CHAPTER THREE
The Power of HEX
Finding Slivers of Data
RONELLE SAWYER IS INVESTIGATING whether Jose McCarthy has potentially engaged in the unlawful distribution of his organization’s intellectual property to a competitor, Ms. Janice Witcome, Managing Director of the XYZ Company.
Ronelle is faced with examining millions of pieces of potential evidential data residing on Jose’s hard drive, looking for the proverbial needle in the haystack, a sequential occurrence of the character string “X,” “Y,” “Z.” Ronelle has deciphered the character’s decimal equivalent into individual binary values, and now must make sense of this run on string of 1s and 0s in an effort to identify a similar string of 1s and 0s on the hard drive seized from Jose’s office.
Our running case is used as a basic illustration of a complex scenario, to communicate to the reader the complexities behind essential building blocks of cyber forensics. It is important for the reader to note that in an actual investigation, searching for a character string of the company name, “XYZ,” as in our example case, may not be ideal as it would generate many false positives. The reader should keep in mind that the examples used in this book are utilized to express forensic concepts or ideas, and not investigative assistance.
The process of deciphering binary values into their decimal equivalents can become very tedious, time-consuming, and very expensive, especially if the string of binary values is large. Fortunately for Ronelle, the binary string representing the characters “X,” “Y,” and “Z” is relatively small.
How can Ronelle better represent this binary string without the tedium of decimal computation as discussed previously? The solution, convert the binary string of 1s and 0s into their hexadecimal equivalent notation.
Hexadecimal (abbreviated as HEX) is strictly a human friendly representation of binary values. A HEX character is often prefixed with 0x (zero, sub x) to denote it from another encoding system. So, 0x3F tells the reader that 3F is HEX, and not ASCII.
The computer or processor does not calculate in HEX. Software can convert binary to HEX, but the microprocessor itself does not perform its mathematical computations in HEX. HEX is a base 16 character code, which, as we will see, works well at representing binary.
Why? The 16 characters representing HEX are the symbols 0–9, representing values 0 to 9, and A, B, C, D, E, and F, representing values 10 to 15. There are thus 16 unique characters, each of which corresponds to a pattern of four bits.
The 16 HEX values along with their assigned decimal and binary conversions can be seen in Table 3.1.
TABLE 3.1 HEX, Binary, and Decimal Equivalents
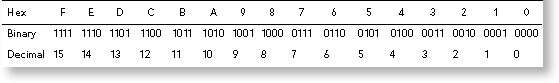
As seen in Table 3.1, the 16 HEX characters can assume all possible 4 bit binary values (24 = 16).
In order to understand how binary is converted to HEX we need to examine the concept of a byte a “bit” more closely.
A byte is split (for human understanding, again this is not something the processor does when computing) into two equal halves called nibbles. A single HEX character corresponds to one nibble’s worth of data, 4 bits. However, a standard encoding character needs a full byte or 8 bits for representation. So, two nibbles need to be paired in order to accomplish this representation.
Thus, we have four (4) bits per nibble (see Figure 3.1), two (2) nibbles per byte (see Figure 3.2), and eight (8) bits per byte (see Figure 3.3).
FIGURE 3.1 Four Bits Equals One Nibble
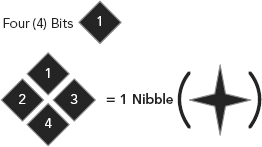
FIGURE 3.2 Two Nibbles Equal One Byte
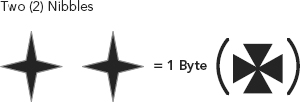
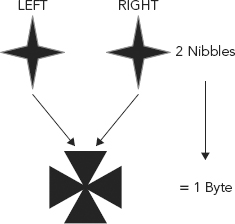
FIGURE 3.3 Eight Bits Equals One Byte
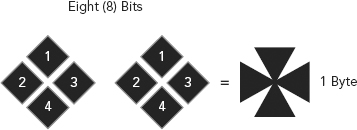
Thus in Figure 3.3, we see that eight (8) bits equal one (1) byte.
It can also be said then, that eight bits, or two nibbles, equals one byte (see Figure 3.4).
FIGURE 3.4 Bit, Nibble, and Byte Equivalents

It is important to remember a byte stands alone when representing a character or symbol, whereas a nibble cannot; it needs its other half (or said another way—a standard encoding character needs a full byte or eight bits for representation).
Therefore, two nibbles must be paired in order to accomplish this representation. Remember, a HEX character code has 16 unique values—A through F and 0 through 9.
How many binary values (bits) are needed to represent 16 unique values? The answer: 2^4 (2 . . . 4 . . . 8 . . . 16).
