9
Data Falsification Detection in AMI: A Secure Perspective Analysis
1Department of Electrical and Electronics, Sri Krishna College of Engineering and Technology, Coimbatore, India
2Department of Electronics and Communication, Sri Krishna College of Engineering and Technology, Coimbatore, India
Abstract
Advanced metering infrastructure (AMI) being a crucial component of smart grid environment has enormous attractive characteristics and relatively low cost of installation. AMI makes communication in two-way possible between the smart metering infrastructure and utility centers which facilitates functionalities like automated reading of meter data and power distribution monitor and control. Nevertheless, the implementation of AMIs poses several challenges and threats which can, in turn, deteriorate its benefits. This paper gives an overview of various attack scenarios associated with AMI with major focus on data falsification attacks. In data falsification attacks, attackers aim to inject malicious codes or false data to tamper legitimate data. A detailed analysis of the various detection schemes that are available to effectively detect such attacks is also given on the paper.
Keywords: Advanced metering infrastructure, smart meter, false data injection, detection
9.1 Introduction
The numerous enhancements and improved innovative potential of smart grid environment create grid architecture complex and expose the grid to a variety of attacks. Advanced metering infrastructure (AMI) acts as a basic element of the smart grid, as it answerable for gathering, estimating, investigating vitality use information, and transmitting this information to the information concentrator and afterward to a focal framework in the utility side [1]. However, they may experience diversity of threats, together with both physical and cyberattacks. Malicious attackers or software may attempt to obliterate meter reading. Recognizing attacks toward smart meters is a crucial test for building a security system. Smart grid primarily has four segments including supervisory control and data acquisition (SCADA), AMI, communication protocols, and standards and plug-in hybrid vehicle (PHEV). Smart meter being a part of AMI gives exact estimation with robotize remote perusing intensity utilization. Certain smart meters can likewise combine with home machines of smart nature in order to control them so as to work effectively utilizing power. Each of the capacities accomplished using communication in two-way manner using sensors. Smart meters carry out mainly two different functions on communication. The primary function is to transfer gathered information to the service organization in order to get orders for operation. Subsequent function is trading of information to hardware so as to maintain the home energy management system (HEMS). In addition, there exist other correspondence methods that are generally utilized on smart meters for transmitting information to service organization. The methods are power line carrier (PLC) and radio frequency (RF). Because of smart meter information assortment along with correspondence capacities, this might turn into an objective by malicious attackers wishing to make profit by taking or controlling smart meter information [2]. The protection for these attacks can be made by securing all interchanges among smart meters and utility organizations. In addition, smart meters must be introduced at secure areas so they cannot be handily messed with genuinely.
For smart meter protection, three major techniques may be observed: first one being intrusion detection system (IDS), second one is remote attestation technologies, and third method is smart meter software modeling. Detecting false data injection (FDI) attacks are given main focus here. Remaining part of paper is ordered as follows. Section 9.2 provides an outline of AMI. In Section 9.3, there is a close look at the AMI attack scenario. In Section 9.4, data falsification attacks in AMI are discussed, and Section 9.5 gives an analysis of data falsification detection methods. Section 9.6 concludes paper.
9.2 Advanced Metering Infrastructure
AMI deployment combines three main functionally intense components including smart meters, communications network, and data organization system which facilitate bidirectional communication among customers and utility companies [3]. System as a whole enables numerous vital functionalities which otherwise would not have been possible or that needed manual effort. Such functions include the capability of automatic and remote power usage measurement, service connection and disconnection, tamper detection, outage identification and isolation, and voltage monitoring. AMI, in addition, enables utility centers to provide novel time-based programs and incentive schemes to support customer community to decrease power demand peaks and handle power consumption charges. This is done by collaborating with customer technologies like programmable communicating thermostats and in-home displays, web portals, etc.
The main component of AMI is smart meters that are deployed at the customer’s site and are used to collect power collection data at specified intervals. Such data can be made use of for several major tasks like on demand response, load management, and automatic billing. Communication networks enable the smart meters to convey precise, consistent, and huge data streams in a well-timed manner. These network systems join end systems and smart meters so as to handle data communicating among information systems and smart meters in AMI [4]. The end system performs functions like transmission and reception of data, propagating operational instructions to meters along with storing time-based load information of meters in order of supporting billing customers. Without deployment of smart meters and communications management systems which connects them, most of demand-reducing and cost saving impacts and benefits from AMI would not be benefited. The data management system in AMI serves the data acquisition and organization function along with real-time monitoring and report generation. This component usually validates and cleans data before its processing and also deals with long-term storage and management of data. Figure 9.1 shows AMI architecture.
