Chapter 4. Dealing with Everyday Glitches
Most IT glitches are identified and addressed quickly. Still others can take days or even weeks before they’re repaired. On the surface, these system errors are, at a minimum, annoyances that reflect an oversight or a shortcut in the software design. In many cases it may not be a shortcut at all, but a reflection of the growing complexity of the infrastructure.
The results of an IBM Global CEO study released in 2010 further indicate that the IT infrastructure will continue to become more complicated. The survey participants included more than 1,500 CEOs, general managers, and government officials from 60 countries spanning 33 industries. While eight in ten of the survey participants expect the complexity of the IT infrastructure to increase, only 49 percent believe that their companies are prepared to handle it.1
Adding to this is the fact that we continue to breathe in data like it’s air. The current size of the world’s digital content is equivalent to all the information that could be stored on 75 billion Apple iPads, or the amount that would be generated by everyone in the world posting messages on the microblogging site Twitter continuously for a century.2
All of these factors contribute to unintentional yet insidious glitches. This chapter looks at how these glitches make their way into the infrastructure and what we can do to more effectively manage the processes that allow them to proliferate.
The Evolving IT Infrastructure
Keeping up with trends and determining what’s hype and what’s real are only part of the typical ten-hour workday in the IT industry. The biggest challenges come from sustaining the infrastructure that fuels the business. To put the complexity of the evolving IT infrastructure in perspective, take a closer look at Figure 4.1. It maps the types of tools, software languages, and embedded systems within the context of Internet services.3
Figure 4.1 Technology map of Internet services
Within each slice of the pie are hundreds of potential technology products that can be added to the infrastructure. As we continue to innovate in the pursuit of productivity, we also need to properly manage that innovation so that we are not draining our physical and intellectual IT resources.
However, building more efficient business models through the IT infrastructure is not an easy feat. In some instances, the risks outweigh the rewards because you don’t just have to reinforce your infrastructure. You also have to be mindful of the infrastructures managed by the companies you’re doing business with online.
Increasingly complex infrastructures, a rise in the amount of data we continue to consume, and the growth of online collaboration and commerce are contributing to the creation of these unintentional yet insidious glitches.
These glitches aren’t headline news, but they do stall productivity. They are the everyday hiccups that cause us to reboot our computers, unnecessarily spend time on customer support lines alerting staff to issues, and basically make us think twice about doing business again with certain vendors.
Breaking down some of the complexities of the infrastructure is a matter of stepping back and understanding how we’ve accumulated so much technology. Three critical factors contribute to this:
• The availability of cheap and powerful processors
• Reduced costs through outsourcing
• Easier access to enterprise software
The Availability of Cheap and Powerful Processors
A walk around any appliance store is evidence of how we’ve been able to add more technology into our homes. We’ve souped up our washers and dryers to make them more energy-efficient. Our coffee pots automatically know to start brewing at the same time our light-sensitive digital alarm clocks help us start the day. And our refrigerators are programmed to adjust to temperature fluctuations if their doors are continually opened and closed, as is the case when my kids are home. Although all these innovations certainly make our lives easier, they also illustrate just how much technology is entrenched in every action and interaction.
As IBM’s Software Group Senior Vice President, Steve Mills, told me during our interview for this book, “There are one billion transistors for each person on the planet. We’re seeing an almost cosmic-like expansion where intelligence is everywhere. Everything will become instrumented, including supply chains, health care networks, cities, and even natural systems like rivers.”4
As Mills pointed out, we’ve been putting intelligence into products and devices for decades. We’ve been able to do this because the price of 64-bit processors has dropped significantly, making them easier and less expensive to embed in products.
To put this in perspective, the speed of the processor determines how fast the computer or device will process information. This speaks directly to Moore’s Law, which was published in 1965. It states that the number of transistors on a chip will double about every two years.5 Since the first 64-bit processor was introduced in 1992,6 the power continues to accelerate with each iteration. Since many of our consumer devices don’t require more than 64-bit processors to deliver high-end features, this explains the price drop and why the latest appliances and devices are now fully loaded.
