Chapter 1
Basic Device Configuration
Objectives
Upon completion of this chapter, you will be able to answer the following questions:
How do you configure initial settings on a Cisco switch?
How do you configure switch ports to meet network requirements?
How do you configure secure management access on a switch?
How do you configure basic settings on a router to route between two directly connected networks, using CLI?
How do you verify connectivity between two networks that are directly connected to a router?
Key Terms
This chapter uses the following key terms. You can find the definitions in the Glossary.
power-on self-test (POST) Page 2
BOOT environment variable Page 3
Redundant Power System (RPS) LED Page 4
automatic medium-dependent interface crossover (auto-MDIX) Page 13
Introduction (1.0)
Welcome to the first module in CCNA Switching, Routing, and Wireless Essentials! You know that switches and routers come with some built-in configuration, so why would you need to learn to further configure switches and routers?
Imagine that you purchased a model train set. After you had set it up, you realized that the track was just a simple oval shape and that the train cars ran only clockwise. You might want the track to be a figure-eight shape with an overpass. You might want to have two trains that operate independently of each other and are able to move in different directions. How could you make that happen? You would need to reconfigure the track and the controls. It is the same with network devices. As a network administrator you need detailed control of the devices in your network. This means precisely configuring switches and routers so that your network does what you want it to do. This module has many Syntax Checker and Packet Tracer activities to help you develop these skills. Let’s get started!
Configure a Switch with Initial Settings (1.1)
Switches interconnect devices. Unlike a router, which must be initially configured to be operational in a network, switches can be deployed out of the box without initially being configured. However, for management and security reasons, switches should always be manually configured to better meet the needs of the network.
In this section, you learn how to configure initial settings on a Cisco switch.
Switch Boot Sequence (1.1.1)
Before you can configure a switch, you need to turn it on and allow it to go through the five-step boot sequence. This topic covers the basics of configuring a switch and includes a lab at the end.
After a Cisco switch is powered on, it goes through the following five-step boot sequence:
Step 1. The switch loads a power-on self-test (POST) program stored in read-only memory (ROM). POST checks the central processing unit (CPU) subsystem. It tests the CPU, dynamic random-access memory (DRAM), and the portion of the flash device that makes up the flash file system.
Step 2. The switch loads the boot loader software. The boot loader is a small program stored in ROM that is run immediately after POST successfully completes.
Step 3. The boot loader performs low-level CPU initialization. It initializes the CPU registers, which control where physical memory is mapped, the quantity of memory, and its speed.
Step 4. The boot loader initializes the flash file system on the system board.
Step 5. Finally, the boot loader locates and loads a default IOS operating system software image into memory and gives control of the switch over to the IOS.
The boot system Command (1.1.2)
The switch attempts to automatically boot by using information in the BOOT environment variable. If this variable is not set, the switch attempts to load and execute the first executable file it can find. On Catalyst 2960 Series switches, the image file is normally contained in a directory that has the same name as the image file (excluding the .bin file extension).
The IOS operating system then initializes the interfaces using the Cisco IOS commands found in the startup-config file. The startup-config file is called config.text and is located in flash.
In the following snippet, the BOOT environment variable is set using the boot system global configuration mode command. Notice that the IOS is located in a distinct folder and the folder path is specified. Use the command show boot to see what the current IOS boot file is set to.
S1(config)# boot system flash./c2960-lanbasek9-mz.150-2.SE/c2960-lanbasek9-mz.150-2. SE.bin
Table 1-1 defines each part of the boot system command.
Table 1-1 The boot system Command Syntax
Command |
Definition |
boot system |
The main command |
flash. |
The storage device |
c2960-lanbasek9-mz.150-2.SE/ |
The path to the file system |
c2960-lanbasek9-mz.150-2.SE.bin |
The IOS file name |
Switch LED Indicators (1.1.3)
Cisco Catalyst switches have several status LED indicator lights. You can use the switch LEDs to quickly monitor switch activity and performance. Switches of different models and feature sets will have different LEDs and their placement on the front panel of the switch may also vary.
Figure 1-1 shows the switch LEDs and the Mode button for a Cisco Catalyst 2960 switch.
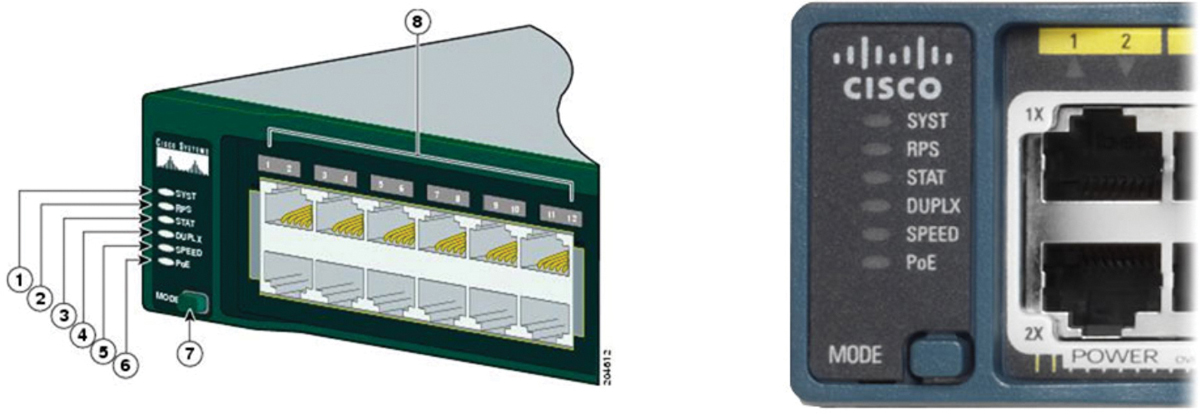
Figure 1-1 Cisco Catalyst 2960 LEDs and Mode Button
The Mode button (7 in Figure 1-1) is used to toggle through port status, port duplex, port speed, and if supported, the Power over Ethernet (PoE) status of the port LEDs (8 in Figure 1-1).
Table 1-2 describes the purpose of the LED indicators (1 through 6 in Figure 1-1), and the meaning of their colors.
Table 1-2 LED Indicators
LED Label |
Name |
Description |
1 SYST |
|
|
2 RPS |
|
|
3 STAT |
Port Status LED |
|
4 DUPLX |
Port Duplex LED |
|
5 SPEED |
Port Speed LED |
|
6 PoE |
Power over Ethernet (PoE) Mode LED |
|
Recovering from a System Crash (1.1.4)
The boot loader provides access into the switch if the operating system cannot be used because of missing or damaged system files. The boot loader has a command-line that provides access to the files stored in flash memory.
The boot loader can be accessed through a console connection following these steps:
![]()
Step 1. Connect a PC by console cable to the switch console port. Configure terminal emulation software to connect to the switch.
Step 2. Unplug the switch power cord.
Step 3. Reconnect the power cord to the switch and, within 15 seconds, press and hold down the Mode button while the System LED is still flashing green.
Step 4. Continue pressing the Mode button until the System LED turns briefly amber and then solid green; then release the Mode button.
Step 5. The boot loader switch: prompt appears in the terminal emulation software on the PC.
Type help or ? at the boot loader prompt to view a list of available commands.
By default, the switch attempts to automatically boot by using information in the BOOT environment variable. To view the path of the switch BOOT environment variable type the set command. Then, initialize the flash file system using the flash_init command to view the current files in flash, as shown in Example 1-1.
Example 1-1 Initialize Flash File System
switch: set BOOT=flash:/c2960-lanbasek9-mz.122-55.SE7/c2960-lanbasek9-mz.122-55.SE7.bin (output omitted) switch: flash_init Initializing Flash... flashfs[0]: 2 files, 1 directories flashfs[0]: 0 orphaned files, 0 orphaned directories flashfs[0]: Total bytes: 32514048 flashfs[0]: Bytes used: 11838464 flashfs[0]: Bytes available: 20675584 flashfs[0]: flashfs fsck took 10 seconds. ...done Initializing Flash.
After flash has finished initializing you can enter the dir flash: command to view the directories and files in flash, as shown in Example 1-2.
Example 1-2 Display Flash Directory
switch: dir flash:
Directory of flash:/
2 -rwx 11834846 c2960-lanbasek9-mz.150-2.SE8.bin
3 -rwx 2072 multiple-fs
Enter the BOOT=flash command to change the BOOT environment variable path the switch uses to load the new IOS in flash. To verify the new BOOT environment variable path, issue the set command again. Finally, to load the new IOS type the boot command without any arguments, as shown in Example 1-3.
Example 1-3 Configure the Boot Image
switch: BOOT=flash:c2960-lanbasek9-mz.150-2.SE8.bin switch: set BOOT=flash:c2960-lanbasek9-mz.150-2.SE8.bin (output omitted) switch: boot
The boot loader commands support initializing flash, formatting flash, installing a new IOS, changing the BOOT environment variable, and recovery of lost or forgotten passwords.
Switch Management Access (1.1.5)
To prepare a switch for remote management access, the switch must have a switch virtual interface (SVI) configured with an IPv4 address and subnet mask or an IPv6 address and a prefix length for IPv6. The SVI is a virtual interface, not a physical port on the switch. Keep in mind that to manage the switch from a remote network, the switch must be configured with a default gateway. This is very similar to configuring the IP address information on host devices.
