Chapter 4. Security and Risk Management
Terms you’ll need to understand:
![]() Security governance principles
Security governance principles
![]() Compliance
Compliance
![]() Regulation
Regulation
![]() Laws that address software licensing and intellectual property
Laws that address software licensing and intellectual property
![]() Professional ethics
Professional ethics
![]() Threat
Threat
![]() Vulnerability
Vulnerability
![]() Security and risk management
Security and risk management
![]() Single loss expectancy (SLE)
Single loss expectancy (SLE)
![]() Annual rate of occurrence (ARO)
Annual rate of occurrence (ARO)
![]() Residual risk
Residual risk
![]() Annual loss expectancy (ALE)
Annual loss expectancy (ALE)
Topics you’ll need to master:
![]() Calculations used for risk management
Calculations used for risk management
![]() Approved approaches to good security management
Approved approaches to good security management
![]() How to perform qualitative risk analysis
How to perform qualitative risk analysis
![]() How to perform quantitative risk analysis
How to perform quantitative risk analysis
![]() How to perform hybrid risk analysis
How to perform hybrid risk analysis
![]() Good resource protection
Good resource protection
![]() The role of security policies, procedures, guidelines, and baselines
The role of security policies, procedures, guidelines, and baselines
![]() Proper data classification
Proper data classification
![]() Proper implementation of security roles
Proper implementation of security roles
![]() How to perform risk calculations
How to perform risk calculations
Introduction
The security and risk management domain identifies data classification and evaluation. This domain also introduces security governance and protection of intellectual property. Each of these is driven by documents that include policies, procedures, and guidelines. These documents are of great importance because they spell out how the organization manages its security practices and details what is most important to the organization. These documents are a roadmap, demonstrating the level and amount of governance an organization has. These documents are not developed in a void. Senior management must lead by driving this process. Senior management has the vision, knows the overall goals of the organization, and knows the mission of the organization.
This chapter goes into more depth in discussing the two techniques used to calculate risk: qualitative and quantitative. The key to mastering this domain is understanding these two processes. Is one method better than the other? No, both quantitative and qualitative risk assessment methods have advantages and disadvantages. It is important that the CISSP candidate understand the differences, and how each can be used to address threats, assess risk potential, and evaluate the organization’s vulnerabilities.
Finally, it’s important not to forget the employees. Employees play a key part in this process. They are tasked with carrying out the policies implemented by management. Although the workers of the organization will want to do the right thing and help the company succeed, they must be trained. This training can be on a wide range of topics, from ethics, to acceptable use, to social engineering. Training helps employees know what the proper actions are and understand the security practices of the organization. The overall goal of this domain, like the others you have studied, is to ensure confidentiality, integrity, and availability of an organization’s assets and information.
Security Governance
Security management has changed throughout the years. In the 1970s, the focus was on computer security, whereas in the 1980s and 1990s, the focus shifted to data and information security systems. Only during the last few years have more organizations begun to look at security more holistically.
Today, there is a focus on governance, which encompasses all of security. Good governance requires total enterprise protection, often referred to as a holistic enterprise security program, which includes physical, logical, and administrative components. Luckily for security management, there are many guidance documents available to help build an effective security management program. Some examples of these include:
![]() Government recommendations—NIST SP 800-30, NIST SP 800-55, and NIST SP 800-100
Government recommendations—NIST SP 800-30, NIST SP 800-55, and NIST SP 800-100
![]() Security configuration recommendations—The NSA Security Configuration Guides and RFC 2196, The Site Security Handbook
Security configuration recommendations—The NSA Security Configuration Guides and RFC 2196, The Site Security Handbook
![]() Standards—ISO 17799, Trusted Computer System Evaluation Criteria (TCSEC), Information Technology Security Evaluation Criteria (ITSEC), and Common Criteria (CC) regulations such as United States Health Insurance Portability and Accountability Act (HIPAA) and Sarbanes-Oxley (SOX)
Standards—ISO 17799, Trusted Computer System Evaluation Criteria (TCSEC), Information Technology Security Evaluation Criteria (ITSEC), and Common Criteria (CC) regulations such as United States Health Insurance Portability and Accountability Act (HIPAA) and Sarbanes-Oxley (SOX)
Risk management is the ultimate requirement in support of all information security activities. One of the key documents that can be used to achieve this goal is ISO/IEC 27002. It is considered a code of practice for information security. ISO 27002 provides the best practice guidance on information security management. It is divided into 12 main sections:
![]() Risk assessment and treatment
Risk assessment and treatment
![]() Security policy
Security policy
![]() Organization of information security
Organization of information security
![]() Asset management
Asset management
![]() Human Resources security
Human Resources security
![]() Physical and environmental security
Physical and environmental security
![]() Communications and operations management
Communications and operations management
![]() Access control
Access control
![]() Information systems acquisition, development, and maintenance
Information systems acquisition, development, and maintenance
![]() Information security incident management
Information security incident management
![]() Business continuity management
Business continuity management
![]() Compliance
Compliance
ISO 27002 is written for the individuals responsible for initiating, implementing, and/or maintaining information security management systems. Its goal is to provide a template for protectors, provide technical guidance, and to help train those tasked with protecting the organization’s assets.
Third-Party Governance
Governance is not just about managing in-house processes; it is also about managing external entities. Third-party governance must verify compliance with all stated security objectives, requirements, regulations, and contractual obligations that have been agreed upon. As reliance on third parties continues to grow so does the need to manage these relationships. Some of the documents used for third-party governance are listed here:
![]() Interconnection Security Agreement (ISA)—A security document that specifies the requirements for establishing, maintaining, and operating an interconnection between systems or networks. The document lists the requirements for connecting the systems and networks, and details what security controls are to be used to protect the systems and sensitive data. An ISA typically maintains a drawing of the network topology and details how specific systems and networks are connected.
Interconnection Security Agreement (ISA)—A security document that specifies the requirements for establishing, maintaining, and operating an interconnection between systems or networks. The document lists the requirements for connecting the systems and networks, and details what security controls are to be used to protect the systems and sensitive data. An ISA typically maintains a drawing of the network topology and details how specific systems and networks are connected.
![]() Interoperability Agreement (IA)—A document that specifies any and all requirements for creating and maintaining requirements for companies to be able to exchange data. As an example, United Airlines may code-share flights with Hawaiian Airlines, so both need access to a common data set.
Interoperability Agreement (IA)—A document that specifies any and all requirements for creating and maintaining requirements for companies to be able to exchange data. As an example, United Airlines may code-share flights with Hawaiian Airlines, so both need access to a common data set.
![]() Memorandum of Understanding (MOU)—This documents specifies terms and conditions for outsourcing partner organizations that must share data and information resources. To be legally binding, the MOU must be signed by a representative from each organization that has the legal authority to sign. Such documents are typically secured, as they are considered confidential.
Memorandum of Understanding (MOU)—This documents specifies terms and conditions for outsourcing partner organizations that must share data and information resources. To be legally binding, the MOU must be signed by a representative from each organization that has the legal authority to sign. Such documents are typically secured, as they are considered confidential.
![]() Authorization to Operate (ATO)—A formal statement that authorizes operation and agrees to accept any and all risks.
Authorization to Operate (ATO)—A formal statement that authorizes operation and agrees to accept any and all risks.
![]() Continuity of Operations (COOP)—Things will go wrong and when they do the COOP specifies the processes and procedures that organizations must put in place to ensure that businesses can continue to operate.
Continuity of Operations (COOP)—Things will go wrong and when they do the COOP specifies the processes and procedures that organizations must put in place to ensure that businesses can continue to operate.
![]() Service Level Agreement (SLA)—Sometimes used in conjunction with an ISA or MOU. If the outsourcing provider with which you have signed an MOU is going to provide a time-sensitive service, an SLA is one way to obtain guarantees of the level of service the partner is agreeing to provide. The SLA should specify the uptime, response time, and maximum outage time that the provider is agreeing to. For a service fee, the provider agrees to repair or replace the equipment within the contracted time.
Service Level Agreement (SLA)—Sometimes used in conjunction with an ISA or MOU. If the outsourcing provider with which you have signed an MOU is going to provide a time-sensitive service, an SLA is one way to obtain guarantees of the level of service the partner is agreeing to provide. The SLA should specify the uptime, response time, and maximum outage time that the provider is agreeing to. For a service fee, the provider agrees to repair or replace the equipment within the contracted time.
![]() Operating Level Agreement (OLA)—Functions in conjunction with SLAs in that it supports the SLA process. The OLA defines the responsibilities of each partner’s internal support group. For example, the SLA may promise no more than five minutes of downtime, while the OLA will define which group and resources will be used to meet that downtime goal.
Operating Level Agreement (OLA)—Functions in conjunction with SLAs in that it supports the SLA process. The OLA defines the responsibilities of each partner’s internal support group. For example, the SLA may promise no more than five minutes of downtime, while the OLA will define which group and resources will be used to meet that downtime goal.
![]() Uptime Agreement (UA)—Details the agreed amount of uptime, usually as a percentage. For example, UAs can be used for network services, such as a WAN link, or equipment, such as a server. It’s common to see uptimes like 99.999%, which is equal to about five minutes’ downtime per year.
Uptime Agreement (UA)—Details the agreed amount of uptime, usually as a percentage. For example, UAs can be used for network services, such as a WAN link, or equipment, such as a server. It’s common to see uptimes like 99.999%, which is equal to about five minutes’ downtime per year.
![]() Nondisclosure Agreement (NDA)—Used to protect confidential information. For example, before taking the CISSP exam, you will be asked to sign an NDA stating that you will not reveal exam questions to others.
Nondisclosure Agreement (NDA)—Used to protect confidential information. For example, before taking the CISSP exam, you will be asked to sign an NDA stating that you will not reveal exam questions to others.
![]() Business Partnership Agreement (BPA)—A legally binding document that is designed to provide safeguards and compel certain actions among business partners in relation to specific security-related activities. The BPA is a written agreement created by lawyers along with input from the partners; it contains standard clauses related to security and cooperation.
Business Partnership Agreement (BPA)—A legally binding document that is designed to provide safeguards and compel certain actions among business partners in relation to specific security-related activities. The BPA is a written agreement created by lawyers along with input from the partners; it contains standard clauses related to security and cooperation.
Note
One item that should be reviewed when dealing with business partners is the Statement of Auditing Standards 70 (SAS 70). The SAS 70 report verifies compliance and that the outsourcing or business partner has had its control objectives and activities examined by an independent accounting and auditing firm.
Organization Processes
Risk management requires an understanding of the organization and its time-sensitive business requirements. It’s also a fact that nothing stays static in business. Organizational units change, products and services are added and removed, and portions of a business may be spun off or divested. Let’s discuss some of the common types of events that a security professional may have to deal with.
First, there are mergers and acquisitions. A merger can be defined as the combination of two or more commercial entities into a single surviving entity. From the standpoint of risk, there are many things that can go wrong. Businesses typically look for synergy, but some businesses just don’t fit together. Regardless of the situation, some questions must be asked before the merger. Is the merger a win for both companies? Is the purpose of the merger to siphon off resources, such as talent and intellectual property, and then spin off a much weaker company later?
Sometimes companies enter a merger–acquisition phase without an adequate plan of action. This can potentially lead to security exposures and increased expenditures.
Lastly, many people don’t like change. Once a company culture is established and people become set in their ways, attitudes can be hard to change. Mergers are all about change, and that goes against the grain of what many employees expect.
