Responsibilities During an Incident
The IRT is the single point of contact during an incident. It provides management with information as to what has occurred and what actions are being taken. It serves as the repository for all related incident information. Keeping a repository to determine the root cause of the incident is an important team function.
During an incident, a core team is formed to respond to the threat. FIGURE 12-1 depicts a typical IRT core team. Not all members of the core team will be activated for every security event. Some security events are small and localized and thus need a smaller core team. Other events are major and impact the entire enterprise, requiring maximum effort by all core team members. At the time of a security event, the IRT manager determines which resources are needed to address the specific incident. Additionally, notice that upper management is not considered part of the core team. Instead, upper management is a consumer of the results of the core IRT. Upper management is, however, a critical decision maker in responding to an incident.
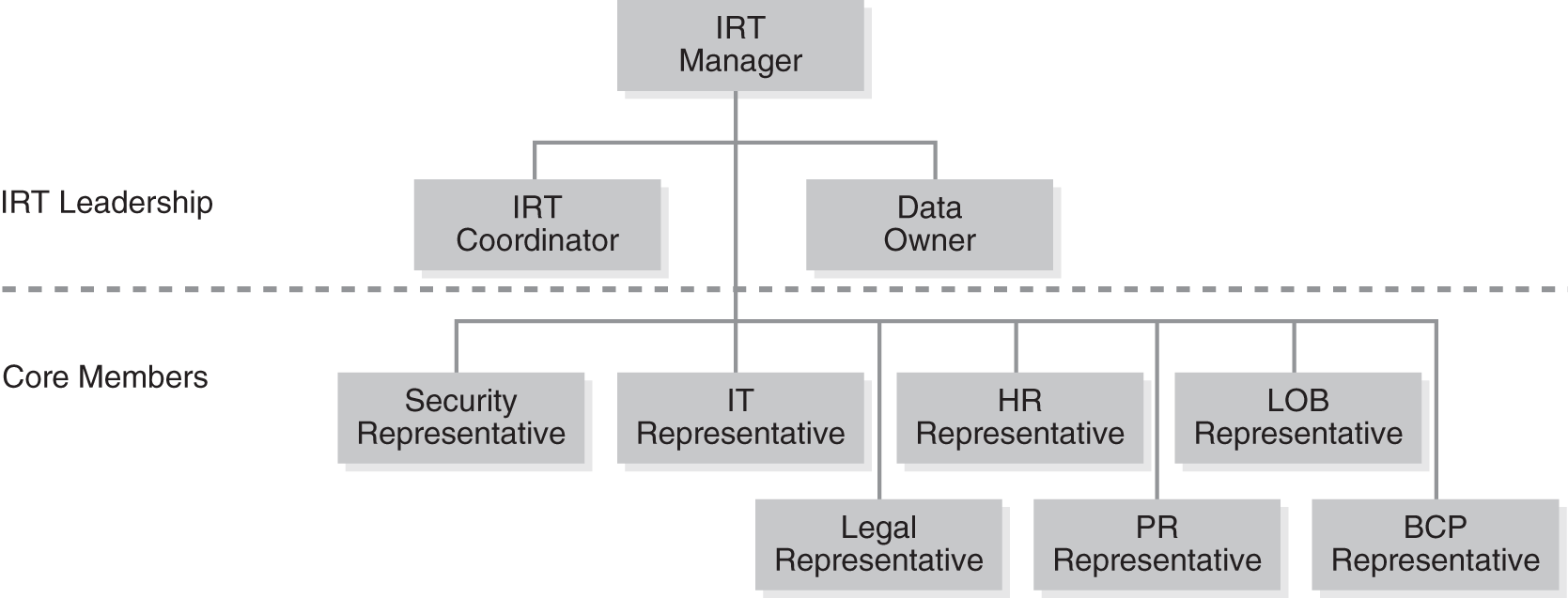
FIGURE 12-1 Core incident response team.
Users on the Front Line
It’s the responsibility of all users in an organization to support the efforts of the IRT. When the IRT responds to an incident, time is of the essence. It’s important that the users on the front line provide quick response to requests for information. Such requests may include preserving evidence. The users may be requested to document events and assist in gathering evidence.
