identity of the request and requester and the identity of the input store for the requester's response. In VDML, individual requests are not tracked, so it is sufficient for the production rate of the requests to equal the production rate of the responses.
A common application of an asynchronous deliverable flow (to a store) is to deliver exceptions for processing by another collaboration, for example, handling of scrap or rejection of a customer order. This has been regarded as a “side effect” flow since it initiates action not included in the response to a delegation.
Process Optimization
There are various techniques to achieve process optimization that may have implications to the value stream beyond the implementation of individual capability methods. The following are examples.
• Building to forecast vs building to order should reduce customer time to delivery
• Batch production, balancing setup costs against timeliness, and inventory costs
• Sequencing of requests as for an automobile production line, to avoid bursts of high work content at individual stations
• Sharing resources across capability methods
• Selection of operating location for utilization of special facilities or product distribution
• Sequencing work to manage priorities
• Managing rework
These factors should be considered as part of value stream design. Since they will likely impact the design of individual capability methods, they may indirectly impact other value streams or they may impact the ability to share certain capability methods. Since these factors can affect the success of multiple value streams, they should be considered from an enterprise perspective.
Value Contribution Development
Completion of the value stream requires the addition of one or more value propositions and value add elements for contributions of activities. A value proposition brings together measurements of the values that are important to customers in a market segment, and it computes a level of satisfaction for each along with an overall satisfaction level based on the relative importance of each of the value types. If there are subgroups of customers that expect different value measurements or give different weights to the values, then there should be different value propositions for these market segments. If there are market segments that buy products with different features, then it may be necessary to define different value streams that represent the flow and value contributions for the differences in features.
Each value proposition is supported by a value contribution network—the network of value adds elements that contribute to that value proposition. The following paragraphs describe development of the value contribution network. Note that a VDML modeling tool and predefined value and measurement library entries should make these operations much easier than they may appear here.
Identify Customer Values
Development of the value contribution network should start with a value proposition. For each value proposition, the value types of interest to the recipient/customer must be identified. This is the minimal set of values to be measured in the network.
Update Values Library
The value types of interest should be added to the values library if not already there. For each value type, the unit of measure must be defined. Value categories should be added to include new values in the taxonomy.
Attach Value Adds to Activities
Each activity in the value stream must be considered in order to attach value add elements for those value types of interest that are relevant to the work of that activity.
The value measurements of each capability method may be specified directly if more detail (an activity network) is not available, but in a more complete model, these measurements will be derived from the contributions of the activities within the capability method.
Insert Value Add Elements Into the Value Network
Each value add element must be linked into the value network for its value type. The value network generally parallels the activity network deliverable flows.
Assign Tentative Measures
It is useful to assign value measurements to each of the value add elements for testing purposes. These may be defined for a test scenario.
Define Value Aggregation Formulas
The formulas for aggregation of value measurements will depend on the nature of the value type and the associated share of production associated with the value add (the planning percentage of the associated output deliverable). Value measurements returned from delegation must be adjusted to reflect the share of production addressed by the requesting activity.
Refine Value Proposition
Each value proposition must be linked to the value aggregations for each value type of interest to the recipient. Note that there may be a different value proposition, with different values of interest for different market segments.
Define Satisfaction Computations
The aggregated value measurement for each value type must be translated to a customer satisfaction measurement in the value proposition. This formula will depend on the relationship between the value measurement and the satisfaction scale as well as the upper and lower bounds of satisfaction. Some value measurements may have a linear relationship to satisfaction while others may best be described by a curve. This formula is important so that changes to the model that affect value measurements will be properly expressed as customer satisfaction.
Define Weights
Weights must be assigned to each value type in a value proposition to reflect the level of interest the customer has for that value type. The default is to use the weights to compute a weighted average for overall customer satisfaction. These weights could also be computed with a formula for a nonlinear impact. For example, an “unsatisfactory” satisfaction level for a value type could be very important while a “good” satisfaction level might be of less concern.
Participation in Electronic Commerce
An enterprise will engage in electronic commerce to exchange products and services with suppliers, customers, and other business partners.
Interactive Business Relationships
Asynchronous exchanges are the normal mode for a business network exchange because the exchanges with customers, suppliers, or other business partners are not tightly coupled. The parties in a business network (collaboration) send and receive deliverables asynchronously and a party may be involved in exchanges with many different business networks (other parties). In the business network, there are not shared stores, but it is expected that the receiving activity of each party will deliver input deliverables to a receiver's internal store for processing.
In general, electronic commerce between enterprises can be viewed as a loosely coupled integration of services in much the same way that services are used within the enterprise. Suppliers in a supply chain are providing the service of delivering products to the production process and the recipient later returns payment. Banks provide a service for accepting and cashing a check, and the check submitter receives credit for the payment. Transportation carriers provide services for pickup and later delivery of packages. The primary difference between internal services and electronic commerce involves concerns about security, trust, and autonomy.
In some cases, the information exchanged might not be private and the interaction may be trivial, such as in a request for a stock quote. The service provider may not be particularly concerned about the identity of the service user, but the service user is dependent on the identity and integrity of the provider for an accurate and timely stock quote. In other cases, such as the transfer of funds, identities of the service user and service provider are both critical and the information content is highly confidential. Security considerations are discussed in Chapter 7.
Trust requires a business relationship beyond technical compatibility. Each party must be assured that the other party will fulfill its obligations. Reputation may be a factor in determining the quality and reliability of the service. This assurance still requires human participation in the establishment of business relationships. In some cases, this will be established by consortia or other general affiliations that screen members and provide assurance of good faith relationships among them. A discussion of establishing trust is beyond the scope of CBA and the scope of this book, but electronic signatures that establish legal obligations are addressed in Chapter 7.
Business Networks
VDML models business network collaborations between the enterprise and its customers, its suppliers, and its other business partners. Two different views are defined for business network exchanges: (1) value proposition exchange and (2) deliverable exchange. Note that the other parties in a business network exchange are often typical participants such as a customer of a market segment represented as a member of a community.
