Roles, Responsibilities, and Accountability for Personnel
It’s important to understand the relationship between individuals and organizational roles and committees. Many IT processes pass through numerous hands. Sometimes it goes through a committee or a group of individuals. For example, an organization may have a governance or management oversight to review major projects that have significant budgets. The difference between governance and management oversight is an important distinction. Governance oversight approves the controls and approach by which risk is to be managed. Management oversight executes within the rules set by the governance body. For example, a governance committee may say all projects costing more than $50,000 must be reviewed and approved by the chief information officer and the IT senior leadership team (SLT). It’s then up to the CIO to ensure that management processes follow the governance rules. This could mean having the project team present the proposed project in an SLT meeting and getting a formal vote of approval.
 NOTE
NOTE
Individuals do not work in isolation. They are supported by organizational roles. The organizational roles implement a framework that establishes the standards for identifying and managing risk. Collectively, these roles and the organizational support help define the risk culture.
The Seven Domains of a Typical IT Infrastructure
Managing access to data can be a complex issue. Data can be in emails, in a word-processing document, or on a file server, or it can be accessed through a product application. Regardless, data must be understood and protected. Within the seven domains of a typical IT infrastructure (User, Workstation, LAN, WAN, LAN-to-WAN, Remote Access, and System/Application) are special roles responsible for data quality and handling. The following individuals work with the security teams to ensure data protection and quality:
- Head of information management
- Data stewards
- Data custodians
- Data administrators
- Data security administrators
The head of information management role is the single point of contact responsible for data quality within the enterprise. This person deals with all aspects of information. This person establishes guidance on data handling and works closely with the business to understand how information drives profitability. A business person, as opposed to a technologist, typically fills this role.
Data stewards are the individuals responsible for ensuring data quality within the business unit. Data stewards are the owners of the data. They approve access. They work closely with information management to ensure the business gets maximum value from the data. They define the business requirements for data and create descriptions of what the data is and how it will be used.
Data custodians are individuals in IT responsible for maintaining the quality of data. These individuals make decisions on how the data is to be handled given the requirements from the data steward. Whereas the data steward’s primary role is to design and plan, the custodian’s primary role is implementation.
Data administrators are responsible for executing the policies and procedures such as backup, versioning, uploading, downloading, and database administration.
Data security administrators have a highly restricted role. They grant access rights and assess threats to the information assurance (IA) program.
Organizational Structure
