Practice Exam
Certified Information Systems Auditor (CISA)
This exam consists of 135 questions that reflect the material covered in this book. The questions represent the types of questions you should expect to see on the Certified Information Systems Auditor exam; however, they are not intended to match exactly what is on the exam. The exam requires candidates to use higher learning skills, working through more than just knowledge questions.
Some of the questions require that you deduce the best possible answer. In other cases, you are asked to identify the best course of action to take in a given situation. Some questions are considered enhanced in that you will be required to examine a figure, graphic, or other item to properly answer the question. You must read the questions carefully and thoroughly before you attempt to answer them. It is strongly recommended that you treat this exam as if it were the actual exam. The actual exam has 200 questions with a four-hour time limit. This means that you should spend no more than two hours and 42 minutes on this practice exam. When you take it, time yourself, read carefully, and answer all the questions to the best of your ability. It also worth noting that passing the exam requires the candidate to be familiar with a voluminous list of terms. Although the candidate is expected to know what the acronyms stand for, most will be spelled out on the actual exam.
The answers to all the questions appear in the “Answers to Practice Exam Questions” chapter, next in the book. Check your letter answers against those in the answer key, and then read the explanations provided. If you answer incorrectly, you should return to the appropriate chapter in the book to review the material.
Practice Exam Questions
1. Which type of sampling is best when dealing with population characteristics such as dollar amounts and weights?
![]() A. Attribute sampling
A. Attribute sampling
![]() B. Variable sampling
B. Variable sampling
![]() C. Stop-and-go sampling
C. Stop-and-go sampling
![]() D. Discovery sampling
D. Discovery sampling
2. Which of the following sampling techniques is generally applied to compliance testing?
![]() A. Attribute sampling
A. Attribute sampling
![]() B. Variable sampling
B. Variable sampling
![]() C. Stop-and-go sampling
C. Stop-and-go sampling
![]() D. Discovery sampling
D. Discovery sampling
3. To guarantee the confidentiality of client information, an auditor should do which of the following when reviewing such information?
![]() A. Contact the CEO or CFO and request what sensitive information can and cannot be disclosed to authorities
A. Contact the CEO or CFO and request what sensitive information can and cannot be disclosed to authorities
![]() B. Assume full responsibility for the audit archive and stored data
B. Assume full responsibility for the audit archive and stored data
![]() C. Leave all sensitive information at the owners’ facility
C. Leave all sensitive information at the owners’ facility
![]() D. Not back up any of his or her work papers
D. Not back up any of his or her work papers
4. Which of the following best describes materiality?
![]() A. An audit technique used to evaluate the need to perform an audit
A. An audit technique used to evaluate the need to perform an audit
![]() B. The principle that individuals, organizations, and the community are responsible for their actions and might be required to explain them
B. The principle that individuals, organizations, and the community are responsible for their actions and might be required to explain them
![]() C. The auditor’s independence and freedom from conflict of interest
C. The auditor’s independence and freedom from conflict of interest
![]() D. An auditing concept that examines the importance of an item of information in regard to the impact or effect on the entity being audited
D. An auditing concept that examines the importance of an item of information in regard to the impact or effect on the entity being audited
5. Which of the following sampling technique is best to use to prevent excessive sampling?
![]() A. Attribute sampling
A. Attribute sampling
![]() B. Variable sampling
B. Variable sampling
![]() C. Stop-and-go sampling
C. Stop-and-go sampling
![]() D. Discovery sampling
D. Discovery sampling
6. Which of the following descriptions best defines auditor independence?
![]() A. The auditor has high regard for the company and holds several hundred shares of the company’s stock
A. The auditor has high regard for the company and holds several hundred shares of the company’s stock
![]() B. The auditor has a history of independence and even though the auditor has a niece that is employed by the company, he has stated that this is not a concern
B. The auditor has a history of independence and even though the auditor has a niece that is employed by the company, he has stated that this is not a concern
![]() C. The auditor has previously given advice to the organization’s design staff while employed as the auditor
C. The auditor has previously given advice to the organization’s design staff while employed as the auditor
![]() D. The auditor is objective, not associated with the organization, and free of any connections to the client
D. The auditor is objective, not associated with the organization, and free of any connections to the client
7. Which of the following meets the description “the primary objective is to leverage the internal audit function by placing responsibility of control and monitoring onto the functional areas”?
![]() A. Integrated auditing
A. Integrated auditing
![]() B. Control self-assessment
B. Control self-assessment
![]() C. Automated work papers
C. Automated work papers
![]() D. Continuous auditing
D. Continuous auditing
8. Which of the following sampling techniques would be best to use if the expected discovery rate is extremely low?
![]() A. Attribute sampling
A. Attribute sampling
![]() B. Variable sampling
B. Variable sampling
![]() C. Stop-and-go sampling
C. Stop-and-go sampling
![]() D. Discovery sampling
D. Discovery sampling
9. Which of the following offers how-to information?
![]() A. Standards
A. Standards
![]() B. Policy
B. Policy
![]() C. Guidelines
C. Guidelines
![]() D. Procedures
D. Procedures
10. The type of risk that might not be detected by a system of internal controls is defined as which of the following?
![]() A. Control risk
A. Control risk
![]() B. Audit risk
B. Audit risk
![]() C. Detection risk
C. Detection risk
![]() D. Inherent risk
D. Inherent risk
11. Which of the following items makes computer-assisted audit techniques (CAAT) important to an auditor?
![]() A. A large amount of information is obtained by using specific techniques to analyze systems.
A. A large amount of information is obtained by using specific techniques to analyze systems.
![]() B. An assistant or untrained professional with no specialized training can utilize CAAT tools, which frees up the auditor to participate in other activities.
B. An assistant or untrained professional with no specialized training can utilize CAAT tools, which frees up the auditor to participate in other activities.
![]() C. CAAT requires more human involvement in the analysis than multifunction audit utilities.
C. CAAT requires more human involvement in the analysis than multifunction audit utilities.
![]() D. CAAT requires the auditor to reduce the sampling rate and provides a more narrow audit coverage.
D. CAAT requires the auditor to reduce the sampling rate and provides a more narrow audit coverage.
12. The risk that a material error will occur because of weak controls or no controls is known as which of the following?