It is important to remember that we are dealing with binary values, so any math will need to be base two. So the “base” number of calculation is 2:
![]()
A HEX value can, therefore, exactly correspond to all 16 values, each four bits in length.
To help understand this further let us revisit a previously asked question, “how many bits would be necessary to represent the four seasons (winter, spring, summer, and fall)?”
One bit gives us only two possible values, 0 or 1. This would be sufficient to represent the state of a light On or Off but not four seasons. Remember, we are looking for binary values, Base 2, so each value will only have two possible states.
Two bits would actually give us the four possible values needed to represent four seasons: 00, 01, 10, and 11, as shown in Table 3.2. This can be done mathematically as well: 2 × 2 = 4.
TABLE 3.2 Two Bits Representing Four Possible Values
| Bit 1 | Bit 2 |
| 0 | 0 |
| 0 | 1 |
| 1 | 0 |
| 1 | 1 |
A HEX value can therefore exactly correspond to all 16 possible four-bit values. The 16 HEX characters (A–F, 0–9) can be represented by four binary values (e.g., 1101, 0110, 0010) per character, such that the HEX character “A,” for example, is represented by the binary value 1010. (See Table 3.3.)
TABLE 3.3 HEX Characters and Binary Equivalents

Remember, four bits equals one nibble; therefore, one HEX character represents one nibble.
In summary:
1 bit = binary value of 0 or 1
4 bits = nibble = one HEX character
2 nibbles = 1 byte
8 bits = 1 byte
1 byte = 2 HEX characters
So, to answer the question which led off this discussion, why use HEX to represent binary? Because both a byte and 2 HEX characters represent eight bits, totaling 256 potential values.
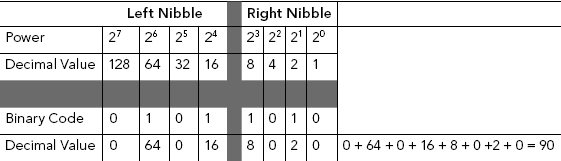
In order to differentiate between two nibbles, one is referred to as the left nibble and the other as the right nibble.
HEX, as we have demonstrated, uses a base of 16. We can split a byte into two groups of four bits each (e.g., nnnn nnnn). Each individual group is then referred to as a nibble.
The right nibble with all of its bits turned off, or 0000, is equal to a value of 0; with all of its bits turned on, 1111, the right nibble has a value of 15 (8 + 4 + 2 + 1).
Let’s summarize (see Figures 3.5, 3.6, and 3.7).
FIGURE 3.5 Four Bits Equal One Nibble
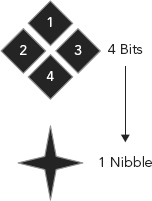
FIGURE 3.6 Eight Bits Equals Two Nibbles
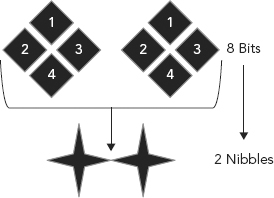
FIGURE 3.7 Two Nibbles Equal One Byte
Remember nibbles work in pairs, left and right. See Table 3.4.
TABLE 3.4 Left and Right Nibble
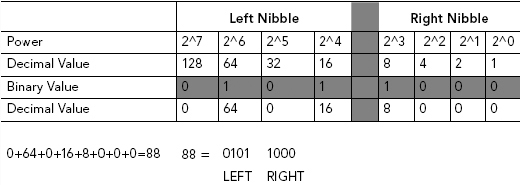
Let’s compare a decimal conversion with a conversion to HEX, using Ronelle’s relatively small binary string representing the characters “X,” “Y,” and “Z.”
The binary value of the characters “X,” “Y,” and “Z” equals 010110000101100101011010.
If we split these values into four-bit chunks representing nibbles, and pair them up to form a byte, the result is shown in Table 3.5. Figure 3.8 shows the decomposition of a byte, beginning with the nibble, both the right and left, and the individual bit. We need four (4) bits to make a nibble, and two (2) nibbles to make a byte.
FIGURE 3.8 Data Basics
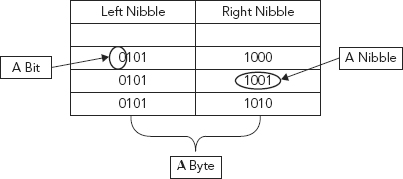
TABLE 3.5 Left and Right Nibbles for the Binary Value 010110000101100101011010
| Left Nibble | Right Nibble |
| 0101 | 1000 |
| 0101 | 1001 |
| 0101 | 1010 |
Table 3.6 shows how easily we can convert binary into decimal.
