Microsoft Vista: Securing User Access
Introduction
Windows Vista provides many security benefits, including enhancements to the Vista logon architecture, a new feature called User Account Control (UAC), smart card enhancements, and Network Access Protection (NAP). It also includes redesigned and redeveloped Remote Assistance functionality.
Although Microsoft designed Vista to be more secure, nothing really applies more security to your system than “defense in depth.” Defense in depth is the technical term for a secure system that is applied in layers. Vista provides a new level of security with its enhancements. This is combined with ensuring that users handle their credentials properly; that they understand other concepts of physical security, such as limiting access to the systems you want to secure; and that they comply with these concepts. When correctly applied, a security policy and other security defenses create a secure multilayered “onion.” If one layer is exploited or penetrated, others still stand guard.
Windows Vista is secure by design and offers many layers of security by itself. By following Microsoft’s Trustworthy Computing initiative, the developers of Windows Vista have designed the software to eliminate the most common Windows-based attacks, such as buffer overflows. In addition, other known weaknesses to the logon subsystems have been reworked. User access has always been an issue and tough to secure within Microsoft’s camp, but with Vista, secure advancements have been made to make these simple exploits a thing of the past. Because of the way Windows was initially designed, an attacker could exploit the OS’s subsystems in many ways with Vista gaining access to the OS by sitting directly at the console, through malware and other subvert tactics to deploy rootkits, is very difficult. Administrative access using the Administrator account was considered gaining the keys to the castle, so use of it has been severely limited as well. Many exploits have been designed to thwart the system’s access defenses, and many attacks have been developed to gain administrative access to the system. In the next section, we discuss the main updates to security user access within Vista and how to configure them. We also provide a brief overview of some of the most common attacks used to thwart a system’s access defenses and controls.
Access Control Fundamentals
To protect system and network resources from theft, damage, or unwanted exposure, administrators must understand who initiates this risky behavior, why they do it, and how they do it. Obviously, hackers and those with ill intent are the ones trying to gain access, but the methods by which they do constantly evolve, as do the operating systems (such as Vista) themselves.
Understanding the concepts access control can be vital to keeping any system secure. Ensuring physical access control means you will attempt to control physical access to the servers, networked workstations, network devices, and cabling connections. You also must be aware of other security considerations when working with wireless media, portable systems such as laptops and personal digital assistants (PDAs), and removable media such as Universal Serial Bus (USB) stick drives, DVDs, CD-ROMs, and external hard disks. By limiting your exposure, using secure methods of authentication, and practicing general workstation security, you will also inherently limit your exposure to risk.
Limiting Exposure
An effective security plan does not rely on one technology or solution, but instead takes a multilayered approach. Compare this approach to a business’s physical security measures; most companies don’t depend on just the locks on the building’s doors to keep intruders and thieves out. Instead, they might also have perimeter security (a fence), perhaps additional external security such as a guard or a guard dog, external and internal alarm systems, and, to protect special valuables, further internal safeguards such as a vault. Most administrators keep data backup copies off-site in a secure location in case of fire or some other natural disaster. For example an IT network and system security policy should be similarly layered.
For example, an effective IT security policy could incorporate the following:
■ Firewalls at network entry points (and possibly a DMZ or screened subnet between the local area network [LAN] and the network interface connected to the Internet) that function as perimeter protection
■ Password protection at local computers, requiring user authentication to log on, to keep unauthorized persons out, ensuring that all passwords used are limited by the user’s ability to keep them simplified
■ Access permissions set on individual network resources to restrict access of those who are “in” (logged on to the network)
■ Encryption of data sent across the network or stored on disk to protect what is especially valuable, sensitive, or confidential
■ Network and systems infrastructure (such as servers, routers, and switches) located in locked rooms with camera’s to prevent people with physical access from accessing data without authorization
■ Use of antivirus and other hardening applications such as host-based intrusion detection systems (IDSes), host-based firewalls, and spyware defenses such as Windows Defender
Understanding Attacks
Although there are many, some of the most common attacks to access control come in the form of attempts to bypass your secure credentials, or getting software on the host machine that can do it for you from the inside, also known as a rootkit.
Password Cracking
The best way to get into a system is to “trick” the system into thinking you’re an authorized user. In many cases, you can do this simply by using a valid account name and password. This method is called password cracking. In this section, we will look at the tools and resources hackers use to obtain and/or crack passwords. Security administrators need to be aware of all the techniques and tools that can be used to impersonate a legitimate user, and how they work. Understanding how a crack was accomplished provides valuable clues to the cracker’s skill level and how determined he is to get into a particular network, as well as other characteristics that can help track down the culprit.
In computer security, there are three basic ways to validate user identity: the “what you know” method (with the password being what you know); the “what you have” method mentioned, which requires physical possession of some object such as a smart card; and the “what you are” method, which uses biometrics data such as a fingerprint or retinal or iris scan.
It’s important to know that the vast majority of networks rely solely on the first method, so anyone who knows or can guess the correct password that goes with a valid username can get in. Password cracking involves acquiring valid passwords. This can be done in several ways, including the following:
■ Brute force attacks Brute force might not be the most elegant solution for a hacker in search of a password, but it can be very effective—especially if strong password policies aren’t enforced. In its simplest form, a brute force attacker tries one possible password after another until she hits on the right one. Although someone can perform this process manually with a lot of time and patience, in practice it is usually done (much more efficiently) using a program that runs through all the words in a dictionary file, which is simply a large list of words (in what is sometimes called a dictionary attack) and other possible character combinations. Some of these cracking programs are very sophisticated and allow the cracker to implement rules or criteria. For example, if the cracker is able to obtain some information about the password—for example, the cracker knows that it consists of five alpha characters and three numeric—she can create a rule that will limit the program’s attempts to passwords that fit the criteria (apple123, seven890, and so on). This strategy narrows the number of possible passwords and speeds the cracking process. Also note that newer password-cracking tools and programs grow more and more sophisticated—an entire attack can be launched from one program with multiple dictionary files, the program can intelligently append numbers and special characters to the equation in hopes of gaining access. Remember, Brute Force means just that—through brute force and nonstop checking, the password will eventually be cracked. The only way to defend against a brute force attack is to periodically change your password to a new and evenly secure one.
■ Interception of passwords Another means of intercepting passwords is to use a keystroke logger. A keystroke logger is a hardware device or software program that captures and records every character that is typed— including passwords. It is often possible to detect an unauthorized packet sniffer on the wire using a device called a time domain reflectometer (TDR), which sends a pulse down the cable and creates a graph of the reflections that are returned. Users who know how to read the graph can tell whether and where unauthorized devices are attached to the cable.