![]() A. Control risk
A. Control risk
![]() B. Audit risk
B. Audit risk
![]() C. Detection risk
C. Detection risk
![]() D. Inherent risk
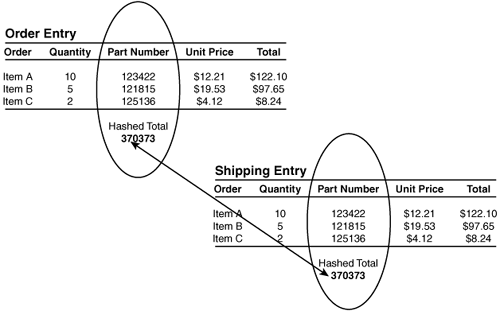
D. Inherent risk
13. You have been asked to audit a series of controls. Using Figure E.1 as your reference, what type of control have you been asked to examine?
![]() A. Amount total
A. Amount total
![]() B. Hash total
B. Hash total
![]() C. Item total
C. Item total
![]() D. Data checksum
D. Data checksum
Figure E.1
14. Which of the following is the best tool to extract data that is relevant to the audit?
![]() A. Integrated auditing
A. Integrated auditing
![]() B. Generalized audit software
B. Generalized audit software
![]() C. Automated work papers
C. Automated work papers
![]() D. Continuous auditing
D. Continuous auditing
15. You have been asked to perform an audit of the disaster-recovery procedures. As part of this process, you must use statistical sampling techniques to inventory all backup tapes. Which of the following descriptions best defines what you have been asked to do?
![]() A. Continuous audit
A. Continuous audit
![]() B. Integrated audit
B. Integrated audit
![]() C. Compliance audit
C. Compliance audit
![]() D. Substantive audit
D. Substantive audit
16. According to ISACA, which of the following is the fourth step in the risk-based audit approach?
![]() A. Gather information and plan
A. Gather information and plan
![]() B. Perform compliance tests
B. Perform compliance tests
![]() C. Perform substantive tests
C. Perform substantive tests
![]() D. Determine internal controls
D. Determine internal controls
17. Which general control procedure most closely maps to the information systems control procedure that specifies, “Operational controls that are focused on day-to-day activities”?
![]() A. Business continuity and disaster-recovery procedures that provide reasonable assurance that the organization is secure against disasters
A. Business continuity and disaster-recovery procedures that provide reasonable assurance that the organization is secure against disasters
![]() B. Procedures that provide reasonable assurance for the control of database administration
B. Procedures that provide reasonable assurance for the control of database administration
![]() C. System-development methodologies and change-control procedures that have been implemented to protect the organization and maintain compliance
C. System-development methodologies and change-control procedures that have been implemented to protect the organization and maintain compliance
![]() D. Procedures that provide reasonable assurance to control and manage data-processing operations
D. Procedures that provide reasonable assurance to control and manage data-processing operations
18. Which of the following is the best example of a detective control?
![]() A. Access-control software that uses passwords, tokens, and/or biometrics
A. Access-control software that uses passwords, tokens, and/or biometrics
![]() B. Intrusion-prevention systems
B. Intrusion-prevention systems
![]() C. Backup procedures used to archive data
C. Backup procedures used to archive data
![]() D. Variance reports
D. Variance reports
19. Which of the following is not one of the four common elements needed to determine whether fraud is present?
![]() A. An error in judgment
A. An error in judgment
![]() B. Knowledge that the statement was false
B. Knowledge that the statement was false
![]() C. Reliance on the false statement
C. Reliance on the false statement
![]() D. Resulting damages or losses
D. Resulting damages or losses
20. You have been asked to implement a continuous auditing program. With this in mind, which of the following should you first identify?
![]() A. Applications with high payback potential
A. Applications with high payback potential
![]() B. The format and location of input and output files
B. The format and location of input and output files
![]() C. Areas of high risk within the organization
C. Areas of high risk within the organization
![]() D. Targets with reasonable thresholds
D. Targets with reasonable thresholds
21. Which of the following should be the first step for organizations wanting to develop an information security program?
![]() A. Upgrade access-control software to a biometric or token system
A. Upgrade access-control software to a biometric or token system
![]() B. Approve a corporate information security policy statement
B. Approve a corporate information security policy statement
![]() C. Ask internal auditors to perform a comprehensive review
C. Ask internal auditors to perform a comprehensive review
![]() D. Develop a set of information security standards
D. Develop a set of information security standards
22. Which of the following is primarily tasked with ensuring that the IT department is properly aligned with the goals of the business?
![]() A. Chief executive officer
A. Chief executive officer
![]() B. Board of directors
B. Board of directors
![]() C. IT steering committee
C. IT steering committee
![]() D. Audit committee
D. Audit committee
23. The balanced score card differs from historic measurement schemes, in that it looks at more than what?
![]() A. Financial results
A. Financial results
![]() B. Customer satisfaction
B. Customer satisfaction
![]() C. Internal process efficiency
C. Internal process efficiency
![]() D. Innovation capacity
D. Innovation capacity
24. Which of the following is the purpose of enterprise architecture (EA)?
![]() A. Ensure that internal and external strategy are aligned
A. Ensure that internal and external strategy are aligned
![]() B. Map the IT infrastructure of the organization
B. Map the IT infrastructure of the organization
![]() C. Map the IT infrastructure of the organization and ensure that its design maps to the organization’s strategy
C. Map the IT infrastructure of the organization and ensure that its design maps to the organization’s strategy
![]() D. Ensure that business strategy and IT investments are aligned
D. Ensure that business strategy and IT investments are aligned
25. Which of the following types of planning entails an outlook of greater than three years?
![]() A. Daily planning
A. Daily planning
![]() B. Long-term planning
B. Long-term planning
![]() C. Operational planning
C. Operational planning
![]() D. Strategic planning
D. Strategic planning
26. A new IT auditor has been asked to examine some processing, editing, and validation controls. Can you help define the control shown in Figure E.2?
![]() A. Validity check
A. Validity check
![]() B. Reasonableness check
B. Reasonableness check
![]() C. Existence check
C. Existence check
![]() D. Range check
D. Range check
Figure E.2
27. Senior management needs to select a strategy to determine who will pay for the information system’s services. Which of the following payment methods is known as a “pay as you go” system?
![]() A. Single cost
A. Single cost
![]() B. Shared cost
B. Shared cost
![]() C. Chargeback
C. Chargeback
![]() D. Sponsor pays
D. Sponsor pays
28. Which of the following is the best method to identify problems between procedure and activity?
![]() A. Policy review
A. Policy review
![]() B. Direct observation
B. Direct observation
![]() C. Procedure review
C. Procedure review
![]() D. Interview
D. Interview
29. You are working with a risk-assessment team that is having a hard time calculating the potential financial loss to the company’s brand name that could result from a risk. What should the team do next?