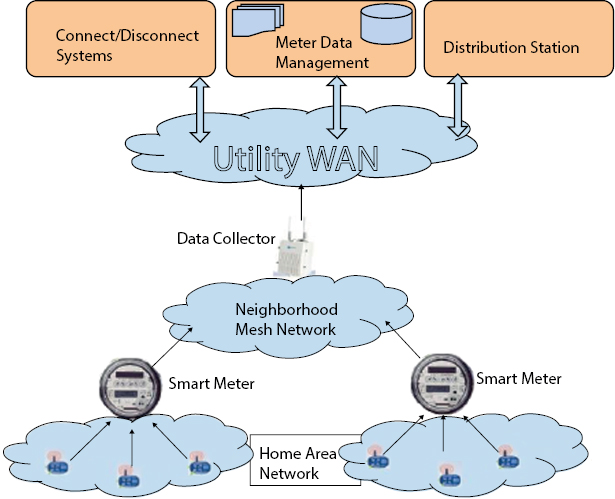
Figure 9.1 AMI architecture.
Various devices for control along with sensors are deployed in smart meter for the correct identification of different devices and parameters in order to permit transmit instruction signals and data. Enormous number smart meters are deployed to correspond with utility centers by way of AMI network. The two-way networks are either mesh, hierarchical, or hybrid. Intermittent collection, storage, and propagation of voluminous data packets are done via the communication network. Each element of the AMI executes its own purpose and together attains the overall functionality of the infrastructure.
9.3 AMI Attack Scenario
The wireless nature of communication in AMI and the inherent properties of its implementation create suitable attack surface for attackers. The main features of AMI that attract attackers include the provision to have access to lots of low computation equipments, sensitive end user information access, visibility of cases like energy outage, and knowledge of energy consumption–related financial information. As a result, attackers find it easy to perform malicious activity on communication system and may intend to steal end user information, disconnect certain regions, etc. [5].
Distributed Denial of Service (DDoS) can be considered as a major attack type of AMI. In this case, the attack is performed on the data collection unit of AMI which affects the communication functionality of communication network. Usually, attackers consider smart meters as their entry point and would perform malicious actions like physical tampering and malware installation, forming coordination among compromised meter to target for further attack, and the generation and propagation of large amount of malicious data packets. Another type of attack in AMI deals with stealing customer information. Here, the attacker performs eavesdropping on network traffic of smart meters to get customer information and learn their behavior. Steps like physical access of meter by way of methods like brute force attack to get decryption key, intercepting of messages, and decryption and content collection from messages are done as part of this attack. Another type of attack is the sending of remote commands like disconnect. Here, attacker tries to use remote messages to smart meters to disconnect many of the end users [6]. The attacker would carry out steps like exploit network vulnerability or physically tamper device like data communication unit to install malware, collect data from meters including IP addresses, and may send remote disconnect commands to meters.
Several types of attack categories have been identified on AMI. These include Denial of Service (DoS), spoofing, eavesdropping, physical attack, and communication attacks. DoS attacks include collision in packet propagation, packet flooding, jamming, routing table alteration, packet drop, node destruction, and resource deterioration. Spoofing attacks include impersonation of regular or master nodes, man-in-the-middle attack and wormhole problem. Attacks in AMI can also be categorized as physical attacks and cyberattacks based on the location of its occurrence. Physical attacks include physically destroying meter components, disconnecting meters, reversing the meters, and the likes. Cyberattacks involve network exploitation, injection of malicious code or data, eavesdropping of network communication and data, and flooding of network bandwidth so as to make it unavailable to legitimate users.
9.4 Data Falsification Attacks
Among the different types of attack scenarios for AMI as discussed in the previous section, a characteristic attack in real time is the tampering of legitimate information of a smart meter infrastructure by way of injecting malicious code of data or falsified data for monetary benefits. This type of attack can be either a cyberattack or a physical attack (by way of physically tampering the components). The problem is usually done using consequent steps. In the start, attacker weakens network capacity so as to disconnect the network to consume physical memory information. The second step is to inject malicious data to meters and executing illegal modification of legal data in physical memory [7]. Data falsification could be categorized as deductive, additive, and camouflage mode of attack. These three attack modes are associated with electricity theft where in attackers aim at stealing electricity power. In deductive mode strategy, customers of compromised meters reduce meter reading of consumed power, whereas in additive mode, a load altering would be launched in order to increase power consumption reading to affect both end users and utilities. In camouflage method, entire margin of deductive mode is balanced using additive mode, in which a set of end users will have lesser power bills at the expense of others, and the overall mean aggregate energy consumption of a microgrid remains unaffected.