■ Social engineering Unlike the other attack types, social engineering does not refer to technological manipulation of computer hardware or software vulnerabilities, and it does not require much in the way of technical skills. Instead, this type of attack exploits human weaknesses—such as carelessness or the desire to be cooperative—to gain access to legitimate network credentials. The talents that are most useful to the intruder who relies on social engineering techniques are the so-called “people skills,” such as a charming or persuasive personality or a commanding, authoritative presence. Social engineering is, in many cases, the easiest way to gain unauthorized access to a computer network.
Rootkits
Despite its name, a rootkit attack is not a method of obtaining root account privileges—at least, not directly. It is a group of programs that install a Trojan logon replacement with a backdoor, along with a packet sniffer, on UNIX systems as well as Windows systems. The sniffer can then be used to capture network traffic, including user credentials, thus giving the user access to the root account by logging on with legitimate credentials.
Rootkits come in all shapes and sizes. For example, a rootkit can be hidden within any Trojan horse, or other form of malware. Four types of rootkits can cause you numerous headaches: persistent, memory-based, user-mode, and kernel-mode.
Persistent rootkits are launched every time the system is rebooted. If your system has a rootkit on it, if it’s persistent, every time you restart the system the rootkit will reappear, even after you think you may have cleaned it off your system. Persistent rootkits are commonly found deep within the file system or in the system Registry. Memory-based rootkits resides only in memory (RAM), and when the system is rebooted after it’s cleaned, the rootkit should be gone. User-mode rootkits are very tricky because they try to evade detection by antimalware programs. By intercepting system calls, the rootkit is able to trick the system into believing that it is no longer installed. Kernel-mode rootkits are quite possibly the worst, because like user-mode rootkits, they evade detection and directly manipulate the system’s kernel. This means that the rootkit could take itself out of a running process and not appear in the Task Manager, for example.
Using Encryption
Cryptography is a word derived from the Greek kryptos (“hidden”), and the use of cryptography predates the computer age by hundreds of years. Keeping secrets has long been a concern of human beings, and the purpose of cryptography is to hide information or change it so that it is incomprehensible to people for whom it is not intended. Cryptographic techniques are an important part of a multilayered security plan. Some security measures, such as implementation of a firewall and use of access permissions, attempt to keep intruders out of the network or computer altogether, much like fences and door locks attempt to keep burglars off the grounds or out of the house. Cryptography provides an inner line of defense. Like a wall safe that is there in case the burglars do make it inside your house—and to protect valuables from people who are authorized to come into your house—cryptography protects data from intruders who are able to penetrate the outer network defenses and from those who are authorized to access the network but not this particular data.
Cryptographic techniques concern themselves with three basic purposes:
■ Authentication Verifying the identity of a user or computer.
■ Confidentiality Keeping the contents of the data secret.
■ Integrity Ensuring that data doesn’t change between the time it leaves the source and the time it reaches its destination.
One or more of these goals may be a priority, depending upon the situation.
All three mechanisms can be used together, or they can be used separately when only one or two of these considerations are important. In the following sections, we look more closely at how each one works in relation to network security.
Cryptographic techniques include encryption, which involves applying a procedure called an algorithm to plain text to turn it into something that will appear to be gibberish to anyone who doesn’t have the key to decrypt it. Encryption is a form of cryptography that “scrambles” plain text into unintelligible cipher text. Encryption is the foundation of such security measures as digital signatures, digital certificates, and the public key infrastructure that uses these technologies to make computer transactions more secure. Computer-based encryption techniques use keys to encrypt and decrypt data. A key is a variable (sometimes represented as a password) that is a large binary number—the larger, the better. Key length is measured in bits, and the more bits in a key, the more difficult the key will be to “crack.”
Secure Protocols
The protocols used for authenticating identity depend on the authentication type. Some common protocols used for authentication include Kerberos and Secure Shell (SSH).
Kerberos
Kerberos is a logon authentication protocol that is based on secret key (symmetric) cryptography. It usually uses the DES or Triple-DES (3DES) encryption algorithm, although with the latest version, Kerberos v5, algorithms other than DES can be used. Kerberos uses a system of “tickets” to provide verification of identity to multiple servers throughout the network. Vista was also released with enhancements to the base Kerebos protocol so that it can now work with AES.
This system works a little like the payment system at some amusement parks and fairs where, instead of paying to ride each individual ride, customers must buy tickets at a central location and then use those tickets to access the rides. Similarly, with Kerberos, a client who wants to access resources on network servers is not authenticated by each server; instead, all the servers rely on “tickets” issued by a central server, called the Key Distribution Center (KDC). The client sends a request for a ticket (encrypted with the client’s key) to the KDC. The KDC issues a ticket called a Ticket-Granting Ticket (TGT), which is encrypted and submitted to the Ticket-Granting Service (TGS). The TGS can be running on the same physical machine that is running the KDC. The TGS issues a session ticket to the client for accessing the particular network resource that was requested (which is usually on a different server). The session ticket is presented to the server that hosts the resource, and access is granted. The session key is valid only for that particular session and is set to expire after a specific amount of time. Kerberos allows mutual authentication; that is, the identities of both the client and the server can be verified.
SSH
SSH was designed to replace the use of Telnet, an IPv4 based protocol found on the application layer of the TCP/IP based OSI model. Telnet is used to gain remote access into systems and provide for a terminal in which text characters can be sent to and from a client to a server. Because this protocol is extremely old, it is easily exploited. Telnet sends data back and forth in cleartext. This includes the “credentials,” such as the username and password. Because Telnet can be easily sniffed by a sniffer or acquired in a Man-in-the-Middle attack, using Telnet should be avoided at all costs.
SSH allows users to log on to UNIX systems remotely. Both ends of the connection (client and server) are authenticated, and data—as well as passwords—can be encrypted. 3DES, Blowfish, and Twofish are encryption algorithms that are supported by SSHv2, which also allows the use of smart cards.
Authentication Devices
Other hardware-based components of your network security plan may include devices that provide extra security for authentication, such as:
■ Fingerprint scanners
■ Retinal and iris scanners
■ Voice analysis devices
These devices can be used in environments that require a high level of security for secure and reliable network authentication. Microsoft has acquired Biometric API (BAPI) technology from I/O Software and plans to incorporate support for biometrics authentication devices into future versions of its OSes. Windows Vista systems support smart card authentication as the main form of verifiable secure access into the system.
