Using the Trust Center
You use the Trust Center to change security and privacy settings in Microsoft Access. Take the following steps to work with the Trust Center:
- Click the Microsoft Office button and select Access Options.
- Select Trust Center on the left side of the Access Options dialog box.
- Click Trust Center Settings. The Trust Center dialog box appears. Here, you can set the various security settings for Microsoft Office Access 2007.
Working with the Message Bar
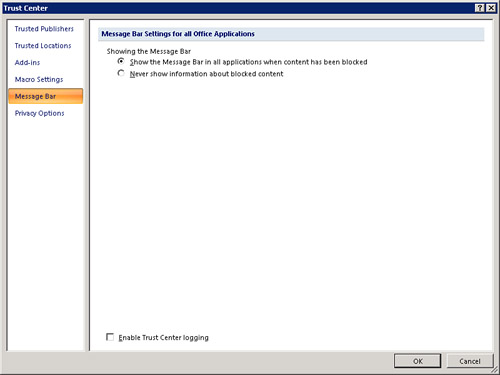
The message bar provides quite a bit of valuable information. Access displays security alerts, workflow tasks, server document information, and policy messages. The message bar appears by default whenever it is appropriate. You can use the Trust Center to control when the message bar displays (see Figure 17). The first option shows all appropriate security messages. The second option hides the message bar in all situations. This feature interacts with the Disable All Macros Without Notification option. If you click Disable All Macros Without Notification, you won’t get message bar alerts. If you select Never Show Information About Blocked Content, you will not receive any warnings about security issues, regardless of the other settings that you have selected in the Trust Center.
Figure 17 The message bar options of the Trust Center dialog box allow you to control when the message bar displays.
Using Privacy Settings
A homograph is a word that sounds like other words that have different meanings. Examples are to, two, and too In Internet terms, a homograph is a website that sounds like a well-known website but actually links you to a website that isn’t legitimate. Phishers spoof the domain names of banks, credit card issuers, and other companies to gather your personal information. Links in your application can open you and your users up to homo-graph attacks and phishing schemes. Fortunately, the Trust Center can help to protect you and your users from homograph attacks and phishing schemes.
By default, you get security alerts whenever you have a document open and you click to navigate to a website that has potentially been spoofed. Access also warns you when you attempt to open a file from a website with an address that has a potentially spoofed domain name.
Working with Access Macros and VBA Code
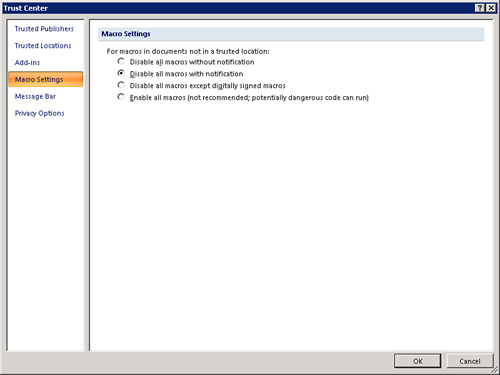
You use macros to automate frequently used tasks. Unfortunately, a hacker can place a virus in an Access database that can propagate to your machine, or even your network. For this reason, Access protects you against potentially unsafe macros and VBA code. You use the Macro Settings options in the Trust Center to control how your application reacts to macros (see Figure 18).
Figure 18 The Macro Settings allow you to determine what happens when your application contains a macro or VBA code.
If you choose Disable All Macros Without Notification, no macros run. If you want to run macros in a database with this setting in place, you must place any unsigned macros in a trusted location. The Trust Center ignores databases located in a trusted location.
If you choose Disable All Macros With Notification, Access disables macros but provides you with a warning that macros are present. This is the default setting. It’s up to you as to whether you want to enable macros in each database. When you enable a macro, it is active only for the current session.
If you choose Disable All Macros Except Digitally Signed Macros, Access disables all macros, except those with a digital signature from a trusted publisher. With this option, Access notifies you that a publisher is not trusted. You are given the option of enabling the signed macros or of trusting the publisher. Access disables all unsigned macros without notification.
