
Mobile Devices
Domain Objectives
• 1.1 Given a scenario, install and configure laptop hardware and components.
• 1.2 Compare and contrast the display components of mobile devices.
• 1.3 Given a scenario, set up and configure accessories and ports of mobile devices.
• 1.4 Given a scenario, configure basic mobile-device network connectivity and application support.
 Given a scenario, install and configure laptop hardware and components
Given a scenario, install and configure laptop hardware and components
Although an increasing number of laptops have no user-replaceable parts, there are still many existing and new models from a variety of manufacturers that will need replacement keyboards, upgraded RAM or mass storage, or other types of upgrades. This objective gives you the “inside story” on what to expect.
Hardware/Device Replacement
Laptops can break, but when they do, the problem is usually a component that can be replaced.
The most common replacements (or upgrades) include keyboards and other input devices, hard drives, and RAM, but there are several additional components that you might be called upon to swap out. Many of these components can be seen in Figures 1.1-1 and 1.1-2.
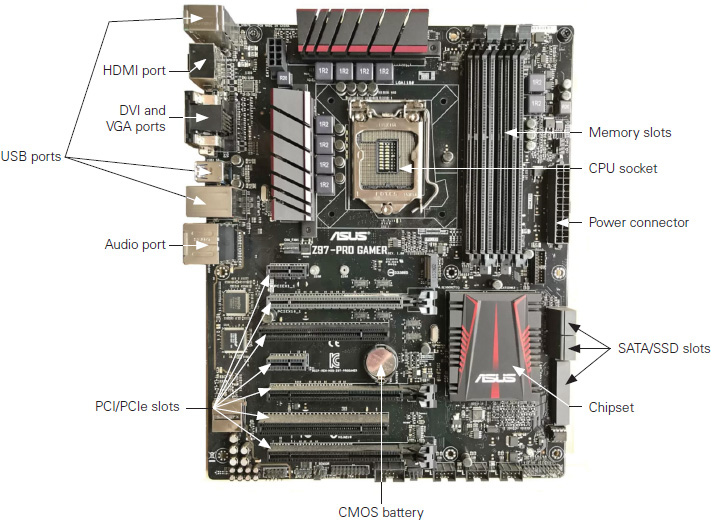
FIGURE 1.1-1 The major components on the top side of a typical laptop system board
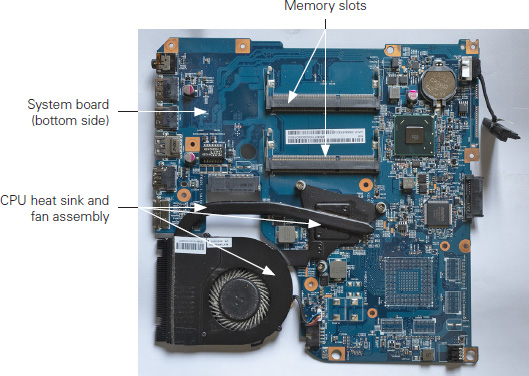
FIGURE 1.1-2 The bottom side of a typical system board
Cross-Reference
Be sure to apply electrostatic discharge (ESD) precautions when upgrading or replacing laptop field replaceable units (FRUs). The companion book in this set, Mike Meyers’ CompTIA A+ Core 2 Certification Passport (Exam 220-1102), provides coverage on ESD protections and preventive measures.

CAUTION Before attempting any laptop hardware or component replacement, refer to its service or owner’s manual or access it online. Because laptops differ so much from brand to brand and model to model, the steps vary a great deal, and if you don’t use proper procedures to disassemble a laptop, you might end up with more problems than when you started!
Keyboard
Replacing a laptop keyboard varies in difficulty from model to model. With some laptops, removing the old keyboard can be as easy as removing a retaining screw from the bottom of the laptop and pushing the keyboard up. However, some models require that almost all other components be removed before the keyboard can be removed.

NOTE If the built-in laptop keyboard fails and can’t be replaced right away, you can attach an external keyboard through a USB physical or wireless connection or through a Bluetooth connection.
Hard Drive
The term hard drive is used for a variety of mass storage devices using magnetic or solid-state technologies. You can replace a hard disk drive (HDD), solid-state drive (SSD), or solid-state hybrid drive (HHD or SSHD) easily in any recently manufactured traditional laptop; it’s almost certainly a 2.5-inch SATA drive (most are 7 mm thick, but a few thicker drives won’t fit into some laptops). Otherwise, no difference exists between 2.5-inch drives and their larger 3.5-inch brethren (see Figure 1.1-3).

FIGURE 1.1-3 The 2.5-inch and 3.5-inch drives are mostly the same.
Hard drive replacement is a little different on laptops than on desktops: find the hard drive hatch—either along one edge or on the bottom—and remove the screws (see Figure 1.1-4).
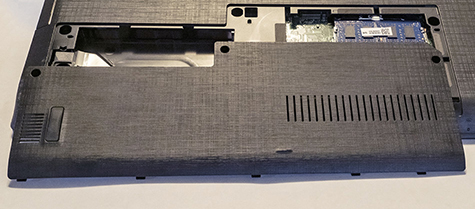
FIGURE 1.1-4 Removing the drive compartment hatch. Some laptops, like this one, use a single cover for access to hard drives and RAM.
Remove the old hard drive, detach its mounting hardware, and install the mounting hardware on the new drive. The mounting hardware might include brackets, shock bumpers, or a protective cover over the drive’s circuit board (see Figure 1.1-5).
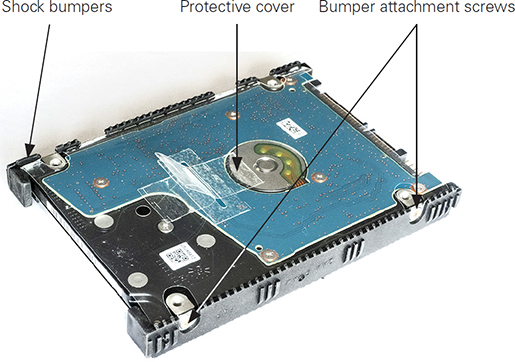
FIGURE 1.1-5 The mounting hardware on this hard drive must be removed and attached to the new drive so it will fit properly in the computer.
Next, slide the new drive into its place (see Figure 1.1-6), making sure it is firmly connected to the drive interface and secured in place. Reattach the hatch, boot the computer, and install an operating system (OS) if necessary.
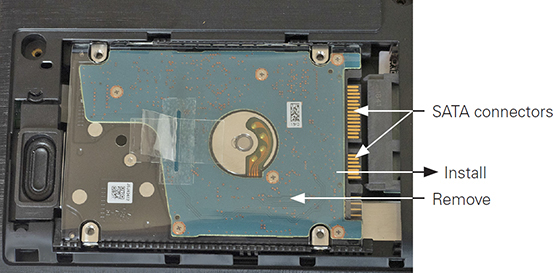
FIGURE 1.1-6 Inserting a replacement drive

NOTE Some laptops require the user to remove many components before upgrading the drive. Try to avoid upgrading these systems.
SSD vs. Hybrid vs. Magnetic Disk
One of the best laptop upgrades is to an SSD from a magnetic disk (HDD). It’s less storage for the money, but SSDs are faster, lighter, quieter, cooler, use less power, and lack mechanical parts easily damaged by bumps, drops, and travel. SSDs are available in both the traditional 2.5-inch laptop form factor and smaller form factors, most notable the M.2 design. Some laptops, like the one shown in Figure 1.1-7, can use both. M.2 SSDs are available in two types: those that emulate SATA drives as well as versions known as NVMe drives. These connect to the PCIe bus, which is much faster than the SATA bus.

