The Stuxnet Worm and the Vulnerability of the U.S. Electric Power Grid
In the realm of information security, there are always new predators who present ever-more-advanced threats to the operation and control of our infrastructure. These types of attacks are stealthy and may employ both simple infection techniques and advanced approaches to malware to be spread after an initial infection has occurred. There are a variety of motives behind these advanced threats, which include political, national, and individual reasons. One of the most sophisticated of these advanced persistent threats emerged in the form of a worm identified as the Stuxnet worm. And Stuxnet is not alone. There are also a number of other infamous destructive threats, among which are Ghostnet, Aurora, and Night Dragon.
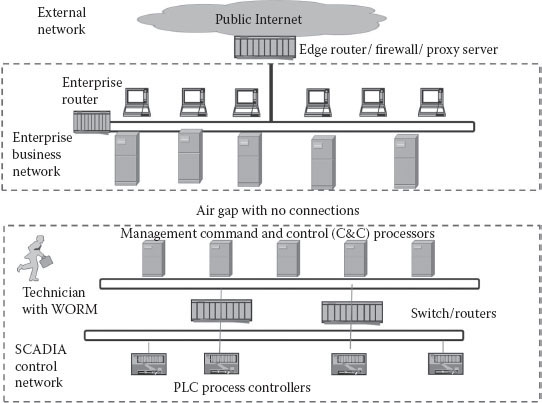
The Stuxnet worm presents an infection that is quite simple in its means of initial infection, which occurs when a personal flash drive carrying the Stuxnet worm is inserted into a target personal computer or process controller, containing a sophisticated spread mechanism. For example, a systems technician from the target site would have his personal computer infected by standard means. The technician then passes that infection to a flash drive, which he carries to work and inserts into one of the computers connected to the business corporate network of the target enterprise. The ultimate target of the worm is the system control and data acquisition (SCADA) network, which is isolated from the business corporate network. However, the technician also carries the flash drive across to the SCADA network, which then moves across that network to the various controllers and data acquisition processors, infects them, and begins the programmed mischief.
The Stuxnet worm was first discovered in June 2010. The worm was originally designed to attack Siemens-produced programmable logic controllers (PLCs) and data acquisition processors that control electromagnetic processes for industrial control systems (ICSs). Stuxnet was a Windows-based worm and was designed to operate as a digital weapon. The worm is estimated to have destroyed up to 1000 Iranian centrifuges (10%) sometime between November 2009 and late January 2010. It affected thousands of computers in Iran, specifically targeting Iran’s nuclear centrifuges. Different variants of Stuxnet targeted five Iranian organizations, with the probable target widely suspected to be Iran’s uranium enrichment infrastructure. While the origin of the attack remains unacknowledged, most believe that it was created and deployed through a joint effort by teams from the United States and Israel.
The worm operates by exploiting four zero-day flaws in the Windows operating system. A zero-day flaw is a security vulnerability wherein the vendor of the software is unaware of its existence, and its exploitation may result in potentially disastrous effects. Hackers take full advantage of this vulnerability before the vendor even becomes aware of the flaws and can install a patch or version update. For Stuxnet, there are four exploitable vulnerabilities, which include (1) exposure to the use of personal USB flash drives by system technicians, (2) three network techniques employed in the system, (3) the use of common Siemens Step 7 project files, and (4) Siemens’ WinCC command and control (C&C) database and connections. SIMATIC WinCC is a (SCADA and human–machine interface (HMI) system from Siemens. SCADA systems are used to monitor and control physical processes involved in industry and infrastructure on a large scale and over long distances. One aspect of this worm proved most dangerous. Although it was specifically targeted at Siemens PLCs deployed in Iran, it quickly spread to the business systems network. From there, it emanated through the Internet to countries around the world, infecting not only Siemens’ PLCs but also many computer systems employed outside Iran.
The worm was initially introduced to the target network via the insertion by a system technician of a Stuxnet-infected USB flash drive. The technician inserted the drive carrying the worm into the target business operations network of the target, which was physically separated from (and not network-connected to) the SCADA centrifuge control systems. However, that technician later carried the infected flash USB drive across to the SCADA system as well, as he performed his normal work activities. After the insertion of the flash USB, the worm self-installed, propagating across the SCADA network and scanning for specific Siemens Step7 software on computers that communicate with and control the PLCs of the target technology of the victim (the centrifuges in Iran’s nuclear materials manufacturing facilities). If any of the infected computers are not connected to a PLC, the malware will lay dormant until such a connection becomes available. When it does reach these specific computers, the worms install a rootkit to make the virus undetectable by most virus scanners. Not only was the worm undetectable by virus scanners but it also silently updated and redistributed itself. When the worm was active, it would monitor the PLCs and gather information about them. After collecting data about the centrifuges, Stuxnet would then take them over. And once the PLCs were taken over, the Stuxnet virus would cause the devices to overwork themselves (spinning out of control) into failure (in effect, producing another version of a denial-of-service attack by means of a worm infection). Furthermore, Stuxnet would provide false feedback about the failure of the controllers until it was too late for human intervention to fix them. It is this level of sophistication that leads many to believe that it could have only been done by U.S. and Israeli software experts. The fact that there were so many variables involved with this level of attack implies that a new, advanced level of attack has now become the norm. As of 2010, the Stuxnet virus has affected many computers globally. Table 20.1 shows the distribution of all the estimated number of computers that the worm has compromised.
