Case Studies and Examples of Successful IT Security Policy Compliance Monitoring
The following sections show different case studies and examples related to IT security policies and compliance monitoring. Private sector and public sector case studies and examples are included.
Private Sector Case Study 1
In this example, a large sales organization with a dedicated IT staff suffered a major outage due to a minor change to a printer. The lack of compliance with change management policies was a contributing cause for the outage.
The organization had a subnet hosting multiple servers and a printer. Routers connected this subnet to other subnets on the network. All systems were working until a new server was added to the network with the same IP address as the printer. This IP address conflict prevented the printer from printing and prevented the new server from communicating on the network. This problem is like having two identical street addresses in the same Zip code. At best, each address will get some mail, but not all of it. Similarly, on a network, each IP address will receive some traffic, but not all traffic that is expected. At best, you will see inconsistent performance.
The problem with the new server wasn’t discovered right away. However, a technician began troubleshooting a problem with the printer on the same subnet. While troubleshooting, the technician suspected a problem with the IP address. The technician changed the IP address for the printer to 10.1.1.1, as shown in FIGURE 15-4. This change didn’t solve the problem, but the technician forgot to change the IP address back to normal. As you can see in the figure, the change caused a conflict between the printer and the default gateway. The printer and the near side of the router both had the same IP address, and neither was working.
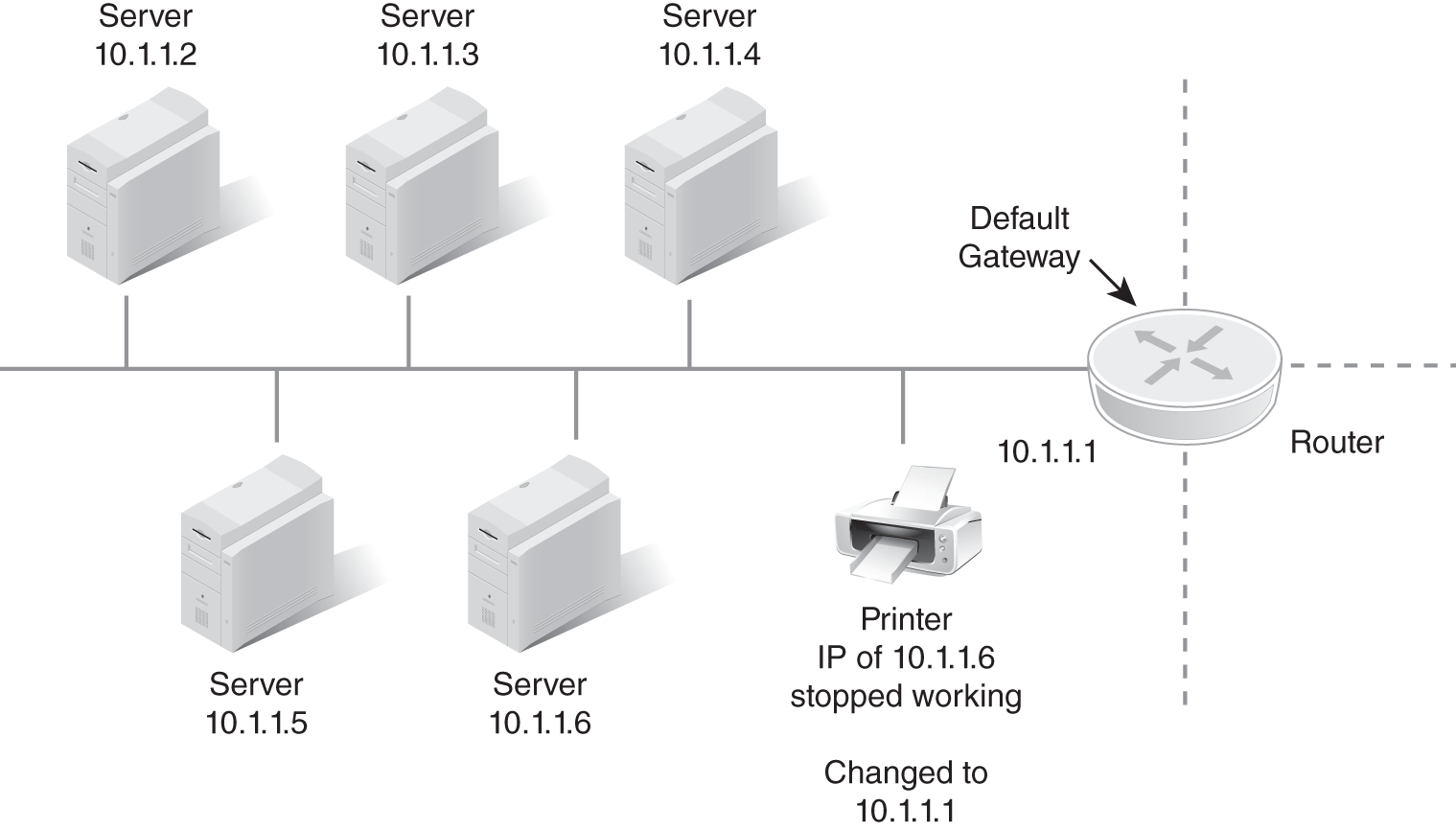
FIGURE 15-4 Misconfigured printer results in outage for multiple servers.