FIGURE 1.1-7 A laptop with both SATA and SSD drives

EXAM TIP Make sure you are familiar with installing and configuring solid-state drives (SSDs) and magnetic hard disk drives (HDDs).
1.8 Inch vs. 2.5 Inch
Today, 2.5-inch HDDs and SSDs dominate laptop designs, as 1.8-inch HDDs have fallen out of favor due to flash memory usurping their role in portable music players and other small portables. These days, 1.8-inch HDDs are quite rare. If you encounter one, it almost certainly will be in an older portable on the small end of the scale.
Cross-Reference
For more on HDDs and SSD, see Domain 3.0, Objective 3.4.
Memory
Some laptops have upgradeable memory (RAM) slots, and other portables may not. RAM for portable devices, and especially laptop PCs, has its own small outline DIMM (SO-DIMM) form factor. Older SO-DIMMs (DDR and DDR2) were configured with 200-pin expansion cards. The DDR3 and DDR3L (low-voltage) cards used 204-pin SO-DIMMs, and the 260-pin DDR4 and 262-pin DDR5 SO-DIMMs. A DDR5 SO-DIMM has a 4800 MT/s (megatransfers per second) data rate and is currently available with 8 GB, 16 GB, and 32 GB memory capacities. Figure 1.1-8 shows examples of the DDR3, DDR4, and DDR5 SO-DIMMs.
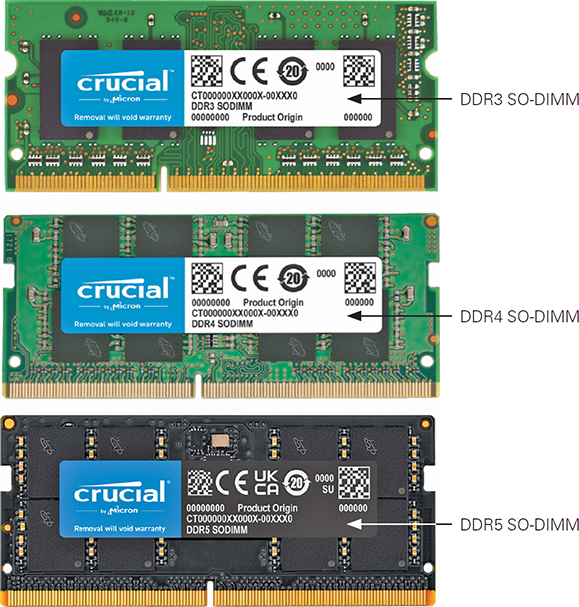
FIGURE 1.1-8 Examples of DDR3 (top), DDR4 (middle), and DDR5 SO-DIMMs (bottom) (images courtesy of Micron Technology, Inc.)

NOTE The DDR5 SO-DIMM may not be backward compatible, even on DDR4 systems.

EXAM TIP Memorize the SO-DIMM form factors—and the associated memory technologies—for the CompTIA A+ 220-1101 exam. (Note that the CompTIA objectives use “SODIMM,” without the hyphen.)
When installing RAM, just like with a desktop, protect yourself and the portable by removing all power and taking ESD precautions. With portables, this includes removable batteries. If the portable has built-in batteries, consult the manufacturer’s resources to check if and how you can safely work on it.

CAUTION Some portables have both built-in and removable batteries.
Once you know you can work safely, consult the manufacturer’s website or manual to confirm what kind of RAM the portable requires. Next, check the existing RAM configuration to confirm what you need to buy. To go from 4 GB to 8 GB, for example, you need to know if the portable has one 4-GB module or two 2-GB modules. You should also match the clock speed and timing of the existing module.
Second, locate the RAM slots. Depending on the system, the RAM slots might be under the same panel that you remove to access the hard drive (refer back to Figure 1.1-4) or under a separate panel (see Figure 1.1-9) on the bottom of the portable. Then you push out the retaining clips, and the RAM stick pops up (see Figure 1.1-10). Gently remove the old stick of RAM and insert the new one by reversing the steps.

FIGURE 1.1-9 Removing a RAM panel
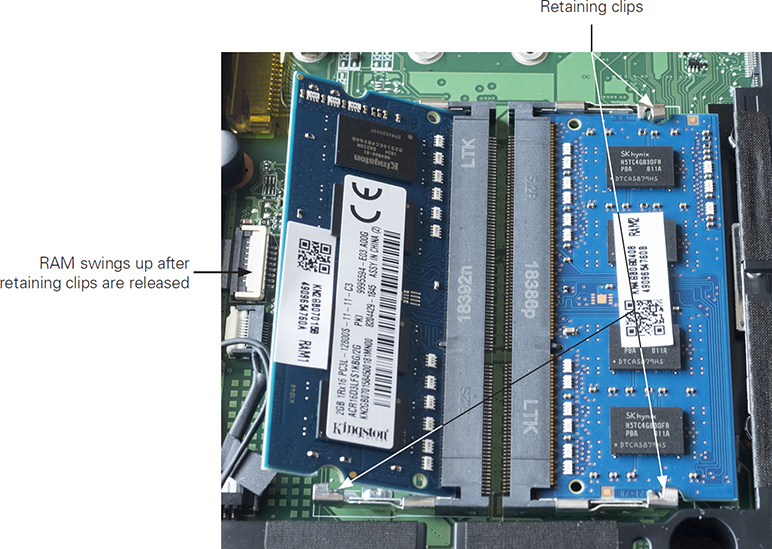
FIGURE 1.1-10 Releasing the RAM
Some portables (and desktops) have shared memory that enables the video card to borrow regular system RAM, providing performance comparable to its mega-memory alternative at a much lower cost. Unfortunately, the term shared memory is a bit misleading: the video card reserves this memory, and performance can suffer if the system runs out of it.

EXAM TIP RAM and hard drives are usually the easiest components to replace.
Some CMOS utilities can change the amount of shared memory, while others can just toggle the setting. In both cases, more system RAM will improve overall performance when the OS and CPU get more usable RAM; the upgrade can also improve video performance if the system either shares a percentage of all RAM or lets you adjust the amount.
Cross-Reference
For more about laptop and desktop RAM types and specifications, see Domain 3.0, Objective 3.3.
Wireless Card
A wireless card is sometimes relatively easy to swap, as it may be accessible from the panel covering the hard drive and/or RAM. Before choosing an upgrade, make sure you check out the supported models, as an unsupported card won’t be recognized by your system. If you upgrade a wireless expansion card, remember to reattach the antenna leads coming from the display in the correct locations. Depending on the age of the system, the wireless card might use a Mini-PCIe (refer back to Figure 1.1-1) or M.2 form factor.

EXAM TIP Make sure you are familiar with the form factors used for wireless cards/Bluetooth modules.
Physical Privacy and Security Components
Laptop computers and other mobile devices don’t stay in any one location, by design, which requires their physical security to be more specific to them than is the case for stationary devices. The physical security measures that protect desktop computers can also protect laptops, but only when the laptops are located within their coverage. A laptop that is moving about requires a special form of physical security that must also provide for data privacy as well.
Physical Security
The general objective of physical security is to restrict physical access to a device and, in turn, restrict logical access to its private content. Because a laptop is portable, its physical security must be portable as well. Certain aspects of physical security are difficult to apply to a laptop, such as preventing physical proximity, physical contact, and even physical possession. But wait, aren’t those the physical aspects we need to secure? Yes, but more importantly, we need to secure any access to private or sensitive information or services located on the device. In other words, for a laptop, physical security amounts to denying access to the laptop’s resources despite weak or nonexistent physical security.
The A+ Core 1 exam may include questions or content related to two of the methods used to secure laptops and their stored content: biometrics and near-field scanning.
Biometrics
Biometrics is used to both identify and authenticate someone attempting to gain access to a laptop and its resources. Biometrics involves the capture of one or more human traits for comparison against a prerecorded standard of the same measurements. Common biometric scans used with laptops and mobile devices include voice recognition, a fingerprint, the recognition of facial features, or an iris or retina scan of an eye.
Much like how a password is established as a control device, any of these biometric measurements and scans require a baseline capture to which future scans will be compared. Biometrics is, for the most part, reliable, and as the technology continues to develop, it becomes more and more reliable. However, biometric systems can produce two security flaws that, just like a password, require monitoring and the renewal of the baseline: false negatives and false positives.
A false negative occurs when the biometric scan of an authorized user results in the user being denied access. On the other hand, a false positive, which many be a more troublesome problem, occurs when an unauthorized supplicant is granted access in error.

