Information Dissemination—How to Educate Employees
Educating users can be a formal or informal process. Formal methods are those that communicate policies in a formal training environment, such as a classroom or CBT. The advantage of formal training is that you know who’s taking the training, and you can measure, to some extent, its effectiveness.
Remember that people learn in different ways. It’s a good idea to select multiple methods to disseminate security policy messages and materials. Because people learn differently, this increases your odds of reaching everyone. For example, those that find computer-based training less appealing may find a department newsletter more relevant to their job.
It’s also important to understand the culture and the audience in the organization. If an organization has many remote offices, face-to-face presentations of the material will be less practical. In addition, some organizations distribute too many newsletters. Some users simply stop reading newsletters due to the volume. As a consequence, newsletters may not be the best choice for communicating critical information. The following is a list of potential ways to disseminate security policy information:
- Telephone town hall meetings
- Emails
- Newsletters
- The company intranet
- Posters
- Face-to-face presentations
- Giveaways such as pins, mugs, sticky notes, and so on
- Contests that include prizes
Any communication method that keeps the security message “alive” is effective. You are usually limited by time and money; however, communicating the policy message does not have to be expensive. It’s limited only by imagination. You could sponsor a security policy awareness contest. It might be as simple as asking individuals to answer security policy trivia questions online. The winner gets a basket of goods worth less than $20. For just a few dollars, you can apply creative ideas to engage employees and reinforce key messages.
 NOTE
NOTE
Security awareness is more than just formal training. It’s reinforcing the message and keeping information security in everyone’s mind. The policies themselves are good resources for individuals.
To successfully disseminate security policy messages, you need a communications plan. A communications plan outlines what information is to be shared. A communications plan defines the message, the people, and the method of delivery. By laying out an entire communications plan, you can quickly assess if the right message is reaching everyone.
When developing a communications plan, you should ask yourself the following key questions:
- Who communicates?—Are the right people delivering the message to build credibility for the effort?
- What is the target audience?—Is everyone receiving the appropriate message?
- What is communicated?—Is the right message being delivered?
- How is it communicated?—Are we delivering the message in the most efficient manner?
- When is it communicated?—Is the communication well timed?
- What collateral is used?—Is the message being delivered consistently?
- What objective is achieved?—Are specific goals being achieved?
TABLE 13-2 depicts a simple communications plan that has two events. Both events are to be communicated by senior management. The first communication event prepares middle management for the announcement to staff. One can anticipate questions during a policy launch. Leadership needs to be well prepared to answer questions from staff, which makes the policy rollout more effective. The second communication event is the actual kick-off of the security awareness effort.
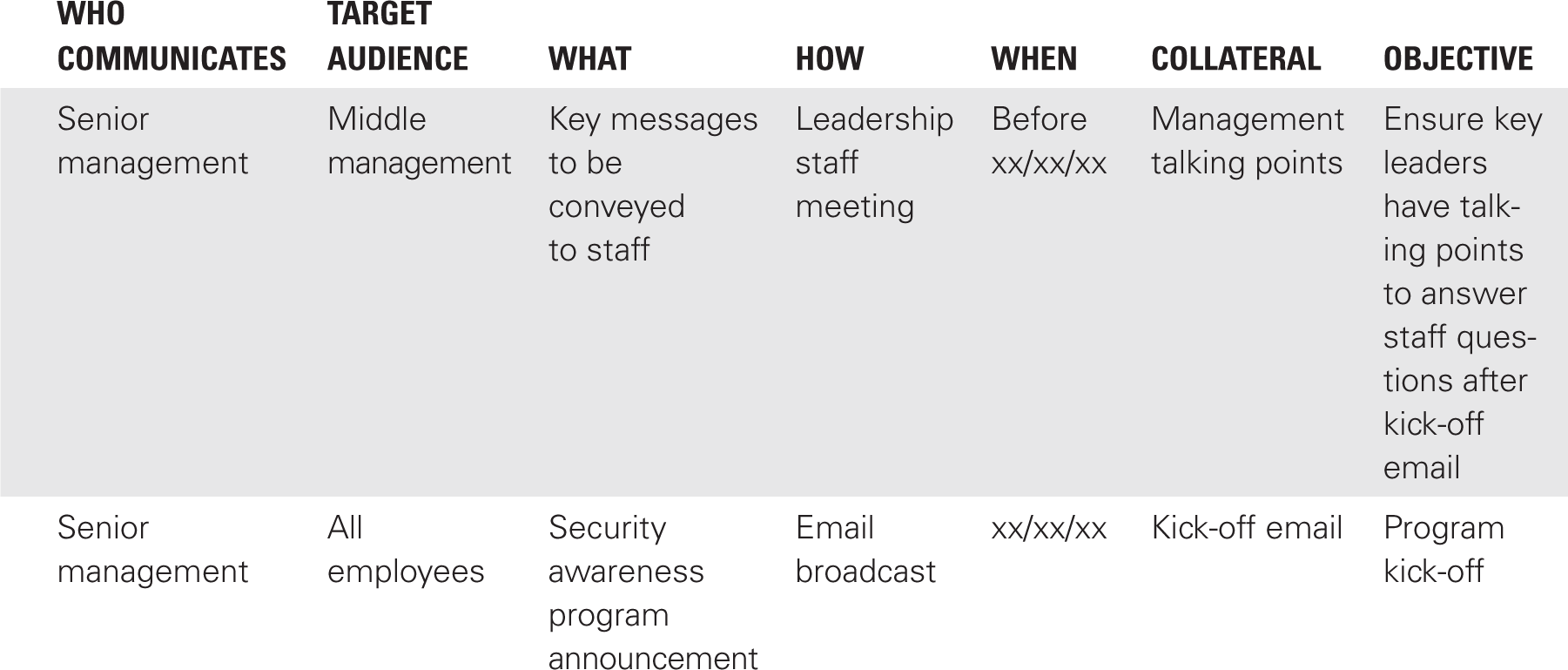
A communications plan can help rationalize the implementation strategy. For example, your strategy may call for everyone to receive at least three communications during the first six months of the security awareness program. If that’s the case, by scanning the Target Audience column in the communications plan, you can quickly determine if the goal is being achieved.
