What Are Information Systems Security Policies?
Security policies are actually a collection of several documents. They generally start with a set of principles that communicate common rules across the enterprise. It is these principles that governance routines use to interpret more detailed policies. Principles are expressed in simple language. An example may be an expression of risk appetite by employing the “need-to-know” approach to the granting of access. From these security principles flow security policies that detail how the principles are put into practice.
When combined, these policy documents outline the controls, actions, and processes to be performed by an organization. An example is the requirement that a customer provide a receipt when returning an item to a retail store for a refund. That may be a simple example of a policy, but essentially, it places a control on the return process. In the same manner, ISS policies require placement of controls in processes specific to the information system. ISS policies discuss the types of controls needed but not how to build the controls. For example, a security policy may state that some data can be accessed only from the office. How the security control would be built to prevent remote access, for example, would not appear in the policy.
ISS policies should cover every threat to the system. They should include protecting people, information, and physical assets. Policies should also include rules of behavior such as acceptable use policies. The policies must also set rules for users, define consequences of violations, and minimize risk to the organization. Enforcement will depend on the clarity of roles and responsibilities defined in policies. Remember, you need to hold people accountable for policies. When it’s unclear who is accountable, a policy becomes unenforceable. Other documents in the policy framework provide additional support.
There are typically six different types of documents in a framework:
- Principles—Establish the tone at the top and the authority by which policies are enforced
- Policy—A document that states how the organization is to perform and conduct business functions and transactions with a desired outcome
- Standard—An established industry norm or method, which can be a procedural standard or a technical standard implemented organization-wide
- Procedure—A written statement describing the steps required to implement a process
- Guideline—A parameter within which a policy, standard, or procedure is suggested but optional
- Definitions—Statements that define the terms used in the policy documents and set the context in which the policies documents are interpreted
Many people refer to all these documents as “security policies,” but they aren’t necessarily. FIGURE 1-5 depicts the relationship among these six types of documents. The figure shows that procedures and guidelines support policies. In addition, the figure indicates that standards influence policies. The six documents fall into two groups: internal and external. Standards are external documents. The other five are internal documents.
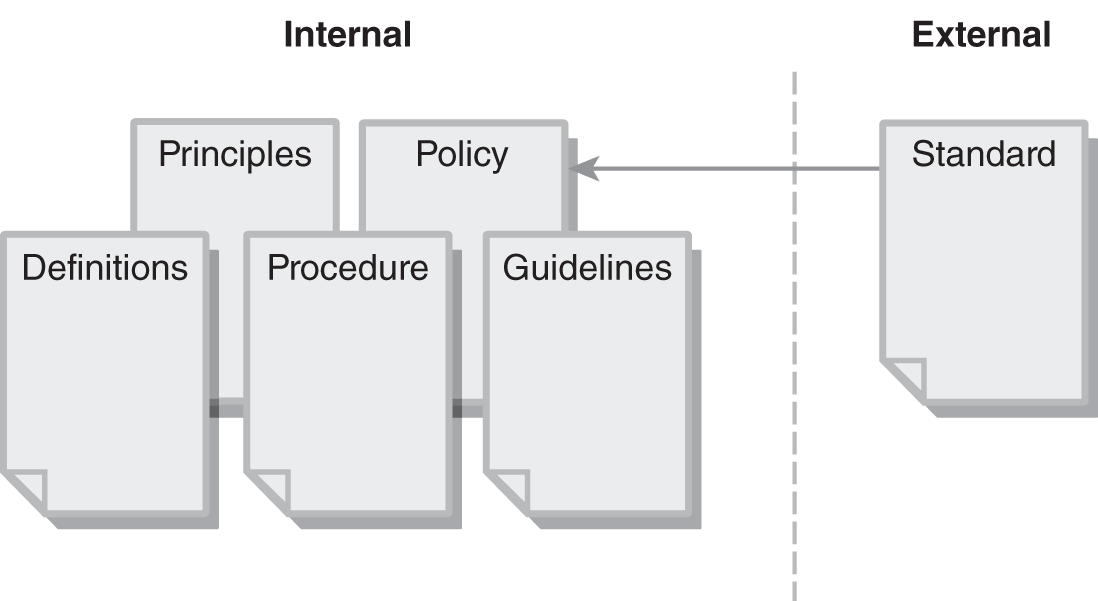
FIGURE 1-5 Internal versus external documents.
