Chapter 6. The Mobility and Network Maze
“Great discoveries and improvements invariably involve the cooperation of many minds. I may be given credit for having blazed the trail, but when I look at the subsequent developments I feel the credit is due to others rather than to myself.”
—Alexander Graham Bell
While disruptive technologies, monopolies, investors, and first-mover advantage were the talk of the ’90s, they also were quite the center of attention in the ’70s—the 1870s.
After all, the invention of the telephone led to some of the biggest technology disruptions of the 20th century. Alexander Graham Bell was one of many inventors who believed that the telegraph’s ability to send and receive messages through code could be expanded to include transmitting voice.
Bell was naturally inquisitive and partially inspired by his future father-in-law’s financial incentive to disrupt Western Union’s telegraph monopoly. His invention of the telephone set in motion the rudimentary beginnings of today’s voice and data communications.
Fast-forward to today. The telephone has migrated from a static tool to a mobile device that’s like an appendage for many of us. Yet the infrastructure to support the mobile explosion faces serious challenges. This chapter explores the following topics:
• The increasing dependence on mobile technologies
• The impact of mobile access on the evolving IT infrastructure
• Sustaining an infrastructure to support current and future technologies
The Increasing Dependence on Mobile Technologies
Advances in mobile devices are driving up the dependence on mobile technologies despite the fragility of cell phones and wireless connectivity. The infrastructures to support them will be further strained in the near future as a result of the growth of the mobile Internet and the rise of teleworkers.
The Growth of the Mobile Internet
There’s no denying the increase in connectedness to corporate infrastructures and the Internet using smartphones, tablet computers, laptops, and other mobile devices. Just one small slice of this market, smartphones, is growing at a rapid pace. Table 6.1 illustrates just how quickly the smartphone market grew from 2008 to 2009.1
Table 6.1 Worldwide Mobile Phone Sales, 2008 and 2009
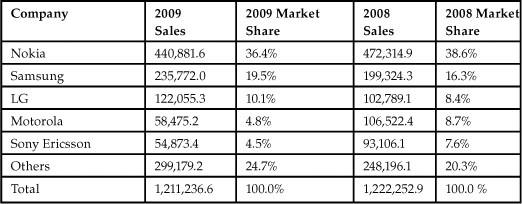
The prospects for continued prosperity in the smartphone market are strong and indicate that smartphones are increasingly being used to download and share information. This makes sense, considering that the growth in the mobile device market has been exponentially faster than any previous computing technology.2 Not to mention the highly successful launch of Apple’s iPad in 2010, which also relies on the infrastructure to access information, videos, music, and games.
Speaking of the infrastructure strain, as you may recall, the iPad launch was followed by concerns about AT&T’s ability to handle the additional network demands the new product would create. Five days after the iPad launch, Phil Bellaria and John Leibovitz of the Federal Communications Commission (FCC) posted the following on their blog:
“With the iPad pointing to even greater demand for mobile broadband on the horizon, we must ensure that network congestion doesn’t choke off a service that consumers clearly find so appealing, or frustrate mobile broadband’s ability to keep us competitive in the global broadband economy.”3
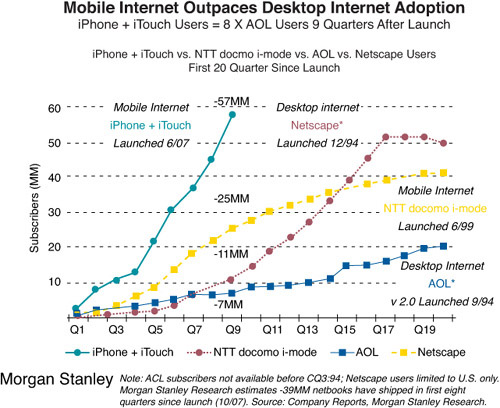
What all of this adds up to is a rapidly growing mobile Internet that will be bigger than the desktop Internet by 2015. Figure 6.1 illustrates how the mobile Internet is outpacing desktop Internet adoption.4 But can the networks keep up with the demand? If not, what are the consequences of failure?
