VIRTUAL PRIVATE NETWORKS (VPNS) allow organizations to transmit private and sensitive data securely over public intermediary networks. The Internet can serve as a cheap long-distance carrier for WAN connections established using VPNs. VPNs use native-operating system features or third-party software, as well as hardware devices, including edge routers, firewalls, and VPN appliances. Remote access for mobile users, linked multi-office intranets, and secured access into an extranet are common VPN architecture solutions.
The use of VPNs on small home networks to corporate global networks has dramatically expanded the ways people connect and do work. Through the use of VPNs, telecommuting employees, business partners, traveling workers, suppliers, distributors, and others can benefit from secured connectivity even while geographically distant. With a basic understanding of VPNs, you can begin designing and planning your own VPN solution.
VPN is the acronym for "virtual private network." A short and direct definition is that a VPN is a mechanism to establish a secure remote access connection across an intermediary network, often the Internet. VPNs allow remote access, remote control, and highly secured communications within a private network. VPNs employ encryption and authentication to provide confidentiality, integrity, and privacy protection for network communications.
A more involved exploration of the phrase "virtual private networks," however, can reveal other import aspects that such a succinct definition overlooks. The term VPN has its origins in the telecommunications world. A telephone VPN created a PBX-like system for businesses without the need for deployment of true private branch exchange (PBX) hardware. Instead, the system used a public telephone service and the PBX services at the telco's central offices. This service/product sold under the name Centrex (a combination of the terms central and exchange) in the 1960s through the 1980s.
After the proliferation of computer networks and Internet connectivity, the term VPN evolved to refer to tunneling connections across network links. Early computer VPNs focused on the tunneling or encapsulation processes and rarely included encryption services. Today, VPNs are almost always secured using encryption. However, you should never assume anything is totally secure, especially connections over public networks. You should always confirm that a product performs encryption properly before depending on it for sensitive operations.
A VPN creates or simulates a network connection over an intermediary network. But, what makes a VPN private? At least three possible mechanisms can work:
When the primary organization owns all of the network infrastructure components, including switches, routers, and cables. A true private VPN occurs when a single organization owns all of the hardware supporting their VPN. However, few organizations actually own all of the connections between their locations, so this is usually impractical or prohibitively expensive. This wholly owned and operated system constitutes a trusted VPN.
When a dedicated set of channels is used across leased telco connections. This method provides physical isolation even on third-party equipment; hence privacy is maintained. This type of system is more practical, but is still expensive. This can also be called a trusted VPN, since you must be able to trust the owner of the hosting infrastructure to protect network communications against eavesdropping.
When encryption ensures privacy even over public networks, such as the Internet. This method is the most reliable, as the other two options are still at risk to eavesdropping. Additionally, encryption to provide privacy is not only practical, it is the least expensive option as well. This system can be called a secured VPN.
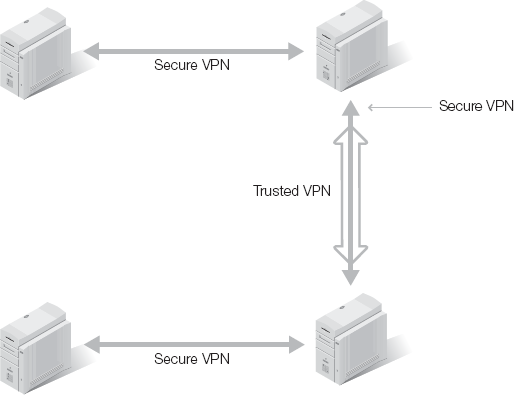
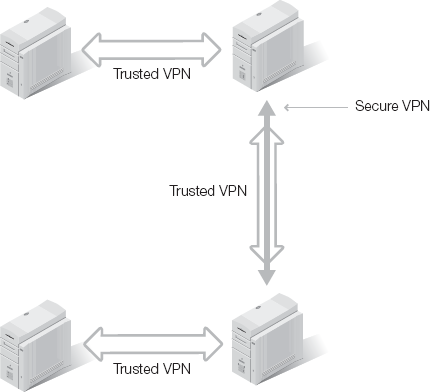
A fourth type private VPN is possible, known as a hybrid VPN. This form of VPN establishes a secure VPN over trusted VPN connections. A trusted VPN allows an organization to know and control the pathway of their transmissions. However, a trusted VPN does not protect against eavesdropping or alteration. A secure VPN protects the confidentiality and integrity of data, but does not control or ensure the transmission path. When you combine these two VPN techniques, you create a potentially more secure and practical solution. Two possible layouts of hybrid VPNs are shown in Figures 3-1 and 3-2.
VPNs are often associated with remote access or remote control. However, these associations need clarification to have value. Remote control is the ability to use a local computer system to remotely take over control of another computer over a network connection. In a way, this process is the application of the thin client concept on a modern fully capable workstation to simulate working against a mainframe or to virtualize your physical presence. This application is generally the same as a VPN, which creates a remote network connection rather than a remote control session.
With a remote control connection in place, the local monitor, keyboard, and mouse control a remote system. This process looks and feels like you are physically present at the keyboard of the remote system, which could be located in another city or even on the other side of the world. Every action you perform locally acts as if you were physically present at that remote computer virtually via the remote control connection. The only limitations are the speed of the intermediary network link and inability to physically insert or remove media and peripherals.
You might think of remote control as a form of software-based thin client or terminal client. In fact, many thin client and terminal client products sell as remote control solutions. Many modern operating systems include remote control features, such as Remote Desktop found in most versions of Windows. Once enabled, a Remote Desktop Connection remotely controls another Windows system from across the network. You can learn more about Remote Desktop in Chapter 14 "Real World VPNs."
Remote access is different from remote control. A remote access link enables access to network resources using a WAN link to connect to the geographically distant network. In effect, remote access creates a local network link for a system not physically near the network. Over a remote access connection, a client system can technically perform all the same tasks as a locally connected client. Network administrators can impose restrictions on what resources and services a remote access VPN client can use.
Remote access and VPNs were originally supported over dial-up telephone links using modems. Today, remote access encompasses a variety of connection types including ISDN, DSL, cable modem, satellite, mobile broadband, and more. Due to the wide availability of high-speed Internet connections, VPNs and other remote access solutions have become very popular for both personal and business-purposes.
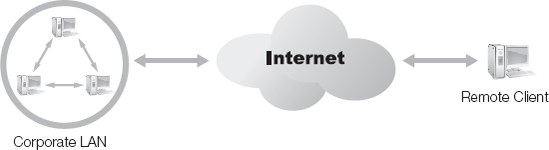
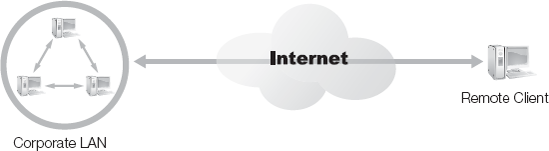
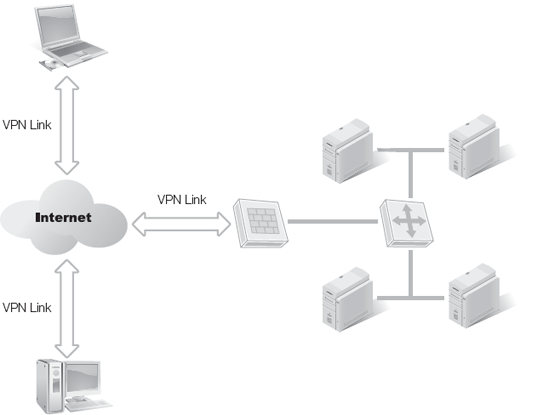
In many cases, a remote access connection is created from a remote client back to a primary network. If the remote client needs to connect directly to the LAN, such as over a dial-up connection, a RAS server will host a modem to accept the connection. If the remote client can use the Internet to access the LAN, then a local Internet connection is necessary. Once a normal LAN connection or Internet connection runs from the client, the VPN link is possible. Once the connection is established, the remote client now interacts with the network as if it were locally connected.