Smart Card Authentication
The term smart card has several different meanings. In a broad sense, it refers to any plastic credit-card-size card that has a computer chip (a memory chip and/or a tiny microprocessor) embedded in it to hold information that can be changed (as opposed to less “smart” cards that use a magnetic strip that holds static information). A smart card reader—a hardware device—is needed to write to and read the information on the card. Smart cards can be used for different purposes, but one of the most popular is for authentication. Satellite television services use smart cards in the SATV receiver to identify the subscriber and that subscriber’s service level. Banks use smart cards for conducting transactions. These cards are especially popular in Europe.
Smart cards can also be used for network logon authentication. This provides an extra level of security, the “something you have” factor. The cards are generally resistant to tampering and relatively difficult for a hacker to compromise, because they are self-contained. They’re also inexpensive in comparison with biometrics authentication devices.
Smart cards used for logon authentication generally store a digital certificate that contains user identification information, the user’s public key, and the signature of the trusted third party that issued the certificate, as well as a time for which the certificate is valid. The certificates are stored on the cards by an authorized administrator. To log on with a smart card, a user must insert the card in the reader or swipe it through and enter a PIN that is associated with the card. If the PIN is compromised, an administrator can change it or issue a new card. To use smart cards for network logon, the computer must run an OS that supports smart card authentication, such as Windows 2000, Windows XP, or Windows Vista.
A number of companies manufacture smart cards and readers. Some vendors make keyboards that have built-in smart card readers, and there are combination fingerprint scanner/smart card readers for providing both card-based and biometrics security. Although smart cards provide for extra security, they (like all authentication methods) are not foolproof. Many cryptographers have been able to “break” smart card encryption. In general, there are two methods for defeating smart cards: logical and physical. An example of a logical attack is erasing parts of the data on the embedded microchip by raising or dropping the voltage; in some cases, this activity “unlocks” the security without deleting the data. A physical attack might involve actually cutting the chip out of the card and using a laser-cutter microscope to examine it. Although a determined attacker might be able to crack the smart card in this way, these methods are not easy and they don’t always work.
Biometrics Authentication
Biometrics authentication devices rely on physical characteristics such as a fingerprint, facial patterns, or iris or retinal patterns to verify user identity. Biometrics authentication is becoming popular for many purposes, including network logon. A biometrics template or identifier (a sample known to be from the authorized user) must be stored in a database for the device to compare to a new sample given during the logon process. Biometrics are often used in conjunction with smart cards in high-security environments. The most popular types of biometrics devices are the following:
■ Fingerprint scanners These are widely available for both desktop and portable computers from a variety of vendors, connecting via a USB or Personal Computer Memory Card International Association (PCMCIA, or PC Card) interface.
■ Facial pattern recognition devices These devices use facial geometry analysis to verify identity.
■ Hand geometry recognition devices These are similar to facial pattern devices but analyze hand geometry.
■ Iris scan identification devices Iris scanners analyze the trabecular meshwork tissue in the iris, which is permanently formed during the eighth month of human gestation.
■ Retinal scan identification devices Retina scanners analyze the patterns of blood vessels on the retina.
Keeping Workstations Secure
Many network security plans focus on the servers but ignore the risk posed by workstations that have network access to those servers. It is not uncommon for employees to leave their computers unsecured when they leave for lunch or even when they leave for the evening. Often there will be a workstation in the receptionist area that is open to visitors who walk in off the street. If the receptionist manning the station must leave briefly, the computer—and the network to which it is connected—is vulnerable unless steps have been taken to ensure that it is secure. A good security plan includes protection of all unmanned workstations. A secure client OS such as Windows NT, Windows 2000, Windows XP, Windows Server 2003, and Windows Vista requires an interactive logon with a valid account name and password in order to access the OS (unlike Windows 9.x or ME). These systems allow users to “lock” the workstation when they are going to be away from it, so someone else can’t just step up and start using the computer. Organizations must not depend on access permissions and other software security methods alone to protect the network.
If a potential intruder can gain physical access to a networked computer, he is that much closer to accessing valuable data or introducing a virus onto the network. Many modern PC cases come with some type of locking mechanism that will help prevent an unauthorized person from opening the case and stealing the hard disk. Locks are also available to prevent use of the disk drive, copying of data to disk, or rebooting the computer with a disk.
Improving the Logon Architecture
When Windows Vista was initially on the drawing board, many efforts went into redesigning the logon architecture. The logon architecture is the grouping of systems and subsystems that will allow you to log on to your workstation. Based on the “architecture,” it will provide a way to control the logon securely so that a security posture is maintained. If logon architecture was developed without security in mind, many exploits could be created (as they were in the past) to manipulate and exploit these subsystems and gain access to the system. Because Microsoft has to comply with C2 and other Orange Book standards, having a weak and crackable logon process is unacceptable.
With Windows Vista, the new logon architecture offers enhanced security benefits. Besides offering an improved, stable, and more reliable logon experience, Microsoft has completely rewritten the logon architecture to ensure that any services or functions not directly related to the logon process are now removed and used in other subsystems within Windows Vista.
The logon architecture has been completely redesigned to facilitate more secure forms of authentication, such as smart cards. Before Vista, many administrators and engineers held the responsibility of developing the Graphical Identification and Authentication (GINA) interface beyond what is was initially intended to do. Developers worked to supplement other forms of authentication, such as biometrics system, and other forms of security, such as one-time password tokens (OTPs).
With the redevelopment of the logon architecture for Windows Vista, Microsoft made sure that there was a stronger level of security that could (or should) be used when a user logged on to a system. Now, the primary form of authentication for Windows Vista is the use of a smart card. Because the logon architecture has been extended to meet new security demands, you can now work with new credential types easily by using the new Credential Provider, an application programming interface (API) that allows the Vista OS to remain secure, while still enabling users to write or develop code to interact with the OS. The Credential Provider API was created to support multiple credential types when logging on to the Vista system. Because Windows Vista doesn’t support the use of a GINA, it’s important that new Credential Providers handle this function—for instance, by allowing for multiple authenticating methods and devices, such as biometrics and smart cards. With the use of the Credential Provider API, you can now choose or combine multiple authentication methods when logging on to Vista. The Credential Provider also allows developers to manipulate the existing architecture to build new or future methods of authentication into Windows Vista.
