The Seven Domains of a Typical IT Infrastructure
Examining risk from a data perspective involves following data through an end-to-end process. As you move through your technology infrastructure, you’ll find similar risk and policy issues. There are many ways to group security policies. A common method is to group common risks and related policy issues into domains. These domains share similarities but are distinctive enough to allow logical separation into more manageable security areas. An advantage of this method is that each domain typically focuses on a different target audience. This means security awareness and training can be more precisely targeted. Recall the McCumber cube introduced in Chapter 1; it looked at security from multiple perspectives including data at rest, data in transit, and data in processing.
In this section, you will learn the definition of these domains. This section examines the attributes of each domain so you can gain a better understanding of the issues. Later in the chapter, you will examine the business issues and policy challenges of these problems, along with risk mitigation techniques.
FIGURE 4-1 illustrates seven typical domains of an IT infrastructure, which include:

FIGURE 4-1 The seven domains of a typical IT infrastructure.
- User—This domain refers to any user accessing information. This includes customers, employees, consultants, contractors, or any other third party. These users are end users.
- Workstation—This domain refers to any endpoint device used by end users. This can mean any smart device in the end user’s physical possession. For the purposes of this chapter, it’s any device accessed by the end user, such as a smartphone, laptop, workstation, or mobile device.
- LAN—This domain refers to the organization’s local area network (LAN) infrastructure. A LAN connects two or more computers within a small area. The small area could be a home, office, or group of buildings.
- WAN—A wide area network (WAN) covers a large geographical area. The Internet is an example of a WAN. A private WAN can be built for a specific company to link offices across the country or globally. Many businesses use the Internet for communicating between offices and regions. The Internet has become so inexpensive and reliable that it is often the first choice of businesses. Communications are typically secured through the use of encryption.
- LAN-to-WAN—This domain refers to the technical infrastructure that connects the organization’s LAN to a WAN. This allows end users to access the Internet. Communications flow in both directions in the LAN-to-WAN domain.
- Remote Access—This domain refers to the technologies that control how end users connect to an organization’s LAN. A typical example of remote access is someone connecting to the office network from a home computer. End users can use a WAN to access a LAN; for example, an end user could use the Internet to create a private and secure session to connect with the office through a virtual private network (VPN) connection.
- System/Application—This domain refers to the technologies needed to collect, process, and store information. The System/Application domain includes hardware and software.
Although there are many advantages to grouping policies in this way, it can be hard to understand how data is controlled. In other words, it could be challenging to understand the end-to-end layers of controls. One way to overcome this challenge is to map business requirements by examining each of these logical segments. These requirements provide constraints upon end users and ultimately determine how security controls are designed.
Take a look at each of the seven domains to better understand how data is treated and how many common constraints are placed on them by the business.
User Domain
The User domain refers to any end user accessing information in any form. This includes how end users handle physical information such as printed reports. Control of physical information starts well before someone ever touches a keyboard. It must start with end user awareness of policies and on-the-job training. As good as an awareness program is, formal education programs are no substitute for the experience gained from on-the-job training. Onboarding refers to new employee training. Even if your organization doesn’t have a formal on-the-job training program, something as simple as giving someone a “buddy” to show him or her how the area operates often achieves many of the same goals.
 WARNING
WARNING
How coworkers treat data can significantly influence an employee’s behavior beyond any formal awareness training. Regardless of training, if coworkers and management treat policies as unimportant, a new employee might also treat policies as unimportant.
An end user must be familiar with several key policies before accessing company information. Some of the more important policies you should include in an awareness training program include:
- Acceptable use policy—An acceptable use policy (AUP) establishes a broad set of rules for acceptable conduct when a user accesses information on company-owned devices. For example, this policy may set rules on what type of website browsing is permitted or if personal emails over the Internet are allowed.
- Email policy—An email policy discusses what’s acceptable when using the company email system. The policy is much more specific than the broad statements found in an AUP policy.
- Privacy policy—A privacy policy addresses the importance the organization places on protecting privacy. It also discusses the regulatory landscape and government mandates. This policy discusses how to handle customer data as well as the individual obligation to protect the information.
- System access policy—A system access policy includes rules of conduct for system access. This policy covers end user credentials like IDs and passwords. The policy may also be specific to the business or application.
- Physical security and clean desk policy—The physical security and clean desk policy outlines conduct in the workplace. It typically covers the expectation that employees will lock up sensitive information before going home at the end of the workday. This is what the term clean desk refers to.
- Corporate mobility policy—An organization’s corporate mobility policy sets expectations on the use and security of mobile devices. This policy could also set requirements on using personal devices to access company systems. For example, there is a growing trend of allowing personal smartphones to access company email systems. This reduces costs because the company does not have to issue phones. But it also creates new risks, because companies have less control over devices they do not own.
