Virtualization and Cloud Computing
Virtualization and cloud computing are becoming more popular and important, separately and in tandem, for individual users and organizations large and small. Cloud computing depends on virtualization for efficiency, and virtualization is changing the way data centers operate. In this section, we look at virtualization and cloud computing and their roles in our interactions with the internet and web.
Virtualization
A virtual something is anything that is used to simulate the look, feel, or function of something else. In computing, a virtual object, such as a machine, server, or router, is the simulation of its functions through software. The process of creating virtual devices using software is grouped under the term virtualization.
Before the technologies of hardware and software virtualization became available, increasing the computing capacity of any organization (including homes) meant adding hardware and maybe more software, or both. Regardless of the size of the addition, the equipment cost, the impact of downtime for installation, the reconfiguration of the system and network, and quite possibly the cost of hiring additional computing staff and training them can be high. In a rapidly growing company, the impact of repeating this process frequently can be expensive over time. Figure 1-16 illustrates both hardware and software virtualization.
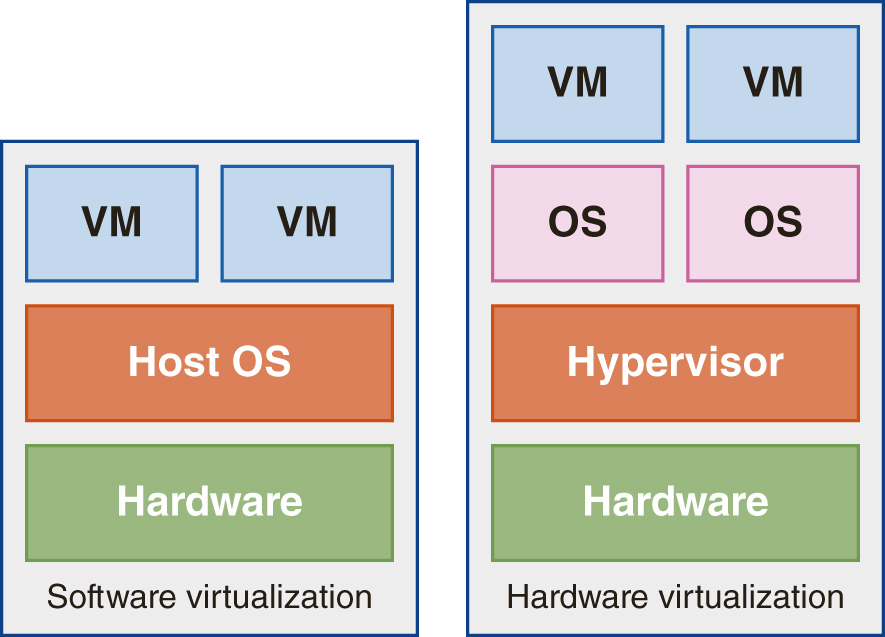
FIGURE 1-16 The basic differences between software and hardware virtualization.
Virtualization is not a recent concept. Although it’s been a hot topic over the past 10 or so years, its roots reach back into the 1960s, when multiple users were able to access a single mainframe computer for batch processing. The concept of a super-supervisor (operating system), or hypervisor, was developed by IBM engineer Don Skiba in 1969. In 1972, IBM released the Virtual Machine/Cambridge Monitor System (VM/CMS) that included virtual memory support and the Hercules operating system emulator. Over the next two decades, most of the development in virtualization was for mainframe and minicomputers as extensions to their operating systems.
One of the first virtualization applications was virtual memory, in which hard disk space is used to extend main memory to hold idle or swapped out portions of active programming. Figure 1-17 illustrates this process. This technology was introduced for mainframes and is still in use on PCs today. During the 1990s, several developments by a variety of technical and academic organizations advanced the capability of creating a virtual environment. Developments like AT&T’s Simultask, Locus Computing’s Merge/386, Insignia Solutions’s SoftPC, and Connectix’s VirtualPC proved that the abstraction of physical systems into virtual operating environments was viable.