In Figure 3-3, a LAN and a remote client have a connection to the Internet. These two connections are independent of each other. The LAN's connection is usually a permanent or dedicated connection supporting both inbound and outbound activities with the Internet. The remote client's connection to the Internet can be dedicated or non-dedicated. In the latter case, the connection is established before a VPN can be created. Once both endpoints have a connection to the intermediary network, in this case the Internet, then the VPN can be created. In Figure 3-4, a new network connection is established from the remote client to the LAN across the intermediary network. This new network connection is the VPN.
VPNs can operate over standard Internet connections or dedicated business communication circuits, such as ATM and Frame Relay. However, the additional expense of a dedicated, isolated, and even secured business circuit isn't necessary with a VPN.
A VPN can operate securely over the Internet and still provide high levels of security through solid encryption. This allows inexpensive insecure links to replace expensive business-leased lines without sacrificing security.
VPNs are one of the most efficient and cost-effective means to provide secure remote connectivity. VPNs take advantage of cheap long distance connections when established over the Internet, since both endpoints only need a local Internet link. The Internet itself serves as a "free" long distance carrier. Because the speed of the VPN depends on the speed of the local Internet link, you still might want an optical carrier (OC) line (such as an OC-1 at 51.84 Mbps) for high-speed connectivity.
Connections from a LAN to an intermediary network, can support VPN traffic only or allow a combination of both VPN and normal non-VPN traffic. The latter configuration is less secure, but offers you flexibility as to whether all communications must be VPN-secured or not. An Internet connection reserved solely for VPN use, therefore, is not necessary. An OC-1 line is more than capable of supporting one or more VPN links in addition to numerous non-VPN Internet sessions with no difficulty or latency.
Setting up VPNs can require extensive knowledge and expertise on the part of the IT or security administrator. For example, some important concerns of secure VPNs include:
All VPN traffic must be authenticated and encrypted. A VPN without authentication is not private, and a VPN without encryption is insecure.
All VPN endpoints must abide by the same security parameters and algorithms. Each VPN tunnel must have corresponding encryption key sets to securely exchanged encrypted content. Additionally, the same security policy should govern all endpoints.
Proper encryption protocols must ensure that no external third-party can affect the security of the VPN. Weak encryption makes a "secure" VPN worthless.
When you use a trusted VPN you need to consider its own unique concerns:
Only the trusted VPN provider should be able to modify the channels or pathway of the VPN. A trusted VPN is based on the provider's ability to limit and control access to the VPN's content.
Only the trusted VPN provider can add, remove, or change data in the trusted channel. Violating this violates the trust the client places in the provider.
The addressing and routing performed within the trusted VPN must be defined before the VPN goes online. These services are usually pre-defined in the SLA (service level agreement), but may be dynamically modified for each VPN connection.
Even hybrid VPNs have an important focus for concern, namely that the segments of the VPN that are trusted vs. secured need clear definition. Mistaking security for trust—or vice versa—can have devastating results.
VPNs use tunneling or encapsulation protocols. Tunneling protocols encase the original network protocol so that it can traverse the intermediary network. In many cases, the tunneling protocol employs encryption so that the original data traverses the intermediary network securely. The protocols that create VPNs include IPSec, PPTP, L2TP, SSL, and TLS. The dominant forms of secure VPNs use IPSec or SSL/TLS as the tunneling/encapsulation protocol. You can learn more about VPN protocols in Chapter 13.
Most VPNs use software that operates on top of the operating system of a host. However, some VPN appliances can support VPN connectivity without adding any software to the host. In much the same way that a host firewall only works on the host where it is installed, an appliance firewall provide security services for the entire network. A host VPN software product allows a single host access to VPN services, while a VPN appliance allows an entire network to access VPN services. Read more about VPN hardware devices in Chapter 13.
VPNs simplify many business networking problems by providing an easy and efficient means to securely connect headquarters, remote offices, traveling workers, and telecommuters.
The reasons to deploy and use VPNs vary greatly among organizations. Many of the obvious reasons are based on the benefits of a VPN (discussed in the following section). Nevertheless, other reasons are based on business or personal factors needing the solutions VPNs readily provide.
Cost is always a significant factor in any business decision. Budgets are never unlimited (at least, not outside of Congress), so organizations must shepherd their limited funds to accomplish their missions and goals. One common goal is high productivity. Granting workers the ability to access and use resources in a timely and efficient manner assists in the completion of work. When those resources are computer files or network services, employees no longer need to be in the same building as those resources. Remote access to resources, therefore, is becoming more common than ever.
Secure remote access is essential. As the proliferation of access and connectivity spreads from work to home to portable/mobile devices, access to the Internet and private LANs is becoming ubiquitous. Companies must use security controls on resource access or suffer the consequences of insecure access methods. With the removal of physical limitations for access comes the loss of control over where and how workers connect back into the private LAN.
Workers connect into the company LAN from mobile phones, through Internet cafés, over hotel networks, and at random Wi-Fi hotspots. Many use personally owned laptop computers and hand-held mobile devices rather than officially issued company systems. All of these are outside the control of the company's IT and security department. The only option is to limit LAN connections to those that can be secured. Thus, VPNs have become a necessity in the brave new mobile and interconnected world.
VPNs support remote access from a wide variety of complex devices, reduce risk caused by insecure access locations, and enable interaction with all LAN resources. Furthermore, flexibility, scalability, ease of administration, reliability, and more make VPNs an obvious choice in the face of modern connectivity risks and challenges.
Does every worker and every organization need VPNs and remote access? No. Many worker situations exist where VPNs are not the correct solution. These include any form of work that requires special tools, physical access to equipment, or close supervision by managers.
Remote access, mobile connectivity, and secured communications are solid reasons to deploy and use a VPN. But are these the only positive aspects of a VPN?
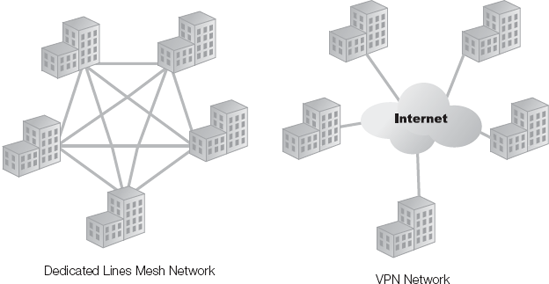
The most often touted benefit of VPNs is cost savings. They are a great way to save on long distance charges for telecommuters and traveling workers. They also create huge savings for businesses that would only need local Internet links for a VPN rather than a dedicated leased line between each location (Figure 3-5). The farther away each business location is and the more locations a company has, the more of a cost savings a VPN can generate.
Additionally, to truly compare the connectivity that a VPN offers to dedicated leased lines, you need a full mesh of leased lines. A full mesh requires a line between each business location. This allows for a direct communication between one site and another. Since a VPN across the Internet would provide the equivalent site-to-site communication capabilities, only a mesh network of dedicated lease lines can truly compare. This solution is obviously very expensive compared to a VPN's significant cost savings.