- Social networking policy—The social networking policy has emerged as a type of code of conduct. With the rise of social media, many businesses are concerned about employees posting information about the company on these sites. This policy provides guidance to employees. For many organizations, posting any information about the business beyond the employee’s name and title is strictly forbidden.
Authentication is one of the most important components of the User domain. You must determine an authentication method that makes sense for your organization. Your authentication method must also meet business requirements.
The use of user IDs and passwords as authentication methods remains a minimum standard for many organizations. It is considered a foundational control for many businesses. The ID and password can be widely used, and a password can be easily reset in the event an end user forgets it. The low cost and high efficiency of this method of authenticating users also represent its greatest weakness. Because IDs and passwords have been used throughout the history of modern computing, exploits of this authentication method continue to be refined. More advanced mechanisms, such as two-factor authentication, are being implemented more widely. These methods are designed to overcome the weaknesses of bad passwords or of someone guessing a password. For many businesses, however, IDs and passwords alone are not enough. In addition to two-factor authentication, there are many methods to improve the authentication process. Authenticating the end user device in combination with the ID and password provides a stronger authentication method. For example, access may be restricted only to work hours on devices issued by the business for employees with a valid ID and password. Although the ID and password may be compromised, the risk is reduced because access would be denied on noncompany computers.
The best and most common method for ensuring you know who is being authenticated is to restrict access to an ID and password to a single individual and force individuals to change their password often. The key lesson is that authentication must make sense in the business context in which you use it.
Another key component is authorization. Authorization is especially important in large, complex organizations with thousands of employees and hundreds of systems. Authorization is what takes place once the user is authenticated. The next step is to determine what the user has access to. The single most important concept, regardless of the authorization method used, is to obey the principle of least-privileges. Any users should only be authorized to access data/take actions directly required by their job role and no more. No matter how trusted and how well trained the user is, he or she should be given access to only enough to do his or her job. The authorization method must clearly define who should have access to what. One popular method is role-based access control (RBAC). In this method, instead of granting access to individuals, you assign permissions to a role. Then you assign one or more individuals to that role.
The huge advantage of RBAC is speed of deployment and clarity of access rights. Let’s assume you hire an accountant named Nikkee and you grant her access to 12 systems, many spreadsheets, email folders, and more. If you had to grant that access to her individual ID, it could take you days or even weeks. Given the complexity of a system, you may need to grant hundreds of permissions. The volume of permissions means there is a good chance of an error by missing something or granting too many rights. Now let’s assume you hire a second accountant named Vickee. You would have to start the process over again to grant her rights to the systems, spreadsheets, and so on. What’s even more time-consuming is if one of these individuals leaves, you must go through a similar process to remove her access.
Instead, let’s assume you previously set up a role called “Accountant” and granted all necessary permissions to this role. Creating a new account would take the same time as creating a single user without RBAC. But creating a role is a one-time event. When you hire Nikkee and Vickee, you can connect their IDs to the Accountant role, quickly giving them access to the systems, spreadsheets, and email folders they need to perform their jobs. Now let’s say Vickee is promoted. You can quickly remove her ID from the Accountant role and place her ID in a Senior Accountant role. You reduced deployment time for these individuals from days or weeks to hours or minutes. By listing the people connected to the roles and the permissions within the roles, you can clearly see who has access to what business resources. This clarity of access helps an organization control access to its critical processes, manage its risk, and prove to regulators that it manages customer data properly. FIGURE 4-2 illustrates the RBAC concept.
