Human Nature in the Workplace
A successful security policy implementation depends on people understanding key concepts and embracing the material. Understanding and influencing different personalities in the workplace will be important to achieving that success. But it’s not just the needs of the internal employee you need to consider. A variety of stakeholders will have an interest in information security policies, including external parties such as vendors, customers, and regulators. As competition grows globally, new channels of sales and products appear. These factors are usually accompanied by a change in technologies. Enormous efforts and resources are spent to document, debug, and map an organization’s processes to these technologies. Over time, technology, frameworks, and standards evolve to become best practices. Success does not come by technology or process alone. Successful security policy implementation depends on the correct alignment of people, processes, and technology.
How much time and resources are placed on the people element? Too often, not enough.
This section explores human nature in the workplace. More precisely, it looks at different personality types and how they affect the adoption of security policies. A successful security policy implementation is defined in part when an employee understands the key concepts and can apply them broadly to situations that are not anticipated. Going beyond what one is told helps define a successful implementation of security policies.
One practical method of gaining support and educating staff is storytelling. At a previous position, this author would make a habit of sending out a brief story each month to the employees of that company. The story briefly told of a salacious security breach, then explained that this is why a given policy or policies were in place. The communication was both brief and interesting to employees. This proved to be an effective method for communication.
Basic Elements of Motivation
What is motivation? What makes a help desk employee work persistently to fix your problem? It’s being enthusiastic, energized, and engaged to achieve a goal or objective. A lack of motivation can be measured in poor customer service and doing the minimum to get by, with mediocre results.
There are several possible sources of motivation: pride, self-interest, fear, desire, and success. Some of these are appropriate for the workplace, others less so. Fear is not usually recommended. Clearly, there are consequences for failing to adhere to policies, but the primary motivation to follow policies should not be fear. Having employees take pride in their work and understand their own interest is served by policies, and employees’ desire to perform well in the workplace are positive methods of motivation and should be used.
Good leadership can motivate employees. Consider, for example, when information security policies are implemented effectively across all teams but one. A review of differences between the teams would be in order. Suppose that review indicates that all teams across the enterprise use the same technology and received the training, and that all other factors were the same, except that, of course, different teams have different leadership. Then the unsuccessful implementation could be attributed to lack of effective leadership.
An important first step is ensuring that leadership at all levels of the company values security. It begins, of course, at the top executive levels, but valuing security must permeate all levels of management, including midlevel and lower-level managers.
Pride
Pride is part of human nature. Individuals are more likely to become motivated when they are working on something that is important. If your work is discarded or trivialized, you’re less likely to put in a high-quality effort the next time. Conversely, if you understand the goals and objectives of the team and see how your individual efforts contribute, you will likely feel a sense of obligation. It also builds team pride and spirit, which are important for future successes.
An important component of pride involves an understanding of the overall goals and objectives. Management is responsible for informing employees of their roles and how their efforts contribute to the larger goal. This is where good leaders can motivate, and poor leaders can derail a good security policy. A manager’s comment, “You must do it because the security department says to” is a good indication of poor leadership. In this case, management may not embrace the policy, and more important, staff might perceive the policy as a burden. That perception can lead to the staff doing only the bare minimum. Conversely, a manager could approach the employees and outline the problem being solved. He or she might add their personal endorsement of the action taken. The manager could position the policy change as an opportunity to expand staff skills and to stress the importance of protecting the customer.
Pride can be a powerful motivator. It can also create competition and a sense of self-worth. Managers must control competition so that the sole measure of success is not simply completing the task first. Managers must also promote helping each other so the “team” can succeed. Measuring success needs to include all the values important to the organization, including quality of service, customer satisfaction, and teamwork.
In order to utilize pride as a motivating factor in security, it is important to accurately communicate the value of security to the entire organization. This begins with a realistic understanding of the threats. The entire organization needs to understand the dangers, so that they understand the countermeasures and the reasons for policies. Then employees can be motivated to excel at security. The security goals must be integrated with the business goals. For example, a sales team that is only evaluated on sales volume, without any concern for security, won’t take pride in exceeding security goals.
Self-Interest
Self-interest, and sometimes self-preservation, is also part of human nature. Humans tend to repeat behavior that is rewarded. Having well-defined goals and objectives for individuals helps them understand what they must achieve. Those who achieve these goals receive rewards. Those who exceed these goals typically receive bigger or better rewards. Those individuals are “high achievers” or high performers. High achievers receive promotions more often and are models for others to emulate. To promote the importance of information and adherence to information policies, you should gain the support of high performers.