TABLE 3.6 Binary to Decimal
![]()
Table 3.7 shows the conversion of binary values into their HEX equivalent.
TABLE 3.7 Binary to HEX
![]()
Combining Tables 3.6 and 3.7 produces the results shown in Table 3.8.
TABLE 3.8 HEX, Binary, and Decimal Equivalent
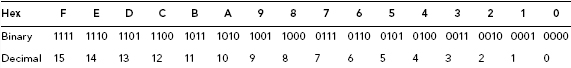
To continue using Ronelle’s binary string representing the characters “X,” “Y,” and “Z” as part of her search strategy to determine Jose’s culpability, Ronelle first converts the ASCII values to their binary equivalent as shown in Tables 3.9, 3.10, and 3.11.
TABLE 3.9 ASCII “X” Converted to Binary Equivalent 01011000
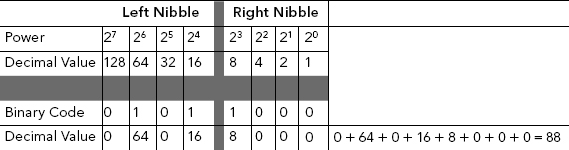
TABLE 3.10 ASCII “Y” Converted to Binary Equivalent 01011001
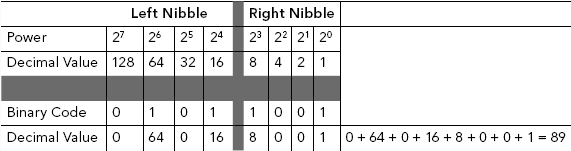
TABLE 3.11 ASCII “Z” Converted to Binary Equivalent 01011010
Summarized, Ronelle’s data is shown in Table 3.12.
TABLE 3.12 Decimal to Binary Conversion
| ASCII | Decimal Value | Binary Value |
| X | 88 | 0101 1000 |
| Y | 89 | 0101 1001 |
| Z | 90 | 0101 1010 |
Next, Ronelle converts the binary values to their HEX equivalent, as shown in Tables 3.13, 3.14, and 3.15.
TABLE 3.13 Binary 01011000 Converted to HEX
![]()
TABLE 3.14 Binary 01011001 Converted to HEX
![]()
TABLE 3.15 Binary 01011010 Converted to HEX
![]()
Table 3.16 summarizes Ronelle’s conversion efforts to give her the HEX values of the ASCII characters she must search for on Jose’s hard drive.
TABLE 3.16 HEX Equivalent of ASCII Characters “X,” “Y,” and “Z”

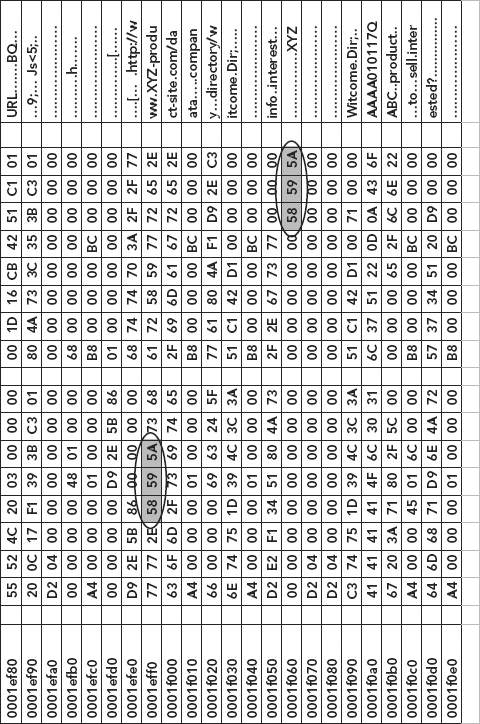
Thus, Ronelle must search for the HEX string 58595A, which represents the ASCII characters “X,” “Y,” and “Z.”
Using a HEX editor, Ronelle looks for the very distinguishable 58595A HEX value representation to uncover the occurrence of any reference to the XYZ Company on Jose’s hard drive.
A HEX editor is a program which allows you to view and or edit compiled programs and binary data files.
These editors are called HEX editors because they most often present data in hexadecimal format. Hexadecimal is used because it is easier for most humans than working in binary. In addition, hexadecimal is frequently useful because computers tend to work with eight-bit bytes of information and because ASCII is an 8-bit code.
You can’t see all the bytes stored in a file using a regular application to open the file, and there are no applications available to view deleted items. Sometimes, part of the file is missing, including the piece that contains the executable code launching the application needed to open it in the first place.