NOTE The Windows Biometric Framework (WBF), located on the Windows Control Panel, provides native support for the interface, management, and control of biometric devices interfaced to a computer.
Near-Field Scanners
Although the technology is more of a protective application than a pure security measure, near-field scanning can safeguard a computer from harm by detecting electromagnetic interference (EMI) within a configured range of a device. As mobile devices move about, EMI signals in an area may be strong enough to cause damage to system and power components.
A near-field scanner measures the amount of voltage in a time period or by frequency and quantifies it. The resulting metric is used to determine if a threat exists and, if so, to alert the user. Older near-field scanning systems used an onboard antenna, but more recent systems employ a scanner receiver to detect any electrical charges in its vicinity. Understand, though, that near-field scanning works over relatively small distances.
REVIEW
Objective 1.1: Given a scenario, install and configure laptop hardware and components Laptop hardware and component issues you might deal with include the following:
• Keyboard replacement
• Hard drive (2.5 inch) removal and installation
• Use an SSD (2.5 inch or M.2), if you can, to improve performance and durability.
• Memory (SO-DIMM) types and their removal and installation
• Wireless card removal and installation
• Biometric devices for authentication and identification security
1.1 QUESTIONS
1. Your client wants you to upgrade the RAM, wireless cards, and storage in a collection of laptops from different vendors. Which of the following do you need to perform the work successfully? (Choose all that apply.)
A. Service manual for each model
B. Specialized tools
C. Specifications
D. All of the above
2. You are specifying the components you want in an ultimate gaming laptop. Which of the following standards provides the best opportunity for high-performance mass storage?
A. SATA
B. USB
C. M.2
D. Mini-PCIe
3. Which of the following laptop components typically requires the least disassembly to swap or upgrade?
A. Hard drive
B. RAM
C. CPU
D. Smart card reader
4. Your client wants to switch from SATA hard disk to SATA SSD storage in their fleet of laptops. Which of the following pieces of advice is most likely to be correct?
A. Buy M.2 drives because all laptops have M.2 slots.
B. SSDs are no faster than hard disk drives, so don’t bother switching.
C. Replacing hard disk drives with SSDs can provide better performance.
D. SSDs are more fragile than hard disk drives.
5. Your client has stripped components from retired laptops to use for replacement parts in more recent laptops. Which of the following is most likely to be compatible with a newer laptop?
A. Hard drive
B. RAM
C. Wireless card
D. Optical drive
1.1 ANSWERS
1. D A service manual provides detailed teardown and reassembly instructions; specialized tools help you open cases without breaking parts; specifications inform you of standard features and supported upgrades.
2. C M.2 drives using NVMe are the fastest mass storage devices.
3. B Most laptops with upgradeable RAM have the modules under an easy-to-remove panel on the bottom of the case.
4. C SSDs in the SATA form factor provide faster performance than SATA hard disk drives.
5. A As long as a SATA 2.5-inch hard drive will physically fit into a laptop, it can be used as a replacement (a few hard drives are too thick for some laptops, but that is rare).
 Compare and contrast the display components of mobile devices
Compare and contrast the display components of mobile devices
The displays on or in mobile devices, including those on laptop computers, are very complex components. As a certified A+ technician, you can expect to encounter, troubleshoot, and diagnose the displays across the gamut of mobile devices, which will likely include smartphones, tablet, laptop, and notebook PCs, and other smaller handheld devices. This objective covers the subjects, topics, and content you can expect to see on the A+ Core 1 exam (220-1101).
Types of Displays
As mentioned, mobile devices are available in an expanding range of sizes and capabilities, which are determined by the technology each uses to create a displayed image. The overall size of a mobile device is largely a function of its display’s size and its technology. A mobile device’s display, which is commonly a liquid crystal display (LCD) or an organic light-emitting diode (OLED), typically ranges from 3 inches to as much as 20 inches on some laptop PCs.
LCD
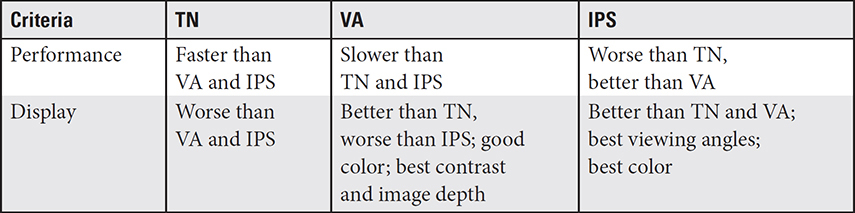
An LCD display is backlit with light-emitting diodes (LEDs). Mobile devices incorporate three LCD display types: twisted nematic (TN), vertical alignment (VA), and in-plane switching (IPS). Table 1.2-1 compares these display types for performance and quality.
TABLE 1.2-1 LCD Displays on Mobile Devices

ADDITIONAL RESOURCES For some additional information on the different LCD types, read the article “Monitor Panel Types | TN, IPS, VA Pros and Cons Explained – Pick the Right Display Technology!” by Dusan Stanar at the VSS Monitoring website (https://www.vssmonitoring.com/monitor-panel-types/).

EXAM TIP Know the differences between the IPS, TN, and VA LCD technologies.
LED
An LED display on a mobile device uses light-emitting diodes (LEDs) to construct and show images, typically on a flat-screen display. An LED display provides a bright color image with higher efficiency that other types of monitors, including an LCD. In fact, an LED display consumes as much as 50 percent less power than an LCD, which is important to the life of the battery in a mobile device.
An LED is a type of semiconductor that emits light when electricity is passed through it. An LED contains red, green, and blue sub-pixels that can blend to produce a particular color or shade. There are four primary types of LED displays:
• Edge-lit LED This is actually an LCD monitor that has LEDs along the edges of the display that shine light toward the center of the display to light an image. The LEDs enable the displayed image to be viewed from several angles.
• Full-array LED As its name implies, a full-array LED display has LEDs throughout the display area to produce sharp images and finer dimming. This type of display is popular on gaming and video streaming systems.
• Direct-lit LED This type of LED display places LEDs in rows, which limits its capability to produce true colors, including black. Its images are in gray tones only.
• Organic LED (OLED) OLEDs provide a superior display quality without separate backlighting. OLEDs illuminate pixels using negatively and positively charged ions. The three other forms of LEDs, and LCDs as well, use backlighting to sharpen their images, but OLED pixels provide all the light needed.
Display Panel Components
The display panel of a mobile device, especially laptops and notebook PCs, typically contains more than just the display. The display panel typically also houses the Wi-Fi antenna and the onboard webcam and microphone. There is a difference between a display panel, which is essentially the “lid” of the mobile PC, and the display assembly, which is only the display itself and its connecting wires and components.
Because the same panel can work in a wide variety of laptop models, finding a compatible display panel is easier than finding a compatible display assembly, and purchasing only a panel is less expensive than purchasing an assembly. In a few cases, it might be possible to switch screen types (from matte to glossy, for example). When swapping the panel only, take particular care to note the placement of component wires and how they are routed around the panel.
The following sections cover the system components commonly included in a display panel.

EXAM TIP Expect a question or two on the A+ 220-1101 exam involving a typical scenario that requires the replacement of the screen or components in the screen (for example, a cracked display panel, digitizer/touchscreen failure, Wi-Fi antenna malfunction, and so on).
Wi-Fi Antenna Connector/Placement
A broken mobile device display can be serviced in one of two ways: replace the entire display assembly or swap the display panel only.