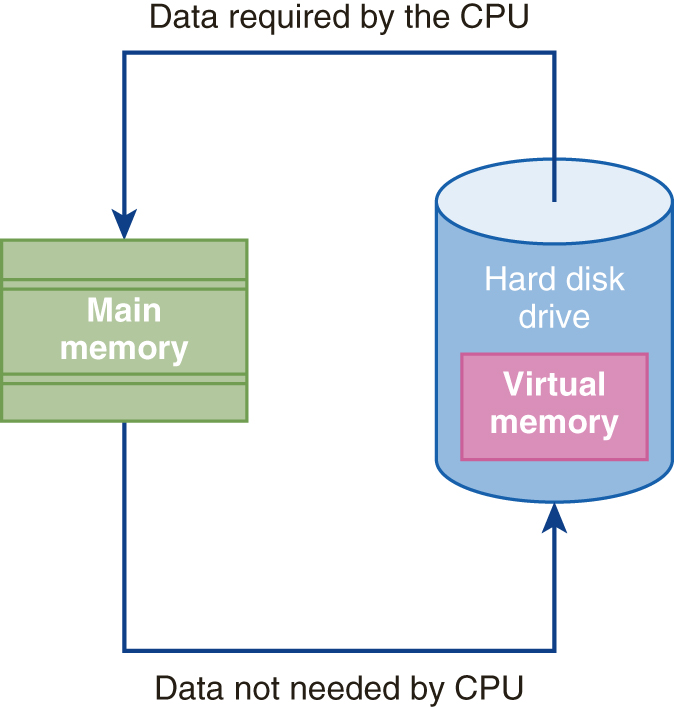
FIGURE 1-17 Virtual memory is a portion of the hard disk drive that is used to extend main memory.
In 1999, VMware announced its product VMware Virtual Platform, which was only the beginning of the virtualization software boom. The virtualization products available today are far more advanced than those available in the early 2000s. In today’s virtual world, companies have the capability to partition their servers to continue using existing applications, regardless of the operating system on which they were developed. Servers can be leveraged to support multiple concurrent tasks, and facility and infrastructure costs can be reduced or avoided altogether.
How Virtualization Works
The key element to implementing a virtualized environment is the hypervisor, which is also known as the virtual machine manager (VMM), and the supervisor of supervisors (hyper is a stronger form of super). The hypervisor is essentially the operating system for the virtualized environment. It controls the interaction between virtual machines (VMs) and the physical resources of the physical hardware. Figure 1-18 compares a physical computing environment with how it might appear in a virtualized configuration.
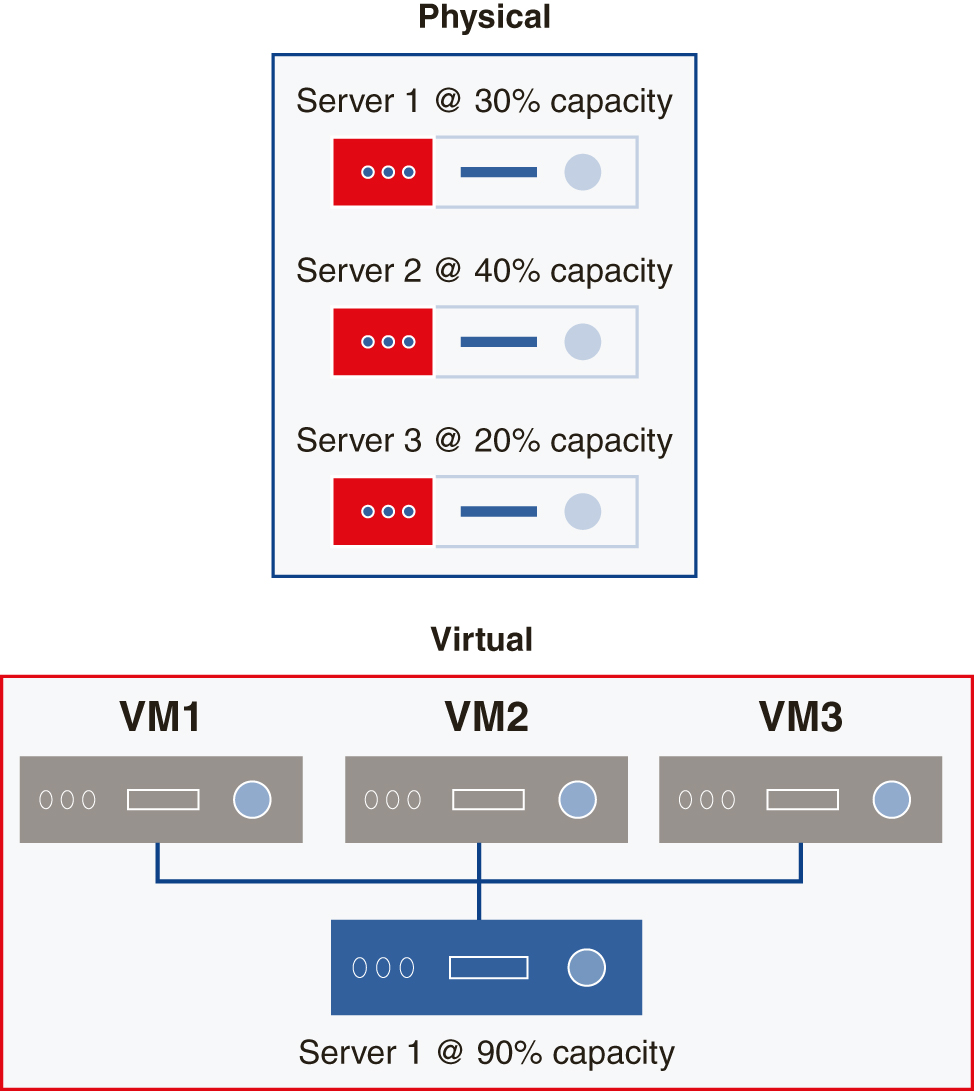
FIGURE 1-18 A three-computer physical environment can become a one-computer virtual environment.
Hypervisor.
The hypervisor can be installed as either a Type 1 or Type 2 configuration. A Type 1 installation is where the hypervisor is installed on a computer directly on the hardware, meaning the hypervisor is taking the place of an operating system. A Type 2 installation places the hypervisor on top of a native operating system. Type 1 installations, which are referred to as “bare metal” installations, are typically in situations where only virtual machines are to be configured on the system. The same can be expected of a Type 2 installation, but other processes could conceivably operate on the computer as well. However, this is not a common practice. Regardless of the type of installation used, the Type 1 hypervisor or the Type 2 operating system on which the hypervisor sits is the host operating system that is running on the host machine.
Virtual Machines.
The main function of a hypervisor is to provide support for the VMs created on the host. This includes acting as the effective “device driver” for all of the virtual resources allocated to each of the VMs. The resources required by a VM are indicated in the configuration when the VM is defined. The hypervisor then allocates the physical resources (RAM, hard disk, etc.) per each VM’s configuration and need. Because these resources are virtual, all of a VM’s requested resources may not be allocated until they become needed by the VM.
