Network security is a large part of information security for many different types of networks, whether they are public, private, government, or academic. Whether attacks are malware, denial of service (DoS), sniffing, or man in the middle (MitM), networks need to be properly secured against them to avoid a complete shutdown of services. To do this, it is important to get an understanding of network security threats in order to better understand how to protect networks against these threats with proper defenses.
Network security threats fall into four primary categories: confidentiality attacks, integrity attacks, availability attacks, and common attacks. Confidentiality attacks can include packet sniffing, or the fact that data being transmitted over Internet Protocol (IP) may be subject to decryption by a malicious attacker. For example, if a user is connecting to a server via the File Transfer Protocol (FTP), a malicious attacker could use a packet-sniffing software such as Wireshark to sniff critical information that can include the destination server IP, your user name, and your password.
Integrity attacks can include cross-site scripting (XSS). In these attacks, which prey on vulnerable web pages, an attacker will inject malicious code to essentially hijack a user’s session. Once the session is hijacked, the attacker can have the malicious code executed and send the victim’s data to a malicious database to be retrieved later by the hacker. However, this isn’t the only form of integrity attack. Recently, MitM attacks have preyed on weak computer cryptography protocols to intercept “encrypted” packets that may contain personal information (often banking information).
Availability attacks are most often DoS attacks. Attackers will use these methods when they would like certain networks to be rendered unreachable or temporarily disabled. There are two subclasses of integrity attacks: local DoS and remote DoS attacks. Local DoS attacks can include the injection of IP packets into a network, saturating the bandwidth to unusable levels and thus bringing the network to a halt. An example of remote DoS attacks can include the pinging to death of a web server, which can bring websites down for hours, even days, at a time. Availability attacks are performed on a daily basis throughout the Internet, and as their sophistication grows it becomes harder to defend against these attacks.
Common attacks can be attributed to address translation poisoning attacks and other routing attacks. A common tactic can include domain name system (DNS) spoofing. In this attack, the attacker will inject data into the DNS resolver’s cache. Once this has been performed, the name server will provide an IP address that was not originally requested but can navigate the victim’s traffic to another computer or server.
While these network attacks can be very menacing, there are plenty of defenses against them. For IP defense, a firewall can be put in place within your local network to help prevent malicious traffic from entering or exiting your network. Another defense that can be used is packet filtering. Packet filtering can help in common attacks by blocking incoming packets based on certain specific ports. Another key element of network security is the use of an intrusion detection system. These detection systems look for anomalies to see if there has been unauthorized access into a system. While these systems are not perfect, there is at least some mechanism in place if a drastic intrusion has occurred that a user might not be able to see.
Overall, network attacks are inevitable. However, there are proper defense mechanisms that can be put in place to at least combat attacks if they happen on a system.
We started out looking at a case study (the Anthem break-in) and tried to understand how the break-in happened and what tracking efforts were deployed by the company in an attempt to understand the events that took place. A combination of social engineering, watering-hole techniques, and spear phishing was used to infiltrate the company and inject potent combinations of spyware and malware to penetrate the systems more deeply. Through under-the-radar testing, hackers gained relevant knowledge concerning the capability of their software to infiltrate trial systems.
We evaluated the details and strategies that hackers used. Their attacks were composed of various types of malware and spyware, which included viruses, rootkits, worms, and so on. We also evaluated algorithms and Rivest–Shamir–Adleman (RSA). We briefly discussed browser security and web applications security, and then we looked at the domain name structure. Finally, having looked at the domain applications, we will now examine network security itself.
When we evaluate the network, we will primarily focus on evaluating Layer 2, Layer 3, and Layer 4 protocols. This is not to say that we should disregard the other layers in the seven-layer model (illustrated in Figure 14.1), but for now, we will focus on specific vulnerabilities affecting the access, link, and transport layers.
Figure 14.1 Layers of the TCP/IP process.
Starting with Layer 2, and given our familiarity with the MAC layer, we know that the Media Access Control (MAC) addresses in the network access layer are associated with the network interface card (NIC) and use 48 bits out of the available 64 bits. Frequently, Layer 2 is a point-to-point protocol over private lines. It tends to be a simple protocol, but it is nevertheless useful. At Layer 3, we’ve examined the IP, whose job is to address source and final destination segments that are passed to the network. We will also talk a little bit about Transmission Control Protocol (TCP) and will touch briefly on port numbers, which are used to create a connection between an application and TCP. This will establish a contextual reference that will set the stage for an exploration of the vulnerabilities found at all of the different network layers.