In a declining economic market, there’s significant pressure on companies to cut jobs to save money. Employees who feel their jobs are at risk will not take chances. This could lead to individuals doing the minimum to stay out of trouble. Worse yet are individuals who feel they will be next to be let go. They may be angry and try to undermine management efforts. When an organization lays off employees, it’s often called a reduction in force. Generally, it’s not a good idea to implement significant policy changes during a force reduction.
Discipline also has an important self-preservation effect on our behavior. When an employee fails to perform, disciplinary action might be required. How management handles disciplinary actions either motivates or demotivates an employee. Unfortunately, discipline must be an element of security policy enforcement.
Everyone has strengths and weakness. Most people make mistakes, and at some point, they will do something foolish. One management approach is to look at an employee’s pattern of behavior more than at individual errors in judgment. This approach has its limits, as in a case of sexual harassment or fraud. Except for these extreme cases, though, when management accepts failures as part of individual and team growth, a culture of taking chances emerges. More important, this approach creates the trust that encourages employees to report policy failures and breakdowns. Not only the individual employee, but also the whole organization can learn from such failures. This experience is often referred to as “lessons learned.” Making it easier to record and track these lessons learned will allow the information security team to improve policies to prevent future problems.
 NOTE
NOTE
Disciplining employees can be risky if you don’t do it right. You need to make sure that you do not discipline different employees differently for the same policy violation. Your inconsistency could lead to a lawsuit or a claim of employment discrimination. Always work through your human resources department and strictly follow company procedures in disciplining employees.
Taking chances and going beyond what’s expected define high achievers and high-performance teams. Because security policies cannot define every event, their success depends on employees taking action by applying core principles to new situations. For example, you may have a clear policy and related process for setting up administrator accounts. Assume a vendor provides support for your organization. Assume it’s not unusual for the vendor to request to change access to devices they support. Historically, it requests access changes once or twice a year. Now let’s assume you receive a request from the vendor representative (in accordance with established processes) to remove all existing administrator accounts and replace them with new accounts. The request follows established processes.
However, those employees who understand the risks associated with administrator accounts and those who feel empowered might challenge the request and ask for additional authorization, even though additional approvers are not required by policy. And it might turn out that the vendor representative asking to make those highly unusual changes has just been fired or has just been the victim of some form of identity theft. In this scenario, the high-achieving employees who had the systems knowledge and the confidence to challenge the vendor rep could be what protect the organization.
Success
Wanting to be successful is part of human nature. Anyone who has played on a winning team knows the feeling. It’s simply a lot more fun being on the winning team than on the team that always comes in last. Even if you are a high performer, it’s hard to get motivated if your team as a whole keeps losing. It is no different in the workplace. Individuals build confidence when frequently recognized for their successes. These individuals quickly become highly motivated. Equally important, they can motivate others and support others to win. This is an essential element in creating a winning team. They can also afford to take chances and are more likely to build on their success by going beyond what’s required.
Success is measured as the perception of how well you perform your work. This can, in turn, be defined by how you work as part of the team, ethical behavior, and the perception of your customers. There are certainly other definitions of success that are more narrow. Whatever one’s definition, the desire for something we label as success seems universal.
You need to have some proficiency in soft skills to convince an organization to adopt security policies. Soft skills refer to certain social personality traits such as the ability to communicate and project optimism. Mastering these soft skills is essential to influencing others. This is particularly important when trying to sell new security policy and control concepts. More and more, business relies on the agility of its workforce to adapt to the unexpected. These skills are just as highly valued as technical knowledge. In other words, the “people” part of the equation is also critical to implementing security policies. Soft skills help turn people into high performers who apply their own knowledge effectively and draw out the best from others. Successful implementation of security policies over time will change individual attitudes. If that success continues throughout the organization, a culture that is more security and risk aware may emerge. This culture shift makes it much easier in the future to identify and mitigate risk.
Pride, self-interest, and success issues overlap and interact. Sustaining motivation comes by creating the right balance among these basic elements. When you achieve balance, you motivate not only individuals, but also teams, departments, and entire organizations. FIGURE 5-1 depicts these three basic elements of motivation and their intersections.