Figure 6.1 Morgan Stanley: mobile Internet outpaces desktop Internet adoption
Frustrated Carriers, Frustrated Consumers
With the rising adoption rates of mobile devices comes a decline in the quality of service and performance offered by the carriers. A 2010 consumer satisfaction survey conducted by J.D. Power and Associates found that the biggest issues with quality of service involve dropped calls, interference, failed connections, voice distortion, echoes, and lack of immediate notification of voicemail and text messages.5
As consumers rely more on their mobile devices to download data as opposed to using them for person-to-person calls, the issues of access, bandwidth, and network reliability come to the forefront.
In December 2009, AT&T President and Chief Executive Officer, Mobility and Consumer Markets Ralph de la Vega spoke about the issue of bandwidth availability at the UBS 37th Annual Global Media and Communications Conference. de la Vega told financial analysts that the “amount of growth and data that we are seeing in wireless data is unprecedented.”6
de la Vega explained that AT&T is considering various options to address its service issues. Although he didn’t provide full details, public reports mention that efforts are under way to add 2,000 cell sites,7 and there is the potential for a tiered pricing structure. Additionally, AT&T is aiming to further educate consumers about their data consumption through the “Mark the Spot” iPhone application, which lets users report problems such as dropped calls and spotty coverage.
In his speech, however, de la Vega also stated that three percent of AT&T smartphone customers represent 40 percent of the network’s data traffic.8 In outlining how AT&T can more effectively handle the traffic, he said, “We’re going to try to focus on making sure we give incentives to those small percentages to either reduce or modify their usage so they don’t crowd out the customers on those same cell sites.”
Many consumers interpreted AT&T’s efforts to educate customers about data consumption as a request to decrease data downloads. Shortly after AT&T addressed the UBS audience, technology industry journalist Dan Lyons introduced “Operation Chokehold” through his satirical blog, The Secret Diary of Steve Jobs.9 Initially meant to be a joke, following is the text from the blog post:
Subject: Operation Chokehold
On Friday, December 18, at noon Pacific time, we will attempt to overwhelm the AT&T data network and bring it to its knees. The goal is to have every iPhone user (or as many as we can) turn on a data intensive app and run that app for one solid hour. Send the message to AT&T that we are sick of their substandard network and sick of their abusive comments. The idea is we’ll create a digital flash mob. We’re calling it Operation Chokehold. Join us and speak truth to power!
It wasn’t long before Operation Chokehold had more than 4,000 Facebook fans and the FCC got involved. Jamie Barnett, the FCC’s Chief of Public Safety and Homeland Security, read the following statement to ABC News:
FCC Statement in Response to Operation Chokehold
“Threats of this nature are serious, and we caution the public to use common sense and good judgment when accessing the Internet from their commercial mobile devices. To purposely try to disrupt or negatively impact a network with ill intent is irresponsible and presents a significant public safety concern.”10
Although Lyons wrote some additional blog posts regarding less extreme alternatives to Operation Chokehold, this was one message that made its way through the network. In this instance, both the consumers and the service provider have a point. As customers rely more and more on their mobile devices, they expect unlimited data access, as outlined in their contracts. Meanwhile, the service providers are doing their best to respond to consumer demand, yet they can be hindered by their own infrastructures.
The Rise of Teleworkers
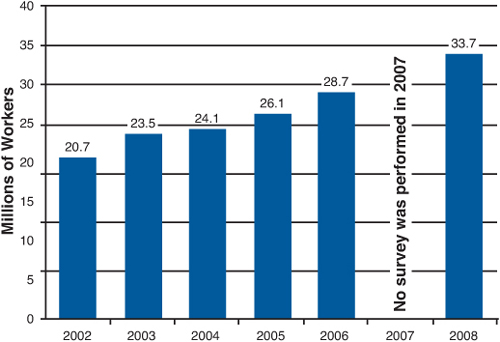
With collaboration software and mobile devices everywhere, as well as increased awareness of our carbon footprint, it’s easy to understand the rise in the number of teleworkers. Figure 6.2 shows this steady increase from 2002 to 2008.11
Figure 6.2 U.S. teleworkers: WorldatWork Telework Trendlines 2009 survey brief, February 2009
The network traffic from teleworkers isn’t completely about the number of employees trying to remotely log on to the company intranet or check their e-mail. It’s more about their role as knowledge workers and how much data they are downloading, creating, and sending to colleagues. If you’ve ever patiently waited for a large presentation or audio file to open on your desktop, you know how critical bandwidth and speed are to productivity.