Note that there is an issue between MAC addresses and IP addresses. This is because, typically, users will use IP to go across the Internet. But when the packet gets close to the destination, the packet is delivered over Ethernet. Generally, it doesn’t need to look at the IP address to complete that transition. But given the nature of the situation, it essentially requires a translation process. The edge router will basically broadcast the request on that network, which may elicit responses from any device on that network. This serves to highlight the fact that previously, many of the communications taking place within the network were directed under inherent trust. Individuals’ operating devices trusted that other devices on the network were authorized devices. Therefore, it becomes obvious that vulnerabilities are built into this early model.
Also, part of the discussion will include border gateways, which act as the heart of the Internet. These are generally located in the backbone. Essentially, an area network and another area network are bridged through the use of border area gateways. These are subject to vulnerability.
Specifically, the following threats will be discussed in detail:
Packet sniffing (confidentiality issues): When packets go across the network, there are several ways in which a packet can be sniffed by several devices on the network.
Session hijacking (integrity issues): This involves diverting traffic to a different service.
Address translation poisoning attacks (common issues): This involves Address Resolution Protocol (ARP) and route table corruption, which is a common occurrence, as any device can respond to an ARP request.
Further, there are more concrete security problems. The following include ARP, which is not an authenticated protocol. Source IP addresses do not typically get checked. This poses a threat because seldom do devices check the veracity of the IP addresses. This provides hackers with the ability to give themselves a different IP address. However, MAC addresses provide some buffering for these issues. Additionally, network packets that are sniffed by untrusted hosts are also a concrete security problem. TCP state also poses a security risk as it can easily be guessed by hackers.
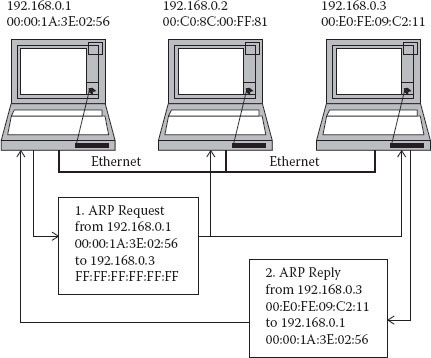
ARP is a broadcasting protocol that is primarily used to translate IP addresses to Ethernet MAC addresses. Each host (PC or server) on the network has a table of the IP and MAC address, and every switch also stores a table of the MAC and IP addresses. Together, they serve to provide address resolution between these two layers. Figure 14.2 illustrates the way ARP works. ARP represents a vulnerability because it is easy to spoof ARP requests and replies.
Figure 14.2 Basic Address Resolution Protocol (ARP) process.
ARP spoofing or poisoning occurs when hackers send fake or spoofed ARP messages to an Ethernet local area network (LAN). This allows hackers to trick machines into associating their IP addresses with the attackers’ MAC address. In other words, hackers are basically falsely putting in their MAC address and beating the authentic reply, and then essentially getting all the traffic from the associated IP addresses. What are the defenses for this type of spoofing? Prebuilding a static ARP table is one of the solutions; however, this is messy and hard to sustain as it does not easily allow for dynamic changes and requires a significant amount of maintenance. Other defense methods include Dynamic Host Configuration Protocol (DHCP) snooping, which allows users to leverage access control lists to ensure that hosts only use the IP addresses that are assigned to them and only enable access to authorized DHCP servers. Arpwatch can also be used to send out information, in the form of e-mail, to cycle through a verification process and improve transparency.
Note that IP is unreliable by design. In other words, it is a best-effort protocol that only serves an addressing purpose. The routers along the network path essentially only look at the destination IP address, and the routing tables are set up so that they provide the router with information concerning the output port and the respective MAC address associated with the device sending the packet, as opposed to the destination IP address. Routing does not make any attempt to get the packet to the destination but instead functions more as a distributed process. This type of protocol is different from the way specific types of networks work. Multiprotocol label switching (MPLS) is a good example of a network that attempts to identify the best path to the destination. However, IP is an addressing and routing protocol and not much else. This best-effort concept, realistically, creates some vulnerability. One of the key issues associated with IP vulnerabilities is packet sniffing.
