Banking Security, Zeus, and SpyEye
As online banking becomes more prevalent globally, it is of the utmost importance to demonstrate the security measures in place around online banking. By examining what is currently of concern to banks in the area of online security, coupled with where the banking industry is headed, flaws in banking information security become increasingly prominent. Currently, banks are concerned with denial-of-service (DoS) attacks, online fraud, both Zeus and SpyEye Trojans, and a wide array of mobile banking threats.
DoS attacks are happening more frequently to banks, recently occurring at Wells Fargo, Citigroup, JPMorgan Chase, and Bank of America. During a DoS attack, hackers establish a series of meaningless connections to the bank’s website, connections that are meant to overwhelm the bank’s servers. Once the servers become overwhelmed and crash or freeze, they are rendered inaccessible until the banks fix them. To help curb this problem, the banks have been working with their bandwidth providers to help weed out malicious traffic prior to that traffic arriving at the bank’s servers. Recently, however, hackers have become more sophisticated in their approach to denial-of-service attacks. And they have utilized more powerful machines to attack the secure communication protocols that banks and their customers use to communicate transactions with one another. A common type of DoS attack begins with the principle attacker establishing a DoS attack master device. Then, the attacker infects hundreds of user computers, which are widely distributed across the country and increasingly across the globe. Then, the principal attacker sends an instruction to each of the commandeered user computers to begin accessing a target bank’s servers, such that they overwhelm the edge routers and switches and bring the servers to a standstill. This process can be activated repeatedly. And these attacks can be architected as waves: The East Coast PCs can start, then the midwestern ones can begin, then the West Coast ones begin, and then those in South East Asia begin. As the bank’s security personnel deal with one set of transmissions, another one begins, and waves of transactions keep rolling in from across the globe. The web of commandeered user computers are called a botnet and sometimes a zombie network, since the user is not aware of what his or her PC is performing as part of this zombie botnet. An example of such a DoS attack architecture can be seen in Figure 10.1. The DoS attacking agents are widely spread geographically, e.g., California, Texas, Illinois, Florida, New York, and maybe Maine. Thus, they present a distributed DoS (DDoS) attack, since the bots are distributed and all simultaneously attempt a DoS attack.
Figure 10.1 A multilevel zombie bot attack led by a remote botmaster.
While DDoS attacks are a growing problem, fraud has always been of prime concern within the banking industry as whole; it presents a huge risk, and the online banking format means that this is now especially the case. Two recent cases of online fraud spawned from two Trojan viruses known as Zeus and SpyEye. The Zeus Trojan is a package that is designed to run on versions of Microsoft’s Windows operating system. This virus was able to steal banking information by implementing a keystroke logger within each commandeered host computer’s web browser, along with a form-grabbing utility that would take personal and banking information. This Trojan was spread through downloads and e-mail phishing scams that installed the Trojan on the host’s computer. Once the eastern European hackers had the information, they would wire thousands of dollars to fake accounts. In total, Zeus was responsible for the theft of more than $70 million from people all over the globe. In 2010, SpyEye, another form of Trojan malware, surpassed Zeus as the most dangerous banking Trojan. SpyEye is considered a “man-in-the-browser” technique that allows criminals to impersonate the customer to the bank and impersonate the banks to the customer with almost undetectable perfection. This makes protection from SpyEye a very difficult problem.
The future of online banking threats increasing arises from “man-in-the-mobile” threats. In these circumstances, hackers rely on the growing trend of performing mobile banking on smartphones and tablets. This is especially problematic for online banking and other services utilizing one-time short message service (SMS) or “texting” for authentication of devices. Figure 10.2 illustrates an example of how a traditional man-in-the-middle (MitM) attack is performed, wherein the attacker inserts himself in the middle of a mobile banking transaction between a mobile user and the bank, and even between two mobile users who are processing a transaction between themselves involving a common bank.
Figure 10.2 The structure of a man-in-the-middle (MitM) attack.
Furthermore, hackers can also gain control of a customer’s mobile device or a user’s browser and not merely imitate the user but also actually be the user sending the false transaction from the user’s device, therefore facing a lesser chance of detection.
Modern hacking is often motivated by potential fiscal returns from the use or sale of data obtained in a malicious attack. Therefore, banks, with their large array of financial data and customer information as well as knowledge of the complete network interconnecting the banking system across the globe, are a primary target for hackers. The financial industry carries a significant security burden as a result of the data that their servers maintain. Customers of a bank or credit union have rather high identification and access standards set by how an individual customer’s finances are managed. As these user groups request access by means of their mobile devices, which are integrated with software features such as Mint.com, users and financial institutions alike are widening the attack options for potential attackers.