Clearly, the Stuxnet worm embodies the next generation of information security threats. The sophistication and targeting of this worm is absolutely unprecedented in the world of information technology. While this attack may be one of a kind in the present world, it is a glimpse of what may be to come in the future of information security attacks. Among the children of Stuxnet are the Duqu worm and one created by the Equation Group.
Table 20.1 Estimated Percentage of Computers the Stuxnet Worm Has Affected Globally
Country |
Infected Computers (%) |
Iran |
58.85 |
Indonesia |
18.22 |
India |
8.31 |
Azerbaijan |
2.57 |
United States |
1.56 |
Pakistan |
1.28 |
Others |
9.2 |
More Details of the Stuxnet Worm Used for Cyber Warfare
The Stuxnet virus was a significant attack from a political, economic, computer science, and cyber-warfare perspective. The virus is a Windows-based worm that used a then-unprecedented zero-day exploit. The specific purpose of the worm was to ruin centrifuges that were electronically controlled by an ICS. The target was an Iranian government–owned nuclear facility. What was most interesting about this act of cyber warfare is that it is believed to have originated from sources based in the United States.
As an ICS virus, Stuxnet was designed to target the specific controllers in use at that facility. The controllers were designed, built, and installed by the industry-leading supplier of such technology, Siemens of Germany. The worm, once installed, modifies the code on the PLCs, the industry versions of what many enthusiasts are currently employing.
An Arduino and a raspberry programmable logic unit are similar in nature, with input/output (I/O) pins capable of carrying out the industrial control functions of motors and other devices. The Stuxnet virus attacked three separate components: the Windows OS, the Siemens PLC software, and the PLC board itself. The nuclear facility had a network that was separated from the business network and from the public Internet. It was isolated and considered “localed down.” The design of the infection mechanism anticipated that technicians would bring information back and forth by means of portable USB flash drives (including those provided by Siemens) loaded with software, technical specifications, and instruction manuals. The designers anticipated that if the worm was installed in the USB drives at Siemens or on a technician’s personal computer—or especially on a computer in the more vulnerable business network of the enterprise—eventually, a technician would bring the infected USB drive across to the isolated SCADA management and control network. The process depended on an understanding of how technicians currently operate and perform their tasks. If one loads the worm onto a USB drive and the potential victim technician plugs it into an operational machine, it can spread within that closed but networked environment. Later, the worm can once again infect another inserted USB drive and be transported to the business network, where it can spread through the Internet. The worm quickly began to propagate internationally onto home and non-target industry business machines as well as other SCADA controllers. However, the worm very likely began its journey at the Siemens factory, where it was transferred to a flash drive and then transported around that factory either through the factory network or by a factory employee using a USB drive, where it could propagate and seek appropriate means to be transported to the target enterprise’s location and networks.
Both PLCs are conceptually similar to the Siemens logic board attacked by the Stuxnet virus. These boards use I/O pins that open up digital control functionality of analog technologies such as sensors and actuators. The nuclear facility had a local area network (LAN) that was locked down, so the attack vector was able to propagate the worm through USB flash memory drives. The attack goal was for an infected flash memory drive to make its way inside the facility to plug into a computer on the LAN to spread to centrifuge controlling machine(s). The worm itself was quite effective at spreading undetected, and it propagated internationally into home and non-target industry business machines. Eventually, the worm spread to a flash drive of a facility employee where it could propagate through the close LAN and infect the desired target machine(s). Once a machine within the LAN is infected, Figure 20.1 outlines the architecture that the Stuxnet worm is capable of navigating through and around.
USB flash memory was used as a secondary “Sneakernet” into private LANs such as the Iranian SCADA system. Once it reached a machine connected to the vulnerable Siemens hardware and software, it performed the following operations:
1. A kernel rootkit is installed on Windows to spoof digitally signed drivers
2. Stuxnet inserts itself into “Step 7” Controller Software by Siemens
3. A PLC rootkit inserts code to hide its presence in the Siemens PLC
Figure 20.1 The network architecture that the Stuxnet worm was designed to travel around.