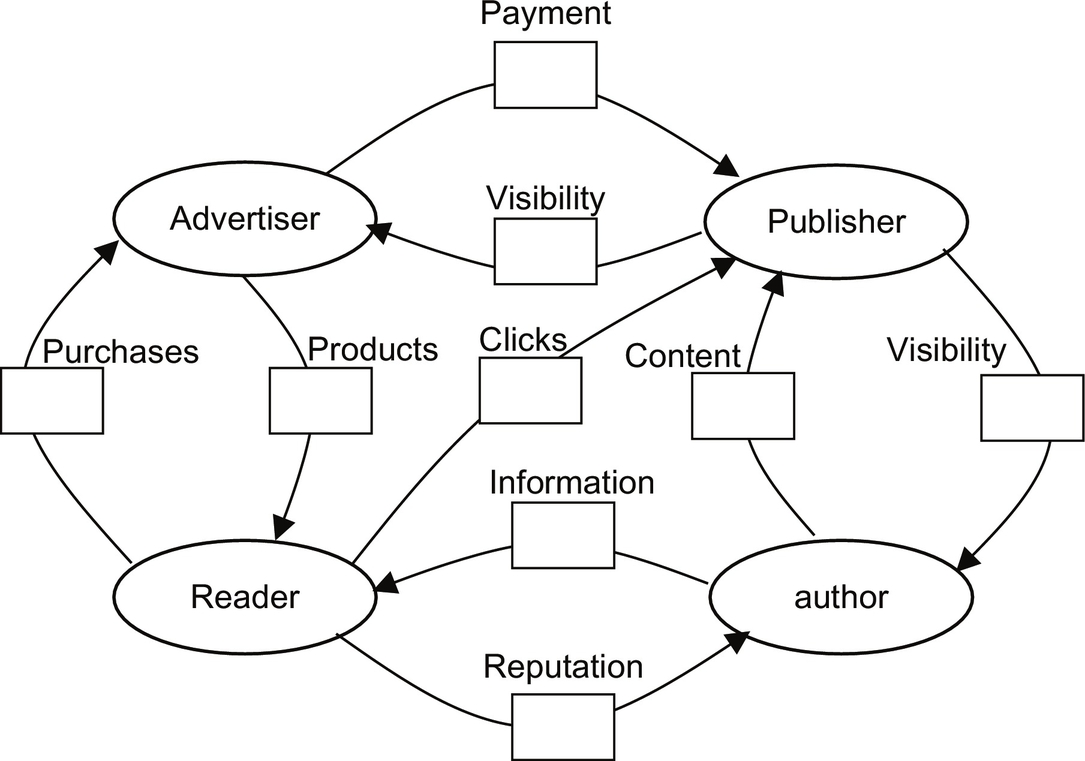
In a value proposition exchange, each party is the sender and recipient of value propositions from other party(s). Each party must perceive a net gain from the exchanges in order for the collaboration to be viable. This is useful when considering a new business model, particularly where there are multiple parties involved. For example, a blog publisher, depicted in Fig. 3.9, must ensure that bloggers, advertisers, and readers each realize some benefit from participating.
In a deliverable exchange, the focus is on the flow of deliverables. One party may deliver a product and a recipient delivers payment. However, this exchange may be more complex if it includes related deliverables such as a proposal or quote and response, a shipping notice, an invoice, and a payment. The modeler must determine the level of detail that is needed to support the business design. Note that greater detail of exchanges may be deferred to the technical, operational design of service units.
It is important to link a deliverable exchange to its supporting value stream. The end product of a value stream may be delivered by an activity of the selling party to an activity of the customer party and another activity of the selling party receives payment which is delivered to a store for processing.
The operational exchange, the next level of design detail, is usually more complex, and different activities of a party may send and receive deliverables such as changes, cancellations, status reports, quotes, and other documents.
Capability Unit Management
There are four primary aspects to management of a capability unit: (1) Capability method design, (2) management of resources, (3) management of operations, and (4) value optimization. These aspects may be all managed directly by one organization unit, or some aspects may be delegated or acquired from other collaborations.
Capability Design
The operational design of an activity network is the responsibility of an organization unit that is the capability method owner. This will be separated from responsibility for performing the capability method when there is a need for multiple organizations to perform it. For example, a budgeting capability method may be defined by the accounting organization for use by all organization units. This can ensure policy compliance, security, or operating consistency. This may limit the ability of a provider organization unit (that performs the method) to innovate and improve its operations.
Resource Management
A parent organization unit, separate from a capability method provider, may have responsibility for resource management where there is an opportunity for economies of scale or workload balancing among similar capability methods. Typically, this will be a capability unit organization. The manager of resources owns stores. Consumable resources are used from a store and replenished by input deliverable flow. Personnel and other reusable resources are obtained from pools (a specialized store). These resources are assigned from their pool when needed and released when no longer needed. Not all personnel and resources for a capability are necessarily owned by the same organization unit, but their store must be accessible by the capability methods that need them.
Operational Management
Operational management focuses on the day-to-day operation of a capability method. The operational manager is in charge of the work being done, supervises the participants, and resolves problems. Generally, this will be the capability unit that offers the capability.
Value Optimization
Optimization of a capability is based on its impact on the value streams that use it, the values it contributes, and the importance of those values to the value stream consumers. Typically, there will be a trade-off between speed, quality, and cost. For some value streams, speed may be important where cost may be most important for other value streams. Since shared capability methods will impact multiple value streams, it is important that the impact of changes be evaluated from an enterprise perspective.
Consequently, capability service level agreements should include measurements of value contributions, and consumers of a capability service should monitor compliance, particularly for those value types that are important to their value stream customers.
If a capability method uses another capability method that makes a change affecting a value measurement, the value measurement change will show up in the value measurement of the calling capability method and any methods that call it, directly or indirectly. This propagation of effect works in the VDML model, but it may be more difficult to observe in business operations. This reinforces the importance of monitoring for compliance with a service level agreement.
Capability Outsourcing
An outsourcing relationship will take a somewhat different form. Outsourcing is the use of an external entity to provide a client with external services that would otherwise be provided by an internal capability method, capability unit, or complementary set of capability methods.
Analysis of capabilities should include capabilities that are outsourced even though the enterprise does not own the elements of those capabilities. The outsourced services must be integrated with the enterprise operations—they contribute values that must be considered in the resulting value propositions. An outsourced capability can achieve greater economies of scale and may be more scalable to respond to changes in seasonal demand or market share. Capability should be distinguished from competency where a competency of an enterprise requires that the enterprise own the elements of the capability, usually for competitive advantage. A capability should not be outsourced if it is important to differentiation in the marketplace or if there is no competition between outsourcing providers.
The enterprise will not have control over the implementation of an outsourced capability and must rely on marketplace competition to control the cost and performance of the services. The typical purpose of outsourcing is to realize economies of scale and scalability that cannot be achieved within the enterprise. As the enterprise organization is transformed to a CBA, it is important to consider outsourcing as an alternative to the transformation and consolidation of existing capabilities.
The exchange with an outsourcing provider will incorporate one or more capability methods (services) into one or more value streams. The outsourcing provider can be viewed as a capability unit with multiple, complementary capability methods. Depending on the nature of the outsourced capability, the delegations may be tightly coupled, the same as for an internal capability or they may be loosely coupled, asynchronous deliverable flows.
In general, the focus will be on the service interfaces and level of service agreements. The outsourcing provider implementation will be a black box, preserving the option of the provider to change its implementation to address new business challenges and opportunities.
There may be other exchanges through business networks for management of the outsourcing relationship and payment for services. Managers within the enterprise do not control the resources or the operations of the outsourced service units. The enterprise must manage the services on the basis of a service contract, costs, and performance metrics, along with assessment of the satisfaction of internal users with the outsourced service.
The service interfaces require close attention. The interfaces are more difficult to change because the same services are being used by other enterprises. In addition, all requirements must be reflected in the interface specification and service level agreement; otherwise, there is no basis for corrective action when the service does not meet expectations.