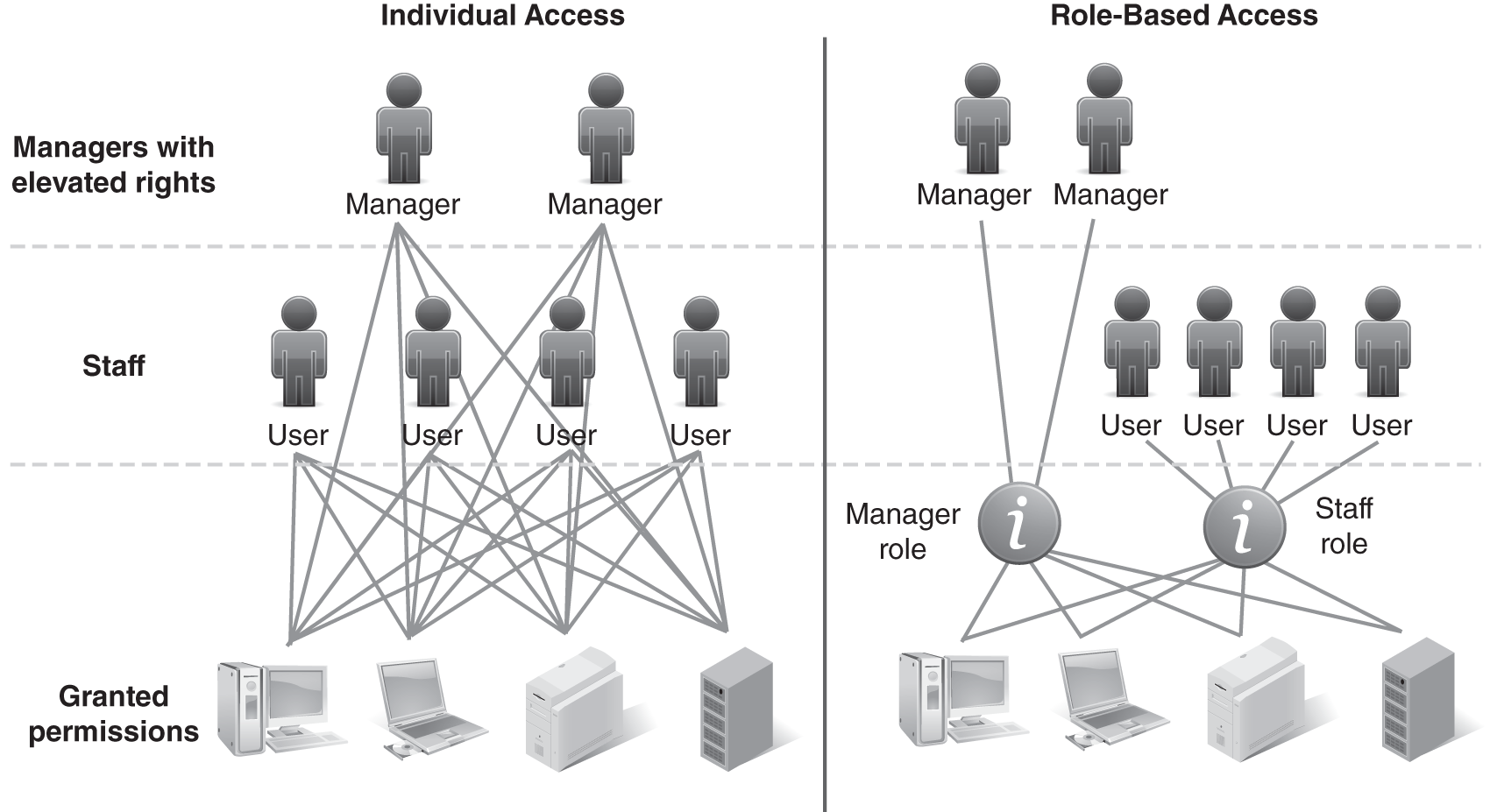
FIGURE 4-2 Role-based access control concept.
RBAC is effective, but other methods have been developed. In January 2014, NIST issued publication 800-162, entitled “Guide to Attribute Based Access Control (ABAC).” Attribute-based access control (ABAC) relies on specific attributes associated with the login. For example, if a loan officer logs in from a bank computer during normal business hours, he may be given broader access than if the same loan officer logs in from a remote computer in a foreign country from an IP address he has never used before. The attributes are all the properties about the login. The source of the login, the time of day, and the nature of the activity are all considered.
You might allow a travelling salesperson to log in from Malaysia, but not your accountant. Or, you may allow the accountant to log in, but only to read files, not to delete data. Clearly, setting up ABAC is a bit more complicated, but well worth the effort. You may have encountered a primitive version of ABAC when logging in to your bank’s website. If you log in from a different machine, one that has not been previously used to log in, there might be additional login steps. A common step is to text a code to the user’s phone that must also be entered. This is a primitive, rather limited version of ABAC.
To add a bit more detail to ABAC, the model essentially looks at attributes and then applies a simple Boolean logic. The attributes can be user attributes, resource attributes (what is being accessed and how), environmental attributes (where is the access from, what time of day, etc.), or any other attribute that is relevant. These systems are sometimes called claims-based access control (CBAC) or policy-based access control (PBAC). The term PBAC is used due to the fact that the decision-making process is often governed by policies. A policy might state that users can be granted access only within the continental United States or that remote users have limited rights and increased logging/monitoring.
Workstation Domain
The Workstation domain includes any computing devices used by end users. Usually, the term workstation refers to a desktop or laptop computer; however, a workstation in the context of this chapter can be any end user device that accesses information. Control on your handheld device, like a smartphone, would fall within this domain.
 NOTE
NOTE
For the purposes of this chapter, the term workstation refers to any end user device that accesses information.