Table 20.2 Four Steps in the Stuxnet Attack Procedure
Step 1 |
“The core of Stuxnet was a large .DLL file that deposited onto machines. This came packaged with dozens of smaller .DLLs and components inside of it, all wrapped together in layers of encryption that had to be cracked and removed before they could decipher the code.” |
Step 2 |
Stuxnet worm would “first check if 32 or 64 bit, only 32 bit was fully vulnerable.” |
Step 3 |
“If Stuxnet decided to proceed, the second driver then got activated. This one had two tasks—the first was to infect any USB flash drive that got inserted into the machine, which it would do for only twenty-one days after Stuxnet infected the machine. The second, and most important, task was to decrypt and load the large .DLL, and its various components, into the machine’s memory.” |
Step 4 |
“Once the large .DLL and its contents were all unpacked and loaded into memory, Stuxnet searched for new machines to infect and called home to the C&C servers to report its new conquest—but unless it found the Siemens Step 7 or WinCC software installed on the machine, Stuxnet would go dormant on the machine once these steps were done.” |
This layer-based attack embedded the malicious code deep within the operational layers of the Iranian nuclear facility, granting significant control and reporting its capabilities. Table 20.2 describes its attack procedure in greater depth but does not dive into the logic programming that took place. The computational science behind Stuxnet is addressed under the section “Stuxnet Deconstructed.”
Worms operate with a form of artificial intelligence (AI) or simple decision-making logic on how it might best be able to replicate and continue its survival and infection goals. The AI that was built into Stuxnet, after performing the prioritized activities listed in Table 20.2, would perform the secondary goal of replication. Stuxnet searched out channels whose details hardcoded into it, and its success depended on detecting one of the vulnerable avenues it was coded to look for.
The malicious hacker knows that the paths to success are often defended against, making success dependent on the art and creativity of detecting new attack vectors that are not anticipated and thus the most difficult to detect and defend against. The seven Stuxnet paths listed next were obtained from two information security researchers, Paul Mueller and Babak Yadegari at the University of Arizona.
Stuxnet searches for computers running Siemens’ WinCC as an interface to their SCADA systems. It connects using a password hardcoded into WinCC, and attacks its database using SQL commands to upload and start a copy of itself on the WinCC computer.
Stuxnet can use Windows shared folders to propagate itself over a local network. It places a dropper file on any shares on remote computers, and schedules a task to execute it. ESET says the task is scheduled to run the next day, whereas Symantec claims it is scheduled for two minutes after the file is shared.
Path 3: Via the MS10-061 Print Spooler 0-Day Vulnerability
Stuxnet copies itself, places the copy on remote computers via this vulnerability, and then executes the copy, thereby infecting the remote machines. In brief, Stuxnet ‘prints’ itself to two files in the %system% directory on each target machine, using the 0-day privilege escalation. It then executes the dropper file to infect the computer.
Path 4: Via the MS08-067 SMB Vulnerability
If a remote computer has this vulnerability, Stuxnet can send a malformed path over SMB (a protocol for sharing files and other resources between computers); this allows it to execute arbitrary code on the remote machine, thereby propagating itself to it.
Stuxnet will infect Siemens SIMATIC Step7 industrial control projects that are opened on an infected computer. It does this by modifying DLLs (Windows Dynamic Link Library; a library of shared objects: code, data, and resources) and an .exe file in the WinCC Simatic manager, so that they execute Stuxnet code as well. The additional code will insert Stuxnet into Step7 project directories.
While reports and estimates existed for the damage and effectiveness of the Stuxnet worm, official public recognition of the cyber attack did not take place until November 29, 2010. The president of Iran, Mahmoud Ahmadinejad, announced in a public statement regarding the cyber attacks’ damage that “They succeeded in creating problems for a limited number of our centrifuges with the software they had installed in electronic parts.”
Although a reliable primary source from the International Atomic Energy Association (IAEA) said that estimates of damaged centrifuges were around 1000–2000 units, the damaged centrifuges did not stop, but the attack did significantly slow the progress of the Iranian nuclear program. However, a secondary, hangover-like effect exists with worms that autonomously propagate and infect. In order to prevent a worm from continuously infecting new machines, updated definitions must be downloaded to the operating systems. Businesses and personal users are slow to update their computing equipment, leading to the same challenge that an unvaccinated individual would encounter when matched with a contagious viral infection. Although Iran was the specific target of the attack, worms do not recognize geographic boundaries of countries that openly participate in the Internet Corporation for Assigned Names and Numbers (ICANN) and domain name servers addressing shared through the Internet Assigned Numbers Authority (IANA). The list of countries infected by the spreading Stuxnet worm (including the United States) were
■ Iran
■ Indonesia
■ India
■ Pakistan
■ Uzbekistan
■ Russia
■ Kazakhstan
■ Belarus
■ Kyrgyzstan
■ Azerbaijan
■ United States
■ Cuba
■ Tajikistan
■ Afghanistan
A recent article by Michael Kenny, “Cyber-Terrorism in a Post-Stuxnet World” explains the lasting damage of cyber warfare on a global scale. Once a worm is introduced into the digital landscape, it acts as a model from which derivatives of similar code can develop. Politically, a damaging aspect of Stuxnet was the revealing information of a U.S.-sponsored or “state”-sponsored cyber-espionage project. Prior to this, involvement of the United States in cyber espionage was not recognized, and citizens heavily patronized the efforts of state-sponsored hacking.