An organizational structure can tell you a lot about how risk is managed. It defines priorities through the teams’ specialties. It defines how the organization perceives its threats. It also indicates how agile the response might be. FIGURE 8-3 defines a theoretical information security organization in the private sector. Notice the layer of executive governance of the security function in this example. Executive governance provides oversight for the security process and authority to execute.
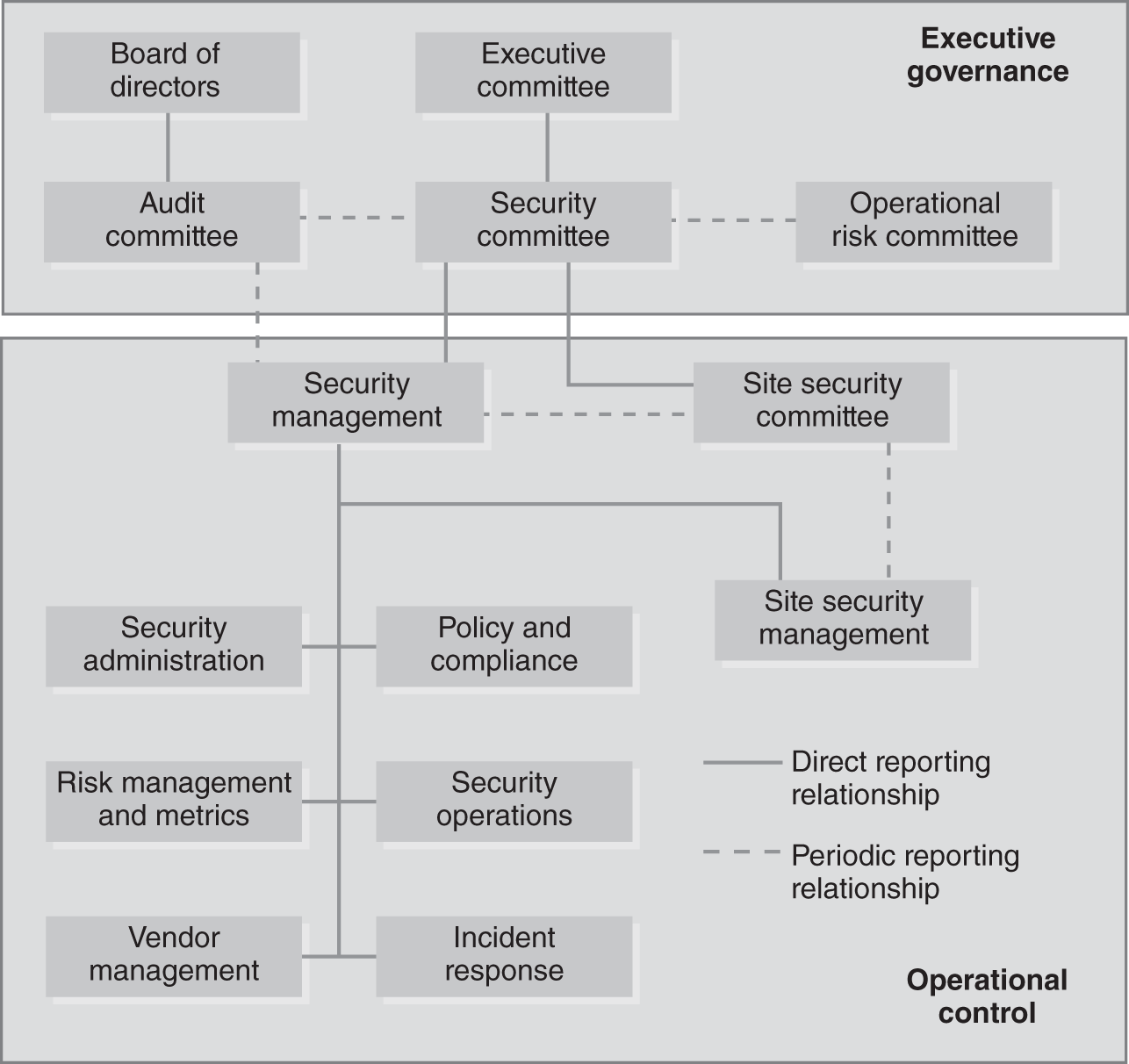
FIGURE 8-3 Information security organizational structure.
The board of directors establishes an audit committee to deal with audit issues and nonfinancial risks. The chief information officer (CIO) reports to the audit committee about technology issues. The chief information security officer (CISO) may also report issues directly to the audit committee. Alternatively, the CISO may report to the CIO. Then the CIO’s role is to report the security issues. The CISO may have a legal requirement to report to the board directly. For example, the Gramm-Leach-Bliley Act (GLBA) requires reporting to the board on the status of the GLBA program. That report is created and presented to the audit committee by the CISO. Keep in mind that the board of directors creates the audit committee. Consequently, issues on security coming to the board would generally go through the audit committee.
The primary issue in an effective audit committee is less about who is on it and more about their autonomy. This means that the audit committee must be free from interference from any part of the organization. Although audit committees are made up of internal employees, it is a good idea to have an outside party perform the actual audit. This does not completely eliminate the chance of influence but does absolutely ameliorate it.
The executive committee helps set priorities, removes roadblocks, secures funding, and acts as a source of authority. The security committee members are leaders across the organization. This combination ensures buy-in from the business for the information security program. This is typically where a balance is reached between the needs of the business and the needs of the enterprise to implement effective security controls. So, it’s important that the line of business (LOB) senior leadership be represented. The higher the level of LOB representation in the committee, the higher the committee’s perceived authority. The CISO is usually the chairperson. The CISO sets the committee agenda and facilitates discussions. The security committee reports its issues and budget requests to the executive committee. The executive committee aligns the security committee with the organization’s goals and objectives.
The security committee may have a less formal relationship with the audit committee and the operational risk committee. The committees will exchange information and on occasion agree to joint initiatives. Although less formal, these are key relationships. For example, the operational risk committee provides important information on the risk appetite of the organization. Knowing the risk appetite can help the security committee understand business requirements and priorities at an operational level. Conversely, the risk committee needs to understand the information security capability and emerging risks. In this way, the risk committee can determine which business activities are riskier than others. Consider a business that wants to sell a product on the Internet for the first time. The risk committee needs to understand the general risks associated with this type of activity and, broadly, the organization’s security capability.
