Chapter 5
Advanced Web Attacks
Information in this chapter:
In today’s web environment there is an explosion of dynamic or active content which has been used to deliver all sorts of experiences to the client and make their web experience more enjoyable as well as exciting. Content such as streaming media, audio, interactive apps and others have become commonplace due to the unique and powerful abilities that come with active content, its deployment and use. Dynamic content types such as ActiveX, Java, JavaScript and the like have had a huge impact on the usability and rich experience that web users have come to expect. We will cover these technologies in this chapter.
Of course with every benefit comes a downside and in the case of active content many new weaknesses have been exposed that made several forms of exploitation possible. In this particular chapter we see how increased complexity and features may make the web experience more satisfying, but at the same time, it makes it more challenging to secure.
What is Active Content?
Active content is a feature of websites and web applications that has emerged in increasing amounts over the past decade. Active content is any content that can be considered dynamic, interactive, or add more functionality to a web page. The intention behind active content on the web is to make the browsing and overall Internet experience more enjoyable. Common forms of this type of content include items that can display video, audio, Flash, toolbars, and much more. Active content can be used to create “splash pages” or options like drop-down menus on websites and web applications. With the use of active content, the options available for using it seem limitless. Figure 5.1 shows an example of active content.
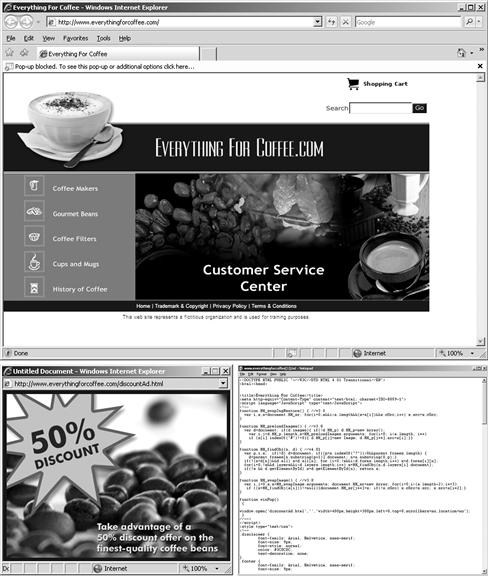
Figure 5.1 A Closer Look at Active Content
As seen in this example of active content, there are many technologies working behind the scenes such as JavaScript to provide much of the functionality used from menu selection to how the user interacts with the site. Based on this technology, you can only imagine the amount of exploits based on client-side attacking that can take place. That is what this chapter is going to cover—the dangers, and how to mitigate.
Warning
As shown in Figure 5.1, the active content and pop up windows triggered the Pop-up Blocker in Windows Internet Explorer. Make sure that when you attempt to secure your client from attack, this security method is chosen.
Did You Know?
Active content fits well within the definition of dynamic content as it represents a mechanism through which developers and designers can create an interactive and richer environment for their visitors.
Of course like any new technology all the forms of active content have been shown to lead to security risks of all types. Active content has been shown to be a credible source of threats such as phishing, buffer overflows, remote code exploits, and others.
What makes active content types such a security threat? In essence it is the fact that you, as the client, are downloading scripts and even whole executables and running them on your local system. Due to the nature of this interaction and setup it is more than possible for malicious code to be “pulled” onto a victim system and run providing information or resources to an attacker.
However, before we can take a look at the attacks that are possible, let’s take a look at the technologies that are considered active content and how each fits into the picture.
The problem is getting worse, with the ability to cause extensive and far reaching damage to systems malicious individuals and others are turning to active types of content to do things such as steal data and compromise systems.
A Mix of Active Technologies
Active content is a broad term and definition and can easily cause confusion as to what exactly fits the profile of this type of technology. In this section we will take a high level overview of the technologies included in the pantheon of active technologies and explore each one later in the chapter. In the following sections we will highlight the technologies considered as “active content” and then expand on each technology in more depth as we progress through the chapter and the book.
Java and ActiveX Controls
These technologies are very closely related and popular as forms of active content as we will see. Java and ActiveX are two technologies that act very similar as they both download software that is installed and run from a client system which can lead to untold problems. Over the past few years ActiveX and Java controls have been used to install all sorts of malware and other content on a system.
A Closer Look at Active Content Types
In the previous section we took a high level look at the different content types that are available and saw a little of what they are as an introduction. In this section we will examine each of these active content types a little close with the intention of seeing what makes them tick and the risks associated with each.