Usually, when an end user seeks to access information, he or she authenticates in the User domain. Once he or she is known, the end user is often authorized to the workstation itself. Each workstation has an identity much like an end user. Not only can you restrict end users to specific workstations, but you can also restrict what workstations are allowed on your network. This is important when connecting to a network wirelessly because wireless access may be available to the public. Most wireless access points restrict which devices can access the internal network. Wireless access points should also encrypt the traffic between the authorized wireless device and the entry point for the LAN.
 NOTE
NOTE
Authentication of a workstation and encryption of wireless traffic are Workstation domain and LAN domain issues. The assignment of a workstation identity and configuration of the wireless protocol is a Workstation domain issue. The authentication and encryption of the traffic is a LAN domain issue.
The Workstation domain defines the controls within the workstation itself, such as limiting who can install software on the workstation. Some end users share a workstation; therefore, it is important that settings be stable and that one end user not be able to affect another. To achieve this, end users often have limited rights on workstations. That means they can typically access the software that’s been installed, and they have some rights to configure the software to their needs, but they do not have unlimited rights to make changes that could affect another user. This also ensures that an end user does not inadvertently infect the workstation with a virus or malware. Most domain controls ensure that appropriate antivirus software is loaded and runs on each workstation.
A central management system typically manages workstations such as Microsoft System Center Configuration Manager (SCCM). Note that although many still use the old name, Microsoft has changed it to Microsoft Endpoint Configuration Manager. The Microsoft Endpoint Configuration Manager combines System Center Configuration Manager and Systems Management Server. These management systems have evolved over time and help an organization save time and money, and greatly improve response time. Can you imagine having to visit hundreds or thousands of desktops individually to apply a patch or install a piece of software? Fortunately, those days are long over.
Regardless of the management software used, different brands all generally share many of the same capabilities. The key functionalities to look for are these:
- Inventory management—An inventory management system tracks devices as they connect to the LAN. This builds an inventory of which devices are on the network and how often they connect to the LAN. Information inventories are useful for investigating security incidents and ensuring regulatory compliance.
- Discovery management—A discovery management system detects software that is installed on a device. It can also detect information on a workstation. This is highly specialized software that is not routinely used.
- Patch management—A patch management system ensures that current patches are installed on devices. It’s important to apply security patches in a timely manner to address known vulnerabilities.
- Help desk management—A help desk management system provides support to end users through a help desk. Help desk technicians may remotely access a device to diagnose problems, reconfigure software, and reset IDs.
- Log management—A log management system extracts logs from a device. Typically, log management software moves logs to a central repository. Typically, the volume of logs is so large that it takes special software to automatically search and highlight potential risks. Administrators scan these logs to find security weaknesses or patterns of problems.
- Security management—A security management system manages workstation security. This may include ensuring end users have limited rights and that new local administrator accounts are not present. The unexpected addition of local administrator accounts may be an indication that a security breach has occurred.
With the widespread adoption of personal handheld devices, a number of issues have become important in the Workstation domain. It is likely that users within your organization have their own devices. These devices, if allowed to connect to your network, become workstations. This brings up several questions regarding security, but the most important is whether or not to allow such devices to connect. The common approaches are:
- Bring your own device (BYOD)—With bring your own device (BYOD), users are allowed to bring their own device to work and to connect to the network. This is sometimes augmented with specific security requirements, and in some cases Network Access Control (NAC). NAC scans the device to ensure it complies with security requirements.
- Choose your own device (CYOD)—Users are given a list of approved devices, and if the user purchases one of those, they can connect it to the company network.
- Company-owned and -provided equipment (COPE)—The company or organization provides devices. This has the advantage of allowing greater control over security, but it can be cost prohibitive.
Whatever the choices made, the issue of personal devices must be addressed. Currently, these are primarily smartphones; however, implantable medical devices, smart eyewear, exercise/fitness devices, and other networked devices are becoming increasingly common.
LAN Domain
The LAN domain encompasses the equipment that makes up the LAN. A LAN typically has network devices that connect a local office or buildings. A LAN can be either simple or complex. If you have a wireless network device at home, you have a simple LAN. Let’s say you have a home cable modem connected to a wireless device, which is usually called a wireless router. The wireless router creates a LAN, bridging your cable modem to your home computer. This wireless router is your LAN access point to the Internet.
The following are definitions for common network devices found on LANs:
- Switch—A switch is similar to a hub, but it can filter traffic. Hubs are old technology that don’t really exist today. A hub would simply send copies of all traffic out all ports. That quickly proved inefficient and was replaced by switches. You can set up rules that control what traffic can flow where. Unlike hubs, which duplicate traffic to all ports, a switch is typically configured to route traffic only to the port to which the system is connected. This reduces the amount of network traffic, thus reducing the chance that someone will intercept communications. Switches direct traffic based on the destination media access control (MAC) address. Thus, they are only used internally in networks.
- Router—A router connects LANs, or a LAN and a WAN. Routers direct traffic based on the destination IP address, as well as rules programmed into the router.