![]() A. Calculate the return on investment (ROI)
A. Calculate the return on investment (ROI)
![]() B. Determine the single loss expectancy (SLE)
B. Determine the single loss expectancy (SLE)
![]() C. Use a qualitative approach
C. Use a qualitative approach
![]() D. Review actuary tables
D. Review actuary tables
30. What operation-migration strategy has the highest possible level of risk?
![]() A. Parallel
A. Parallel
![]() B. Hard
B. Hard
![]() C. Phased
C. Phased
![]() D. Intermittent
D. Intermittent
31. Many organizations require employees to rotate to different positions. Why?
![]() A. Help deliver effective and efficient services
A. Help deliver effective and efficient services
![]() B. Provide effective cross-training
B. Provide effective cross-training
![]() C. Reduce the opportunity for fraud or improper or illegal acts
C. Reduce the opportunity for fraud or improper or illegal acts
![]() D. Increase employee satisfaction
D. Increase employee satisfaction
32. The balanced score card looks at four metrics. Which of the following is not one of those metrics?
![]() A. External operations
A. External operations
![]() B. The customer
B. The customer
![]() C. Innovation and learning
C. Innovation and learning
![]() D. Financial data
D. Financial data
33. You have been assigned to a software-development project that has 80 linked modules and is being developed for a system that handles several million transactions per year. The primary screen of the application has data items that carry up to 20 data attributes. You have been asked to work with the audit staff to determine a true estimate of the development effort. Which of the following is the best technique to determine the size of the project?
![]() A. White-boxing
A. White-boxing
![]() B. Black-boxing
B. Black-boxing
![]() C. Function point analysis
C. Function point analysis
![]() D. Source lines of code
D. Source lines of code
34. Which of the following is the preferred tool for estimating project time when a degree of uncertainty exists?
![]() A. Program Evaluation and Review Technique (PERT)
A. Program Evaluation and Review Technique (PERT)
![]() B. Source lines of code (SLOC)
B. Source lines of code (SLOC)
![]() C. Gantt
C. Gantt
![]() D. Constructive Cost Model (COCOMO)
D. Constructive Cost Model (COCOMO)
35. Which of the following techniques is used to determine what activities are critical and what the dependencies are among the various tasks?
![]() A. Compiling a list of each task required to complete the project
A. Compiling a list of each task required to complete the project
![]() B. COCOMO
B. COCOMO
![]() C. Critical path methodology (CPM)
C. Critical path methodology (CPM)
![]() D. Program Evaluation and Review Technique (PERT)
D. Program Evaluation and Review Technique (PERT)
36. Which of the following is considered a traditional system development lifecycle model?
![]() A. The waterfall model
A. The waterfall model
![]() B. The spiral development model
B. The spiral development model
![]() C. The prototyping model
C. The prototyping model
![]() D. Incremental development
D. Incremental development
37. You have been assigned as an auditor to a new software project. The team members are currently defining user needs and then mapping how the proposed solution meets the need. At what phase of the SDLC are they?
![]() A. Feasibility
A. Feasibility
![]() B. Requirements
B. Requirements
![]() C. Design
C. Design
![]() D. Development
D. Development
38. Which of the following is not a valid output control?
![]() A. Logging
A. Logging
![]() B. Batch controls
B. Batch controls
![]() C. Security signatures
C. Security signatures
![]() D. Report distribution
D. Report distribution
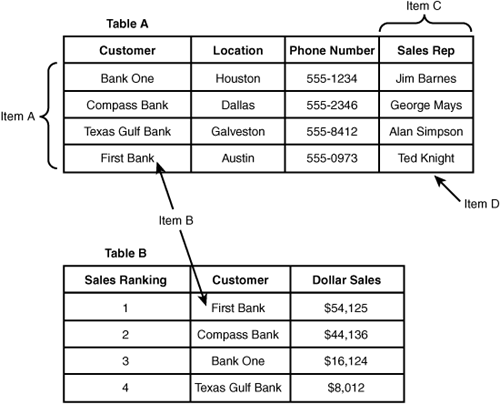
39. The following question references Figure E.3. Item A refers to which of the following?
![]() A. Foreign key
A. Foreign key
![]() B. Tuple
B. Tuple
![]() C. Attribute
C. Attribute
![]() D. Primary key
D. Primary key
Figure E.3
40. You have been asked to suggest a control that could be used to determine whether a credit card transaction is legitimate or potentially from a stolen credit card. Which of the following would be the best tool for this need?
![]() A. Decision support systems
A. Decision support systems
![]() B. Expert systems
B. Expert systems
![]() C. Intrusion-prevention systems
C. Intrusion-prevention systems
![]() D. Data-mining techniques
D. Data-mining techniques
41. You have been asked to suggest a control that can be used to verify that batch data is complete and was transferred accurately between two applications. What should you suggest?
![]() A. A control total
A. A control total
![]() B. Check digit
B. Check digit
![]() C. Completeness check
C. Completeness check
![]() D. Limit check
D. Limit check
42. Which of the following types of programming language is used to develop decision support systems?
![]() A. 2GL
A. 2GL
![]() B. 3GL
B. 3GL
![]() C. 4GL
C. 4GL
![]() D. 5GL
D. 5GL
43. You have been asked to work with a new project manager. The project team has just started work on the payback analysis. Which of the following is the best answer to identify the phase of the system development lifecycle of the project?
![]() A. Feasibility
A. Feasibility
![]() B. Requirements
B. Requirements
![]() C. Design
C. Design
![]() D. Development
D. Development
44. In many ways, IS operations is a service organization because it provides services to its users. As such, how should an auditor recommend that the percentage of help-desk or response calls answered within a given time be measured?