Microsoft Silverlight
Microsoft’s latest web development technology known as Silverlight is a web application tool that allows for the integration of multimedia, computer graphics, animation and interactivity into the web environment. The plug-in was first released as a video streaming plug-in with subsequent versions adding interactivity features and support. As of this writing the current version is 5. By most standards Silverlight is roughly equal to Adobe Flash in features and capabilities (not to mention security issues).
Silverlight is a free plug-in, powered by the .NET framework and compatible with multiple browsers, devices and operating systems. Silverlight is available for most browsers on the market, however it is limited to specific versions of the Windows Operations system like Windows Vista, 7 and 2008. It also relies on the .NET Framework. The .NET Framework is a software package developed by Microsoft that helps to supply much of the underlying technology needed to operate Silverlight such as the ability to do application development against it. It provides the class library used for Silverlight functionality.
Microsoft launched its Silverlight technology approximately three years ago as a platform for delivering rich media applications to web clients. This technology shares a lot in common with its competing technology Adobe Flash as it is designed to provide a means for presenting content and creating online applications. However, Silverlight should not be thought of as a mere clone of Adobe Flash, rather it does have enough differences to make it unique in some ways.
Microsoft has positioned Silverlight as part of a push of all its online services, but as a developer level service. The intention is to provide technologies that will allow developers to create dynamic applications and content, but like any tool the potential for abuse exists.
Note
Microsoft Silverlight is designed to allow the use of many different types of content including high-definition video. Developers who choose to use Silverlight even have the option of hosting their content on Microsoft’s servers so they do not have to host media files and other applications themselves. The idea is that developers can create high-quality streaming video and other applications and not have to worry about the reliability and availability of backend services.
Silverlight based applications work by delivering a special text-based markup language to the client’s browser known as XAML. XAML, known as Extensible Application Markup Language, is used to describe the content and graphical elements that the user will interact with and present content. In other words, XAML is what makes the content possible, but it is not something that user themselves actually see or even are concerned about. The use of XAML makes Silverlight different than its competing technology Adobe Flash. Whereas Flash applications are an amalgam of code and markup compiled into a single unit Silverlight presents plain text in the code of a web page that can be crawled and indexed by web pages.
The following is a sample of Silverlight XAML code:
<UserControl x:Class=“MySilverlight.Page”
xmlns=“http://schemas.microsoft.com/winfx/2006/xaml/presentation“
Note
Developers of Flash applications and content do have the option of wrapping their code in text and comments embedded in the web page code if they so choose, but they must actually make the effort. Silverlight applications on the other hand do not require this to be done through and extra effort as the text is already there making the application more findable.
Silverlight is still fairly new in the marketplace so it is difficult to pin down any specific security problems, but it is reasonable to expect that the security problems on the client side will be similar to what is in Flash.
You can also install and use the Silverlight Toolkit as seen in Figure 5.2. With this toolkit, the Software Development Kit (SDK) and other Silverlight tools and examples, you can delve into the inner workings of Silverlight to see how flexible the technology is. It will also show you how attackers can easily use this technology against you.
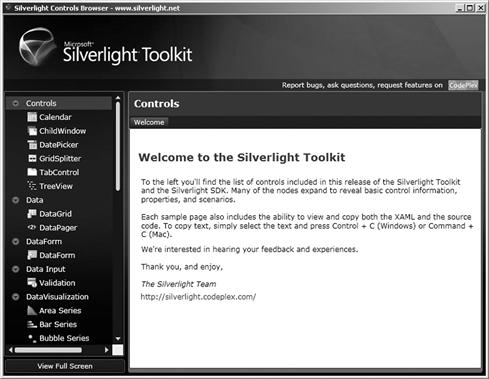
Figure 5.2 The Silverlight Controls Browser
As we have just covered, there are many types of technologies available to produce active content. There are also many others; however these are the ones that seem to be used most commonly. Others such as VBScript, Flash and Actionscript will be covered in more detail throughout this book.
All these active content types were never intended to be a security risk or be harmful to clients in any way, but each in some way has become a weapon in the hand of an attacker. While each browser on the market offers some capabilities that will block the use of such content most users are not willing to lose the functionality in favor of increased security. In light of the fact that users and companies are unlikely to shut off the use of such content it is up to us as security professionals to consider the risks of each technology accordingly, we will start with this process by taking a closer look at each of the technologies in turn. It should also be noted that in order to use specific sites and their added functionality, at times the end user may be required (or forced) to download and use specific technologies ultimately removing “choice” from the equation. It should also be noted that active content also exploits mobile devices just as easily as servers and desktop.