In Figure 1-2, the switch virtual interface (SVI) on S1 should be assigned an IP address. A console cable is used to connect to a PC so that the switch can be initially configured. The indicated IP addresses display the default gateway of PC1 and S1.
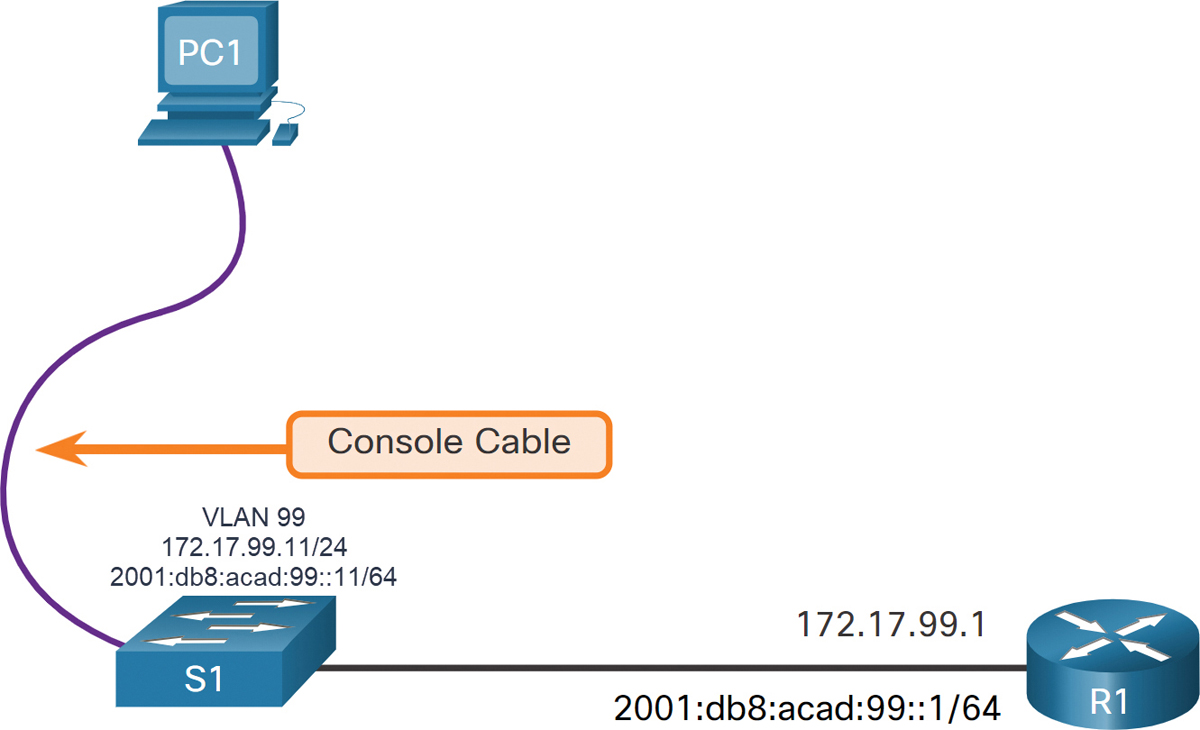
Figure 1-2 Console Connection to a Switch
Switch SVI Configuration Example (1.1.6)
By default, the switch is configured to have its management controlled through VLAN 1. All ports are assigned to VLAN 1 by default. For security purposes, it is considered a best practice to use a VLAN other than VLAN 1 for the management VLAN, such as VLAN 99.
![]()
Step 1. Configure the Management Interface on S1. From VLAN interface configuration mode, an IPv4 address and subnet mask is applied to the management SVI of the switch. Specifically, SVI VLAN 99 will be assigned the 172.17.99.11/24 IPv4 address and the 2001:db8:acad:99::11/64 IPv6 address as shown in Table 1-3.
Table 1-3 Configure IPv4 and IPv6 Addressing for the Management Interface
Task |
IOS Commands |
Enter global configuration mode. |
S1# configure terminal |
Enter interface configuration mode for the SVI. |
S1(config)# interface vlan 99 |
Configure the management IPv4 address. |
S1(config-if)# ip address 172.17.99.11 255.255.255.0 |
Configure the management IPv6 address. |
S1(config-if)# ipv6 address 2001:db8:acad:99::11/64 |
Enable the management interface. |
S1(config-if)# no shutdown |
Return to the privileged EXEC mode. |
S1(config-if)# end |
Save the running config to the startup config. |
S1# copy running-config startup-config |
Note
The SVI for VLAN 99 will not appear as “up/up” until VLAN 99 is created and there is a device connected to a switch port associated with VLAN 99.
Note
The switch may need to be configured for IPv6. For example, before you can configure IPv6 addressing on a Cisco Catalyst 2960 running IOS version 15.0, you will need to enter the global configuration command sdm prefer dual-ipv4-and-ipv6 default and then reload the switch.
Step 2. Configure the Default Gateway. The switch should be configured with a default gateway if it will be managed remotely from networks that are not directly connected, as shown in Table 1-4.
Table 1-4 Configure the Default Gateway
Task |
IOS Commands |
Enter global configuration mode. |
S1# configure terminal |
Configure the default gateway for the switch. |
S1(config)# ip default-gateway 172.17.99.1 |
Return to the privileged EXEC mode. |
S1(config)# end |
Save the running config to the startup config. |
S1# copy running-config startup-config |
Note
Because it will receive its default gateway information from a router advertisement (RA) message, the switch does not require an IPv6 default gateway.
Step 3. Verify Configuration. The show ip interface brief and show ipv6 interface brief commands are useful for determining the status of both physical and virtual interfaces. The output shown in Example 1-4 confirms that interface VLAN 99 has been configured with an IPv4 and IPv6 address.
Note
An IP address applied to the SVI is only for remote management access to the switch; this does not allow the switch to route Layer 3 packets.
Example 1-4 Verify IP Configuration
S1# show ip interface brief
Interface IP-Address OK? Method Status Protocol
Vlan99 172.17.99.11 YES manual down down
(output omitted)
S1#
S1# show ipv6 interface brief
Vlan99 [down/down]
FE80::C27B:BCFF:FEC4:A9C1
2001:DB8:ACAD:99::11
(output omitted)
Lab - Basic Switch Configuration (1.1.7)
![]()
In this lab, you will complete the following objectives:
Part 1: Cable the Network and Verify the Default Switch Configuration
Part 2: Configure Basic Network Device Settings
Part 3: Verify and Test Network Connectivity
Part 4: Manage the MAC Address Table
Configure Switch Ports (1.2)
In this section, you learn how to configure switch ports to meet network requirements.
Duplex Communication (1.2.1)
The ports of a switch can be configured independently for different needs. This section covers how to configure switch ports, how to verify your configurations, common errors, and how to troubleshoot switch configuration issues.
Full-duplex communication increases bandwidth efficiency by allowing both ends of a connection to transmit and receive data simultaneously. This is also known as bidirectional communication and it requires microsegmentation. A microsegmented LAN is created when a switch port has only one device connected and is operating in full-duplex mode. There is no collision domain associated with a switch port operating in full-duplex mode.
Unlike full-duplex communication, half-duplex communication is unidirectional. Half-duplex communication creates performance issues because data can flow in only one direction at a time, often resulting in collisions. Half-duplex connections are typically seen in older hardware, such as hubs. Half-duplex hubs have been replaced by switches that use full-duplex communication by default.
Figure 1-3 illustrates full-duplex and half-duplex communication.