The most important role for the risk committee is an objective review of risk. This involves a careful risk analysis. Such an analysis begins with a thorough business impact analysis (BIA) for all business units. As much as possible, quantifiable data should be used. This data includes metrics such as maximum tolerable downtime (MTD), maximum time to recovery (MTTR), and mean time before failure (MTBF). These are common metrics that provide quantifiable data to be used in disaster recovery and business continuity planning; however, they also help influence risk analysis. Not everything will be quantifiable, however. In some cases, that will leave only qualitative analysis. The main issue is that the risk committee remain as objective as possible.
The security management role is held by the CISO. The security committee is the key committee for the CISO. This is where the CISO can set the agenda and direction of the security and risk program.
Security administration in Figure 8-3 refers to centralized access management. Centralized access management involves creating and maintaining user IDs, which includes granting users access rights. This also includes building roles and ensuring appropriate levels of segregation of duties. The team most likely works with project managers and developers to ensure application security requirements are met. Depending on the volume of projects, this function could be separated from security policy management.
The policy and compliance team is responsible for creating, reviewing, approving, and enforcing policy. This team works with legal to capture policy regulatory requirements. The policy and compliance team provides interpretation of policies; approves deviations from policies; interfaces with regulators, providing evidence of compliance; and monitors the effectiveness of and adherence to policies.
The risk management and metrics team reviews the business processes and identifies potential risks and threats. The team works closely with the business to understand potential for fraud. Team members communicate with the other security teams to provide them with their assessment and analysis. They similarly use the other security teams as a source for metrics. By combining various metrics, they develop a scorecard that indicates key risks and the effectiveness of the security function. They also create reports for the CISO to present to various leaders.
A security operations team monitors for intrusions and breaches. Team members monitor firewalls and network traffic. When a breach is discovered, they activate the incident response team (IRT). The IRT responds to breaches and helps the business recover. Furthermore, the IRT assesses how the breach occurred and makes recommendations for improvement. The IRT performs forensic examinations and investigations, and interfaces with law enforcement agencies.
The vendor management team manages security concerns with vendors and third parties. Before data leaves the organization and is processed by a third party, this team performs an assessment on that vendor. Some organizations have adopted the concept of permission to send. In other words, data is not allowed to leave the organization until it’s been verified that the vendor’s control environment meets the organization’s own requirements. Only then will permission to send be granted.
Figure 8-3 is a theoretical model based on combining a number of the best practices from various frameworks. This hybrid organizational structure illustrates the need for support from leadership and business. The number of teams and amount of specialization depends on the volume of activity, the complexity of the environment, and funding. The key point is that these teams do not operate in isolation. An organizational framework creates specialties that have the agility to respond quickly while continuously working to reduce risk to the business.
Organizational Culture
The organizational culture influences how IT security policies are implemented. It starts with the tone at the top—how senior leaders deal with the CISO. Security professionals are skilled in gathering threat information and analyzing the impact to the organization. They also are skilled at identifying threats and vulnerabilities and then presenting these findings.
These are important and difficult skills to master. Equally important is the ability to navigate the organizational culture. These soft skills are especially important for a CISO. The CISO must connect and build trust with the business. Without building trust, the IT security team may be viewed as overhead rather than a partner in reducing risk.
 WARNING
WARNING
Security frameworks define policy and set behavior expectations. Policies cannot address every situation an employee might encounter. Good training on the policies’ core principles, along with common sense, will arm employees with what they need to be successful.
As a security professional, you must not talk strictly in threat terms. You must have the ability to connect with line of business leaders and talk about threats in terms of risk to the business. For example, it’s more effective to talk about how malware could prevent the service desk from helping a customer than to talk about the technical way in which malware can infect a machine.
Successfully dealing with the organization’s culture means understanding how to drive value to the business. This means working with the business to draft comprehensive security strategies to increase the business’s capability. For example, the business may strive to be a virtual organization with extensive remote access. This means working on how to extend the perimeter to remote laptops versus focusing on why the risks for such a plan could be too high.
The key point is not to be out of step with the organizational culture. You must drive security solutions into the organization in a way that will resonate and be perceived as delivering value to the business.