Did You Know?
Don’t be too focused on the fact that web browsers are vulnerable to the dangers presented here as the risks can be encountered in other situations such as with email programs. Don’t forget that the majority of email clients on the market support HTML and text formats for messages and as such it is possible to see some exposure on these clients and any client that can display HTML. Consider a web browser and an email client as equal—equally exploitable by active content.
ActiveX
ActiveX controls are a technology that Microsoft introduced in the mid-1990’s as a new web development mechanism. However even though the technology was first introduced in the mid-1990s it has a long and storied history that we will briefly cover here in an effort to give some background to how the technology works.
The ActiveX story begins with a technology known as OLE or Object Linking and Embedding. OLE was and is a technology that is designed to facilitate the creation of what is known as compound or hybrid document or content types. In layman’s terms this means that one could take an Excel spreadsheet and place it within a Word document allowing for the display of one piece of content with another. The advantage here is that new complex types of content can be made from different sources as well as allowing one to double-click on the content type to edit it in the original application that created it. While this was a beneficial feature, this foundation was built upon for what was known later as OLE2. OLE2 was introduced by Microsoft as a way to introduce a feature known as Component Object Model (COM). COM, in layman’s terms, is a technology designed to facilitate communication between applications and allow them to share data and services more effectively. COM, as a technology or process, was later used to much greater effect and degree in process and software that had nothing to do with compound documents such as ActiveX. In fact, ActiveX controls may even be viewed as the third version of OLE controls. Distributed Component Object Model (DCOM) was then created due to the distributed nature of applications to facilitate a better way to provide “middleware” between applications such as N-Tier designs where a front-end web server communicated with middleware installed via DCOM on application servers interacting with data on backend SQL database servers.
Implementation wise ActiveX is a technology that works by automatically downloading and executing on the client side (specifically in the web browser in most cases). Developers using their programming language of choice such as C, C++, Visual Basic or Java can develop their own controls to perform whatever task they see necessary. This also shows us something important about ActiveX, it is not a programming language itself, but rather a somewhat clearly defined set of rules that spell out how a control can be developed. This flexibility means that a developer is free to choose the language that they can author the control in, but also allows for a wide range of possibilities for both friend and foe alike. Figure 5.3 shows what an ActiveX Control is used for and the forcing of an installation for software that may or may not be malicious.
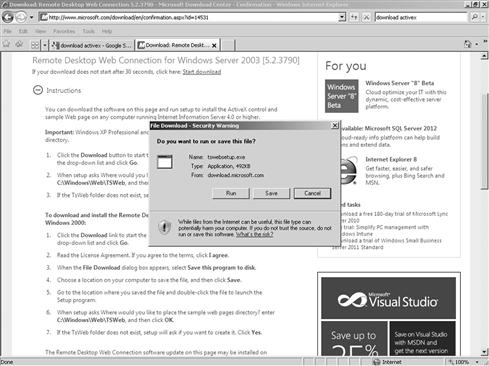
Figure 5.3 Downloading an ActiveX Control
ActiveX has numerous potential security problems, some of which we will examine here to gain a better understanding of how a malicious party can exploit weaknesses in the technology.
Warning
ActiveX can be particularly problematic to security due largely to the way it operates on a system. ActiveX functions by using the resources of a system for example using memory, hard disk and network connections on the local computer. Upon further consideration it is easy to see that ActiveX could easily be used to consume resources on a local computer or even read personal settings and data on a computer.
ActiveX primarily relies on digital signatures to improve security from a trusted third party which usually is an entity such as Verisign. The goal of this signature is to give the client a clear idea of who created the control as well as assert that the control is trustworthy to a degree. Signatures are placed upon the control when it is created and stay with the control during its lifetime or until it expires.
Enhancing the security of ActiveX even further is something known as Authenticode which is built into Internet Explorer itself. This technology is designed to more thoroughly check a digital certificate and verify that it has not been altered prior to download. Authenticode, in the default configuration of Windows, will not even allow a control that is unsigned to be downloaded much less installed on a system. Of course users can make themselves victims of malicious controls if they choose to override the defaults and allow unsigned controls to be installed without prompting them about the danger as seen in Figure 5.4.
