Legal Implications of IT Security Policy Enforcement
Technology makes it easy to transact business. Computers provide an effective method of communication and record keeping. Technology offers the ability to automatically keep an audit trail. This ease of use and creation of massive amounts of data have security policy enforcement implications. Data must be preserved and retrievable for a host of legal reasons.
Failure to properly retain records can lead to significant fines. This is especially true for data related to a lawsuit. Destroying records can jeopardize a company’s case. It can also lead to criminal charges. Even the innocent destruction of data can lead to accusations of negligence, withholding or hiding information, and altering or destroying evidence. So how long should you retain data? That depends on the content, organization, and location. For example, the Texas state Government Code, Section 441.158, requires local governments to retain records on annexation permanently. On the other hand, certain minutes of government meetings need be retained for only two years. Such legal distinctions must be assessed by a legal department and incorporated into policies and security practices to ensure the data is adequately archived.
In general, destroying records prematurely can actually cause far more problems than it might solve. If you have a reasonable expectation that some civil litigation is imminent, you have a duty to retain relevant records. Failure to do so could have substantial consequences. Older data should be destroyed only in accordance with well-established policies and only if there is no reasonable expectation that the data may be required in some context such as a legal proceeding.
It’s important to enforce security policies on data retention. This includes the preservation of data. The security policies must ensure that record keeping is accurate and securely maintained. Electronic discovery (e-discovery) is a part of the legal process. It’s used to gather computer-generated information for a legal action. This can be far more complicated than the discovery of paper documents because of the massive amount of data an organization holds.
FIGURE 14-2 illustrates this point. Consider a simple loan document. Notice from the figure that information from the original document is used to generate a monthly statement. The statement now contains personal financial information. That document, in turn, may be used to generate a late notice. The notice may be tied to an email correspondence with the customer. And so on. The personal financial information could even be sent to an external collection agency. The data most likely is stored in multiple systems. This is depicted to the far left—note the information is flowing through loan, customer service, collection, and accounts receivable applications.
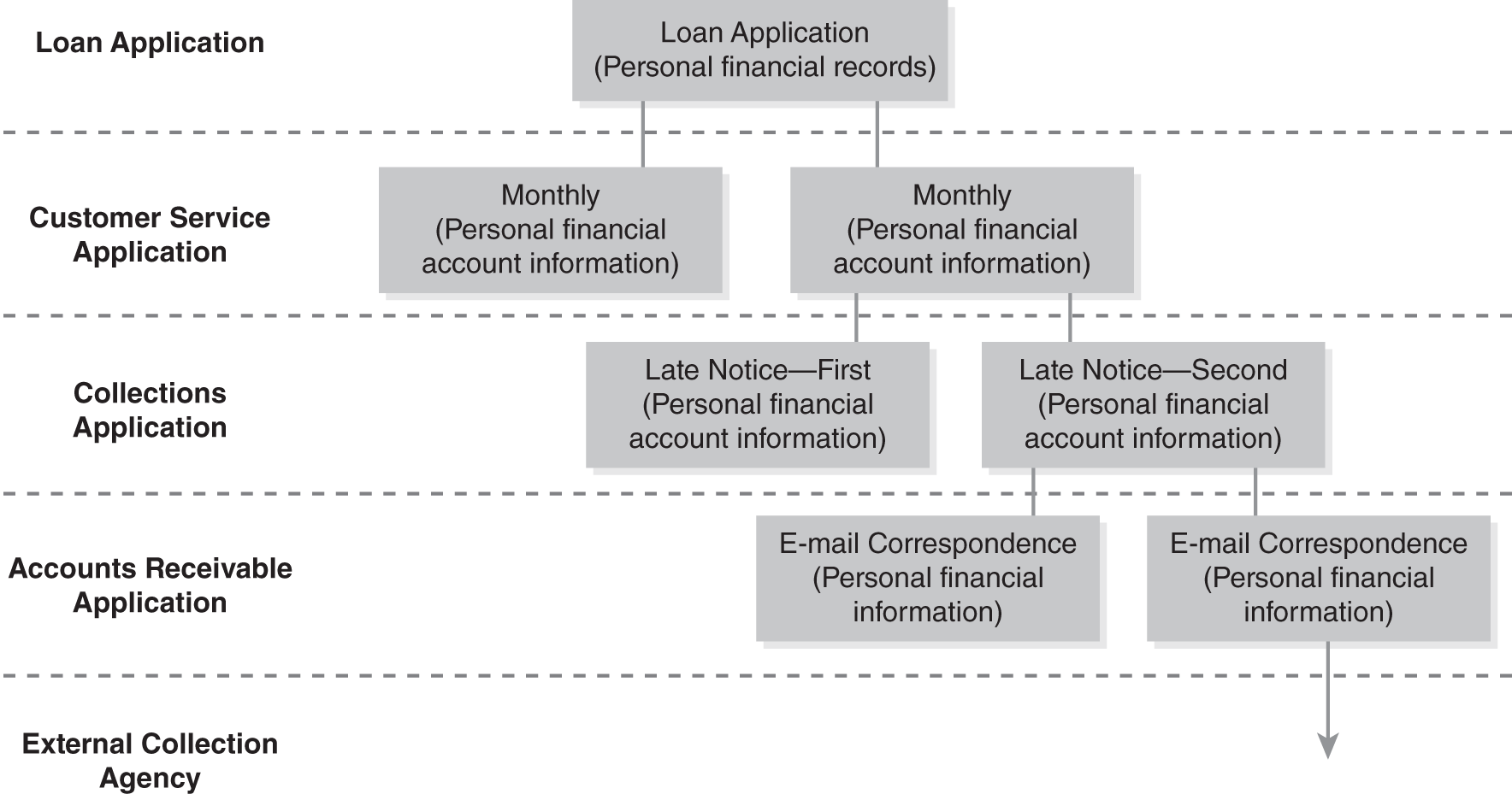
FIGURE 14-2 Illustration of how data quickly expands.
Over the years, hundreds of documents can be generated in multiple systems. You can quickly see the problem when an organization is required under e-discovery to produce documents and identify everyone who accessed these documents. The effort to retrieve this information is significant.
The legal implication of policy enforcement is not just about protecting data. There’s a host of issues that need to be considered when writing security policies. You may not be able to terminate a user based on a violation of security policy. It depends on how the policy was written, HR policy, and the security awareness training provided.
Even the deployment of security devices can have legal implications. For example, a honeypot is a network security device that acts as a decoy. Its sole purpose is to look like a tempting target to a hacker. When a hacker attempts to break into the honeypot, it records the hacker’s actions. This can be used as evidence of an attack. A honeypot also allows you to analyze the attack methods in great detail. This information can be used to harden other devices. This type of device has legal implications, however. Other security devices such as a firewall can be used to stop a hacker; however, a honeypot, by its nature, attempts to lure the hacker. Even more legal complications arise when a honeypot is put in the DMZ and publicized. This type of deployment raises the question of whether the organization is encouraging an illegal act.
Smartphones not owned by the organization are a challenge, even if the organization has a policy stating they can configure and wipe the device. Who has control when employees use smartphones for company business? It’s especially hard to tell when an employee leaves the firm and disconnects the device from the organization’s control. How does the organization ensure the device is wiped? There are legal implications for wiping devices not owned by the organization. Policy alone cannot provide sufficient legal authority to access the device unless an employee has granted such rights through some binding agreement.
The key point is that legal implications with security policies come in many forms. It’s important that you build a good working relationship with the legal department. It can ensure that security policies can be enforced without causing legal problems.