For the security professional it’s common to be asked to quickly establish connectivity with the proposed business partner. While there is a need for connectivity, security should remain a driving concern. You need to understand the proposed merger partner’s security policies and what controls they are enforcing. The last thing you would want to allow is an attacker’s entry into your network through the merging company’s network.
There will always be security concerns when it comes to merging diverse companies You should also be concerned with items such as the following:
![]() Rules—What is or is not allowed by each individual company.
Rules—What is or is not allowed by each individual company.
![]() Policies—High-level documents that outline the security goals and objectives of the company.
Policies—High-level documents that outline the security goals and objectives of the company.
![]() Regulations—Diverse entities may very well be governed by different regulatory entities or regulations, such as PCI or HIPAA.
Regulations—Diverse entities may very well be governed by different regulatory entities or regulations, such as PCI or HIPAA.
![]() Geography—A company that is located in London, England will be operating on different standards than one that is based in San Jose, California.
Geography—A company that is located in London, England will be operating on different standards than one that is based in San Jose, California.
![]() Demerger/divestiture—Any time businesses break apart you have many of the same types of issues to deal with.
Demerger/divestiture—Any time businesses break apart you have many of the same types of issues to deal with.
![]() Trust or clearance level—The level of access or control of any current or new employees accessing information.
Trust or clearance level—The level of access or control of any current or new employees accessing information.
![]() Skill set, training, and awareness—Level of users and employee training with access to company information systems.
Skill set, training, and awareness—Level of users and employee training with access to company information systems.
Protection of Intellectual Properly
Although the laws discussed in the following list are specific to the United States, intellectual property is agreed on and enforced worldwide by various organizations, including the United Nations Commission on International Trade Law (UNCITRAL), the European Union (EU), and the World Trade Organization (WTO). International property laws protect copyrights, patents trademarks, and trade secrets. These were discussed in some detail in Chapter 2.
The length of a copyright in the United States and the European Union is life plus 70 years.
Privacy Laws and Protection of Personal Information
Privacy laws are of critical importance because technology has simplified the process of accumulating large amounts of data about individuals. Commercial and government databases contain tremendous amounts of data that can be used to infringe on people’s sense of privacy and anonymity. The misuse of these databases can lead to targeted advertising and disclosure of personal preferences that some individuals believe is intrusive. Privacy is increasingly being recognized as a fundamental right in many countries and organizations that hold personal information are being required to protect it.
The European Union has been on the forefront in developing laws that protect individual privacy. The European Union deals with privacy on the federal level and has a department called the Data Protection Authority. This authority has the power to enforce privacy directives. E.U. privacy guidelines enacted in 1998 state the following:
![]() Data is to be used only for the purposes for which it was collected and within a reasonable time.
Data is to be used only for the purposes for which it was collected and within a reasonable time.
![]() If requested, individuals are entitled to receive a report on data about them.
If requested, individuals are entitled to receive a report on data about them.
![]() An individual’s personal data cannot be disclosed to third parties unless authorized by statute or consent of the individual.
An individual’s personal data cannot be disclosed to third parties unless authorized by statute or consent of the individual.
![]() Persons have a right to make corrections to their personal data.
Persons have a right to make corrections to their personal data.
![]() Transmission to locations where equivalent personal data protection cannot be assured is prohibited.
Transmission to locations where equivalent personal data protection cannot be assured is prohibited.
The European Union has also implemented a concept known as the right to be forgotten. It has been in practice in the European Union and Argentina since 2006. On request, information that is irrelevant, private, or no longer relevant should be removed from Internet searches.
In the United States, the federal government reacts only to obvious abuses when they are reported. Privacy laws are driven by government actions.
The Fourth Amendment of the United States Constitution is the basis of privacy law in the United States. Two laws worth noting are the Privacy Act of 1974 and the Identity Theft and Assumption Deterrence Act of 1998. The Privacy Act of 1974 limits the personal information a federal agency can collect, maintain, and disclose. The Identity Theft and Assumption Deterrence Act of 1998 raises the penalties for identity theft and establishes that the person whose identity was stolen is a true victim. Before passage of this act, only a credit grantor who suffered monetary losses was considered a victim.
Even with these laws in place, there is still a large amount of information that can be obtained about individuals in the United States. To get a better idea about what types of information are available, take a moment to review Table 4.1. Although most of these sites will give you some information for free, for just a few dollars you can get much more. This is just a short list; there are many more sites from which to gather personal information.
Note
Although the United States and the European Union take a different approach to privacy, U.S. companies handling information from customers based in the European Union must be aware of the European Commission’s 1998 Directive on Data Protection (Safe Harbor), and provide a standard for privacy protection equal to what would be provided in the European Union.
Relevant Laws and Regulations
Security professionals should be aware of the laws that pertain to them locally and understand terms such as due care and due diligence. Due care is taking reasonable care to protect the assets of an organization. For example, think of it as information gathering. Doing the right thing over a period of time—implementation—is considered due diligence.
The CISSP exam does not test you on country-specific laws, but you should have an understanding of laws in your region of the world. The following laws are mentioned briefly:
![]() Computer Fraud and Abuse Act (CFAA) of 1986—Amended in 1996, it now makes distribution of malware illegal. It deals with computers used by the federal government, but can include others.
Computer Fraud and Abuse Act (CFAA) of 1986—Amended in 1996, it now makes distribution of malware illegal. It deals with computers used by the federal government, but can include others.
![]() Federal Sentencing Guidelines of 1991—Provides guidelines to judges so that sentences are handed down in a more uniform manner for crimes dealing with computers.
Federal Sentencing Guidelines of 1991—Provides guidelines to judges so that sentences are handed down in a more uniform manner for crimes dealing with computers.
![]() Economic Espionage Act of 1996—Defines strict penalties for those accused of espionage.
Economic Espionage Act of 1996—Defines strict penalties for those accused of espionage.
![]() U.S. Child Pornography Prevention Act of 1996—Enacted to combat and reduce the use of computer technology to produce and distribute child pornography.
U.S. Child Pornography Prevention Act of 1996—Enacted to combat and reduce the use of computer technology to produce and distribute child pornography.
![]() U.S. Patriot Act of 2001—Strengthens computer crime laws to expand law enforcement’s capability to fight terrorism; has been the subject of some controversy.
U.S. Patriot Act of 2001—Strengthens computer crime laws to expand law enforcement’s capability to fight terrorism; has been the subject of some controversy.
United States Legal System and Laws
The U.S. legal system can trace its roots to the United Kingdom. The United States, United Kingdom, and Canada all use a common law system. Common law is based on previous rulings and principles such as stare decisis—the concept that court cases that are similar should be decided in a consistent manner. Common law also recognizes the rule of reasonable doubt and that a defendant is innocent until proven guilty. Categories of common law include:
![]() Criminal law—Criminal law exists to punish someone who violates the government’s laws and is therefore considered to have committed crimes against society. Cases are brought forth by the state or federal government. Punishment can include financial penalties, imprisonment, or both. Broadly speaking, felonies are more serious crimes that can result in large fines and more than one year of imprisonment, while misdemeanors are less serious crimes that result in smaller fines and no more than one year of imprisonment. Penalties for both are designed to punish criminals and deter criminal activity.
Criminal law—Criminal law exists to punish someone who violates the government’s laws and is therefore considered to have committed crimes against society. Cases are brought forth by the state or federal government. Punishment can include financial penalties, imprisonment, or both. Broadly speaking, felonies are more serious crimes that can result in large fines and more than one year of imprisonment, while misdemeanors are less serious crimes that result in smaller fines and no more than one year of imprisonment. Penalties for both are designed to punish criminals and deter criminal activity.
![]() Civil law—Civil law has no ability to prescribe prison time. Cases are brought forth by victims or those individuals who believe they have been wronged. Victims are compensated by means of financial awards of punitive, compensatory, or statutory damages if the defendant is found guilty. Punitive damages are determined by a jury. Compensatory damages are payments based on actual damage, whereas statutory damages are awarded based on law and preset limits.
Civil law—Civil law has no ability to prescribe prison time. Cases are brought forth by victims or those individuals who believe they have been wronged. Victims are compensated by means of financial awards of punitive, compensatory, or statutory damages if the defendant is found guilty. Punitive damages are determined by a jury. Compensatory damages are payments based on actual damage, whereas statutory damages are awarded based on law and preset limits.
![]() Administrative (regulatory) law—Administrative law establishes standards of performance and conduct that governmental agencies expect from industries, organizations, officials, and officers. Individuals and organizations that violate these laws can be punished by financial penalties and/or imprisonment. These laws typically apply to industries such as health care, financial, industrial, petrochemical, and pharmaceutical.
Administrative (regulatory) law—Administrative law establishes standards of performance and conduct that governmental agencies expect from industries, organizations, officials, and officers. Individuals and organizations that violate these laws can be punished by financial penalties and/or imprisonment. These laws typically apply to industries such as health care, financial, industrial, petrochemical, and pharmaceutical.
International Legal Systems and Laws
Legal systems vary throughout the world regarding the rights of the accused, the role of the judge, the nature of evidence, and other essential legal concepts. Claims and cases can be handled quite differently; Figure 4.1 shows an example of where some of these various systems are used in the world.
Much of Europe is based on civil (code) law, also known as Napoleonic law. Civil law evolved in Europe from around the time of the Roman Empire. The Romans used Corpus Juris Civilis, which featured a comprehensive system of written rules of law that serves as the basis of civil law used today. The major difference between civil law and common law is that civil law uses legislation as the main source of legal rulings in court cases.
Religious law is based on religious tenets. Examples include halakha in Judaism and sharia in Islam. The Islamic system is an autonomous legal system based on religious tenets and references items found in the Qur’an. China and some African countries use customary law, which is based on the concept of what is considered customary and normal conduct.
If two or more of these legal systems are combined, the result is a mixed law system. Mixed law systems are noted for their inclusion of more than one type of legal framework and might feature components of two or more basic types. As an example, Louisiana has features of both civil law and common law, whereas parts of the Middle East mix customary law with religious law.
This international patchwork of legal systems is superimposed on international property laws that affect data handling, so although the CISSP exam will most likely focus on common law, it is important that the CISSP candidate understand the differences between the various legal systems used around the world.
Computer Crime and Hackers
Hackers are one of the threats that CISSPs must be prepared to deal with. It’s commonly thought that only one tenth or so of all the computer crimes committed are detected. How could this be true? It is difficult to develop accurate numbers regarding the detection and reporting of computer crime. Many crimes go undetected and others are detected but never reported to law-enforcement agencies or the general public. Some companies are worried about a possible negative reputation and the loss of customers; others are afraid that it might make them appear vulnerable. One good source of information about computer crime and data breaches is at www.informationisbeautiful.net/, which has a list of the top data breaches for each year, as shown in Figure 4.2.
There are multiple attack vectors for computer crime:
![]() Physical security attack—Physically accessing systems
Physical security attack—Physically accessing systems
![]() Personnel security attack—Harassing, extorting, or threatening employees
Personnel security attack—Harassing, extorting, or threatening employees
![]() Communications attack—Eavesdropping on wired, wireless, or satellite communications
Communications attack—Eavesdropping on wired, wireless, or satellite communications
![]() Logical attack—Logically accessing systems
Logical attack—Logically accessing systems
![]() Social engineering attack—Tricking employees or others into providing access or information
Social engineering attack—Tricking employees or others into providing access or information
No discussion of computer crime would be complete without a review of the criminals. Most security professionals think of computer criminals as hackers. Originally, the term hacker was used for a computer enthusiast who enjoyed understanding the internal workings of a system, computer, and computer network. Over time, the popular press began to describe hackers as individuals who broke into computers with malicious intent. The industry responded by developing the term cracker, which is short for criminal hacker. The term was meant to describe individuals who seek to compromise the security of a system without permission from an authorized party; however, the public continues to use the term hacker to describe the computer criminal. There are actually many other terms that can be used to identify the criminal and to categorize criminal activities, including the following:
![]() Phreakers—The original hackers. These individuals hacked telecommunication and PBX systems to explore their capabilities and make free phone calls.
