Employee Awareness and Training
The goal of employee awareness and training is to ensure that individuals have the knowledge and skills needed to implement the security policies. The primary objective of a security awareness program is to educate users. A well-executed awareness and training program can do much more. Some additional benefits include:
- Reinforcing core organizational values
- Giving management an opportunity to demonstrate support
- Creating opportunities for employees to acquire new skills, leading to increased job satisfaction
Awareness includes teaching employees about policies and core security concepts. Effective security awareness helps drive acceptance. When users understand policies, they can be held accountable for observing the policies. This promotes a long-term security culture shift. With so much at stake, it’s important to have a well-thought-out approach to education.
Typically, an organization offers security awareness training. This is broken down into two components:
- Awareness—To increase understanding of the importance and value of security policies
- Training—To provide the skills needed to comply with security policies
Awareness should be an ongoing effort that reinforces key concepts. The awareness component is important, because it sets the tone and goals for security policy implementation. By setting realistic goals, you build credibility for the policies. Awareness also promotes candid conversations. Security awareness is, in part, about effective marketing and messaging.
The training component is more straightforward than creating awareness. In security training, you review security policies in detail. You discuss how the policies apply to individual roles. You set expectations on behavior. Security training focuses on mechanics—what is expected to be done and when. Often, in security policy training, you will discuss the supporting processes. For example, you might discuss restricting security administrator accounts. This can lead to a discussion on how to grant rights.
Technical TIP
You should expect some level of participation by executives during training. An executive may simply stop by to kick off a session. A few opening remarks in a training session can send a powerful message throughout the organization. Also, consider videotaping a message from a senior leader as an effective communication technique. This avoids the problem of scheduling his or her time for multiple training sessions.
Organizational and Individual Acceptance
Users are more likely to accept what they understand. Security awareness is the first step in getting people to think about security. Security awareness training gives you an opportunity to explain the value of security policies. When security policies help users do their work, they are more likely to consider the policies to have value. Consequently, the goal of the security awareness program should be to gain support as well as to teach material. You need to tailor training to the users. For example, the type of training senior leaders receive would be different from individual user training.
Collectively, user behavior defines the organization’s acceptance of security policies. When security policies are widely accepted, they become part of the culture. That tends to reduce risk, resulting in a lower number of security incidents. The converse is also true. When security policies are not widely accepted, there’s an increase in security incidents. It’s important that users embrace security policies to ensure the policies are used and thus effective.
Motivation
Ideally, awareness should excite and inspire, as well as train; however, motivation is a broader topic. How individuals are motivated varies by person. One clear motivation is self-interest. When management rigorously enforces security policies, that becomes a powerful motivator. This can be demonstrated by how management holds users accountable for failing to follow policies. Users need to know that management is serious about implementing security policies. This clear message of rewards and discipline is important in motivating users.
 TIP
TIP
Best practices and standards often include information on how to create a security awareness training policy. Following this guidance can ensure that you meet regulatory requirements. For example, FISMA security awareness compliance is based on NIST Special Publications 800-16 and 800-50.
Untrained or unmotivated employees can make poor decisions. Poor decisions can lead to security incidents, even when individuals are trained. Poor decisions can occur anywhere within the organization. A user can fall prey to social engineering pretexts. A user can fail to report a control weakness. Management can fail to act when a report is received. Risk experts can fail to correctly assess the extent of the vulnerability. Senior leaders can fail to fund the mitigation. Regardless of the failure, there’s a danger that policies will be perceived as ineffective when security incidents rise.
The key point is that effective security policy implementation depends on acceptance. Acceptance depends on the individuals who perceive value in the policy. Ultimate acceptance depends on the value being demonstrated by lowered risk to the organization. Security awareness and training is an opportunity to communicate value and get employees motivated.