- Firewall—A fire wall is a software or hardware device that filters traffic into and out of a LAN. Many can do deep-packet inspection, in which the firewall examines the contents of the traffic as well as the type of traffic. You can use a firewall internally on the network to further protect segments. Firewalls are most commonly used to filter traffic between the public Internet WAN and the internal private LAN.
A LAN in the business world is far more complex than a home LAN and has many layers of controls. This chapter looks at two general types of LANs, flat and segmented networks.
A flat network has few controls, or none, to limit network traffic. When a workstation connects to a flat network, the workstation can communicate with any other computer on the network. Think of a flat network as an ordinary neighborhood. Anyone can drive into the neighborhood and knock on any door. This doesn’t mean whoever answers the door will let the visitor in; however, the visitor has the opportunity to talk his or her way in. In the case of flat networks, you can talk your way in by being authorized or by breaching a server, for instance, by guessing the right ID and password combination. Flat networks are considered less secure than segmented networks because they rely on each computer (i.e., each home on the block) to withstand every possible type of breach. They are also less secure because every computer on the network can potentially see all the network traffic. This means a computer with a sniffer can monitor a large portion of the communication over a LAN. A sniffer can capture the traffic on a network. This includes recording IDs and passwords in the clear. So, if there’s a special code, secret knock, or handshake at the door, it has also been recorded. That’s why most security policies require passwords to be encrypted when passed through the network.
 NOTE
NOTE
Many standards require network segmentation. Payment Card Industry Data Security Standard (PCI DSS), for example, requires network segmentation to further protect credit cardholder information. Segmented networks allow different security policies for different segments. Your database servers probably require higher level security than does the front desk workstation.
A segmented network limits what computers can say to each other and how they are able to talk to each other. By using switches, routers, internal firewalls, and other devices, you can restrict network traffic. Continuing the analogy from the previous paragraph, think of a segmented network as a gated community. To access that neighborhood, you must first approach a gate with a guard. The guard opens the gate only for certain traffic to enter the community. Once inside, you can knock on any door. A segmented network acts as a guard, filtering out unauthorized network traffic. Frankly, any network that is more than trivial in size should be segmented.
LAN-to-WAN Domain
The LAN-to-WAN domain is the bridge between a LAN and a WAN. A LAN is efficient for connecting computers within an office or groups of buildings; however, to connect offices across the country or globally you need to connect to a WAN. Generally, routers and firewalls are used to connect a LAN and WAN. The Internet is a WAN. Like many WANs, the Internet is public and considered unsecure. FIGURE 4-3 illustrates the basic LAN-to-WAN network layers.
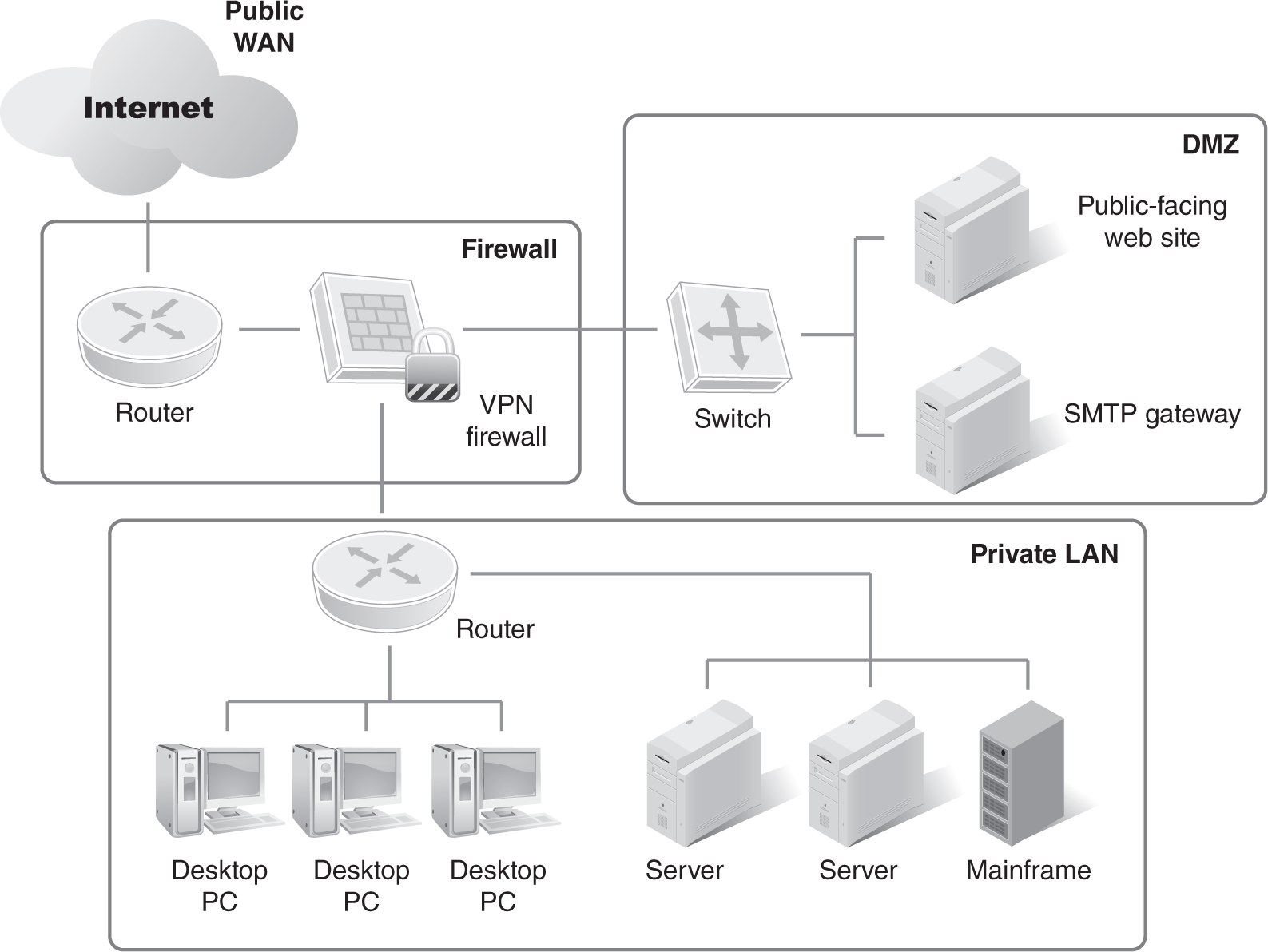
FIGURE 4-3 Basic LAN-to-WAN network layers.