![]() A. Uptime agreements
A. Uptime agreements
![]() B. Time service factor
B. Time service factor
![]() C. Abandon rate
C. Abandon rate
![]() D. First call resolution
D. First call resolution
45. What is the correct term for items that can occur without human interaction?
![]() A. Lights out
A. Lights out
![]() B. Automated processing
B. Automated processing
![]() C. “Follow the sun” operations
C. “Follow the sun” operations
![]() D. Autopilot operations
D. Autopilot operations
46. Which of the following is an example of a 2GL language?
![]() A. SQL
A. SQL
![]() B. Assembly
B. Assembly
![]() C. FORTRAN
C. FORTRAN
![]() D. Prolog
D. Prolog
47. When discussing web services, which of the following best describes a proxy server?
![]() A. Reduces load for the client system
A. Reduces load for the client system
![]() B. Improves direct access to the Internet
B. Improves direct access to the Internet
![]() C. Provides an interface to access the private domain
C. Provides an interface to access the private domain
![]() D. Provides high-level security services
D. Provides high-level security services
48. Regarding cohesion and coupling, which is best?
![]() A. High cohesion, high coupling
A. High cohesion, high coupling
![]() B. High cohesion, low coupling
B. High cohesion, low coupling
![]() C. Low cohesion, low coupling
C. Low cohesion, low coupling
![]() D. Low cohesion, high coupling
D. Low cohesion, high coupling
49. Bluetooth class 1 meets which of the following specifications?
![]() A. Up to 5 m of range and .5 mW of power
A. Up to 5 m of range and .5 mW of power
![]() B. Up to 10 m of range and 1 mW of power
B. Up to 10 m of range and 1 mW of power
![]() C. Up to 20 m of range and 2.5 mW of power
C. Up to 20 m of range and 2.5 mW of power
![]() D. Up to 100 m of range and 100 mW of power
D. Up to 100 m of range and 100 mW of power
50. When discussing electronic data interface (EDI), which of the following terms best describes the device that transmits and receives electronic documents between trading partners?
![]() A. Value Added Network (VAN)
A. Value Added Network (VAN)
![]() B. X12
B. X12
![]() C. Communications handler
C. Communications handler
![]() D. Electronic Data Interchange For Administration Commerce And Transport (EDIFACT)
D. Electronic Data Interchange For Administration Commerce And Transport (EDIFACT)
51. Which type of network is used to connect multiple servers to a centralized pool of disk storage?
![]() A. PAN
A. PAN
![]() B. LAN
B. LAN
![]() C. SAN
C. SAN
![]() D. MAN
D. MAN
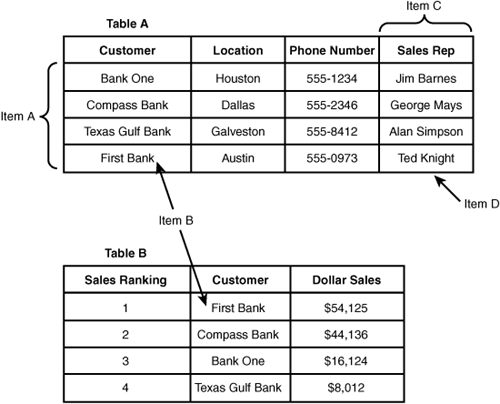
52. The following question references Figure E.4. Item C refers to which of the following?
![]() A. Foreign key
A. Foreign key
![]() B. Tuple
B. Tuple
![]() C. Attribute
C. Attribute
![]() D. Primary key
D. Primary key
Figure E.4
53. Which layer of the OSI model is responsible for packet routing?
![]() A. Application
A. Application
![]() B. Transport
B. Transport
![]() C. Session
C. Session
![]() D. Network
D. Network
54. Which of the following types of testing is usually performed at the implementation phase, when the project staff is satisfied with all other tests and the application is ready to be deployed?
![]() A. Final acceptance testing
A. Final acceptance testing
![]() B. System testing
B. System testing
![]() C. Interface testing
C. Interface testing
![]() D. Unit testing
D. Unit testing
55. Which of the following devices can be on the edge of networks for basic packet filtering?
![]() A. Bridge
A. Bridge
![]() B. Switch
B. Switch
![]() C. Router
C. Router
![]() D. VLAN
D. VLAN
56. MAC addresses are most closely associated with which layer of the OSI model?
![]() A. Data link
A. Data link
![]() B. Network
B. Network
![]() C. Session
C. Session
![]() D. Physical
D. Physical
57. The IP address of 128.12.3.15 is considered to be which of the following?
![]() A. Class A
A. Class A
![]() B. Class B
B. Class B
![]() C. Class C
C. Class C
![]() D. Class D
D. Class D
58. Which of the following statements is most correct? RIP is considered...
![]() A. A routing protocol
A. A routing protocol
![]() B. A routable protocol
B. A routable protocol
![]() C. A distance-vector routing protocol
C. A distance-vector routing protocol
![]() D. A link-state routing protocol
D. A link-state routing protocol
59. Which of the following test types is used after a change to verify that inputs and outputs are correct?
![]() A. Regression testing
A. Regression testing
![]() B. System testing
B. System testing
![]() C. Interface testing
C. Interface testing
![]() D. Pilot testing
D. Pilot testing
60. Which of the following is an example of a 5GL language?
![]() A. SQL
A. SQL
![]() B. Assembly
B. Assembly
![]() C. FORTRAN
C. FORTRAN
![]() D. Prolog
D. Prolog
61. Which of the following types of network topologies is hard to expand, with one break possibly disabling the entire segment?
![]() A. Bus
A. Bus
![]() B. Star
B. Star
![]() C. Token Ring
C. Token Ring
![]() D. Mesh
D. Mesh
62. What is the most important reason to use plenum-grade cable?
![]() A. Increased network security
A. Increased network security
![]() B. Less attenuation
B. Less attenuation
![]() C. Less cross-talk
C. Less cross-talk
![]() D. Fire-retardant coating
D. Fire-retardant coating
63. Which of the following copper cable network configurations is considered the most secure from eavesdropping or interception?
![]() A. A switched VLAN using multimode fiber cable
A. A switched VLAN using multimode fiber cable
![]() B. A Token Ring network using Cat 5 cabling
B. A Token Ring network using Cat 5 cabling
![]() C. A switched network that uses Cat 5e shielded cable
C. A switched network that uses Cat 5e shielded cable
![]() D. A bus network using 10BASE2 cabling
D. A bus network using 10BASE2 cabling
64. Which of the following is an iterative development method in which repetitions are referred to as sprints and typically last 30 days?
![]() A. Scrum
A. Scrum
![]() B. Extreme programming
B. Extreme programming
![]() C. RAD
C. RAD
![]() D. Spiral
D. Spiral
65. Which type of database is shown in Figure E.5?
![]() A. Relational
A. Relational
![]() B. Network
B. Network
![]() C. Hierarchical
C. Hierarchical
![]() D. Floating flat
D. Floating flat
Figure E.5
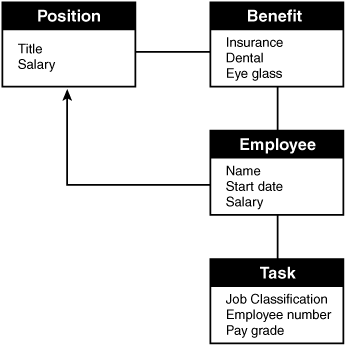
66. As a new auditor, you have been asked to review network operations. Which of the following weaknesses should you consider the most serious?