Phreakers—The original hackers. These individuals hacked telecommunication and PBX systems to explore their capabilities and make free phone calls.
![]() Script kiddies—A term used to describe younger attackers that use widely available, freeware vulnerability assessment tools and hacking tools that are designed for attacking purposes only. These attackers typically have very limited programming or hacking skills and depend on tools written by others.
Script kiddies—A term used to describe younger attackers that use widely available, freeware vulnerability assessment tools and hacking tools that are designed for attacking purposes only. These attackers typically have very limited programming or hacking skills and depend on tools written by others.
![]() Disgruntled employees—Employees who have lost respect for the employer and act accordingly. These individuals might or might not have more skills than script kiddies. Insiders or former insiders are a real risk because of the knowledge they have or the access they might possess.
Disgruntled employees—Employees who have lost respect for the employer and act accordingly. These individuals might or might not have more skills than script kiddies. Insiders or former insiders are a real risk because of the knowledge they have or the access they might possess.
![]() Cyberterrorists/cybercriminals—Individuals or groups who are typically funded to conduct clandestine or espionage activities on governments, organizations, and people in an unlawful manner. These individuals are typically engaged in sponsored acts of defacement, DoS/DDoS (Denial of Service/Distributed Denial of Service) attacks, identity theft, financial theft; they may also compromise critical infrastructure, such as nuclear power plants, electric plants, water treatment plants, and so on.
Cyberterrorists/cybercriminals—Individuals or groups who are typically funded to conduct clandestine or espionage activities on governments, organizations, and people in an unlawful manner. These individuals are typically engaged in sponsored acts of defacement, DoS/DDoS (Denial of Service/Distributed Denial of Service) attacks, identity theft, financial theft; they may also compromise critical infrastructure, such as nuclear power plants, electric plants, water treatment plants, and so on.
![]() Corporate spy/government spy—Elite hackers who have specific expertise in attacking vulnerabilities of systems and networks. These attackers can be differentiated by their level of skill. These individuals know what they want and will go to great lengths to get it. They have no interest in making a public name for themselves, which sets them apart from hackers of years ago who were motivated by notoriety.
Corporate spy/government spy—Elite hackers who have specific expertise in attacking vulnerabilities of systems and networks. These attackers can be differentiated by their level of skill. These individuals know what they want and will go to great lengths to get it. They have no interest in making a public name for themselves, which sets them apart from hackers of years ago who were motivated by notoriety.
If you want to learn more about hacking and all the players in the security realm, such as hackers, security professionals, and law enforcement, consider local options such as ISSA and INFRAGARD or security conferences such as Black Hat or DEF CON. Conferences are one of the ways you can gain ISC2 continuing professional education (CPE) credits and learn more about current security trends and exposures.
Sexual Harassment
United States law requires companies to provide a safe workplace where employees are free from sexual harassment and offensive behavior. Therefore, companies that fail to enforce acceptable use policies (AUPs) could find themselves in legal jeopardy.
Risk Management Concepts
Risk management is the systematic ongoing approach to analyzing risk, identifying threats, and implementing controls to mitigate risk. With any new topic, the terminology and semantics used within the context of the technology can be confusing, misused, and misrepresented. Risk management should be driven by senior management, who appoint someone to lead the risk assessment process.
When senior management is driving the process, a company has top-down support for a security program; this is the preferred method. Sometimes senior management might not see the value of a structured risk assessment process. In these situations, a bottom-up process might still be able to drive the risk assessment process.
It is imperative that individuals driving the risk assessment gain the support of senior management. One common technique to secure senior management commitment and support is by educating them using a formal presentation. Presentations can communicate key aspects of the overall risk management program and remind senior management that they are ultimately responsible.
A major part of risk management includes developing the risk-management team, identifying threats and vulnerabilities, placing a value on the organization’s assets, and determining how you will deal with the risk you uncover.
After senior management is on board, the risk management process can begin. The goal of this process is that the organization build the controls necessary to protect the organization’s staff and assets, while meeting stakeholder expectations.
Risk Management Frameworks
The risk management framework supports the risk management process. As an example, British Standard BS 31100 provides guidance on the objectives, mandate, and commitment to manage risk. Another example is NIST Special Publication 800-37, “Guide for Applying the Risk Management Framework to Federal Information Systems”, which details a six-step risk management framework (RMF). These steps are listed below and are shown in Figure 4.3:
![]() Categorize
Categorize
![]() Select
Select
![]() Implement
Implement
![]() Assess
Assess
![]() Authorize
Authorize
![]() Monitor
Monitor
Some of the other approaches to risk management and assessment that have been developed include:
![]() Factor analysis of information risk (FAIR)—An approach to risk management that develops baselines of probabilities for the frequency and magnitude of loss events. It’s considered an add-on to existing risk frameworks.
Factor analysis of information risk (FAIR)—An approach to risk management that develops baselines of probabilities for the frequency and magnitude of loss events. It’s considered an add-on to existing risk frameworks.
![]() Risk factor analysis—Another approach to risk analysis that uses a six-step methodology to identify factors that drive the behavior of the project schedule, cost, and technical performance.
Risk factor analysis—Another approach to risk analysis that uses a six-step methodology to identify factors that drive the behavior of the project schedule, cost, and technical performance.
![]() Probabilistic risk assessment—Designed for use with large-scale complex projects where risk is defined as a feasible detrimental outcome of an activity or action. The results are expressed numerically.
Probabilistic risk assessment—Designed for use with large-scale complex projects where risk is defined as a feasible detrimental outcome of an activity or action. The results are expressed numerically.
Note
A risk register is one of the tools that can be used to act as a repository of identified risk and the nature of each risk. You can see an example of one here: www.slideshare.net/KashifMastan/risk-register-34631122
Risk Assessment
A risk assessment, unlike risk management, has a start and stop date. It is the process of identifying and prioritizing risks to a business. Completion of this assessment is crucial. Without it, you cannot design good security policies or procedures to defend your company’s critical assets. Risk assessment requires individuals to take charge of the risk-management process.
First, let’s define the basic concepts of risk, threat, and vulnerability.
Risk is the probability or likelihood of an occurrence or realization of a threat. There are three basic elements of risk from an IT infrastructure perspective:
![]() Asset—A component or an item of value to an organization, such as data assets.
Asset—A component or an item of value to an organization, such as data assets.
![]() Threat—Any circumstance that could potentially cause loss or damage to an asset.
Threat—Any circumstance that could potentially cause loss or damage to an asset.
![]() Vulnerability—A weakness in infrastructure, design, or components that might be exploited by a threat to destroy, damage, or compromise an asset.
Vulnerability—A weakness in infrastructure, design, or components that might be exploited by a threat to destroy, damage, or compromise an asset.
A threat is any agent, condition, or circumstance that could potentially cause harm, loss, damage, or compromise to an asset. From an IT perspective, threats can be categorized as circumstances that can affect the confidentiality, integrity, or availability of an asset. Threats can be natural, man-made, or technical. Threats can result in destruction, disclosure, modification, or corruption of corporate resources, or can cause a denial of service.
A vulnerability is a weakness in the design of a product, a weakness in the implementation of a product, or a weakness in how the product’s software or code was developed. Vulnerabilities can be reduced or even possibly eliminated by the implementation of safeguards, controls, and security countermeasures.
Note
Controls are mechanisms used to restrain, regulate, or reduce vulnerabilities. Controls can be corrective, detective, preventive, or deterrent.
Before you start to fret over how one person could ever accomplish this task alone, understand that risk management is a big job. You’ll need co-workers and employees from other departments to help. To do an effective job of risk management analysis, you must involve individuals from all the different departments of the company. Otherwise, you run the risk of not seeing the big picture.
It’s hard for any one person to understand the inner workings of all departments. Sure, as an IT or security administrator, you understand the logical risks the IT infrastructure faces, but do you really have a grasp of the problems HR might have? These might include employee controls, effective termination practices, and control of confidentiality information. Bringing in key employees from other functional areas is required if you expect the risk management process to be successful. Consider including employees from each of the following groups in a risk management team:
![]() Information system security
Information system security
![]() IT and operations management
IT and operations management
![]() System and network administration
System and network administration
![]() Internal audit
Internal audit
![]() Physical security
Physical security
![]() Business process and information owners
Business process and information owners
![]() Human Resources
Human Resources
![]() Physical safety
Physical safety
Asset owners should also be represented on the team. Because the asset owners are responsible for assets, they should have a voice in the types of controls that are implemented. Having asset owners on the team ensures the team is aware of, and can address, the many threats it will need to examine.
The team must also be kept informed and guided by personnel knowledgeable about the legal and regulatory requirements of the organization. As an example, some teams are established specifically to examine ways to decrease insurance costs, reduce attacks against the company’s technical infrastructure, or even to verify compliance with government standards such as GLBA, SOX, or HIPAA.
After the risk management team has been established, their tasks are to
1. Perform asset valuation
2. Perform threat analysis
3. Perform quantitative or qualitative risk assessment
4. Choose remedial measures
5. Reduce, assign, or accept the risk
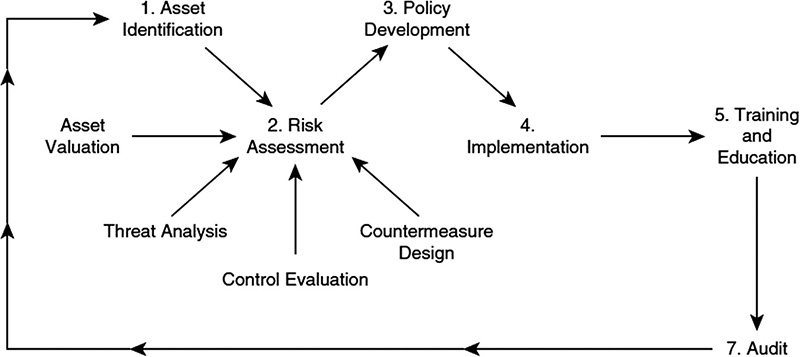
The key security management practices necessary to assess risk have been broken into six broad steps shown here and in Figure 4.4:
1. Asset identification
2. Risk assessment
3. Policy development
4. Implementation
5. Training and education
6. Auditing the security infrastructure
Now that we have created a risk management team that has the support of senior management, let’s examine the methods used to place a value on assets.
Asset Identification and Valuation
The next step is to list the value of organization’s assets. A proper asset valuation enables the organization’s risk management team to start making business decisions regarding deployment of security controls and security countermeasures.
One of the most important steps for securing an organization’s assets is to identify and inventory all of those assets. For example, imagine you work for a bank that is in charge of protecting a customer database containing names, Social Security numbers, and addresses. You would want to place a much higher level of control over these assets than you would another database that contained locations, manager names, and phone numbers of all your bank’s local branches. Yet you would not know the level of protection if you were unaware of the database asset. Without a complete and accurate inventory of all assets, an asset valuation cannot be performed.