How do you move data from an unsecure WAN to a secure LAN? Typically, you begin by segmenting a piece of your LAN into a demilitarized zone (DMZ). The military uses the term DMZ to describe a buffer between two opposing forces. The DMZ sits on the outside of your private network facing the public Internet. Servers in the DMZ provide public-facing access to the organization, such as public websites. By definition, you must allow more people to access your web server than you would allow to access your internal network. The DMZ will allow public access to servers such as web servers, while preserving the more robust access control within your network. Sitting between the DMZ and internal network are firewalls that filter traffic from the DMZ servers to the private LAN servers. Often, the DMZ sits between two layers of firewalls. The first firewall allows limited Internet traffic into the DMZ, and the second highly restricts traffic from the DMZ servers into the private network.
There are a number of different network architecture designs that can be used to connect your internal private LAN with the external Internet WAN. The key point is to understand that you need some layer of firewalls to limit traffic between these domains. Creating a network segment like the DMZ as a buffer between the LAN and WAN is a good way to protect your private network.
In recent years, some firewalls have added behavior and heuristic checks. Basically, this means the firewalls learn over time what “normal” looks like. By recording volume and type of traffic, they create a pattern. When these behaviors change dramatically, firewalls can limit traffic and alert the security teams. For example, assume typical overseas customers represent 3 percent of your website’s traffic, but then suddenly turn into 99 percent of your traffic. This could be an indication of a potential breach, especially if that country of origin is known to be a source for hacks. Although each individual transaction looks valid, collectively the pattern can trigger firewall rules to restrict access.
WAN Domain
The WAN domain, for many organizations, is the Internet. Alternately, large organizations can lease dedicated lines and create a private WAN. However, as connectivity to the Internet has become more reliable, many organizations have switched from private WANs to using the Internet to connect offices all over the world.
A challenge for companies using the Internet to connect offices is how to keep communications secure and private. A common solution is a virtual private network (VPN). By setting up network devices at both offices, you can create an encrypted tunnel through the Internet. The tunnel protects communication between the offices from eavesdropping. You can use a dedicated network device whose only function is to create and manage VPN traffic. These devices are VPN concentrators. Many firewalls also have the capability to create and maintain a VPN tunnel.
Organizations can lower communication costs by using VPN tunnels instead of leasing private lines for WANs. Beyond cost, there’s also the issue of time. Leased lines for WANs can take weeks to months to order, contract for, install, and set up. Most companies already have an Internet connection. They can add VPN-compatible devices at both ends to establish a VPN tunnel in days. For small and medium-size companies, it’s the only practical solution given the cost and technical complexities.
Cloud computing has emerged as a major technology. Sources predict cloud computing in the United States will reach $150 billion by the end of 2020.2 Forbes predicts it will be over $300 billion by the end of 2022.3 Eighty-one percent of all enterprises are already implementing or working on cloud computing strategies. McAfee reports that the average employee actively engages with over 30 cloud services.4 By any measure, cloud computing is becoming ubiquitous. Most projections show that this will continue to grow in coming years.