NOTE CompTIA’s specific language for the antenna is Wi-Fi antenna connector/placement (although the industry-standard term is Wi-Fi). This refers to the wireless antenna wires that run along the top and sides of the screen assembly and connect to the Wi-Fi card.
When you’re swapping a display assembly, it’s important to note how the Wi-Fi antenna wires are connected to the wireless card. Even if you are only swapping a panel, you might need to move the wires out of the way. When you find it necessary to move them, it’s important to properly position the Wi-Fi antenna wires around the panel and reconnect them to the wireless card. If they are pinched or broken, the laptop’s Wi-Fi will stop working.
Figure 1.2-1 illustrates the position of Wi-Fi antenna wires and other components in a typical laptop display assembly.
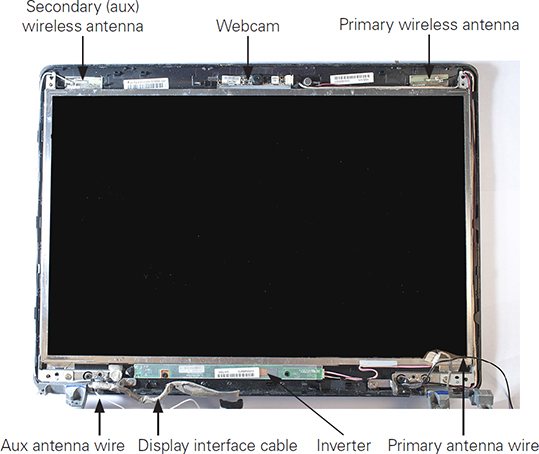
FIGURE 1.2-1 Wi-Fi antennas and other components in a typical laptop display panel
Camera/Webcam
The camera/webcam (refer to Figure 1.2-1) is also built into the display assembly. The webcam can be replaced if it stops working. However, it’s usually easier to replace a failed webcam with a USB version. If you decide to replace the webcam, be sure to note how it is attached to the display assembly and connected to the system board.
Microphone
Some laptops include a microphone in the screen assembly, while others place the microphone in the base of the laptop. If the laptop has a microphone in the screen assembly, be sure to disconnect it before swapping the screen assembly and be sure to reconnect it during the replacement process.
Inverter
Laptops that use older LCD screens with cold cathode fluorescent lamp (CCFL) backlighting require an inverter to convert DC power to AC power to control the backlight (refer to Figure 1.2-1). If the inverter fails, the screen will be extremely dim (use a flashlight to see if the screen still works). Replacing an inverter is a relatively easy and inexpensive repair to make because it is accessed from the bottom of the display assembly and is a plug-in component.
Touchscreen/Digitizer
Older laptops often used a separate touchscreen/digitizer layer, making repairs both expensive and more complicated. (A digitizer is the component that provides the “touch” part of a touchscreen. The digitizer’s fine grid of sensors under the glass detects your finger’s touch and signals to the OS its location on the grid.) Recent touchscreen laptops typically use display panels with integrated touchscreens, making the process of swapping the panel easier.
REVIEW
Objective 1.2: Compare and contrast the display components of mobile devices A typical laptop display assembly includes the following:
• LCD panel (standard) or OLED panel (only very recent laptops)
• LCD has a fluorescent or LED backlight.
• OLED has no backlight.
• Wi-Fi antenna wires
• Camera/webcam
• Microphone (might be built into the base on some models)
• Inverter, but only on older LCD screens with fluorescent backlights
• Touchscreen/digitizer (might be a separate display panel layer on older models)
• LCD technologies, including IPS, TN, and VA
1.2 QUESTIONS
1. Your client has a cracked laptop screen, but the laptop still works. Which of the following might be the most cost-effective solution?
A. Replace the display panel.
B. Replace the display assembly.
C. Replace the laptop.
D. Replace the laptop with a desktop.
2. Your client decided to have a laptop display assembly swapped. Now, the Wi-Fi connection doesn’t work. Which of the following is the most likely cause?
A. The webcam was plugged into the wireless card.
B. The Wi-Fi card was not reconnected to the wireless antennas.
C. The new assembly is not compatible with the current wireless card.
D. Wi-Fi wires were broken during the swap.
3. A user reports that an older laptop isn’t displaying anything. However, when you plug in an external display, the laptop can be used. Which of the following would you check first?
A. Digitizer
B. Microphone
C. Inverter
D. Wi-Fi antennas
4. The wireless antennas in a laptop display assembly are usually located where?
A. Lower-left and lower-right corners of the display
B. Bottom center of the display
C. Top center of the display
D. Top-left and top-right corners of the display
5. Your client uses a laptop for live chats with her salesforce, but her webcam has failed. The weekly chat is in two hours. What should you do?
A. Arrange for an express swap of her display assembly.
B. Connect a USB webcam.
C. Reimage a spare laptop.
D. Advise her to cancel the chat.
1.2 ANSWERS
1. A Replace the display panel. The other components in the display assembly are working, so replacing only the panel is likely to be cheaper and probably faster than swapping the entire display assembly.
2. B The Wi-Fi card is in the laptop base, so the wireless antenna wires must be disconnected to swap a display assembly. It’s easy to forget to reattach them.
3. C Check the inverter (on older laptops so equipped). When it fails, the built-in display becomes extremely dim.
4. D The antennas usually are located in the upper-left and upper-right corners of the display assembly.
5. B A USB webcam will work fine, may have better image quality than the built-in webcam, and can be installed and configured in plenty of time for the meeting.
 Given a scenario, set up and configure accessories and ports of mobile devices
Given a scenario, set up and configure accessories and ports of mobile devices
Mobile devices are small and portable, but thanks to a variety of wired and wireless connections, they can also be versatile. In this objective you are introduced to the main types of accessories available for mobile devices and the ways in which they can be connected.
Connection Methods
Mobile devices have many of the same types of connections and options as desktop devices do. These include wired ports, wireless devices, and accessories. Wired connections can be used for data synchronization and transfer to a larger computer, for charging, and for tethering to share a cellular connection. You need to be able to identify several wired connection types for the CompTIA A+ 220-1101 exam.
Universal Serial Bus
The universal serial bus, which is most commonly referred to as USB, connects a wide variety of devices to other devices, such as printers, external storage devices, keyboards, mice, and other controllers. USB has replaced the standard serial and parallel interfaces for the most part. Like these interfaces, USB provides for data transmission but also supplies 5 volts (5V) of power through a standard connection and cable. This allows low-voltage devices (those needing 5V of power or less) to connect and operate without requiring additional external power sources. A single USB jack has the capability of supporting as many as 127 USB devices using a series of unpowered USB hubs. USB devices that need more than 5V of power can connect through a powered USB hub that connects directly to a power source.
Since their introduction in the mid-1990s, the USB standards have expanded to a variety of versions and connector configurations, often distinguished by their overall size and pin array. USB connectors are identified in a confusing overlap of types (aka generations and form factors) and versions that specify the cabling and transfer speeds, among other characteristics. Types and versions are commonly used interchangeably and in combination. However, simply put, USB types are denoted by letters (as in A, B, and C) and USB versions by numbers (such as 2, 3, and 4). The sections that follow explain the USB types and versions you should know for the A+ Core 1 exam.

NOTE USB standards advanced from the original USB 0.7 to the developing USB 4.0. Market acceptance, or the lack of it, drove the early developments, but the first version to gain acceptance was USB 1.1. USB versions 1.0 and 1.1 were later renamed as USB 2.0 LowSpeed and USB 2.0 FullSpeed, respectively.
There are three basic USB types or form factors:
• Type-A The original and likely most commonly used USB connector
• Type-B Smaller, squarish-shaped connector compatible with nearly all other USB types
• Type-C Asymmetric and slightly oval connector
Figure 1.3-1 shows each of these USB types.

FIGURE 1.3-1 The three basic USB connector types
USB-C
A USB-C cable, shown in the upcoming Figure 1.3-3, uses Type-C 24-pin connectors for transferring power of up to 100 watts and data as fast as 10 Gbps. These capabilities make the USB-C cable suitable for connecting video devices, such as monitors, transferring data between computers or phones, and charging any compatible devices. A standard USB-C cable has Type-C connectors at each end, but there are USB-C to USB-A converters that can be used for interfacing with USB Type-A ports. One of the better features of a USB-C/Type-C connector is that it is completely reversible and can be inserted into a plug with either side up.
Micro-USB
The micro-USB connector is the smallest of the USB types and has been commonly used for connecting and charging mobile devices, such as MP3 players, smartphones, cameras, and more. There are several varieties of micro-USB cables, each intended to connect a micro-USB device to another USB port, commonly of a different type and typically a USB 3.0 or Type-C connector. Figure 1.3-2 and Figure 1.3-3 show examples of this cable.

FIGURE 1.3-2 A micro-USB cable with a USB 3.0 connector

FIGURE 1.3-3 From left to right: USB-C, micro-USB, and Lightning cables
There are a variety of micro-USB cables, each having a different USB type connector on the other end of the cable. Commonly used micro-USB cables are the micro-USB to Type-A, micro-USB to Type-B, and the USB 3.0.
Mini-USB
The mini-USB is essentially a sub-family of USB cables that includes versions with Type-A, Type-B, and hybrid Type-AB connectors. The most commonly used mini-USB connector is the 5-pin Type-B, which is popular in card readers, MP3 players, digital cameras, and many mobile PC storage devices. All mini-USB interfaces are sealed and essentially waterproof and dustproof. However, because they are smaller in size than other USB types, which is both a plus and a disadvantage, they are easily misplaced and can be difficult to remove from a device.
Lightning Connector
The Lightning connector was introduced in 2012 along with the iPhone 5 and several other Apple products for use in charging and synchronizing its devices. Apple continues to use the Lightning connector for its iPhones but has switched some devices to the USB-C interface. An example of a Lightning cable is shown in Figure 1.3-3.
Lightning is an 8-pin digital signal connector that can be attached to a device with dual-orientation, meaning no up or down sides. Each of the pins is connected directly to the reverse side pin in its position.
Cross-Reference
To learn more about these cables, their features, and how they are used, see Domain 3.0, Objective 3.1.
Serial Interfaces
The A+ Core 1 exam objectives indicate that you may encounter serial interfaces on the 220-1101 exam. So, let’s take a quick look at this topic.
At one time, the peripheral devices on a PC were connected primarily as either a serial or a parallel interface. Simply defined, a serial interface sends or receives data one bit at a time in a series or in what is known as a temporal (time) format. In comparison, a parallel interface transmits data on a set of parallel carriers, usually wires, as a spatial group. Here’s the short version: serial is one bit at a time on one wire and parallel is more than one bit at a time and more than one wire. Serial interfaces are used by USB and Serial Attached SCSI (SAS) devices.
Near-Field Communication
Near-field communication (NFC) uses chips embedded in mobile devices that create electromagnetic fields when these devices are close to each other or touching each other (typical ranges are anywhere from a few centimeters to only a few inches). The fields can be used to exchange contact information, small files, and even payment transactions through stored credit cards using systems like Apple Pay and Google Pay.
The OS determines the exact features of a smartphone. For example, Apple supports NFC only for Apple Pay, while Android smartphones also support file transfer.
Bluetooth
Bluetooth is a short-range wireless technology that can be used for personal area networking, connections to wireless speakers, mice, and keyboard devices, as well as connections to headsets, microphones, and wearables. Bluetooth implementations in mobile devices generally have a range of no more than 10 meters (about 33 feet).
Hotspot
Many smartphones and tablets with cellular support can share their cellular Internet connection with other devices by enabling a hotspot. The hotspot feature turns the device into a wireless router with an SSID (service set identifier) and password. When the hotspot device shares that information with Wi-Fi-enabled devices, those devices can connect to the Internet. The range of a hotspot connection varies according to the Wi-Fi standard used by the smartphone and the location (outdoors has a longer range than indoors).