When recording information about the organization’s assets, you should record the following information:
![]() Identification
Identification
![]() Location
Location
![]() Risk
Risk
![]() Protection
Protection
![]() Owner
Owner
Assets can be both tangible and intangible. One final important aspect offered by documented asset management is demonstrated due care. To valuate an asset properly, appreciate that the value is often based on more than just the cost to create or purchase that item. Consider the following:
![]() What did the asset cost to acquire or create?
What did the asset cost to acquire or create?
![]() What is the liability should the asset be compromised?
What is the liability should the asset be compromised?
![]() What is the production cost should the asset be made unavailable?
What is the production cost should the asset be made unavailable?
![]() What is the value of the asset to competitors and foreign governments?
What is the value of the asset to competitors and foreign governments?
![]() How critical is the asset, and how would its loss affect the company?
How critical is the asset, and how would its loss affect the company?
![]() What skill sets and how many hours per day, week, or month are required to maintain this asset?
What skill sets and how many hours per day, week, or month are required to maintain this asset?
![]() What are the subsystems, applications, hardware, or software that this asset is dependent on?
What are the subsystems, applications, hardware, or software that this asset is dependent on?
After listing the values of assets, the team can consider the organization’s most critical systems, resources, applications, and data. This information provides the ability to prioritize investments for security controls and security countermeasures. Controls are not cost-free and require expenditure of limited funds. Most organizations must justify the investment needed for proper security controls and security countermeasures.
Without an asset valuation, it is difficult to understand a control’s return on investment (ROI), or the cost-benefit analysis pertaining to the investment in security countermeasures. Knowing the value of assets that you are trying to protect is also important because it would be foolish to exceed the value of the asset by spending more on the countermeasure than what the asset is worth, or spending more on a control than you stand to lose if a threat targets a vulnerability. A common problem is failing to take into account how the secondary and tertiary systems affect value assigned to key assets.
You can’t protect everything. When defining your scope, organizations have only limited funds and resources, so countermeasures must be strategically deployed to guard what has been deemed most critical. Focus is first given to protect assets that face high levels of risk as the consequence of events that result in high impact. An example of this can be seen in Figure 4.5.
Asset identification and evaluation is also needed for insurance purposes. An organization might determine that some risks should be transferred to third parties. As such, asset valuation offers the organization the capability to accurately assess its business insurance requirements. Starting around the year 2000, some companies actually started offering technical and cyber risk coverage, more popularly known as hacker insurance.
Threats Analysis
Earlier, we discussed how threats can have negative impacts on the organization. Now, let’s look at where these threats might originate. Threats can occur because of technical failures, natural factors, or be caused by humans, maliciously or accidentally. Identifying all potential threats is a huge responsibility. Instead of random brainstorming on potential threats, a somewhat easier approach is to categorize common types of threats (after all, why list a tornado if you live in Alaska):
![]() Natural catastrophes
Natural catastrophes
![]() Physical threat/theft
Physical threat/theft
![]() Human error/insider threat
Human error/insider threat
![]() Application error/buffer overflow
Application error/buffer overflow
![]() Equipment malfunction
Equipment malfunction
![]() Environmental hazards
Environmental hazards
![]() Malicious software/covert channels
Malicious software/covert channels
![]() Disclosure of confidential information
Disclosure of confidential information
![]() Stolen, lost, damaged, or modified data
Stolen, lost, damaged, or modified data
![]() Unauthorized access
Unauthorized access
![]() Terrorism
Terrorism
![]() Viruses, worms, and malware
Viruses, worms, and malware
![]() Denial of service
Denial of service
A threat coupled with a vulnerability and a threat agent can lead to a loss. Think of the threat agent as the individual or group that can manifest the threat. As mentioned earlier, vulnerabilities are flaws or weaknesses in security systems, software, or procedures. An example of a vulnerability is lack of employee training. This vulnerability might permit an improperly trained help desk employee to unknowingly give a password to a potential hacker. This could result in a loss. Examples of losses or impacts include:
![]() Financial loss
Financial loss
![]() Loss of reputation
Loss of reputation
![]() Endangerment or injury of staff, clients, or customers
Endangerment or injury of staff, clients, or customers
![]() Loss of business opportunity
Loss of business opportunity
![]() Breach of confidence or violation of law
Breach of confidence or violation of law
Losses might have immediate or delayed impact. A delayed loss has a negative effect on an organization well after the period of loss. This could perhaps be a few days, a few months, or even a few years. For example, an organization could have its website hacked and thus suffer an immediate loss. No e-commerce transactions can occur until technical support is brought in to rebuild the web server; all normal processing is halted. But these immediate losses might not be the only effects the company feels. Later, when the local news channel reports the company was hacked and that personal information was lost, the company could suffer from poor reputation and lose future customers. State laws vary, but some, such as California, might require the company to report the breach. Customers might remember this event for years to come, and now choose to use a competitor. These are examples of delayed loss.
Take a moment to review Figure 4.6, which displays the relationship among threats, vulnerabilities, and controls. Notice that a threat by itself does not represent a danger, and is not sufficient for a successful attack. A threat agent can be described as the actual circumstance or event that does cause harm to information assets through destruction, disclosure, or modification. Figure 4.6 uses a sample threat of a web application being hacked. The threat is the possibility that someone might hack the web application. The threat agent is the skilled hacker that will perform that attack. The vulnerability is the unpatched buffer overflow on the web application; and the risk is a measure of how probable it is that this attack will be successful.
Identifying threats, vulnerabilities, and controls is just part of the risk management process. Without placing dollar values or using some other metric to assess these variables, how can you start to analyze the threats and vulnerabilities that an organization faces? One approach is to develop a table such as the one shown in Table 4.2. This helps demonstrate the relationship among threats, vulnerabilities, and risks. For example, an intruder can represent a threat that might expose the organization to the theft of equipment because there is the vulnerability of no security guard or controlled entrance. We will look at dollar costs a little later in the chapter, but for now consider the relationship between these items.
The risk management team must gather input from a range of sources in order to identify threats. Sources that might be consulted or considered to help identify current and emerging threats include:
![]() Asset owners
Asset owners
![]() Network administrators
Network administrators
![]() Security administrators
Security administrators
![]() Operations group
Operations group
![]() Facility records
Facility records
![]() Government records and watchdog groups, such as CERT and Bugtraq
Government records and watchdog groups, such as CERT and Bugtraq
![]() Private organizations, such as SANS
Private organizations, such as SANS
Risk management can examine assets and their associated risks by dollar or non-dollar methods. Quantitative assessments assign a cost (monetary value) to assets and anticipated exposures caused by a threat identified in the risk analysis. Qualitative assessment methods use scenarios to drive a prioritized list of critical concerns, and do not focus on dollar amounts. Qualitative and quantitative assessment techniques are described more in the following two sections.
Quantitative and qualitative risk assessment can be combined for a hybrid risk assessment approach, which is more comprehensive.
Quantitative Assessment
Quantitative assessments deal with numbers and dollar amounts. The goal is to assign a cost or a numeric value to the elements of risk assessment and to the assets and threats of a risk analysis.
ExamAlert
When you hear the word quantitative, just remember “quantity.” This will help you remember that it’s numbers-based for the exam.
To fully complete a quantitative risk assessment, all elements of the process (asset value, impact, threat frequency, safeguard effectiveness, safeguard costs, uncertainty, and probability) are quantified. And that’s the problem with purely quantitative risk assessment: It is difficult, if not impossible, to assign dollar values to all elements. Therefore, some qualitative types of measurements often augment quantitative elements. A quantitative assessment requires substantial time and personnel resources. The quantitative assessment process involves:
1. Single Loss Expectancy (SLE)—This step involves determining the single amount of loss you could lose on an asset if a threat becomes realized. SLE is calculated as follows:
Single loss expectancy = Asset value × Exposure factor
Items to consider when calculating the SLE include the physical destruction or theft of assets, the loss of data, the theft of information, and threats that might cause a delay in processing. The exposure factor is the measure or percent of damage that a realized threat would have on a specific asset.
2. Annual Rate of Occurrence (ARO)—The purpose of an ARO is to determine the likelihood that an unwanted event will occur annually. Simply stated, how many times is this expected to happen in one year?
3. Determine annual loss expectancy (ALE)—This third and final step of the quantitative assessment seeks to combine the potential loss and rate per year to determine the magnitude of the risk. This is expressed as annual loss expectancy (ALE). ALE is calculated as follows:
Annualized loss expectancy (ALE) = Single loss expectancy (SLE) × Annualized rate of occurrence (ARO)
When performing the calculations discussed in this section, you should include all associated costs such as these and ensure that they are considered during SLE calculation:
![]() Lost productivity
Lost productivity
![]() Cost of repair
Cost of repair
![]() Value of the damaged equipment or lost data
Value of the damaged equipment or lost data
![]() Cost to replace the equipment or reload the data
Cost to replace the equipment or reload the data
Caution
What makes quantitative assessment difficult is that it is hard to place a dollar amount on every possible event and to extrapolate all the costs associated with that event.
When these costs are accumulated and specific threats are determined, the annualized loss expectancy can be calculated. This builds a complete picture of the organization’s risk and allows the organization to plan an effective strategy.
Review Table 4.3; we can work through the virus risk example given. First, calculate the SLE. The SLE requires that you multiply the asset value by the exposure factor:
$9,450 × 0.17 = $1,650
The asset value is the value you have determined the asset to be worth. The exposure factor is the amount of damage that the risk poses to the asset. For example, the risk-management team might consult with its experts and determine that 17% of Word documents and data could be destroyed from a virus.
Next, the ARO is calculated. The ARO is the frequency at which this event is expected to happen within a given period. For example, the experts might have determined that there is a 90% chance of this event occurring within a one-year period. These numbers are not always easy to determine because insurance and historical records, although helpful, do not always provide a complete picture. This is still a scientific guess with a degree of uncertainty.
Finally, the ALE is calculated. The ALE is the SLE multiplied by the ARO:
$1,650 × 0.90 = $1,485
This third and final step of the quantitative assessment seeks to combine the potential loss with the rate per year to determine the magnitude of the risk. You can interpret this figure to mean that the business should expect to lose an average of $1,485 each year due to computer viruses.
Automated tools that minimize the effort of the manual process are available. These programs enable users to rerun the analysis with different parameters to answer “what-ifs.” They perform calculations quickly and can be used to estimate future expected losses more easily than performing the calculations manually. Some individuals swear by these programs, whereas others are more comfortable verifying their results.
ExamAlert
Math is a big component of quantitative assessment; the CISSP exam might require you to use basic formulas on the exam such as SLE, ALE, and ARO. Memorizing and understanding these formulas will help you be fully prepared for the exam.
Qualitative Assessment
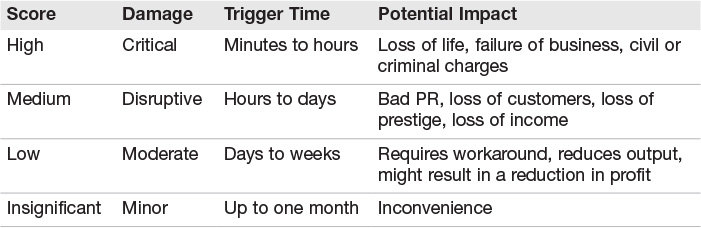
Maybe you are thinking that there has to be another way to perform an assessment. If so, you are right. Qualitative assessment is scenario-driven and does not attempt to assign dollar values to components of the risk analysis. Purely quantitative risk assessment is hard to achieve because some items are difficult to tie to fixed dollar amounts. Absolute qualitative risk analysis is possible because it ranks the seriousness of threats and sensitivity of assets into grades or classes such as low, medium, and high. Table 4.4 provides a sample qualitative scale.