The Windows Vista logon architecture has been completely redesigned in order to accommodate new security features that will make malware and other forms of exploitation almost nonexistent. When you log on to a Vista system, your logon request is handled by three separate sections: the Access Control services, the Cryptography services, and the secure OS. Within the Access Control module, you find Authentication services such as 2 factor authentication, logon, and identity controls. Authorization is handled by processes such as discretionary access control (DAC), mandatory access control (MAC), and Role-Based Access (RBAC), which is used to restrict system access based on authorized users. The Access Control module also handles auditing functions such as event logging. Credential management is handled within this module as well, so any use of a certificate server or smart card resides here, in the Access Control module.
Cryptography services are used to secure a user’s logon experience. This is done by using X.509, or the cryptographic application programming interface (CAPI), which is the cryptographic library provided with Microsoft Windows Vista. Once the secure OS is reached, new features such as isolated desktop and kernel-mode signing are utilized.
Session 0
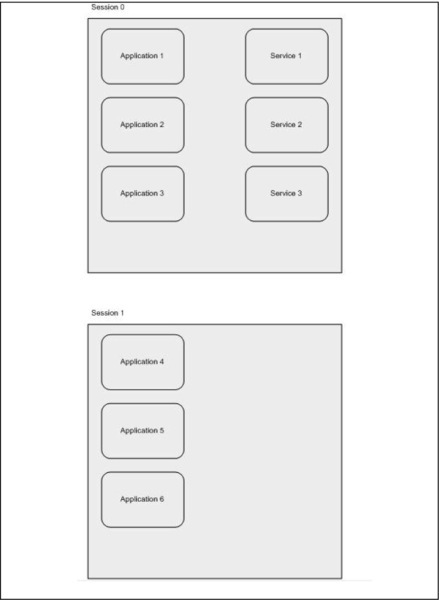
In Windows XP, Windows Server 2003, and earlier versions of the Windows OS, all services run in the same session as the first user who logs on to the console. This session is called Session 0. Running services and user applications together in Session 0 poses a security risk because services run at elevated privileges and therefore are targets for malicious agents who are looking for a way to elevate their own privilege level. Figure 3.1 shows how services and applications run within the same session. Each subsequent session is generated by a new logged-on user, as well as by remote users.
The Windows Vista OS mitigates this security risk by isolating services in Session 0 and making Session 0 noninteractive. In Windows Vista, only system processes and services run in Session 0, as shown in Figure 3.2.
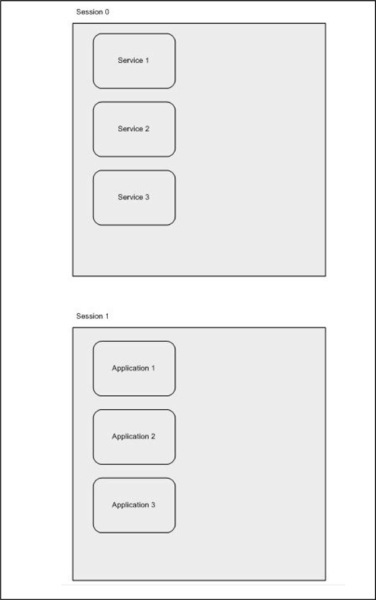
The first user logs on to Session 1, and subsequent users log on to subsequent sessions. This means that services never run in the same session as users’ applications, and are therefore protected from attacks that originate in application code.
Within the session, you also have the Winlogon process, profile selection, the Shell, and the local security authority (LSA). The LSA is responsible for validation of credentials in Windows. This was the case with Windows XP and Windows Server 2003, but with Windows Vista, WinInit handles the LSA, Profiles, and Group Policy, and in other sessions, Winlogon handled each credential provider under the Logon User Interface (LogonUI).
User Account Control
User Account Control (UAC) is a major development within access control and Windows Vista. For example, most of us remember how to use the Run As process. If you wanted to gain access to a process that required administrative privileges, you would have to use Run As so that the process you decided to use could be used with an administrative account if required. In previous versions of Windows, user accounts were configured as members of the local Administrator group, which in turn provided those users with unneeded system privileges and the ability to install and configure applications as well as perform management and administrative tasks on the workstation—all unneeded at times, and fixed within Windows Vista.
User accounts should not be able to do things they do not need to do. All that does is leave the door wide open for malware (or other forms of attack) that could compromise these accounts and allow access to system resources. Users should have only the privileges they need, and nothing more. With Windows Vista, UAC is used to separate user privileges from those that would require administrative rights and access. UAC defines access security by first limiting the surface area for attack. Accounts have been redefined so that if they are compromised, they will pose no security threat, but at the same time will allow for “nonthreatening” tasks to be functional, such as changing the clock’s time, for example. When administrative privileges are needed (such as when installing an application), the user will be prompted for an administrator password. UAC makes user accounts safer for use by prompting the user for approval before allowing him to perform any administrative tasks.
As we mentioned in Chapter 2, UAC will also help shield users from malware and other exploits by allowing each user to require an administrative password to be able to see and use content on the Web. As you learned in Chapter 2, with UAC and parental controls, users can now enjoy a safer Web surfing experience, and children will not be so easily duped into doing things that compromised security in the past.
UAC is also easier to understand. Now, when users are prompted for credentials, UAC more clearly defines what process is invoking it.
Using User Access Control
To use UAC, you simply need to boot your Vista system and use it, because it’s enabled by default. UAC will pop up when administrative privileges are required. Figure 3.3 shows the UAC logon screen.
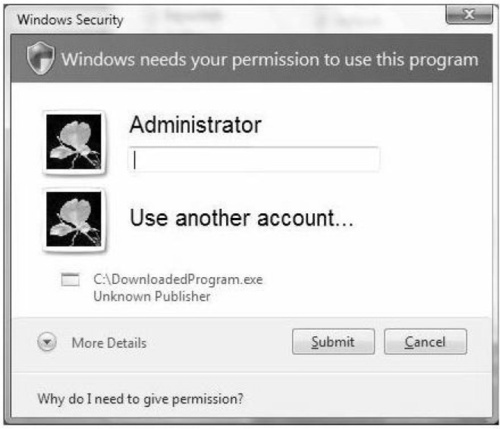
When UAC is invoked, simply supply the credentials needed. Also, note the program icon, which shows the path to the program that invoked UAC to begin with. Sometimes, if a program is malicious, it will appear to be an unknown program or from an unknown publisher. To allow this program to run, you simply need to click the Submit button within the Windows Security dialog. You can also specify different accounts to use if you prefer to not use the Administrator account.