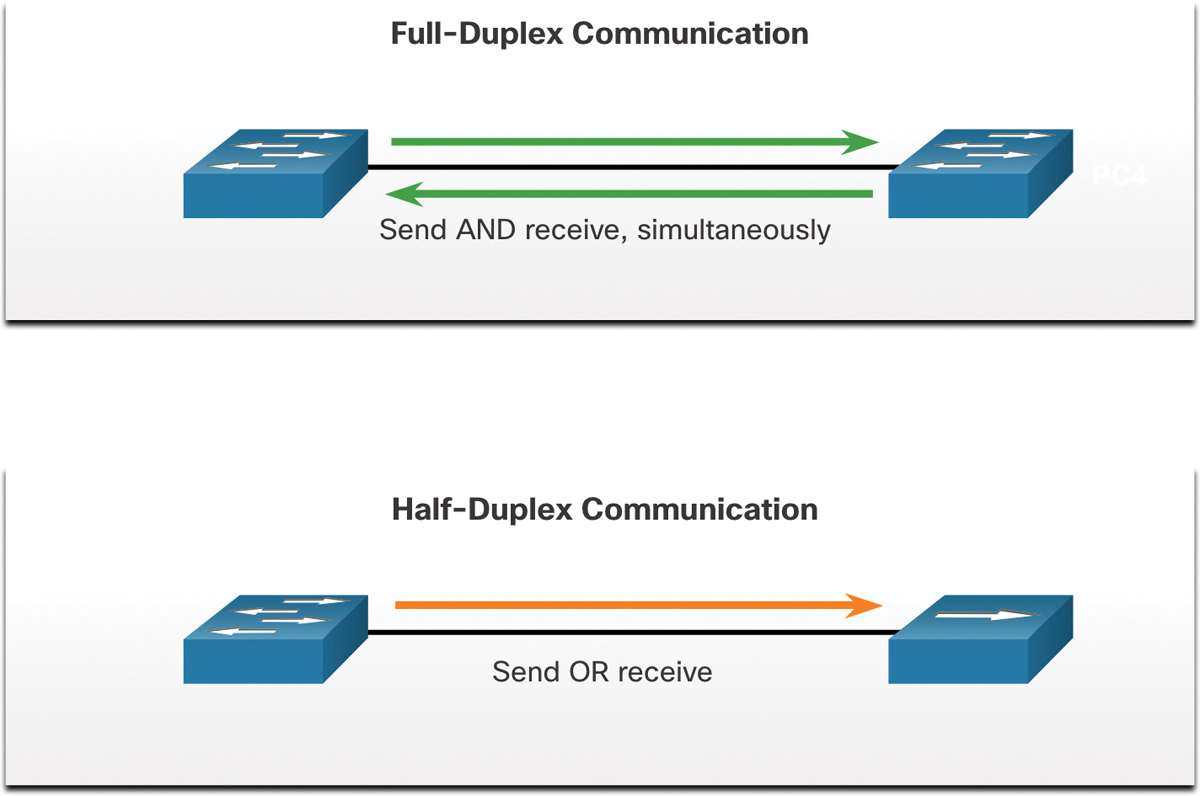
Figure 1-3 Duplex Communications Between Two Switches
Gigabit Ethernet and 10 Gb/s NICs require full-duplex connections to operate. In full-duplex mode, the collision detection circuit on the network interface card (NIC) is disabled. Full-duplex offers 100 percent efficiency in both directions (transmitting and receiving). This results in a doubling of the potential use of the stated bandwidth.
Configure Switch Ports at the Physical Layer (1.2.2)
Switch ports can be manually configured with specific duplex and speed settings. Use the duplex interface configuration mode command to manually specify the duplex mode for a switch port. Use the speed interface configuration mode command to manually specify the speed. For example, both switches in Figure 1-4 should always operate in full-duplex at 100 Mbps.
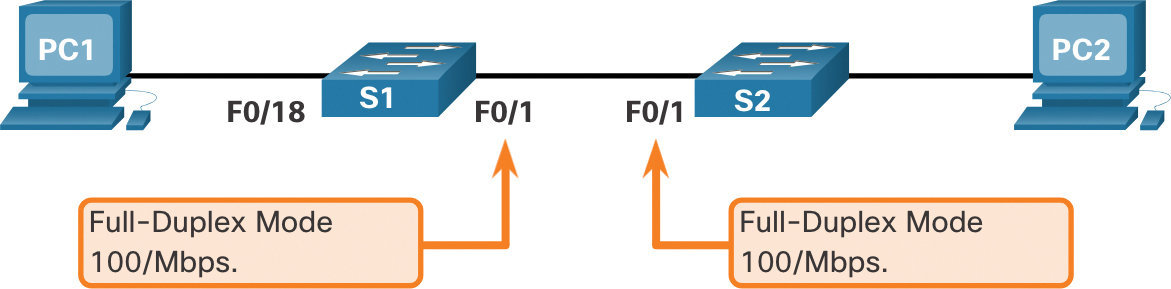
Figure 1-4 Connected Switches Operating at Full-Duplex and 100 Mbps
Table 1-5 shows the commands for S1. The same commands can be applied to S2.
Table 1-5 Duplex and Speed Commands
Task |
IOS Commands |
Enter global configuration mode. |
S1# configure terminal |
Enter interface configuration mode. |
S1(config)# interface FastEthernet 0/1 |
Configure the interface duplex. |
S1(config-if)# duplex full |
Configure the interface speed. |
S1(config-if)# speed 100 |
Return to the privileged EXEC mode. |
S1(config-if)# end |
Save the running config to the startup config. |
S1# copy running-config startup-config |
The default setting for both duplex and speed for switch ports on Cisco Catalyst 2960 and 3560 switches is auto. The 10/100/1000 ports operate in either half- or full-duplex mode when they are set to 10 or 100 Mbps and operate only in full-duplex mode when it is set to 1000 Mbps (1 Gbps). Autonegotiation is useful when the speed and duplex settings of the device connecting to the port are unknown or may change. When connecting to known devices such as servers, dedicated workstations, or network devices, a best practice is to manually set the speed and duplex settings.
When troubleshooting switch port issues, it is important that the duplex and speed settings should be checked.
Note
Mismatched settings for the duplex mode and speed of switch ports can cause connectivity issues. Autonegotiation failure creates mismatched settings.
All fiber-optic ports, such as 1000BASE-SX ports, operate only at one preset speed and are always full-duplex.
Auto-MDIX (1.2.3)
Until recently, certain cable types (straight-through or crossover) were required when connecting devices. Switch-to-switch or switch-to-router connections required using different Ethernet cables. Using the automatic medium-dependent interface crossover (auto-MDIX) feature on an interface eliminates this problem. When auto-MDIX is enabled, the interface automatically detects the required cable connection type (straight-through or crossover) and configures the connection appropriately. When connecting to switches without the auto-MDIX feature, straight-through cables must be used to connect to devices such as servers, workstations, or routers. Crossover cables must be used to connect to other switches or repeaters.
With auto-MDIX enabled, either type of cable can be used to connect to other devices, and the interface automatically adjusts to communicate successfully. On newer Cisco switches, the mdix auto interface configuration mode command enables the feature. When using auto-MDIX on an interface, the interface speed and duplex must be set to auto so that the feature operates correctly.
The command to enable auto-MDIX is issued in interface configuration mode on the switch as shown:
S1(config-if)# mdix auto
Note
The auto-MDIX feature is enabled by default on Catalyst 2960 and Catalyst 3560 switches but is not available on the older Catalyst 2950 and Catalyst 3550 switches.
To examine the auto-MDIX setting for a specific interface, use the show controllers ethernet-controller command with the phy keyword. To limit the output to lines referencing auto-MDIX, use the include Auto-MDIX filter. In Example 1-5, Auto-MDIX is on.
Example 1-5 Verifying Auto-MDIX Setting
S1# show controllers ethernet-controller fa0/1 phy | include MDIX Auto-MDIX : On [AdminState=1 Flags=0x00052248]
Switch Verification Commands (1.2.4)
Table 1-6 summarizes some of the more useful switch verification commands.
Table 1-6 Switch Verification Commands
Task |
IOS Commands |
Display interface status and configuration. |
S1# show interfaces [interface-id] |
Display current startup configuration. |
S1# show startup-config |
Display current running configuration. |
S1# show running-config |
Display information about flash file system. |
S1# show flash |
Display system hardware and software status. |
S1# show version |
Display history of command entered. |
S1# show history |
Display IP information about an interface. |
S1# show ip interface [interface-id] OR S1# show ipv6 interface [interface-id] |
Display the MAC address table. |
S1# show mac-address-table OR S1# show mac address-table |
Verify Switch Port Configuration (1.2.5)
The show running-config command can be used to verify that the switch has been correctly configured. Some important information is shown in Example 1-6:
Fast Ethernet 0/18 interface is configured with the management VLAN 99.
VLAN 99 is configured with an IPv4 address of 172.17.99.11 255.255.255.0.
The default gateway is set to 172.17.99.1.
Example 1-6 Switch Port Configuration Verification
S1# show running-config Building configuration... Current configuration : 1466 bytes ! interface FastEthernet0/18 switchport access vlan 99 switchport mode access ! (output omitted) ! interface Vlan99 ip address 172.17.99.11 255.255.255.0 ipv6 address 2001:DB8:ACAD:99::1/64 ! ip default-gateway 172.17.99.1
The show interfaces command is another commonly used command, which displays status and statistics information on the network interfaces of the switch. The show interfaces command is frequently used when configuring and monitoring network devices.
The first line of the output for the show interfaces fastEthernet 0/18 command in Example 1-7 indicates that the FastEthernet 0/18 interface is up/up, meaning that it is operational. Further down, the output shows that the duplex is full and the speed is 100 Mbps.
Example 1-7 Interface Verification
S1# show interfaces fastEthernet 0/18
FastEthernet0/18 is up, line protocol is up (connected)
Hardware is Fast Ethernet, address is 0025.83e6.9092 (bia 0025.83e6.9092)
MTU 1500 bytes, BW 100000 Kbit/sec, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s, media type is 10/100BaseTX
Network Access Layer Issues (1.2.6)
The output from the show interfaces command is useful for detecting common media issues. One of the most important parts of this output is the display of the line and data link protocol status, as shown Example 1-8.
Example 1-8 Checking Protocol Status
S1# show interfaces fastEthernet 0/18 FastEthernet0/18 is up, line protocol is up (connected) Hardware is Fast Ethernet, address is 0025.83e6.9092 (bia 0025.83e6.9092)MTU 1500 bytes, BW 100000 Kbit/sec, DLY 100 usec,
The first parameter (FastEthernet0/18 is up) refers to the hardware layer and indicates whether the interface is receiving a carrier detect signal. The second parameter (line protocol is up) refers to the data link layer and indicates whether the data link layer protocol keepalives are being received.