Networks can be composed of host devices, switches, routers, and various network end-point devices, including servers. The vulnerability of some designs is observable when promiscuous listeners are attached to that network. Since generally the traffic going over both private and public networks is unencrypted, access to the network may compromise the integrity of the data traveling through the network. Having servers on multiple sides has made some networks particularly vulnerable to this kind of intrusion. As an example, consider corporate networks, such as that of Anthem. It is not uncommon for parts of their network transmissions to be completely encrypted, such as information coming from the outside. The problem then becomes more relevant when one notices that the information traveling within the corporate network is often not encrypted. If hackers acquire access to the inside of the network, data may be compromised, as was the case for Anthem. However, as a method of prevention, many corporations are putting in an effort to encrypt most of the data traveling through their networks based on the RSA encryption standards and IP security (IPSec).
UDP is a protocol that acts at Layer 4. It operates similarly to IP, which means that it doesn’t have a verification mechanism that ensures data receipt. There are minimal guarantees, as with UDP there are no acknowledgments, no flow control, and no message continuation. It differentiates itself from TCP, as its main responsibility is to separate traffic by port, whereas TCP segments each message and negotiates with the destination TCP device in order to transmit relevant data via IP. Given that it is dependent on the integrity of the data transmission, TCP is a connection-oriented protocol as it provides an acknowledgment of receipt at most stages of data retrieval, and lost packets are generally resent and reassembled in the correct order. Concerning TCP, one of the ways that hackers slow down networks is through the use of edge routers. These will be controlled so as to send small packets to reduce the window size, and then each one gets acknowledged. However, while UDP’s focus is smaller and provides no guarantees, it’s important to note that UDP still has value as most network management uses UDP.
TCP sequence numbering is yet another technique to which networks are particularly vulnerable. This takes place because hackers are able to guess and spoof the sequence number of the following packet in TCP communications. For example, take the basic three-way-handshake approach: In the first step, the sender chooses an initial sequence number that is ideally chosen at random. The destination then sends back an acknowledgment that it received that packet coming across, and it takes that sequence number and adds a unit to it. Every time a new set of communications is issued between the two nodes, there is a degree of predictability to each sequence number issued, so hackers tend to take advantage of this by predicting the number and then issuing counterfeit packets. While hackers don’t have full control of the network, they can easily introduce packets with fake source IP addresses and compromise the integrity of the data traveling the network. One defense measure commonly used for this type of hacker spoofing is to turn off the three-way-handshake mechanism.
There are many ways to hijack TCP sessions, and one of these is to use a malicious server in the sequence. These types of servers can be outside the corporate network and outside the firewall but still doing the same basic process. As illustrated in Figure 14.3, Attacker E is attempting to set up a connection. Attacker E is essentially trying to impersonate that server and other PCs that might be behind that server.
Figure 14.3 Attacker impersonation of server.
Attacker E sends a message to Server A, which is also communicating with User B. The attacker then impersonates Server A with the information gained from Server A’s response to the attacker’s message. If packets were exchanged, the attacker can also guess likely SYN numbers for imitation packets. SYN is the series or sequence numbers used with TCP segment in IP packets, especially during the TCP three-way handshake.
There are foreseeable risks that corporations take relative to session hijacking. The first element is data encryption. For example, inside corporate networks, data is often not encrypted. A potential solution to this is to create encryption tunnels within corporate environments to prevent malicious attacks from bogus clients and devices in the environment.
DoS is a type of attack that results from these types of vulnerabilities. Hackers can easily guess sequence numbers and then send and resend constant requests throughout the network to shut down connections. For efficiency, many systems are set up where a large window is negotiated, which enables a range of sequence numbers to be arranged. If the range of these sequence numbers is guessed, hackers have an opportunity to cause a lot of damage in the form of network package flooding.
DoS attacks have two main goals. One is to stop services in the network from operating, and the other is to exhaust the resources available in that network (Figure 14.4).
Figure 14.4 Two main goals of issuing denial-of-service attacks.