Developing an Organization-Wide Security Awareness Policy
Effective security awareness training must reach everyone in the organization. This includes anyone with access to data, including employees, contractors, and vendors. The form of security awareness training may vary depending on the type of user. For example, security awareness training for a vendor might be handled by its parent company. The contract with the vendor should specify the type of awareness training the client requires. Typically, the vendor is responsible for training its employees. This is different from contractors. Contractors usually go through the same type of training as the contracting company’s regular employees. In this case, the contracting organization is responsible for security awareness training.
Contractor training may be condensed, however. If a contractor will be on-site for only a short time—three weeks, for example—it does not make sense to require weeks of security awareness training.
The security awareness policy ensures that education reaches everyone. For example, the policy might require that all users receive security awareness training before being granted access to data. This might include completing basic security awareness training during employee orientation. This ensures newly hired individuals receive training before handling sensitive information.
The security awareness policy typically outlines the frequency and type of training required. Awareness training is conducted at least annually. A security awareness training policy may require the following types of training:
- New employee and contractor—At time of hire before access to data is granted
- Promotion—As individuals are promoted into significantly different roles
- All users—Annual refresher training
- Postincident—After major security incidents, when lack of education was noted
- Vendor—As defined in the contract
It’s important that you know your audience. You should tailor training to resonate with them. For example, humor is often an effective tool in awareness training. Humor can capture an individual’s attention. It can also elicit cooperation and make the topic fun. Although that may be appropriate in larger audiences, it may not be the best choice when training executives. As a general rule, you want to tailor your approach on the basis of:
- Job level—The higher people are in the organization, the more strategic their training needs to be.
- Level of awareness—Some users need more training on basic security concepts.
- Technical skill level—Individuals who are technically savvy may be able to understand threats more easily.
The security awareness policy determines the type of awareness training that’s provided. The policy also defines the audience that receives the training. For example, the policy could require senior management to receive strategic security and policy training. Middle management might be required to take policy and basic security training.
 NOTE
NOTE
All users must receive some type of security awareness training. The policy should define how such training will be delivered.
Training should focus on individual roles and responsibilities. Middle managers need to understand basic security concepts and the risks they may encounter running daily operations. Senior managers are less likely to encounter those risks when they focus on strategic issues in running the organization. Basic security training might include discussion of how to implement encryption methods. This is a real issue that middle management may face. Senior management would have little interest in, or bandwidth for, dealing with basic security issues.
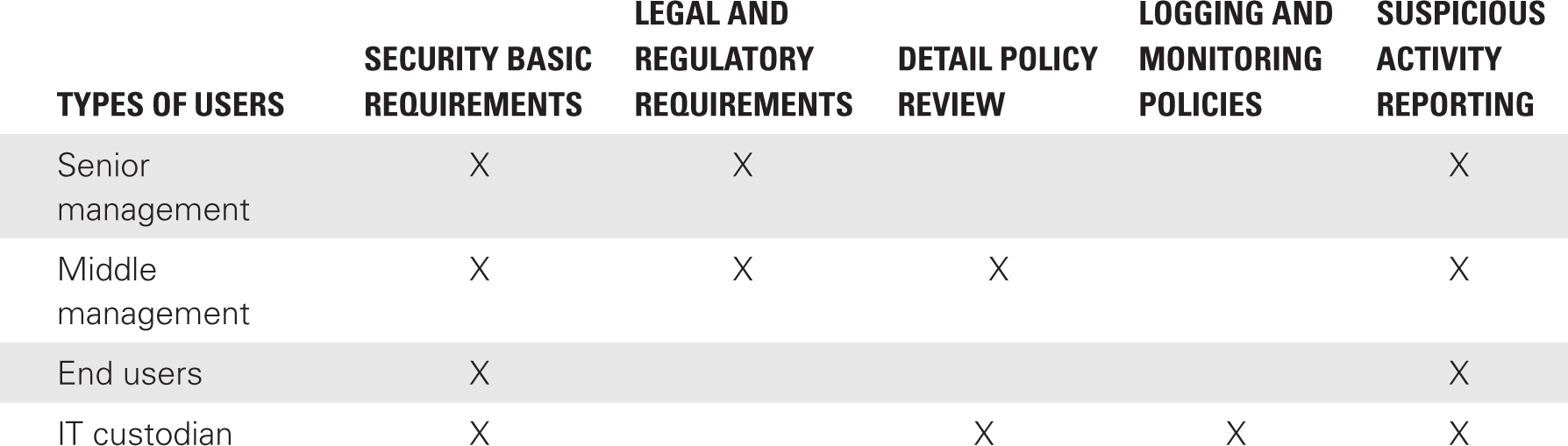
