The Role of Human Resources Policies
Well-defined HR policies provide the framework that governs employee relations. HR policies state core business values and what is expected. They can also prevent misunderstandings. Managers are more likely to engage a worker on sensitive topics, such as lack of performance, when there’s a clear process they can follow to stay out of trouble. Like any written record, the HR policies can be used against an organization in a lawsuit. Poorly drafted policies become evidence to support an employee’s contention that he or she acted within company expectations.
Although HR policies must demonstrate commitment to secure business practices and clearly state values, they must be flexible and defensible in a court of law while meeting business objectives. They must also establish processes for management to follow. You often find HR policy language intentionally vague. This avoids language that could be interpreted as an employment contract or unintended promise. Although they may be flexible in their language, HR policies must be applied consistently across individuals. For example, disciplining two individuals differently for the same security policy violation could result in a lawsuit. In contrast, security policies must be precise, establishing clear expectations of behavior that can be enforced.
Consequently, automated enforcement of security policies shows consistency and often leads to a higher compliance rate than manual controls. It’s also better to stop a security policy violation immediately through automation than to deal with its aftermath. However, how do you enforce security policies when automated controls are not available or ineffective? A classic example is when a worker views inappropriate sexual material on a company computer. Let’s assume it can clearly be shown as willful versus accidentally stumbling onto an inappropriate website. This example starts to show the reliance that security policies have on HR policies to define acceptable behavior and to enforce adherence through disciplinary actions.
 NOTE
NOTE
The acceptable use policy (AUP) is often based in part on HR policy. It establishes expected behavior such as prohibiting access to social networking sites from company computers.
Relationship Between HR and Security Policies
Security policies must be well grounded within HR policies. Don’t look for precision in HR policies. They are better viewed as a foundation on which to build. They establish broad rules of acceptable behavior. These rules cover such topics as expectation of privacy when using company computers to zero tolerance for certain inappropriate behaviors. Security policies can then operationalize these core values and define controls to enforce them. Just as security policies must align to business processes, they must also align to HR policies.
The relationship between HR and security policies can be seen in FIGURE 5-5. This figure depicts several key touch points. Let’s use the previous example of viewing inappropriate material on a company computer. Figure 5-5 illustrates the relationship between HR and security policies. First, an HR policy would state the core value. This could be as simple as “Computers are for company use only.” Or it could detail the type of material prohibited. The security policies could then align by outlining acceptable uses of the Internet. Preventative security controls can be designed to block unacceptable sites. A worker who finds a way around these controls may be discovered through detective controls that scan company computers for unauthorized software and information. If such material is found, management can determine what disciplinary action, if any, is necessary. Management would look to HR policies for guidance. After working with HR, management might decide a formal warning or even termination is appropriate. This illustrates the close alignment needed between HR and security policies.
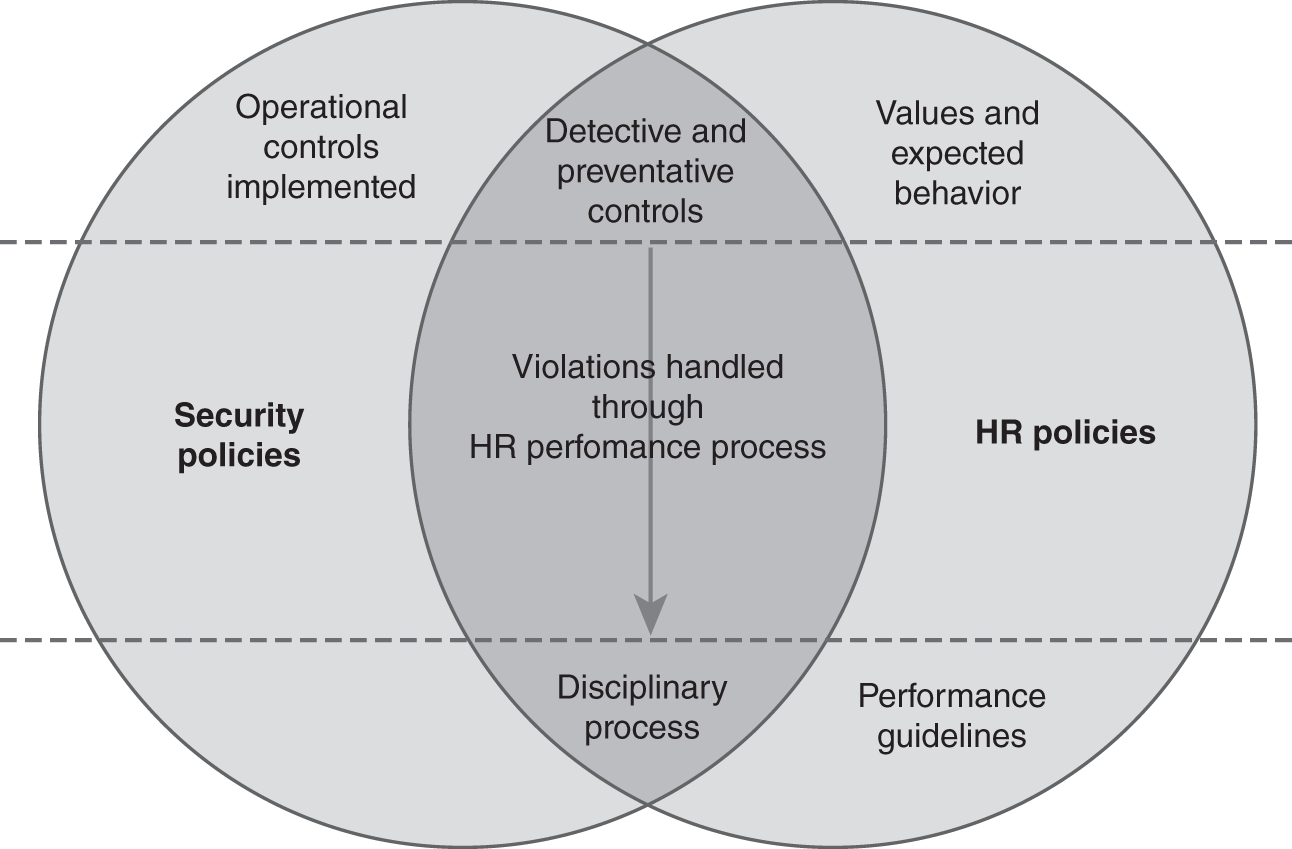
FIGURE 5-5 Conceptual relationship between HR policies and security policies.
Lack of Support
The ability to take disciplinary action to enforce security policies is not the only reason to seek support from HR. A lack of support can also make implementing security policies difficult or impossible. You need to remember that HR is a primary point of contact with workers. It can serve as a point of communication with the employees and a place to resolve conflicts. The following outlines several key areas of support provided by HR regarding security policy implementation:
- HR policy and values—Establishes a baseline of permitted behavior, including the acceptable use of company technology.
- Security awareness—Promotes understanding of security policies.
- Exit interview—Allows departing employees to express how effective security controls are in enabling or inhibiting employee productivity. This candid expression allows for the continued improvement of security policies.
- Event monitoring—Allows a broader understanding of how effective security policies have been implemented.
- Disciplinary action—Provides a process to adjust behavior to align with security policy expectations.
- Source of authority—Provides authority for establishing security controls.
You need HR support to make sure you are interpreting the language correctly. These interpretations become the basis of key security policies such as monitoring employee behavior on company equipment. If you don’t have the right interpretation of HR policies, it’s difficult or impossible to design effective security controls to prohibit certain behavior.
Security policies rely on employees understanding and cooperating with the rules. Security awareness is one of the best ways to achieve this understanding. A good security awareness program starts when a new employee walks in the door. It’s reinforced at least annually and as an employee is promoted into new responsibilities. A lack of HR support makes it impossible to provide security awareness to new employees, when they are first hired or when their jobs change.
Continuous improvement relies on people telling you what is and isn’t working. A good source for this information is an employee departing a company. You ask current employees what they think. But do you know if they are just telling you what you want to hear? They may not want to make waves. Individuals departing a company tend to be more candid with less to lose. Most HR departments conduct an exit interview. They ask basic questions about the work environment and why the person is leaving. It’s also a good opportunity to ask a few well-selected questions on security. This could help you understand the strengths and weaknesses of the information security program. A lack of HR support means you never get to ask the question to know where your security weaknesses may lie.
An important part of HR’s job is to field complaints from employees. No matter how good you are at explaining security policies, at some point you will ruffle someone’s feathers. Count on them calling HR to complain. To get HR staff on your side, you need to let them know exactly how and why you are implementing security policies. They are skilled in listening and communicating with employees on sensitive matters. They can support you to help defuse problems. They can explain how the policies align with company values. They can reinforce key security awareness messages. A lack of support has the opposite effect. Complaints can escalate and get out of hand. Worse yet, if HR takes the employee’s side, you may find yourself backing down on security policies or weakening the security awareness message.
You have learned how HR support relates to disciplinary action. If security policies are not enforced, employees inevitably perceive them as unimportant. Management needs the broad mandates within HR policies to assess employee performance. This includes how well people follow security policies. Without this HR support, security policies become optional and unenforceable.
Security policies, like any policy, must have a mandate. Someone in authority has to say, “This is important” and “You have to do it.” Often this comes from executive leadership. On occasion you can point to key values within HR policies as an additional source of authority. Doing so also provides a perceived mandate that helps gain support among executives. A lack of HR support makes it more difficult to obtain executive approval for security policies and easier to have them challenged.
In summary, it’s difficult or impossible to implement security policies without HR support. Fortunately, HR in most organizations understands its role in helping implement security policies. It’s rare to find an HR department that attempts to hinder implementation of security policies. More likely, you will find different degrees of support. The relationship with HR is an important one for the information security team to develop.