Think of cloud computing as a way of buying software, infrastructure, and platform services on someone else’s network. You rent this capability when you need it and stop paying when you are done. It’s like renting a car: If you have out-of-town guests, you might rent a large van while they are in town. Your costs are incurred during their stay. When your guests leave, you return the van and go back to driving your two-seat sports car. Likewise, cloud computing allows you to rent additional computing power when you need it and release it when the demand is low. Access to cloud computing is typically through the WAN (i.e., Internet).
Remote Access Domain
The Remote Access domain is nothing more than an enhanced User domain. The only difference is that you are traveling from a public unsecure network into the private secure company network. You have all the issues you have in the User domain plus special remote authentication and network connectivity issues.
Remote authentication has always been a concern because the person is coming from a public network. Do you truly know that individual is an employee, or is he or she a hacker pretending to be an employee? There’s less of a concern when accessing the network within the office. The office might have guards at the entrance, locked doors, badges, and visibility of people sitting at workstations. Over the Internet, how do you know who’s on the other side of the wire? Most organizations today feel that an ID and password combination is not an adequate authentication method for remote access.
Many companies require two-factor authentication for remote access. Two-factor authentication requires an end user to authenticate his or her identity using at least two of three different types of credentials. The three most commonly accepted types of credentials are as follows:
- Something you know—Refers to something only you are supposed to know, such as your ID and password combination. You should never share your password with anyone.
- Something you have—Refers to a unique device that you must have in your physical possession to gain access. This physical device could be your computer itself. In general terms, all devices have identities, from your laptop to your phone. The physical device you are logged on with can be used as a way of verifying your identity.
- Something you are—Refers to some sort of biometric feature such as a fingerprint scanner.
Technical TIP
There are many ways to verify a computer’s identity. A common method is using digital certificates. In general terms, the certificate acts like a digital fingerprint. Of course, this requires issuing digital certificates to all computers you wish to have connect to your system. This is useful in verifying that the user is on a specific computer. For example, suppose a bank wants to make sure any money wired is sent from only one computer in a locked room. That would provide both a physical and logical control over sending money. The wire application could verify the digital fingerprint of the remote computer to verify that any wire request is coming from a specific authorized computer.
Many organizations today require two-factor authentication for remote users. The authentication factors may be an ID/password combination (something you know) plus some type of token or smart card (something you have) to authenticate remote access. This provides a high level of confidence that the remote user is an employee. Some tokens can be loaded directly to the company laptop. The laptop becomes something you must have to connect remotely.
 NOTE
NOTE
In 2012, the Federal Financial Institutions Examination Council (FFIEC) issued guidance entitled “Authentication in an Electronic Banking Environment.” It requires financial institutions go beyond using just IDs and passwords. It requires banks to use multifactor authentication more widely.
Remote network connectivity has the issues previously discussed with WAN domains: how to keep communications secure and private. A VPN is typically the solution. You can configure a VPN to permit only predefined workstations to be connected. Each site has a dedicated hardware device that creates an encrypted tunnel through the Internet. This is typically called a site-to-site VPN connection. A remote user can also create a VPN tunnel. Instead of having VPN hardware at home, you have a desktop or laptop with software called a VPN client. This VPN client communicates with the VPN hardware to create the same type of encrypted tunnel through the Internet. This is typically called a client-to-site VPN connection. In both cases, VPN is used to secure the communication through the Internet. FIGURE 4-4 illustrates the site-to-site and client-to-site connectivity.