Whether or not you subscribe to Moore’s Law, it’s impossible to overlook the 2010 introduction of the Itanium line processors by Intel, the world leader in silicon innovation.7 The world’s fastest processors allow us to process information and download larger, multimedia-rich files and applications at speeds never before possible while more efficiently balancing the consumption of energy. Making data and digital files that much more accessible to an increasing number of connected users increases our reliance on technology. The more dependent we are on technology, the more technology we need. To take advantage of this processing power without slowing down our applications or allowing glitches to quickly sneak past inspection comes down to the health of the IT infrastructure itself.
Reduced Costs Through Outsourcing
The rise of outsourcing for software development activities will remain a controversial topic for the foreseeable future. On paper, it appears to be a cost-effective way to take advantage of overseas IT skills, yet the results have been mixed. The biggest disconnect has been in justifying the cost savings in comparison to the quality of service delivered. Lower quality software cook is often rife with glitches.
However, the benefits of outsourcing can be reaped if both the client and service provider take the right approach. Elizabeth Grealy, CEO and cofounder of Grealy Globalization Enterprises, a Boston, Massachusetts consulting firm specializing in ensuring successful outsourcing engagements, shared with me some of these critical success factors:8
• Top-level support. Make sure the senior management team, including the CIO and CEO, are fully vested in the success of the outsourcing program, from vendor selection through the ongoing progression of a mutually beneficial relationship with the outsourcing firm.
• Experienced management team. The maturity and discipline of the management team—of both the client and the service provider—are directly tied to the cost savings and benefits that can be gained. As Grealy pointed out, “When you have a team sitting outside your office, you can pull them in for a quick meeting or for fast turn-around on a project. With outsourcing, you need to have vision and be proactive in the way that the project is being managed and executed, because you are working with a remote team. Essential to a successful outsourcing experience is the need for structure, including formalized requirements, scope, communication, and development processes and issues management.”
• Accurate assessment of what can be outsourced. Distinguish between core and noncore activities to determine which projects should be outsourced. The core activities are considered the company’s intellectual property and are the primary revenue-generating functions that are best handled by the company itself.
• Consult with reputable outsourcing experts. It’s worth the investment to cultivate a relationship with a globalization expert if you are interested in an outsourcing program. In evaluating experts, be sure they can help define the business requirements, will outline the infrastructure for an outsourcing program, and will help steer the efforts that result in successful engagements. Additionally, they should be conversant in relevant software languages and development methodologies and understand the nuances of your industry.
• Consider the following factors in the decision process:
• The team’s experience with industry and technology and their education levels
• Experience and history of the service provider
• Potential language barriers for customer-facing assignments
• Knowledge of local laws and the ability to enforce contractual agreements
• The physical infrastructure of the outsourcer’s offices, including building security, access to the office through modernized roadways, and stable electricity
• The IT infrastructure of the outsourcer’s offices, including networks and disaster recovery plans
• Geopolitical status of the country and the service provider
• Leave nothing to chance. Be extremely detailed and clear in outlining the scope of work, roles and responsibilities, deliverables, and service level agreements.
• Establish governance processes and policies around the following:
• Security and confidentiality standards
• Staff reporting structure
• Legal agreements including noncompete clauses
• Auditing to ensure adherence to corporate and regulatory requirements
• Try before you buy. If you are planning to outsource more sophisticated software development efforts, consider having a prototype developed by the proposed team to validate their development skills and their ability to apply those skills to your code.
• Be prepared for turnover. It’s no secret that turnover rates at some outsourcing firms can be high. While you can’t force an employee to stay, you can build contingencies and incentives into the contract. These hold the outsourcer responsible for meeting the deadline with a quality product and reward the outsourcer at the project’s completion.
• Take an incremental approach. Allocate appropriate time for proper knowledge transfer. As with any major IT effort with a new team, you should take an incremental approach to ensure the work’s quality and consistency.
• View outsourcing as a partnership. A stronger relationship with the service provider is established through trust in every exchange and business transaction. From a more tactical point of view, it’s important to invest in team-building exercises, employee exchange programs, and staggered schedules to ensure live conversations among the integrated team. Fostering an environment where there is trust and the outsourcing team feels like part of your organization is a critical part of reducing turnover, improving productivity, and raising the quality of product that’s delivered.