Part of launching an attack that provides significant returns for the attacker is to understand to whom to sell information, how to leverage and liquidate it, and how to remain as anonymous as possible while coordinating these risks. Attackers cannot simply use banking and financial information to pull money directly into their accounts; this would be a traceable and reversible operation. Instead, they must use a variety of transitional processes or vectors to cleanse the money. These accountability cleansers are called money mules and may be a purely digital or physical fraudulent company used by hackers. The “mule” then takes a percentage or fee for risking themselves in the cleansing process.
Risk Management Process for Banks
It is a fact that all online banks of significant size or holdings will be attacked. This means it is not a question of “if” they will be attacked but instead “what, when, where.” The answer is not to shut down the bank, but instead to manage the risk that is presented by operating in this industry. All banks take on a varying amount risk with every decision that is made at every employee level. In fact, the most common methods by which banks lose valuable customer information are not a computational-based attack vector. Social engineering is a method of “attacking” humans from a behavioral perspective, understanding their context and how to make them at ease with releasing potentially damaging information. Figure 10.3 lists three general areas of risk—credit, market, and operations risks.
Figure 10.3 Risks for banks and customers from bank attacks and fraud.
The area of operations risk contains a wide range of vulnerabilities, from the processes that employees use to do their job to the systems they use to input customer data. The goal is to mitigate these risks using training techniques, with topics ranging from all aspects of a social perspective where individuals might be vulnerable, to the very specific aspect of ensuring that all modifications, updates, and patches to software and hardware are routinely applied in a timely fashion.
The two specific attacks previously mentioned, Zeus and SpyEye, have had profound effects on international banking services. While primarily attacking European banking, some U.S.-based banks have also been affected by both forms. Each is a MitM form of attack beginning with the use of keystroke logging or form-grabbing techniques to acquire credentials. After passwords have been acquired to obtain authorized access, they lock the user’s machine after installing “CryptoLocker Ransomware,” which is a form of “scare-ware.” This software forces users to input their credit card information with the promise that they will be able to begin use their machines again after they have been unfrozen.
While using online banking software, SpyEye and Zeus have the ability to hijack or steal the session “cookies” that are used to maintain state data and security between sessions. A compromised system can have this secure session data hijacked and transferred to a remote host. That host is then able to perform operations under the user’s stolen account. In 2012, IOActive, Inc. performed an advanced analysis of the SpyEye and Zeus malware, revealing the depth of the software’s capabilities, and it published an open report of its analysis. Computers infected with either of these become part of a botnet from which commands can be remotely executed. From such botnets, malware is often broadcast to variety of demographics and targets with the hope that the compromised security of a less valuable system may lead to the compromise of higher-level and higher-value systems. Figure 10.4 portrays the sequence by which bank fraud frequently occurs.
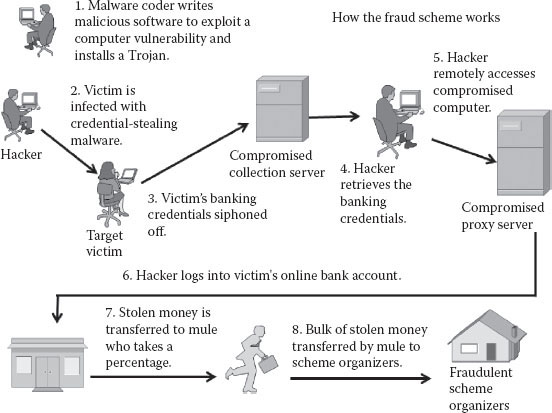
Figure 10.4 A schematic layout of how bank fraud works.
Bank fraud tends to occur in the following steps. First, a malware coder writes malicious software to exploit computer vulnerability and installs a Trojan. Once the victim’s computer is infected with credential-stealing malware, the victim’s banking credentials are siphoned. The hacker retrieves the credentials, gaining complete control of the computer and the ability to remotely access and direct the compromised computer. The hacker then logs into the victim’s online bank account, transfers money to a “mule,” and then transfers the money from the mule to the criminal organizers of the operation, which may be an individual but frequently is some fraudulent company.
Both the owners of infected machines and the financial institutions are victims of this fraudulent action. The money mules transfer stolen money for criminals, while shaving a small percentage for themselves and shielding the original attacker and the criminal organization that is the ultimate recipient of the stolen funds. Financial criminals can be separate individuals or collections of malware coders, malware exploiters, and mule organizations.
Analyzing, assessing, and then protecting via information gained from the risk management process and information security measures invoked are factors that determine how competitive and successful a bank will be in the future.
A sequence of major financial security events from 1999 to 2011 is arrayed in Figure 10.5.
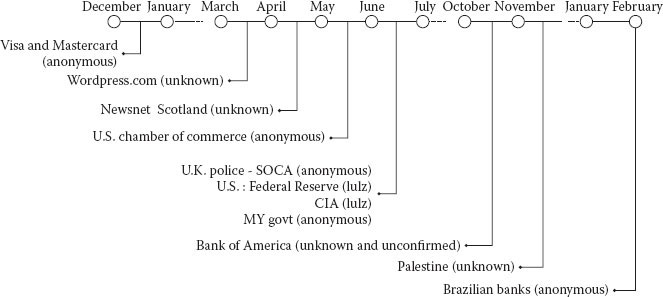
This culminated in a series of DoS attacks in 2011 on financial institutions, government branches, international police agencies, and news organizations throughout the globe, as illustrated in Figure 10.6.