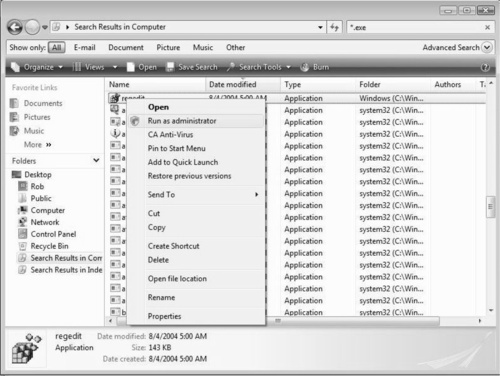
There are other ways to use UAC. For example, you can mark an application to run in an elevated fashion at all times, as well as set other advanced configurations. You also can disable UAC altogether. When you want to run a program as elevated, simply right-click the application to show the Run as administrator menu option, as shown in Figure 3.4. Here, we run Regedit, which is used to open and modify the contents of the Registry with administrative privileges.
Marking an Application
You can mark applications to run in an elevated fashion very easily by finding the application in which you want to configure and right-clicking it, selecting the Compatibility tab from the Properties dialog box, and under Privilege Level, selecting Run this program as an administrator. In Figure 3.5, we view the elevation of Regedit by modifying the privilege level to allow the program to run as an administrator.
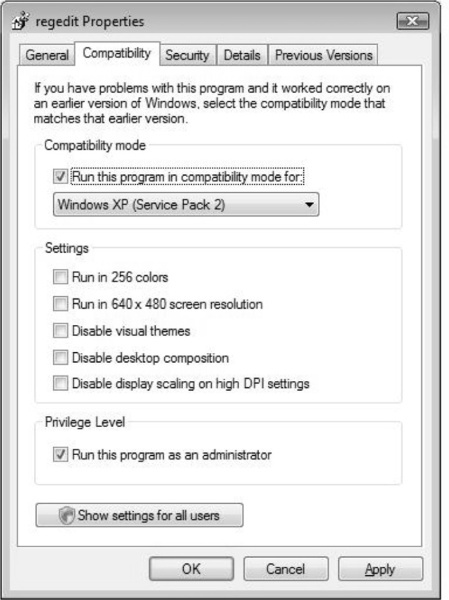
Using the Local Security Policy to Configure UAC
You can disable Admin Approval Mode and UAC from prompting for credentials to install applications, and change the elevation prompt behavior, by changing the configuration within the Local Security Policy.
To disable Admin Approval Mode and UAC, click on the Start menu. When you open the menu, select All Programs | Accessories | Run. Type secpol.msc in the text area to open the Local Security Policy Microsoft Management Console (MMC), and click OK. The Local Security Policy MMC will open, as seen in Figure 3.6.
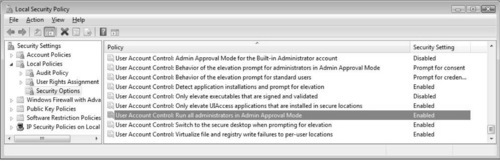
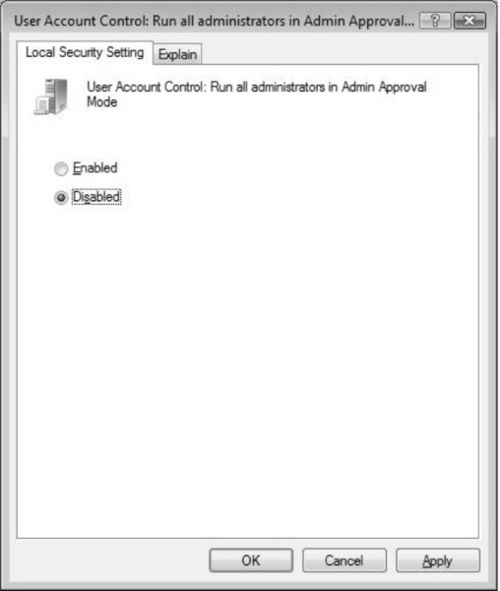
Once it is opened, drill down to the Security Options node in the MMC navigation pane. You can access this by going to Local Policies, and then clicking on the Security Options node. Scroll down until you find the User Account Control settings. Once there, you will find quite a few options you can adjust for UAC. Figure 3.7 shows disabling the Admin Approval Mode and UAC by selecting Disabled and clicking OK.
Disabling UAC When Installing Applications
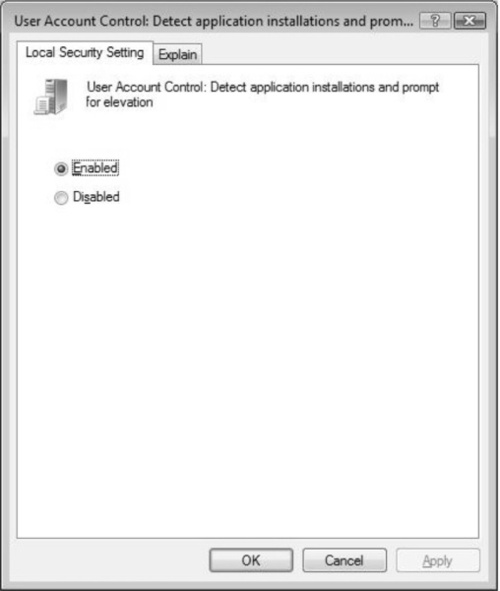
You may want to disable UAC from prompting for credentials to install applications if you trust the users using the system to install applications without being prompted every time they do. For example, some users may be trusted to handle the installation of applications on their systems, or you may support a number of remote users that need to install applications remotely from time to time. In cases such as these, you may disable UAC from prompting each time someone needs to install an application.
From the Local Security Policy MMC, drill back down the UAC options in the Security Options node and select User Account Control: Detect application installations and prompt for elevation. As seen in Figure 3.8, you can enable or disable this option. Click OK for the settings to take place.
Changing the Prompt for UAC
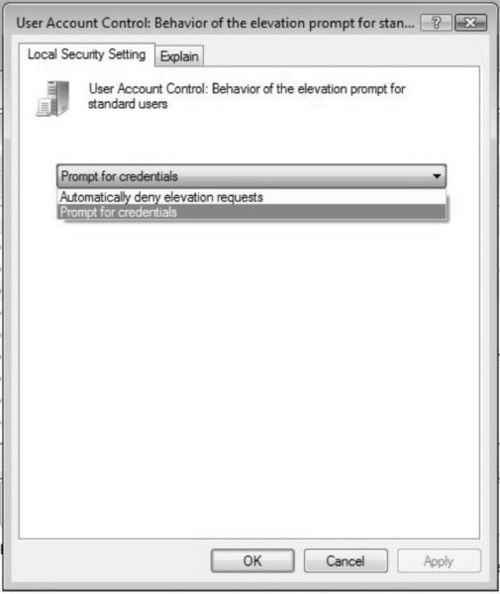
You can also change how UAC will be invoked by changing the behavior of the elevation prompt for standard users. When standard users use the Vista system, either UAC can prompt them or you can configure it to automatically deny any elevation requests. You would do this to lock down the system completely and not allow users to even be prompted when privileges need to be elevated. The user can either be prompted for credentials (this setting requires username and password input before an application or task will run as elevated) or denied completely. Figure 3.9 shows the UAC settings you can adjust.