An application running on a VM “sees” its environment the same as it would on a nonvirtualized computer. It interacts with an operating system inside the VM, it requests hardware services from the operating system, and it operates in its allocation of RAM. The only difference in this environment is that the application is blind to the interactions of the guest (VM) operating system with the hypervisor.
Hardware resources allocated to each VM are software that interacts with the hypervisor that, in turn, interacts with either the hardware directly (Type 1) or through the host operating system (Type 2). The VM application sees the virtual devices as it would running on a physical computer. A VM can simulate a complete computer system or just one particular process as a guest on a host computer. One host can run multiple VMs concurrently.
Virtualization technologies are popular solutions for network, storage, and servers. When you virtualize a network, you split the bandwidth into more manageable channels assigned to servers or other devices in real time. When you virtualize storage, resources physically located on multiple servers appear as a single storage entity. Server virtualization uses multiple servers that appear as one on your computer without your having to manage their actual physical servers, processors, and operating systems. Grid and cloud computing are specific virtualization approaches and implementations.
Cloud Computing
Cloud computing allows users to access resources or processing that is located beyond their local firewall. Another way to look at cloud computing is that it is the access to specific applications and services provided by dedicated internet-based servers, which are typically virtualized. Cloud computing shifts local processing (applications and services) to remote service providers over the internet. Cloud computing further relieves an organization of the costly need for centralized computing and its maintenance costs. If more computing power is needed, cloud service providers are generally able to expand a subscriber’s services.
Services that offer access to applications, infrastructure, development platforms, and several other solutions are said to operate “in the cloud.” So, why is it called “the cloud?” Telephone company diagrams had been using a cloud image to represent the circuit switching processes between central offices (COs) of the plain old telephone system (POTS) and the public switched telephone network (PSTN). To depict the randomized switching of the internet, the cloud was used once again. Diagrams and drawings created when the internet and networks were just emerging tended to emphasize a particular aspect or detail of the network. Anything beyond or between emphasized areas was depicted as a cloud.