A standard can be a process or a method for implementing a solution. This involves technology, hardware, or software that has a proven record of performance. This can be a procedural or implementation standard or a technical deployment standard implemented company-wide. For the purposes of ISS, a standard is the set of criteria by which an information system must operate. Standards exert external influence on the creation of policies. An organization can have internal standards. Often these standards are tailored to the organization based on some external best practice. The proper application of standards provides assurance that lessons learned within the industry have been considered.
 NOTE
NOTE
Standards become the measuring stick by which an organization is evaluated for compliance. The Federal Information Processing Standards (FIPS) publications are examples of standards. You can view FIPS publications online at https://www.nist.gov/itl/publications-0/federal-information-processing-standards-fips.
A policy principles document communicates general rules that cut across the entire organization. Principles are written in plain English and focus on key risks or behaviors. When reading security principles, think of them as senior executives expressing their goals and objectives. They express core values of the organization that often include the areas where there will be zero tolerance for transgression.
A policy is a document that states how the organization is to perform. It describes how to conduct business functions and transactions with a desired outcome. It sets the stage for secure control of information. It is the “who does what to whom and when” document. It should reflect what leadership commitments are to protecting information. Defined roles and responsibilities lay the foundation for enforcing the policy.
 NOTE
NOTE
A policy is often approved by the most senior levels of management. A procedure or guideline is often approved by lower-level management responsible for the implementation of policies.
A procedure is a written statement describing the steps required to implement a process. Remember that procedures support policies and standards. Procedures describe how to accomplish specific tasks. A more detailed procedure produces a more error-free result. Procedures are not written just for humans to follow. Well-written procedures are often used to document requirements for automated processes.
A guideline sets the parameters within which a policy, standard, or procedure can be used. A guideline is optional. It is a policy-support document. Similar to procedures, guidelines help businesses operate more smoothly. They are not as rigid. Although optional, they set a direction to be taken whenever possible. Once the new approach has been widely adopted, a guideline can transition into a policy.
A policy definitions document is often overlooked, yet it’s enormously important. It’s often used by auditors and regulators when evaluating the soundness of controls. Think of it this way: If you and someone else were speaking two different languages, you might recognize some of the other person’s words. Yet, the depth of the meaning of these words could easily get lost. Even common words can have many meanings in the context of a policy. For example, if a policy refers to a user ID, does the policy apply to nonhuman and human IDs equally? If the term platform is used, does it mean desktop or server or router? Words in policies must be rich in meaning, clear, and concise. A well-constructed policy dictionary is key to achieving this goal.
How Policies and Standards Differ
Now that you know what policies are, let’s discuss the difference between policies and standards. Policies implement controls on a system to make it compliant to a standard. Standards influence the creation of policies. Standards often determine a minimum requirement but can be very detailed in nature. Laws or agreed-upon practices produce standards. Standards then become the criteria for governance or certification and accreditation.
Standards often start with industry norms. Over time, organizations that represent the industry develop and publish standards. These standards often become the measuring stick by which regulators judge organizations. It’s not uncommon for a company to adjust standards to meet specific needs, and then republish them internally as a company standard or internal policy.
Be cautious when deviating too far from industry standards. There are both civil and legal penalties for not following them. Consider the Payment Card Industry Data Security Standard (PCI DSS). It calls for the following penalties:
- Fines of $500,000 per data security incident
- Fines of $50,000 per day for noncompliance with published standards
How Policies and Procedures Differ
In a similar manner, you can contrast the difference between policies and procedures. As a reminder, policies are requirements placed on processes. Procedures are the technical steps taken to achieve those policy goals. Procedures can contain step-by-step instructions on the performance of a task. They can also identify how to respond to an incident.
Within a policy framework, there could exist a policy stating the requirement for disaster recovery planning. A separate procedural document would call out specific tasks to provide recovery services. In other words, procedures are the how-to document.