9.5 Data Falsification Detection
Detection of data falsification attacks is a major concern so as to implement security measures to mitigate the same. Several data falsification detection mechanisms are found in the literature and they could be generally classified as state estimator detection, classification-based detection, and consensus detection. Classification-based schemes make use of total and detailed profiling of each meter to detect attacks. It makes use of ideas like neural network and support vector machines for detection [8]. These systems are computationally very expensive and are impractical in real scenarios of AMI which are enormously large with millions of meters. State-based detection requires additional hardware components to be deployed at various areas of AMI for detection. This makes it complex and expensive. Consensus-based approach uses parametric techniques, non-parametric techniques, and mean aggregate outlier analysis for detecting data falsification. The detection is done by comparing predicted and observed consensus, that is, if the variation among two is bigger than particular predefined value, then falsification is confirmed. The difficulty with this technique is that the mean energy consumption data vary readily and have innate unstable nature of consumption and thus create major barriers for comparison.
Several detection schemes have been proposed for detecting FDI in smart grid environment. Though such schemes cannot be as such used in AMI scenario, many of the schemes designed for AMI resemble certain characteristic feature of smart grid schemes. Many algorithms are identified for detection in grid scenario like generalized likelihood ratio test and geometrically designed residual filter [9]. Authors in [10] and [11] introduced cumulative sum test–based detection method (CUSUM) to detect FDIA. Machine learning approaches was also been proposed to identify such attacks [12, 13]. To identify vulnerable nodes, relationship of physical parameters of system can be used [14]. In [15], a detection scheme is proposed where the entire system categorized as subsystems by means of partition algorithm and extended distributed state estimation is carried out. In [16], investigation of two main properties of smart grid that reflect its property is used. A parameter that indicates voltage fluctuation and another one is quantitative node voltage stability index. A higher value of the second parameter indicates a higher risk aspect. Cluster algorithm is used to group the nodes and detect suspicious ones. State forecasting detection is done to find sensitive measurements and several attack vectors are built for further results.
A model for smart meter threat is proposed in [17] for AMI network. Colored Petri net model is exploited in the paper to build the threat model. The detection mechanism is based on spying domain, secret data for meters and event log and the system is found to work even if the underlying software changes [18]. Paper discusses a real-time and light weight method uses a two-tier detection scheme for AMI. The primary tier examines if Harmonic to Arithmetic Mean Ratio in cumulative daily energy consuming data outside an ordinary value or not. Confirming discrepancies is identified in first tier are definitely attacks, tier 2 observes total residuals value among proposed value and safe range for some days. If the residual value is beyond a standard limit, then FDI is confirmed. The data omission aspect is not dealt with in the paper which could be implemented with a slight modification in second tier. Principal component–based data falsification detection is identified in [19]. A parameter called Mahalanobis distance is calculated between test data and historical data, and if its value is found to be outside an already fixed standard value, then test data is confirmed to be falsified. The scheme is found to have high detection ratio. An efficient hidden Markov model–based FDI detection and HMM based-method to detect false data injection attacks in AMI is discussed in this chapter [20, 21]. The method quickly and accurately detects attack by building a global state vector and training it using available meter data. The storage space problem is lessened using a fast Viterbi algorithm, and it also improves data decoding that is done using the vector.
9.6 Conclusion
Various attack scenarios of AMI are identified in the paper with prime focus given on data falsification attacks. Several detection schemes are available in literature that can effectively detect such FDI of AMI and concise analysis in those approaches is given in the paper. Though numerous attack detection schemes are available for smart grid, they cannot be as such implemented for AMI because of its unique characteristics. Detection of data falsification attacks in AMI is of a major concern based on which efficient security schemes have to be implemented considering its computational potential and limited memory.
References
1. Khattak, A.M., Khanji, S.I.R., Khan, W.A., Smart Meter Security: vulnerabilities, threat impacts, and countermeasures. 2019 Springer.
