What Is Information Assurance?
Too often you will hear the terms information systems security and information assurance used interchangeably; however, they are not the same thing. Information assurance (IA) grew from information systems security. The high-level difference is that ISS focuses on protecting information regardless of form or process, whereas IA focuses on protecting information during process and use. You can see some of these differences as you examine the security tenets, also known as the “five pillars of the IA model”:
- Confidentiality—Generally accepted as ISS and IA tenets
- Integrity—Generally accepted as ISS and IA tenets
- Availability—Generally accepted as ISS and IA tenets
- Authentication—Generally accepted as an IA tenet
- Nonrepudiation—Generally accepted as an IA tenet
The first three—confidentiality, integrity, and availability—are bedrock principles throughout information security. These are often referred to as the CIA triangle. (Some sources refer to this as the CIA triad; the two terms are synonymous.) This is not to suggest that authentication and nonrepudiation are not information security concerns. The goals are similar; however, the approach and focus are different. IA imposes controls on the entire system regardless of the format or media. In other words, IA ensures data is protected while being processed, stored, and transmitted. This ensures the confidentiality, integrity, availability, and nonrepudiation of the data.
Confidentiality
Confidentiality is the goal of ensuring that only authorized individuals are able to access information. A user should be granted access only to the specific information necessary to complete his or her job.
Typical users do not need unlimited access to all systems and all data. In fact, in regulated environments, if ordinary users had such access, this would be viewed as a compliance issue and a violation of law. Many organizations have adopted the need-to-know principle. In brief, this means that you gain access only to the systems and data you need to perform your job. For example, payroll personnel may need your employee and personal information, such as salary and Social Security number. Your manager may need access to your salary for budgeting but not your Social Security number. By restricting access, you maintain confidentiality.
 NOTE
NOTE
Another consideration of confidentiality is how to protect data in the event of a breach or unauthorized access. One way to resolve this issue is to use encryption. This is considered a security layered approach. A breach in one layer will be caught by another. In this case, even if data is improperly accessed, it still cannot be read.
FIGURE 1-2 depicts the confidentiality tenet. The figure represents three users—two are regular users; one is a privileged user. User A and User B have limited access rights to data. User A can read only data stored in the product list, whereas User B can read and update all data in the database. The privileged user has elevated database administration privileges; however, even he or she might not have access to all data.
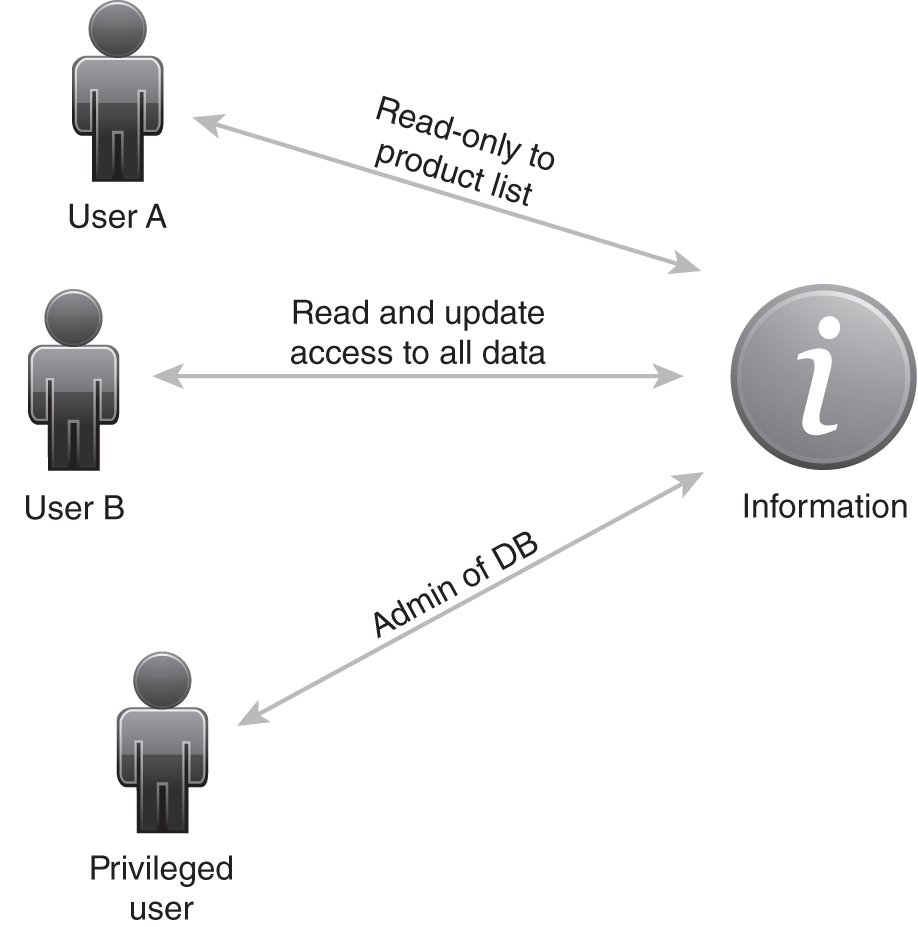
FIGURE 1-2 The confidentiality tenet.