Since we can expect that the number of telecommuters will continue to increase, we need to be sure that our infrastructures really can accommodate this growing population in the workforce. For many employers, this isn’t just about accommodating the ability to work from home on an intermittent basis. This is about the war for talent and making sure you can effectively recruit and retain the best employees for your team, regardless of where they choose to live.
Supporting the Road Warriors
Legions of employees such as insurance investigators, ambulance drivers, and sales reps typically don’t work in a traditional office but depend on the speed and resiliency of the network, quality of data, and available bandwidth capacity for their livelihood. Following are two examples that illustrate the importance of a sound infrastructure to support employees on the road. The first example is from the commercial trucking industry, and the second is from the New York City police department.
Data Quality in Commercial Trucking
Perhaps you’ve seen a truck stuck under a bridge or an 18-wheeler trying to back up on a busy stretch of road. These types of maneuvers often lead to accidents because the drivers are unfamiliar with the area or have inaccurate information about the route. Even though professional truck drivers possess a truck-specific global positioning system (GPS) and a mobile device, they need to be assured that the software that generates the routes doesn’t contain a glitch and that they can instantly connect to the office network in the event of an emergency.
For example, when the I-35W Mississippi River bridge collapsed on August 1, 2007, it affected river, road, bicycle, and pedestrian passageways as well as air transit.12 Professional truckers who were customers of Maptuit, a supplier of realtime commercial navigation software, were rerouted within minutes. Had the update to the truckers on that route been stalled due to a network capacity issue or faulty data, the trucks could have potentially blocked ambulances from entry to the site, thereby compounding the already tragic scene in Minneapolis. Not to mention the impact on the goods in transport and their company’s bottom line.
According to Rick Turek, chief technology officer at Maptuit, it’s the responsibility of management to explain to software developers the ramifications of a glitch if the code they’re working on will eventually play a role in the business and personal lives of others. Turek explains, “When it comes to our software development processes, every member of the team understands that a mistake can impact the physical well-being of the driver. It can also potentially cost a trucking fleet millions of dollars.”
Technology shortcomings, whether they are due to flawed software or simply the limitations of the devices themselves, should not be discovered as hazardous materials or other precious cargo is en route.
Sorry, Wrong House Raid
The other example of how a computer glitch can have an impact on the safety of citizens happened to 83-year-old Walter Martin and his 82-year-old wife, Rose. The law-abiding Brooklyn, New York couple were the victims of a computer glitch that started when the police department tried to automate its computer system that tracks crime complaints and internal police information.13
The glitch that got into the New York City police department’s database in 2002 resulted in 50 raids on the Martins’ home over a period of eight years. When the police input the names of suspects into its database, the glitch directed them to the Martins’ home. The definitive source of the glitch was never confirmed, yet it’s likely that a criminal suspect either lived in the home at one point or provided it as a false address.
The Martins have since been assured that the glitch has been fixed. But these types of missteps can distract our police and other public servants from protecting citizens who actually need help.
The situation with the Martins is not a straightforward mobile glitch. However, when you think about the validity of the data that law enforcement officers rely upon as they perform their jobs outside of traditional office walls, you realize how a seemingly simple glitch can have a strong ripple effect.
The Impact of Mobile Access on the Evolving IT Infrastructure
Just as we are seeing a surge in our connectedness as individuals, we’re also seeing a rise in businesses’ reliance on remote access to the IT infrastructure. As much as we can recognize the productivity benefits of this fact, we are also further straining our infrastructures due to limited bandwidth. Let’s take a closer look at these influences, which include the following:
Cloud Computing
More and more companies that were previously limited by technical and financial resources are taking advantage of subscription-based software offerings, also known as software as a service (SaaS). Supported by the cloud computing platform, SaaS is a way to host applications and services on a shared, sometimes remote server, and access them through a “cloud.” Those applications and services ideally can be accessed from nearly any computer anywhere in the world.
If you’ve been around technology for a while, you know that the concept of cloud computing is not new. Businesses have consistently relied on shared resources—specifically, networks—to house information in the interest of saving money.
Yet cloud computing makes access to applications and services easier and cheaper and further reduces the costs of managing those applications internally. This is ideal for applications that are used by many employees and that don’t require intensive programming to make them work. Some of these applications include word processing and spreadsheets, as well as sales-related tools and customer relationship management packages.
At first it appeared that cloud computing was ideal for small businesses that wanted to alleviate the work associated with application management and the associated high administration costs and licensing fees. However, large organizations also see significant cost savings and efficiency benefits in making part of their infrastructure available through a cloud.