A cyber forensic investigator needs a binary/HEX editor for analyzing file structures. Viewing HEX allows Ronelle to go beyond the application or file, and it will allow for the viewing of all data contained within a file, including remnants of old files or even deleted files, which may exist on Jose’s hard drive.
Figure 3.9 is a representative example of the output view of a HEX editor.
FIGURE 3.9 HEX Editor (sample view)
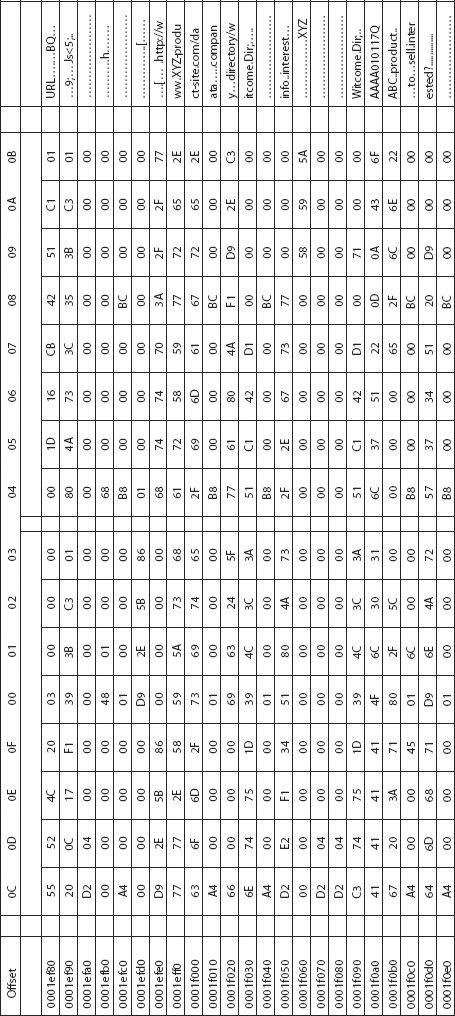
A HEX editor consists of four distinct display areas, or panels, each having its own significance and conveying specific information relative to the editor itself, as well as providing essential information to the investigator.
The four distinct display areas are:
1. Header Panel (A)
2. Address Panel (B)
3. HEX-data Panel (C)
4. Character Panel (D)
These four panel areas of the HEX editor are identified in Figure 3.10.
FIGURE 3.10 The Four Panel Areas of the HEX Editor
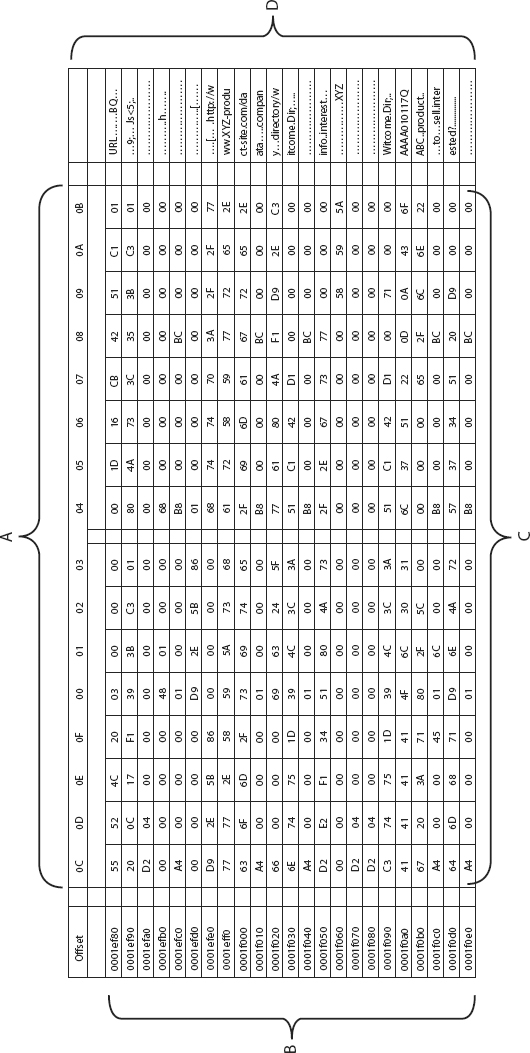
Header Panel (A)
The header panel displays the headers of any of the other three panels (see Figure 3.11). Among them, HEX-data panel (C) uses the byte offsets relative to the beginning of the line as its header.1
FIGURE 3.11 Header Panel
Address Panel (B)
Every byte in a file is assigned a number, called its address, starting at 0 for the first byte of the file, 1 for the second byte, and so on. See Figure 3.12.