![]() A. Data files can be amended or changed by supervisors.
A. Data files can be amended or changed by supervisors.
![]() B. Data files can be lost during power outages because of poor backup.
B. Data files can be lost during power outages because of poor backup.
![]() C. Sensitive data files can be read by managers.
C. Sensitive data files can be read by managers.
![]() D. Copies of confidential reports can be printed by anyone.
D. Copies of confidential reports can be printed by anyone.
67. Which of the following is the best example of a control mechanism to be used to control component failure or errors?
![]() A. Redundant WAN links
A. Redundant WAN links
![]() B. Just a Bunch of Disks/Drives (JBOD)
B. Just a Bunch of Disks/Drives (JBOD)
![]() C. RAID 0
C. RAID 0
![]() D. RAID 1
D. RAID 1
68. Which of the following is the best technique for an auditor to verify firewall settings?
![]() A. Interview the network administrator
A. Interview the network administrator
![]() B. Review the firewall configuration
B. Review the firewall configuration
![]() C. Review the firewall log for recent attacks
C. Review the firewall log for recent attacks
![]() D. Review the firewall procedure
D. Review the firewall procedure
69. Which of the following is not a circuit-switching technology?
![]() A. DSL
A. DSL
![]() B. POTS
B. POTS
![]() C. T1
C. T1
![]() D. ATM
D. ATM
70. Which of the following uses a process to standardize code modules to allow for cross-platform operation and program integration?
![]() A. Component-based development (CBD)
A. Component-based development (CBD)
![]() B. Web-based application development (WBAD)
B. Web-based application development (WBAD)
![]() C. Object-oriented systems development (OOSD)
C. Object-oriented systems development (OOSD)
![]() D. Data-oriented system development (DOSD)
D. Data-oriented system development (DOSD)
71. Data warehouses are used to store historic data of an organization. As such, which of the following is the most accurate way to describe data warehouses?
![]() A. Subject oriented
A. Subject oriented
![]() B. Object oriented
B. Object oriented
![]() C. Access oriented
C. Access oriented
![]() D. Control oriented
D. Control oriented
72. Which of the following access-control models allows the user to control access?
![]() A. Mandatory access control (MAC)
A. Mandatory access control (MAC)
![]() B. Discretionary access control (DAC)
B. Discretionary access control (DAC)
![]() C. Role-based access control (RBAC)
C. Role-based access control (RBAC)
![]() D. Access control list (ACL)
D. Access control list (ACL)
73. While auditing the identification and authentication system, you want to discuss the best method you reviewed. Which of the following is considered the strongest?
![]() A. Passwords
A. Passwords
![]() B. Tokens
B. Tokens
![]() C. Two-factor authentication
C. Two-factor authentication
![]() D. Biometrics
D. Biometrics
74. If asked to explain the equal error rate (EER) to another auditor, what would you say?
![]() A. The EER is used to determine the clipping level used for password lockout.
A. The EER is used to determine the clipping level used for password lockout.
![]() B. The EER is a measurement that indicates the point at which FRR equals FAR.
B. The EER is a measurement that indicates the point at which FRR equals FAR.
![]() C. The EER is a rating used for password tokens.
C. The EER is a rating used for password tokens.
![]() D. The EER is a rating used to measure the percentage of biometric users who are allowed access and who are not authorized users.
D. The EER is a rating used to measure the percentage of biometric users who are allowed access and who are not authorized users.
75. You have been asked to head up the audit of a business application system. What is one of the first tasks you should perform?
![]() A. Interview users
A. Interview users
![]() B. Review process flowcharts
B. Review process flowcharts
![]() C. Evaluate controls
C. Evaluate controls
![]() D. Determine critical areas
D. Determine critical areas
76. Closed-circuit TV (CCTV) systems are considered what type of control?
![]() A. Corrective
A. Corrective
![]() B. Detective
B. Detective
![]() C. Preventive
C. Preventive
![]() D. Delayed
D. Delayed
77. According to ISACA, the second step in the business continuity planning (BCP) process is which of the following?
![]() A. Project management and initiation
A. Project management and initiation
![]() B. Plan design and development
B. Plan design and development
![]() C. Recovery strategy
C. Recovery strategy
![]() D. Business impact analysis
D. Business impact analysis
78. You have been asked to review the documentation for a planned database. Which type of database is represented by Figure E.6?
![]() A. Relational
A. Relational
![]() B. Network
B. Network
![]() C. Hierarchical
C. Hierarchical
![]() D. Floating flat
D. Floating flat
Figure E.6

79. Which of the following issues ticket-granting tickets?
![]() A. The Kerberos authentication service
A. The Kerberos authentication service
![]() B. The RADIUS authentication service
B. The RADIUS authentication service
![]() C. The Kerberos ticket-granting service
C. The Kerberos ticket-granting service
![]() D. The RADIUS ticket-granting service
D. The RADIUS ticket-granting service
80. Which of the following is the most important corrective control that an organization has the capability to shape?
![]() A. Audit plan
A. Audit plan
![]() B. Security assessment
B. Security assessment
![]() C. Business continuity plan
C. Business continuity plan
![]() D. Network topology
D. Network topology
81. Which one of the following is not considered an application system testing technique?
![]() A. Snapshots
A. Snapshots
![]() B. Mapping
B. Mapping
![]() C. Integrated test facilities
C. Integrated test facilities
![]() D. Base case system evaluation
D. Base case system evaluation
82. Which of the following statements regarding recovery is correct?
![]() A. The greater the recovery point objective (RPO), the more tolerant the process is to interruption.
A. The greater the recovery point objective (RPO), the more tolerant the process is to interruption.
![]() B. The less the recovery time objective (RTO), the longer the process can take to be restored.
B. The less the recovery time objective (RTO), the longer the process can take to be restored.
![]() C. The less the RPO, the more tolerant the process is to interruption.
C. The less the RPO, the more tolerant the process is to interruption.
![]() D. The greater the RTO, the less time the process can take to be restored.