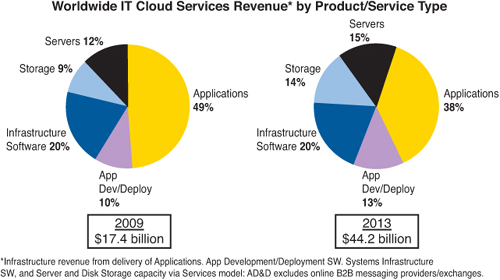
It’s clear that the cloud computing market is poised for continued growth as more companies adopt it as part of their IT strategy. According to a research report from IT industry analysts at IDC, revenue from cloud computing is expected to reach over $44.2 billion by 2013.14 Figure 6.3 breaks down the revenue from this segment according to product/service type.
Figure 6.3 Cloud computing revenue growth through 2013
The immediate questions for many business professionals with regard to cloud computing are the safety and security of their data when it’s not located on their premises. This genuine concern is why we are seeing and hearing more conversations about public versus private clouds. With private clouds, companies can reap the same benefits of the cloud model, but they don’t share any of the applications with any other company, as is the case with public clouds.
Whether using a public or private cloud environment, the end user still needs to go through the Internet for information or applications that are located in one of those clouds. This further underscores the importance of a sound infrastructure to support the influx of network traffic.
As IT analyst and blogger Joe McKendrick pointed out, “Many organizations—and departments within organizations—are becoming both providers and consumers of services. Some organizations or vendors will still publish more than they consume, and others will consume more than they publish. But the lines are getting blurrier all the time.”15
Should faulty software practices make their way into a cloud, they might impact a wider audience than a more traditional on-premises model of software ownership. Therefore, we need to be that much more diligent when it comes to developing the applications and services that will be accessed via a cloud.
The Mobile Cloud
Meanwhile, software developers are writing code specifically to support the growing demand for mobile applications, a market that is expected to reach $9.5 billion by 2014—an 88 percent leap from 2009.16 To the average user, the mobile application runs just as it would on his or her laptop or desktop computer, yet all the power to run the application comes from the cloud, not the mobile device. Behind the scenes, this requires some tweaking to the code to make those applications accessible on the go.
Although 75 percent of today’s mobile cloud-based application market caters to the enterprise user,17 we can expect demand from the consumer market in the near future. This demand will be driven by technology innovations that are currently under way. They will make it easier to conduct commerce and banking transactions via mobile devices, resulting in the global accumulation of 6.5 billion mobile connections by 2014.18
The Full Spectrum
At the risk of oversimplifying the process, sending and transmitting data from device A to device B usually involves several different networks before the message reaches its final destination.
Whether one network is stronger than another is less important than the fact that speed and delivery are based on the frailty of the weakest link in the chain. Some networks are more reliable than others, but all are ultimately limited by the amount of available spectrum. In layman’s terms, this means that there is a greater likelihood that we will have more trouble connecting and downloading through our mobile devices in the near future before the situation improves.
This issue was made clear when FCC chairman Julius Genachowski addressed an audience at the Cellular Telecommunications Industry Association (CTIA) conference in October 2009. He stated, “I believe that the biggest threat to the future of mobile in America is the looming spectrum crisis.”19
To put things in perspective, as of December 2009, approximately 834MHz of total spectrum was available. However, the FCC believes that most of this will primary be taken by year end 2010. Making things a bit more complicated is Genachowski’s prediction that total wireless consumption could grow from 6 petabytes a month as of November 2009 to 400 petabytes per month by 2013. This is the data equivalent of the entire written works of mankind from the beginning of recorded history in all languages—times eight.
You may wonder why we can’t just make more spectrum available. Think of spectrum as a very busy city bus during rush hour, when only so many seats are available. Building new buses takes time and involves technology, business, and government. So some folks will get seats, others will have to stand for part of the ride, and still others will have to wait for the next bus.
The situation is certainly not as cut-and-dried as it may sound. The FCC’s 2011 budget of $352.5 million includes a proposal for a National Broadband Plan for better and more widespread coverage and improved public safety. It also contains recommendations for indefinitely extending the authority of the FCC to auction spectrum licenses.20 Although many of us may take for granted our constant connectedness, a very real threat is looming due to limited spectrum. It is holding back our ability to offer better-quality health care, emergency medical care, and education in many remote areas.