FIGURE 3.12 Address Panel
The address panel displays the address of the byte at the beginning of the line.2
HEX-Data Panel (C)
The middle hexadecimal area is the most commonly used area of a HEX editor. It lists each byte of the file in a table, usually 16 bytes per line.
In Figure 3.13, the first eight bytes of the file are “55-52-4C-20-03-00 00 00.” The HEX-data panel lists the hexadecimal value of each file byte; default is 24 bytes per line. It works in the HEX editing mode, and displays the hexadecimal value of each byte as a two-character field.3
FIGURE 3.13 HEX-Data Panel
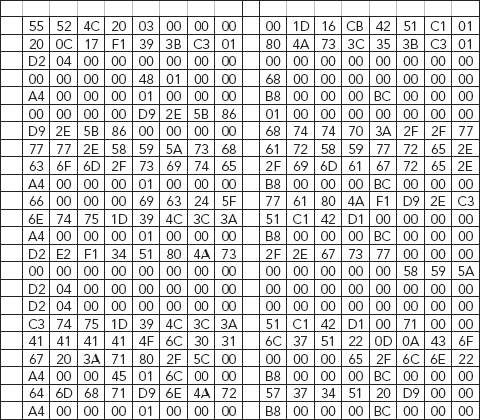
Character Panel (D)
Figure 3.14 shows the details of the character panel.
FIGURE 3.14 Character Panel

The character panel displays the ASCII value of each file byte. It only provides the view of printable characters; non-printable characters are shown as a period character (“.”) or with another user-defined character.4
Ronelle will now search the HEX editor looking for any occurrence of the HEX value 58595A, as she knows that this value represents the characters “X, Y, and Z.”
If Ronelle finds the HEX sequence 58595A within the data retrieved from Jose’s hard drive, then this is likely stronger evidence, which might further implicate Jose in the potential theft of intellectual property and involvement between Jose and the XYZ Corporation.
HEX Value 58595A
In Figure 3.15, we see a representative example of how the HEX value 58595A might appear to Ronelle as she examines the HEX editor data panel.
FIGURE 3.15 HEX Value 58595A as It Appears in the HEX Editor
THE NEEDLE WITHIN THE HAYSTACK
Why do humans need a friendly way to view binary? Most humans will have a very difficult time attempting to make sense out of long strings of 1s and 0s, end to end, for more than, say, eight positions. Quick, what does this say: 0110100001100101011011000110110001101111?
Cyber forensic investigators MUST have a thorough understanding of the process by which raw bits of data are turned into information, and how complex silicon devices interpret pulses of energy, assigning these pulses the computable values of one and zero, and then into higher order numerical values, and eventually into characters that are understood by their carbon-based handlers. This provides Ronelle and cyber forensic investigators a means to find the sliver of data they are looking for, amid potentially billions of bytes of extraneous data.
A document or file has what is sometimes called headers or supplemental data, placed at the beginning of a block of data. In data transmission, the data following the header are called the body. The header in effect binds the body to the software needed to open it or otherwise access it.
For example, a document created with Microsoft (MS) Word may have difficulty being opened using Adobe Acrobat Reader/application. This is because there is code embedded within any document created using MS Word, which tells the operating system that MS Word (or other compatible software) is needed in order to open the document.
If the code which binds the document to its native software is somehow overwritten or “erased,” the software will not be able to reassemble the document into its native format or into a format readable by the user, thereby causing the document to be inaccessible and unreadable by the user.
Some of these data, such as incriminating text (the occurrence of “XYZ” for example), may however still reside in a document, on a disk, within the hard drive. Ronelle would not want to miss this potentially incriminating evidence and would need a verifiable way to cull through the millions of bytes of data on Jose’s hard drive. Finding such evidence could substantiate or refute the claims brought by ABC Inc. against its employee Jose, in the theft of ABC’s intellectual property.
For a cyber forensic investigator to properly search for a keyword contained within data seized from an entire hard drive (or even from data narrowed down to a specific folder or specific image within a user’s hard drive), it is best to use HEX to assist in accomplishing this herculean task.
Viewing HEX allows an investigator to go beyond the application or file. It allows for the viewing of all the data contained within a file including remnants of old or even deleted files.
With this introduction of the basics of “computer math,” we are ready to kick it up a level in Chapter 4 to working in the world of HEX, the cyber forensic investigator’s best friend.
1. “What Is a Hex Editor?” Hexprobe, retrieved December 10, 2009, www.hexprobe.com/hexprobe/hex_editor.htm.
2. Ibid.
3. Ibid.
4. Ibid.