Stuxnet marked a watershed in cyber warfare, not only demonstrating the United States’ willingness to engage in offensive cyber attacks against its most intransigent adversaries, but also revealing a level of physical destruction with computer code that was previously reserved for kinetic bombings and physical sabotage.
Once malicious code is used in an attack, the shrapnel of code it leaves behind is quickly dissected, analyzed, and repurposed by both malicious individuals and white-hat defenders. Unlike smart bombs that have millions of dollars of technology invested in them yet are rendered inaccessible upon detonation, intangible code lives on throughout systems. Once the Stuxnet virus was intercepted, new variations using the same mechanism emerged. Worms, viruses, and malicious code can often come back to haunt their own creators. From an economic standpoint, the lawlessness of the dark web will repackage and sell malicious exploits to the highest bidder(s) multiple times over.
The Stuxnet virus was innovative in its targeting of ICSs. But due to the release of a blueprint of this type to the world, new vectors of attack have become a reality. Much of the U.S. infrastructure is managed by means of industrial control systems such as the SCADA system provided by the Siemens Corporation. SCADA-controlled and managed smart grid technology has been implemented across the United States to manage electricity delivery where needed in a cost-effective fashion.
In December 2007, Congress passed, and the president approved, Title XIII of the Energy Independence and Security Act of 2007 (EISA). EISA provided the legislative support for the Department of Energy (DOE)’s smart grid activities and reinforced its role in leading and coordinating national grid modernization efforts.
The Stuxnet worm provided distinct lessons and mitigation techniques in the information security arena. Often, drastic security problems must be experienced to provoke others to implement the necessary measures to prevent such attacks. One such lesson is that even “air gapped” systems with heavy physical security can be breached when user behavior has not been secured.
Clearly, people are the weak link in security. It can be easier to trick people than to hack into computing systems by force. Social engineers exploit people’s natural tendency to trust and be helpful. These malicious social engineers also take advantage of our tendency to respond when faced with a crisis, acting quickly, sometimes to our own detriment.
Since this attack, a greater emphasis on the dangers of flash drives has been ever present in the computing environment. Many companies now operate with the assumption that they have already been breached and have not yet discovered what is leaking out. Monitoring three critical areas can assist with understanding when malicious activity is occurring inside a company:
1. Authentication: A mechanism, analogous to the use of passwords on time-sharing systems, for the secure authentication of the identity of network clients by servers and vice versa, without presuming the operating system integrity of either (e.g., Kerberos).
2. Authorization: A process ensuring that correctly authenticated users can access only those resources for which the owner has given them approval
3. Accounting: Provides the methodology for collecting information about the end user’s resource consumption, which can then be processed for billing, auditing, and capacity-planning purposes
Response and Industrial Control Security
With this framework in place, companies have at least a base protection and monitoring level. To provide ample defense, it is recommended that public entities such as governments and private entities create partnerships. These partnerships provide opportunities to share strategic security information about their breaches and mitigation techniques to provide better defenses for all. These threats will only increase in the future. Best practices exist for nearly all technical infrastructure, and these best practices need to be rigorously enforced and audited at a minimum. As more physical aspects of the world are controlled by information and communication technology, greater physical harm upon malicious activity can be inflicted. Seven techniques can assist in providing a base level of invasion prevention and a deterrent to malicious reconnaissance of potential target systems:
Whitelisting bans all software from executing unless it is on a maintained list of corporately approved applications.
Advanced firewalls: advanced security properties that can be configured in Windows Firewall.
Unidirectional one-way only gateways: one gateway to exit and another to enter.
Advanced intrusion detection software employing behavioral analysis.
Security information and event management (SIEM) software combined with log analysis software observes all activity and events that have occurred in the system and examines the log tapes containing a before and after picture of each instance of activity on the complete computer system.
Compliance managers on duty 24/7 to be consulted when any abnormal activity is detected.