It’s important to assign a consistent and subjective assessment of the risk to specific IT assets. This typically involves a group or team of members participating in the assessment. Asset owners responsible for maintaining the confidentiality, integrity, and availability of the IT asset should have a voice in the process. The basic steps for a qualitative assessment are:
1. List all the organization’s critical IT assets in a spreadsheet.
2. Specify the critical threats and vulnerabilities for each IT asset in the spreadsheet. There might be more than one critical threat or vulnerability for a given IT asset.
3. Develop a consistent exposure severity scale to measure impact. A value from the scale should be assigned according to the IT asset and the specific threat that can be exploited.
4. Organize and prioritize the risk assessment results from the most critical to the least. This will immediately bring to the top of the list those assets that have the greatest risk to exploitation from a threat or vulnerability.
5. Prioritize funds for security controls and security countermeasures for those IT assets that have the greatest importance to the organization, and have the greatest exposure to risk.
6. Ensure that the organization’s critical IT assets achieve the appropriate confidentiality, integrity, and availability controls according to the threat and security policy.
The result of the qualitative assessment process is this prioritized list, and might look something like the information provided in Table 4.5. Notice how facility power is identified as a critical concern.
A disadvantage of performing a qualitative assessment is that you are not working with dollar values, so it is harder to communicate the results of the assessment to management personnel, who are used to working with dollar amounts. However, qualitative assessments can be completed quickly.
Qualitative assessment is subjective, based on opinions from the team or experts in the company, but not always an exact assessment that senior management will want to receive from you. For example, when predicting the possibility for a natural disaster or even man-made incidents, one can never establish exact numeric certainty.
The Delphi technique is one approach to qualitative risk assessment. The Delphi technique uses a group approach designed to allow individuals to contribute anonymous opinions. The idea is to avoid being swayed by pushy people, to find synergy, and to allow participants to be honest.
Facilitated Risk Assessment Process (FRAP) is another subjective process that obtains results by asking questions. It is designed to be completed in a matter of hours, making it a quick process to perform. Qualitative assessments can use many techniques such as brainstorming, surveys, questionnaires, checklists, one-on-one meetings with asset owners, and interviews.
NIST provides another resource for qualitative risk assessment methodologies. NIST 800-53 defines confidentiality, integrity, and availability as categories of loss and then ranks each loss based on a scale of low, medium, and high. The ranking is subjective:
![]() Low—Minor inconvenience that could be tolerated for a short period of time.
Low—Minor inconvenience that could be tolerated for a short period of time.
![]() Medium—Could result in damage to the organization or cost a moderate amount of money to repair.
Medium—Could result in damage to the organization or cost a moderate amount of money to repair.
![]() High—Would result in loss of goodwill between the company and clients or employees. Could result in a legal action or fine or cause the company to lose revenue or earnings.
High—Would result in loss of goodwill between the company and clients or employees. Could result in a legal action or fine or cause the company to lose revenue or earnings.
Table 4.6 displays an example of how this assessment is performed. As you can see, no dollar amounts are used. Potential loss is only ranked as high, medium, or low.
Regardless of the method used, quantitative or qualitative, the results of the risk assessment process provide the team with the information needed to make a decision as to how to handle risk. Before moving on to that step, Table 4.7 summarizes the differences between quantitative and qualitative risk assessments.
There are many ways to perform a qualitative risk assessment. As an example, in New Zealand they use the ANZ 4360 standard for qualitative risk assessment.
Countermeasure Selection
After you have identified potential risk and estimated its impact, the team is tasked with determining how to compensate for the potential risk. There are three acceptable ways in which the team can respond:
![]() Risk acceptance addresses risk by accepting the potential cost of the loss if the risk occurs. This option can be chosen when no other options are available or the potential loss is small when compared to the project’s benefits. If this is the chosen path, it is important to prepare contingency plans to make sure you will be able to deal with the risk if it occurs. As an example, if your daughter was planning a wedding you might decide that because your daughter has her heart set on a summer wedding on the beach in the Bahamas, it might be best just to go along. After all, is it really wise to go against the wishes of your wife and your daughter? Although what she doesn’t know is that the hotel has agreed to allow you to hold the event indoors should the weather turn bad. Just knowing there is a contingency plan can make everyone feel a little better.
Risk acceptance addresses risk by accepting the potential cost of the loss if the risk occurs. This option can be chosen when no other options are available or the potential loss is small when compared to the project’s benefits. If this is the chosen path, it is important to prepare contingency plans to make sure you will be able to deal with the risk if it occurs. As an example, if your daughter was planning a wedding you might decide that because your daughter has her heart set on a summer wedding on the beach in the Bahamas, it might be best just to go along. After all, is it really wise to go against the wishes of your wife and your daughter? Although what she doesn’t know is that the hotel has agreed to allow you to hold the event indoors should the weather turn bad. Just knowing there is a contingency plan can make everyone feel a little better.
Note
Some sources list risk avoidance as an option. This simply means that you avoid the activity to avoid the risk. Depending on the situation, this may not be possible.
![]() Risk transference is another valid approach. Insurance is an example of risk transference. Insurance can be used to transfer a portion or all of the potential cost of a loss to a third party. To transfer the risk, you will move ownership of the risk to a third party. The third party assumes the risk but the organization is saddled with the cost of the insurance. Back to the example of the wedding, you could transfer some of the risk by buying hurricane, travel and hotel insurance. It should be understood in the real world risk transfer may be a viable option for a continuity of operations (COOP) plan to replace tangible items such as furniture, hardware, buildings, etc. for recovery operations following a disaster; however, it is a fallacy that this method for risk option will work for data protection and reputation. The best option for data protection is encryption and backups.
Risk transference is another valid approach. Insurance is an example of risk transference. Insurance can be used to transfer a portion or all of the potential cost of a loss to a third party. To transfer the risk, you will move ownership of the risk to a third party. The third party assumes the risk but the organization is saddled with the cost of the insurance. Back to the example of the wedding, you could transfer some of the risk by buying hurricane, travel and hotel insurance. It should be understood in the real world risk transfer may be a viable option for a continuity of operations (COOP) plan to replace tangible items such as furniture, hardware, buildings, etc. for recovery operations following a disaster; however, it is a fallacy that this method for risk option will work for data protection and reputation. The best option for data protection is encryption and backups.
![]() Risk mitigation could mean implementing a countermeasure to alter or reduce the risk. Examples of risk reduction include firewalls and encryption, increased frequency of patch management, and/or stronger authentication. Consider again the example of your daughter’s wedding. To reduce the risk, you might have asked her to postpone the wedding until next spring to reduce the possible ill effects of a major storm.
Risk mitigation could mean implementing a countermeasure to alter or reduce the risk. Examples of risk reduction include firewalls and encryption, increased frequency of patch management, and/or stronger authentication. Consider again the example of your daughter’s wedding. To reduce the risk, you might have asked her to postpone the wedding until next spring to reduce the possible ill effects of a major storm.
What approach is the right cost? That depends on the cost of the countermeasure, the value of the asset, and the amount by which risk-reduction techniques reduce the total risk to a value that is acceptable. Acceptable risk or risk tolerance is the minimum acceptable risk that an organization is willing to tolerate. When assessing safeguards, it’s important to look at the total cost of ownership (TCO). The TCO includes purchase price, maintenance fees, updates, insurance, etc. All costs are included. The risk assessment team must try to find a solution that provides the greatest risk reduction while maintaining the lowest annual cost. These concepts are expressed numerically by the following formula:
Threat × Vulnerability × Asset value = Total risk
No organization can ever be 100% secure. There will always be some risk left over. This is known as residual risk, the amount of risk left after safeguards and controls have been put in place. The formula for this concept is
(Threats × Vulnerability × Asset value) × Controls gap = Residual risk
The objective is to balance the cost of control against the value of the asset and potential for loss, and not to spend more on the control than the cost of the asset itself, as illustrated in Figure 4.7.
Note
Any risk involving human life is extremely high and should be given the highest priority.
At the completion of the risk-handling step, the risk assessment team will produce a final report that presents all the findings, information, assessments, and recommendations for the organization. The final assessment report becomes the instrument used by management to make sound business decisions pertaining to the organization’s overall risk and vulnerability assessment, and is the basis for how that organization will mitigate the identified risks, threats, and vulnerabilities.
Note
What’s cost-benefit analysis? The cost-benefit analysis of a safeguard or protection measure is measured as the control gap:
ALE before the safeguard – ALE after the safeguard = control gap (value of the safeguard to the organization).
This formula can be used to evaluate the cost-effectiveness of a safeguard or to compare various safeguards to determine which are most effective. The higher the resulting value is, the more cost-effective the safeguard is. Most organizations should avoid spending more funds on a control than the actual cost of the asset itself, but not always—private organizations and government agencies have different priorities. As an example, federal, state, and local government may sometimes provide controls to protect critical systems regardless of the cost of the controls. Often, it is not easy to measure the potential for damage with a numeric value as discussed previously.
Some organizations use a risk analysis matrix. A risk matrix looks at likelihood and impact. One example can be seen in MITRE’s Risk Matrix Users Guide.
Develop and Implement Security Policy
Security is truly a multilayered process. After an assessment is completed, administrative controls should be reviewed. Policies can be created or modified based on the results of the risk assessment. The assessment should help drive policy creation on items such as the following:
![]() Passwords
Passwords
![]() Patch management
Patch management
![]() Employee hiring and termination practices
Employee hiring and termination practices
Note
Low-level checks refer to checks completed for employees starting at low-level jobs. Before they move to a higher-level position, additional checks should be performed. Some companies are even moving to rolling and continuous background checks.
![]() Backup practices and storage requirements
Backup practices and storage requirements
![]() Security awareness training
Security awareness training
![]() Antivirus
Antivirus
![]() System setup and configuration
System setup and configuration
![]() System hardening
System hardening
For security to be effective, it must start at the top of an organization and permeate every level of the hierarchy. Senior management must make decisions on what should be protected, how it should be protected, and to what extent it should be protected. These findings should be crafted into written documents.
Before these documents are locked in as policies, they must be researched to verify that they will be compliant with all federal, state, and local laws. These documents should also clearly state what is expected from employees and how the company will deal with policy violations.
Security Policy
Policies are high-level documents developed by senior management to transmit the guiding strategy and philosophy of management to employees. Management and business process owners are responsible for the organization, and for designing policies that will guide it toward success. Policies apply a strong emphasis to words spoken by management. They define, detail, and specify what is expected from employees and how management intends to meet the needs of customers, employees, and stakeholders. Policies are high-level documents that provide a general statement about the organization’s assets and what level of protection they should have. Well-written policies should spell out who’s responsible for security, what needs to be protected, and what is an acceptable level of risk. They are much like a strategic plan because they outline what should be done but don’t specifically dictate how to implement the stated goals. Security policies can be written to meet advisory, informative, and regulatory needs. Each has a unique role or function. Table 4.8 shows the relationship of policies to strategic, tactical, and operational control.
One specific type of policy is the organization’s security policy. A security policy dictates management’s commitment to the use, operation, and security of information systems. It specifies the role security plays within the organization. A security policy should be driven by business objectives and should meet all applicable laws and regulations. It should also be used as a basis to integrate security into all business functions. It serves as a high-level guide to develop lower-level documentation such as procedures (see Figure 4.8). A security policy must be balanced in the sense that all organizations are looking for ways to implement adequate security without hindering productivity.