The default gateway is the path for all server communications out of the subnet. Because there was a conflict with the default gateway, none of the servers on the subnet was able to get traffic out of the subnet. They were all operating, but clients outside of the subnet couldn’t use them. With several servers no longer working, the problem was quickly escalated. Senior administrators were called in and discovered the problems. They corrected the IP address on the printer and provided some on-the-job training to the original technician.
Notice how this problem started with a small error. The new server was added using an IP address that was already used by the printer. After the printer IP address change, all the servers on the subnet lost network access. Change management and configuration management processes would have ensured this new server was added using a configuration that didn’t interfere with other systems. Additionally, change management would have prevented the change to the printer’s IP address.
As it turns out, this was the turning point for this company. It was one of a long string of problems caused by unauthorized changes. Management finally decided to implement a formal change management process and hired an outside consultant to help them.
Private Sector Case Study 2
In 2018, there was a breach of the Marriott hotel chain. Personal and financial information of 500 million guests over a four-year period was exposed. The breach involved unauthorized access to a database on or around September 10, 2018.
The hotel chain revealed that for many of those records, the data could include birth date and passport number. In some cases, the data also included payment card numbers and payment card expiration dates, but the payment card numbers were encrypted using Advanced Encryption Standard encryption (AES-128). Thus, it is unlikely the attackers could decrypt that data.
Thus, this case study has mixed results. The breach itself was egregious. However, the fact that credit card information was encrypted, as per PCI DSS, may ameliorate the impact of the breach. Conversely, many security analysts opine that the breach should have been detected sooner.
Nonprofit Sector Case Study
This is an older case study, but still relevant today. In June 2013, it was reported that Stanford University’s Lucile Packard Children’s Hospital had had a data breach. An employee reported on May 8, 2013, that an unencrypted laptop containing medical information on pediatric patients had been stolen. The laptop contained personal information on 13,000 patients, including their names, ages, medical record numbers, and surgical procedures, as well as the names of physicians involved in the procedures, and telephone numbers. The computer involved was no longer in use; it was, in fact, nonfunctioning. But it had not been properly disposed of when it was taken out of service.
This was the fifth major data breach for the hospital within a space of four years. In January 2013, to give another example, the hospital reported that a laptop containing medical information for 57,000 patients had been stolen from a physician’s car.
These events show a lack of compliance with HIPAA regulations. Encrypting laptops with sensitive information is a de facto standard in the healthcare industry. It’s also a requirement for many regulations, including those of HIPAA.
So how could this happen when the regulations and industry best practices are clear? That there were five major breaches within such a brief period suggests a systemic failure of the university to define its security policies, train its staff, and then hold them accountable with strict enforcement.
The Stanford episodes highlight three areas worth thinking about:
- Policy enforcement
- Awareness training
- Equipment disposal
With HIPAA standards and industry best practices so clear, you might assume that policy enforcement was lacking. There should have been a complete inventory of laptops and a crosscheck to ensure they were all encrypted.
Enforcement needs to be aggressive. Some organizations are very strict about enforcing these policies. For example, all laptops are required to be encrypted before they are issued. Scans are performed regularly to ensure laptops remain encrypted. When a device is found to be unencrypted (as in the case of an older or “legacy” device), the user is given a short window—a matter of days—to have it encrypted. A user who fails to comply loses access, and leadership is notified to take management action. Having a consequence for failing to follow security policy is an important enforcement tool.
University officials cited new and improved “HIPAA training” being put in place. This again might suggest that policies were in place but were not followed. Congress enacted HIPAA in 1996. The law’s requirements are well defined and known. The need to put new HIPAA training in place suggests a lack of employee awareness. If this is one of the causes, it illustrates that having a good policy is not enough. Compliance with the policy depends on a skilled workforce that embraces its implementation as part of day-to-day duties.
Equipment disposal seems the most puzzling part of the story. Why a broken device was still in the possession of the end user is confusing. As soon as a device is disabled, it should be immediately turned over to IT personnel and the information contained within properly disposed of. In this case, the delay in turning over the old device seems inappropriate. The employee had been issued a new device and the old laptop was considered “nonfunctional.” Many organizations in such a case would insist on receiving the damaged device before issuing a new one. This is a good policy.
It is also interesting that university officials emphasized that the “nonfunctioning” laptop had “a seriously damaged screen.” The screen has nothing to do with the data contained within the laptop. Offering screen damage as a reason to be less concerned about the theft of the device raises questions about officials’ understanding of the threat. The hard drive is what matters. A laptop screen can be replaced or, even more easily, bypassed with an external monitor. Or the hard drive can be quickly moved to another machine.
 NOTE
NOTE
Always remember, breaches are about the data. Regardless of the damage to a physical device, as long as the hard drive is intact, the data on a stolen machine is at risk. That’s why encrypting the hard drive of a portable device is considered an industry best practice in many cases.