The service interfaces should be based on industry standards, if available. The enterprise should be able to switch to an alternative service provider if the current provider is not meeting expectations. Furthermore, the ability to switch to alternative services ensures competition between service providers to drive improvements in cost and performance.
Obviously, if the same services are available to competitors, they cannot be a source of competitive advantage. At best, outsourcing moves the enterprise to a best-practices level of performance. At the same time, the management of the enterprise does not have the burden of managing the implementation or ongoing operation of the service, although it is important for enterprise management to measure performance and enforce service agreements.
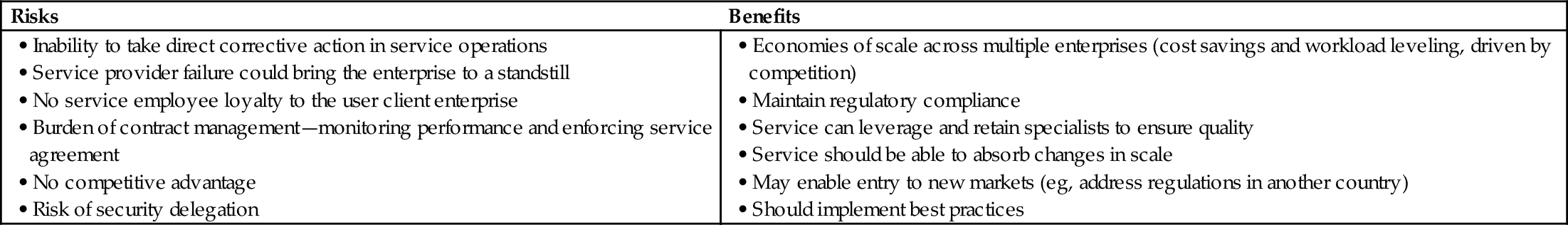
The risks and benefits of outsourcing are outlined in Table 3.1.
Table 3.1
Risks and Benefits of Outsourcing
Operational Design
A VDML model is a conceptual representation of the business. In order to meet operational needs, additional design details must be added. Here, we will examine the necessary expansions of the CBA conceptual business design to develop the operational business design.
Operational Design Alignment
The building blocks of the CBA align with the operational design of the agile enterprise. The scope of business processes discussed in Chapter 4 must align with the scope of the activity networks of capability methods. The operational level models add details that include flow control for individual transactions; handling of exceptions; application of business rules; security mechanisms; accounting facilities; and ancillary services for monitoring, maintenance, and control of service delivery.
In an operational design, the service unit will correspond to the capability unit and include ancillary services as well as computer applications for management of the capability. Consequently, in a CBA enterprise, the VDML model used by management will align with the operational business design such that the model can properly be the basis for development of operational design details, and measurements of business operations will provide the value measurements of the VDML model for the same product offering and circumstances. This enables managers to refer to the VDML model to understand the context of measurements, the consequences of disruptions, the implications of proposed changes, and the viability of strategic plans.
Service Unit Design
A capability unit identifies an organization responsible for the management of a capability, its personnel, resources, facilities, data management, and the capability methods that provide associated services. A service unit expands on the capability unit specification to define operationally complete capabilities. Fig. 3.10 depicts aspects of a typical service unit.
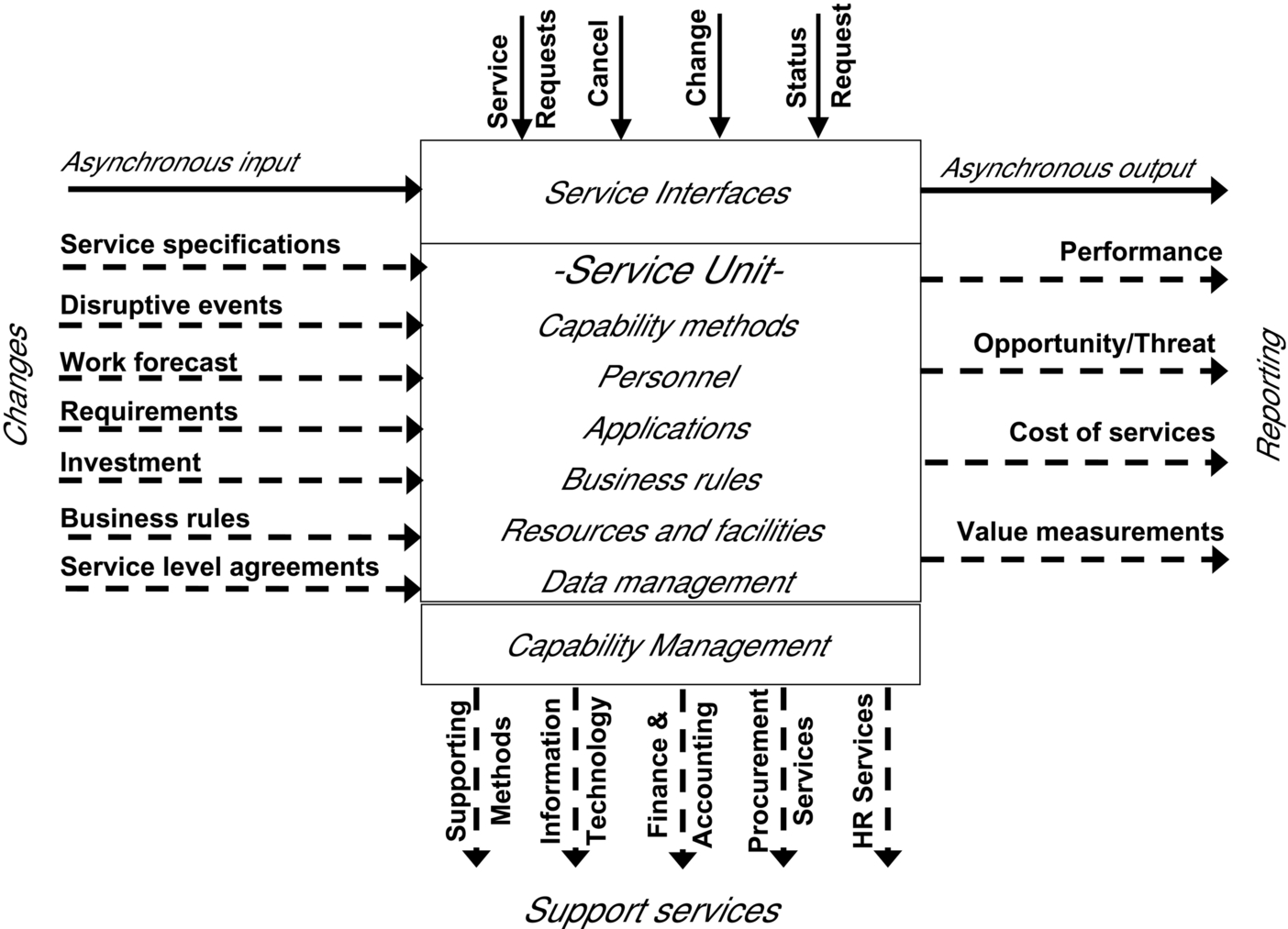
While this pattern implies considerable functionality beyond the VDML representation of the corresponding capability unit, VDML could be used to model these additional, detailed capabilities but that would obscure the business design abstraction. However, this could be modeled in VDML as a typical service unit pattern that engages a set of shared capabilities.