Based on the output of the show interfaces command, possible problems can be fixed as follows:
Interface is up and line protocol is down: This indicates a problem exists. There could be an encapsulation type mismatch, the interface on the other end could be error-disabled, or there could be a hardware problem.
Interface is down and line protocol is down: This is an indication that a cable is not attached, or some other problem exists. For example, in a back-to-back connection, the other end of the connection may be administratively down.
Interface is administratively down: This indicates that the interface is manually disabled (the shutdown command has been issued) in the active configuration.
The show interfaces command output displays counters and statistics for the FastEthernet0/18 interface, as highlighted in Example 1-9.
Example 1-9 Interface Counters and Statistics
S1# show interfaces fastEthernet 0/18
FastEthernet0/18 is up, line protocol is up (connected)
Hardware is Fast Ethernet, address is 0025.83e6.9092 (bia 0025.83e6.9092)
MTU 1500 bytes, BW 100000 Kbit/sec, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s, media type is 10/100BaseTX
input flow-control is off, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input never, output 00:00:01, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
2295197 packets input, 305539992 bytes, 0 no buffer
Received 1925500 broadcasts (74 multicasts)
0 runts, 0 giants, 0 throttles
3 input errors, 3 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 74 multicast, 0 pause input
0 input packets with dribble condition detected
3594664 packets output, 436549843 bytes, 0 underruns
8 output errors, 1790 collisions, 10 interface resets
0 unknown protocol drops
0 babbles, 235 late collision, 0 deferred
Some media errors are not severe enough to cause the circuit to fail but do cause network performance issues. Table 1-7 explains some of these common errors, which can be detected using the show interfaces command.
Table 1-7 Common Errors Detected by the show interface Command
Error Type |
Description |
Total number of errors and includes runts, giants, no buffer, CRC, frame, overrun, and ignored counts. |
|
Frames that are discarded because they are smaller than the minimum packet size for the medium. For instance, any Ethernet frame that is less than 64 bytes is considered a runt. |
|
May be forwarded or discarded depending on the model of the switch. A giant frame is an Ethernet frame greater than 1,518 bytes. |
|
CRC errors are generated when the calculated checksum is not the same as the checksum received. |
|
Sum of all errors that prevented the final transmission of datagrams out of the interface that is being examined. |
|
Collisions |
Number of messages retransmitted because of an Ethernet collision. |
A collision that occurs after 512 bits of the frame have been transmitted. |
Interface Input and Output Errors (1.2.7)
“Input errors” is the sum of all errors in datagrams that were received on the interface being examined. This includes runts, giants, cyclic redundancy check (CRC), no buffer, frame, overrun, and ignored counts. The reported input errors from the show interfaces command include the following:
Runt Frames: Ethernet frames that are shorter than the 64-byte minimum allowed length are called runts. Malfunctioning NICs are the usual cause of excessive runt frames, but they can also be caused by collisions.
Giants: Ethernet frames that are larger than the maximum allowed size are called giants. Giants may be forwarded or discarded depending on the model of the switch.
CRC errors: On Ethernet and serial interfaces, CRC errors usually indicate a media or cable error. Common causes include electrical interference, loose or damaged connections, or incorrect cabling. If you see many CRC errors, there is too much noise on the link and you should inspect the cable. You should also search for and eliminate noise sources.
“Output errors” is the sum of all errors that prevented the final transmission of datagrams out the interface that is being examined. The reported output errors from the show interfaces command include the following:
Collisions: Collisions in half-duplex operations are normal. However, you should never see collisions on an interface configured for full-duplex communication.
Late collisions: A late collision refers to a collision that occurs after 512 bits of the frame have been transmitted. Excessive cable lengths are the most common cause of late collisions. Another common cause is duplex misconfiguration. For example, you could have one end of a connection configured for full-duplex and the other for half-duplex. You would see late collisions on the interface that is configured for half-duplex. In that case, you must configure the same duplex setting on both ends. A properly designed and configured network should never have late collisions.
Troubleshooting Network Access Layer Issues (1.2.8)
Most issues that affect a switched network are encountered during the original implementation. Theoretically, after it is installed, a network continues to operate without problems. However, cabling gets damaged, configurations change, and new devices are connected to the switch that require switch configuration changes. Ongoing maintenance and troubleshooting of the network infrastructure is required.
To troubleshoot scenarios involving no connection, or a bad connection, between a switch and another device, follow the general process shown in Figure 1-5.

Figure 1-5 Troubleshooting Process for Network Layer Issues
Use the show interfaces command to check the interface status.
If the interface is down:
Check to make sure that the proper cables are being used. Additionally, check the cable and connectors for damage. If a bad or incorrect cable is suspected, replace the cable.
If the interface is still down, the problem may be due to a mismatch in speed setting. The speed of an interface is typically autonegotiated; therefore, even if it is manually applied to one interface, the connecting interface should autonegotiate accordingly. If a speed mismatch does occur through misconfiguration, or a hardware or software issue, then that may result in the interface going down. Manually set the same speed on both connection ends if a problem is suspected.
If the interface is up but issues with connectivity are still present:
Using the show interfaces command, check for indications of excessive noise. Indications may include an increase in the counters for runts, giants, and CRC errors. If there is excessive noise, first find and remove the source of the noise, if possible. Also, verify that the cable does not exceed the maximum cable length and check the type of cable that is used.
If noise is not an issue, check for excessive collisions. If there are collisions or late collisions, verify the duplex settings on both ends of the connection. Much like the speed setting, the duplex setting is usually autonegotiated. If there does appear to be a duplex mismatch, manually set the duplex to full on both ends of the connection.
Syntax Checker—Configure Switch Ports (1.2.9)
![]()
Configure a switch interface based on the specified requirements.
Refer to the online course to complete this activity.
Secure Remote Access (1.3)
In this section, you learn how to configure the management virtual interface on a switch.
Telnet Operation (1.3.1)
You might not always have direct access to your switch when you need to configure it. You need to be able to access it remotely, and it is imperative that your access is secure. This section discusses how to configure Secure Shell (SSH) for remote access. A Packet Tracer activity gives you the opportunity to try this yourself.
Telnet uses Transmission Control Protocol (TCP) port 23. It is an older protocol that uses unsecure plain text transmission of both the login authentication (username and password) and the data transmitted between the communicating devices. A threat actor can monitor packets using Wireshark. For example, in Figure 1-6, the threat actor captured the username admin and password ccna from a Telnet session.
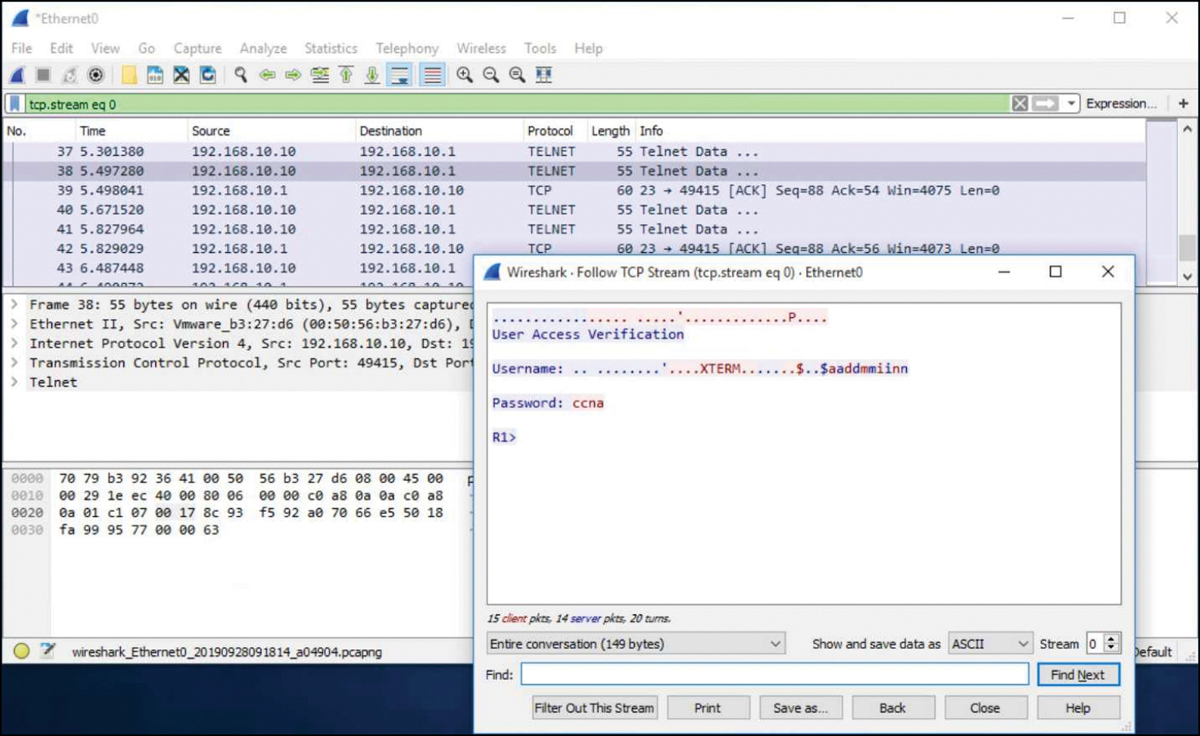
Figure 1-6 Telnet Session Capture
SSH Operation (1.3.2)
Secure Shell (SSH) is a secure protocol that uses TCP port 22. It provides a secure (encrypted) management connection to a remote device. SSH should replace Telnet for management connections. SSH provides security for remote connections by providing strong encryption when a device is authenticated (username and password) and also for the transmitted data between the communicating devices.