Significant benefits can be gained through outsourcing. According to Grealy, “If approached and managed properly, companies can save between 20 and 30 percent annually through outsourcing.”
Creating sound infrastructures isn’t solely an issue of internal versus external employees. The more hands that are involved in developing software, the greater the risk of vulnerability and compromises in the end product if the organization lacks agreed-upon standards and approaches. Using technology to automate part of the software development processes and flag potential issues before they get too far down the line can also improve the overall quality of the code, regardless of whose hands are at the keyboard.
Easier Access to Enterprise Software
The software as a service model has enabled more companies to take advantage of higher-end features and functions without needing to add headcount to manage the software. Although a third party owns and manages the software, the technology itself still intersects with your infrastructure through the employee’s computer. This can potentially add a level of risk due to greater exposure of your infrastructure.
Along with the subscription-based software model is the ability for companies to easily download new versions of enterprise software that are made available through the vendor. Although upgrades can boost productivity, they also add to the infrastructure if no process is in place to ensure that older versions are phased out properly.
Two additional factors are driving up the expansion of technology in a company and the complexity of managing it:
• Healthy curiosity among IT professionals
• A mismatch between technology and business
Healthy Curiosity Among IT Professionals
IT professionals tend to be curious about the latest development tools, applications, and programming languages. One of the roles of an IT professional is to closely watch and test the latest technology offerings.
However, avoiding introducing rogue technology into the company is a two-step process that requires a system of checks and balances. It takes into account people and processes as well as the overall business value the technology brings to the company.
The first step of avoiding this behavior is using a road map that is aligned with the company’s business direction. Realistically, a clear vision should account for the next 24 months. To stay on course with that road map, you should ask two questions before you purchase or download any technology:
• Does it benefit the organization economically and strategically?
• Can we easily build it ourselves?
The second step is trusting that your senior-level IT professionals have the experience to answer those two questions. Along with their effective people-management skills comes the need to institute IT processes that will prohibit unauthorized technology from making its way into the company. Although leadership, trust, and experience are valuable assets, the organization also must put controls in place that prevent technology from being used if it doesn’t reflect the larger business goals or could disrupt the company’s day-to-day operations.
In the context of healthy curiosity, it would be impossible to overlook the contributions of the open source community, because open source often helps solve business challenges. However, before you decide to allow open source software into your infrastructure, be sure that you have a dedicated team internally to manage it and participate in the advancement of the community. Before selecting an open source solution and purchasing a service plan, be sure that the vendor behind it has a dedicated team for service and support. That way, you won’t rely on unknown, external resources for the latest patches, upgrades, and answers to questions.
A Mismatch Between Technology and Business
Even after a thorough product evaluation, a mismatch can occur between the technology’s features and its ability to help support business goals. This can happen for several reasons, all of which can interrupt the flow of business. Two of the more common issues are skills and unrealistic expectations:
• Skills: When a company purchases more-complex technologies, the contract usually includes professional consulting services so that the client can get up and running quickly to start seeing the benefits that were promised during the sales process. During this time, the company employees should be immersed in learning about the new technology and working very closely with the professional services consultants so that skills and knowledge are transferred and the company can sustain the technology after the consultant engagement ends. Even with simple software we subscribe to over the Internet, if it’s not easy to use, the investments will be for naught.
When it comes to service contracts, it’s the responsibility of the vendor and client to ensure that the internal team has as much knowledge of the product as the consultant within a reasonable amount of time.
A simple formula for success is to divide the project into thirds. One third of the time should be dedicated to ramp-up, another third allocated to self-sufficiency, and the final third should be dedicated to mastery.
Let’s assume that the average enterprise software project is scheduled to run for 18 months. You should expect that employees are close to being fully self-sufficient within 12 months. Not coincidentally, this time frame usually aligns with the software and service renewal license, so that’s something to keep in mind as you negotiate the renewal.