2. Mehra, T., Dehalwar, V., Kolhe, M., Data Communication Security of Advanced Metering Infrastructure in Smart Grid. 2013 5th International Conference on Computational Intelligence and Communication Networks.
3. Depuru, S.S.S.R., Wang, L., Devabhaktuni, V., Gugi, N., Smart meters for power grid: Challenges, issues, advantages and status. Power Systems Conference and Exposition (PSCE), pp. 1–7, 2011.
4. Parvez, I., Sarwat, A.I., Wei, L., Sundararajan, A., Securing Metering Infrastructure of Smart Grid: A Machine Learning and Localization Based Key Management Approach. Energies, 9, 691, 2016.
5. Bhattacharjee, S., Thakur, A., Silvestri, S., Das, S.K., Statistical Security Incident Forensics against Data Falsification in Smart Grid Advanced Metering Infrastructure. 2017 ACM.
6. Grochocki, D., Huh, J.H., Berthier, R., Bobba, R., Sanders, W.H., AMI Threats, Intrusion Detection Requirements and Deployment Recommendations. 2012 IEEE Third International Conference on Smart Grid Communications (SmartGridComm).
7. Sgouras, K.I., Kyriakidis, A.N., Labridis, D.P., Short-term risk assessment of botnet attacks on advanced metering infrastructure. IET Cyber-Phys. Syst.: Theor. Appl., 2, 3, 143–151, 2017.
8. Lo, C.-H. and Ansari, N., CONSUMER: A Novel Hybrid Intrusion Detection System for Distribution Networks in Smart Grid. 2013 IEEE, vol. 1, no. 1, June 2013.
9. Oozeer, M.I., and Haykin, S., Cognitive Risk Control for Mitigating Cyber-Attack in Smart Grid. IEEE Access, 7, 125806–125826, 2019.
10. Pasqualetti, F., Dörfler, F., Bullo, F., Cyber-physical attacks in power networks: Models, fundamental limitations and monitor design, in: Proc. Decision Control Eur. Control Conf., pp. 2195–2201, 2011.
11. Kosut, O., Jia, L., Thomas, R.J., Tong, L., Malicious data attacks on the smart grid. IEEE Trans. Smart Grid, 2, 4, 645–658, Oct. 2011.
12. Li, S., Yilmaz, Y., Wang, X., Quickest detection of false data injection attack in wide-area smart grids. IEEE Trans. Smart Grid, 6, 6, 2725–2735, Dec. 2014.
13. Liu, L., Esmalifalak, M., Ding, Q., Emesih, V.A., Han, Z., Detecting false data injection attacks on power grid by sparse optimization. IEEE Trans. Smart Grid, 5, 2, 612–621, Mar. 2014.
14. Xiao, Y., Chen, H.H., Du, X., Guizani, M., Stream-based cipher feedback mode in wireless error channel. IEEE Trans. Wireless Commun., 8, 2, 662–666, Feb. 2009.
15. Anwar, A., Mahmood, A.N., Tari, Z., Identification of vulnerable node, clusters against false data injection attack in an AMI based smart grid. Inf. Syst., 53, 201–212, Oct. 2015.
16. Cramer, M., Goergens, P., Schnettler, A., Bad data detection and handling in distribution grid state estimation using artificial neural networks, in: Proc. IEEE Eindhoven PowerTech, Jun. 2015, pp. 1–6.
17. Xu, R., Wang, R., Guan, Z., Wu, L., Wu, J., Du, X., Achieving efficient detection against false data injection attacks in smart grid, special section on security analytics and intelligence for cyber physical systems. IEEE Access, 5, 13787–13798, 2017.
18. Liu, X., Zhu, P., Zhang, Chen, K., A collaborative intrusion detection mechanism against false data injection attack in advanced metering infrastructure. IEEE Trans. Smart Grid, 6, 5, 2435–2443, 2015.
19. Bhattacharjee, S. and Das, S.K., Detection and Forensics against Stealthy Data Falsification in Smart Metering Infrastructure. 2018 IEEE.
20. Singh, S.K., Bose, R., Joshi, A., Energy Theft Detection in Advanced Metering Infrastructure. 2018 IEEE.
21. Li, B., Lu, R., Xiao, G., HMM-Based Fast Detection of False Data Injections in Advanced Metering Infrastructure, vol. 6, pp. 1–6, Dec. 2017.
- *Corresponding author: [email protected]