Most likely you’ve used one or more of the cloud applications or services a number of times, perhaps without knowing it. Several of the applications we use every day are in the cloud. Applications like Microsoft Office 365, Google Office Apps, Zoho Office Online Suite, Apple iWork for iCloud, and many others are examples of the tools accessible in the cloud. Examples of other commonly used applications in the cloud are email services, gaming, and shopping, to name just a few of what is available. Some of these services and application offerings are free to use after registration, but many require a subscription on either a monthly or annual basis.
To access cloud-based applications, a subscriber logs onto the gateway webpage of a cloud service provider (CSP). A common practice is that this gateway to the CSP’s services lists only the services to which the user has subscribed, such as accessing a development server, retrieving or sending email, performing accounting or other business functions, or using any of hundreds of available applications and services. In most cases, application data are stored remotely on the CSP’s storage systems and not on a local system. This frees the subscriber to access the cloud services using a much thinner client than would be possible if the processing were localized.
Figure 1-19 illustrates the elements of a subscriber connecting to a CSP’s systems. Many CSP systems, especially those with a high number of users, front the applications with a load balancer, which could be a router, switch, or dedicated appliance. The purpose of the load balancing is to forward the incoming service request to the server that will provide the best response time. The server that receives the incoming request performs the appropriate processing, accessing the data store, if needed, and sends the results back to the requesting subscriber.
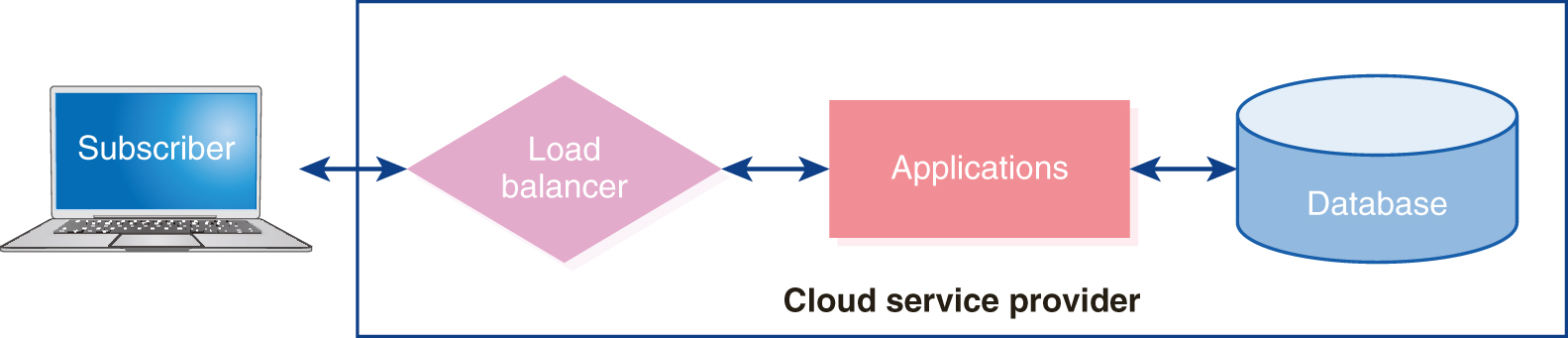
FIGURE 1-19 A simplified view of the elements in a subscribed cloud service.
The benefits of this technology can be significant. With the processing and distribution handled remotely, cloud computing levels the playing field for companies that lack the funds to constantly upgrade their network to accommodate new technologies and applications. A company is able to leverage its existing hardware and network equipment with any future system growth occurring only at the CSP’s data center.
Types of Cloud Computing
While the National Institute of Systems Technology (NIST) identifies three primary cloud service delivery models, subscribers may choose from an increasing number of service models. Perhaps the overall goal of cloud computing is Everything-as-a-Service (EaaS or XaaS). We haven’t quite reached that goal as yet, but we’ve made a very good start.