The operation of an internal monitoring system observing all activity in real time as it occurs and comparing that activity to a maintained file of normal activity that is specific to certain individuals at certain times of day and days of the week and occurring against certain defined and approved systems.
Stuxnet provided an example of the entirety of what it takes to launch a relatively successful cyber attack. Once malicious code is released, it can be deconstructed and repurposed, much like obtaining the blueprints for a physical weapon. This was the first publically known malware designed for “real-world damage.” The lasting effects of this attack are still represented daily in the information and data security arena.
The U.S. government acknowledges the challenges a networked infrastructure can bring, which is why it developed one of the world’s largest “hack labs.” The National SCADA Test Bed (NSTB) was created in 2003 to help detect and block vulnerabilities such as the Stuxnet virus. The NSTB provides “a core testing environment to help industry and government identify and correct vulnerabilities in SCADA equipment and control systems within the energy sector.” This testbed offers significant resources for these industry and government stakeholders to use:
■ More than 17 testing and research facilities
■ Field-scale control systems
■ 61 miles of 138 kV transmission lines
■ Seven substations
■ Advanced visualization and modeling tools
The most updated cyber-security legislation relating to infrastructure within the energy sector was an executive order released in 2013, “Improving Critical Infrastructure Cybersecurity.” Like most science-based hobbies, there comes a time when technologies transition outside of the hobbyist world into mainstream production and are then leveraged as a platform for political means. Much like the adoption of social media, the malicious use of computer programming followed this same path.
The Vulnerable U.S. Electronic Power Grid
The U.S. electric power grid is divided into three regions. The Eastern Interconnection connecting the East Coast states, through to the Midwestern states ending in the Dakotas and down to Mississippi. The interconnections are made at many points and do not depend on a sole interconnection junction (Figure 20.2).
Figure 20.2 The U.S. electric power grid with interconnecting points displayed.
The Western Interconnection covers those western plains states all the way through to the West Coast states. A third region, the Electric Reliability Council, encompasses and serves just the State of Texas.
These three regions are then interconnected between themselves at multiple spots, leading to a completely interconnected national electric grid.
Within those three grids, there are a number of regional subgrids and regional governing authorities (Figure 20.3).
More than 17,800 generators are involved in providing more than 1,100 GW (gigawatts) of power to their interconnected set of connections. The system contains more than 211,000 miles of high-voltage lines and over 6 million miles of low-voltage lines. These lines serve over 125 million residential customers, more than 17.6 million commercial customers, and more than 775,000 industrial customers, plus local, state, and national government agencies.
The electric grid system is managed by a set of ISCs and SCADAs. It should come as no surprise that these management and control systems are constructed, deployed, and operated in the same fashion and with either similar or exactly the same control equipment. Siemens is both the primary designer of such control systems and quite frequently the provider of the specific ISC and SCADA hardware and software deployed on most systems that are dependent on processors controlling electric facilities, whether they be grids or centrifuges. If one knows how Siemens PLCs work, one can apply this knowledge to the entire infrastructure.
Components and Operating Elements of the U.S. Electric Power Grid
1. Generators and substations composed of protective relays, circuit breakers, transformers, SCADA remote terminal units (RTUs), surge arresters, phase shifter, flexible alternating current (ac) transmission systems, phasor measurement units, and sensors.
2. Lines and cables, including extra-high-voltage AC lines, high-voltage direct current (dc) lines, superconducting lines, fault current limiters, and dynamic line rating systems.
3. To control the electric grid network, a set of control centers incorporating the following energy management system components: state estimation, economic dispatch, unit commitment, contingency analysis, automatic generator control, phase monitoring and alarming systems, oscillation detection, and constantly updated system modeling systems.
A whole connected network of electricity providers including coal, wind, hydroelectric, and nuclear plants are used to provide energy to the power grid itself and through it the end users of supplied electric power across the United States.
There is a growing appreciation as to the importance of the intercommunication and information delivery networks for supporting the operation of this national power grid, including supplying information to the controlling components, data acquisition components, and the people who manage, support, provision, modify, fix, improve, extend, and modernize this smart electric power grid network. It is the information conveyed to the grid control components and the PLCs, monitors, and data acquisition and storage processors that make it a smart electric power grid. The foundation of a smart grid is the communication infrastructure, and the role of this infrastructure is to expand its functions to cover an increasing number of aspects of the entire power grid.
Key applications for communications technology in smart grids include enabling the efficient operation of solar cells, detecting faults in grid transformers, managing power peaks, monitoring power consumption in businesses and homes, controlling equipment that uses electric power, and communicating between the different pieces of equipment and management processors. The communication format can be selected to match the application, with possibilities including wired communication, wireless communication, and power-line communication.