Caution
The key element of a policy is that it should state management’s intention toward security.
Policies can come in many forms. Policies can be advisory, informative, or regulatory. These are reviewed next and should help you understand how policies can be designed to meet a variety of goals.
Advisory Policy
The job of an advisory policy is to ensure that all employees know the consequences of certain behavior and actions. Here’s an example advisory policy:
Illegal copying: Employees should never download or install any commercial software, shareware, or freeware onto any network drives or disks unless they have written permission from the network administrator. Be prepared to be held accountable for your actions including the loss of network privileges, written reprimand, probation, or employment termination if the Rules of Appropriate Use are violated.
Informative Policy
This type of policy isn’t designed with enforcement in mind; it is developed for education to inform and enlighten employees. The following is an example informative policy:
In partnership with Human Resources, the employee ombudsman’s job is to serve as an advocate for all employees providing mediation between employees and management. This job is to help investigate complaints and mediate fair settlements when a third party is requested.
Good policy strikes a balance and is both relevant and understandable. If a policy is too generic, no one will care what it says because it doesn’t apply to the company. If a policy is too complex, no one will read it—or understand it if they did.
Regulatory Policy
These policies are used to make certain that the organization complies with local, state, and federal laws. Regulatory policy reinforces applicable laws to include applicable administrative laws, such as HIPAA, FERPA, and SOX; it also explains the applicable parts of specific laws in a way that the employees can understand. This is an area in which the CISSP should work closely with the HR and legal departments. A sample regulatory policy might state:
Because of recent changes to Texas State law, the Company will now retain records of employee inventions and patents for 10 years; all email messages and any backup of such email associated with patents and inventions will also be stored for 10 years.
Standards
Standards are much more specific than policies. Standards are tactical documents because they lay out specific steps or processes required to meet a certain requirement. As an example, a standard might set a mandatory requirement that all email communication be encrypted. Although the standard does specify encryption, it doesn’t spell out how it will be accomplished; this is left for the procedure.
Baselines
A baseline is a minimum level of security that a system, network, or device must adhere to. Baselines are usually mapped to industry standards. As an example, an organization might specify that all computer systems comply with a minimum Trusted Computer System Evaluation Criteria (TCSEC) C2 standard. TCSEC standards are discussed in detail in Chapter 5, “Security Engineering.” Your security policy might also address the minimum baseline standard for encryption requirements for sensitive data.
Guidelines
A guideline points to a statement in a policy or procedure by which to determine a course of action. It’s a recommendation or suggestion of how things should be done. It is meant to be flexible so that it can be customized for individual situations.
Caution
Don’t confuse guidelines with best practices. Whereas guidelines are used to determine a recommended course of action, best practices are used to gauge liability. Best practices state what other competent security professionals would have done in the same or similar situation.
Procedures
A procedure is the most specific of security documents. A procedure is a detailed, in-depth, step-by-step document that details exactly what is to be done. As an analogy, when my mom sent my wife the secret recipe for a German chocolate cake, it described step-by-step what needed to be done and how. It even specified a convection oven, which was listed as an absolute requirement.
Procedures are detailed documents that are tied to specific technologies and devices. You should expect to see procedures change as equipment changes. As an example, imagine that your company replaced its Check Point border device such as a firewall, VPN, or IDS with a Cisco border device. Although the policies and standards dictating the device’s role in your organization probably will not change, the procedure for configuration of the firewall will.
It’s unfortunate that sometimes instead of the donkey leading the cart, the cart leads the donkey. By this, I mean that sometimes policies and procedures are developed because of a negative event or an audit. The audit or policy shouldn’t be driving the process; the risk assessment should be. The assessment’s purpose is to give management the tools needed to examine all currently identified concerns. From this, management can prioritize the level of exposure they are comfortable with and select an appropriate level of control. This level of control should then be locked into policy.
Types of Controls
One of the main reasons to have a variety of control types is to provide the organization with true defense in depth. Each control type provides a different level of protection, and because each level can be tweaked to meet the needs of the organization, the security administrator has a very granular level of control over the security mechanisms. Security mechanisms can serve many purposes, although they are primarily used to prevent, detect, or recover from problems. The best approach is for the organization to focus the bulk of its controls on prevention because this allows the organization to stop problems before they start. The three access control types include administrative, technical, and physical controls.
Administrative Controls
Administrative controls are the policies and procedures implemented by the organization. Preventive administrative controls can include security awareness training, strong password policies, HR practices, and robust pre-employment checks.
Note
Does your company enforce acceptable use policies (AUPs)? AUPs are considered one of the best methods to deter unacceptable activity.
Technical Controls
Technical controls are the logical controls you have put in place to protect the IT infrastructure. Technical controls include strong authentication (biometrics or two factor), encryption, network segmentation, DMZs, and antivirus controls.
Physical Controls
Physical controls are the ones you can most likely see. These controls protect against theft, loss, and unauthorized access. Examples of physical access controls include guards, gates, locks, guard dogs, closed-circuit television (CCTV), and alarms.
Access Control Categories
Access controls can be used with different levels of granularity to provide more effective levels of control. The access control categories (as seen in Table 4.9) are as follows:
![]() Deterrent—Used to deter a security violation.
Deterrent—Used to deter a security violation.
![]() Preventive—Prevents the incident. An example of this control could be the use of encryption.
Preventive—Prevents the incident. An example of this control could be the use of encryption.
![]() Detective—Alerts and aids in identification after the incident.
Detective—Alerts and aids in identification after the incident.
![]() Corrective—Repairs damage and restores systems after the incident. An example might be applying patches.
Corrective—Repairs damage and restores systems after the incident. An example might be applying patches.
![]() Recovery—Restores normal operations. An example might be the deployment of backups.
Recovery—Restores normal operations. An example might be the deployment of backups.
![]() Compensating—Blunts the damage or acts to contain the event or incident.
Compensating—Blunts the damage or acts to contain the event or incident.
Note
Some items can fit in more than one category. Consider locks, which can be a delaying mechanism but can also be a deterrent.
Be sure you understand the three types of controls that can be used to limit access—administrative, technical, and physical—and what is contained within each set. This is required knowledge for the CISSP exam. The controls vary from domain to domain. On the actual exam be sure to read each question carefully.
Implement Personnel Security
An organization’s personnel security process should begin before the employee is ever hired. During the recruitment process, a prospective employee’s background needs to be reviewed to make sure the right person is hired for the job. Some items to review include:
![]() Background check
Background check
![]() Reference check
Reference check
![]() Educational verification/certification check
Educational verification/certification check
![]() Criminal, financial, and credit checks
Criminal, financial, and credit checks
![]() Driving record or other types of verification depending on the specific job
Driving record or other types of verification depending on the specific job
Performing these tasks up front can save the company time and money in the recruitment process and help prevent time and effort lost by hiring the wrong person for a job.
New-Hire Agreements and Policies
One great way to make sure your employees know what is expected of them is to perform a new-hire orientation. This is the time to discuss issues such as nondisclosure agreements (NDAs), good security practices, and AUPs. The goal of this training is to teach your employees your established security policies and procedures. The training should include the employee agreeing to and signing the AUP. Organizations benefit when each employee actively participates in the security of the organization.
Practices that keep employees focused on security include handing out pens, notepads, or other items that outline a few of the organization’s security policies. Companies should hold semiannual reviews that refresh employee’s knowledge of current policies and require updated signatures. Posters can help reinforce good security practices. Another idea is to send out periodic security-awareness emails or newsletters that reinforce the practices of good security.
Separation of Duties
Separation of duties describes the process of dividing duties so that one person cannot perform a critical task alone. This can mean having dual controls in place, which require more than one person to complete a critical task. This concept closely ties to the principle of least privilege, meaning you only give someone the minimum level of access or rights that are needed. As an example, some banks divide the safe combination numbers between two employees. Each employee has three of the six numbers needed to unlock the safe. Without some form of collusion, there is no way one person can obtain access to the safe’s contents.
Organizations that have titles, roles, and duties clearly defined by policy are able to better highlight conflicts of interest and develop a separation of duties matrix. Separation of duties usually falls into four areas of control:
![]() Authorization—Verifying cash, approving purchases, and approving changes
Authorization—Verifying cash, approving purchases, and approving changes
![]() Custody—Accessing cash, merchandise, or inventories
Custody—Accessing cash, merchandise, or inventories
![]() Record keeping—Preparing receipts, maintaining records, and posting payments
Record keeping—Preparing receipts, maintaining records, and posting payments
![]() Reconciliation—Comparing dollar amounts, counts, reports, and payroll summaries
Reconciliation—Comparing dollar amounts, counts, reports, and payroll summaries
Job Rotation
Although it’s always nice to have cross-trained employees, job rotation is about more than redundancy and control. Its primary benefit is that it allows an organization to maintain backup personnel to more easily identify fraudulent activities. For example, if John is stealing money from the company and Steve is rotated into John’s position and discovers such activities, only a deep friendship would keep Steve from telling the boss that John is a thief.
Least Privilege
The principle of least privilege is another important concept that can go a long way toward an organization achieving its security goals. Least privilege means that individuals have just enough resources to accomplish their required tasks.
As an example, imagine that your company has just added computer terminals to several of the conference rooms. These terminals have been placed where attendees of meetings, consultants, and sales representatives can access product information. Proper design dictates that these computers be allowed limited Internet access, but that all other Web activities be blocked. In other words, services such as network browsing, email, File Transfer Protocol (FTP), and Telnet are not available. This design reduces the opportunity for resource misuse.
Over time, even the principle of least privilege can result in authorization creep, which means that employees moving from job to job keep picking up more rights and access. Rights and access that are no longer needed should be removed.
Tip
Least privilege is not a concept strictly for individuals. In fact, it is extremely important to apply to sensitive systems, facilities, and applications. All applications and processes should run with the minimum amount of privilege necessary to avoid further exploitation in case they are ever compromised. A great example of this was Internet Information Services IIS. It used to operate with system permissions; this was way too much privilege for a web server. This issue has been corrected since Windows Server 2003 and IIS 6.0.
Mandatory Vacations
Even though everyone thinks it’s great that Jane hasn’t taken a vacation in 10 years, the fact that the accountant is always at work might be a problem. Jane appears to be a dedicated employee but might not have taken a vacation because she is performing fraudulent activities. By remaining on the job, she is able and available to provide cover for her scheme. Fraudulent activities are much easier to uncover when employees are required to take their vacations. Mandatory vacations provide time for audits and for illicit activities to be discovered.
Termination
Employees will eventually leave organizations for one reason or another. Employees might leave of their own free will or they might leave because they are terminated. Termination sometimes is necessary, but many surveys show that it is one of the most disliked tasks managers are required to do. To protect the organization, managers should use standardized termination procedures. This structured process helps ensure that everyone is treated equally and that employees don’t have the opportunity to destroy or damage company property. Some prudent steps to incorporate into this procedure include:
1. Disabling computer and facility access immediately at the time of notification.
2. Monitoring the employee while he or she packs belongings.
3. Ensuring that at no time is the employee left alone after the termination process has started.
4. Verifying that the employee returns company identifications and other company property, including access tokens, smart phones, and laptops.
5. Escorting the employee from the building.
What is most important is to avoid making this an adversarial process. Such situations only give employees more reasons to retaliate.
Security Education, Training, and Awareness
Employees look to their employers to provide training. Without proper training, employees are generally unaware of how their actions or activities can affect the security of the organization. One of the weakest links in security is the people who work for the company. Social engineering attacks prey on the fact that users are uneducated in good security practices; therefore, the greatest defense against these types of attacks is training, education, and security awareness (see Figure 4.9).