Cloud computing is represented and explained in two general models. There are service delivery models and service deployment models. A deployment model could present a delivery model, but a delivery model cannot also be a deployment model. Confused? Let’s look at it this way: a service delivery model is the “what” of accessing the cloud. Are you accessing an application, a particular configuration of hardware and software, or are you leasing an entire system? The answers to these questions identify the service delivery model you need. For example, if you only need to access an accounting system and store your data in a secure location, you would be looking for a cloud service; if you wish to develop programming on a particular system configuration, you’re looking to subscribe to a platform; and if you wish to perform virtually all of your computing and processing in the cloud, you are definitely an infrastructure subscriber. The service deployment model identifies the “who” of the cloud, meaning who in terms of the authorized individuals, groups, companies, etc. is authorized to access a particular service delivery model.
Service Deployment Models
NIST defines three primary cloud service deployment models: two basic deployment models and a hybrid deployment model. Several variations of these basic cloud deployment models are also in use by corporations, companies, and communities.
The two basic cloud deployment models are as follows:
-
Private cloud—A private cloud is a closed access structure to which access is usually restricted to members of a group, club, company, or organization. A private cloud can be hosted completely in-house, much like an intranet, or through a CSP. The downside of an internal private cloud is that the maintenance, performance, and security of the systems also remains internal.
-
Public—A public cloud can be in essence a private cloud offered over a public network, such as a civic wide area network (WAN) or the internet. Many public networks are accessible without a subscription fee, but there are those that users must buy a subscription to have access. Social media websites are examples of public networks as are pay-to-play sites. Membership is the constant factor of a public cloud.
A hybrid cloud deployment model combines public cloud deployment with private cloud restrictions. An example of a hybrid cloud deployment is a private cloud with restricted access to sensitive information that is the source data to a business intelligence application running at a CSP through a public cloud network.
A variety of specialized cloud deployment models exist, but for the most part, they are variations on public, private, or both deployment models. Perhaps the most common of these cloud deployment models is a community cloud. Typically, a community cloud is formed in support of one or more areas of concern, action, or support. Examples of community clouds are local political party registrations, combined charitable organization campaigns, interdenominational religious conferences, and the like.
Service Delivery Models
The three cloud service delivery models defined by NIST are Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS). Each of these delivery models is described in the following:
-
Software as a Service (SaaS) —Much of the cloud-based applications you access regularly are included in the SaaS model. SaaS applications are those that subscribers access on a CSP’s servers via the internet. Cloud-based servers provide a specific application or service to the subscriber, typically through the subscriber’s web browser. This enables clients to access applications with reduced licensing considerations and without the need for specific hardware. SaaS removes the need for a company to consider multiple installations, software updates, and other local administration requirements. Any application you access through a web browser is most likely SaaS.
-
Platform as a Service (PaaS)—Sometimes very specialized or unusual configurations of hardware and software are required for testing, prototyping, and other activities that cannot be supported in-house. A PaaS can be configured to provide the customized needs of a subscriber. PaaS systems are commonly used to build specific programming, testing, or modeling environments that would either be too costly or time-consuming to build in-house.
-
Infrastructure as a Service (IaaS)—A method of delivering an infrastructure that includes servers, storage, networking, along with virtualization and other specialized components that are accessed via the internet. The CSP is responsible for hardware and software in terms of updates, maintenance, and availability of the subscribed environment. The subscriber typically pays on a per-usage basis for the use of the service.
The variations of “aaS” or as-a-Service offerings in the cloud continue to grow. Some of the more popular of these service delivery types are as follows:
-
Artificial Intelligence as a Service (AIaaS)—Provides a variation of both SaaS and PaaS that allows AI developers to test and model algorithms without making the considerable investment in equipment and software
-
Backup as a Service (BaaS)—Provides services that allow subscribers to back up their systems on the cloud without the worry of storage space and physical security
-
Cloud as a Service (CaaS)—A “full meal” offering that combines SaaS, PaaS, and IaaS services into a single subscription
-
Desktop as a Service (DaaS)—Provides thin client users with a full desktop experience
-
Network as a Service (NaaS)—Subscribers have full networking functionality without owning the necessary hardware and software or technicians to maintain it
-
Unified Communications as a Service (UaaS)—Provides managed and hosted integrated communications services that typically include networking, Voice over Internet Protocol (VoIP), and messaging
-
Video-conferencing as a Service (VaaS)—Provides cloud-based video and telephone conferencing services typically at a higher quality level than subscribers could afford to purchase
It’s likely as new technologies emerge and it becomes economical for new services to move to the cloud, more as-a-Service delivery models will become available.