Integrity
Integrity ensures that information has not been improperly changed. In other words, the data owner must approve any change to the data or approve the process by which the data changes. There are several ways to ensure that data is protected. Many operating systems allow permissions on data files and directories to provide restricted access. These containers typically reside on a server that requires users to log on and authenticate to gain approved access. This ensures that only users who have the data owner’s permission can change the information. Often, access is limited to an application. In this way, a user does not access data directly. The user accesses the application. The application accesses the data. So, the application acts as a gateway. This allows for more fine-grained granting of access, often referred to as entitlement. With entitlement, you can restrict the type of access a user has. For example, the application can allow a user to approve a payment but limit the amount to less than $1000. Encryption also ensures integrity as well as confidentiality. Encryption protects data from being viewed or changed by unauthorized users. Only users with the proper key can change or view encrypted data. Encryption is often used to protect data being transmitted or moved. Encryption can also be used to protect data at rest.
FIGURE 1-3 depicts the integrity tenet. There are two users, an application, a database management system (DBMS), and the data. The application control limits the type of change a user can make. The DBMS rules prevent unauthorized changes to data. User A can change data. User B can only retrieve data.
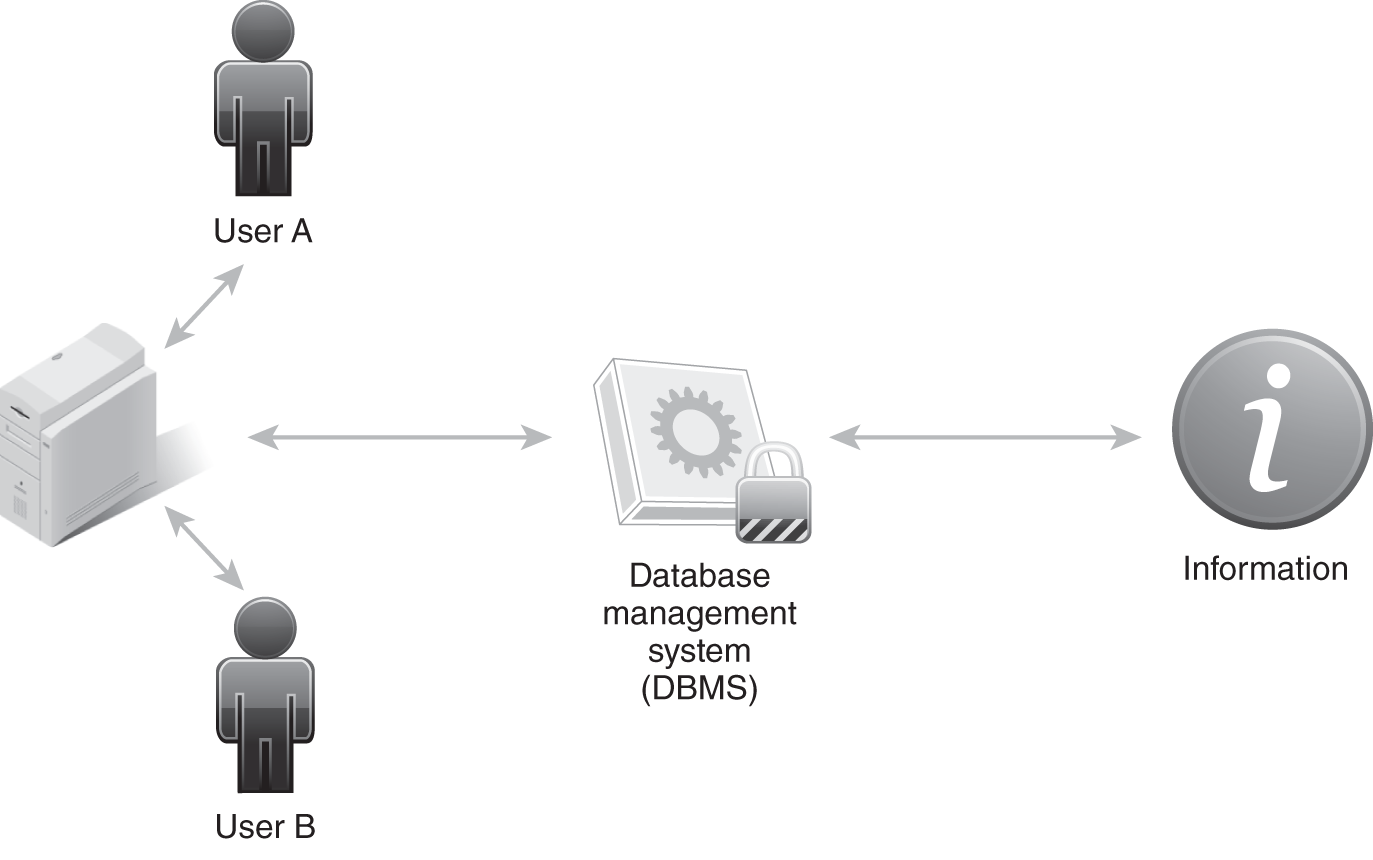
FIGURE 1-3 The integrity tenet.