Remote Assistance
With the advanced development in Windows Vista access control, it is no wonder that Remote Assistance has been redesigned and redeveloped. Remote Assistance has historically been used (or not used) to access user desktops and interact with users through their systems. For example, why pick up a phone and call when you can use Remote Assistance just as quickly, and it comes with Vista? Many times, Remote Assistance is not used and is simply disabled, but with the Vista enhancements you may want to try it out again. One of the major enhancements to Vista is simply the redeveloped communication architecture, which enables Remote Assistance to work more quickly and efficiently than in past versions.
As it has been redesigned, Remote Assistance is now a stand-alone application (it is no longer a part of the Help and Support Center). In addition, it has advanced session logging to keep track of what assistance has already been given. Windows Vista’s version of Remote Assistance has been limited to conserve bandwidth. Bandwidth is saved by disallowing the use of “voice” over the Remote Assistance session. Because Windows XP Remote Assistance supports voice sessions, it will not be compatible with Windows Vista’s version.
A more important issue is that a person who is running Windows Vista will not be able to offer assistance to someone who is running Windows XP. Therefore, if your organization’s help desk depends on Remote Assistance, you will probably want to make sure the help desk staff are the last ones upgraded to Windows Vista.
To access Remote Assistance, click the Start button and select All Programs | Maintenance | Remote Assistance. You can also change Remote Assistance settings by opening the Control Panel and selecting System and Maintenance. When you click on Allow remote access, UAC will check your credentials and then allow you to change settings. Figure 3.10 shows the Control Panel.
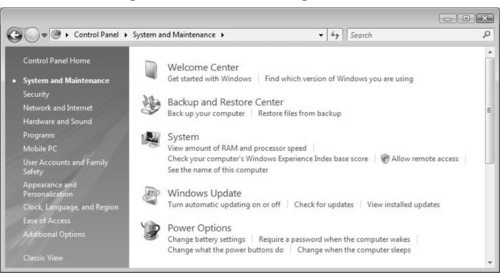
You can select the Remote tab in the System Properties dialog box, as seen in Figure 3.11. Here, you can allow Remote Assistance by selecting the checkbox. You can click OK to close the System Properties dialog box, or click on Advanced to change more settings.
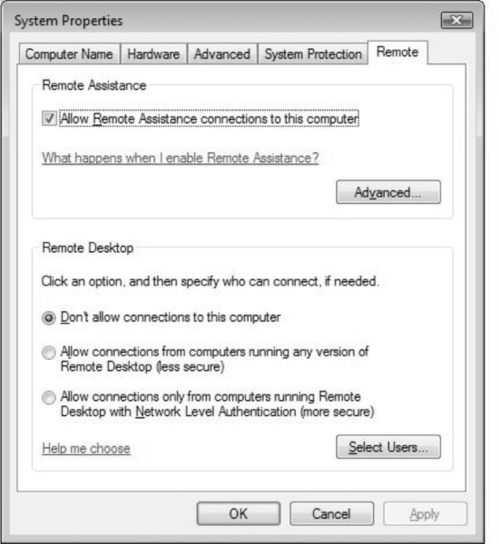
Figure 3.12 shows the advanced Remote Assistance Settings dialog box. Here you can adjust invitation settings and allow for remote control of the end-user system.
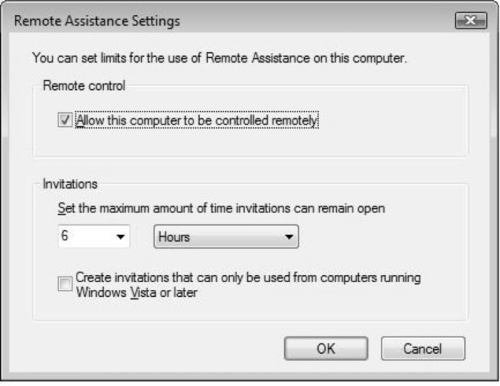
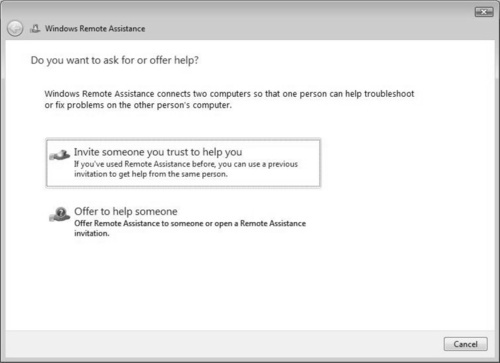
When launching Remote Assistance, you will see a screen that gives you the choice of either inviting someone to help you or offering to help someone. By selecting Invite, you are essentially saying that you trust that person to enter your system.
The newly developed Remote Assistance will allow for highly granular logging to an XML file stored on the local system. Although this version of Vista could have provided more information, it definitely provides more information than past versions of Remote Assistance.
Using Remote Assistance
To use Remote Assistance with Windows Vista, click on the Start button and then click on Help and Support. Under Ask Someone, click on Remote Assistance. Then click on Invite Someone You Trust to Help You. As you can see in Figure 3.13, two main parties are involved when working with Remote Assistance: experts and novices.
In order to use Remote Assistance, an expert will receive an invitation from a novice. The novice supplies the needed password to the expert and the expert can then connect using these credentials. The expert then initiates a session with the novice’s computer. The novice’s computer will also check to ensure that the expert used a valid invitation and that the invitation is still open. If the expert uses the correct password, the invitation is still open and valid, and the novice will receive a notification alert that the expert wants to start a Remote Assistance session.
Once the credentials are verified, the next step is for the novice to choose to start the session. Once this happens, the Novice Chat dialog box opens on the novice’s system and the Expert Console opens on the expert’s system. Now, the expert can control the user’s desktop and see what is happening in real time. The expert can use the Expert Console to “Take Control” of the novice’s system. This sends a message to the novice’s system that the expert is now requesting to take control of the system.
There are three methods by which the novice can stop the expert’s control of the novice’s computer: Press the Esc key, hold down the Ctrl key, and then press the C key, or click Stop Control next to the novice’s chat window.