The users on the front line also play an important role in detecting an incident. You increase the likelihood that incidents are detected early when an alert user reports suspicious activity.
System Administrators
The system administrator may be a core member of the IRT team. System administrators help analyze the threat and recommend immediate response. These individuals know the technology and technical infrastructure. They know how it’s been customized. They are in a good position to assist with the response.
System administrators have the authority to make critical changes to repel an attack. The term system administrator can mean system, application, and network administrator. These individuals have the skills to identify anomalies to the configuration and the ability to respond. For example, they can disconnect devices from the network.
System administrators would also be critical to recovery of the environment. Administrators typically perform reconstruction. This is an important task that often needs to be performed to resume operations.
Information Security Personnel
The information security team has several roles during an incident. Team members may be the first to recognize the security breach. This is because the security team monitors the environment for signs of security breaches, such as intrusion detection alerts. In addition, information security staff members understand the layers of security. They understand the points of potential breach.
The incident response process is typically designed and managed by information security personnel. Security personal are either directly or indirectly involved in most IRT activities. These activities include:
- Discovery
- IRT activation
- Containment
- Analysis and threat response
- Incident classification
- Forensics
- Clean-up and recovery
- Postevent activities
The information security team often provides management and oversight of an incident response. They are facilitators and subject matter experts on security and risk. As such, they may or may not be the individuals tasked with performing the activities listed. In some organizations, these functions are performed by information security personnel. The security team is often responsible only for ensuring the activity occurs. For example, forensic investigations demand a highly specialized skill set. They require significant training and special tools. Forensic investigations are often needed to find out what the root cause of the incident is, even if criminal charges are unlikely to be filed. However, if the attack can be traced to a specific attacker, failure to follow standard criminal procedures can render the evidence unusable. Many organizations do not have the skills and tools to do a forensic review. Some organizations have only basic capabilities. Information security personnel often arrange for a forensic review through an outside firm.
Security personnel also ensure reviews are conducted after an incident to ensure lessons are learned and adopted. The role information security personnel most often perform is writing the final incident report to management. This role makes sense because in their oversight role they see all the issues. They track the timeline of the event. They can see the big picture and combine all the incident issues into a single document.
Management
Management provides authority and support for the IRT’s efforts. When parts of the organization are not supporting or reacting quickly enough, it is management’s responsibility to remove barriers.
Management also makes key decisions on how to resolve the incident. It’s important to remember that the IRT recommends and management approves. If a purely technical decision needs to be made, the IRT operates independently. But a decision that significantly affects the business should be escalated to management, if possible. Management should empower the IRT with enough authority to take drastic action quickly when time is critical. One of the decisions to be made will be when to notify law enforcement, in the event of a cyberattack.
Support Services
This is a broad category that refers to any team that supports the organization’s IT and business processes. The help desk, for example, would be a support services team.
During an incident, the help desk may be in direct contact with customers who are being impacted by the attack. The help desk, at that point, becomes a channel of information on the incident. It’s vital that the help desk provide a script of key talking points during an incident. Such a script can be very short and only refer questions to another area. Or the script can give more detail with the intent of keeping the public informed. These scripts should be developed and distributed by the PR department.
 WARNING
WARNING
Absent effective communication to management during a security event, there’s a risk that various levels of leadership will take actions that make the impact of the breach worse or delay its recovery. The IRT manager must be proactive and have well-established channels of communication with management. This communication includes letting management know the status of the incident and what steps are being taken.
Other Key Roles
The IRT manager is the team lead. This individual makes all the final calls on how to respond to an incident. He or she is the interface with upper management. The IRT manager makes clear what decisions management needs to make. This person also advises management of the ramifications of not making a decision.
The IRT coordinator role is to keep track of all the activity during an incident. This person acts as the official scribe of the team. All activity flows through the IRT coordinator, who maintains the official records of the team. It’s a critical position because what is recorded becomes the basis for the reconstruction of the event to determine a long-term response.