• Unrealistic expectations: In an ideal world, the new technology easily blends with the existing technology a company has in place. When this isn’t the case—which often happens—making everything work together can take a long time. This is often the point where companies begin to reassess their purchase as well as the skill set of the team responsible for integrating the technology. This is a critical juncture, because it can bring to light the shortcomings in the technology as well as the staff. And you know where fingers are likely to point if you’re the software vendor.
To avoid losing the client, proving the value of the technology and creating demonstrable success that can be used to win other clients, it’s important to establish milestones and report cards with the customer before any work starts.
It’s easy and natural to want to just jump into the project. However, both sides need to agree on the road map as well as ongoing check-ins on progress. Otherwise, the project is vulnerable to failure in the form of a dissatisfied customer who may also have the right to pursue litigation.
With all these activities happening on a regular basis, you can see how the infrastructure continues to expand and contract. Even in instances where enterprise software has been displaced in favor of a competitor’s offering, remnants probably will remain in the form of source code or customized applications. If that source code or those applications are not actively being used, make sure that they’re no longer lingering and draining network resources.
Dispelling Seven Common IT Myths
Maintaining realistic expectations about technology is key to realizing productivity gains. With this in mind, following are seven common IT myths. The explanations clarify some of the more common misperceptions about what technology can and can’t do:
• Computer science is an exact science. The term “computer science” is a misnomer. I suggest we change the category name to the “art of computer science.” If you think about software programming in terms of languages and how different aspects of those languages are linked to create an application, you start to see the real art behind computer science. Put another way, even though the English alphabet has only 26 letters, we manage to put those letters together in many different ways. Although we must follow processes and protocols in the art of computer science according to the programming language, we also have much freedom in how software is designed and developed. This is the stuff of innovation, yet it can also be a source of glitches. Perhaps if we infuse more business courses into the computer science curriculum to help put the efforts of software development in a business context, we can decrease some of the coding errors that arise.
• The next big software release will address the issues. The software development process has four fixed dials: time, features, resources, and quality. Those dials are constantly fine-tuned as the software is developed, and any change to one dial affects the others.
For example, not properly estimating the time it takes to include certain features can affect the staff that’s dedicated to the project, the quality of the final product, and the product release.
As is often the case, major product releases—those that end in a .0 or .5—tend to sacrifice quality to meet deadlines. This is why developers typically wait for the next point release from the vendor instead of using the major release version that is being marketed. This is a wise decision in many cases, but what can happen is the software vendor may release a series of point releases and patches to fix the known issues. IT departments must be careful to track the consistency in the version that’s being used, because inconsistent versions that are being tweaked by a company’s development team are ripe for the creation of glitches.
• It works out of the box. Retail software products are designed to work immediately as described, but enterprise software has varying degrees of customization. If you read any marketing material from an enterprise software vendor that touts its out-of-the box enterprise capabilities, think twice before you invest.
• The code is documented. This is a best practice to shoot for so that the company and any new team members will know exactly where the team left off in the development process. But it’s unrealistic given the time constraints facing most IT staff. A lack of documentation contributes to knowledge drain across the board, but technology can be used to automate and track the more staid processes and mitigate some of these risks.
• The documentation explains everything. Documentation is critical to reducing the IT staff’s learning curve, although there are varying degrees of quality when it comes to explaining how the software will work. This is why investing in professional consulting services and training classes to augment the team’s existing skills and hands-on experience can be worthwhile.
• All hackers are evil. The definition of a hacker is a clever programmer.9 Of course, the impact of some of that clever programming has created a negative connotation for the term. Once the trust hurdle has been cleared, however, there’s something to be said for having someone on your team who knows the system’s ins and outs, can find the holes and plug them, and will contribute to creating a stronger infrastructure.
• The biggest threat is outside the walls. We know about the threat of cyber attacks and cyber crime, and we are aware of the enemy within, but employees also can create cracks in the infrastructure.