If you select the Enable All Macros option, you allow all macros in all databases to run without warning. This option is potentially very dangerous, and you should give some deep thought as to whether you really want to select it.
Security Tips and Tricks
There are certain situations regarding macros that you should know about. The first situation that you should know about is when a macro is not signed. You therefore cannot verify the publisher. Unless you know that the macro was from a trustworthy source, you should not enable the macros. With Microsoft Office Access 2007, you can do anything with a disabled database except run macros and VBA code.
The second situation is when the macro has been digitally signed but the signature has expired. As with the first situation, you should not run the macros contained in the database except if you know that the database is from a trustworthy source.
The next situation is when the macro signature is invalid. As with the preceding two situations, you should not run macros in a database with an invalid signature. In fact, the reason that the signature may not be valid is that someone tampered with it!
Another situation is when the macro signature is not trusted. In this case, the signature is valid, but you haven’t yet opted to trust the publisher. When this situation occurs, a security dialog box appears, allowing you to trust all macros provided from the publisher of the database that you are opening. When you select that option, you are adding the publisher to the Trusted Publishers list in the Trust Center.
Working with Trusted Locations
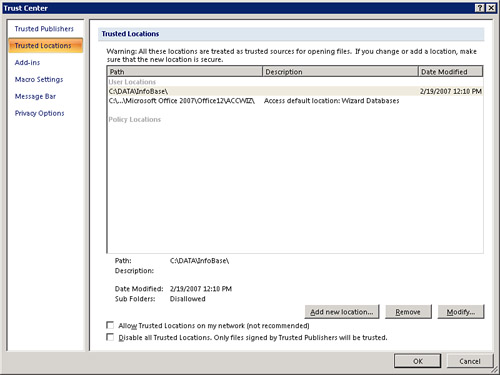
The Trusted Locations portion of the Trust Center appears as shown in Figure 19. Using trusted locations, you can eliminate the need to enable the macros in a database each time you open it. You can leave the security settings at the default value, requiring you to enable macros in each of your databases that are not in a trusted location. Macros in any databases placed in a trusted location are automatically enabled, and you won’t receive any security alerts.
Figure 19 The Trusted Locations part of the Trust Center allows you to manage the locations of your files.
You can place your databases with macros and VBA code in a directory on your local machine or in a directory on the network. There are a couple of issues you should be aware of with each option. If you store your macros on your local machine, make sure that you use a Microsoft Windows logon password to protect your computer. This will keep people from tampering with your macros or your Access settings. Storing your databases on a network drive is less secure. The reason is that more people have access to them. Do not place your files in a public folder on a network share. This makes them very susceptible to tampering. Finally, if you opt to store your files on your local machine, do not place them within the Documents or My Documents folders because this will greatly increase your security risk. Instead, place them in a subfolder within the Documents or My Documents folders and make that folder the trusted location.
Creating a Trusted Location
To create a trusted location, you must first go to the Trusted Locations page of the Trust Center. Here’s the process.
- Click the Microsoft Office button and select Access Options. The Access Options dialog box appears.
- Click Trust Center on the left side of the dialog box.
- Click the Trust Center Settings command button. The Trust Center dialog box appears.
- Click Trusted Locations on the left side of the dialog box. Your dialog box appears as shown previously in Figure 19.
- Click Add New Location. The Microsoft Office Trusted Location dialog box appears (see Figure 20).
Figure 20 The Microsoft Office Trusted Location dialog box allows you to add trusted locations.

- Enter the path for the trusted location and indicate whether you also want to trust subfolders. Finally, you can enter a description of the location that you are adding.
- Click OK to complete the process. The location that you added appears in the list of trusted locations.
Removing a Trusted Location
Just as you can add a trusted location, you can remove one as well. Here are the steps involved:
- Click the Microsoft Office button and select Access Options. The Access Options dialog box appears.
- Click Trust Center on the left side of the dialog box.
- Click the Trust Center Settings command button. The Trust Center dialog box appears.
- Click Trusted Locations on the left side of the dialog box.
- Select the location that you want to remove.
- Click the Remove button. Access removes the location without any warning.