As corporations seek to reduce IT infrastructure costs, a common technique is to allow employees to telecommute. Telecommuting allows workers to access corporate resources whether the employee works from home, while traveling, or while on-site with a customer. In the past, telecommuting clearly implied the use of dial-up connections to connect with the company LAN.
With the proliferation of high-speed broadband connections and WiFi, telecommuting has become more plausible and realistic. Through the use of VPNs, telecommuting enables a true remote office rather than just a file exchange and communication system. VPNs make telecommuting not only possible, but also practical and secure. VPNs make expanding the workforce no longer a geographically limited proposition.
Extranets are often deployed as businesses establish new partnerships or seek more interaction with suppliers, distributors, and other external entities. Extranets are border networks, similar to a DMZ, where resources are hosted for access by external entities. However, unlike a DMZ, an extranet is not open for public use. Only a limited and specific set of users is allowed to connect into an extranet. Often, this limitation means that a specific VPN configuration is necessary to access the extranet's resources. With VPNs, extranets are both possible and practical.
VPNs allow for system administrators to remotely manage and control a network. VPNs allow employees to work from anywhere. VPNs allow friends to create WAN links to support multiplayer games. VPNs allow technical support to remotely repair client systems. A VPN is the solution anytime a network connection is needed between two systems or two networks, but installing a direct cable connection is unfeasible.
Often, the real benefits of a VPN are not from the VPN itself, but from all the new possibilities for work, research, learning, and play feasible because of a VPN. These benefits include:
Reduced equipment costs
Unlimited geographic connectivity
Increased flexibility and versatility of worker location
Improved privacy & confidentiality due to strong encryption
Verified transmission integrity
Fully scalable global infrastructure and architecture
Rapid deployment options
Flexible integration with existing networks and technologies
Faster return on investment (ROI) than traditional WAN infrastructures
Reduced dependence on long-distance carrier solutions
Reduced support burden as ISP
Individuals and organizations that use VPNs and integrate them in new and unique ways are sure to reap additional benefits. History shows us that as new means of communication are created, they often change and are used in ways that were unpredictable at the beginning of their adoption. However, VPNs are not perfect, and some very real and challenging issues limit the use of VPNs.
While the use of VPNs has many benefits, you need to evaluate the very real and distinct limitations before you put a VPN in place.
Although a VPN connection offers flexible secure communication options, it does not ensure quality of service. A VPN link is dependent upon the stability, throughput, and availability of the ISP connection as well as the intervening network connections between endpoints. VPNs over the Internet can easily suffer from latency, fragmentation, traffic congestion, and dropped packets. This also results in a lack of dedicated bandwidth between business sites, because of the volatility of the Internet.
While VPNs are excellent solutions over nearly every broadband connection option, over dial-up a VPN can be difficult to maintain. VPN traffic is encrypted and encrypted traffic does not compress. Most dial-up modem connections rely on compression—mainly hardware compression—to improve connection speed. When compression is not possible, a significant and noticeable speed reduction occurs. Additionally, VPN tunnel management can impose a significant increase in management overhead because of changes in protocol headers, potential authentication latency, and a prolonged connection establishment negotiation.
Another area of concern is the minor risk or potential of data exposure while in transit over the Internet. This is only a real concern if the VPN does not use encryption, uses poor encryption, or configures the encryption improperly. Proper security management will eliminate this as a serious concern.
Vulnerabilities exist at VPN endpoints. With a VPN, side attacks against the encrypted link are nearly eliminated. However, data entering or leaving the VPN is at risk. An end-user computer could be infected by malicious code that can traverse the VPN link into the company LAN. Also, private and confidential data from the company LAN can be copied across the VPN link to the end-user computer. On this computer, that data is less secure and subject to a wider range of threats.
You should also consider the increased difficulty in providing technical support remotely. This is especially true when the remote connection itself is not functioning. In addition, it's more difficult to keep remote systems in compliance with security settings, conduct training, allow supervisory oversight, enable HR management, and monitor user activities.
Not every person is a good candidate for a remote user. Those who are easily distracted, who are not motivated, or whose home environment is not conducive to work are prime examples of those who should stay in the office rather than work from home.
An even larger concern is granting open or blanket unrestricted network-resource access to those connecting via VPN. You must enforce stronger authentication and authorization limitations on VPN users, especially on VPN telecommuters. Remote users should have access only to those resources necessary for their current tasks. Unlimited access to network resources can quickly result in exploitation and confidential data leakage, if the remote user or the remote computer is compromised.
If you understand these limitations and address them properly, you can help to avoid catastrophic mistakes when correctly installing and productively using VPNs. One of the primary tools to accomplish this is the VPN policy.
Effective VPN policies are those that clearly define security restrictions imposed on VPNs that align with the overall IT mission and goals of your organization. VPNs can offer numerous exciting possibilities of mobility and interconnection. However, VPNs can also be a risk to the confidentiality and stability of your organization's infrastructure.
Like all security policies, your VPN policy should derive from a thorough risk assessment and analysis. Without fully understanding the assets, processes, threats, and risks of VPNs, you can't effectively use or manage them.
Developing your VPN security policy is not a simple or straightforward task. You need to plan for time and effort to address a wide variety of issues and concerns. Some of the aspects of design and planning of a VPN policy include (but are not limited to):
Consider the benefits and drawbacks of software and hardware VPN solutions
Impose stringent multi-factor authentication on all VPN connections
Implement strong access control (authorization) restrictions on all VPN connections
Define how the VPN will be managed, through what interfaces, and by whom
Define the mechanisms of providing remote technical support for VPN telecommuters
Enable detailed auditing on all activities occurring across or through a VPN
Define distinct qualifications on granting user access to telecommuting VPNs
Prescribe the user training requirements for all VPN activities
You can learn more about crafting a VPN policy in Chapter 12.
One of the first decisions you face when deploying a VPN is: what device will serve as the termination point of the secured tunnel? You have several options, but often the decision rests on where in the network infrastructure you want to position the tunnel endpoint. Additionally, the features the VPN device provides may be a factor in the decision, as well.
Such factors include deciding which devices have sufficient processing power to maintain wirespeed even with heavy traffic and complex encryption. Another concern is whether NAT is present, as this can impose problems for tunnel mode encryption. (Learn more about this topic in Chapter 13 in the section, "VPNs and NAT.")
The three primary VPN device models are edge router, corporate firewall, and VPN appliance. In addition to the selection of the VPN device, you have several architectural decisions to make, as well. These focus on the intended purpose, function, or use of the VPN, such as remote access, host-to-host, site-to-site, and extranet access.
With edge routers as the VPN termination point, the VPN link exists only over the public intermediary networks, not within the private LAN(s). This does require that the edge router support VPN connectivity.
Edge router VPN termination ensures that a firewall can filter the traffic exiting the VPN on its way into the LAN. This method insures that all traffic, regardless of transportation means, complies with the firewall's filtering rules. If the VPN terminates inside the firewall, then traffic from the VPN could potentially violate security because it was not firewall-inspected.
VPN termination on edge routers is best suited for controlled access into the DMZ. Such a configuration grants business partners easy access to the DMZ without exposing their traffic to the Internet or granting them unnecessary access to the private LAN.
Terminating the VPN at the corporate firewall is possible if the firewall supports VPN services. Not all firewalls provide this service, so this depends on your choice of make and model of the firewall product. With a firewall-to-firewall VPN across the public network, users from one network LAN can access resources in another network LAN without additional complexities. Primarily, this configuration treats the VPN link between the firewall endpoints as just another route in the LAN (actually WAN). The benefit here is that users don't need to re-authenticate or abide by additional firewall restrictions when the VPN terminates at the corporate firewall.