Note that not all capability methods will be implemented as information systems service units as described here. Some implementations may be completely embedded in conventional computer applications, and others may be implemented as human activities performed on physical deliverables with oral responses to questions and an individual or team that works according to a standard pattern of activities. In these cases, it may be necessary to implement specialized interfaces and protocols for integration with the enterprise information infrastructure.
Service Interfaces
The service interfaces on the top of the diagram are the interfaces for engaging the services defined by associated capability methods along with related services that are required for a full, operational capability. These are synchronous requests. Multiple services will require multiple processes that may all require consideration if the service implementation changes, although this will be easier to coordinate within one responsible service unit organization. It is also likely that specialized services will result in tighter coupling with users, in turn resulting in propagation of effects to users when the service unit makes internal changes. Each service unit should be designed to accommodate service parameters and specifications that enable a generic service to meet a range of user requirements.
There are also possible, asynchronous inputs and outputs—exchanges through stores. These must also be specified in the interface and performance specifications.
Note that though the focus is on service units that are electronically integrated and rely on automated business processes and applications, equivalent mechanisms must be considered where there are other manual exchanges based on paper or voice communications.
Supporting Applications
Most of the services managed by a service unit will involve some automated record-keeping or computations. These applications or tools are the responsibility of the service unit organization. The service unit must also take responsibility for the design of automated business processes.
Some services, such as a tax computation, for example, may be fully automated and on the surface involve only a computer application. However, there is an organization responsible for the computer application and for ensuring its accuracy and reliability. Though people might not be directly involved in the operation, people maintain the tax rates and computations. This may involve other people or other services to identify changes to tax rates and regulations. There may be still other people involved in technical maintenance such as adapting the computation to new information technology. All these capabilities and associated responsibilities are part of delivering a tax computation service. To the typical user, and from an executive management perspective, the tax computation service provides tax computations in response to requests.
The implementation of the service obviously involves much more, including the use of other services. These implementation considerations are the responsibility of the service unit organization.
Changes
Fig. 3.10 shows a variety of inputs as changes. These are not part of the normal operation of the services and are therefore not modeled in the capability methods. However, these inputs suggest that some action is required by the service unit organization to modify the services.
In the case of the service specifications and service level agreements, these will be the result of some collaboration involving representatives of the service unit, consumers of services, and enterprise leadership to ensure that they are appropriate from an enterprise perspective. A service unit is required to comply with its service interface specifications and its service level agreements. These specifications are effectively contracts with the rest of the enterprise. They may be changed as a result of new requirements or improvements in the service unit implementation, but they cannot be changed unilaterally. Performance metrics are based on performance against these specifications, and users of the services, as well as potential future users, rely on conformance to the specifications.
Reporting
Fig. 3.10 also shows outputs for reporting on the right side of the diagram. Performance measurements and opportunity/threat identification are for consideration of higher management and may support investments or other action for adaptation or improvement of the service implementations. The cost of services supports billing for services as discussed later. These are related but not the same as the statistical costs in the VDML model. The value measurements are actual measurements that may be used to investigate problems or compute the averages that are needed to support analysis in the VDML model.
Support Services
The other services indicated with dashed arrows at the bottom of the diagram include supporting capability methods engaged through delegation, and administrative support services that are necessary for the service unit to maintain its capability, but they do not contribute directly to the value of each unit of production. These support services—accounting services, IT services, HR services, and procurement services—have their own value streams that deliver value for the management of the enterprise and the business operations they support.
Service Unit Management
Service unit management involves the work of administration, problem solving, and dealing with changes as well as other factors that affect the appropriate application of the general capability and the specific services that are offered.
In addition, the service unit is responsible for the internal operation of the service unit such as
• Management of resources within the service unit. This involves ensuring the availability of resources
• Workload balancing for optimal utilization of personnel and facilities across multiple capability methods and potentially with related service units under shared management
• Batch processing or other methods for optimization of cost (such as setup and maintenance) versus timeliness of operations
• Process improvement
• Personnel training and supervision
• Design and improvements of computer applications
• Implementation of business rules
• Maintenance of facilities
• Data management, including the security, integrity, and accessibility of associated master data (see Chapter 6) and data that support the service unit operation and reporting
• Risk analysis and mitigation
• Business continuity preparedness
Legacy System Service Unit
A legacy application may be “wrapped” in a service unit with interfaces appropriate to the capabilities it supports. It is important that the interfaces conform to the logical data model discussed in Chapter 6 and that they reflect industry standards if possible. The legacy application may then function somewhat like an outsourced capability where there is little control over the implementation.
Billing for Services
Billing for services is an accounting function supported by the observed cost of services. It is not explicit in the diagram, but it is an essential aspect of any service. Each service unit must recover its costs, and the cost of each service must include the costs of services it uses. This is essential for effective motivation and management decision-making.
The cost of services reported on the right of the diagram includes both the total periodic cost of the service unit and the cost that is billed for individual units of service. The cost that is billed is based on analysis that determines the direct costs plus an allocation of overhead costs for each unit produced.
Costs of support services will be incorporated as overhead in the activities or value streams they support. For example, machine repair is a support service that may be identified as a capability unit. It may have a routine and preventive maintenance value stream and an emergency repair value stream. Both of these will require acquisition of parts and personnel scheduling. The costs of these services will be billed to consumers of the services based on usage, or allocated by some other formula. The service unit will incorporate these costs as overhead for the cost of its units of production.
The cost of services internal to the enterprise is determined by financial cost analysts, whereas the cost of external services is determined by negotiation of service prices with external providers.
Accurate cost accounting is essential for four purposes: (1) pricing, (2) performance evaluation, (3) billing for services, and (4) enterprise design. Cost determines the profit margin on products and services. Without accurate costing, it is difficult to determine an appropriate price or even whether a product or option should be continued.
Cost is an indicator of the efficiency of a service unit. Costs provide a basis for accountability of service unit managers, planning for process improvements, investment in new methods, service unit redesign, organizational changes, consolidations, outsourcing, and technology upgrades. Billing can influence users with respect to the utilization of a service, and it may influence the behavior of the service unit personnel in attempts to reduce costs.
Determination of the cost of a unit of service is not trivial, since there are both costs directly attributable to the particular service and costs that are shared. For example, the service unit incurs the cost of an employee even if the total work of providing all services does not require the employee 100% of the time. Since much of the work of a service unit may be automated, considerable employee time may be allocated to problem resolution and process improvement. From time to time, these employees may engage in projects funded by outside initiatives so that the service unit cost may go down, but then local projects may be delayed.