Figure 20.3 The three grid regions of the overall U.S. power grid.
Wireless communication simplifies installation because no wiring is required, and a variety of wireless technologies is now available with transmission capabilities ranging from near-field to long distance. For example, remote meter reading (in which power usage is monitored at regular intervals) can be accomplished by incorporating power meters into a wide-area wireless network. It also seems likely that power-line communication (which uses existing electric power wiring) will become widely used for applications such as communications among different pieces of equipment within a single building.
A smart grid uses communications technology (networks) and information systems (computers with applications) to interlink and control all components of the power grid, including generating stations, distribution facilities, transformers, businesses, and households. It is a system intended to enable the stable supply and efficient usage of electrical power. The latest technology is used to give “intelligent” functions to the entire power distribution grid, making it a “smart” grid that is capable of reducing emissions of greenhouse gases and boosting energy efficiency.
The idea of the smart grid is not merely to bring innovations to the power distribution system. Its scope of application is broad and multibranched, and it is hoped that the adoption of smart grids will give rise to a variety of new services and industries. Businesses related to smart grids that are considered to have high growth potential include the following:
1. New systems for storing and managing energy
2. Sales and billing systems for solar energy, and so on
3. “Visualization” of power usage and AMR using smart meters
4. Household appliance control (demand response, demand side management, etc.)
5. Security (antitheft), fire alarm systems, and so on
Power plants, power-transmission towers, smart grid networks, smart grid operations and management centers, green power generation units, windmill transmission fields, and all the high-and low-power transmission lines comprise the electric power delivery system.
Irreplaceable Large Power Transformers and Our Smart Grid Risk
Ted Koppel’s new 2015 book Lights Out describes the danger of having tens of thousands of almost irreplaceable large power transformers (LPTs) installed across the United States. These transformers are on average 38–40 years old and are the most critical component in the bulk power transmission grid, sending electric power across large swathes of the country. These LPTs cost between $3M and $10M to replace and are manufactured overseas. As such, they must be transported by rail or truck to a shipping port, shipped to the United States, and then transported by flatbed truck across the country. The transformers are the size of a small house, and the trains and train tracks can no longer handle them. A road path must be cleared for giant special-purpose, 70-feet-long, 12-axle, extra-wide platform trucks to carry these transformers across country to the installation site. Then, specially trained and skilled technicians must test, update, and connect them to the SCADA networks and controlling PLCs, and then connect them to the power grid.
These transformers come in a variety of voltage classes, some in the 345–500 kV or 230–500 kV ranges, and many others, none of which are interchangeable. If you only have one variation available, you have to modify the whole transmission center to use a different one, rather than use one at the same capacity as the damaged one.
The LPTs are used to ramp up the power for distance transmission, and there are also an array of step-down transformers used to extract power from the high-powered grid and drop the voltage to the level required for local distribution. The local distribution center then controls the flow of lower voltage electricity to businesses and residences in local cities, towns, and villages and for use in the countryside: on farms, in barns, and in rural homes.
Although the LPTs themselves are not directly connected to the Internet, they and the step-down transformers are, by necessity, connected to the SCADA C&C systems for delivery of management commands and operational information feedback. These C&C management systems and the PLCs are networked together and are connected via a network to drive the transformers.
This is the same design as occurred in Iran, where it was assumed that isolating the SCADA C&C and PLC devices (which were on their own isolated network and were connected to and driving the centrifuges) provided security, due to their separation from the Iranian government network and the public Internet. However, as Ted Koppel points out, all it took to infect the Iranian PLCs and thus damage the centrifuges was for an unsuspecting technician to plug a thumb drive carrying the Stuxnet worm into the server on the C&C system network.
In the same manner, it would take only a power grid technician carrying his installation instructions, transformer specs, and step-by-step installation process (specific to that version of the transformer technology and PLC) on a USB flash drive for that SCADA system to be infected and for the LPTs to be damaged.
Those will be an attractive target for destruction similar to the centrifuges in Iran. They are controlled by the Siemens PLC processors; these are part of a Siemens SCADA network that is updated over the Internet, as well as being vulnerable to a tech plugging in a thumb drive containing instructions, pictures, and… a variation of the Stuxnet worm.
Power companies have been moving forward with the adoption of electronic meters and automated meter reading (AMR) as ways to reduce the personnel costs associated with meter reading (the manual checking of the gauges of electric meters to determine power use) and to combat tampering by means of magnets and the like. By adopting electronic power meters, power companies are able to collect a variety of types of data on power usage, allowing them to provide a more fine-tuned service. For example, by offering pricing plans that make it cheaper to consume power during the times of day when usage is lowest overall, they provide consumers with a way to save on their power bills (by using electricity when it is cheapest) and reduce the load on the grid during peak times.