 TIP
TIP
Regardless of form, include your communication channels in your communications plan.
Hard Copy Dissemination
Hard copies of policies are rarely sent out today. The challenge in sending out volumes of paper is the cost and accuracy of the material. All of the security policies, standards, processes, and guidelines in an enterprise can be thousands of pages long. That doesn’t include the supporting materials, such as executive summaries, slide decks, and spreadsheets. Consequently, it’s not practical to disseminate the material in print form. Printing costs would be high, and it would take time, money, and effort to disseminate. In addition, as soon as changes to the material are made, the printed material is out of date. Putting policies on an internal intranet website is very effective. These can be easily updated and are readily available to all employees.
 TIP
TIP
Determining which materials are candidates for hard copy publishing will depend on the organization. The rule of thumb is to avoid sending hard copies where possible. When this is not possible, keep hard copies to a small amount of material with a limited distribution.
Posting Policies on the Intranet
The best method for communicating security policies is through a document-handling server such as an intranet. These servers offer multiple benefits, such as:
- Costs to disseminate material are low.
- Policies are kept current.
- Policies are searchable.
- Changes to policies can be highlighted.
- You can link to supporting material.
Many organizations already have an intranet. Consequently, the incremental costs for housing security policies are minimal. Centralized security policy management helps you keep policies current.
A significant advantage of electronic over hard copies is the ability to search for documents. Anyone who has browsed the Internet is familiar with search engines. You can enter key phrases and get a list of related documents. The same technology applies to an intranet. Your internal policies can be quickly searched for key phrases. In seconds, thousands of pages can be searched. For example, assume a business has decided to work with a vendor to process sensitive information. A quick search of policies using the keyword “vendor” may return a half-dozen documents. The topics may range from the need for a vendor assessment to secure connection requirements.
Another powerful tool of document-handling servers is the ability to track changes. When a modified policy is released, it’s helpful to know the exact wording that was changed. Policies often include a high-level explanation of the changes but few details. The ability to view the actual word-level changes in the policy is a powerful tool. This allows you to better assess the impact of the change on your existing controls.
Another significant benefit is the ability to link policies to supporting materials. The supporting materials can be executive summaries, slide decks, or a wide array of educational material. You can link any supporting material that makes it easier to understand the policy. For example, suppose you are reading a security policy on database logging, but you don’t quite understand the material. You notice a slide deck linked to the policy. After clicking on it, you are presented with a tutorial created by the database administrator explaining how to apply the policy.
Using Email
Although the level of sophistication on how policies are disseminated varies between organizations, most organizations still rely on email. Organizations depend on email to approve policies and keep management informed on implementation activities.
Email also plays a central role in most communications plans. Email allows you to notify a large population about major events. It also allows you to track everyone who has read the notification. This is a good tool for ensuring that individuals are properly notified of policy releases. Email also allows you to send out surveys and follow up on how well the implementation is being perceived.
Brown Bag Lunches and Learning Sessions
A brown bag session is a training event. An expert on a topic is invited to share his or her thoughts, ideas, and experiences. The term brown bag came about because sessions were usually held at lunchtime, and people brought their own lunches in brown bags. Nowadays these sessions may or may not be held over lunch, and if they are, lunch may even be catered. As a broad term, brown bag can be applied to a wide variety of less formal training situations.
The core concept of a brown bag usually applies to a small group of people that has access to one or more experts. Participants ask the experts questions. The experts guide the conversation. There may or may not be a formal presentation. The key idea is that the sessions are less scripted than a formal classroom setting.
The level of success of these sessions depends on the expert. A brown bag session provides an opportunity to persuade and influence both the experts and the attendees. Regardless of your position on a topic, a brown bag session is a good opportunity to create a personal connection.
Brown bag sessions can also be divided by type of security policy. For example, a new policy on acceptable email use might be of particular concern to customer service. A security team member might be the selected expert to help explain why the new policy has been implemented and talk through how email communication with customers might change.