Corporate firewall termination of the VPN means that the traffic entering or leaving the VPN does not pass through the filtering restrictions of the firewall. Instead, the firewall simply serves as a tethering point for the VPN tunnel endpoint. Any traffic not associated with the VPN, however, is subject to firewall investigation.
This configuration has a potential limitation. As the number of VPN links increases or the traffic load of the VPNs increases, the resulting increase in cryptographic computations could interfere with the firewall's wirespeed filtering performance. In this case, perform a trend analysis to monitor for this condition and improve firewall performance before a bottleneck occurs.
A third device option is a dedicated VPN appliance. Unlike an edge router or firewall termination point, a dedicated VPN appliance specifically handles the load of a VPN, instead of VPN support being an add-on service.
You can position a VPN appliance outside the corporate firewall, in a similar location to an edge router, so that all VPN traffic passes through firewall filters. A VPN appliance can also reside inside the corporate firewalls to prevent firewall filtration. This deployment is similar to the corporate firewall concept, at least in terms of not filtering VPN traffic. This second deployment method also ensures that no external entity can interfere with the endpoints of the VPN tunnel.
These techniques are useful when corporate firewalls already exist that do not support the VPN technology or architecture you want. So rather than replacing the firewalls, you install an additional dedicated VPN appliance.
The first VPN architecture is basic remote access (Figure 3-6). Remote access VPN is also known as host-to-site VPN since it supports single-host VPN connections into a LAN site. This design grants individual telecommuters or traveling workers easy access into the private LAN. A single LAN can support several remote users with any of the VPN endpoint concepts: edge router, corporate firewall, or VPN appliance.
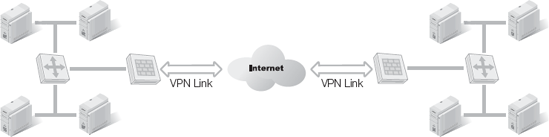
A second VPN architecture is site-to-site (Figure 3-7). Site-to-site VPNs are also known as LAN-to-LAN VPNs or WAN VPN connections between LANs. Regardless of the name, a site-to-site VPN supports secure connections between LANs over intermediary public networks. When you install it properly, a site-to-site VPN can be an inexpensive mechanism to create a single distributed LAN (also known as a WAN) for a multi-location organization. A site-to-site VPN uses any of the VPN endpoint concepts: edge router, corporate firewall, or VPN appliance.
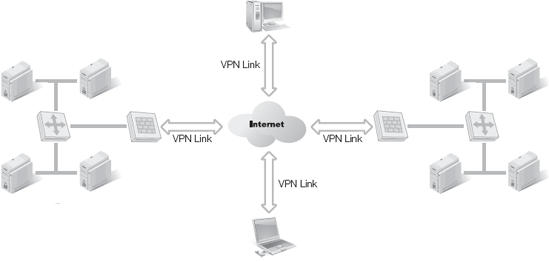
A slight variation on the site-to-site VPN is the site-to-site VPN with remote mobile users. This is a combination of the site-to-site VPN concept with remote access VPNs (Figure 3-8). The benefit of this architecture is the ability to add new employees with secure connections to the LAN without needing additional corporate facilities to provide on-site workspaces.
A third VPN architecture is host-to-host. Host-to-host VPNs are also known as client-to-server or remote-to-office or remote-to-home VPNs. A host-to-host VPN is a direct VPN connection between one host and another. This mechanism operates over a public network or within a private network. Over a public network, a host-to-host VPN provides a secure connection against the public. Over a private network, it provides an additional level of security for mission-critical or highly sensitive transactions.
Host-to-host VPNs labeled as client-to-server VPNs create secure client interaction with the services of a resource host. This is similar to, but not exactly the same as, a secure Web link between a Web browser and a Web server. SSL can be used for application protocol security, as it is with secure Web sessions, or as a VPN protocol. As a VPN protocol, SSL operates at the network layer; as a Web session security tool, it operates at the top of the transport layer. You can learn more about SSL operations in Chapter 13.
A remote-to-office VPN is a direct link between a portable or home system and an office workstation. This VPN link up allows a user to work from home or while traveling without sacrificing access to resources, services, or applications that might only be installed (or licensed) for use on the office workstation computer. This VPN can establish a remote control session as commonly as a remote access session.
A remote-to-home VPN connects a work computer or a portable computer back to a home system, effectively the opposite configuration of the remote-to-office. The remote-to-home VPN grants you access to a home computer while you are away from the house.
The host-to-host VPN variations usually depend on software VPN solutions native to the operating system or third-party applications installed on the host. However, some VPN appliances are adaptable to these simpler host-to-host connectivity architectures.
A fourth VPN architecture is extranet access. With a VPN tunnel endpoint positioned at or inside the perimeter of an extranet, this option serves as a pathway for business partners, distributors, suppliers, and so forth to gain access to corporate resources without exposing their traffic to the Internet or granting them unnecessary access to the private LAN.
Additionally, a VPN linked into the extranet as opposed to the DMZ provides greater security to the remote entities. A VPN link to the DMZ exposes the remote entities to any threats found in the DMZ. Since the DMZ is publicly accessible, it's risky. An extranet VPN grants the remote entity secure communications without significant risks at the VPN termination point.
VPNs commonly serve as a choke point to control which external entities have access to the extranet. Only those granted specific access, assigned user accounts, and provided configuration details are able to configure and establish a VPN link with an extranet.
VPNs can use two main types of encapsulation encryption. These are known as tunnel mode and transport mode encryption.
Tunnel mode encryption protects the entire original IP packet's header and payload. This encrypted packet becomes the payload of a new IP packet with a new IP header. This form of encryption ensures that the identities of the original endpoints of the communication are kept confidential while the traffic traverses the secured link. Tunnel mode encryption is commonly used by VPNs linking network sites together or providing secure remote access.
Transport mode encryption protects only the original IP packet's payload. The encrypted payload retains its original IP header. This form of encryption only protects the payload, not the identities of the endpoints. Transport mode encryption helps VPNs link individual computers together.
Encryption and a secure VPN are virtually inseparable. A secure VPN exists only because its traffic is encrypted. But some trusted VPNs may or may not use encryption. To fully understand and appreciate the operations of VPNs, you need a reasonable understanding of encryption.
Encryption is just one aspect of the larger topic of cryptography. Cryptography is the art and science of hiding information from unauthorized third parties. Cryptography occurs through a complimentary and reversible process: encryption and decryption. Encryption is the process of converting original usable form data, called plain text, into unusable chaotic form, called ciphertext. Decryption is the process of converting ciphertext back into plain text. A real-world communication product must provide both encryption and decryption.
Modern cryptography is based on algorithms. An algorithm is a set of rules and procedures, usually mathematical in nature, that define how the encryption and decryption processes operate. Algorithms are often very complex. Many algorithms are publicly known and anyone can investigate and analyze the strengths and weaknesses of an algorithm.
Encryption algorithms use a key. The key is a unique and secret number that controls the encryption and decryption processes performed by the algorithm. A key is a very large binary number measured or defined in terms of its bit length. The bit length of the key is the number of binary digits that compose the key. For example, a key of 128 bits is 128 binary digits long.