Table 3.2 illustrates a hypothetical cost allocation for the Assembly Service applied to Product 123. This example illustrates the nature of cost accounting and some of the difficulty in defining reasonable cost for individual services. The example service provides three operations, A, B, and C. Operation A is the primary service. The rows represent variations in the request options where the first row, Base, represents the product without options. The Fixed Cost column is allocation of the total fixed cost of $8000 based on the variable costs in the column to the left. Different ways of allocating fixed costs may be more appropriate for different types of service units; for example, the option cost variances may be only associated with the cost of purchased material and not the costs incurred in performing the operations in this service unit. It may also be important to divide costs between labor and material so that sources of costs of a service and total product cost can be better understood.
Table 3.2
Assembly Service Unit Cost Model
| Assembly Service | Operations | All Operations Total | Fixed Cost | Net Cost | ||||||
| Product 123 | A | B | C | Volume | Variable Cost | |||||
| Request Attribute | Volume | Cost | Volume | Cost | Volume | Cost | ||||
| Base | 400 | 4000 | 10 | 100 | 4 | 40 | 414 | 4140 | $7419.35 | $11,559.35 |
| V | 200 | 40 | 3 | 30 | 1 | 10 | 204 | 80 | $143.37 | $223.37 |
| W | 150 | 45 | 2 | 40 | 2 | 2 | 154 | 87 | $155.91 | $242.91 |
| X | 130 | 26 | 5 | 5 | 1 | 1 | 136 | 32 | $57.35 | $89.35 |
| Y | 10 | 50 | 0 | 0 | 0 | 0 | 10 | 50 | $89.61 | $139.61 |
| Z | 25 | 75 | 0 | 0 | 0 | 0 | 25 | 75 | $134.41 | $209.41 |
| Total | 915 | 4236 | 20 | 175 | 8 | 53 | 928 | 4464 | 8000 | $12,464.00 |
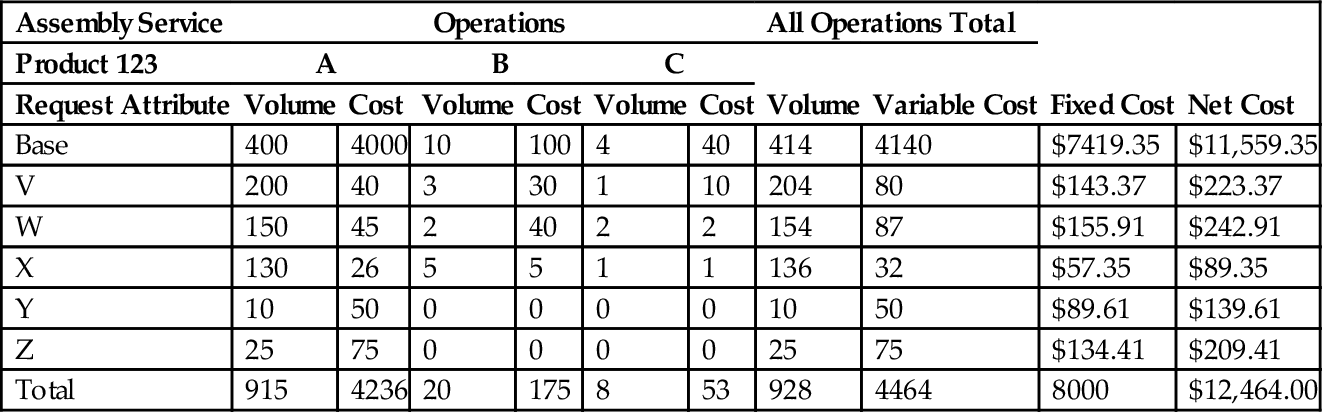
This cost model represents costs for a time period—for example, a week—and the product mix that occurred during that week is indicated in the Volume column. For some analyses, it may be sufficient to consider the average cost contribution of this service based on a typical product mix. For other types of analysis, such as pricing, it is important to understand the costs of the various options as well as the typical volumes, since marketing strategy should reflect profitability of different products and product options. A robust cost analysis model would support consideration of costs and pricing under simulated variations of product mix.
Note that the total cost of a particular product configuration in a time period (ie, based on a specific mix) is computed here by adding the associated marginal costs of all the operations that contribute to that product. In the example, this would include the product base cost and the cost for any associated options. It must also include the cost of components produced by services that are not performed in direct response to a customer order, as where orders are filled from inventories. These may be included as cost of materials earlier in the value stream.
Consequently, billing rates for service units are approximations based on expected workload, product or service option mix, and use of support service units. If the workload goes down, the cost per unit goes up because there are fixed costs involved. Nevertheless, users of a service unit need to be able to plan for the costs they will incur as a basis for planning and decisions that may affect their operations as well as when and how this service unit is used.
Service Specifications
The following paragraphs describe key elements of a service unit specification:
• Service unit name. An identifier for the service unit that corresponds to the capability unit name in the VDML model.
• Offering descriptions. This is descriptions of each capability method being offered.
• Versions and their life-cycle status. There may be multiple versions of service implementation in different stages of their life cycles: There may be versions under development, multiple current versions during a rollout to multiple sites, or versions that are no longer active but could be restored if a serious problem is encountered with a current version. Distinguishing features should be described. Service unit versions include software, business process specifications, resources, skills, facilities, or other aspects of the service unit that change to achieve a new service unit implementation.
• Interfaces and versions. Every service offered by the service unit must have a well-defined service interface. An interface includes specifications of service requests and choreography if applicable. A single version of a service unit implementation may have multiple versions of an interface to accommodate the transition of users of the service unit from one version to another. Interface versions should also have effective dates, both when available and when deprecated.
• Billing specifications. This defines the basis for computation of service charges to be billed to service users.
• Level of service specifications. These are the performance targets for the service, primarily response times, scheduled availability, and quality of results that are measurable at the service interface.
• Value contributions. Identification of the value contributions associated with each service. Since measurements will likely vary depending on context, a VDML model or actual production should be the source of measurements.
• Business continuity. Specification of contingency plans for circumstances that could prevent continued operation of one or more services or affect recovery time.
• Security. The level of security requirements of the services goes beyond the interface and level of service specifications to address implementation considerations involving other forms of exposure or disruptions of service. This includes the security of stored data and potential functional intrusion. See Chapter 7 regarding security issues.
• Used interfaces and versions. These are references to the interfaces of other services used by the specified service. Different versions of a service may use different versions of interfaces to other services.
• Scalability. Capacity limits or nonlinear impact of changes in volume on cost, timeliness, or quality. Of particular interest is the extent to which the impact of change in volume of production reaches a hard limit or becomes nonlinear so that, for example, a higher volume increases or decreases the unit cost.
• Access authorization policy. This is a statement of who qualifies to use each of the services offered and the process by which authorization is granted if there is not a shared service for that purpose.
Master Data Management
A service unit requires data to support and record its activities. Data management services are implicit in capability units. While a service unit may share a database with broader scope, the service unit organization should be responsible for the timeliness, accuracy, integrity, and access control of its supporting data and operating records including data that support service unit reporting.