Authentication
Authentication is the ability to verify the identity of a user or device. You probably see authentication in use every day. For example, you might use an online email system such as Google Gmail or Yahoo! Mail. What protects your email is your user ID and password, which you selected when you signed up for the service. This user ID and password are your authentication approach to accessing your email service.
It’s not just humans who need their identities verified. Computers often exchange information or process transactions on our behalf. While you are asleep, a computer system may by printing your payroll check. Many of these functions are sensitive. As a security professional, you should ensure that only these authorized processes are accessing this sensitive information. This means these computers and automated processes need to be authenticated. Just like an individual, their identity is verified before being granted access to data. For example, services running in Microsoft Windows Server could have an ID assigned. Network devices can exchange information at a network protocol level to verify identity. These nonhuman IDs typically have elevated rights. This means they have lots of authority to access data across multiple systems. It’s important that access to these nonhuman accounts be tightly controlled.
There is a lot involved in maintaining good authentication processes, such as forcing users to change their passwords periodically and forcing rules on how complicated passwords should be. These housekeeping tasks are becoming easier and more automated. One of the more critical keys to success is having credentials that are hard to forge or guess. A good example is a strong password known only to the user. Additionally, these credentials must not be transmitted in the clear over the network. Passwords sent over the network in plaintext, for example, can be observed with network sniffers. In a typical business environment, if these two goals are accomplished as well as many of the housekeeping items previously discussed, you begin to have reasonable assurance you know who is accessing your computer systems.
Availability
Availability ensures information is available to authorized users and devices. A major challenge to availability is the spread of denial of service (DoS) attacks. The technological sophistication and intensity of DoS attacks have increased significantly in recent years. These attacks flood a server with information that overwhelms its ability to process, causing the server to crash. Thus, the service becomes unavailable. The point of the attack is not to steal information but to crash the system. DoS attacks are often measured by the amount of information flooding the server. The typical measurement is in Gbps (gigabits per second). The size of DoS attacks keeps growing. In 2018, it was reported that the average DoS attack was bigger than 26 Gbps, and the maximum attack size was 359 Gbps.1 However, in 2019, the average size decreased by 85 percent, and the maximum attack size decreased by 24 percent.2
Initially, the information owner must determine availability requirements. The owner must determine who needs access to the data and when. Is it critical that data be available 24/7, or is 9 to 5 adequate? Does it need to be available to remote or only local users? The raw business requirements then need to be translated into technical and operational commitments, such as hours of operations for when the systems would be available.
After availability requirements are determined, you must assess the threats and implement appropriate controls. Associated with the servers is all the network equipment that provides interconnectivity and remote access. Proper configuration of these devices will allow access to the information when needed.
Nonrepudiation
Nonrepudiation is both a legal term and a concept within information security. The idea is simple—nonrepudiation is the assurance that an individual cannot deny having digitally signed a document or been party to a transaction. As a legal concept, it is the sum total of evidence that proves to the court’s satisfaction that only one person could have executed that transaction.
Before the Internet, individuals struggled with the question. When you sign a legal document, often you need a notary. That notary is there to be part of the nonrepudiation process of gathering evidence. He or she takes copies of your identification and matches signatures. Some even take a thumbprint. All this effort is so that later you cannot claim it wasn’t you who signed.
So how do you sign a document electronically? A leading method is to use a digital signature. If used properly, the electronic signature cannot be forged and is digitally timestamped. Most important, the receiver of the document can verify it is your digital signature. But even a digital signature relies on a private key that must be protected. It’s worth noting that these digital signatures are legally binding under the U.S. Federal ESIGN Act of 2000.