Sustaining an Infrastructure to Support Current and Future Technologies
In my conversation with IBM Senior Vice President Steve Mills about the broadband issue, Mills said, “We as a society are getting a lot of information from physical mobile devices and collecting and analyzing that information to make everyday things smarter. We need to get creative and make the infrastructure we depend upon work better and last longer.”21
Two points are key to sustaining our infrastructures to accommodate the continued growth of the mobile market:
• Improved infrastructures to support the network
Additional Network Capacity
As many IT and business professionals are aware, network capacity can be added in many ways. Separate from the spectrum issue, adding network capacity is about making the most of your existing network. It’s like trying to pack a suitcase for a long trip where you need to take everything that’s on your list, so you have to carefully arrange how it will all fit together.
Short-term improvements that we’re likely to see over the next few years include offloading traffic via WiFi and femtocell or upgrading to the high-speed packet access (HSPA) standard. Longer-term improvements include the long-term evolution (LTE) fourth-generation mobile broadband standard and an optimized spectrum. Let me explain those industry terms from a more pedestrian point of view.
In basic terms, WiFi is short for wireless fidelity. Users with WiFi-enabled computers and mobile devices can access the Internet through a wireless network, which is separate from a fixed network. It’s like having an additional faucet in your house. This can help offload the network strain, because users are spread out across a network or are on an entirely different network.
However, the busier the location in terms of people who want to jump on the wireless network, the harder it can be to access the Internet. The service providers are aware of this issue, and efforts are under way to create more hotspot networks to accommodate even more wireless access. For example, in May 2010, AT&T tested a WiFi hotspot pilot program in New York City’s Times Square. AT&T wanted to address smartphone and device traffic and to test the feasibility of creating more of these hotspots without draining its already overloaded network.22
A femtocell is a small base station that can sit in your home or small business. It improves broadband connections for customers while improving the service provider’s coverage and capacity. It does this by relocating communications activities from the licensed cellular spectrum to a less expensive wireless option of voice over Internet protocol (VoIP). If you’ve ever had a conversation through your computer using Skype, the Internet voice and video communications service, you’ve experienced VoIP technology. Figure 6.4 shows a femtocell.23

The HSPA standard allows for higher data transfer speeds and more capacity. It also reflects the latest innovations in making the transmission of data through a network as quick and efficient as possible.
LTE is the highly anticipated standard for mobile voice based on its global roaming capabilities across different operators. It is not the same as HSPA. In terms of growing interest in supporting LTE, 15 public safety organizations of the National Public Safety Telecommunications Council (NPSTC) have already unanimously voted to endorse it. They hope to build a nationwide, interoperable broadband network that will further enhance communications in the event of an emergency.24
Improved Infrastructures to Support the Network
These efforts to advance the network infrastructure to support the overall growth in Internet adoption and widespread mobile device usage could be hindered if the infrastructure that is supposed to support the network is fractured.
As Mills told me, this will not be easy, especially when you consider this comment from him: “So much of IT investments are allocated to maintaining the networks. You want to add to what’s there without diminishing what exactly you can use, and you want to make your infrastructure require less maintenance and less repair.”
Many variables are involved in addressing bandwidth, capacity, and spectrum availability. Software can’t solve every network congestion problem, nor can it better fortify the physical pipes and wires that transmit messages. However, software can make the most of our existing infrastructures if applied appropriately. Various software applications and tools categorized under operations support systems (OSSs) and business support systems (BSSs) are designed to help telecommunications providers do the following:
• Optimize network speed
• Reduce traffic
• Prioritize traffic according to size
• Monitor capacity and performance
• Prevent dropped messages and calls
However, with evolving infrastructures, new standards, various applications, and services already on the network, upgrading to support the latest standards such as LTE or HSPA is not as simple as adding new technology. One of the biggest challenges is that wireless networks typically contain various tools, components, and software from different vendors. Sometimes these technologies can be easily integrated, and other times they can’t.