Locally, these attacks are focused on process crashing and forcing system reconfiguration. Remotely, the attacks are predominantly focused on sending malformed packets that crash buggy services.
Hackers try to send spawning process commands to fill the process table. Additionally, hackers tend to fill up the whole file system and saturate the communications bandwidth. Remotely, packet floods are used to block the network from utilizing its resources properly.
Synchronize (SYN) flooding is one of the standard approaches in which hackers send a string of messages after they have successfully guessed the sequence number. This string of SYN messages looks valid, and victim devices tend to not look at the source for further authentication. The victim allocates resources for each request as the data is stored and forwarded, which engenders a vicious cycle of continuous forwarding until timeout, which is capped by the new incoming packets. In essence, resources are exhausted, and incoming real requests are rejected as the network devices are operating at full capacity and bandwidth. It is no more effective than other channel capacity–based attacks today.
In this attack scenario, hackers tend to send ping requests to broadcast addresses via Internet Control Message Protocol (ICMP) echo requests. The result is a lot of responses as every host on the target network receives that ping and, therefore, generates another ping reply to the victim. This, in turn, overloads the victim with the resulting ping reply stream. To prevent this type of attack, users must not allow any remote ICMP echo request to come through, especially those with broadcast address destinations.
Internet Control Message Protocol
This is a core part of network management. Frequently, workgroups will have a responsible individual that will leverage ICMP to determine if there is a valid connection. Its primary uses include providing feedback about the network operation via error reporting, reachability testing, and congestion control.
Distributed Denial-of-Service Attacks
An attacker will create a botnet out of zombie devices. The attacker basically triggers the zombie devices to attack another victim network. The trigger will contain valuable information or details concerning the attack, and the devices will leverage this data to complete the attack.
There are a number of methods that hackers will leverage in order to hide the fact that they are trying to achieve a DDoS attack. First of all, they pursue companies that have a big distributed network. This makes it hard to distinguish whether the traffic coming in from zombie devices is false or whether it is authentic. Another technique they use is called pulsing zombie floods. This creates stop-and-start flooding, which also makes it difficult to identify the source of the attacks.
Cryptographic Network Protection
We assume that Layer 7 is where the applications programs are located. Layer 6 contains all kinds of routines related to remote procedural call software; this is also where encryption is housed. The next layer up containing TCP then passes it on with further information attached and moves the data through all layers. Generally, IPSec is what is used at Layer 6 for solving encryption issues. The commonly used technique known as clocking has been too easy to guess, so random number generators have become the desired approach for assigning sequence numbers.
While examining Layers 2, 3, and 4, consider Layer 1 as well. There is a common semantic misunderstanding as to what Layer 1 actually is. Layer 1 is not the media by which data is transmitted. Instead, Layer 1 is in the computer, and it is the connection to the transport media. An example is the Ethernet card, which enables communication between the Ethernet cable and the port on the computer. The physical layer encodes the bits that are sent out over the network. Layer 2 is in charge of the framing and transmission of a collection of bits into individual messages sent across a subnetwork.
Physical/Link-Layer Threats: Eavesdropping
Eavesdropping (also termed sniffing) is one of the threats found in Layers 1 and 2. This is becoming a particular phenomenon affecting cell phones. There are many ways to sniff at the physical layer. Multiple tools including Wireshark and tcpdump/windump are enabling the scanning or capturing of relevant transmission components such as MAC addresses. There’s a multitude of techniques that enable hackers and attackers to steal photons as well. The physical/link-layer threats do not just pick up the signal but also disrupt the signals.
Physical/Link-Layer Threats: Spoofing
Spoofing must have root administrative access to do damage, but the basic concept behind this kind of attack revolves around gaining physical access to a subnetwork. Once the attacker has gained access, they can easily create false messages. Spoofing poses a greater threat when it is combined with eavesdropping, as the attacker is able to determine the state of the victim’s communication. This further allows the attacker to create his or her own spoofed communication traffic, which matches that of the authentic network. The combined technique is known as bling spoofing.