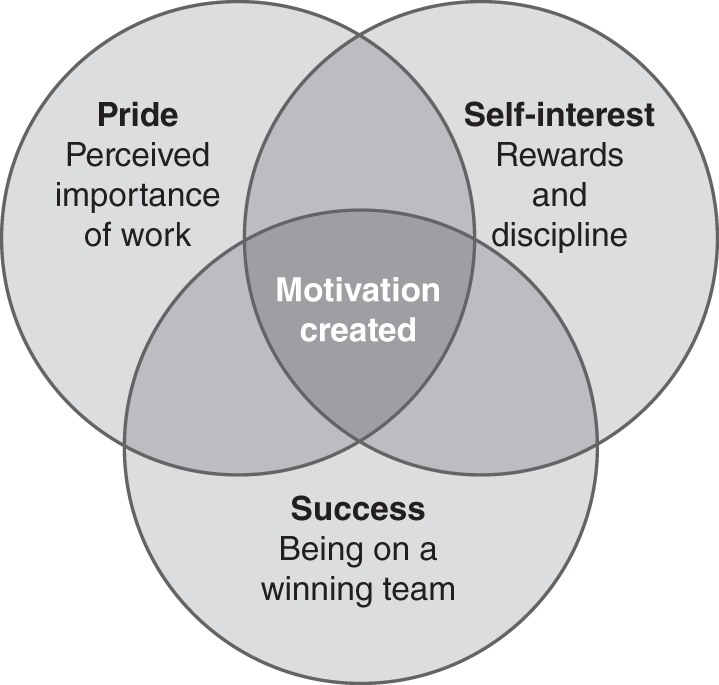
FIGURE 5-1 Three basic elements of motivation.
Motivated employees are far more likely to embrace the implementation of security policies. This leads to more risks being identified and mitigated for the organization.
Personality Types of Employees
It’s easy to see firsthand that individuals react differently in the workplace. What motivates one person does not always work for another. Understanding different personality types within a team is key to understanding how to motivate people. It’s important to understand and appreciate the differences. This understanding allows you to leverage talents more effectively.
Let’s illustrate this point with a simple example. Assume you’re dealing with two key stakeholders in the Finance and Audit departments. The financial analyst may be analytical and want to know about the financial impact of implementing the new security policy. The auditor may be more focused on the outcome. What risks will be reduced after the policy is implemented? There may also be a host of individuals with a wide variety of motivations. Being able to recognize these differences will allow you to speak to the points of interest that will be most persuasive. Talking to financial analysts about threats might be good background to justify a project, but it doesn’t address their potential concern about going over budget.
 NOTE
NOTE
Understanding personalities is particularly important in dealing with stakeholders. Stakeholder is a term referring to individuals who have an interest in the success of security policies. During the early stages of implementing a policy, the stakeholders play a critical role. If you understand their personalities and needs, you can motivate them to support the implementation.
HR Magazine identified eight classic personality types in the workplace. They are commanders, drifters, attackers, pleasers, performers, avoiders, analyticals, and achievers. In many ways, the personality names speak to the individual traits of each type. The following is a high-level summary of each of these traits:
- Commanders—Are demanding and not tactful. They might come across at best as impolite and at their worst as rude and abrupt. They are forceful when attempting to achieve stated goals. They can be agents for change, breaking from the past and overcoming barriers within the organization.
- Drifters—Are uncomfortable with structure and deadlines. They might be great with people and communications because what they lack in discipline may be offset by their creativity and thinking outside of the box.
- Attackers—May seem angry or even hostile toward ideas and others on the team. They are critical of others’ ideas. They may know why things fail but offer no alternative solutions. They can be helpful in understanding the risks associated with a new policy, but don’t expect them to offer solutions to make the policies better.
- Pleasers—Are very kind and thoughtful to others. They want everyone to “feel good” and will put their own self-interest aside for the good of the whole. They may shy away from enforcing rules that offend others. These individuals would not affect enforcing security policies.
- Performers—Like to be center stage. They like to entertain and be the center of attention. They develop over time a wit and charm to capture people’s attention. They may not be the highest producers and may be in the habit of self-promotion. These individuals are good candidates to promote awareness of and training in security policies. Their wit and humor, when harnessed, are effective in communicating why the security policy is important.
- Avoiders—Like to fly under the radar and be in the background. They tend not to take chances or do anything that brings attention on them. They will do precisely what’s asked of them but not much more. Although not good as leaders at looking beyond the letter of the policy, they will execute the security policy and related processes consistently.