Sending an Invitation
There are three available options for sending the Remote Assistance invitation: Windows Messenger, e-mail, or saving the invitation as a file. Select one of the three options to send an invitation to an end user.
Using Windows Messenger
You can use the Windows Messenger service to invite help. It’s the preferred method because it’s quick (it happens almost in real time), and an online indicator shows the novice that the expert is in fact online and can receive an invitation. Windows Messenger will also work better over the Internet by providing additional functionality and security. You can open Windows Messenger by going to the Actions menu, selecting and starting Remote Assistance, and then clicking on the desired contact. You can also right-click a Windows Messenger contact and select Start Activities, and then click on Request Remote Assistance.
Using E-mail
Another method in which a novice can send an invitation is through the use of e-mail. The e-mail will contain an attachment that includes the invitation from the novice to the expert. The expert will be prompted to provide a password when the attachment is opened.
Sending an Invitation As a File
In addition to Windows Messenger and e-mail, you can send an invitation in the form of a file. This option enables the novice to automatically save an invitation file to the local drive or to a network share. When the expert receives the file, she can double-click it to open the invitation and start the Remote Assistance session.
Network Access Protection
Microsoft has designed Windows Vista so that end-user access is secure, whether users realize it or not. With Vista, new security controls have been implemented to secure what accesses the system without the user’s knowledge. For example, you might not know that malware has infiltrated your system until it unleashes its payload. With Vista’s Network Access Protection (NAP), Vista has implemented a new level of security to secure access and control the spread of malware.
All Windows systems need security updates. To join a network, a system must comply with what’s called a health policy. This is usually maintained on a health policy server. With NAP, if a client does not meet the rules of a healthy machine, the system will not be allowed to join the network until it has been updated. NAP is a network access control system that lets IT administrators ensure that only “healthy” machines connect to their networks, while enabling potentially “unhealthy” machines to be cleaned before they gain access.
The NAP client in Windows Vista simplifies the enforcement of network health policies and protects against malicious network attacks by enabling organizations to establish requirements for client health status (such as current software updates and up-to-date virus scanner signatures), and enforcing those requirements when the client connects to the network. If a client machine does not meet the health requirements, NAP can automatically update the machine or direct it to a separate “quarantine” area until the user or administrator can fix the situation.
NAP is an extensible platform that provides an infrastructure and API for health policy enforcement. Independent hardware and software vendors can plug their security solutions into NAP, so IT administrators can choose the security solutions that meet their unique needs—and NAP helps ensure that every machine on the network makes full use of those solutions.
Summary
Windows Vista provides many new security benefits to secure access to users’ systems. User access control has always been a weak point for Windows systems, but with the creation of Windows Vista, those security issues have been addressed.
Microsoft created Windows Vista to eliminate the most common Windows-based attacks, such as buffer overflows and the manipulation and exploitation of service accounts. In addition, Vista provides secured user access. User access has always been tough to secure. Because of the way Windows was initially designed, an attacker could exploit the OS’s subsystems in many ways.
Enhancements to the Vista logon architecture include a new feature called UAC, smart cards, and NAP. It also includes redesigned and redeveloped Remote Assistance functionality.
When using UAC, you will not allow a malicious attacker to bypass controls placed on standard user accounts, because if one is jeopardized, it will most likely not offer any kind of path to administrative privileges that could be used for harmful purposes.
Remote Assistance is used to offer help to remote users working on systems with remote assistance available, such as Windows XP SP2, Windows Vista, and Longhorn. With Windows Vista, Remote Assistance has been redeveloped to allow for better use of bandwidth and more security controls. Be aware that some functionality in Vista will not interoperate with Windows XP SP2.
NAP, or Network Access Protection, is new to Windows Vista and Longhorn. With NAP, a new level of security has been implemented to secure users’ access to systems and control the spread of malware. NAP will ensure that your systems stay up-to-date. NAP keeps systems that are infected with malware or are not up-to-date from jeopardizing your network by not be allowing infected systems on to a network until they are updated.
Solutions Fast Track
Access Control Fundamentals
☑ Understanding access control is vital to keeping any system secure. Ensuring physical access control means you will attempt to control physical access to the servers, networked workstations, network devices, and cabling connections. You also must be aware of other security considerations when working with wireless media, portable systems such as laptops and personal digital assistants (PDAs), and removable media such as Universal Serial Bus (USB) stick drives, CD-ROMs, and hard disks.
☑ An effective security plan does not rely on one technology or solution, but instead takes a multilayered approach.
☑ Although there are many, some of the most common attacks to access control come in the form of attempts to bypass your secure credentials, or getting software on the host machine that can do it for you from the inside, also known as a rootkit.
☑ Defense in depth is a multilayered approach to network security. By using firewalls, access control with secure credentials, a security policy, and so on, you apply a layered security posture that is hard to unravel.
Improving the Logon Architecture
☑ The new logon architecture in Windows Vista offers enhanced security benefits. Besides offering an improved, stable, and more reliable logon experience, Microsoft has completely rewritten the logon architecture to ensure that any services or functions not directly related to the logon process are now removed and used in other subsystems within Windows Vista.
☑ The logon architecture has been completely redesigned to facilitate more secure forms of authentication, such as smart cards. Before Vista, many administrators and engineers held the responsibility of developing the GINA interface beyond what it was initially intended to do. Developers worked to supplement other forms of authentication, such as biometrics systems, and other forms of security, such as OTP.
☑ The Windows logon architecture provides two main components: Winlogon and the GINA DLL. A DLL allows one library of information to serve multiple executable programs that may all share the same information or library. Vista does not support a GINA; instead, Microsoft replaced it with Credential Providers.
☑ The Windows Vista logon architecture has been completely redesigned in order to accommodate new security features that will make malware and other forms of exploitation almost nonexistent. When you log on to a Vista system, your logon request is handled by three separate sections: the Access Control services, the Cryptography services, and the secure OS.
☑ In Windows XP, Windows Server 2003, and earlier versions of the Windows OS, all services run in the same session as the first user who logs on to the console. This session is called Session 0. Running services and user applications together in Session 0 poses a security risk because services run at elevated privileges and therefore are targets for malicious agents who are looking for a way to elevate their own privilege level. The Vista OS mitigates this security risk by isolating services in Session 0 and making Session 0 noninteractive.
☑ One of Windows Vista’s main enhancements is the development and use of smart cards as a way to access the system securely.
User Access Control
☑ UAC is used to secure access to administrative privileges by allowing only standard accounts to have limited functionality.