As new technologies are introduced to accommodate the growth in mobile connectivity, applying IT governance practices to software development can improve the integrity of the network infrastructure. This applies to the vendor developing the OSSs/BSSs as well as the company that is aiming to upgrade its network. In this regard, IT governance can support the development of the software that is critical to sustaining the wireless network. More specifically, it can help do the following:
• Maximize network capacity by identifying gaps or redundancies that lead to congestion
• Ease integration of new technologies by proactively identifying development errors before they become part of the final code
• Illustrate the impact of changes on the infrastructure before the new system goes live
Cruise Control in the Fast Lane
There’s no stopping the amount of data that continues to be generated on a daily basis, and our reliance on mobile technology will only increase. For companies that want to better manage customer expectations from a business and consumer perspective, the following four actions are recommended:
• Initiate consumer and employee education efforts with regard to how we may be inadvertently straining the network when we unnecessarily run data-intensive applications on our mobile devices. This doesn’t mean that we shouldn’t continue to use these devices; it means that we need to be aware of when they’re actively pulling from the network, unbeknownst to us. I liken this to leaving the lights on in your home all day when you won’t be there.
• Conduct a thorough evaluation of the current state of the IT infrastructure and readiness to support new industry standards. This includes streamlining unnecessary traffic patterns that exist in the network, addressing redundancies in software and tools, and mapping the necessary integration efforts that will need to be executed.
• Actively participate in industry standards bodies to help steer direction where appropriate and to better prepare for the pending infrastructure changes.
• Elevate the role of IT governance to support the increase in exchanges that will take place in the cloud, through social networks and company collaboration tools.
As I think about the mobile industry, I recall the first time I saw a cell phone, which was probably back in the 1980s. It was about the size of a tennis shoe, weighed about as much as a college textbook, and cost about $1,000.
When I think about how far we’ve come in mobile technologies in such a short time, I have an even deeper respect for the collective efforts that have enabled us to be more productive in our work, more efficient in our emergency responses, and more in touch with our families and friends.
Enabling these efforts to continue to flourish is the responsibility of all facets of the IT industry, not just the service provider or the mobile device manufacturer. It will require continuous commitment from leaders across business, technology, and government.
Endnotes
1. Gartner. “Competitive Landscape: Mobile Devices, Worldwide, 4Q09 and 2009.”
2. Morgan Stanley. “Mobile Internet Report.” December 2009.
3. Blogband: The Official Blog of the National Broadband Plan. “Message from the iPad: Heavy Traffic Ahead.” http://blog.broadband.gov/blog/index.jsp?entryId=138385.
4. Morgan Stanley. “Mobile Internet Report.” December 2009.
5. J.D. Power and Associates 2010 Wireless Call Quality Performance Study, Volume 1.
6. New York Times. “AT&T to Urge Customers to Use Less Wireless Data.” Jenna Wortham. December 9, 2009.
7. AT&T Fact Sheet. Network Performance. http://www.att.com/Common/merger/files/pdf/AT&TNetworkPerformance.pdf.
8. AT&T. UBS 37th Annual Global Media and Communications Conference. December 9, 2009.
9. The Secret Diary of Steve Jobs. http://www.fakesteve.net/2009/12/operation-chokehold.html.
10. ABC News. “Operation Chokehold”: Did iPhone Protest Against AT&T Succeed?
11. Telework Trendlines™ 2009 Report. WorldatWork.org.
12. Minnesota Department of Transportation. National Transportation Safety Board Investigation. November 14, 2008. http://www.dot.state.mn.us/i35wbridge/.
13. Associated Press. “Cops: Computer glitch led to wrong address.” March 19, 2010.
14. International Data Corporation. “IDC’s Cloud Services: Global Overview.” September 2009.
15. Interview with Joe McKendrick by Jeff Papows. February 2010.
16. Juniper Research. “Mobile Cloud Applications & Services: Monetising Enterprise and Consumer Markets 2009–2014.” January 2, 2010.
17. Ibid.
18. Gartner press release. Gartner Highlights Key Predictions for IT Organizations and Users in 2010 and Beyond. January 13, 2010.
19. CTIA IT & Entertainment Conference. Keynote: Julius Genachowski. October 7, 2009.
20. Federal Communications Commission. National Broadband Plan. http://www.broadband.gov.
21. Interview with Steve Mills by Jeff Papows. December 2009.
22. AT&T press release. AT&T Launches Pilot Wi-Fi Project in Times Square. May 25, 2010.
23. Picture of Motorola femtocell. Source: Motorola.
24. National Public Safety Telecommunications Council press release. http://www.npstc.org/documents/Press_Release_NPSTC_Endorses_LTE_Standard_090610.pdf.