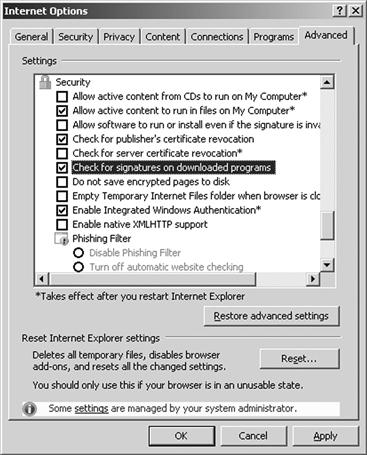
Figure 5.4 Configuring your Browser to Prompt for Unsigned Controls
Microsoft has made many recommendations over the years telling users not to download controls that are not signed, but this has not stemmed the tide any and users still download questionable controls at their peril. You can see what ActiveX controls have been download and installed as well as delete them within your Internet Options within Internet Explorer as seen in Figure 5.5.
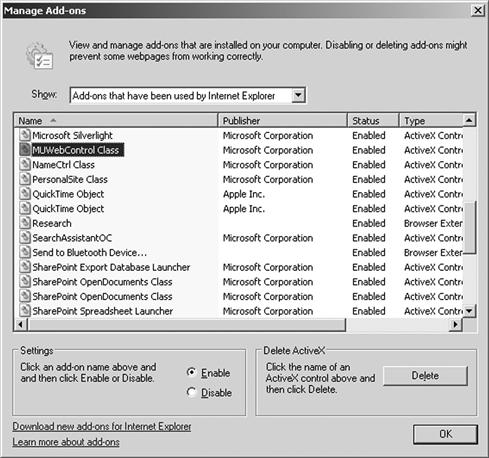
Figure 5.5 Adding and Removing ActiveX Controls
Warning
Many types of spyware that have cropped over the last few years have been made possible through the use; some would say abuse, of ActiveX. Interestingly enough, some spyware gets installed through ActiveX without having to sneak by the user and install in the background due to its ease of use, tie-ins to the base operating system and most times, lack of configured security options. In these cases the spyware is installed with the user’s consent even though they may not know it as the installation permission is hidden inside a very long and confusing license agreement. This leads to a lot of spyware getting installed successfully and with a user’s consent (even though they don’t realize it). Interestingly enough ActiveX usually prompts the user with a security warning, users have been known to fail to treat these warnings in a cautionary manner and instead treat it as a sign of approval because the control typically is signed with the help of someone such as Verisign or whatever other Certificate Authority (CA) approved it. Most times however, it can come from an un-trusted source and appear as though its trusted. Lastly, making this even easier the author of the spyware would be a situation where the user has low security settings which allow them to bypass the security warning completely. This final situation could occur if the security settings are set to “enable” instead of “prompt” for ActiveX objects and controls.
Probably the biggest security risk with ActiveX controls is the simple fact that they have almost unlimited access to the client system. Any Windows system that is running an ActiveX control is particularly vulnerable as this configuration gives full access to the operating system meaning that the risk is much higher. In fact due to the unique nature of ActiveX controls and the unlimited access they have to the host operating system the risk of running them is much higher than compared to any of the other technologies discussed here in this chapter. To help mitigate this risk and reduce the exposure to the client Microsoft did develop the system of registration designed to authenticate a control prior to download, but this is not total security for the client. You should also be aware that ActiveX technology now comes integrated into many other software packages such as Flash.
As briefly discussed earlier, a potential risk in Internet Explorer due to ActiveX is something known as the drive-by download. In this technique and attacker preys upon the fact that users do not typically read the license agreement or have reconfigured their browser to not display warnings. By using this technique with the user’s lack of interest in security or protecting the browser an ActiveX control can get installed quite easily taking control of a system or gathering information from the client. To prevent this from happening Microsoft introduced a feature known as ActiveX Opt-in in Internet Explorer 7. With this feature enabled the user will be prompted if they wish to install a new control or not potentially preventing controls from getting installed without the user’s knowledge. Figure 5.6 shows the ActiveX Opt-In prompt feature.