For example, Figure 1-7 shows a Wireshark capture of an SSH session. The threat actor can track the session using the IP address of the administrator device. However, unlike Telnet, with SSH the username and password are encrypted.
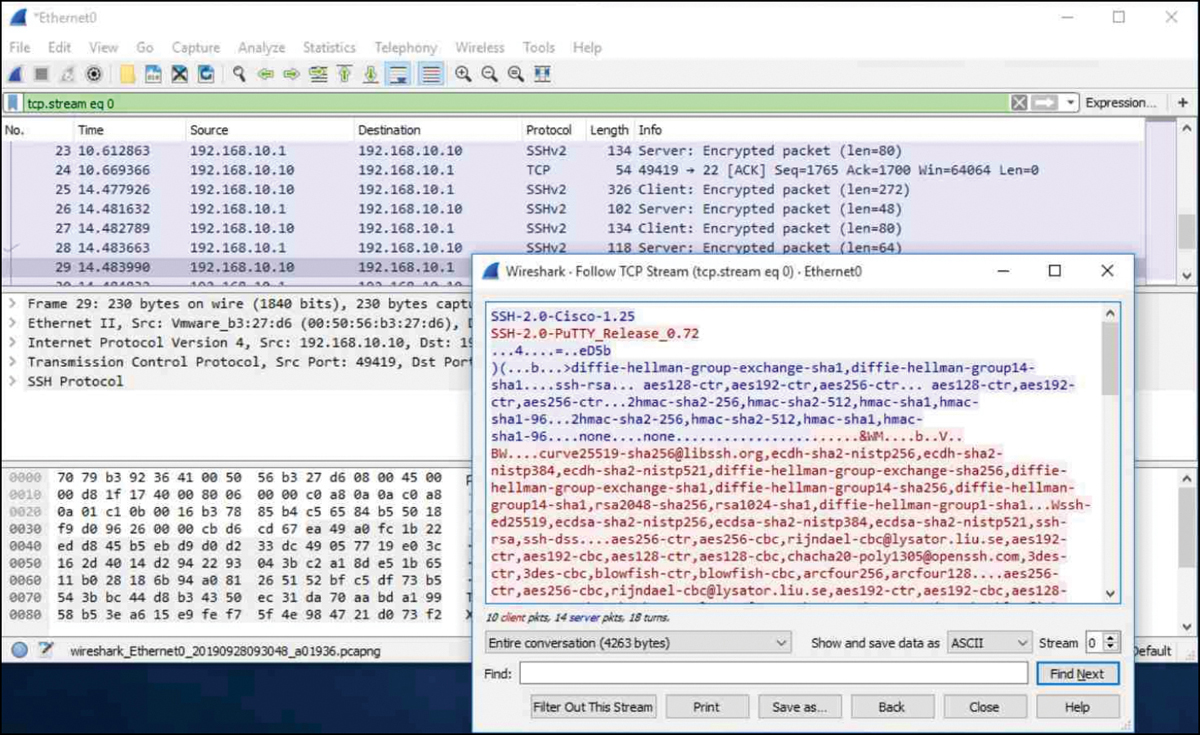
Figure 1-7 SSH Session Capture
Verify the Switch Supports SSH (1.3.3)
To enable SSH on a Catalyst 2960 switch, the switch must be using a version of the IOS software including cryptographic (encrypted) features and capabilities. Use the show version command on the switch to see which IOS the switch is currently running. An IOS filename that includes the combination “k9” supports cryptographic (encrypted) features and capabilities. Example 1-10 shows the output of the show version command.
Example 1-10 Checking Whether the IOS Supports SSH
S1# show version Cisco IOS Software, C2960 Software (C2960-LANBASEK9-M), Version 15.0(2)SE7, RELEASE SOFTWARE (fc1)
Configure SSH (1.3.4)
Before configuring SSH, the switch must be minimally configured with a unique hostname and the correct network connectivity settings.
![]()
Step 1. Verify SSH support. Use the show ip ssh command, as shown in Example 1-11, to verify that the switch supports SSH. If the switch is not running an IOS that supports cryptographic features, this command is unrecognized.
Example 1-11 Verify SSH Support
S1# show ip ssh
Step 2. Configure the IP domain. Configure the IP domain name of the network using the ip domain-name domain-name global configuration mode command. In Example 1-12, the domain-name value is cisco.com.
Example 1-12 Configure the IP Domain
S1(config)# ip domain-name cisco.com
Step 3. Generate RSA key pairs. Not all versions of the IOS default to SSH version 2, and SSH version 1 has known security flaws. To configure SSH version 2, issue the ip ssh version 2 global configuration mode command. Generating a Rivest, Shamir, Adleman (RSA) key pair automatically enables SSH. Use the crypto key generate rsa global configuration mode command to enable the SSH server on the switch and generate an RSA key pair. When generating RSA keys, the administrator is prompted to enter a modulus length. The sample configuration in Example 1-13 uses a modulus size of 1,024 bits. A longer modulus length is more secure, but it takes longer to generate and to use.
Note
To delete the RSA key pair, use the crypto key zeroize rsa global configuration mode command. After the RSA key pair is deleted, the SSH server is automatically disabled.
Example 1-13 Generate RSA Key Pairs
S1(config)# crypto key generate rsa How many bits in the modulus [512]: 1024
Step 4. Configure user authentication. The SSH server can authenticate users locally or using an authentication server. To use the local authentication method, create a username and password pair using the username username secret password global configuration mode command. In Example 1-14, the user admin is assigned the password ccna.
Example 1-14 Configure User Authentication
S1(config)# username admin secret ccna25
Step 5. Configure the vty lines. Enable the SSH protocol on the vty lines by using the transport input ssh line configuration mode command, as shown in Example 1-15. The Catalyst 2960 has vty lines ranging from 0 to 15. This configuration prevents non-SSH (such as Telnet) connections and limits the switch to accept only SSH connections. Use the line vty global configuration mode command and then the login local line configuration mode command to require local authentication for SSH connections from the local username database.
Example 1-15 Configure the VTY Lines
S1(config)# line vty 0 15 S1(config-line)# transport input ssh S1(config-line)# login local S1(config-line)# exit
Step 6. Enable SSH version 2. By default, SSH supports both versions 1 and 2. When supporting both versions, this is shown in the show ip ssh output as supporting version 2. Enable SSH version using the ip ssh version 2 global configuration command, as shown in Example 1-16.
Example 1-16 Enable SSH Version 2
S1(config)# ip ssh version 2
Verify SSH Is Operational (1.3.5)
On a PC, an SSH client such as PuTTY is used to connect to an SSH server. For example, assume the following is configured:
SSH is enabled on switch S1.
Interface VLAN 99 (SVI) with IPv4 address 172.17.99.11 on switch S1.
PC1 with IPv4 address 172.17.99.21.
Figure 1-8 shows the PuTTY settings for PC1 to initiate an SSH connection to the SVI VLAN IPv4 address of S1.
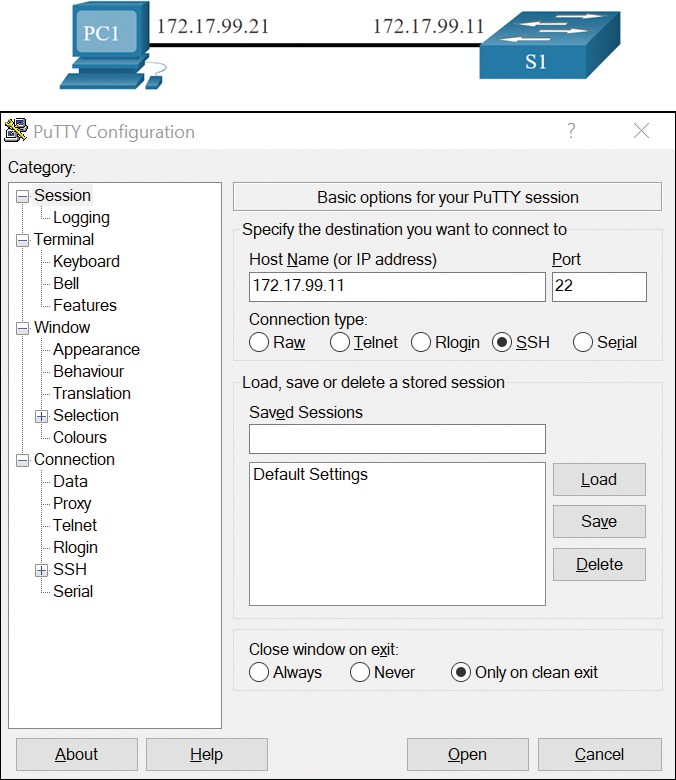
Figure 1-8 PuTTY Settings
When connected, the user is prompted for a username and password, as shown in Example 1-17. Using the configuration from Example 1-14, the username admin and password ccna are entered. After entering the correct combination, the user is connected via SSH to the command line interface (CLI) on the Catalyst 2960 switch.