The bit length of an algorithm's key defines that algorithm's key space. The key space is the range of keys that are valid for use for that specific algorithm. Any key created using the specific number of binary digits of the key length is part of that algorithm's key space. This key space includes every number between a key of all 0s to a key of all 1s (remember this is binary code with only 1s and 0s as digits). This means that 2^128 number of keys are available to an algorithm with a key length of 128 bits. 2^128 in decimal is over 3.4 × 10^38.
Three main types of algorithms operate within the realm of cryptography: symmetric, asymmetric, and hashing.
Symmetric cryptography is based on algorithms that use a single, shared secret key. A common way to remember the type of key used by symmetric is to remember a synonym for symmetric: same. The same key must encrypt and decrypt data and the same key must be shared with all communication partners of the same session.
Symmetric cryptography is very fast in comparison to asymmetric cryptography, typically 10,000 times faster with similar key length and message size. Generally, the longer the length of a symmetric key, the stronger the encryption produced. Most algorithms have one or only a few key length options, so picking an algorithm with a longer key often ensures stronger encryption. Keys shorter than 128 bits are considered weak, keys of 128 to 256 bits are considered strong, and keys longer than 256 bits are considered very strong. That's why when you select a symmetric cryptography product, you should only use solutions employing 128 bit or longer keys.
Selecting a strong algorithm is more involved than just key length; you also need to consider other issues, such as use of random numbers, use of the avalanche effect, and resistance to reverse engineering attacks. Most weak algorithms do not survive long once released to the public, so most consumers do not need to focus as much on the details of the algorithm as to look for algorithms that support longer keys. The general rule (which does gloss over some of the details) is that longer keys are better. For more information on cryptography, selection of algorithms, and the internal workings of algorithms, please consult "Schneier's Cryptography Classics Library" or "Introduction to Modern Cryptography."
Note
Hypothetical communication partners Bob and Alice are commonly used to describe and discuss the functions of cryptography.
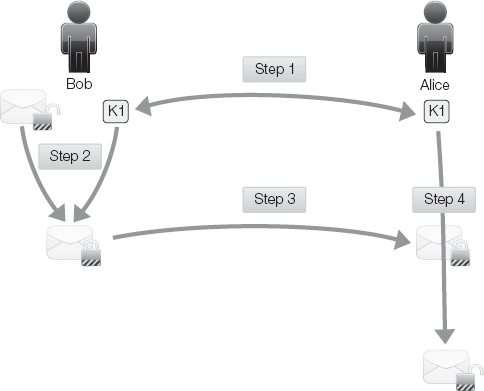
Symmetric cryptography works as follows (Figure 3-9):
Bob and Alice exchange a symmetric key (K1) (This process is normally performed by an asymmetric process or "out of band" communication).
Bob encrypts a message with the shared symmetric key.
Bob transmits the message to Alice.
Alice decrypts the message using the shared symmetric key.
The security service provided by symmetric cryptography is confidentiality. Symmetric encryption, with a reasonably long key, prevents unauthorized third parties from accessing or viewing the contents of communications or stored data files. Symmetric cryptography protects files on storage devices, as well as data in transit. In fact, due to its strength and efficiency, symmetric cryptography is the preferred method to secure data in storage or in transit of any size.
Some examples of symmetric cryptography algorithms or systems include: DES, 3DES, AES, CAST, RC4, RC5, RC6, RC7, IDEA, Twofish, and Blowfish.
VPN solutions employ symmetric cryptography to protect communications in transit. This protection prevents unauthorized eavesdropping or mid-stream modifications.
Asymmetric cryptography is based on algorithms that use either key pairs or some other special mathematical mechanism. Asymmetric cryptography that uses key pairs is commonly known as public key cryptography. All public key cryptography is asymmetric, but some asymmetric algorithms are not public key algorithms. A common way to remember the types of keys or non-keys that are used by asymmetric cryptography is to remember a synonym for asymmetric: different. Different keys are used for different purposes, different keys are used by different members of the communication session, and some systems use something different from keys altogether.
Asymmetric cryptography is very slow in comparison to symmetric cryptography. This is due to the complexity of the math used by these algorithms, as well as the length of asymmetric keys (when there are keys). Public key cryptography uses keys that are 1024 to 8192 bits long (and sometimes longer).
Asymmetric cryptography also uses math based on a concept known as one-way functions. A one-way function is a mathematical operation performed in one direction relatively easily, but impossible or nearly so to reverse. This type of math was formalized into cryptographic algorithms only in the late 1970s.
Asymmetric cryptography, therefore, is slow in comparison to symmetric due to its extremely long keys and its extraordinarily complex mathematical functions. Thus, asymmetric is generally not suitable for encrypting bulk data for storage or transmission; instead this type of encrypting is best suited for identity proofing and key exchange.
The protections provided by asymmetric cryptography are authenticity and non-repudiation. Authenticity is a term used to convey the combination of authentication and access control. Based on usage, especially with public key cryptography, asymmetric solutions can prove the identity of the source of a message (authentication) or control the destination or receiver of a message (access control). Additionally, when used properly, asymmetric cryptography may provide proof that a sender sent a message and prevent them from being able to credulously deny sending it. This is known as non-repudiation.
Public key cryptography, a sub-set of asymmetric cryptography, is based on key pairs. Each participant in a communication or community has a discrete key pair set. The key pair set consists of a private key and a public key. The private key is kept secure and private at all times. The public key is put out for open public access and use. The key pairs work together as opposites. The encryption or encoding that one of the keys performs can only be undone by the opposite key of the pair.
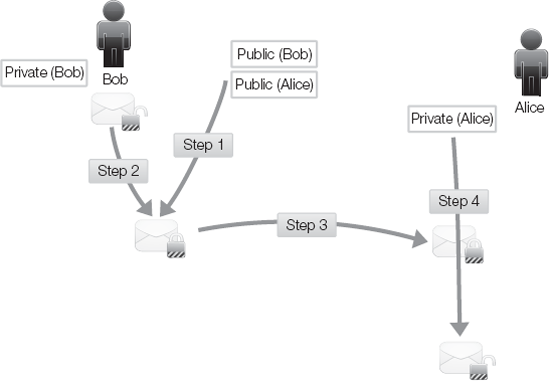
One mechanism afforded by asymmetric cryptography is a digital envelope. It works as follows (Figure 3-10):
Bob obtains Alice's public key.
Bob encodes a message with Alice's public key.
Bob sends the message to Alice.
Alice decodes the message using her private key.
The encoded message is only readable by Alice who has the corresponding private key. A digital envelope ensures that the message is only accessible by the intended recipient, namely the owner of the corresponding private key. The mechanism of digital envelope exchanges symmetric keys between communication partners. In this mechanism, one side of the conversation performs key generation, and then exchanges that key securely. This is the mechanism VPNs use to exchange keys securely.
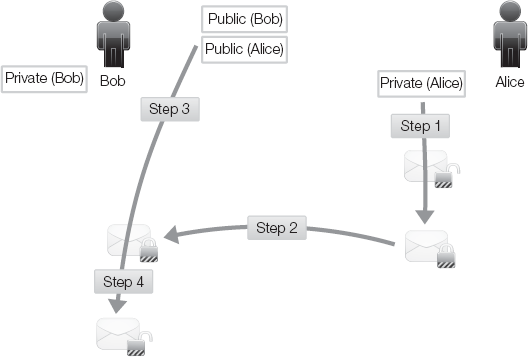
Another mechanism afforded by asymmetric cryptography is a digital signature. A digital signature proves the identity of the sender. It works as follows (Figure 3-11):
Alice uses her private key to encode a message.
Alice sends the encoded message to Bob.
Bob accesses Alice's public key.