Typically, the most vulnerable areas for Layer 3 components are the source and destination addresses, plus the routers and their routing tables. Keep in mind that the routers have a designated algorithm that they use to build their routing tables. They sustainably build and maintain the routing tables for themselves. Therefore, it becomes interesting to see how malicious devices create false links and routing processes to disrupt this process. Source IP addresses are never checked because the router does not care where things came from. It leverages the IP addresses solely to determine the next forwarding output port. Each output port has an associated MAC address attached to that port, giving hackers the flexibility to set packets with bogus or arbitrary source and destination addresses to disrupt the operation of these devices.
Fragmentation of the packets is another method commonly used by hackers to evade network monitoring. They also utilize timed fragmentation to avoid rotating monitor systems. By manipulating areas such as the time-to-live and the identification fields, hackers gain more flexibility, which helps them evade security checkpoints.
A variety of issues affect both TCP and UPD protocols at Layer 4. Among them it is not uncommon to find:
■ Disruption threats
■ Injection threats
■ Spoofing threats
TCP is not involved directly in the network. TCP is the sender and the receiver that sets up a flow control mechanism. The only place that TCP is involved in the network is when it acts as a slowdown mechanism that essentially reduces the window size to slow down the network for a temporary period of time. In most cases, we observe that there are only two TCPs talking to each other. Also note the specifications surrounding port numbers. The source and destination ports are built for a set of standard or known programs. Specific sets of ports are used for specific applications, and the remaining ephemeral ports are used mostly ad hoc. Also note that the upper limit for these ports has expanded in the last years.
The sequence number is then used as an authentication by that mechanism. TCP sends a FIN control message if it wishes to terminate (finish) a session with a destination site. The destination site must then reply with its own FIN control message to acknowledge receipt and acceptance of the finish of the transmission. If only one site wishes to terminate (finish) the transmission session, it sends an RST control message, which does not require acknowledgment. Given that it requires this acknowledgment, hackers have tapped into this and have issued false FIN messages to disrupt the process. This, again, is dependent on authentication that relies on sequence numbers, which, in turn, are easily guessed by hackers. By injecting data into the packet data field, hackers can also cause damage to the packet. But perhaps one of the most important areas of concern is servers that are attached to networks in which routers have been compromised. From here, traffic is diverted easily via that corrupted router.
Hackers use a technique termed blind spoofing to guess specific sequence numbers. Keep in mind that each host tells its initial sequence number to the other host. From here, hackers can easily guess the spec used to determine the sequence numbers and can prepare the remaining pieces of information to stage the attack (Figure 14.5).
Figure 14.5 Using blind spoofing to guess specific sequence numbers.
Once they’ve compiled all relevant data and have launched an attack that has given them access to a trusted network, hackers can then create a fake connection to leverage a server’s trust or to frame a given client. As a precaution, network engineers can leverage the use of a random number generator. However, this can become difficult to implement every day as routers don’t have a built-in random number generator.
Other varieties of network attacks include, but are not limited to, attacks that target
■ DHCP for bootstrapping Internet access
■ DNS for mapping hostnames to IP addresses
■ TCP cheating on fairness
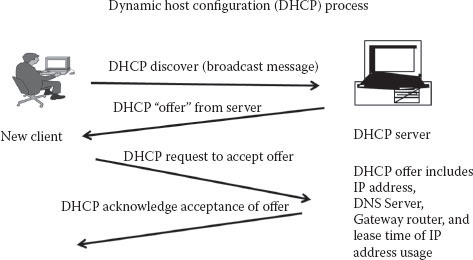
DHCP is a bootstrapping technique. If a new PC does not yet have an IP address, the device sends out a discovery message to a central DHCP server (frequently supplied by a corporation with a large number of employees requiring IP addresses), and the DHCP server will respond with loaned temporary IP number to be used by that device—frequently for that particular day but possibly for longer. In some situations, the DHCP server will provide static addresses, but the working assumption is that the company will leverage the DHCP servers to distribute, by lending, a more limited set of corporate IP addresses for temporary usage by its employees. Figure 14.6 illustrates the IP leasing process as it occurs via a DHCP server.
Figure 14.6 Dynamic host configuration process.