Login as: admin Using keyboard-interactive Authentication. Password: S1> enable Password: S1#
To display the version and configuration data for SSH on the device that you configured as an SSH server, use the show ip ssh command. In Example 1-18, SSH version 2 is enabled.
S1# show ip ssh SSH Enabled - version 2.0 Authentication timeout: 120 secs; Authentication retries: 3 To check the SSH connections to the device, use the show ssh command as shown. S1# show ssh %No SSHv1 server connections running. Connection Version Mode Encryption Hmac State Username 0 2.0 IN aes256-cbc hmac-sha1 Session started admin 0 2.0 OUT aes256-cbc hmac-sha1 Session started admin S1#
Packet Tracer—Configure SSH (1.3.6)
![]()
SSH should replace Telnet for management connections. Telnet uses insecure plain text communications. SSH provides security for remote connections by providing strong encryption of all transmitted data between devices. In this activity, you secure a remote switch with password encryption and SSH.
Basic Router Configuration (1.4)
Every network has unique settings that must be configured on a router. This section introduces basic IOS commands that are required to configure a router.
Configure Basic Router Settings (1.4.1)
Up to now, this module has covered only switches. If you want devices to be able to send and receive data outside of your network, you have to configure routers. This section teaches you basic router configuration and provides two Syntax Checkers and a Packet Tracer activity so you can practice these skills.
Cisco routers and Cisco switches have many similarities. They support a similar modal operating system, similar command structures, and many of the same commands. In addition, both devices have similar initial configuration steps. For example, the following configuration tasks should always be performed. Name the device to distinguish it from other routers and configure passwords, as shown in Example 1-19.
Example 1-19 Basic Router Configuration
Router# configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)# hostname R1 R1(config)# enable secret class R1(config)# line console 0 R1(config-line)# password cisco R1(config-line)# login R1(config-line)# exit R1(config)# line vty 0 4 R1(config-line)# password cisco R1(config-line)# login R1(config-line)# exit R1(config)# service password-encryption R1(config)#
Configure a banner to provide legal notification of unauthorized access, as shown Example 1-20.
Example 1-20 Configure a Banner
R1(config)# banner motd $ Authorized Access Only! $ R1(config)#
Save the changes on a router, as shown in Example 1-21.
Example 1-21 Save the Configuration
R1# copy running-config startup-config Destination filename [startup-config]? Building configuration... [OK]
Syntax Checker—Configure Basic Router Settings (1.4.2)
![]()
In this Syntax Checker activity, you configure basic settings for R2.
Refer to the online course to complete this activity.
Dual Stack Topology (1.4.3)
One distinguishing feature between switches and routers is the type of interfaces supported by each. For example, Layer 2 switches support LANs; therefore, they have multiple FastEthernet or Gigabit Ethernet ports. The dual stack topology in Figure 1-9 is used to demonstrate the configuration of router IPv4 and IPv6 interfaces.

Figure 1-9 Dual Stack Topology
Configure Router Interfaces (1.4.4)
Routers support LANs and WANs and can interconnect different types of networks; therefore, they support many types of interfaces. For example, G2 ISRs have one or two integrated Gigabit Ethernet interfaces and High-Speed WAN Interface Card (HWIC) slots to accommodate other types of network interfaces, including serial, DSL, and cable interfaces.
To be available, an interface must be
Configured with at least one IP address: Use the ip address ip-address subnet-mask and the ipv6 address ipv6-address/prefix interface configuration commands.
Activated: By default, LAN and WAN interfaces are not activated (shutdown). To enable an interface, it must be activated using the no shutdown command. (This is similar to powering on the interface.) The interface must also be connected to another device (a hub, a switch, or another router) for the physical layer to be active.
Description: Optionally, the interface could also be configured with a short description of up to 240 characters. It is good practice to configure a description on each interface. On production networks, the benefits of interface descriptions are quickly realized as they are helpful in troubleshooting and in identifying a third-party connection and contact information.
Example 1-22 shows the configuration for the interfaces on R1.
Example 1-22 R1 Dual Stack Configuration
R1(config)# interface gigabitethernet 0/0/0 R1(config-if)# ip address 192.168.10.1 255.255.255.0 R1(config-if)# ipv6 address 2001:db8:acad:1::1/64 R1(config-if)# description Link to LAN 1 R1(config-if)# no shutdown R1(config-if)# exit R1(config)# interface gigabitethernet 0/0/1 R1(config-if)# ip address 192.168.11.1 255.255.255.0 R1(config-if)# ipv6 address 2001:db8:acad:2::1/64 R1(config-if)# description Link to LAN 2 R1(config-if)# no shutdown R1(config-if)# exit R1(config)# interface serial 0/0/0 R1(config-if)# ip address 209.165.200.225 255.255.255.252 R1(config-if)# ipv6 address 2001:db8:acad:3::225/64 R1(config-if)# description Link to R2 R1(config-if)# no shutdown R1(config-if)# exit R1(config)#
Syntax Checker—Configure Router Interfaces (1.4.5)
![]()
In this Syntax Checker activity, you will configure R2 with its IPv4 and IPv6 interfaces.
Refer to the online course to complete this activity.
IPv4 Loopback Interfaces (1.4.6)
Another common configuration of Cisco IOS routers is enabling a loopback interface.
The loopback interface is a logical interface that is internal to the router. It is not assigned to a physical port and can never be connected to any other device. It is considered a software interface that is automatically placed in an “up” state, as long as the router is functioning.
The loopback interface is useful in testing and managing a Cisco IOS device because it ensures that at least one interface will always be available. For example, it can be used for testing purposes, such as testing internal routing processes, by emulating networks behind the router.
Loopback interfaces are also commonly used in lab environments to create additional interfaces. For example, you can create multiple loopback interfaces on a router to simulate more networks for configuration practice and testing purposes. In this curriculum, we often use a loopback interface to simulate a link to the Internet.
Enabling and assigning a loopback address is simple:
Router(config)# interface loopback number Router(config-if)# ip address ip-address subnet-mask
Multiple loopback interfaces can be enabled on a router. The IPv4 address for each loopback interface must be unique and unused by any other interface, as shown in Example 1-23, configuration of loopback interface 0 on R1.
Example 1-23 Loopback Interface Configuration
R1(config)# interface loopback 0 R1(config-if)# ip address 10.0.0.1 255.255.255.0 R1(config-if)# exit R1(config)# %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to up
Packet Tracer—Configure Router Interfaces (1.4.7)
![]()
In this Packet Tracer activity, you configure routers with IPv4 and IPv6 addressing.
Configure Router Interfaces.
Verify Directly Connected Networks (1.5)
It is always important to know how to troubleshoot and verify whether a device is configured correctly. The focus of this section is on how to verify connectivity between two networks that are directly connected to a router.
Interface Verification Commands (1.5.1)
There is no point in configuring your router unless you verify the configuration and connectivity. This section covers the commands to use to verify directly connected networks. It includes two Syntax Checkers and a Packet Tracer.
There are several show commands that can be used to verify the operation and configuration of an interface. The topology in the previous Figure 1-9 is used to demonstrate the verification of router interface settings.
The following commands are especially useful to quickly identify the status of an interface:
show ip interface brief and show ipv6 interface brief: These display a summary for all interfaces including the IPv4 or IPv6 address of the interface and current operational status.
show running-config interface interface-id: This displays the commands applied to the specified interface.
show ip route and show ipv6 route: These display the contents of the IPv4 or IPv6 routing table stored in RAM. In Cisco IOS 15, active interfaces should appear in the routing table with two related entries identified by the code ‘C’ (Connected) or ‘L’ (Local). In previous IOS versions, only a single entry with the code ‘C’ will appear.
Verify Interface Status (1.5.2)
The output of the show ip interface brief and show ipv6 interface brief commands can be used to quickly reveal the status of all interfaces on the router. You can verify that the interfaces are active and operational as indicated by the Status of “up” and Protocol of “up”, as shown in Example 1-24. A different output would indicate a problem with either the configuration or the cabling.
Example 1-24 Verify Interface Status
R1# show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0/0 192.168.10.1 YES manual up up
GigabitEthernet0/0/1 192.168.11.1 YES manual up up
Serial0/1/0 209.165.200.225 YES manual up up
Serial0/1/1 unassigned YES unset administratively down down
R1# show ipv6 interface brief
GigabitEthernet0/0/0 [up/up]
FE80::7279:B3FF:FE92:3130
2001:DB8:ACAD:1::1
GigabitEthernet0/0/1 [up/up]
FE80::7279:B3FF:FE92:3131
2001:DB8:ACAD:2::1
Serial0/1/0 [up/up]
FE80::7279:B3FF:FE92:3130
2001:DB8:ACAD:3::1
Serial0/1/1 [down/down] Unassigned
Verify IPv6 Link Local and Multicast Addresses (1.5.3)
The output of the show ipv6 interface brief command displays two configured IPv6 addresses per interface. One address is the IPv6 global unicast address that was manually entered. The other address, which begins with FE80, is the link-local unicast address for the interface. A link-local address is automatically added to an interface whenever a global unicast address is assigned. An IPv6 network interface is required to have a link-local address, but not necessarily a global unicast address.