EXAM TIP Be able differentiate the wireless connection types, including NFC, Bluetooth, and hotspot.
Accessories
Although mobile devices have many built-in features, they can use accessories to provide even more functionality. The following sections describe the accessories you need to understand for this objective.
Touch Pens
Also known as a stylus, a touch pen is a handheld pointing device that can be used on capacitive touchscreens. Touch pens can be used on smartphones, tablets, and other devices with touchscreen displays. A touch pen works much like your finger in that it absorbs the electricity of the touchscreen and identifies a specific location on the display.
Headsets
Headsets can connect to mobile devices via traditional 3.5-mm mini-jacks, USB, or wirelessly via Bluetooth. Headsets designed for use with smartphones or gaming include microphones.
Speakers
Mobile devices often have very small speakers with limited power. To increase volume and make it easier for groups to hear music, connect external speakers via 3.5-mm speaker jacks or wirelessly via Bluetooth.
Webcams
A webcam is a small digital camera that can be connected to a computer to capture video images in real time. Like any digital camera, a webcam captures images using a matrix of light detectors in a light-sensing chip, which is either a charge-coupled device (CCD) or a CMOS image sensor (the most common these days). The name “webcam” refers more to its software that formats the video for the Web.
Docking Station
Business-oriented laptops can connect (Transformers style) with docking stations that provide a host of single- and multi-function ports. The typical docking station uses a proprietary connection but adds ports or devices not available on the original laptop, such as a network port, optical drive, and so on (see Figure 1.3-4, top device).

FIGURE 1.3-4 Port replicator (bottom) versus docking station (top)
Port Replicator
A port replicator provides a permanent home for video, network, and audio cables that you would otherwise attach to and detach from a laptop as you move it around. Port replicators typically connect to the highest-bandwidth port (such as USB 3.0, 3.1, 3.2 and USB-C or Thunderbolt) and subdivide the bandwidth among port devices. Figure 1.3-4 shows a typical port replicator for a MacBook Pro or Air compared with a docking station for a Microsoft Surface Pro.

EXAM TIP The difference between port replicators and docking stations is sometimes unclear. For purposes of the CompTIA A+ 220-1101 exam, a docking station connects to a proprietary port, whereas a port replicator connects via a standard port. The Microsoft Surface Dock shown in Figure 1.3-4 is a true docking station because it plugs into the proprietary charging/docking port on the Surface Pro and adds a network port. The third-party port replicator for macOS-based laptops connects to a Thunderbolt port on a MacBook, MacBook Air, or MacBook Pro.
Trackpads and Drawing Pads
A trackpad is a user interface device that senses downward pressure and movement that is converted into cursor or pointer locations and movements. Also known as a touchpad, a trackpad is included in many laptop computers as an alternative to an external mouse. Trackpads and drawing pads, which are typically used with a stylus, work much like touchscreens and touch pens in that the touch device grounds the pad and its location is passed to the computer to move a visible cursor.
REVIEW
Objective 1.3: Given a scenario, set up and configure accessories and ports of mobile devices Mobile devices feature various types of connections and accessories, including the following:
• Universal serial bus (USB), including USB-C, micro-USB, and mini-USB
• Lightning
• Serial interfaces
• Near-field communication (NFC)
• Bluetooth
• Hotspots
• Touch pens
• Headsets
• Speakers
• Webcams
• Docking stations use a proprietary connection but add ports or devices not available on the original laptop, such as a network port and optical drive.
• Port replicators provide a permanent home for video, network, and audio cables that you would otherwise attach to and detach from a laptop as you move it around.
• Trackpads/drawing pads are typically used with a stylus and work much like touchscreens and touch pens in that the touch device grounds the pad and its location is passed to the computer to move a visible cursor.
1.3 QUESTIONS
1. Which of the following is not a wired connection type found on many mobile devices?
A. Micro-USB
B. Mini-USB
C. USB-C
D. NFC
2. Bluetooth can be used for which of the following accessories? (Choose all that apply.)
A. Headset
B. Battery pack
C. Game pad
D. Speaker
3. Your supervisor asks you about using a smartphone to make a payment at a convenience store. Which feature needs to be activated?
A. USB
B. Tethering
C. NFC
D. Hotspot
4. Your client has just purchased a new model iPad Pro. Which type of charge/sync cable does she need to use?
A. Lightning
B. USB-C
C. Thunderbolt
D. 30-pin
5. You’re prevented from connecting your laptop computer to a video display because the laptop lacks an HDMI port. Which of the following devices could be used to solve this problem?
A. Lightning cable
B. USB-C hub
C. Port replicator
D. Serial cable
1.3 ANSWERS
1. D An NFC connection is a type of wireless interface. The other answers are common types of wired connectors into which a matching cable can be inserted.
2. A C D Bluetooth cannot be used for battery charging but works with Bluetooth-equipped speakers, headsets, game pads, and other input/output devices.
3. C Near-field communication (NFC) can be used for cardless payment at convenience stores.
4. B The newest iPad Pro models have switched from Lightning to USB-C.
5. C A port replicator or docking station may supply the missing HDMI port.
 Given a scenario, configure basic mobile-device network connectivity and application support
Given a scenario, configure basic mobile-device network connectivity and application support
In this objective, you learn how to configure mobile devices, including cellular and wireless devices, for e-mail and other mobile applications.
Wireless/Cellular Data Network (Enable/Disable)
The majority of today’s mobile devices are able to connect to two different communication technologies to access a network, including the Internet: cellular (cell phone) and wireless (Wi-Fi) networks. Only recently has either of these mediums been a viable means of connecting to a network from a mobile device.
Mobile Device Communication
Cellular networks became a usable way to connect to a network, and especially to the Internet, with the introduction of the fourth-generation (4G) long-term evolution (LTE) cellular technologies. The emerging 5G standard will improve the performance of cellular-based network access and provide the technology to support a merger of cellular networking with Wi-Fi standards.
A Wi-Fi network connection applies the IEEE 802.11 standard that is appropriate and compatible with the wireless communication technology of the particular mobile device. Wi-Fi communications are over the air radio frequency (RF) communications.
Cross-Reference
For more information on the IEEE 802.11 wireless networking standards, see Domain 2.0, Objective 2.3.
Regardless of the technology used to access a network from a mobile device, this capability likely needs to be configured and enabled (or disabled, if so desired). Generally, these actions are performed in the Settings or Preferences page of a system, using roughly the same steps.
By default, cellular-enabled devices, such as smartphones and some tablets, are enabled for communication to cellular data networks. However, on non-cellular (that is, Wi-Fi) devices such as laptops, notebooks, and some tablets, these connections must be configured and enabled manually.
Mobile devices such as laptops, notebooks, and some tablets running a full operating system, such as Windows, macOS, or Linux, have defined methods for configuring and enabling a connection to one or both of the communication mediums. Tablets, personal digital assistants (PDAs), and smartphones that are running a specialized version of Windows or macOS, or a version of Android or IOS, use a process that is particular to that system to enable or disable network communications over either technology.

EXAM TIP For the A+ Core 1 exam, you should know the general process involved to enable, share, and disable access to a network over a cellular or Wi-Fi network on a mobile device.
Enabling/Disabling Cellular Communication
Smartphones and cellular-based tablets, by default, have a Subscriber Identification Module (SIM) card or an embedded SIM (eSIM) that permits the device to connect and communicate with a specific cellular network service such as LTE or broadband. Some laptops and tables may have an eSIM, but for the most part, these devices must connect to a cellular service though a USB cellular modem (see Figure 1.4-1) or a cellular router device. Cellular modems commonly have their own specific configurations that are typically set by default.

FIGURE 1.4-1 A USB cellular modem with a SIM card adapter
The process used on a Windows laptop to configure and enable a connection to the Internet using a cellular network involves the following steps:
1. Insert the SIM card into its holder, slot, or USB modem. Without a SIM or eSIM, cellular communications cannot be configured.
2. Access the Start menu and click the gear wheel icon on the left edge of the window to open Settings.
3. On the Setting menu page, click the Network & Internet selection.
4. On the Network and Internet page, select Cellular from the left-hand panel and do the following:
a. In the Data Roaming Options drop-down menu on the right-side of the page, select either Don’t Roam (which is the default selection) or Roam.

NOTE The preceding action sets a value for the InternetAlwaysOn DWORD of the HKEY_LOCAL_MACHINESOFTWAREMicrosoftWwanSvcRoamingPolicyForPhone key.
b. Close Settings.