Now, power companies are going further by introducing advanced metering infrastructure (AMI). AMI is defined as a comprehensive power control system that, in addition to AMR and improved service for consumers, includes capabilities such as operation and maintenance of power equipment over a wide area, support for recovery from natural disasters (such as lightning strikes), and sale of power from solar cells (sale of electricity to the power company). The electric meters with the advanced functions needed to make AMI a reality are known as smart meters. Smart meters can measure power usage almost in real time, and, by establishing communication links with the power company via a wide area network (WAN), it is possible to implement capabilities such as bidirectional power control and bill payment by means of prepaid cards. Future possibilities include enabling power companies to adjust air-conditioner temperature settings via the network in order to reduce power demand peaks. The introduction of smart meters is already required under national or state policies in some countries overseas.
Programmable Logic Controllers
The operation and control of this national electric power grid is performed by a set of distributed PLCs (computer processors), and the primary designer, manufacturer, deliverer, and maintainer of these components is Siemens of Germany. Siemens dominates the market for the controlling processors and software used to manage and control industrial systems, including nuclear, hydroelectric, and wind-power systems, all of which contribute to the electric power and the grid systems that transport and deliver electricity to users across the nation.
PLCs are capable of performing the same tasks as hard-wired controllers; however, with their advanced computer processors and software, PLCs are capable of more complex applications. PLC application programs and distributed electronic communication lines replace much of the interconnecting wires required by a hard-wired controller. Furthermore, PLCs allow for connecting and reconnecting by means of software and parameter changes, correcting errors and modifying the controlling applications. They do this in an easier way than local, hard-wired control devices (which are still frequently required to connect many isolated field devices), although they provide a much less flexible approach to controlling and interconnecting a set of distributedprocess components.
Some of the additional advantages of PLCs are that they are smaller physically than many hard-wired solutions and allow for easier and faster provisioning of changes. Also, PLCs have centrally available and integrated diagnostics and override functions. Finally, PLC applications can be updated with partial or complete new versions and can duplicate and further distribute those new versions over a controlled interconnected network in a faster and less expensive fashion.
Siemens makes several PLC product lines in the SIMATIC® S7 family, including the S7-200, the S7-300, and the S7-400, which are used by electric power companies across the world.
Distribution Transformers and Controllers
Distribution transformers are found in secondary substations and connect to three-phase low-voltage lines that deliver electricity to points of supply. Electricity customers are charged for their consumption based on the measurements registered in meters present at the point of supply. PLC signals are injected into key elements. The PLC signal PRIME is a narrowband PLC band, used by utilities for power line communication distribution transformers as propagation in the distribution grids. Technology in CENELEC A communicates with meters at maximum data rates of 122.9 kbps.
PRIME technology establishes subnet works rooting at distribution transformers in secondary substations, where the so-called base nodes are installed, to communicate with service nodes present at meters in smart metering environments. These are alternatives for PLC signal injection, either single phase or three phase, through different field tests, in order to improve overall network constitution and the performance of meters. The results and conclusions may be extrapolated to any other low-voltage PLC technology in the same frequency band. The conclusions of the paper make recommendations to use specific PLC injection configurations depending on the topologies under study, and they provide guidance for product development in this area, which has a fundamental influence on the results obtained for the PLC communication system (Figure 20.4).
Figure 20.4 Components of a typical PLC management and control system for distributed electric energy.
The optimization algorithm implemented for the energy management at the SCADA outer loop control could not be implemented directly on the SCADA system, as this complex controller needs mathematical operations that are not present at usually available SCADA systems. A strategy was developed to couple the SCADA system with The MathWork’s MATLAB® software.
The communication between SCADA and MATLAB was performed using the Dynamic Data Exchange (DDE) protocol. This communication protocol, developed in the 1990s but still very common, permits the exchange of data between two independent running (client and server) software programs.
In the developed application, the MATLAB software was the client, as it initiates the communication; and the SCADA software was the server, as it responds to the client’s requests.
Among the different information formats supported by DDE Protocol, the TEXT format was selected, as this format was supported by both SCADA and MATLAB software.
Four different communication protocols (LAN, DDE, MPI, PROFIBUS) are working simultaneously at different levels of the developed platform.
Local PLC Inner-Loop Controller
At the inner loop of the developed strategy (PLC level), several algorithms had been developed. These algorithms were built using the Grafcet methodology—Sequential Function Chart. The designed algorithms were implemented using the Ladder Diagram Language.
The main purpose of the developed programs associated with the RES stations is the monitoring of the electric power generated. Renewable Energy Systems Ltd. (RES) is a leader in the engineering, construction, and operation of electrical energy systems including wind, solar, transmission, and energy storage projects.