The show ipv6 interface gigabitethernet 0/0/0 command displays the interface status and all the IPv6 addresses belonging to the interface. Along with the link local address and global unicast address, the output includes the multicast addresses assigned to the interface, beginning with prefix FF02, as shown in Example 1-25.
Example 1-25 Verify IPv6 Link Local and Multicast Addresses
R1# show ipv6 interface gigabitethernet 0/0/0 GigabitEthernet0/0/0 is up, line protocol is up IPv6 is enabled, link-local address is FE80::7279:B3FF:FE92:3130 No Virtual link-local address(es): Global unicast address(es): 2001:DB8:ACAD:1::1, subnet is 2001:DB8:ACAD:1::/64 Joined group address(es): FF02::1 FF02::1:FF00:1 FF02::1:FF92:3130 MTU is 1500 bytes ICMP error messages limited to one every 100 milliseconds ICMP redirects are enabled ICMP unreachables are sent ND DAD is enabled, number of DAD attempts: 1 ND reachable time is 30000 milliseconds (using 30000) ND advertised reachable time is 0 (unspecified) ND advertised retransmit interval is 0 (unspecified) ND router advertisements are sent every 200 seconds ND router advertisements live for 1800 seconds ND advertised default router preference is Medium
Verify Interface Configuration (1.5.4)
The output of the show running-config interface command displays the current commands applied to the specified interface, as shown in Example 1-26.
Example 1-26 Verify Interface Configuration
R1# show running-config interface gigabitethernet 0/0/0 Building configuration... Current configuration : 158 bytes ! interface GigabitEthernet0/0/0 description Link to LAN 1 ip address 192.168.10.1 255.255.255.0 negotiation auto ipv6 address 2001:DB8:ACAD:1::1/64 end R1#
The following two commands are used to gather more detailed interface information:
show interfaces: Displays interface information and packet flow count for all interfaces on the device.
show ip interface and show ipv6 interface: Displays the IPv4 and IPv6 related information for all interfaces on a router.
Verify Routes (1.5.5)
The output of the show ip route and show ipv6 route commands reveal the three directly connected network entries and the three local host route interface entries, as shown in Example 1-27.
R1# show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
Gateway of last resort is not set
192.168.10.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.10.0/24 is directly connected, GigabitEthernet0/0/0
L 192.168.10.1/32 is directly connected, GigabitEthernet0/0/0
192.168.11.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.11.0/24 is directly connected, GigabitEthernet0/0/1
L 192.168.11.1/32 is directly connected, GigabitEthernet0/0/1
209.165.200.0/24 is variably subnetted, 2 subnets, 2 masks
C 209.165.200.224/30 is directly connected, Serial0/1/0
L 209.165.200.225/32 is directly connected, Serial0/1/0
R1#
R1# show ipv6 route
IPv6 Routing Table - default - 7 entries
Codes: C - Connected, L - Local, S - Static, U - Per-user Static route
C 2001:DB8:ACAD:1::/64 [0/0]
via GigabitEthernet0/0/0, directly connected
L 2001:DB8:ACAD:1::1/128 [0/0]
via GigabitEthernet0/0/0, receive
C 2001:DB8:ACAD:2::/64 [0/0]
via GigabitEthernet0/0/1, directly connected
L 2001:DB8:ACAD:2::1/128 [0/0]
via GigabitEthernet0/0/1, receive
C 2001:DB8:ACAD:3::/64 [0/0]
via Serial0/1/0, directly connected
L 2001:DB8:ACAD:3::1/128 [0/0]
via Serial0/1/0, receive
L FF00::/8 [0/0]
via Null0, receive
R1#
The local host route has an administrative distance of 0. It also has a /32 mask for IPv4, and a /128 mask for IPv6. The local host route is for routes on the router that owns the IP address. It is used to allow the router to process packets destined to that IP.
The IPv6 global unicast address applied to the interface is also installed in the routing table as a local route. The local route has a /128 prefix. Local routes are used by the routing table to efficiently process packets with the interface address of the router as the destination.
A ‘C’ next to a route within the routing table indicates that this is a directly connected network. When the router interface is configured with a global unicast address and is in the “up/up” state, the IPv6 prefix and prefix length are added to the IPv6 routing table as a connected route. The administrative distance of a directly connected network is 0.
The ping command for IPv6 is identical to the command used with IPv4 except that an IPv6 address is used. As shown in Example 1-28, the ping command is used to verify Layer 3 connectivity between R1 and PC1.
Example 1-28 Ping an IPv6 Address
R1# ping 2001:db8:acad:1::10 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:DB8:ACAD:1::10, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Filter Show Command Output (1.5.6)
Commands that generate multiple screens of output are, by default, paused after 24 lines. At the end of the paused output, the --More-- text displays. Pressing Enter displays the next line and pressing the spacebar displays the next set of lines. Use the terminal length command to specify the number of lines to be displayed. A value of 0 (zero) prevents the router from pausing between screens of output.
Another very useful feature that improves the user experience in the CLI is the filtering of show output. Filtering commands can be used to display specific sections of output. To enable the filtering command, enter a pipe ( | ) character after the show command and then enter a filtering parameter and a filtering expression.
There are four filtering parameters that can be configured after the pipe:
The section Filter
The section filter shows the entire section that starts with the filtering expression, as shown in Example 1-29.
Example 1-29 The section Filter
R1# show running-config | section line vty line vty 0 4 password 7 110A1016141D login transport input all
Note
Output filters can be used in combination with any show command.
The include Filter
The include filter includes all output lines that match the filtering expression, as shown in Example 1-30.
Example 1-30 The include Filter
R1# show ip interface brief Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0/0 192.168.10.1 YES manual up up GigabitEthernet0/0/1 192.168.11.1 YES manual up up Serial0/1/0 209.165.200.225 YES manual up up Serial0/1/1 unassigned NO unset down down R1# R1# show ip interface brief | include up GigabitEthernet0/0/0 192.168.10.1 YES manual up up GigabitEthernet0/0/1 192.168.11.1 YES manual up up Serial0/1/0 209.165.200.225 YES manual up up
The exclude Filter
The exclude filter excludes all output lines that match the filtering expression, as shown in Example 1-31.
Example 1-31 The exclude Filter
R1# show ip interface brief Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0/0 192.168.10.1 YES manual up up GigabitEthernet0/0/1 192.168.11.1 YES manual up up Serial0/1/0 209.165.200.225 YES manual up up Serial0/1/1 unassigned NO unset down down R1# R1# show ip interface brief | exclude unassigned Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0/0 192.168.10.1 YES manual up up GigabitEthernet0/0/1 192.168.11.1 YES manual up up Serial0/1/0 209.165.200.225 YES manual up up
The begin Filter
The begin filter shows all the output lines from a certain point, starting with the line that matches the filtering expression, as shown in Example 1-32.
R1# show ip route | begin Gateway
Gateway of last resort is not set
192.168.10.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.10.0/24 is directly connected, GigabitEthernet0/0/0
L 192.168.10.1/32 is directly connected, GigabitEthernet0/0/0
192.168.11.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.11.0/24 is directly connected, GigabitEthernet0/0/1
L 192.168.11.1/32 is directly connected, GigabitEthernet0/0/1
209.165.200.0/24 is variably subnetted, 2 subnets, 2 masks
C 209.165.200.224/30 is directly connected, Serial0/1/0
L 209.165.200.225/32 is directly connected, Serial0/1/0
Syntax Checker—Filter Show Command Output (1.5.7)
![]()
In this Syntax Checker activity, you filter output for show commands.
Refer to the online course to complete this activity.
Command History Feature (1.5.8)
The command history feature is useful because it temporarily stores the list of executed commands to be recalled.
To recall commands in the history buffer, press CTRL+P or the Up Arrow key. The command output begins with the most recent command. Repeat the key sequence to recall successively older commands. To return to more recent commands in the history buffer, press CTRL+N or the Down Arrow key. Repeat the key sequence to recall successively more recent commands.
By default, command history is enabled and the system captures the last 10 command lines in its history buffer. Use the show history privileged EXEC command to display the contents of the buffer.
It is also practical to increase the number of command lines that the history buffer records during the current terminal session only. Use the terminal history size user EXEC command to increase or decrease the size of the buffer.
An example of the terminal history size and show history commands is shown in Example 1-33.
Example 1-33 Setting and Displaying Command History
R1# terminal history size 200 R1# show history show ip int brief show interface g0/0/0 show ip route show running-config show history terminal history size 200
Syntax Checker—Command History Features (1.5.9)
![]()
In this Syntax Checker activity, you use the command history feature.
Refer to the online course to complete this activity.