ADDITIONAL RESOURCES For information on a few other options for using a cellular connection on a Windows 10 or 11 system, visit https://support.microsoft.com/en-us/windows/cellular-settings-in-windows-905568ff-7f31-3013-efc7-3f396ac92cd7.
Enabling/Disabling Wi-Fi Communication
On a Windows 10 system, the steps used to access the settings to enable or disable Wi-Fi are found by choosing Settings | Network & Internet | Wi-Fi. On the Wi-Fi page, this service can be set on (enabled) or off (disabled) using a slide switch, as shown in Figure 1.4-2. (This figure also shows the other connection options available. If a cellular service is available, it would also be listed.) On handheld mobile devices, you should refer to the user’s manual for how to enable or disable Wi-Fi services.
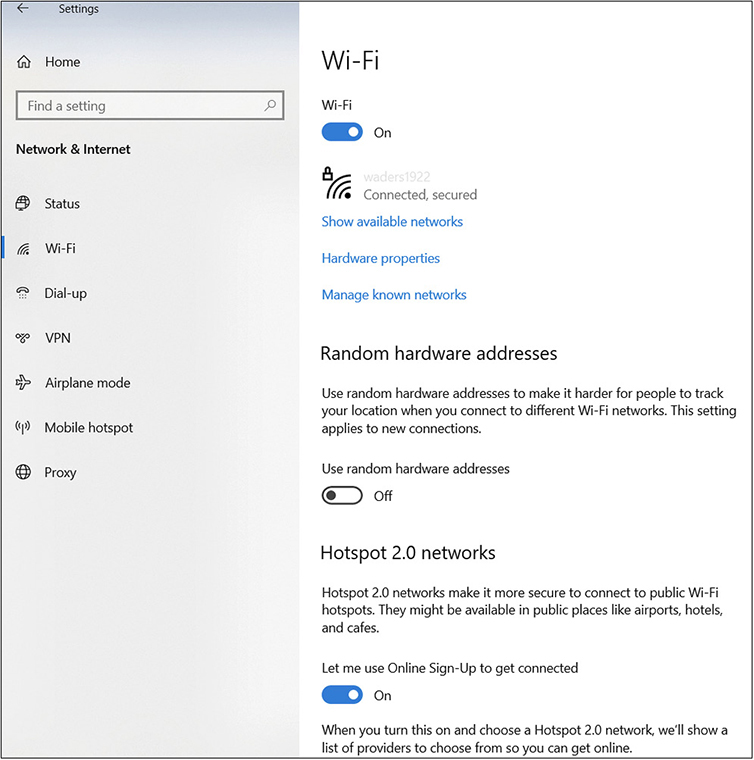
FIGURE 1.4-2 The Network & Internet settings page on a Windows 10 system
Making a Wi-Fi connection on a smartphone or tablet is essentially the same as the process used on a laptop. The settings involved are relatively intuitive: on an iPhone they are under Wi-Fi, and on an Android device they are under Wireless and Networks. Much like with other mobile devices, the Wi-Fi networks within range are listed and you can select one to connect with temporarily or configure one as the default Wi-Fi network.
Wireless Generations
To date, there have been five major “generations” of wireless and cellular communications. Figure 1.4-3 illustrates the path of the generations. Each generation provided important improvements in the technologies and capabilities of wireless telecommunications. Here is a brief summary of each of the generations:
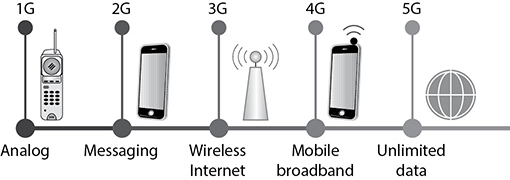
FIGURE 1.4-3 Each of the five generations in telecommunications introduced major developments in mobile and cellular communications.
• The first generation (1G) cellular network provided narrow band analog service with a very limited number of simultaneous callers.
• The second generation (2G) introduced digital transmissions on wider frequency bands with greater mobility. 2G introduced digital encryption of conversations.
• The third generation (3G) added several security features, transmission types, global roaming, and data transmission speeds, which are in the range of 144 Kbps to a theoretical 2 Mbps. 3G provided features that included video conferencing, instant messaging, and cellular VoIP. 3G provided for two-way authentication between a phone and a network.
• The fourth generation (4G) uses an IP-based system and higher transmission rates. 4G provides data speeds of 50 Mbps to 80 Mbps (LTE+) to a maximum distance of 31 miles (endpoint device to tower). 4G provides security features such as secured data in transit, authenticated access, and support for 3DES and AES encryption.
• The fifth-generation (5G) telecommunications standards define a radio access technology (RAT) separated into two frequency ranges: Frequency range 1 (FR1) supports the sub-6 GHz bands of the earlier standards and the 410 MHz to 7.125 GHz spectrum. Frequency range 2 (FR2) supports the range 24.25 GHz to 52.6 GHz. 5G, which is built on the 4G LTE standard, provides data speeds of multiple Gbps or more.
Hotspot
A mobile hotspot device creates a Wi-Fi network to share its cellular data connection (3G, 4G, 4G LTE, or 5G) with other Wi-Fi devices. Wireless providers sell standalone hotspot devices for their network, but many smartphones and tablets with cellular access can be configured to act as a hotspot. As illustrated in Figure 1.4-4, enabling a smartphone (in this case, an Android smartphone) involves enabling a cellular data connection and toggling the hotspot setting. The hotspot configuration enables the device to interact with the Wi-Fi network and serve as a router between it and the cellular network. You should also configure a password to limit access to the hotspot.
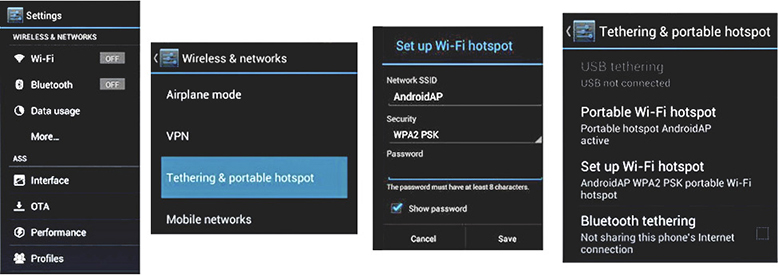
FIGURE 1.4-4 The sequence of screens (left to right) and selections for configuring an Android phone as a Wi-Fi hotspot

NOTE Some devices use the term tethering as a synonym for hotspot.
GSM vs. CDMA
The two primary service protocols used for cellular phone systems are Global System for Mobile Communications (GSM) and code division multiple access (CDMA). GSM is the generally deployed standard and is replacing CDMA slowly, but there are still CDMA networks deployed. Both of these network standards provide about the same features and capabilities, but their major difference is their portability. A GSM SIM card can be removed and installed into a new device with the same provider or that of another provider. CDMA devices are tied to a provider and must remain so.
Preferred Roaming List Updates
As mobile devices travel, they frequently have to pass through areas that don’t have strong signals, or into areas that the carrier does not service, and maintain connection by roaming on another carrier’s network. Your phone’s firmware gets occasional updates to its preferred roaming list (PRL), a priority-ordered list of other carrier networks and frequencies, sent via your phone’s cellular connection (called baseband updates, or over-the-air updates) or through normal OS updates. Updates to the PRL are also sent to cell towers. As the PRL is updated, devices can roam further from their own providers’ coverage area.
CDMA devices may also receive product release instruction (PRI) updates that modify a host of complex device settings. Don’t worry about specifics, here—but a device may need PRI updates if the network is evolving during the lifetime of the device, the device is moving to a new network, or the device has a new owner.