Figure 10.5 Major financial security events from 1999 to 2011.
Figure 10.6 Major denial-of-service attacks in the year 2011.
Online Fraud and the Impacts of Zeus and SpyEye Attacks
Zeus (and its alternate forms ZeuS or Zbot) is a Trojan horse computer malware that runs on versions of both Microsoft Windows and the Apple Mac OS X operating systems. While these attacks can be used to carry out many malicious and criminal tasks, they are most often used to steal banking information by means of man-in-the-browser keystroke logging and form grabbing. Furthermore, they are also used to install the CryptoLocker ransomware. Zeus attacks tend to be focused on spreading mainly through drive-by downloads and phishing schemes. First identified in July 2007, when it was used to steal information from the U.S. Department of Transportation, Zeus became more widespread in March of 2009. And then in June 2009, the security company Prevx discovered that Zeus had compromised over 74,000 FTP accounts on the websites of such companies as Bank of America, Monster.com, ABC, Oracle, Play.com, Cisco, Amazon, BusinessWeek, and even NASA.
Zeus implements its keylogging and screen scraping by way of an import hook to the application program interface (API): “user32!TranslateMessage.” APIs are a set of routines, protocols, and tools for building software applications. The API specifies how software components should interact, and such APIs are particularly useful when programming graphical user interface (GUI) components. One of Zeus’s interesting features is its ability to steal the certificate store (including private keys) by hooking the function “PFXImportCertStore.” At the core of Zeus’s usefulness is its ability to hijack banking sessions and inject custom data into returned hypertext markup language (HTML)-formatted web pages and HTML formatted hypertext files. Zeus then renders them into visible or audible web pages. The data to be injected is specified within the “webinjects. txt” file, which is later built into the Zeus configuration file.
One important feature of the Zeus bot is the ability to download and execute files from a remote location. This gives Zeus the ability to extend its framework or install additional malware. Zeus also performs cookie stealing through the function “InternetGetCookie” to retrieve cookies for the specified URL. The cookie data is then logged to the user.ds file.
The fact that Zeus hooks by way of “wininet.dll” limits the injection to browsers that utilize these functions, implying that Internet Explorer sessions will be vulnerable to injection but Firefox will not. A new version of Zeus that includes support for Firefox is reported to be undergoing beta testing.
SpyEye is similar to Zeus, which is its main rival in the hacking world. SpyEye incorporates many advanced tricks to hide its presence on the local system. The unpacked SpyEye bot image can begin execution either at the entry point specified in its portable executable header, at a private (non-exported) hook procedure executed when the bot has injected itself into a new process, or at one of two private thread routines that execute when the bot has injected itself into an existing process.
Zeus and SpyEye have impacted many companies during the period from 2005 to 2011 (Figure 10.7), but most impact fully against the financial giants—Society General, UBS, and Credit Suisse.
Figure 10.7 Zeus and SpyEye impacted three European banks from 2005 to 2010.
Zeus and SpyEye have attacked organizations spread across the globe on all continents, from North and South America to the counties of Europe and Russia, and the countries of Southeast Asia down to Australia. Their damage has been spread globally.
Since they begin by infecting a target’s browser, Zeus and SpyEye can exercise some extensive damage and exhibit some sophisticated capabilities, allowing criminals to both impersonate the customer to the bank and the banks to the customer with capabilities nearing perfection.
The combined analysis of the Zeus and SpyEye Trojans offers an inside look into the methods that are common to most popular banking Trojans. Understanding the internal details of these Trojans provides a company with the opportunity to offset the underlying functionality of such common malware, rather than just relying on their detection and attempting to prevent individual agents using them.
Zeus and other similar malware lend themselves to many distinct detection methods, but the fact that a company implements a virtualized computer environment with associated isolation techniques offers the unique ability to implement protection that covers an entire range of malware and malware techniques. Physical and virtual memory monitoring can detect and prevent the placement of unwanted hooks and process injections. Having control of the virtual machine and virtual machine monitor offer a great opportunity for system-wide memory page monitoring and intrusion detection and the ability to apply static analysis to a possible malware image before it begins its execution process. Analysis focused on code sections and the detection of suspicious sections would consistently allow the detection of a persistent malware infection early in its infection process.
QUESTIONS
1. What type of attack is “man in the middle” and when does it occur?
2. This method helps hackers hide their trail through a person who receives and transfers money illegally on behalf of others. What is it?
3. What is the stealth strategy of the Zeus Trojan?
4. Give two ways in which SpyEye stays hidden.
5. What is Crypto Lock ransomware and how is it distributed?