The primary source of records, master data, that represent the current state of the business, including records that represent legal obligations or commitments, must be the responsibility of specific service units. Typically master data will be the responsibility of the service unit where data about the associated entity are first created in the enterprise. Each type of master data (eg, customer orders and purchase orders) must be managed by a distinct service unit since updates may come from many sources and users from many organizations may need access. Replicas of master data may be held in other service units for performance or addition of data specific to the alternate service unit, but the master data must be updated for any persistent changes. Data management and master data are discussed more extensively in Chapter 6.
Store Specifications
There may be a number of stores involved in the services of a service unit. The operating measurements of stores should be monitored and appropriate actions taken to ensure that the stores properly complement the affected capability methods.
The following are general types of stores:
• Queue. A queue is a first-in-first-out sequence of individually identifiable business items waiting to be processed. The queue adds delay to the process. At the same time, if the business item arrival interval varies or the receiving process acceptance interval varies, then the queue can ensure that the receiving process always has input. The length of the queue may impact customer value.
• Inventory. An inventory store exists to provide resources on demand to support one or more processes. If the inventory goes to zero, the receiving process may be delayed. If the inventory accumulates, then the cost of inventory may be significant. In addition, if the need for the business item ends, then there may be a surplus for disposal.
• Reusable resources. Pools are specialized stores used for resources that are assigned and returned—typically personnel, facilities, or tools. The number of resources needed will depend on the production rates, the length of time in use, and the proportion of production units that require the resource. If there are insufficient resources, the shortage will cause delay.
• Personnel. When there are multiple people with required capabilities, they are assigned from a pool, essentially the same as other reusable resources. However, some people may have multiple skills but not all the same skills. This means that they may be in multiple pools and assignments for one skill should consider that the person is no longer available for his or her other skill(s). The same may be true for some facilities that can meet the needs of multiple capabilities.
Supporting Information Technology
Implementation of a CBA requires supporting technology. Much of that technology is based on SOA to support the operation and integration of service units. Advances in the last few years, particularly advances in business modeling, further affect the information technology infrastructure.
The potential organization of a tool and die shop illustrates how shared services and current technology can support agility. The shop uses job routings of work to engage a combination of services and to define the sequence of operations needed to deliver custom products. The shop has a number of specialized tools and machines, along with groups of specialized tool and die makers who operate particular machines and apply their skills. The various specialists provide different services.
As a job comes into the shop, a dispatcher prepares a job routing (ie, an ad hoc business process) that defines the sequence of services to be performed. The routing and operator instructions are delivered to tablets of operators as the work moves through the process steps. For some jobs a product or component may be fabricated from several parts by a team of specialists. The fabrication work is delegated to a fabrication capability method.
The operators record their actions and a porter picks up the work product and moves it to the next work station. Required tools are also routed to the next station through tablet instructions to the tool crib and the porter. Specialists may have multiple skills, so they may be assigned to different work stations and equipment based on workloads and job scheduling. The skills, tools, and machines used in each department remain unchanged, but a wide variety of products are produced. The shop is highly adaptive and efficient.
The adaptive routing of this example could be implemented with a product based on CMMN (http://www.omg.org/spec/CMMN/1.0). CMMN activities will engage various capability services as required to complete the requirements of each specific job. The routing can be adapted if there is additional or specialized work not initially anticipated or if there is rework required. Participants are notified when a job requires their action. CMMN is discussed in Chapter 4.
Of course, these automation capabilities may already be in place using specialized software. Application of a CMMN-based system will provide greater flexibility at lower cost including the cost of adapting to further advances of technology.
Technical Infrastructure
It is important that business and technical leaders have an understanding of the technology requirements and their business impact because the supporting technologies represent a significant investment that is essential to achieving the agile enterprise. Here we provide a general overview. We will start with discussion of key components of the technical infrastructure and then examine the implications of mobile computing and cloud computing. Subsequent chapters will discuss certain key technologies in greater depth.
An SOA is the underlying technology of the CBA. For the most part, electronic technology is expected to provide the medium of exchange of information. There are still other forms of media in use, particularly paper forms and voice communications. Nevertheless, today many paper and voice communications are being replaced by electronic communications on smart phones and tablets. Even documents that are attached to physical deliverables are likely identified by bar codes or RFID chips (radio frequency identification) and retrieved electronically.
Therefore, an electronic infrastructure—computing, communications, and associated software and supporting resources—is essential to SOA and CBA. The infrastructure must support standards and consistent implementation (1) to minimize cost and complexity, (2) to enable sharing and flexibility, (3) to ensure security, (4) to integrate applications in diverse technologies, and (5) to enhance speed, reliability, and economies of scale. With the Internet, the electronic infrastructure will support rapid communications with shared capabilities and human participants located around the world.
This infrastructure, along with adaptations for integration of existing systems, requires an upfront investment that increases the costs of early SOA projects but provides significant benefit and lower costs in the long term.
There are several fundamental components that must be part of the enterprise electronic infrastructure to support the integration and operation of service units. Fig. 3.11 depicts the key infrastructure components discussed in the following sections.
An integration component (including messaging, transformation, and access control) is associated with each of the services in Fig. 3.11 (the gray areas). Each service unit is capable of exchanging messages with any other service unit, and these exchanges could extend outside the enterprise. Additional technical details are developed in later chapters.
Reliable Messaging
Communications between service units are primarily through message exchange over the intranet (internal internet technology). Internet technology and middleware support the rapid, ad hoc exchange of messages between many sources and many recipients.
Messages must be communicated with reliable messaging. This means that the messaging system ensures that each message is delivered to a recipient once and only once. In a paper-based world, reliable messaging is accomplished with the use of original documents (so, there is only one) and transaction numbers such as an order number or invoice number.
In an SOA, requests for services and the interactions between requester and provider are communicated as messages. The communications are usually in a store-and-forward mode so that a message can be sent by one participant but held until the recipient is ready to receive and process it. A participant may send a message and continue to do other work rather than suspend activities until the recipient responds. This is described as loose coupling (more specifically, temporal loose coupling) because receivers need not be immediately available to receive messages.
Although these messages are communicated asynchronously from a technical perspective, from a business services perspective, the communications are very fast and support synchronous delegations and deliverable flows as well as asynchronous deliverable flows between collaborations as modeled in VDML.
Message Transformation
Message transformation is required to convert the sender's format of message content (if necessary) to a shared, exchanged form and then transformed to a recipient's form (if necessary). Fig. 3.11 depicts a message transformation capability at the interface to each of the service units. This anticipates that at various times, at a minimum, as new versions of services are implemented, there may be a need for transformation if only on a transitional basis.
Optimization of enterprise operation requires the ability to integrate and exchange data from multiple sources in the enterprise to support operations, analysis, planning, and decision-making. The diversity of sources and uses requires the ability to transform messages to correspond to the requirements of senders and receivers. The preferred approach is to exchange all messages in a consistent, neutral form, and transform a message specific to a sender or a receiver.
In the long term, transformations should be minimal, but transformations will continue to be required for interfaces to legacy systems and for transitions when business changes require changes to message content.