EXAM TIP PRL updates are handled automatically during firmware/OS updates. They are only for CDMA networks. No one but the nerdiest of nerds will ever see these updates.
Bluetooth
As discussed in the previous objective, Bluetooth is a popular way to connect many different types of accessories. Table 1.4-1 covers the process of using Bluetooth on a mobile device.
TABLE 1.4-1 Bluetooth Setup Process
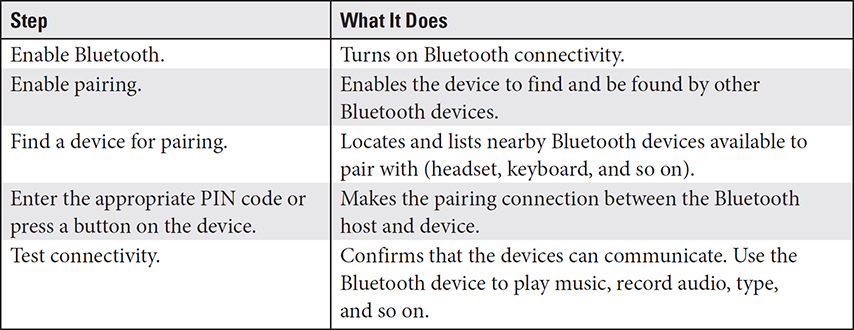

EXAM TIP Given a scenario, know the setup process for Bluetooth pairing.
Two or more paired Bluetooth devices create a personal area network (PAN). Figure 1.4-5 illustrates a very simple PAN, in which each device is paired with other devices in range to create a network. Another Bluetooth network topology is a scatternet, which combines two PANs by connecting a device from either side to link the PANs. Figure 1.4-6 illustrates a simple scatternet.
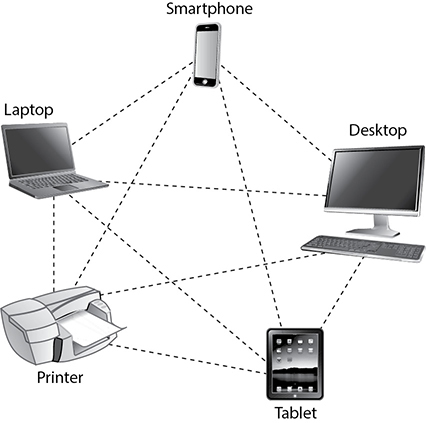
FIGURE 1.4-5 A Bluetooth personal area network (PAN)
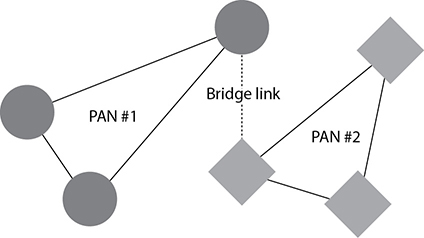
FIGURE 1.4-6 A Bluetooth scatternet connects two or more PANs.
Cellular Location Services
Cellular location services use real-time location tracking to identify a mobile device’s physical and geographical locations. This technology tracks your location constantly, not just at one particular moment. A mobile device commonly includes one or more technologies able to determine its current location. In most cases, these technologies are GPS, radio frequency ID (RFID), Wi-Fi, and cellular RF technology. In order to function, a mobile device uses one or more of these technologies to interact with other devices, which may include geopositioned satellites, network routers, and cell and communication towers. This interaction, which involves a mobile device communicating with one of the multiple types of communication hubs, is used to nail down a device’s precise location. This feature, known as Location Services in iOS and Location in Android, is used by mapping and several other types of apps, but only you provide the apps with permission to use this feature.
Most cellular systems use a triangulation method to determine the general location of a trackable device. As shown in Figure 1.4-7, the distance to each of three (and possibly more) cellular service towers can cause the transmitted signal strength to weaken. The degree to which the signal does weaken is used to determine the distance to the tower. The distance calculations for each tower are combined to locate the device.
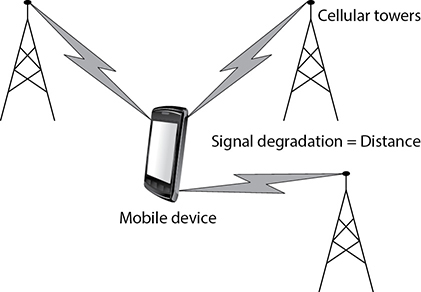
FIGURE 1.4-7 A process called triangulation is used to determine the location of a device.
There are many pros and cons to enabling location services on a cellular or mobile device. Enabling location services can provide a route-finder application with a starting point and the capability of tracking progress. In an emergency, first responders are able to pinpoint the phone’s exact location. You can also let selected friends see your location on their smartphones. There are many other possibilities with location services turned on.
On the other hand, it may not always be safe to broadcast your location. You can’t be sure exactly who may be receiving that information. Knowing where you are could lead to stalking or robbery. And knowing where you aren’t could lead to someone breaking into your home. It’s debated whether the police or a government agency knowing and tracking your location, without a warrant to do so, could be a violation of your civil rights.
Disabling location services on a mobile device won’t completely mask its location. Several applications, and even phone calls, connect to the nearest cell tower, which has a location. Perhaps the only way you can hide your personal location is to not have the device with you. Much of the sharing of a mobile device’s location is done by misconfigured application permissions and settings. Being aware of which apps use location services and carefully assigning their permissions can reduce the chance of location services being used for bad.

ADDITIONAL RESOURCES To learn more about location-based services, read the article “What are location-based services?” at the Ancoris website (https://www.ancoris.com/blog/what-are-location-based-services).
GPS
One of the primary technologies used by location-based services is the Global Positioning System (GPS), which is built into most mobile devices, along with Bluetooth, Wi-Fi hotspots, and cellular towers, to determine the device’s location.
GPS is based on 24 satellites that transmit their location and time to Earth-based GPS receivers. The most common purpose-built GPS device is the navigational aid that mounts on a vehicle’s dashboard or windshield, and you can buy the equivalent for boats, airplanes, bicycles, and more. There are even handheld versions tailored to scuba diving, hiking, hunting, and so on, with features better suited to their niche, such as preloaded special-purpose maps, waterproofing, impact resistance, route memory, bookmarking, stored locations, low-power use, simple replaceable batteries, and other useful sensors or tools. Figure 1.4-8 illustrates a simplified version of GPS integrated into a communications system.
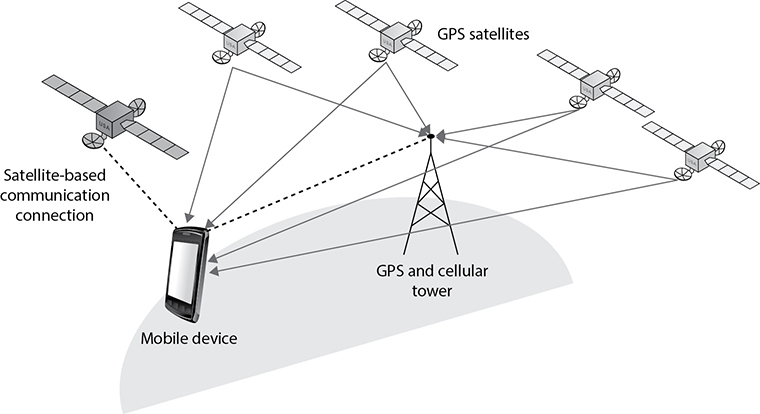
FIGURE 1.4-8 An example of a GPS network
Securing Mobile Devices
Mobile device management (MDM) is a type of security software that enables organizations to secure, monitor, manage, and enforce policies on employees’ mobile devices. MDM is often linked with or based on the use of mobile application management (MAM) software.
Mobile Device Management
MDM involves the use of monitoring, securing, and managing any mobile devices that have access, gain access, or connect to a company’s network and data resources. Employees and possibly customers or suppliers may be allowed to directly connect mobile devices on an internal network. Their activity must be tracked to protect the data asset by applying a carefully thought-out data management program. The purpose of the MDM is to provide the internal IT administrators with the information needed to manage and administer the security of a network. MDM solutions allow IT teams and admins to control and distribute security policies to the mobile devices.
Mobile Application Management
MAM encompasses the entire software development life cycle (SDLC) process for mobile software developed internally or externally, as well as updates, fixes, and retirement of mobile software. MAM can also include the management of application licenses, user account access permissions, and the operating configuration of mobile software. Here are some examples of how MAM is applied:
• Corporate e-mail configuration A corporate or even a small business e-mail system must be configured and fine-tuned to provide e-mail services to mobile devices. Commonly this may also be accomplished through the configuration on the mobile device itself. The information commonly used includes account type, e-mail address, password, logical domain, and the user’s account name.
• Two-factor authentication Unfortunately, shoulder surfing and phishing are often successful in learning a user’s login credentials. The use of a two-factor authentication (2FA) process at login helps to ensure that a mail client is who they claim to be. In a 2FA scheme, the user’s account name and password count only as one factor. A second security factor is commonly a phone number, a PIN code, or a generated code sent to the supplicant’s device.

EXAM TIP Be sure you understand the concept and use of two-factor (multifactor) authentication and the use of biometrics as a part of the MAM process.
• Corporate applications The management of application software on a mobile device is very much like the management of software on an internal network. For example, if a corporation has a customer relationship management (CRM) system, whether the user is local and using a device on the internal network or is remote and several thousand miles away, the client/server nature of the application must be the focus for its confidentiality, integrity, and availability.

EXAM TIP Know the differences between MDM and MAM. MDM concentrates on centrally managing device updates and securing mobile devices, whereas MAM focuses on specific corporate applications.
Mobile Device Synchronization
People generally want their contacts and calendars to match across their devices, so for the CompTIA A+ 220-1101 exam, you need to know how to configure mobile devices to synchronize data across two or more devices to maintain a single set of contacts, one e-mail inbox, one calendar, and perhaps even one set of up-to-date files, folders, or directories. Whether you wish to synchronize a desktop with a mobile device or two, most personal productivity applications and suites now include support to synchronize, or sync, data.