Besides security awareness, you might find that your staff needs more in-depth training in matters of organizational security. This might consist of in-house training programs that teach new employees needed security skills, or the decision to send the security staff offsite for a CISSP education program.
Tip
Employee-awareness programs work best when they are run for short periods and changed frequently.
Regardless of which program your company decides it needs, seven steps can help identify what type of security training is appropriate:
1. Establish organizational technology objectives.
2. Conduct a needs assessment.
3. Find a training program that meets these needs.
4. Select the training methods and mode.
5. Choose a means of evaluating.
6. Administer training.
7. Evaluate the training.
Types of training include the following:
![]() In-house training
In-house training
![]() Web-based training
Web-based training
![]() Classroom training
Classroom training
![]() Vendor training
Vendor training
![]() On-the-job training
On-the-job training
![]() Apprenticeship programs
Apprenticeship programs
![]() Degreed programs
Degreed programs
![]() Continuing education programs
Continuing education programs
Caution
Training and education are not the same. Training programs are of short duration and usually teach individuals a specific skill. Education is broader-based and longer-term. Degree programs are examples of education.
Security Awareness
Awareness programs can be effective in increasing employee understanding of security. Security awareness training helps employees understand how their behavior affects the organization. Security awareness also outlines what is expected of employees. Awareness training must be developed differently for the various groups of employees that make up the organization. Not only will the training vary, but the topics and types of questions you’ll receive from the participants will also vary.
Successful employee awareness programs tailor the message to fit the audience. These are three of the primary groups that security awareness training should be targeted to:
![]() Senior management—Don’t try presenting an in-depth technical analysis to this group; its members are typically interested in the bigger picture. They want to know the costs, benefits, and ramifications if good security practices are not followed.
Senior management—Don’t try presenting an in-depth technical analysis to this group; its members are typically interested in the bigger picture. They want to know the costs, benefits, and ramifications if good security practices are not followed.
![]() Data custodians—This group requires a more structured presentation on how good security practices should be implemented, who is responsible, and what the individual and departmental cost is for noncompliance.
Data custodians—This group requires a more structured presentation on how good security practices should be implemented, who is responsible, and what the individual and departmental cost is for noncompliance.
![]() Users—Training for this group must align with employees’ daily tasks and map to the users’ specific job functions.
Users—Training for this group must align with employees’ daily tasks and map to the users’ specific job functions.
Note
The goal of security awareness is to increase management’s ability to hold employees accountable for their actions and to modify employee behavior toward security.
Social Engineering
Social engineering is the art of tricking someone into giving you something they should not. Those skilled in the art of social engineering can use their skills to gain access or information that they should not have. As organizations develop better physical and technical controls, attackers are always going to look for the easiest path to gain access. This very well could be the manipulation of people. An organization can have the best firewalls, IDS, network design, authentication system, or access controls and still be successfully attacked by a social engineer.
To gain a better understanding of how social engineering works, let’s look at the different approaches these attacks use. In his book, The Science and Practice of Persuasion, Robert Cialdini describes the following six types of behaviors for positive response to social engineering:
![]() Scarcity—Works on the belief that something (such as time) is in short supply. As an example, “I need the password now because my work is past due and the boss is waiting. Can you please help me this one time?”
Scarcity—Works on the belief that something (such as time) is in short supply. As an example, “I need the password now because my work is past due and the boss is waiting. Can you please help me this one time?”
![]() Authority—Work on the premise of power. As an example, “Hi, is this the Help Desk? I work for the senior VP and he needs his password reset to access important email!”
Authority—Work on the premise of power. As an example, “Hi, is this the Help Desk? I work for the senior VP and he needs his password reset to access important email!”
![]() Liking—Works because we tend to do more for people we like than people we don’t. As an example, “Come on, we are friends, you know I would not misuse your password.”
Liking—Works because we tend to do more for people we like than people we don’t. As an example, “Come on, we are friends, you know I would not misuse your password.”
![]() Consistency—People like to be consistent. As an example, “Why should I badge in when everyone else just walks in once someone opens the door?”
Consistency—People like to be consistent. As an example, “Why should I badge in when everyone else just walks in once someone opens the door?”
![]() Social validation—Based on the idea that if one person does it, others will too.
Social validation—Based on the idea that if one person does it, others will too.
![]() Reciprocation—If someone gives you a token or small gift, you feel pressured to give something in return. As an example, “You have already won a free gift. All you must do is take a few minutes to answer a few questions for our survey about your current security infrastructure.”
Reciprocation—If someone gives you a token or small gift, you feel pressured to give something in return. As an example, “You have already won a free gift. All you must do is take a few minutes to answer a few questions for our survey about your current security infrastructure.”
Realize these attacks can be launched person-to-person or computer-to-person. Knowing the various techniques that social engineers use can go a long way toward defeating their potential scams. The primary defense against social engineering is training and awareness. A good resource for more information on social engineering is The Art of Deception: Controlling the Human Element of Security, by Kevin D. Mitnick and William L. Simon (Wiley, 2002).
Professional Ethics Training and Awareness
This section reviews some of the ethical standards and codes that a CISSP should be aware of. Ethics is a set of principles for right conduct. Ethical standards are sometimes different than legal standards: Laws define what we must do, whereas ethics define what we should do. With that being said, you must remember that not everyone will always act ethically.
CISSPs should uphold high ethical standards and promote high ethical standards in others. Some of the ways CISSPs can help promote proper ethical behavior include making sure that organizations have guidelines on computer ethics, ensuring that ethical issues are included in employee handbooks, promoting computer ethics training, and helping to develop ethical policies on issues such as email and other privacy-related topics. There are several ethical standards that the CISSP should be aware of to help point the way toward proper behavior. Some of these include the following:
![]() ISC2 Code of Ethics (www.isc2.org)
ISC2 Code of Ethics (www.isc2.org)
![]() Ten Commandments of Computer Ethics (computerethicsinstitute.org/publications/tencommandments.html)
Ten Commandments of Computer Ethics (computerethicsinstitute.org/publications/tencommandments.html)
![]() RFC 1087 (www.ietf.org/rfc/rfc1087.txt)
RFC 1087 (www.ietf.org/rfc/rfc1087.txt)
![]() NIST 800-14 (csrc.nist.gov/publications/nistpubs/800-14/800-14.pdf)
NIST 800-14 (csrc.nist.gov/publications/nistpubs/800-14/800-14.pdf)
ISC2 Code of Ethics
It’s a requirement for CISSP candidates to subscribe to and support the ISC2 Code of Ethics, which states that a CISSP should
![]() Protect society, the commonwealth, and the infrastructure
Protect society, the commonwealth, and the infrastructure
![]() Act honorably, honestly, justly, responsibly, and legally
Act honorably, honestly, justly, responsibly, and legally
![]() Provide diligent and competent service to principals
Provide diligent and competent service to principals
![]() Advance and protect the profession
Advance and protect the profession
ExamAlert
Exam candidates must read the full Code of Ethics because the exam may include one or two questions related to the code. You can find this document by searching for “Code of Ethics” at www.isc2.org.
Computer Ethics Institute
The Computer Ethics Institute is a group that focuses specifically on ethics in the technology industry. Its website, www.computerethicsinstitute.org, lists the following Ten Commandments of Computer Ethics:
1. Thou shalt not use a computer to harm other people.
2. Thou shalt not interfere with other people’s computer work.
3. Thou shalt not snoop around in other people’s computer files.
4. Thou shalt not use a computer to steal.
5. Thou shalt not use a computer to bear false witness.
6. Thou shalt not copy or use proprietary software for which you have not paid.
7. Thou shalt not use other people’s computer resources without authorization or proper compensation.
8. Thou shalt not appropriate other people’s intellectual output.
9. Thou shalt think about the social consequences of the program you are writing or the system you are designing.
10. Thou shalt always use a computer in ways that ensure consideration and respect for your fellow humans.
ExamAlert
Exam candidates are advised to read the Ten Commandments of Computer Ethics and be able to differentiate it from the ISC2 Code of Ethics.
Internet Architecture Board
The Internet Architecture Board (IAB) is an advisory body of the Internet Society (ISOC). Figure 4.10 shows the layout of the ISOC. The Internet Engineering Steering Group (IESG) is responsible for technical management of IETF activities and the overall Internet standards process. The IAB is responsible for the Internet Standards Process and the Request for Comments (RFC) editor. The actual development of new standards and protocols for the Internet is carried out by working groups chartered by the IETF.
An RFC is an engineering white paper that describes the operation of a protocol, application, behavior, or design of an Internet-connected system. The IAB also has responsibility for architectural oversight of Internet Engineering Task Force (IETF) activities. One RFC that a CISSP should have knowledge of is RFC 1087. The goal of RFC 1087, published by the IAB in January 1987, is to characterize unethical and unacceptable behavior. It states that the following activities are unethical:
![]() Seeking to gain unauthorized access to the resources of the Internet
Seeking to gain unauthorized access to the resources of the Internet
![]() Disrupting the intended use of the Internet
Disrupting the intended use of the Internet
![]() Wasting resources (people, capacity, computer) through such actions
Wasting resources (people, capacity, computer) through such actions
![]() Destroying the integrity of computer-based information
Destroying the integrity of computer-based information
![]() Compromising the privacy of users
Compromising the privacy of users
ExamAlert
Print and review RFC 1087 before you attempt the CISSP exam. It is available at www.faqs.org/rfcs/rfc1087.html.
NIST SP 800-14
Not only do individuals have responsibilities but so do organizations. NIST SP 800-14 (Generally Accepted System Security Principles) was created to outline the responsibilities of organizations that use electronic systems. The more significant points made in NIST SP 800-14 are:
![]() Security supports the mission of the organization.
Security supports the mission of the organization.
![]() Security is an integral element of sound management.
Security is an integral element of sound management.
![]() Security should be cost-effective.
Security should be cost-effective.
![]() Systems owners have security responsibilities outside their own organizations.
Systems owners have security responsibilities outside their own organizations.
![]() Security responsibilities and accountability should be made explicit.
Security responsibilities and accountability should be made explicit.
![]() Security requires a comprehensive and integrated approach.
Security requires a comprehensive and integrated approach.
![]() Security should be periodically reassessed.
Security should be periodically reassessed.
![]() Security is constrained by societal factors.
Security is constrained by societal factors.
Common Computer Ethics Fallacies
Most hackers profess to having ethical standards and many even state that their actions are not ethically wrong. When interviewed, many hackers state that they have their own set of ethical standards. Some of the reasons often used to rationalize their illegal behavior include the following common ethical fallacies:
![]() Computer game—If they don’t protect it, it’s fair game to attack.
Computer game—If they don’t protect it, it’s fair game to attack.
![]() Law-abiding citizen—It’s not physical theft, so it’s not illegal.
Law-abiding citizen—It’s not physical theft, so it’s not illegal.
![]() Shatterproof—If I don’t do damage, or it can be repaired, what’s the problem?
Shatterproof—If I don’t do damage, or it can be repaired, what’s the problem?
![]() Candy-from-a-baby—If it is that easy, how could it be wrong?
Candy-from-a-baby—If it is that easy, how could it be wrong?
![]() Hackers—If I learn from this, it will benefit society and me.
Hackers—If I learn from this, it will benefit society and me.
![]() Free information—All information should be free.
Free information—All information should be free.