A SCADA system usually consists of the following subsystems:
1. RTUs connect to sensors and convert sensor signals to digital data. They have telemetry hardware capable of sending digital data to the supervisory system as well as receiving digital commands from the supervisory system. RTUs often have embedded control capabilities such as ladder logic in order to accomplish Boolean logic operations.
2. PLCs connect to sensors and convert sensor signals to digital data. PLCs have more sophisticated embedded control capabilities (typically one or more IEC 61131-3 programming languages) than RTUs. PLCs do not have telemetry hardware, although this functionality is typically installed alongside them. PLCs are sometimes used in place of RTUs as field devices because they are more economical, versatile, flexible, and configurable.
3. A telemetry system is typically used to connect PLCs and RTUs with control centers, data warehouses, and the enterprise. Examples of wired telemetry media used in SCADA systems include leased telephone lines and WAN circuits. Examples of wireless telemetry media used in SCADA systems include satellite (VSAT), licensed and unlicensed radio, cellular, and microwave.
4. A data acquisition server is a software service that uses industrial protocols to connect software services, via telemetry, with field devices such as RTUs and PLCs. It allows clients to access data from these field devices using standard protocols.
5. A human–machine interface (HMI) is the apparatus or device that presents processed data to a human operator, and through this, the human operator monitors and interacts with the process. The HMI is a client that requests data from a data acquisition server.
6. An historian is a software service that accumulates time-stamped data, Boolean events, and Boolean alarms in a database, which can be queried or used to populate graphic trends in the HMI. The historian is a client that requests data from a data acquisition server.
The basic controllers of the SIMATIC S7-1200 series are ideal for simple and precise as well as safety-related automation tasks and are mainly used in smaller, serial machines working as stand-alone.
Thanks to the integrated I/Os and flexible technology functions, the basic controllers have a minimal footprint and reduced hardware costs.
Moreover, another set of more advanced controllers are used for controlling medium and highly complex machines and for plant automation. Among these are the advanced controllers of the SIMATIC S7-1500 series, which are the standard controllers and support systems used for higher-level control, from controlling serial machines to controlling much more complex plants with high requirements. This Siemens SIMATIC S7-1500 controller series, the long-term successor to the S7-300 and S7-400 systems, which are still in use controlling the industrial environment, is the current standard for all factory automation, including complex safety-related applications.
The SIMATIC S7-1500 software controller is especially suitable for flexible control of special machines with high performance and functional requirements. The absolute independence of the software controller from the operating system has proved to increase the system availability. In addition to the new SIMATIC S7-1500 software controller, the range of the software controllers includes its predecessor, the SIMATIC WinAC.
The distributed controllers SIMATIC ET 200 central processing units (CPUs) combine compactness and flexibility.
Especially in the medium-performance range of machines with distributed intelligence or serial machines with limited footprint, the distributed controllers are the perfect solution for standard fail-safe applications. In addition to the SIMATIC ET 200SP CPUs and the new SIMATIC ET 200SP open controller, the proven SIMATIC ET 200S and ET 200pro CPUs are available as distributed controllers.
These Siemens data acquisition, operational control, and management systems are the modern prototype systems whose design, implementation, deployment, and utilization are common across the mechanized world. It is the control and ultimate destruction of such systems that the Stuxnet worm was designed to achieve.
New variations and mutations of that worm, enhanced by further transmission, infection, control, anonymity maintenance, and eventual destructive action, are entering the dark web marketplace and will soon target electric grid systems, telecommunication systems, air traffic control systems, train and road control systems, subway control systems, and the water and air purification systems of the United States and the industrialized, technology controlled world.
The Stuxnet worm was considered a “zero-day” threat since it took advantage of flaws and mistakes in the operating systems that are common to electric control systems, the systems themselves, the dependence on a single manufacturer to create the design, the software, and the devices that manage and control electrical systems, whether they be nuclear centrifuges or electric power grid controllers.
Furthermore, the systems are vulnerable to the simple process whereby technicians receive specification information, manuals of the operation, and repair and parts lists on digital files, which they can then carry in their pockets on USB flash drives around the standard data-processing routers and firewalls on the industrial system to isolated C&C system networks. This demonstrates the susceptibility that all systems have to simple vulnerabilities. Malware such as the Stuxnet worm has now been modified, extended, and made widely available. Ted Koppel terms it well in his new book. It is inevitable that it will eventually be “lights out” across America.
QUESTIONS
1. What is the process of infection by the Stuxnet worm?
2. What are the three target elements for a Stuxnet worm?
3. What are the five paths of the Stuxnet worm?
4. What is the vulnerability of the U.S. national electric power grid to infection and destruction by means of a variant of the Stuxnet worm?