Differences in format, terms, and units of measure cause incompatibility that is relatively easy to correct. For example, dates may be expressed in different forms, such as dd/mm/yyyy, mm/dd/yyyy, ddd/yyyy (Julian), or other variations. Different terms might be used, for example, to describe employee status, such as temporary, part-time, salaried, and so forth, where they might be expressed in different languages but have the same meanings. Units of measure might be feet and pounds or meters and kilograms. Again, these are relatively straightforward but necessary conversions. Recipients of XML (http://www.w3.org/XML/) messages can allow for unexpected elements that are added for a new version, but more complex changes may require transformation.
For example, the same business entities may be represented, but with different identifiers for individual entities. Then there must be a cross-reference source to support a conversion.
Application adapters provided by integration middleware should provide for transformation between the application internal representation of data and an appropriate XML exchange representation.
Some messages may contain encrypted or signed content. This content must be retained by the creator or initial recipient of the document to preserve its validity. A working document, with encryption removed and signatures validated, may be shared for internal processing. However, the decryption and signature validation should be done by the master owner, not by the middleware transformation facility. This transformation might be performed by a shared security service unit that applies the appropriate keys for encryption and signatures or decryption and signature validation. Signed documents must be preserved in their original form for enforcement/accountability/nonrepudiation. Encryption and signatures are discussed in more detail in Chapter 7.
XML Data Exchange
The messages exchanges are in XML (eXtensible Markup Language) format. XML has been widely recognized as the preferred format standard for exchange of data between information systems that may involve different supporting technologies.
XML was recognized fairly early in the 1990s as a useful form of data interchange. It has several important characteristics:
• XML documents (ie, records) are somewhat self-documenting. Each element is tagged with a descriptive name.
• The fields are variable in length, with special characters designating the beginning and ending so that the format remains valid, even if the length of a field changes and text fields can take whatever space is required.
• A receiving program can select fields of interest based on the tags and ignore any other fields that may have been added by the sender, so the receiver can continue to use documents that have been expanded for other purposes.
• XML is used to specify the structure of XML documents (using XML Schema) so that shared specifications can be used for computational validation.
• XML is also used to express the transformation of XML documents by using Extensible Stylesheet Language Transformations (XSLT) so that there is a standard, computer-interpreted language for document transformation.
• XML is independent of the computing platform and computer languages used to send or receive it, so there is compatibility between diverse sending and receiving technologies.
• XML can be exchanged using HTTP and HTTPS, protocols of the World Wide Web, so that existing ports are compatible and the data can pass through existing firewalls.
• The widely accepted standard for electronic signatures is based on XML. Standards for encryption and signatures for XML documents are discussed in Chapter 7.
XML, along with XML Schema (http://www.w3.org/XML/Schema), XSLT, HTTP, and related standards, has been developed by the World Wide Web Consortium (W3C). Though other forms such as electronic data interchange (EDI) are still widely used, XML has emerged as the preferred form for exchanging electronic documents between systems and enterprises. The verbosity of XML that increases communication overhead is a trade-off for flexibility.
An example use of XML follows. This XML document is structured to contain a collection of customer orders—in the example, there is only one order with two line items:
<?xml version="1.0" encoding="utf-8" ?> < Orders > < Order orderID="103"> < Customer customerID="1234"/> < OrderItems > < Item > < Product productNo="223445"/> < Description > 100-watt speaker, Mahogany case </Description > < Quantity > 2 </Quantity > < UnitPrice > 235.95 </UnitPrice > </Item > < Item > < Product productNo="234523"/> < Description > CD Player, Mahogany case </Description > < Quantity > 1 </Quantity > < UnitPrice > 167.95 </UnitPrice > </Item > </OrderItems > </Order > </Orders >
The XML expressions are indented for readability. Each expression begins with < name > to identify the data element (where name is the name of the data element) and ends with </name > (a slash prefix) to specify the end of the data element. An element may contain a primitive value (ie, a data type that is not defined in terms of other data types), another element, or multiple elements. A primitive element may be expressed with both a name and value together, for example, the Product element in the example, by ending the value segment with />, and other attributes can be expressed with the name such as at the beginning of the Order element in the example. < Orders > could contain multiple orders, but in this case, only one order is shown, which starts with < Order > and ends with </Order >. Within the Order are elements for Customer and Order Items. The Customer element only specifies the customer ID. There are then two order items, each containing several order-item attributes. XML structures are specified with a specialized XML language called XML Schema, so the format can be validated by a generalized computer program.
In many cases, these XML documents capture work products and decisions for which people or organizations should be held accountable, and some of these represent legal records or agreements that require encryption and electronic signatures.
Access Control and Security
The infrastructure must provide protection for the communications between service users and service providers using encryption as required. It must provide the means for determining the identity of participants (called authentication) and for determining whether participants are permitted to make certain requests or receive certain information (called authorization). These access control mechanisms must be complemented with logging and audit support, to ensure accountability and expose inappropriate accesses and attempts. Each service unit in Fig. 3.11 has an access control component that uses the security service. The security service unit includes identification, authentication, and authorization services.
In a CBA, many users are expected to directly or indirectly access many systems. This is partly because optimization of operations requires cross-enterprise access to data and because shared services may be used in a number of contexts. Users should be able to sign on once and then be able to access a number of systems for which they have authorization; this is called single sign-on. Security issues for SOA and the agile enterprise are discussed in more detail in Chapter 7.
Business Collaboration Management System(s)
Business Collaboration Management (BCM) is discussed further in Chapter 4 as next-generation Business Process Management (BPM) that comprehends, not just repeatable business processes and adaptive business processes but all forms of collaboration.
The technical infrastructure should include BCMS (Business Collaboration Management System) products. This includes a BPMN (business process modelling and notation, http://www.omg.org/spec/BPMN/2.0/) tool, a CMMN (case management model and notation) tool, and a DMN (decision model and notation, http://www.omg.org/spec/DMN) implementation to support automaton of business processes—prescriptive, adaptive, and ad hoc. BPMN, CMMN, and DMN are discussed in greater detail in Chapters 4 and 5. These tools should support modeling, execution, and analysis of performance for process improvement. Though an enterprise may have multiple BPMN or CMMN software products, preferred BPMN and CMMN products should be available for automation of business processes anywhere in the enterprise so that the same skills are required and the automation software is readily available as new processes are defined and deployed. Deproliferation of tools reduces licensing costs, eliminates incompatibilities, and enables everyone to use the same tools and representation in designing and improving business processes.
Note that there will still be collaborations identified in VDML that are not automated with BPMN or CMMN systems.
As more attention is given to the broad range of business collaborations, it should be expected that there will be more products to support collaborations and more industry standards. In Fig. 3.11, the BCMS is depicted as an infrastructure service, but it may include multiple services of multiple collaboration tools.
Notification Broker Services
A notification broker is a subscription service. All notices are directed to the notification broker. Systems and service units that act on events subscribe for notice by event type and may specify a filter to limit notices based on event notice attributes.
Events will become increasingly important as more automated support is provided for collaborations and people are engaged with mobile devices. Events and notification are discussed in detail in Chapter 8.