The scope of security awareness training is not one-size-fits-all. One approach to security policy awareness training is to define the user population and types of security awareness training offerings. This allows you to require specific training to address individual needs. TABLE 13-1 is a simple example of this concept. Notice that there are four basic user types defined. The security awareness policy would define each of these user types to ensure individuals in these roles can be quickly enrolled in training. The columns represent the type of training offered. The type and level of training would vary depending on the organization’s needs. Notice the emphasis on reporting suspicious activity. This is reflected by the fact that all users are required to receive this type of training.
In many organizations, this type of training is tracked through an online course registration tool. The application allows an individual to enroll in available training sessions. The application can also automatically assign required courses to individuals and track attendance. Online course registration tools help enforce the security awareness policy. These tools can also show evidence of enforcing the policy.
 NOTE
NOTE
The security awareness policy must require specific training across the organization. This ensures expectations are set consistently. The message and type of training can vary by role.
Conducting Security Awareness Training Sessions
The goal of formal security awareness training is to build knowledge and skills to help workers perform their roles in a way that protects assets and complies with policies. Security awareness training is not just about echoing back the trained material. The measure of success is how effectively the workers apply their training on the job.
There are two common ways of formally delivering security awareness training: in the classroom and through computer-based training (CBT). Both methods are widely used, and both have strengths and weaknesses. Large organizations often use a combination of methods. There are also a host of informational methods. They can be as simple as a manager emailing a policy to the team, asking everyone to read the material. Information dissemination methods are discussed later in this chapter.
In the classroom setting, a trained instructor usually conducts security awareness training. The advantage of having an instructor deliver the training is flexibility. Suppose some training materials were developed under the assumption that the audience has a certain technical skill set. If a session is delivered and the audience doesn’t have the necessary background, an experienced instructor can adjust the delivery accordingly. An instructor in a classroom can answer questions and connect with the class.
There are also drawbacks to a classroom setting. The first is cost. Classroom sessions can be expensive because of facility and travel costs. You need to find a suitable classroom and arrange for everyone’s attendance. Conference rooms can be effective but are sometimes a poor choice, depending on class size and number of interruptions. It’s not uncommon for individuals to be pulled out of training sessions held within the office setting. Alternatively, arranging for a conference room at a local hotel or alternative location comes at a price. Attendance could mean flying individuals to a training location or flying an instructor to remote offices. Another issue is the skill set of the instructor. Experienced instructors are typically in short supply. It takes a specific skill set to facilitate a training session.
The CBT approach can be a lower-cost alternative to classroom training. A number of factors can drive a cost difference between CBT and classroom training. Some of these factors are size of the organization, location, and travel. Larger organizations can find it expensive to hold enough classes to cover enough of the employee population to be effective. Besides, the cost of travel and classroom space at some remote office locations can be high. With CBT you can reach an unlimited number of workers with a consistent set of messages. Online courses also allow workers to learn at their convenience. This can include taking a course at night or on weekends, away from the pressures and distractions of the office.
 NOTE
NOTE
Many organizations use a combination of approaches, offering classroom training and CBT.