Bob uses Alice's public key to unlock the encoding.
This process proves to Bob that the message came from Alice. This is authenticity. A digital signature does not prevent others from viewing the message or confirming the source of the message. A digital signature is not encryption; it does not provide confidentiality protection. VPNs use digital signatures, but they usually employ the version that uses hashing as part of the process (see next example).
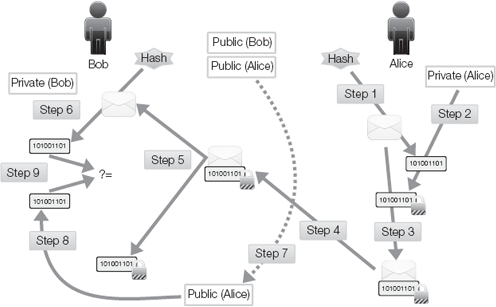
This mechanism of digital signatures improves through the addition of hashing. (Please see the discussion of hashing in the next section.) A digital signature using hashing is a bit more complex, and uses the following procedure:
Alice computes the hash value of a message.
Alice encodes the hash value with her private key. This encoded hash is the digital signature.
Alice adds the encoded hash to the message.
Alice transmits the message.
Bob strips off Alice's digital signature.
Bob hashes the original message to compute its hash.
Bob obtains Alice's public key.
Bob decodes Alice's digital signature to reveal Alice's original hash.
Bob compares Alice's original hash to the hash Bob calculated.
If the hashes are the same, Bob accepts the message as retaining its integrity. This has also proved that the message was from Alice (authenticity). Furthermore, this process ensures that Alice cannot deny having sent it (non-repudiation). VPNs commonly employ this form of digital signature to prove the identity of the endpoints and confirm the integrity of transmissions.
Some examples of asymmetric cryptography algorithms or systems that are not-public key cryptography include: Diffie-Hellmann, El Gamal, and Elliptical curve cryptography (ECC). The most common example of an asymmetric cryptography algorithm or system that is public key cryptography is Rivest-Shamir-Adelman (RSA).
VPN solutions employ asymmetric cryptography to secure symmetric key exchange (via digital envelopes), authenticate VPN link endpoints or users (via digital signatures), and, when used in conjunction with hashing, verify source and integrity of transmitted messages (also digital signatures).
Hashing is the cryptographic function that takes the input of a file or message and creates a fixed length output. The input can be of any size, but the output is a fixed length based on the hashing algorithm used. Hashing does not modify or alter the original data in any way; it simply uses the original data to generate a hash value as a new data item. Common hash value output lengths include 128 bits (such as those produced by MD5), 160 bits (such as those produced by SHA-1), and even 512 bits or more (such as those produced by various members of the SHA-2 family).
Note
The output of a hash algorithm can be called a hash, a hash value, a message digest, a message authenticating code, a fingerprint, a digital value, or a checksum.
Hashing checks integrity. Hashing computes a hash value upon storage or transmission of a file or message, then computes another hash value at the end of the storage period or upon receipt of the transmission. If the before and after hash values are the same, then the message retained its integrity. If the before and after hash values are different, then the message has lost its integrity and is no longer trustworthy or usable.
Hashing verifies integrity based on the complex mathematical functions used in the hashing algorithm itself. A central component or feature of these functions is the avalanche effect. This effect ensures that small changes in the input data produce large changes in the outputted hash value. A single binary digit change in a file should produce a clearly recognizable difference in the resultant hash value.
Hashes are a one-way function. A hash value cannot be reversed directly back into the original data file from which it was calculated. Thus, if an attack obtains a hash value, the data is not at significant risk of being extracted from the hash.
Some examples of hashing algorithms or systems include: MD5, HAVAL, SHA-1, and the SHA-2 variants (SHA-256, SHA-384, SHA-512, etc.).
VPNs employ hashing, often as part of digital signatures, as a method to confirm that transmitted data has retained its integrity. Any mis-matching of hash values discards the received data and requests a re-transmission. This ensures that either end of a VPN connection accepts only fully valid and true data.
Now that you know about symmetric cryptography, asymmetric cryptography, and hashing, let's take a look at the overall process VPNs use to provide secure communications. A basic VPN setup process occurs as follows:
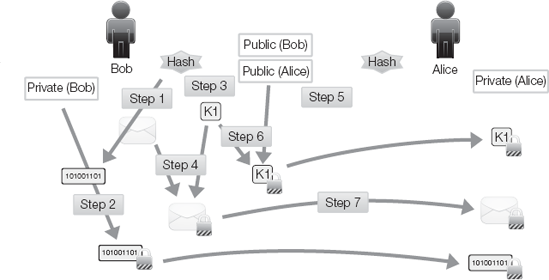
Bob computes the hash from a message (Figure 3-13).
Bob encodes the hash using his private key to create a digital signature.
Bob generates a random symmetric key (K1).
Bob uses K1 to encrypt the message.
Bob obtains Alice's public key.
Bob encodes K1 with Alice's public key to create a digital envelope.
Bob sends the digital signature, the encrypted message, and the digital envelope to Alice.
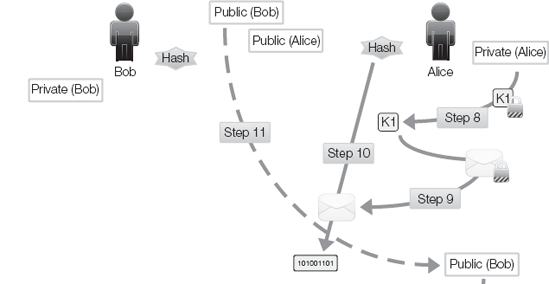
Alice uses her private key to decode the digital envelope to reveal K1 (Figure 3-14).
Alice uses K1 to decrypt the message.
Alice computes the hash of the message.
Alice obtains Bob's public key.
Alice decodes the digital signature with Bob's public key to obtain Bob's hash value.
Alice compares the pre- and post-hash values. If the hash values are the same, then the message has retained its integrity. Thus, the correct public key decoded the digital signature. Bob's identity is verified (authenticity and non-repudiation).
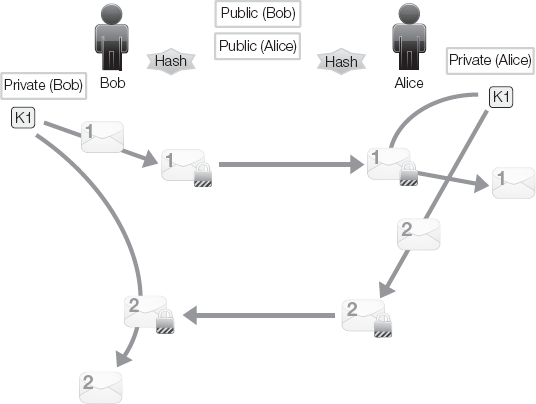
The result of this exchange now enables the symmetric key to secure subsequent messages from Bob to Alice or from Alice to Bob (Figure 3-15). Once a VPN has been established between Bob and Alice, an exchanged session key (K1) exists at both endpoints. Using this shared session key, Bob can encrypt messages (envelope #1) to send to Alice and Alice can encrypt messages (envelope #2) to send to Bob (Figure 3-15).
Variations on this basic VPN session establishment are possible. One variation would be to encrypt both the message and the digital signature with K1. Another variation would have Bob digitally sign K1 with his private key before using Alice's public key to encode it into a digital envelope.
This initial symmetric key exchange establishes the encryption that will protect all subsequent messages for the current communication session. When this session ends and a new VPN session begins, a new symmetric key will initiate the process. However, as long as the current session lasts, the same symmetric key applies.