Tip
While it is true that writing a computer virus is not illegal, distributing it for malicious purposes is illegal according to the CFAA. As an example, Robert T. Morris was not charged with writing the first Internet worm; he was charged and prosecuted for using the code for malicious purposes.
Regulatory Requirements for Ethics Programs
As previously discussed, not everyone sees ethics in the same way. Therefore, there are regulatory requirements in some countries to address ethics and to address proper behaviors and attitudes. In the United States the Federal Sentencing Guidelines for Organizations (FSGO) outlines ethical requirements and may impose different sentences depending on the ethics programs and culture of the organization. Several examples of these are listed here:
![]() The Foreign Corrupt Practices Act (FCPA)—Imposes civil and criminal penalties if publicly held organizations fail to maintain sufficient controls over their information systems and data. FCPA requires these companies to have adequate systems of internal accounting controls.
The Foreign Corrupt Practices Act (FCPA)—Imposes civil and criminal penalties if publicly held organizations fail to maintain sufficient controls over their information systems and data. FCPA requires these companies to have adequate systems of internal accounting controls.
![]() Sarbanes-Oxley Act—This U.S. financial and accounting disclosure and accountability legislation has requirements for ethics. Section 406 of the Sarbanes-Oxley Act outlines code of ethics requirements for senior financial officers.
Sarbanes-Oxley Act—This U.S. financial and accounting disclosure and accountability legislation has requirements for ethics. Section 406 of the Sarbanes-Oxley Act outlines code of ethics requirements for senior financial officers.
![]() Committee for Sponsoring Organizations of the Treadway Commission (COSO)—An internal control framework used by auditors and others, including expected standards of conduct and ethics.
Committee for Sponsoring Organizations of the Treadway Commission (COSO)—An internal control framework used by auditors and others, including expected standards of conduct and ethics.
Note
Although questions dealing with laws specific to any one country are not common on the CISSP exam, it is still important to have a good understanding of the applicable laws under which your organization does business.
Tip
Ethics are not the only item to consider when discussing hackers. Another item of concern is motivation. Hackers are motivated by many different things, ranging from money to the desire to have fun. Some hackers claim that they carry out their activities simply for a cause. Hacking for a cause is known as hacktivism. As an example, in 2015 the hacker group known as Anonymous declared cyberwar against the Islamic State in retaliation for the 2015 Paris terrorist attacks.
Exam Prep Questions
1. The following statement can be found in which standard?
“Systems Owners Have Security Responsibilities Outside Their Own Organization.”
![]() A. Ethics and the Internet
A. Ethics and the Internet
![]() B. RFC 1087
B. RFC 1087
![]() C. ISC2 Code of Ethics
C. ISC2 Code of Ethics
![]() D. NIST 800-14
D. NIST 800-14
2. Which of the following methods of handling risk works by using a third party to absorb a portion of the risk?
![]() A. Risk reduction
A. Risk reduction
![]() B. Risk transference
B. Risk transference
![]() C. Risk acceptance
C. Risk acceptance
![]() D. Risk rejection
D. Risk rejection
3. You have been asked to calculate the annualized loss expectancy (ALE) for the following variables:
Single loss expectancy = $25
Exposure factor = 0.90
Annualized rate of occurrence = 0.40
Residual risk = $30
Which of the following is the resulting ALE?
![]() A. $9.00
A. $9.00
![]() B. $22.50
B. $22.50
![]() C. $10.00
C. $10.00
![]() D. $14.27
D. $14.27
4. Place the following formulas in their proper order:
![]() A. ALE, residual risk, SLE, ARO
A. ALE, residual risk, SLE, ARO
![]() B. ALE, ARO, SLE, residual risk
B. ALE, ARO, SLE, residual risk
![]() C. ARO, SLE, ALE, residual risk
C. ARO, SLE, ALE, residual risk
![]() D. SLE, ARO, ALE, residual risk
D. SLE, ARO, ALE, residual risk
5. Which of the following is the formula for residual risk?
![]() A. (Threats × Vulnerability × Asset value) × Controls gap = Residual risk
A. (Threats × Vulnerability × Asset value) × Controls gap = Residual risk
![]() B. (Threats × Vulnerability × Asset value) = Residual risk
B. (Threats × Vulnerability × Asset value) = Residual risk
![]() C. (Threats / Vulnerability × Asset value) × Control = Residual risk
C. (Threats / Vulnerability × Asset value) × Control = Residual risk
![]() D. (Risk × Vulnerability × Asset value) × Controls gap = Residual risk
D. (Risk × Vulnerability × Asset value) × Controls gap = Residual risk
6. Which of the following is the length of time for copyright in the United States and the European Union?
![]() A. Life plus 20 years
A. Life plus 20 years
![]() B. Life plus 30 years
B. Life plus 30 years
![]() C. Life plus 70 years
C. Life plus 70 years
![]() D. Life plus 100 years
D. Life plus 100 years
7. Which of the following formulas represents total risk?
![]() A. Risk × Vulnerability × Asset value = Total risk
A. Risk × Vulnerability × Asset value = Total risk
![]() B. Threat × Vulnerability × Asset value = Total risk
B. Threat × Vulnerability × Asset value = Total risk
![]() C. Risk × Value/Countermeasure = Total risk
C. Risk × Value/Countermeasure = Total risk
![]() D. Threat - Vulnerability/Asset value = Total risk
D. Threat - Vulnerability/Asset value = Total risk
8. Which of the following is a flaw, loophole, oversight, or error that makes an organization susceptible to attack or damage?
![]() A. Risk
A. Risk
![]() B. Vulnerability
B. Vulnerability
![]() C. Threat
C. Threat
![]() D. Exploit
D. Exploit
9. Which of the following is the most general of security documents?
![]() A. Procedures
A. Procedures
![]() B. Standards
B. Standards
![]() C. Policies
C. Policies
![]() D. Baselines
D. Baselines
10. Which of the following groups is responsible for the actual development of new standards and protocols such as RFC 1087?
![]() A. IESG
A. IESG
![]() B. ISOC
B. ISOC
![]() C. IAB
C. IAB
![]() D. IETF
D. IETF
11. Which organizational role is tasked with assigning sensitivity labels?
![]() A. Management
A. Management
![]() B. The auditor
B. The auditor
![]() C. The user
C. The user
![]() D. The owner
D. The owner
12. When the cost of the countermeasure outweighs the value of the asset, which of the following is the best approach?
![]() A. Take no action
A. Take no action
![]() B. Transference the risk
B. Transference the risk
![]() C. Mitigate the risk
C. Mitigate the risk
![]() D. Increase the cost of exposure
D. Increase the cost of exposure
13. Which ISO document is used for a standard for information security management?
![]() A. ISO 27001
A. ISO 27001
![]() B. ISO 27002
B. ISO 27002
![]() C. ISO 27004
C. ISO 27004
![]() D. ISO 27799
D. ISO 27799
14. TCO does not include which of the following?
![]() A. Software updates
A. Software updates
![]() B. Subscription costs
B. Subscription costs
![]() C. Maintenance costs
C. Maintenance costs
![]() D. Cost of not implementing a control
D. Cost of not implementing a control
15. It is important that the CISSP candidate understand the differences between the various legal systems used around the world. One early system was Corpus Juris Civilis, which featured a comprehensive system of written rules of law that serves as the basis for which legal system today?
![]() A. Civil law
A. Civil law
![]() B. Religious law
B. Religious law
![]() C. Common law
C. Common law
![]() D. Customary law
D. Customary law
Answers to Exam Prep Questions
1. D. NIST 800-14 states that responsibilities exceed the network you are in charge of. Answers A and C both point to RFC 1087 Ethics and the Internet. This statement is also not in the ISC2 Code of Ethics.
2. B. The purchase of insurance to transfer a portion or all of the potential cost of a loss to third party is known as risk transference. All other answers are incorrect: Risk reduction implements a countermeasure, risk acceptance deals with risk by accepting the potential cost, and risk rejection pretends it doesn’t exist.
3. C. $25 × 0.40 = $10, or Single loss expectancy (SLE) × Annualized rate of occurrence (ARO) = Annualized loss expectancy (ALE).
4. D. The quantitative assessment process involves the following steps: Estimate potential losses (SLE), conduct a threat analysis (ARO), determine annual loss expectancy (ALE), and determine the residual risk after a countermeasure has been applied.
5. A. The formula for residual risk is: (Threats × Vulnerability × Asset value) × Controls gap = Residual risk
6. C. Life plus 70 years is the length of time of a copyright in the United States and the European Union. But keep in mind that copyright terms can vary depending on the country and time they were granted.
7. B. Risk is expressed numerically as follows:
Threat × Vulnerability × Asset value = Total risk
All other answers do not properly define the formula for total risk.
8. B. Vulnerability is a flaw, loophole, oversight, or error that makes the organization susceptible to attack or damage. All other answers are incorrect: A risk can be defined as the potential harm that can arise from some present process or from some future event; the event is the action of the threat agent that can result in harm to an asset or service; and an exploit takes advantage of a bug, glitch, or vulnerability.
9. C. Policies are high-level documents. A procedure is a detailed, in-depth, step-by-step document that lays out exactly what is to be done. It’s a detailed document that is tied to specific technologies and devices. Standards are tactical documents. Baselines are minimum levels of security that a system, network, or device must adhere to.
10. D. The actual development of new standards and protocols for the Internet is carried out by working groups chartered by the IETF. Answers A, B, and C are incorrect.
11. D. The owner. Data classification should be performed by the owner. When a data item or object is identified, the owner is the one responsible for assigning a security label. If the military data-classification system is used, that label might be top secret, secret, sensitive, or unclassified. It is not the responsibility of the auditor, management, or the user to assign a label to the data.
12. A. When the cost of the countermeasure outweighs the value of the asset, the best approach is to take no action. This means the asset would cost more to protect than what it is worth. Answers B, C, and D are incorrect because there would be a loss of value in transferring the risk. In such cases, there would be no reason to mitigate the risk because the cost would be prohibitive. This violated good security practices.
13. C. ISO 27004 is the standard for security management. 27001 is focused on requirements. ISO 27002 was developed for BS 7799, and ISO 27799 is focused on health.
14. D. TCO includes all costs including software, updates, and maintenance. The only thing that is not included is the cost of not implementing the control.
15. A. Much of Europe is based on civil (code) law, also known as Napoleonic law. The Romans used Corpus Juris Civilis, which featured a comprehensive system of written rules of law that serves as the basis of civil law used today. Answer B, C, and D are incorrect as the major difference between civil law and common law is that civil law uses legislation as the main source of laws. Religious law is based on religious tenets. China and some African countries use customary law, which may be combined with other legal systems and is based on the concept of what is customary and considered normal conduct. It is important that the CISSP candidate understand the differences between the various legal systems used around the world.
Need to Know More?
Keeping pre-employment checks legal: www.eeoc.gov/laws/practices/
ISO27002 overview: en.wikipedia.org/wiki/ISO/IEC_27002
Security configuration guides: support.microsoft.com/en-us/kb/885409
The site security handbook: www.faqs.org/rfcs/rfc2196.html
Self-audits of employment practices: library.findlaw.com/2000/Aug/1/127767.html
Building effective security policies: www.crcpress.com/Building-an-Effective-Information-Security-Policy-Architecture/Bacik/p/book/9781420059052
Building effective policy: csrc.nist.gov/nissc/1997/panels/isptg/pescatore/html/
Policy templates and information: www.sans.org/security-resources/policies/
Threat analysis: www.linuxjournal.com/article/5567