EXAM TIP Be sure you understand the difference between the synchronization of data and files and performing a backup of the same.
Having the same data available on different mobile (and stationary) devices is the primary benefit of data synchronization. The requirements for this process are a data source, a target for the data, and an application to transfer and synchronize the data on both devices. A source device could be a mobile phone or a desktop computer, and the target device may be any mobile device or desktop PC, or any other combination of devices, provided a synchronization application is available.
Data synchronization is important to anyone who relies on data stored on a mobile device to be just as accurate and timely as the same data stored on a base system. Data synchronization is a two-way street, meaning that the data source could very well be a mobile device, and the target device could be a user’s desktop computer, a cloud application, or even another mobile device.
Data synchronization processes are defined by their targets. The following briefly describes the three target categories.
• Synchronizing to a desktop Mobile devices can synchronize data by connecting to a laptop or desktop computer via USB, Wi-Fi, or Bluetooth. Another way that a mobile computing device can sync to a desktop is using OneDrive or Dropbox as an intermediary. However, this method may only work for data that isn’t updated frequently.
• Synchronizing to the cloud Cloud-based storage sites can be used to pass data between devices, especially when the devices might not be able to communicate directly. Cloud services like NetApp’s Cloud Sync, Apple’s iCloud, and Microsoft Azure AD Connect provide the capability to schedule backups, synchronization, and other data harmonization features.
• Synchronizing to an automobile The latest models of automobiles use synchronization to push firmware and software updates to systems in a vehicle, usually without the owner being involved or even knowing that it happens. The car may also provide data back to the manufacturer regarding the performance of certain onboard systems. Drivers may want to synchronize their smartphone to the sound system for hands-free use or to play music stored on the smartphone.
The types of data and information that can be synchronized between two devices includes just about everything: e-mail messages, calendars and contacts, applications, photos, audio files, video files, browser bookmarks, documents, e-books, and even passwords.
You should expect to encounter a question or perhaps just a reference to the synchronization processes of Microsoft 365, Google Workspace, and Apple iCloud application suites. The synchronization processes for these and other similar products are relatively the same, but the setup processes do vary. Since the primary resource that is synchronized to a mobile device relates to e-mail, the following are some examples of how each is set up.
Synchronize Apple iCloud to an Android Device
iCloud is an application in the Apple system environment. Before you can sync to it, you must establish an account. If you already have an @mac.com or @me.com e-mail account, you are set. If not, you must create one. After doing so, you can then set up synchronization.
On an Android device, perform the following steps:
1. Access the Apps menu and select Settings.
2. Choose Accounts and then Add An Account.
3. Select the appropriate Account Type and, if necessary, the Account Sub-Type.
4. Enter the e-mail address to be synchronized and its corresponding password and then tap Next to continue. You may be prompted for a username, password, or server. If so, provide this information.
5. Provide the SMTP server ID and the related port number and then tap Next.
6. You may be asked for some additional settings for this account, such as frequency, size, and the like. If so, enter this information and tap Next.
7. Assign a name to the account (it will be the name used for outgoing messages from the account). Select Next to create the account.
Synchronize Google Workspace to an Android or iOS Device
As in the previous example, in order to synchronize to a Google Workspace account, you must first have one. If you already have an @gmail.com account, you are good to go. Otherwise, you need to create one.
Next, sign in to the Gmail app:
• For an Android device, access the Gmail app and sign-in.
• For an iOS device:
1. Choose Settings | Accounts & Passwords | Add Account | Gmail.
2. Enter a name, address, and password and then click Next.
3. Re-enter the address and click Next.
4. Choose the items to be synced and click Done.
Synchronize Outlook (Exchange) to an Android or iOS Device
Before beginning to set up the synchronization, create a Microsoft account, if necessary, and install the Outlook for Android app on the Android device, if needed. Use the following steps to set up synchronization between Outlook and the device.
On the Android device:
1. Open the Email app and sign in.
2. Select Manually Setting and fill in the Domain/Username entry.
3. Enter the Exchange server password and choose the Use Secure Connection (SSL) option.
4. Set the frequency to be used for checking for updates in Accounts Options.
5. Give the account a name and tap Done.
On the iOS device:
1. Add the account using Settings | Accounts & Passwords | Add Account and indicate the account type being added.
2. Enter a name, e-mail address, e-mail password, and description, if desired, and tap Save.
Synchronize Outlook (Exchange) to an iOS Device
Before you begin to set up the synchronization, create a Microsoft account, if necessary. Use the following steps to set up synchronization between Outlook and the iOS device:
1. The first step is to identify the Outlook/Exchange account to iOS using Settings | Passwords & Accounts | Add Account | Exchange. Then enter the e-mail address to be synchronized.
1. Enter how you wish to connect to the Exchange server, choosing either Configure Manually or Sign In.
• Configure Manually requires that you set up an Exchange account using your e-mail account and its associated password, plus perhaps some other server-related information.
• Sign In requires only your e-mail address and password, which are transmitted to the Exchange server for validation and to retrieve account information. If multifactor authentication is in use, you will be asked for the additional authentication information.
3. Add the account using Settings | Accounts & Passwords | Add Account and indicate the account type being added.
4. Enter a name, e-mail address, e-mail password, and description, if desired, and then tap Save.
One huge caution, though: if you are synchronizing to or from a cell phone or smartphone, keep the data transfer capacity limit (data cap) in mind. Some files, and probably most files, are larger than you think and may result in additional charges for data transfers.
REVIEW
Objective 1.4: Given a scenario, configure basic mobile-device network connectivity and application support
• The five generations of cellular data networks and communication are 1G, 2G, 3G, 4G, and 5G.
• 1G offered narrow band analog service with a limited number of simultaneous callers.
• 2G provided wider frequency bands and greater mobility. 2G introduced digital encryption.
• 3G added security features, transmission types, global roaming, faster data transmission speeds, and two-way authentication.
• 4G uses IP-based system with data speeds of 50 Mbps to 80 Mbps over a maximum range of 31 miles. Also, it secures data in transit with 3DES and AES encryption, and access is authenticated.
• 5G defines a RAT that is separated into two frequency ranges: FR1 with sub-6 GHz bands, and FR2 built on the 4G LTE, which provides Gbps data speeds.
• A mobile hotspot device creates a Wi-Fi network that shares its data connection with other Wi-Fi devices. A hotspot is also called tethering.
• The primary service protocols for cellular phone systems are Global System for Mobile Communications (GSM) and code division multiple access (CDMA).
• GSM is the generally deployed standard and is replacing CDMA. A GSM SIM card can be removed and installed into a new device.
• CDMA devices are tied to a provider and must remain so.
• A preferred roaming list (PRL) contains networks and frequencies used by other carriers. CDMA devices may receive product release instruction (PRI) updates.
• Bluetooth setup includes the following steps: enable Bluetooth, enable pairing, locate a device for pairing, enter the PIN code, and test connectivity.
• Location services use GPS, RFID, Wi-Fi, or cellular RF technology to identify a device’s location.
• Mobile device management (MDM) is security software that enables organizations to secure, monitor, manage, and enforce policies on employees’ mobile devices.
• Mobile application management (MAM) is a methodology for mobile software development but can also cover operations of mobile software, including corporate e-mail configuration, two-factor authentication, and corporate applications on mobile devices.
• Data synchronization helps to ensure that the same data is available on different devices.
1.4 QUESTIONS
1. Which of the cellular technology generations added security features, transmission types, global roaming, and data transmission speeds of 144 Kbps to 2 Mbps?
A. 1G
B. 2G
C. 3G
D. 4G
E. 5G
2. What technology allows a SIM card to be removed and installed into a new device?
A. CDMA
B. GSM
C. TDMA
D. 5G
3. What feature is used by mapping and location-based apps on mobile devices?
A. Location Services
B. Maps
C. Find My
D. Tips
4. You are getting ready to try out a new Bluetooth headset for your smartphone. After you enable Bluetooth and turn on the headset, which of the following do you need to do to use the headset?
A. Tether the headset.
B. Connect to the hotspot on the phone.
C. Pair the headset with the phone.
D. Run a program.
5. What types of data can be synchronized between a PC and another device?
A. Only text-based data
B. Only e-mail
C. All data
D. No data
1.4 ANSWERS
1. C 3G added security features, transmission types, global roaming, faster data transmission speeds, and two-way authentication.
2. B GSM SIM cards are portable and can be removed from one device and inserted into another device, regardless of the service provider.
3. A Apple’s Location Services feature provides location information to mapping and location-based apps. (The same is true for Google’s Location feature.)
4. C You must pair a new Bluetooth device with your mobile device before you can use the new device.
5. C Virtually all types of data can be synchronized between two devices or between a source and a target.