However, many final electronic transactions do not use digital signatures. In fact, often online banking transactions, money transfers, or buying and selling stock rely on other technology, including strong authentication. Ultimately you want to prove that only that person could have executed that transaction. A leading vendor in this space is IBM, whose flagship product for secure messaging is called Websphere. IBM defines nonrepudiation as an end-to-end service that “can be viewed as an extension to the identification and authentication service.” Although secure messaging ensures the collection and delivery of the transaction, the application that consumes the message still has to be proven as secure.
 NOTE
NOTE
The Federal ESIGN Act defines an electronic signature as an “electronic sound, symbol, or process, attached to or logically associated with a contract or other record and executed or adopted by a person with the intent to sign the record.” To learn more, go to https://www.fdic.gov/regulations/compliance/manual/10/x-3.1.pdf.
It should be noted that the CIA triangle, although widely used in information security, is a somewhat simplistic model, and there have been expansions to it. The McCumber cube is one such expansion of the CIA triangle that is worth discussing. It was described in detail in 2004 in the book Assessing and Managing Security Risk in IT Systems: A Structured Methodology. It looks at security as a three-dimensional cube. The concept is to add more dimensions to the traditional CIA triangle. In addition to the three aspects of the CIA triangle, the location of information is addressed. Is the information in transmission, storage, or processing? Then the security aspect is addressed. Is the issue technology, policy and procedure, or education training and awareness? Thus, one might examine the policy and procedure aspects of confidentiality of data in transmission. Or one might address the technological issues of maintaining integrity of information in storage. The McCumber cube can be seen in FIGURE 1-4.
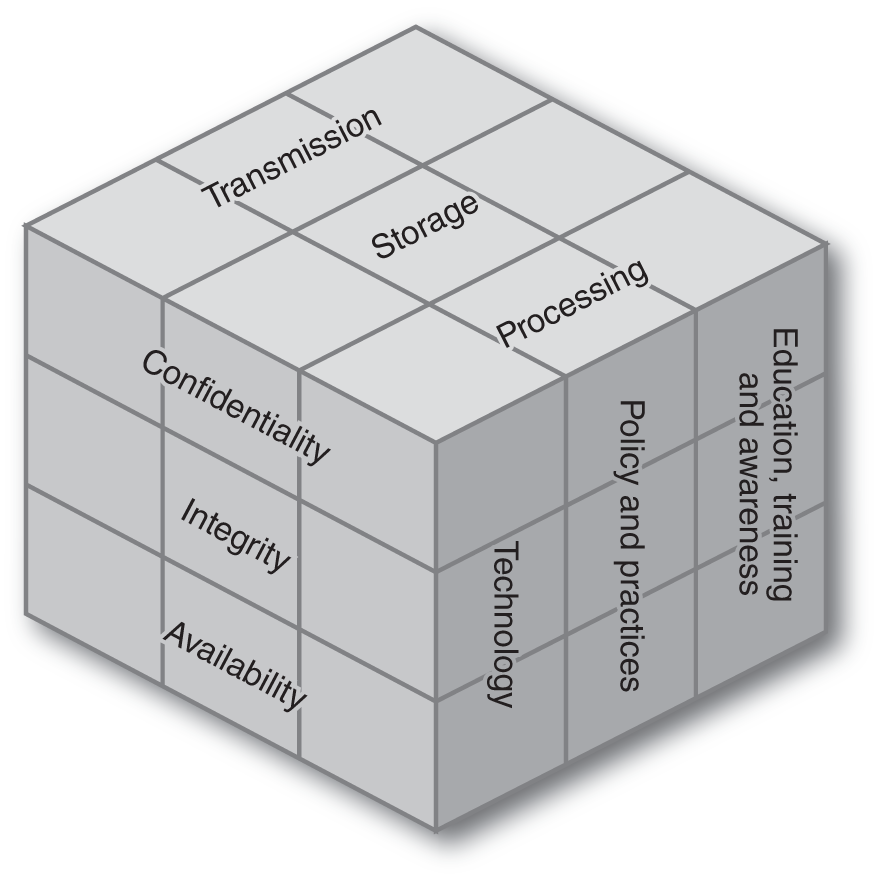
FIGURE 1-4 The McCumber cube.
No one technology is foolproof, so many security experts believe that applying multiple security services collectively that tie the transaction back to a single individual is the best way to meet business needs. The simple fact is the more evidence you gather, the harder it is for that person to deny it. Ideally, businesses want to prove it was your computer, your ID, your digital signature, and your transaction that cannot be repudiated.