D. The greater the RTO, the less time the process can take to be restored.
83. Which of the following best defines the service delivery objective (SDO)?
![]() A. Defines the maximum amount of time the organization can provide services at the alternate site
A. Defines the maximum amount of time the organization can provide services at the alternate site
![]() B. Defines the level of service provided by alternate processes
B. Defines the level of service provided by alternate processes
![]() C. Defines the time that systems can be offline before causing damage
C. Defines the time that systems can be offline before causing damage
![]() D. Defines how long the process can take to be restored
D. Defines how long the process can take to be restored
84. During which step of the business continuity planning (BCP) process is a risk assessment performed?
![]() A. Project management and initiation
A. Project management and initiation
![]() B. Plan design and development
B. Plan design and development
![]() C. Recovery strategy
C. Recovery strategy
![]() D. Business impact analysis
D. Business impact analysis
85. When auditing security for a data center, the auditor should look for which of the following as the best example of long-term power protection?
![]() A. Standby generator
A. Standby generator
![]() B. Uninterrupted power supply
B. Uninterrupted power supply
![]() C. Surge protector
C. Surge protector
![]() D. Filtered power supply
D. Filtered power supply
86. Which of the following would be considered the most complex continuous audit technique?
![]() A. Continuous and intermittent simulation (CIS)
A. Continuous and intermittent simulation (CIS)
![]() B. Snapshots
B. Snapshots
![]() C. Audit hooks
C. Audit hooks
![]() D. Integrated test facilities
D. Integrated test facilities
87. Which of the following is not a replacement for Halon?
![]() A. FM-200
A. FM-200
![]() B. NAF-S-3
B. NAF-S-3
![]() C. FM-100
C. FM-100
![]() D. Argon
D. Argon
88. When discussing biometrics, what do Type 1 errors measure?
![]() A. The point at which the false rejection rate (FRR) equals the false acceptance rate (FAR)
A. The point at which the false rejection rate (FRR) equals the false acceptance rate (FAR)
![]() B. The accuracy of the biometric system
B. The accuracy of the biometric system
![]() C. The percentage of illegitimate users who are given access
C. The percentage of illegitimate users who are given access
![]() D. The percentage of legitimate users who are denied access
D. The percentage of legitimate users who are denied access
89. Class A fires are comprised of which of the following?
![]() A. Electronic equipment
A. Electronic equipment
![]() B. Paper
B. Paper
![]() C. Oil
C. Oil
![]() D. Metal
D. Metal
90. You are performing an audit of an organization’s physical security controls, specifically, emergency controls. When doors that use relays or electric locks are said to fail soft, what does that mean?
![]() A. Locks of this type fail open.
A. Locks of this type fail open.
![]() B. Locks of this type are easy to pick.
B. Locks of this type are easy to pick.
![]() C. Locks of this type fail closed.
C. Locks of this type fail closed.
![]() D. Locks of this type are hard to pick.
D. Locks of this type are hard to pick.
91. Which type of database is represented by Figure E.7?
![]() A. Relational
A. Relational
![]() B. Network
B. Network
![]() C. Hierarchical
C. Hierarchical
![]() D. Floating flat
D. Floating flat
Figure E.7
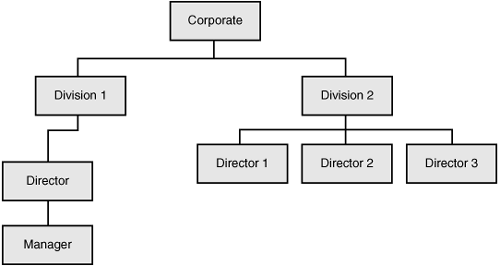
92. Systems control audit review file and embedded audit modules (SCARF/EAM) is an example of which of the following?
![]() A. Output controls
A. Output controls
![]() B. Continuous online auditing
B. Continuous online auditing
![]() C. Input controls
C. Input controls
![]() D. Processing controls
D. Processing controls
93. Which type of access rights control model is widely used by the DoD, NSA, CIA, and FBI?
![]() A. MAC
A. MAC
![]() B. DAC
B. DAC
![]() C. RBAC
C. RBAC
![]() D. ACL
D. ACL
94. Why is the protection of processing integrity important?
![]() A. To maintain availability to users so they have the availability to copy and use data without delay
A. To maintain availability to users so they have the availability to copy and use data without delay
![]() B. To protect data from unauthorized access while in transit
B. To protect data from unauthorized access while in transit
![]() C. To prevent output controls from becoming tainted
C. To prevent output controls from becoming tainted
![]() D. To maintain data encryption on portable devices so that data can be relocated to another facility while being encrypted
D. To maintain data encryption on portable devices so that data can be relocated to another facility while being encrypted
95. A privacy impact analysis (PIA) is tied to several items. Which of the following is not one of those items?
![]() A. Technology
A. Technology
![]() B. Processes
B. Processes
![]() C. People
C. People
![]() D. Documents
D. Documents
96. Which of the following is ultimately responsible for the security practices of the organization?
![]() A. Security advisory group
A. Security advisory group
![]() B. Chief security officer
B. Chief security officer
![]() C. Executive management
C. Executive management
![]() D. Security auditor
D. Security auditor
97. Which of the following guarantees that all foreign keys reference existing primary keys?
![]() A. Relational integrity
A. Relational integrity
![]() B. Referential integrity
B. Referential integrity
![]() C. Entity integrity
C. Entity integrity
![]() D. Tracing and tagging
D. Tracing and tagging
98. Which of the following would a company extend to allow network access to a business partner?
![]() A. Internet
A. Internet
![]() B. Intranet
B. Intranet
![]() C. Extranet
C. Extranet
![]() D. VLAN
D. VLAN
99. What term is used to describe the delay that information will experience from the source to the destination?
![]() A. Echo
A. Echo
![]() B. Latency
B. Latency
![]() C. Delay
C. Delay
![]() D. Congestion
D. Congestion
100. You have been asked to describe what security feature can be found in the wireless standard 802.11a. How will you respond?