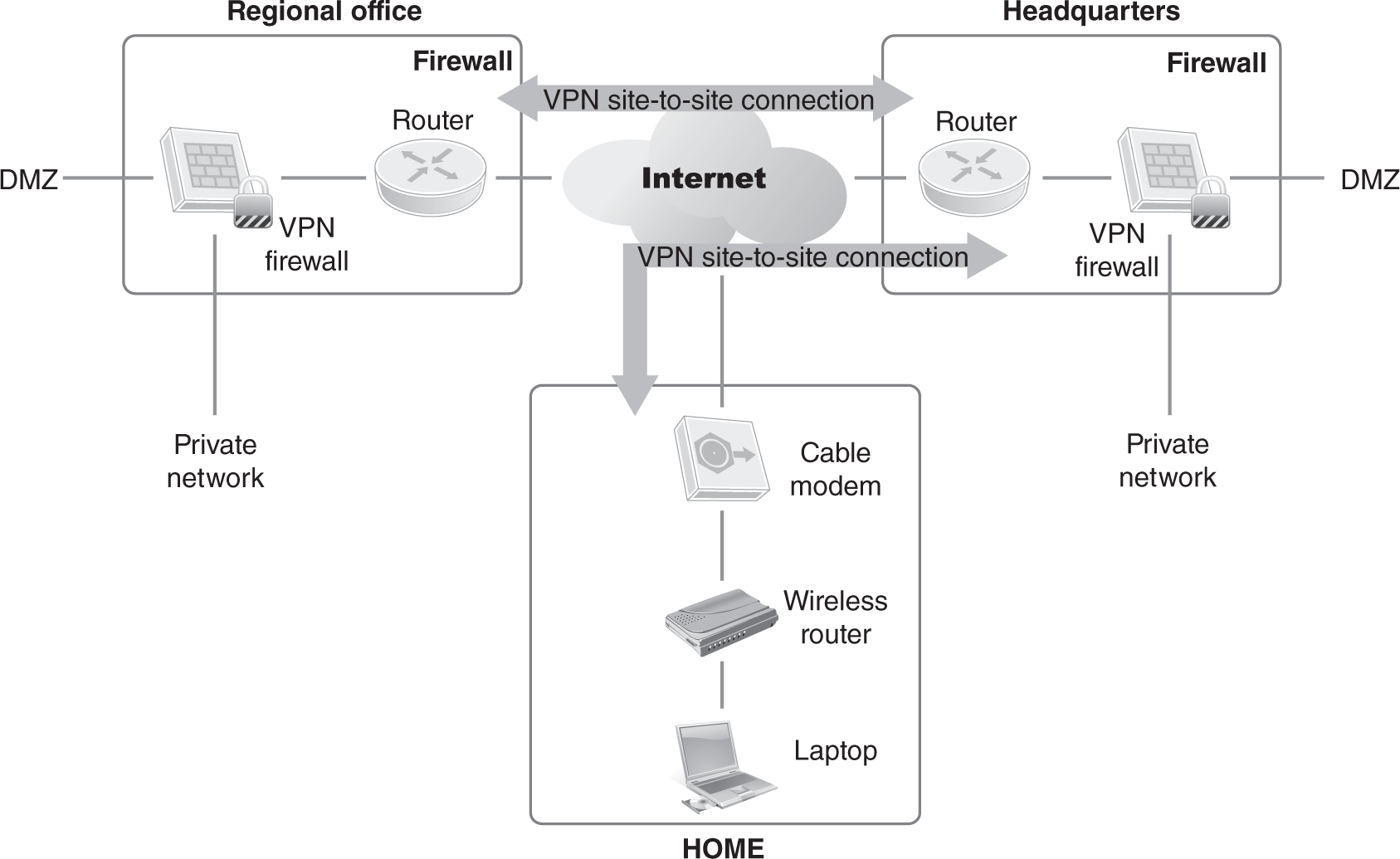
FIGURE 4-4 Basic types of VPN connectivity.
The combination of enhanced remote authentication and network connectivity can be a powerful tool to ensure a network’s protection. Yet these tools also extend the business network anywhere in the world. Consider this scenario: Shelly, an executive, receives a call on a Saturday to approve a change to a vital business shipment. For Shelly to approve the shipment, she must review the changes on an internal system and electronically sign off on the changes; however, she is away for the weekend with her family.
Fortunately, Shelly has her laptop in the hotel, and she has an Internet connection. She signs on to her company laptop and connects to the network using her ID/password and a token she carries on her keychain. A VPN tunnel is established, and her laptop is authorized onto the network. Shelly can now access the system the same way she does from her desk in the office. The encrypted communications are secure and private. She can review the shipment change and approve its release. The use of the ID/password and token achieves authentication and nonrepudiation for any transactions Shelly decides to execute. The confidentiality and integrity of the communication is achieved through encrypting the tunnel.
System/Application Domain
As complex as networks are, they essentially secure communication between an end user and some application software. What collects, processes, and stores data is ultimately software. Business software is typically an application. System software, such as a server operating system, runs business applications. The System/Application domain refers to all the system and application software-related issues.
Application software is at the heart of all business applications. Application software can run on a workstation or server. For example, an application can display a screen by which customers and employees can select products and enter data. Once the information is collected, the application transmits the transaction to a server. The server stores the information in a database to be processed later or instantly processes the transaction, stores the results, and displays information back to the end user. Later an employee can extract data from this ordering application into a spreadsheet to track the total number of orders each month by product type. The application that took the orders, the spreadsheet that tracked the orders, and perhaps the email client used to announce record sales for the month are all examples of application software.
FYI
People often use the terms system software and application software interchangeably. They are not the same. Generally, any business software that an end user (including customers) touches is an application. This includes email, word processing, and spreadsheet software. The operating system, which is the software that runs applications, and software that allows a computer to communicate over a network are system software.