Registry Services
Registry services maintain current information about available services. At a minimum, a registry should provide links to available services so that users of a service can refer to a logical name of the service and be directed to the appropriate network address that may change over time.
In addition, the registry should identify different versions of service interfaces so that either a compatible version can be located or the interactions can be properly adapted or transformed. The registry should provide criteria for the selection of a service from among similar services. Within an enterprise, there may be only one appropriate service for a shared capability, but that is not always the case. For example, there could be services for different time zones or different countries, specialized for different product lines, or located in different physical facilities. The registry might also be extended for identification of approved external services such as supplier services, including, for example, suppliers that might be eligible to bid on a particular class of purchase request.
It may be useful to include additional information on each service for general reference, business management, system configuration, and change control purposes. The registry services should complement or extend the configuration management database (CMDB, https://en.wikipedia.org/wiki/Configuration_management_database) as defined by the Information Technology Infrastructure Library (ITIL). A CMDB supports management of computer applications and IT infrastructure.
It is also desirable for the registry to represent dependencies between services for data processing operations people to determine the implications of service failures and to plan for disaster recovery contingencies. However, a robust, current VDML model of the business should provide a better understanding of the dependencies from a business perspective.
Portal Support
Services are not only used by other service units but by humans as well. Even where a service is always invoked by an automated system, there likely is a need for human access to obtain information about the status of a request or associated data. The human users may come from across and outside the enterprise and include employees, investors, business partners, and customers. They need a way to find the appropriate services and to submit requests. This need for visibility of services to human users should be addressed by appropriate portals—a web site for each community of interest.
Generally, a portal is designed for use by a particular stakeholder community, and a community portal provides access to a variety of services of potential interest in that community. There may be multiple portals for participants in different collaborations where work is supported by specialized smart phone or tablet applications. Each portal should be owned by a service unit that manages the interactions with the associated community.
The design of a portal should address the particular needs of the stakeholder community, should have a consistent look and feel, at least for each community, and may include personalization features. Some portals will need to support internationalization. In addition, the service unit can address the need to translate the form of expression of requests and responses between the stakeholders’ point of view and the internal services that respond to their requests. The infrastructure should support the necessary portal technology.
Performance Monitoring
Effective management of a CBA requires that performance data be captured and made available for monitoring and analysis. This should include evaluation of performance measurements against level of service agreements. It should be possible to obtain current performance data on any service. These measurements should be accessible in the context of a current VDM model of the business and viewed through a management dashboard as discussed in Chapter 6.
Billing for Services
Though costing is primarily a financial responsibility, the IT infrastructure must provide the mechanisms by which service uses are tracked and charges are computed and billed. A billing infrastructure may not be essential in the early stages of transformation to CBA, but it must be part of the strategic infrastructure design.
Billing requirements and cost allocation have been discussed earlier in this chapter as a service unit design requirement.
Mobile Computing
The proliferation of smart phones and tablets is changing the way people communicate and interact with computer systems. People can be always on line. They can obtain access to large records and documents and search for information to support their work.
This has a significant impact on collaboration and access to services. People can be actively participating in a collaboration with others who may be anywhere in the world. They may be notified of an important event, take immediate action, or engage others in resolution of the situation. They can request services and check the status of deliverables they need for further action, and track the status of initiatives from strategic business transformation to a crisis response. We will see the importance of this connectivity to adaptive processes in Chapter 4.
Cloud Computing
In the last few years, cloud computing has emerged as a viable approach to providing data processing services as a utility. Cloud computing adds an important dimension to enterprise agility. It can provide unrestricted scalability as well as seamless failover to move active applications to remote computing sites to ensure uninterrupted computing and communications services. It also means that an enterprise does not need to establish or maintain strong information technology capabilities to configure, maintain, operate, and secure computing and communications services.
At the same time, cloud computing will require integration of the conventional, enterprise computing infrastructure with the cloud infrastructure. This will require some new technical skills and may add complexity to customer support when the IT organization has neither direct control nor knowledge of the cloud operations.
The fundamental concept of cloud computing is that multiple computers are networked and integrated such that applications and data can be located anywhere in the network, resources can be allocated to accommodate changing workloads, and “failover” will relocate an application if it is executing in a node that fails.
There are a variety of alternative forms of cloud computing:
A private cloud is a computing network that is typically on the consumer's premises or in a provider premises but isolated from hardware running applications of other consumers. This form provides the greatest consumer control and also the greatest burden for management of the computing and communications environment.
In a virtual private cloud configuration, multiple consumers share a network of computing hardware, but each has a virtual machine environment (software) that executes and isolates conventional applications and data from those of other consumers. This gets the consumers out of the business of managing hardware and networking facilities, it provides more flexibility for scalability and failover, and it provides some savings from economy of scale.
In a hybrid cloud configuration, the consumer mixes the use of private and public cloud environments. For example, one approach is to keep the data and user interface facilities in the private cloud and run the applications in the public cloud. This minimizes the potential for exposure in the public cloud but is more complex and requires the consumer to remain involved in the full spectrum of data processing operations.
The public cloud approach supports multiple consumers (multitenant) with shared hardware and operating system. This configuration realizes the full potential of cloud computing for distributed computing, scalability, economy of scale, global failover options, dynamic load balancing, and more. Of course, it puts maximum trust in the cloud provider for reliability, security, performance, and regulatory compliance.
An extended cloud opportunity is for multiple consumers to share an application—a multitenant application). This achieves additional economy of scale and supports application billing based on use. But, note that this requires additional application functionality and places additional trust with the application provider to ensure security and maintain expected performance.
We expect the public cloud configuration will be the dominant configuration in the long term. Only very large enterprises will have the scale and expertise to realize benefit from a private cloud. The virtual private cloud may be useful for some applications since it should require the least adaptation of applications, but it achieves only limited virtualization, meaning that it cannot be as transparent in workload balancing, dynamic scalability, and failover. The hybrid configuration is a very cautious approach that requires the consumer to maintain considerable technical expertise and technical operating responsibility.
In the near term, enterprises should be cautious about deploying mission critical or high security systems in the cloud. The flexibility of deployment of applications and data raises additional concerns about data export regulations (data residency) since processing can potentially be transferred to a data center anywhere in the world when a server fails. The technology is still evolving. Eventually, it is likely that it will be very difficult to achieve better security or reliability than that provided by established cloud providers. At the same time, these will be very large providers and a software error might permeate the network and have devastating global, social, economic, and welfare consequences. They could become too big to fail.
▪ Summary and Forward
In the first three chapters, we have introduced the emerging requirements for an agile enterprise, and we have introduced a new modeling language for designing, analyzing, and understanding how a business works from a business leader perspective. Then, we described a general approach to designing an agile enterprise based on value delivery management (VDM) and a CBA supported by an SOA infrastructure.
In the next five chapters, we will go deeper into the details of exploiting information technology for the agile enterprise. In Chapters 9–11, we will focus more on the enterprise transformation and the impact of the agile enterprise and supporting technology on the organization structure, governance, and leadership.