Modifying a Trusted Location
Sometimes you will want to modify the settings associated with a trusted location. To do so, follow these steps:
- Click the Microsoft Office button and select Access Options. The Access Options dialog box appears.
- Click Trust Center on the left side of the dialog box.
- Click the Trust Center Settings command button. The Trust Center dialog box appears.
- Click Trusted Locations on the left side of the dialog box.
- Select the location that you want to modify.
- Click the Modify button. The Microsoft Office Trusted Location dialog box appears (the same dialog box that allowed you to add a trusted location).
- Make the desired changes and click OK to close the dialog box.
Working with Trusted Publishers
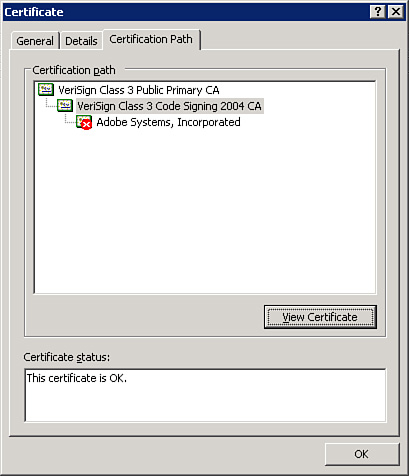
Just as you can trust a file location, you can also trust publishers of database files. The Trusted Publishers page of the Trust Center dialog box appears as shown in Figure 21. In the figure, you can see the list of trusted publishers. To view a certificate, click the View button. The Certificate dialog box appears. The General tab of the dialog box, pictured in Figure 22, shows general information about the certificate. The Details tab, pictured in Figure 23, shows additional information about the certificate. The Certification Path tab shows you a tree of levels of certification (see Figure 24). If you click one of the levels and then click View Certificate, you will see the certificate associated with another certificate in the certification path.
Figure 21 You use the Trust Center dialog box to view a list of trusted publishers.
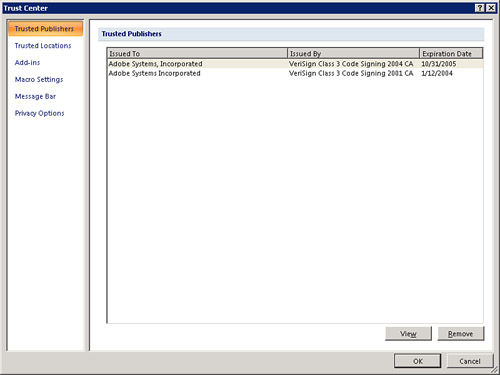
Figure 22 You can easily view the certificate associated with a trusted publisher.
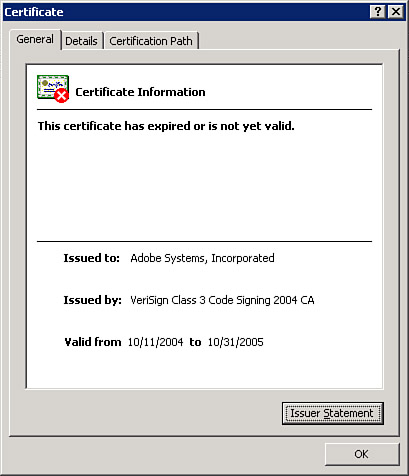
Figure 23 The Details tab shows additional information about a publisher.
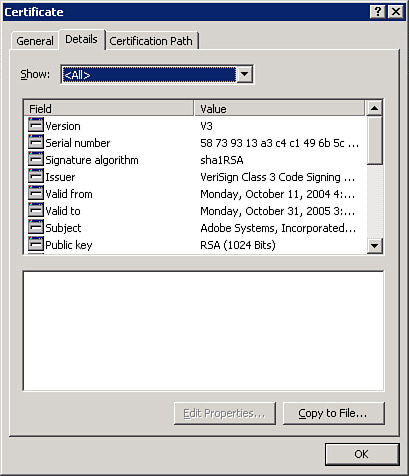
Figure 24 Using the Certification Path tab, you can see publishers included in the certification process