![]() A. Wi-Fi Protected Access (WPA)
A. Wi-Fi Protected Access (WPA)
![]() B. Wired Equivalent Privacy (WEP)
B. Wired Equivalent Privacy (WEP)
![]() C. Temporal Key Integrity Protocol (TKIP)
C. Temporal Key Integrity Protocol (TKIP)
![]() D. Wi-Fi Protected Access 2 (WPA2)
D. Wi-Fi Protected Access 2 (WPA2)
101. Which of the following is not a packet-switching technology?
![]() A. X.25
A. X.25
![]() B. ISDN
B. ISDN
![]() C. Frame Rely
C. Frame Rely
![]() D. ATM
D. ATM
102. Transport-layer security (TLS) can best be described as being found between which two layers of the OSI model?
![]() A. Layers 2 and 3
A. Layers 2 and 3
![]() B. Layers 3 and 4
B. Layers 3 and 4
![]() C. Layers 4 and 5
C. Layers 4 and 5
![]() D. Layers 5 and 6
D. Layers 5 and 6
103. Which of the following descriptions highlights the importance of domain name service (DNS)?
![]() A. Address of a domain server
A. Address of a domain server
![]() B. Resolves fully qualified domain names to IP addresses
B. Resolves fully qualified domain names to IP addresses
![]() C. Resolves known IP address for unknown Internet addresses
C. Resolves known IP address for unknown Internet addresses
![]() D. Resolves IP and MAC addresses needed for delivery of Internet data
D. Resolves IP and MAC addresses needed for delivery of Internet data
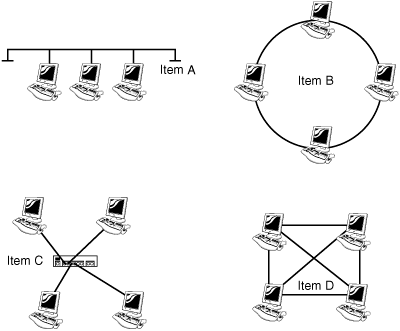
104. Using Figure E.8 as a reference, which of the following best describes a 10BASE5 network design?
![]() A. Item A
A. Item A
![]() B. Item B
B. Item B
![]() C. Item C
C. Item C
![]() D. Item D
D. Item D
Figure E.8
105. You have been asked to describe a program that can be classified as terminal-emulation software. Which of the following would you mention?
![]() A. Telnet
A. Telnet
![]() B. FTP
B. FTP
![]() C. SNMP
C. SNMP
![]() D. SMTP
D. SMTP
106. Which of the following services operates on ports 20 and 21?
![]() A. Telnet
A. Telnet
![]() B. FTP
B. FTP
![]() C. SMTP
C. SMTP
![]() D. DHCP
D. DHCP
107. Which layer of the OSI model is responsible for reliable data delivery?
![]() A. Data link
A. Data link
![]() B. Session
B. Session
![]() C. Transport
C. Transport
![]() D. Network
D. Network
108. An objective of the implementation phase of a newly installed system can include which of the following?
![]() A. Conducting a certification test
A. Conducting a certification test
![]() B. Determining user requirements
B. Determining user requirements
![]() C. Assessing the project to see if expected benefits were achieved
C. Assessing the project to see if expected benefits were achieved
![]() D. Reviewing the designed audit trails
D. Reviewing the designed audit trails
109. Which of the following is the best example of a processing control?
![]() A. Exception reports
A. Exception reports
![]() B. Sequence check
B. Sequence check
![]() C. Key verification
C. Key verification
![]() D. Logical relationship check
D. Logical relationship check
110. Which of the following devices is most closely related to the data link layer?
![]() A. Hub
A. Hub
![]() B. Repeater
B. Repeater
![]() C. Bridge
C. Bridge
![]() D. Router
D. Router
111. Which of the following provide the capability to ensure the validity of data through various stages of processing?
![]() A. Manual recalculations
A. Manual recalculations
![]() B. Programming controls
B. Programming controls
![]() C. Run-to-run totals
C. Run-to-run totals
![]() D. Reasonableness verification
D. Reasonableness verification
112. You overheard the database administrator discussing normalizing some tables. What is the purpose of this activity?
![]() A. Decrease redundancy
A. Decrease redundancy
![]() B. Increase redundancy
B. Increase redundancy
![]() C. Decrease application malfunction
C. Decrease application malfunction
![]() D. Increase accuracy
D. Increase accuracy
113. Which of the following is not included in a PERT chart?
![]() A. The most optimistic time the task can be completed in
A. The most optimistic time the task can be completed in
![]() B. The most cost-effective scenario for the task
B. The most cost-effective scenario for the task
![]() C. The worst-case scenario or longest time the task can take
C. The worst-case scenario or longest time the task can take
![]() D. The most likely time the task will be completed in
D. The most likely time the task will be completed in
114. Verifications such as existence checks can best be described as:
![]() A. A processing control that is considered preventive
A. A processing control that is considered preventive
![]() B. A validation edit control that is considered preventive
B. A validation edit control that is considered preventive
![]() C. A processing control that is considered detective
C. A processing control that is considered detective
![]() D. A validation edit control that is considered detective
D. A validation edit control that is considered detective
115. Referential integrity is used to prevent which of the following?
![]() A. Attribute errors
A. Attribute errors
![]() B. Relational errors
B. Relational errors
![]() C. Dangling tuples
C. Dangling tuples
![]() D. Integrity constraints
D. Integrity constraints
116. Which of the following best describes the difference between accreditation and certification?
![]() A. Certification is initiated after the accreditation of the system to ensure that the system meets required standards.
A. Certification is initiated after the accreditation of the system to ensure that the system meets required standards.
![]() B. Certification is initiated before accreditation to ensure that quality personnel are using the new designed systems.
B. Certification is initiated before accreditation to ensure that quality personnel are using the new designed systems.
![]() C. Accreditation is issued after certification. Accreditation is a management function, while certification is a technical function.
C. Accreditation is issued after certification. Accreditation is a management function, while certification is a technical function.
![]() D. Production and management might see accreditation and certification as basically one and the same.
D. Production and management might see accreditation and certification as basically one and the same.
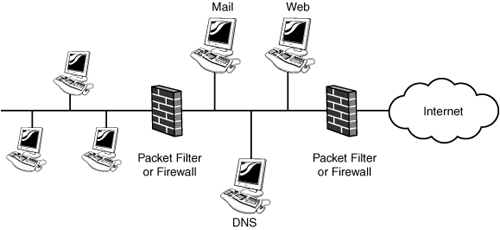
117. You have been asked to review the organization’s planned firewall design. As such, which of the following best describes the topology shown in Figure E.9?
![]() A. Packet filter
A. Packet filter
![]() B. Screened subnet
B. Screened subnet
![]() C. Screened host
C. Screened host
![]() D. Dual-homed host
D. Dual-homed host
Figure E.9
118. Which of the following database designs is considered a lattice structure because each record can have multiple parent and child records? Although this design can work well in stable environments, it can be extremely complex.