- Analyticals—Like structure and deadlines. They measure their success in precise terms of the number of widgets produced in a given time at a given quality level. They tend to be obsessed with precision and attention to detail. They may not be the best at understanding human dynamics, so working with customers and emotions may be a problem. They would be well suited for measuring the effectiveness of the information policy, such as by being part of the quality control function.
- Achievers—Are result-oriented. They may have several traits of the other personality types; for example, they may be self-confident but not at the expense of others. They genuinely want the best result and may seek different ways to achieve it. Achievers are well suited to listening to all stakeholders and crafting security policies that meet both security and business needs.
FYI
Personality assessments have existed for a long time. The Myers-Briggs Type Indicator (MBTI), for example, was first published in 1962. Assessments of personality types have become more widely used recently because computer-based testing makes them easier to deliver and their perceived accuracy has grown. Such an assessment should not, however, be the sole basis for hiring someone. A test can simply help you better understand a job candidate. Personality tests are also helpful when forming teams for long-term or highly important projects. Human resources (HR) books and websites are also good sources for personality type models.
It’s rare that an individual is just one of these personality types. Typically, personality types blend and mix depending on many factors. Dominant traits over time can become your safe zone. A safe zone refers to the skills you are comfortable with to achieve a predictable outcome.
Understanding these personality traits is an advantage in implementing security policies. Often, new security policies represent change. You can use the strengths of these personality traits to overcome objection to the change. For example, analyticals could review detail logs and network designs to identify potential security threats. There is no set rule of how to tap the talent of each of these personality types. Understanding these types allows you to leverage people’s strengths to more quickly implement security policies.
Leadership, Values, and Ethics
Given all the material that has been written on the subject, entire libraries can be built around leadership, business values, and ethics. They are discussed in this section to help you better understand human nature in the workplace. This section focuses on how leadership affects employee behavior and how good leadership can help ensure that employees adhere to policies.
Leaders must require proper behavior from employees and exhibit the same qualities in their own actions. A leader who demonstrates ethical behavior every day is more likely to see that behavior emulated by employees. Good leaders recognize the need to work within these personality types, guide their energy and passion, and get results. A leader’s job is to work through others to achieve specific goals. Implementing security policies is all about working through others to gain their support and adhere to the policies.
There is no secret formula for motivating individuals. Some widely accepted leadership rules that also apply to security policies include:
- Values—Good leaders have core values. Leaders share their core values with employees. Good leaders will seek to understand and convey the importance of security policies. Core values can also apply to the organization.
- Goals—Good leaders have clear vision and set goals. They communicate these goals both to the team and to individuals. They communicate how contributions lead to success. People want to know they are working on something that matters. Good leaders will be able to communicate the importance of the policy to the organization and to individual team goals.
- Training—Good leaders train their team to focus on goals and support each other’s work. A good leader will make sure the team is ready to take on the additional responsibilities outlined in the policy. Training is also a key component of security. All of the policies and technology you can possibly imagine will be ineffective without properly trained employees.
- Support—Good leaders accept failures. Things will go wrong. People will make mistakes. How a leader reacts to these mistakes sets a tone that can be healthy or destructive. The trust a good leader creates is essential in encouraging accurate reporting of whatever is not working. This, in turn, is essential in improving the control environment. When employees trust that they can report noncompliance without repercussions and can report the reason the mistake was made, it’s more likely that the problem can be corrected and kept from recurring. In fact, the practice of candid reporting of problems should be the norm and should be rewarded when it occurs.
- Reward—Good leaders reward results, not personalities. A quick way to demoralize a team is to reward individuals based on who is liked versus who produces. What’s commonly referred to as “company politics” can never be eliminated; however, the more a leader can measure real risk reduction because of security policies and controls, the less interference from office politics will be encountered.
Part of understanding human nature in the workplace is recognizing its complexity. You need to understand what motivates individuals and yourself. A leader can’t simply issue commands and expect good results time after time. Nor can an executive simply mandate information security policies and expect staff to follow them. Good leaders demonstrate core values in their own actions, and they communicate their expectations. They understand the human personality, ignite passions, and inspire people to achieve common goals. Managers and employees must understand these dynamics to approach implementation of security policies in a realistic and thoughtful manner.
 NOTE
NOTE
Implementing security policy means continuous communication with stakeholders. It means being transparent about what’s working and what’s not working. In this way, the control environment can be continuously improved over time.
Being thoughtful about the implementation of security policies and controls means balancing the need to reduce risk with the impact to the business operations. It could mean phasing security controls in over time or simply aligning security implementation with the business’s training events.