FYI
A classroom session can be a positive experience where individuals exchange ideas and make a personal connection with other students and the instructor. Another significant benefit is that the instructor can gauge the audience’s acceptance of the material. Through questions and discussions, an instructor can determine how well the audience has understood the message. Based on this feedback, the instructor can adjust the training to be more effective.
Online courses offer quizzes throughout each session to automatically score competency. An online training tool can also require review of material the attendee found challenging. CBT offers statistical tracking of who takes courses and which part of the material individuals are struggling with.
The CBT approach has drawbacks, though. It can only measure what individuals know about the material. Unlike an instructor, it cannot measure how well the material is being accepted. A strength and weakness of CBT is the consistent format in which it’s presented. The message in the material is consistently delivered; however, some CBT has limited or no opportunity to tailor the message to a specific audience. Finally, CBT is impersonal. Unlike classroom instruction, CBT offers little opportunity to connect with others in the organization.
 NOTE
NOTE
Simply knowing the subject material doesn’t mean you are able to teach the material. It’s important that the core message not change as the material is adjusted to fit the audience. Delivering a consistent message is important.
It’s important to get feedback on the training by the attendees as soon as possible. This feedback should focus on how well the material is being accepted beyond what knowledge was conveyed. In other words, it’s important to know the attendee is using the knowledge rather than simply memorizing the material. Some suggested ways of getting feedback include:
- Anonymous surveys after the session
- Focus groups
- Interviews of attendees
- Exit interviews of individuals leaving the company
- Monitoring compliance through incident reports
Human Resources Ownership of New Employee Orientation
New employees can often be reached through the human resources (HR) department. The HR department usually manages the onboarding of new employees. HR usually has an array of employment documents new employees must complete, from benefits forms to ID badge acknowledgments. HR also provides a series of training sessions to help new employees ease into the organization’s culture. Most organizations add security awareness training to the list of items the HR department provides to new employees. It’s cost efficient, because it simply adds material to new employee training HR conducts. You don’t have to pull new employees offline into a separate training session. It’s also practical from a timing perspective. You don’t want new employees to access sensitive data until they receive training. You want to get to the employees as early as possible.
 TIP
TIP
The security awareness training that all employees must take should be delivered during new-employee orientation. Additional training can be handled after the employee is on the job.
Review of Acceptable Use Policies (AUPs)
A core topic in security awareness training is reviewing the acceptable use policy (AUP). It’s not uncommon to require employees to sign the AUP. This acknowledges they have received and read the policy. The AUP clearly defines what’s considered acceptable and unacceptable use of technology. The AUP, for example, specifies that the organization’s computers should be used for business purposes only. It may also exclude specific types of usage such as gambling or accessing offensive material. The AUP also defines personal responsibilities, such as protecting one’s own password.
One of the more critical training points in an AUP is to prohibit sharing of an individual’s ID and password. Sharing such information can place sensitive data at risk from unauthorized access. It also undermines the concept of nonrepudiation. Assume a supervisor asked a user to share his or her password. This is a violation of the AUP by both the employee and the supervisor. In the real world, if the employee promptly reported the violation, no action would be taken against him or her. Although it may be a violation by the employee, the supervisor is the source of the breach. It’s not always reasonable to expect an employee to stand up against a supervisor, manager, or executive; however, failure to report the violation might be considered significant cause to discipline the employee. In either case, the supervisor should be disciplined for requiring the employee to provide that information. The level of discipline depends on the organization. If the violation leads to a fraud or security breach, there’s a strong case to be made for terminating the supervisor.
 NOTE
NOTE
The acceptable use policy (AUP) is a document that clearly defines a core set of user responsibilities and expectations. It also discusses the consequences of failing to comply. The document is meant to be enforceable. A violation of the policy could lead to disciplinary action, including termination. As a result, the AUP language is precise.
The AUP does more than protect passwords. It also addresses other high-risk behaviors, which should be included in security training:
- Handling and sharing of sensitive customer information
- Transmission of information outside the company
- Handing of company intellectual property