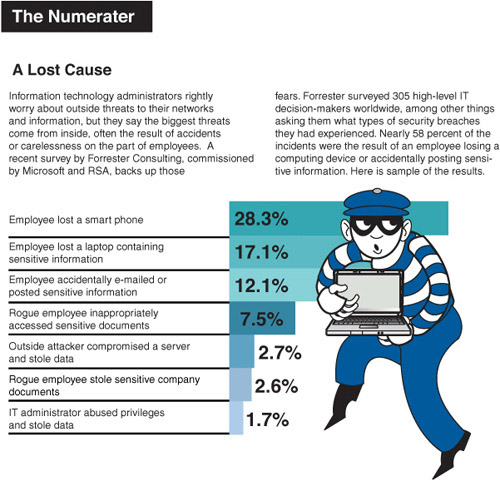
In a 2010 survey of 305 CIOs conducted by Forrester Research, nearly 58 percent of security breaches were the result of an employee’s losing a computing device or accidentally posting information on social networks.10 Figure 4.2, from the Forrester report, breaks down employee security breaches by type.
Figure 4.2 Types of employee security breaches
Investing in the People and the Process
Technology will continue to flow into our businesses, and with that comes its inevitable flaws. Although the customers can’t completely control how the software is developed, they can control how it is customized and managed once it’s part of the IT infrastructure.
From an organizational point of view, this is best achieved through investments in the people and processes behind the technology. Following are suggestions for making the most of these IT investments.
A Company-Wide IT Council
Although the majority of the responsibility for technology rests with the IT department, it shouldn’t end there. Many companies create cross-functional teams when they begin an extensive IT project, and these teams often are disbanded when the project goes live. They may regroup when something goes awry, but typically they don’t meet on a regular basis. Other times, an entirely different team is assembled to evaluate a so-called new solution. These can be valuable in the short term, but they aren’t entirely efficient or cost-effective if there are inconsistent views on how technology will be introduced and managed in a company.
A company-wide IT council would fairly represent each part of the organization on an ongoing basis and would continue to steer the direction of the technology that’s in place to support the larger business goals.
Third-Party Auditing
Aside from what may be required by compliance regulations, more frequent audits on the IT infrastructure are worth considering. All too often we get caught up in our day-to-day activities and are too close to the technology to gain an unbiased view of what works, what could be improved, and where potential glitches may be lurking in the infrastructure. This audit would be conducted by external professional services consultants. They would be responsible for conducting customer feedback surveys and evaluating the IT infrastructure from a business and technical perspective.
IT Asset Inventory
An annual or biannual inventory of what exactly is in the infrastructure can help identify redundant technologies, ease the strain on the network for inactive applications and tools, and help efforts associated with documenting the code. Just be mindful that the inventory process is only to determine what is currently in place. It shouldn’t disrupt the infrastructure until the cross-company IT council deems it appropriate.
Putting IT All Together
Having a deeper understanding of the complexities of the IT infrastructure will help companies derive more value from their technology investments.
Regardless of the current trends and hot acronyms that are being bandied about, the core aspects of building and sustaining a sound IT infrastructure are based on a solid foundation and the ability to enforce policies and procedures to strengthen that foundation.
With those guiding principles in place, a company can easily add more technology to the infrastructure without disrupting productivity or compromising customer satisfaction.
Endnotes
1. Capitalizing on Complexity. Insights from the 2010 IBM Global CEO Study. May 2010.
2. “The Digital Universe Decade.” IDC Digital Universe Study sponsored by EMC. April 26, 2010.
3. Institute of Electronic Business E12 Conference. Lars Kirchhoff. December 1, 2008.
4. Interview with Steve Mills, IBM, by Jeff Papows. December 2009.
5. Electronics. “Cramming More Components onto Integrated Circuits.” Gordon Moore. Volume 38, Number 8, April 19, 1965.
6. IBM. “Understanding 64-Bit PowerPC Architecture.” http://www.ibm.com/developerworks/library/pa-microdesign/.
7. Intel® Itanium® 9300 Processor Raises Bar for Scalable, Resilient Mission-Critical Computing. http://www.intel.com/pressroom/archive/releases/2010/20100208comp.htm.
8. Interview with Elizabeth Grealy, Grealy Globalization Enterprises, by Kathleen Keating. May 2010.
9. The New Hackers Dictionary, 3rd Edition. Eric S. Raymond. MIT Press, 1996.
10. The Value of Corporate Secrets. How Compliance and Collaboration Affect Enterprise Perceptions of Risk. Forrester Research. March 2010.