Packet Tracer—Verify Directly Connected Networks (1.5.10)
![]()
In this Packet Tracer activity, routers R1 and R2 each have two LANs. Your task is to verify the addressing on each device and verify connectivity between the LANs.
Check Your Understanding—Verify Directly Connected Networks (1.5.11)
![]()
Refer to the online course to complete this activity.
Summary (1.6)
The following is a summary of each section in the chapter:
Configure a Switch with Initial Settings
After a Cisco switch is powered on, it goes through a five-step boot sequence. The BOOT environment variable is set using the boot system global configuration mode command. The IOS is located in a distinct folder, and the folder path is specified. Use the switch LEDs to monitor switch activity and performance: SYST, RPS, STAT, DUPLX, SPEED, and PoE. The boot loader provides access into the switch if the operating system cannot be used because of missing or damaged system files. The boot loader has a command line that provides access to the files stored in flash memory. To prepare a switch for remote management access, the switch must be configured with an IP address and a subnet mask. To manage the switch from a remote network, the switch must be configured with a default gateway. To configure the switch SVI, you must first configure the management interface, then configure the default gateway, and finally, verify your configuration.
Configure Switch Ports
Full-duplex communication increases effective bandwidth by allowing both ends of a connection to transmit and receive data simultaneously. Half-duplex communication is unidirectional. Switch ports can be manually configured with specific duplex and speed settings. Use autonegotiation when the speed and duplex settings of the device connecting to the port are unknown or may change. When auto-MDIX is enabled, the interface automatically detects the required cable connection type (straight-through or crossover) and configures the connection appropriately. There are several show commands to use when verifying switch configurations. Use the show running-config command and the show interfaces command to verify a switch port configuration. The output from the show interfaces command is also useful for detecting common network access layer issues because it displays the line and data link protocol status. The reported input errors from the show interfaces command include runt frames, giants, CRC errors, along with collisions and late collisions. Use show interfaces to determine whether your network has no connection or a bad connection between a switch and another device.
Secure Remote Access
Telnet (using TCP port 23) is an older protocol that uses unsecure plain text transmission of both the login authentication (username and password) and the data transmitted between the communicating devices. SSH (using TCP port 22) is a secure protocol that provides an encrypted management connection to a remote device. SSH provides security for remote connections by providing strong encryption when a device is authenticated (username and password) and also for the transmitted data between the communicating devices. Use the show version command on the switch to see which IOS the switch is currently running. An IOS filename that includes the combination “k9” supports cryptographic features and capabilities. To configure SSH you must verify that the switch supports it, configure the IP domain, generate RSA key pairs, configure use authentication, configure the VTY lines, and enable SSH version 2. To verify that SSH is operational, use the show ip ssh command to display the version and configuration data for SSH on the device.
Basic Router Configuration
The following initial configuration tasks should always be performed. Name the device to distinguish it from other routers and configure passwords, configure a banner to provide legal notification of unauthorized access, and save the changes on a router. One distinguishing feature between switches and routers is the type of interfaces supported by each. For example, Layer 2 switches support LANs and, therefore, have multiple FastEthernet or GigabitEthernet ports. The dual stack topology is used to demonstrate the configuration of router IPv4 and IPv6 interfaces. Routers support LANs and WANs and can interconnect different types of networks; therefore, they support many types of interfaces. For example, G2 ISRs have one or two integrated Gigabit Ethernet interfaces and High-Speed WAN Interface Card (HWIC) slots to accommodate other types of network interfaces, including serial, DSL, and cable interfaces. The IPv4 loopback interface is a logical interface that is internal to the router. It is not assigned to a physical port and can never be connected to any other device.
Verify Directly Connected Networks
Use the following commands to quickly identify the status of an interface. show ip interface brief and show ipv6 interface brief to see a summary of all interfaces (IPv4 and IPv6 addresses and operational status), show running-config interface interface-id to see the commands applied to a specified interface, and show ip route and show ipv6 route to see the contents of the IPv4 or IPv6 routing table stored in RAM. The output of the show ip interface brief and show ipv6 interface brief commands can be used to quickly reveal the status of all interfaces on the router. The show ipv6 interface interface-id command displays the interface status and all the IPv6 addresses belonging to the interface. Along with the link local address and global unicast address, the output includes the multicast addresses assigned to the interface. The output of the show running-config interface command displays the current commands applied to a specified interface. The show interfaces command displays interface information and packet flow count for all interfaces on the device. Verify interface configuration using the show ip interface and show ipv6 interface commands, which display the IPv4 and IPv6 related information for all interfaces on a router. Verify routes using the show ip route and show ipv6 route commands. Filter show command output using the pipe ( | ) character. Use filter expressions: section, include, exclude, and begin. By default, command history is enabled, and the system captures the last 10 command lines in its history buffer. Use the show history privileged EXEC command to display the contents of the buffer.
Packet Tracer—Implement a Small Network (1.6.1)
![]()
In this Packet Tracer activity, routers R1 and R2 each have two LANs. Your task is to verify the addressing on each device and verify connectivity between the LANs.
Lab—Configure Basic Router Settings (1.6.2)
![]()
This is a comprehensive lab to review previously covered IOS router commands. You will cable the equipment and complete basic configurations and IPv4 interface settings on the router. You will then use SSH to connect to the router remotely and use IOS commands to retrieve information from the device to answer questions about the router.
Practice
The following activities provide practice with the topics introduced in this chapter. The Labs are available in the companion Switching, Routing, and Wireless Essentials Labs and Study Guide (CCNAv7) (ISBN 9780136634386). The Packet Tracer Activity instructions are also in the Labs & Study Guide. The PKA files are found in the online course.
Labs
![]()
Lab 1.1.7: Basic Switch Configuration
Lab 1.6.2: Configure Basic Router Settings
Packet Tracer Activities
![]()
Packet Tracer 1.3.6: Configure SSH
Packet Tracer 1.4.7: Configure Router Interfaces
Packet Tracer 1.5.10: Verify Directly Connected Networks
Check Your Understanding Questions
Complete all the review questions listed here to test your understanding of the topics and concepts in this chapter. The appendix “Answers to the ‘Check Your Understanding’ Questions” lists the answers.
1. Which interface is used by default to manage a Cisco Catalyst 2960 switch?
The FastEthernet 0/1 interface
The GigabitEthernet 0/1 interface
The VLAN 1 interface
The VLAN 99 interface
2. A production switch is reloaded and finishes with a Switch> prompt. What two facts can be determined? (Choose two.)
A full version of the Cisco IOS was located and loaded.
POST occurred normally.
The boot process was interrupted.
There is not enough RAM or flash on this router.
The switch did not locate the Cisco IOS in flash, so it defaulted to ROM.
3. Which two statements are true about using full-duplex Fast Ethernet? (Choose two.)
Full-duplex Fast Ethernet offers 100 percent efficiency in both directions.
Latency is reduced because the NIC processes frames faster.
Nodes operate in full-duplex with unidirectional data flow.
Performance is improved because the NIC is able to detect collisions.
Performance is improved with bidirectional data flow.
4. Which statement describes the port speed LED on the Cisco Catalyst 2960 switch?
If the LED is amber, the port is operating at 1000 Mbps.
If the LED is blinking green, the port is operating at 10 Mbps.
If the LED is green, the port is operating at 100 Mbps.
If the LED is off, the port is not operating.
5. What is a function of the switch boot loader?
To control how much RAM is available to the switch during the boot process
To provide an environment to operate in when the switch operating system cannot be found
To provide security for the vulnerable state when the switch is booting
To speed up the boot process
6. In which situation would a technician use the show interfaces command?
To determine whether remote access is enabled
To determine the MAC address of a directly attached network device on a particular interface
When packets are being dropped from a particular directly attached host
When an end device can reach local devices, but not remote devices
7. What is one difference between using Telnet or SSH to connect to a network device for management purposes?
Telnet does not provide authentication, whereas SSH provides authentication.
Telnet sends a username and password in plain text, whereas SSH encrypts the username and password.
Telnet supports a host GUI, whereas SSH supports only a host CLI.
Telnet uses UDP as the transport protocol, whereas SSH uses TCP.
8. What is a characteristic of an IPv4 loopback interface on a Cisco IOS router?
It is a logical interface internal to the router.
It is assigned to a physical port and can be connected to other devices.
Only one loopback interface can be enabled on a router.
The no shutdown command is required to place this interface in an up state.
9. What two pieces of information are displayed in the output of the show ip interface brief command? (Choose two.)
Interface descriptions
IPv4 addresses
Layer 1 statuses
MAC addresses
Next-hop addresses
Speed and duplex settings
10. What type of cable would be used to connect a router to a switch when neither supports the auto-MDIX feature?
Coaxial
Crossover
Rollover
Straight-through
11. Which statement regarding a loopback interface is true?
It is an internal virtual interface used for testing purposes.
It is used to loop back traffic to an interface.
It must be enabled using the no shutdown command.
Only one loopback interface can be created on a device.
12. You are implementing remote access to the VTY lines of a switch using SSH and the login local line vty command. Which other command must be entered to avoid being locked out of the switch?
enable secret password
password password
service-password encryption
username username secret password