Historically, network engineers set up proxy servers on the edge of a corporation’s network. These proxy servers would loan external IP addresses to internal company workers to communicate with networks, particularly the public Internet, outside of the working corporate “intranet.” Using the inside private corporate intranet, users employ a private 10.0.0.0 set of IP addresses, which can be duplicated around the world since they only address within private IP networks. At the edge proxy server, the user is lent an outside public IP address to replace the local private 10.0.0.0 address. Given this mechanism, there are many types of threats that can impact this process. Attackers can position themselves at locations where they can listen in on new host DHCP requests. From there, hackers can spoof the entire process, even attempting to beat the DHCP server in its offer of a loaned external public IP address. If the “fake” IP address is accepted by the client requesting the address, then the next IP address issued by the DHCP server will be misaligned, causing disruption in the proxy server process.
If a threat is attached to the local internal Ethernet network, hackers listen to that internal network and send false replies, which will enable them to substitute a fake DNS server or substitute a fake gateway and to launch attacks including invisible MitM attacks.
When users send a message and a connection must be established, the alias name must be translated to a valid IP address expressed in binary (such as 176.142.76.12) via the use of an organization’s or an Internet Service Provider’s (ISP) DNS server. An example is if a message is to a distant DNS server that acts as the root DNS server. If that local DNS server is unfamiliar with that destination alias name, the local DNS sends the request on to the public Internet’s servers, which are provided in duplicate fashion at specific sites across the Internet. The public Internet’s DNS servers know all the local DNS servers that can provide the required alias to IP address translation. They forward the request to that destination local DNS, which provides the translation; this is returned to the original sender’s browser, which then substitutes that real binary IP address in the message to be transmitted. Meanwhile, the sender’s local DNS will remember that translation for a limited time, in case it is required again. If it is a repeated request, it is stored on a more permanent basis.
The DNS server process, then, is constructed in a hierarchical fashion, according to which only the local DNS servers know how to provide the local address translations for their local community. The public Internet’s DNS servers know where all the local DNS servers are located and which address translations they specialize in serving. Local DNS servers will contain all the local information, while the higher-level public Internet DNS servers have knowledge of the DNS servers’ availability, capability, and location; however, they don’t perform specialized address translations themselves, nor do they maintain the knowledge to do so. This equates to all translations being performed at the distributed lower levels of the DNS hierarchy. As a precaution, note that since all translations are performed at the local DNS level, if these become damaged or infected, communication becomes blocked or corrupted.
There is a formal protocol with a particular identification feature for the header. This is part of a UDP message that is included with the source and destination port number. Given that UDP is a best-effort protocol, much of the DNS functioning and network management is unacknowledged. If it doesn’t work, it doesn’t work. All communication over public and private networks depends on the DNS because individuals don’t know specific IPs but rather textual English aliases. Additionally, these IP addresses change on a constant basis; therefore, a system is used to reconcile the differences. The question is now what happens when attackers eavesdrop on DNS queries. The short answer is that they are, once again, empowered to cause a lot of damage to the network. More specifically, they gain the ability to redirect us with misinformation through corrupting of DNS tables. Again, since the DNS is subject to very little validation, this represents a big vulnerability in this system.
Blind spoofing is one of the primary ways to leverage information from the DNS to mislead users. Again, given the nature of UDP, there is no acknowledgment that can be provided to safeguard users. As a defense, it’s important to know a valid set of source and destination ports. However, keep in mind that valid ports can easily be spoofed. A random source port then can be used as a fix.
DHCP is a major source of vulnerability, given that broadcast protocols are inherently at risk of spoofing. When systems are first initializing, they are particularly vulnerable because they lack a trusted foundation. Finally, MitM attacks are insidious, given that there are no indicators that they are occurring.
DNS attacks tend to be opportunistic kinds of attacks. They tend to be fairly straightforward and are designed to poison the cache or the DNS. Specifically, attackers are trying to manipulate victims into engaging in vulnerable activity. Finally, attacks of this nature appear technically remote but can become real practical issues as they are often unforeseen.
QUESTIONS
1. Describe four primary categories that network security falls under.
2. Give an example of each network security attack.
3. What is considered the heart of the Internet and why?
4. What is used to translate an IP address to an Ethernet MAC address?
5. Why is ARP vulnerability important?
6. Explain what a pulsing zombie flood is.
7. What threat is found in Layer 1 and Layer 2?
8. What are the most vulnerable areas for Layer 3?
9. What is the primary way to leverage information from the DNS to mislead users?