![]() A. The hierarchical database-management systems
A. The hierarchical database-management systems
![]() B. The relational database-management systems
B. The relational database-management systems
![]() C. The network database-management systems
C. The network database-management systems
![]() D. The structured database-management systems
D. The structured database-management systems
119. Which of the following is not used when calculating function point analysis?
![]() A. Number of user inquires
A. Number of user inquires
![]() B. Number of files
B. Number of files
![]() C. Number of user inputs
C. Number of user inputs
![]() D. Number of expected users
D. Number of expected users
120. Which of the following is an example of an interpreted programming language?
![]() A. FORTRAN
A. FORTRAN
![]() B. Assembly
B. Assembly
![]() C. Basic
C. Basic
![]() D. Java
D. Java
121. Which of the following is an example of a 4GL language?
![]() A. SQL
A. SQL
![]() B. Assembly
B. Assembly
![]() C. FORTRAN
C. FORTRAN
![]() D. Prolog
D. Prolog
122. Which of the following database takes the form of a parent/child structure?
![]() A. The hierarchical database-management systems
A. The hierarchical database-management systems
![]() B. The relational database-management systems
B. The relational database-management systems
![]() C. The network database-management systems
C. The network database-management systems
![]() D. The structured database-management systems
D. The structured database-management systems
123. You have been asked to explain rings of protection and how the concept applies to the supervisory mode of the operating system (OS). Which of the following is the best description?
![]() A. System utilities should run in supervisor mode.
A. System utilities should run in supervisor mode.
![]() B. Supervisor state allows the execution of all instructions, including privileged instructions.
B. Supervisor state allows the execution of all instructions, including privileged instructions.
![]() C. Supervisory mode is used to block access to the security kernel.
C. Supervisory mode is used to block access to the security kernel.
![]() D. Rings are arranged in a hierarchy from least privileged to the most privileged as the most trusted usually has the highest ring number
D. Rings are arranged in a hierarchy from least privileged to the most privileged as the most trusted usually has the highest ring number
124. You have been asked to design a control. The organization would like to limit what check numbers are used. Specfically, they would like to be able to flag a check numbered 318 if the day’s first check had the number 120 and the day’s last check was number 144. What type of validation check does the department require?
![]() A. Limit check
A. Limit check
![]() B. Range check
B. Range check
![]() C. Validity check
C. Validity check
![]() D. Sequence check
D. Sequence check
125. Which of the following descriptions best describes a delay window?
![]() A. The time between when an event occurs and when the audit record is reviewed
A. The time between when an event occurs and when the audit record is reviewed
![]() B. The time between when an incident occurs and when it is addressed
B. The time between when an incident occurs and when it is addressed
![]() C. The time between when an event occurs and when the audit record is recorded
C. The time between when an event occurs and when the audit record is recorded
![]() D. The difference between a threshold and a trigger
D. The difference between a threshold and a trigger
126. You have been asked to review a console log. What type of information should you expect to find?
![]() A. Names and passwords of system users
A. Names and passwords of system users
![]() B. Application access and backup times
B. Application access and backup times
![]() C. System errors
C. System errors
![]() D. Errors from data edits
D. Errors from data edits
127. During a software change process, auditors might be asked to verify existing source code at some point. What is the most effective tool for auditors to compare old and new software for unreported changes?
![]() A. Function point analysis (FPA)
A. Function point analysis (FPA)
![]() B. Manual review of the software
B. Manual review of the software
![]() C. Variation tools
C. Variation tools
![]() D. Source code comparison software
D. Source code comparison software
128. Which of the following is not a valid processing control?
![]() A. Authorization
A. Authorization
![]() B. Processing
B. Processing
![]() C. Validation
C. Validation
![]() D. Editing
D. Editing
129. Which of the following is not part of the project-management triangle?
![]() A. Scope
A. Scope
![]() B. Time
B. Time
![]() C. Resources
C. Resources
![]() D. Cost
D. Cost
130. Using Figure E.10 as a reference, place the four recovery time objectives in their proper order.
![]() A. Items A, B, C, D
A. Items A, B, C, D
![]() B. Items B, C, D, A
B. Items B, C, D, A
![]() C. Items D, A, C, B
C. Items D, A, C, B
![]() D. Items C, B, D, A
D. Items C, B, D, A
Figure E.10
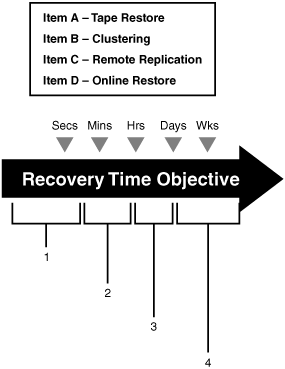
131. When dealing with project-management issues, which of the following is ultimately responsible and must ensure that stakeholders’ needs are met?
![]() A. Stakeholders
A. Stakeholders
![]() B. Project steering committee
B. Project steering committee
![]() C. Project manager
C. Project manager
![]() D. Quality assurance
D. Quality assurance
132. Projects must take on an organizational form. These organizational forms or frameworks can be either loosely structured or very rigid. Which project form matches the description “The project manager has no real authority, and the functional manager remains in charge”?
![]() A. Weak matrix
A. Weak matrix
![]() B. Pure project
B. Pure project
![]() C. Balanced matrix
C. Balanced matrix
![]() D. Influence
D. Influence
133. Which of the following is the best description of the Constructive Cost Model (COCOMO)?
![]() A. COCOMO is a model that forecasts the cost and schedule of software development, including the number of persons and months required for the development.
A. COCOMO is a model that forecasts the cost and schedule of software development, including the number of persons and months required for the development.
![]() B. COCOMO is a model that forecasts network costs associated with hardware, the physical medium, and trained personnel.
B. COCOMO is a model that forecasts network costs associated with hardware, the physical medium, and trained personnel.
![]() C. COCOMO is a forecast model that estimates the time involved in producing a product and shipping to the end user.
C. COCOMO is a forecast model that estimates the time involved in producing a product and shipping to the end user.
![]() D. COCOMO is a model that forecasts the construction of additional companies associated with organizational growth.
D. COCOMO is a model that forecasts the construction of additional companies associated with organizational growth.
134. Which of the following software-estimating methods does not work as well in modern development programs because additional factors that are not considered will affect the overall cost?
![]() A. Facilited Risk Assessment Process (FRAP)
A. Facilited Risk Assessment Process (FRAP)
![]() B. Gantt
B. Gantt
![]() C. Function point analysis (FPA)
C. Function point analysis (FPA)
![]() D. Source lines of code (SLOC)
D. Source lines of code (SLOC)
135. Which of the following is the best example of a quantitative risk-assessment technique?
![]() A. The Delphi technique
A. The Delphi technique
![]() B. Facilitated risk-assessment process
B. Facilitated risk-assessment process
![]() C. Actuarial tables
C. Actuarial tables
![]() D. Risk rating of high, medium, or low
D. Risk rating of high, medium, or low