Reusing a symmetric key poses a slight risk, even for multiple messages in the same session or conversation. To minimize or reduce this risk, some VPNs use rekeying processes. Rekeying discards the current in use key and generates and exchanges a new symmetric key. Rekeying comes in several types:
Time rekeying—Rekeying triggers at a specific time.
Idle rekeying (lag or delay)—Rekeying triggers when a specific amount of idle, lag, or delay in the conversation occurs.
Volume rekeying—Rekeying triggers when a specific amount of traffic is transmitted.
Random rekeying—Rekeying triggers at random time intervals.
Election rekeying—Either member of a VPN session can elect to rekey at any time
If a VPN solution performs mid-session rekeying, you may or may not have an administrative configuration option to manage the rekeying processes. Rekeying may be imbedded in the encryption algorithms. One-time pad encryption systems are also possible. A one-time pad system uses a unique and random symmetric key for each segment of a communication. This is a more complex system, but offers greater security. Attempting to crack a multi-random-key encryption scheme is one of the most difficult attacks against encryption known.
Note
Technically, computers provide pseudo one-time pads, as they are currently unable to produce true random numbers. Instead, a pseudo random number generator (PRNG) is used. A PRNG uses a complex algorithm and the timing chip to produce seemingly random numbers. The result is very good, but not truly random.
You can increase the reliability of authenticity and non-repudiation by using digital certificates instead of plain public and private keys. A digital certificate is a public key and private key pair digitally signed by a trusted third party. This third party is a Certificate Authority (CA). The CA first verifies the identity of the person or company, then crafts and issues the digital certificates.
In addition to improved reliability, certificates also resolve a scalability issue with public key cryptography systems. Without certificates, each system has to manage an ever-expanding library of public keys. With a third-party certificate-based system, each system no longer needs to retain public keys. Instead, they are exchanged at the beginning of each session with the assistance of the CA.
Each host stores only the trusted public keys of the CA. The CA's public keys are stored in the trusted roots list (TRL). Any certificate issued by a trusted CA is accepted as valid, providing the certificate is expired and has not been revoked.
The process is similar to the overall cryptographic process to establish a VPN connection. The primary difference is that instead of a sender's generic private key, the sender's digital certificate encodes the message. Then, the recipient uses the CA's public key to start the unpacking process. The CA's public key decodes the CA's private key encoding around the sender's public key (This is the sender's digital certificate). This confirms the identity of the sender through the CA's issued digital certificates. Then, the recipient uses the sender's public key to decode the sender's private key encoding on the message.
The use of digital certificates adds a few additional steps to the overall process, but this improves the identity verification of the participants in the secured communication. Once a communication session ends, the recipient can discard the sender's public key. Each time a new session starts, the sender's public key will be re-exchanged via the digital certificate process. This reduces the burden of public key management and makes any secure communication service, including VPNs, much more scalable.
Authentication is the process of confirming or proving the identity of a user and is of significant importance for VPNs. Since VPNs allow external entities to connect to and interact with a private network (or system), verifying the identity before granting access is paramount. VPN authentication takes place on two levels: connectivity and user.
When a VPN link starts, the hardware and software components at each endpoint must authenticate to establish the connection. Once the communication link begins, the user performs a separate and distinct authentication process. If either of these identity proofs fail, the VPN is severed.
The actual mechanism of authentication used in either case can vary. Options include username and password, smart cards, token devices, digital certificates, and even biometrics. As a rule of thumb, you should avoid username- and password-only solutions and lean toward multi-factor authentication options. Password-only based authentication is notoriously exploitable and is not reliably secure enough for a VPN.
The VPN services, whether software or hardware, may support authentication directly or indirectly when offloaded to dedicated authentication servers. Offloading can point to any number of widely used AAA (authentication, authorization, and accounting) services or technologies, including RADIUS, TACACS, 802.1x, LDAP, and Active Directory.
When selecting an authentication solution for a VPN, consider the strengths and weaknesses of the authentication factors independently of their VPN integration. If an authentication factor has weaknesses on its own, these are not relieved when used with a VPN.
VPN authentication should be scalable and support interoperability among potential connecting hosts. Don't use authentication that cannot support more than a few dozen users or hosts. Likewise, using a form of authentication that is only available on one platform or operating system will impose limitations difficult and expensive to resolve later.
Authorization is controlling what users are allowed and not allowed to do. Authorization is also known as access control. You must establish clearly defined policies as to what activities will and will not be supported for VPN connections.
An initial concern is defining who is and who is not allowed to establish a VPN connection. By considering VPN a resource rather than just a method of connectivity, clearly not all users should have access to all resources. If VPN connectivity is neither essential to nor conducive of a worker's assigned tasks and responsibilities, they should not be allowed to open or use VPN connections.
Authentication can help enforce this access control issue. Whenever a user account not VPN authorized attempts to authenticate across a VPN, that attempt should fail. In fact, automatically locking such an account is a reasonable security response. Users should have a clear understanding of whether or not they have been granted the privilege of VPN use. Any access of a non-VPN approved user across a VPN, therefore, is either a sign of a policy-violating employee or an outside intrusion attempt.
In addition to locking down use of the VPN itself, restrict access to resources across a VPN, even for authorized users. A VPN does establish a network connection indistinguishable except for speed from a local direct-wired connection, but that does not mean that the same level of authorization is necessary, required, or even recommended.
A stronger application of the principle of least privilege is needed with VPN connectivity. Not all of the tasks and resources employees use when on site are necessarily required for activities they perform remotely. A user should have one level or sphere of access when on-site and a different, smaller sphere of access when connecting through a VPN. This, of course, will depend upon the assignments of the worker and the sensitivity of the resources needed to carry out those assignments, but thoroughly consider this issue before granting default or wholesale access.
Mission-critical resources, processes, and information may be at risk if they're exposed to users connecting over a VPN. Since a remote user's computer is potentially less secure than work stations on-site, the additional risk may be significant. Does a telecommuter or traveling worker actually need access to a specific resource? If not, block access.
Should a remote VPN user be able to transfer sensitive, private, or valuable data to the remote host? This is the risk of information leakage. Once data leaves the LAN, the corporate security infrastructure loses its ability to fully control and protect the information. On a remote host, once the VPN disconnects, the LAN's security protections disappear. The only remaining security left is on the host and practiced by the user.
Remote access is inappropriate or just impractical for some resources. For example, consider preventing printer access by remote VPN users. Do traveling workers need to print documents they are unable to physically handle? Yes, in some situations, remote printing makes sense. But should you allow every local activity over a VPN just because it's possible?
Another authorization concern is whether or not to allow Internet communication for VPN users. If local LAN users are able to access the Internet, then technically so can VPN users. But should they? Is this an additional risk or just an additional bandwidth consumption burden?
If VPN users are unable to access the Internet from the LAN through the VPN, can they access the Internet simultaneously over the same ISP link as their VPN link to the LAN? This configuration is known as a split tunnel. Many organizations see this as a significant risk. This scenario enables the possibility that an Internet attack could breach the remote host, and then use the VPN to access the private LAN. This would be a nearly unrestricted pathway between the Internet and the LAN. Most organizations employ VPN connection solutions that prevent simultaneous local VPN and Internet connectivity on remote hosts.
Even with these VPN authentication issues, the overall process of enforcing access control is essentially the same for both local and remote hosts. In most cases, access control is defined on the resource itself, regardless of where the users are. Keep this in mind as you craft policies defining the parameters of VPN management and use.