☑ Administrator accounts will run in Administrator Approval Mode by default, as will UAC. If changes need to be made, the “shield” icon will appear, marking the use of or need for administrative action. Unless turned off, UAC will be invoked when needed.
☑ User accounts should not be able to do things they do not need to do. All that does is leave the door wide open for malware (or other forms of attack) that could compromise these accounts and allow access to system resources. Users should have only the privileges they need, and nothing more. With Windows Vista, UAC is used to separate user privileges from those that would require administrative rights and access.
☑ UAC defines access security by first limiting the surface area for attack. Accounts have been redefined so that if they are compromised, they will pose no security threat, but at the same time will allow for nonthreatening tasks to be functional. When administrative privileges are needed (such as when installing an application), the user will be prompted for an administrator password. UAC makes user accounts safer by prompting the user for approval before allowing him to perform any administrative tasks.
☑ UAC is also easier to understand. Now, when users are prompted for credentials, UAC more clearly defines what process is invoking it.
☑ UAC will also help shield users from malware and other exploits by allowing each user defined to require an administrative password to be able to see and use content on the Web. With UAC and parental controls, users can now enjoy a safer Web surfing experience, and children will not so easily be duped into doing things that compromised security in the past.
Remote Assistance
☑ Remote Assistance is used to offer help to remote users working on systems with Remote Assistance available, such as Windows XP SP2, Windows Vista, and Windows Server 2007 (codenamed Longhorn).
☑ Remote Assistance has historically been used (or not used) to access user desktops and interact with end users. One of the major enhancements to Vista is simply the redevelopment of the communication architecture, which enables Remote Assistance to work more quickly and efficiently than past versions.
☑ When using Remote Assistance, an end user has to “grant” an administrator access and permission to connect to and manipulate his system.
☑ Vista will not be able to offer full assistance to someone who is running Windows XP. Therefore, if your organization’s help desk depends on Remote Assistance, you will probably want to make sure the help desk staff are the last ones upgraded to Windows Vista.
☑ When using Remote Assistance, XP SP2 will have incompatibility problems. For example, Windows Vista now allows you to pause a session, whereas XP does not.
☑ The newly developed Remote Assistance will allow for highly granular logging to an XML file stored on the local system.
Network Access Protection
☑ NAP is new to Windows Vista and Windows Server 2007. With NAP, a new level of security has been implemented to secure access and control the spread of malware.
☑ To join a network, a system must comply with a health policy, usually maintained on a health policy server. With NAP, if a client does not meet the rules of a healthy machine, the system will not be allowed to join the network until it has been updated.
☑ The NAP client in Windows Vista simplifies the enforcement of network health policies and protects against malicious network attacks by enabling organizations to establish requirements for client health status (such as current software updates and up-to-date virus scanner signatures) and enforcing those requirements when the client connects to the network. If a client machine does not meet the health requirements, NAP can automatically update the machine or direct it to a separate “quarantine” area until the user or administrator can fix the situation.
☑ NAP is an extensible platform that provides an infrastructure and API for health policy enforcement. Independent hardware and software vendors can plug their security solutions into NAP, so IT administrators can choose the security solutions that meet their unique needs—and NAP helps ensure that every machine on the network makes full use of those solutions.
☑ NAP requires functionality and support from the Windows Server 2007 OS. Although the NAP client for Windows Vista is included in the OS, Microsoft will also release NAP client support in Windows XP SP2.
Frequently Asked Questions
The following Frequently Asked Questions, answered by the authors of this book, are designed to both measure your understanding of the concepts presented in this chapter and to assist you with real-life implementation of these concepts. To have your questions about this chapter answered by the author, browse to www.syngress.com/solutions and click on the “Ask the Author” form.
Q: With all the computer and network security products currently on the market, why aren’t all systems completely secured? How do I completely control access to a system?
A: Despite all the excellent products available, the only completely secure computer is one that is turned off. Computer and network security includes a balancing act of security and accessibility, and the two factors will always be at odds. The more secure your systems are, the less accessible they are, and vice versa. Because the very purpose of a computer network is accessibility, no network can ever be 100 percent secure.
Q: Does it matter which remote access authentication protocols are used? Are some more secure than others? Should access control authentication protocols be used?
A: The two most common authentication protocols used for dialup Point-to-Point Protocol (PPP) connections are Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP). PAP merely sends the user’s name and password across the network to the server, in plain-text form. If the packets are intercepted in transit, the password can be read and stolen. CHAP uses symmetric encryption to protect the passwords that are sent over the network. However, the way CHAP works creates a new problem. The server generates a random key called the challenge and sends it to the client; the client uses the key to encrypt the password and sends the encrypted password back to the server. The server looks up the user’s password in its database, uses the same key to encrypt it, and compares the result with the encrypted password sent by the client. Although the plain-text password never passes across the network with this method, the server must store a plain-text version of the user’s password in its database in order to make the encryption for comparison. If an intruder accesses the server’s database, the intruder will have the passwords for all the users. Remote Authentication Dial-in User Service (RADIUS) is a more secure alternative.
Q: Exactly how does social engineering work? Why would anyone reveal his password to a stranger? Does this really happen?
A: Yes, it really happens—and more often than you might think. Skilled social engineers are good con artists; they are masters at making other people trust them. In large companies, employees often aren’t personally familiar with all other employees, so it’s relatively easy for the social engineer to stroll in or even call on the phone and persuade a user that he is a member of the IT department and needs the user’s password. The social engineer might have a convincing story, saying, for instance, that a hacker has gotten into the system and discovered all the password files, and now the IT department needs to know everyone’s old password so that they can reset them and issue new ones to protect against the hacker. Like all con artists, the social engineer usually plays on common human emotions. For example, the engineer will play up the danger that the hacker can access and destroy all of the user’s data if the “IT worker” doesn’t get the password immediately and make the change. In other cases, the engineer might exploit other emotions, such as people’s natural desire to help, claiming that the “IT worker” will get in trouble with the “big boss,” maybe even lose his job, if he is unable to get the password information needed. Social engineers are not above appealing to the user’s ego or pretending sexual/romantic interest in the user to get the password, either. Although some might not categorize it as social engineering, another technique involves simply spying on the user to obtain the password (“shoulder surfing,” or looking over the user’s shoulder as she types the password), or going through the user’s papers to find a written record of the password. Infamous hacker Kevin Mitnik is quoted as saying “You can have the best technology, firewalls, intrusion-detection systems, [and] biometric devices. All it takes is a call to an unsuspecting employee who gives up the information needed.”