VPNs are mechanisms to remotely connect LANs and mobile hosts. VPNs save money and offer worker flexibility. VPNs secure communications over public intermediary networks. VPNs should be used whenever infrastructure costs are high or you need mobile access, and flexibility. VPNs can't guarantee quality of service over the Internet or protect against endpoint device/host vulnerabilities. You should deploy VPNs based on thoroughly researched VPN policies.
VPNs offer many advantages, including a wide range of implementation choices. Various devices and software products support VPN connections. VPNs' endpoints can be inside, on, or outside a firewall. VPNs can support remote access for mobile hosts, create links between individual systems, and support channels between networks. VPNs can employ either tunnel-mode or transport-mode encryption. They can use the same authentication and authorization techniques that you deploy elsewhere for general network security.
Algorithm
Asymmetric cryptography
Authentication, authorization, and accounting (AAA) services
Authenticity
Avalanche effect
Certificate Authority (CA)
Channel
Ciphertext
Client-to-server VPN
Compression
Corporate firewall
Cryptography
Decryption
Dedicated connection
Dedicated leased line
Digital certificate
Digital envelope
Digital signature
Distributed LAN
Eavesdropping
Edge router
Extranet VPN
Fragmentation
Full mesh
Hardware VPN
Hash or hash value
Hash algorithm
Hashing
Host VPN
Host-to-host VPN
Host-to-site VPN
Hybrid VPN
Identity proofing
Intermediary network
Key or encryption key
Key exchange
Key pair
Key space
LAN-to-LAN VPN
Latency
Leased line
Modem
Multi-factor authentication
Non-dedicated connection
Non-repudiation
One-time pad
One-way function
Optical carrier (OC)
Out of band
Private branch exchange (PBX)
Private key
Pseudo random number generator (PRNG)
Public key
Public key cryptography
Public network
Rekeying
Remote access VPN
Remote-to-home VPN
Remote-to-office VPN
Scalability
Secured VPN
Site-to-site VPN
Software VPN
Split tunnel
Symmetric cryptography
Telecommuting
Traffic congestion
Trusted third party
Trusted VPN
Virtual private network (VPN)
VPN appliance
WAN VPN
Which of the following is not a valid example of a VPN?
A host links to another host over an intermediary network
A host connects to a network over an intermediary network
A network communicates with another network over an intermediary network
A host takes control over another remote host over an intermediary network
A mobile device interacts with a network over an intermediary network
Which of the following is not ensured or provided by a secured VPN?
Confidentiality
Quality of service
Integrity
Privacy
Authentication
Which of the following techniques make(s) a VPN private?
A single organization owning all the supporting infrastructure components
Leasing dedicated WAN channels from a telco
Encrypting and encapsulating traffic
Both A and B
Items A, B, and C
What is the primary difference between a VPN connection and a local network connection?
Speed
Resource access
Security
Access control models
Authentication factors
Which of the following is not a true statement?
VPN traffic should be authenticated and encrypted.
VPNs require dedicated leased lines.
Endpoints of a VPN should abide by the same security policy.
VPNs perform tunneling and encapsulation.
VPNs can be implemented with software or hardware solutions.
What is a hybrid VPN?
A VPN with a software endpoint and a hardware endpoint.
A VPN supporting remote connectivity and remote control.
A VPN consisting of trusted and secured segments.
A VPN supporting both symmetric and asymmetric cryptography.
A VPN using both tunneling and encapsulation.
What is the most commonly mentioned benefit of a VPN?
Cost savings
Remote access
Secure transmissions
Split tunnels
Eavesdropping
Which of the following is a limitation or drawback of a VPN?
Intermediary networks are insecure
VPNs are not supported by Linux OSs
VPNs are expensive
VPNs reduce infrastructure costs
Vulnerabilities exist at endpoints
On what is an effective VPN policy based?
A thorough risk assessment
Proper patch management
Business finances
Flexibility of worker local
Training
What form of VPN deployment prevents VPN traffic from being filtered?
Edge router
Extranet VPN
Corporate firewall
Appliance VPN
Host-to-Site VPN
What form of VPN deployment requires additional authentication for accessing resources across the VPN?
Site-to-Site VPN
Corporate firewall
Host-to-site VPN
Edge router
Remote access VPN
Which of the following is not a name for a VPN between individual systems?
Client-to-server
Host-to-host
Remote-to-home
Host-to-site
Remote-to-office
Which of the following is the primary distinction between tunnel mode and transport mode VPNs?
Whether or not it can support network to network links
Whether or not the payload is encrypted
Whether or not it can support host-to-host links
Whether or not the header is encrypted
Whether or not it supports integrity checking
What VPN implementation grants outside entities access to secured resources?
Edge router VPN
Corporate firewall VPN
Site-to-Site VPN
Extranet VPN
Remote control VPN
What form of cryptography encrypts the bulk of data transmitted between VPN endpoints?
Symmetric
Hashing
Public key
Transport mode
Asymmetric
What components create a digital signature that verifies authenticity and integrity?
Public key and session key
Private key and hashing
Hashing and shared key
Session key and public key
Shared key and hashing
By what mechanism do VPNs securely exchange session keys between endpoints?
Digital envelope
Digital forensics
Digital encapsulation
Digital certificate
Digital signature
What are the two most important features of VPN authentication?
Single factor and replayable
Scalability and interoperability
Transparent and efficient
Interoperability and single factor
Replayable and scalable
What VPN access control issue can be enforced through VPN authentication?
Blocking unauthorized VPN users
Restricting access to the Internet
Limiting access to files
Filtering access to network services
Controlling access to printers
When designing the authorization for VPNs and VPN users, what should be the primary security guideline?
Scalability
Multi-factor
Distributed trust
Principle of least privilege
Grant by default, deny by exception
All of the following statements about a host-to-host VPN are true except:
Are commonly supported by the host OS
Must be implemented with VPN appliances
Can be interoperable between different OS products
Usually employs transport mode encryption
Can be established within a private network
All of the following are commonly used in supporting a site-to-site VPN except:
VPN appliance
Commercial firewall
Client VPN software
Edge router
VPN gateway proxy
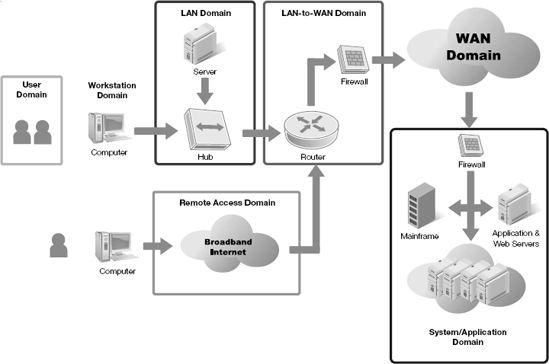
A VPN used to connect geographically distant users with the private network is located within which domain from the seven domains of a typical IT infrastructure (Figure 3-16)?
LAN Domain
User Domain
System/Application Domain
Remote Access Domain
LAN-to-WAN Domain
What feature or function in tunnel mode encryption is not supported in transport mode encryption?
The header is encrypted
The payload is encrypted
The source address is encrypted, but not the destination address
A footer is added to contain the hash value
Provides encryption protection from the source of a conversation to the destination
All of the following statements are true except:
Encryption ensures VPN traffic remains confidential
It is possible to have a private VPN without encryption
VPN authentication ensures only valid entities can access the secured connection
Authorization over a VPN consists exclusively of granting or denying access to file resources
VPN authentication can include multi-factor options