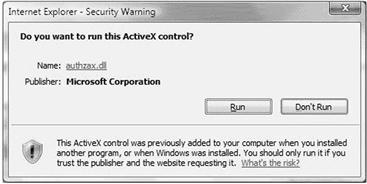
Figure 5.6 Warning when Installing ActiveX Controls
This feature simply prompts the end user that they may be installed an ActiveX control and that they now have an option to run (install) it or not to run (install) it. This then increases the security level of the end user system.
Warning
Software security features can only do so much, even if a user is prompted as to whether or not they wish to install an ActiveX control it is still up to them to proceed or not. If a user still chooses to proceed because they really want to view a site or a type of content there is not much a security feature like Opt-in can do.
Starting with Internet Explorer 7 Microsoft introduced a new feature that provides some protection if a user installs a malicious control, this feature is known as Protected Mode. Protected Mode is only available on the Windows Vista and Windows 7 and Windows 2008. This mode is designed to limit the access malicious content may acquire within the browser and reduce security risks. When this mode is active, which it is by default, Internet Explorer is run as its own isolated process away from other applications immediately reducing the access that anything within the browser may acquire. In fact content within the browser will only be allowed to access two parts of the system a virtualized part of the registry and the Temporary Internet Files folder without further approval by the user.
As you can see ActiveX is a rich and deep technology that can enabled many types of features and abilities within a browser, but at the same time it can be a nasty security risk. We have outlined its basic functionality and how it can be secured at the basic level.
Java
Java is another popular programming language originally introduced by Sun Microsystems in 1995. Since its debut it has become a very popular choice for developing applets, applications, utilities, games, and enterprise applications. Currently Java is supported on a wide range of platforms and technologies including set top boxes, personal computers, handheld devices, and other devices.
Note
Java is supported on just about every major platform including Linux, Unix, MAC OS X, and Windows. The last of these platforms is the most interesting case however as Windows requires a little extra help to support Java. Due to contractual disputes between Sun and Microsoft in the late 90s Microsoft’s license to include Java with the Windows platform was not renewed meaning that third parties must provide this support. Microsoft no longer includes Java with its Windows operating system meaning that those wishing to use Java must seek out third party options to obtain this support.
Java works across multiple platforms by utilizing something known as a Java Virtual Machine (JVM). A Java Virtual Machine is an application or software appliance that is used to execute Java code or “applets” as provided, in this case, by websites. Java applets are installed on a system by a visitor accessing a web page and having the browser automatically downloading the applet and executing it via the Java Virtual Machine. During subsequent visits to the website the Java Applet is cached and starts running much quicker due to the lack of download time.
One of the big benefits of the Java development platform and language is the inclusion of a number of robust security features. Java was designed to include many features that make it one of the more secure development environments and much less prone to attacks that may introduce malicious code and unknown elements onto a system.
One of the biggest security benefits of the Java platform however has to be its sandboxing model. This feature in the Java environment effectively isolates applets and their code within a special software construct that limits their access to resources on the system. The main benefit here is that with unknown or risky applets a high degree of security is provided or ensured as untrusted code does not get any sensitive access where it is not advisable. In the Java environment code will continue to run in this isolated environment until it has been verified through means of a digital signature and through the user actually approving it as trusted.
Did You Know?
Sandboxing is not unique to Java applets and is in fact used in many different applications and environments. Within the context of clients and web security technologies that offer sandboxing as part of their model include Adobe Flash and Silverlight. No matter the environment the concept is still the same however which is that applications or applets receive limited access to the host’s resources.
Java along with ActiveX represents a large portion of the security vulnerabilities present in client-side environments and plug-ins. In fact over the last few years Java has come in second only to ActiveX in the amount of serious vulnerabilities that have been uncovered and exploited. In some cases exploit code exists in the form of proof-of-concept code which show how a particular exploit may be carried out by a properly motivated party.
Did You Know?
Proof-of-concept code is generally created by security researchers and other White hats to prove that a threat and vulnerability exists and is viable. White hat hackers are security professionals who perform exploits to test and understand the exploits their counter-parts (Black hats) do for sport, profit and malicious reasons. Proof-of-concept code is not meant to be used to create any sort of mayhem or maliciousness in the real world, however this does not mean that it cannot be used by a malicious party to do so.
Another area that makes Java particularly easy to target is the extreme proliferation of vulnerabilities and exploit code used to take advantage of these weaknesses. It has been found that numerous exploits that are not merely proof-of-concept, but full blown code and tools designed to leverage the weaknesses in Java applets. The sheer number of exploit code available to take advantage of Java’s failings makes it impossible to focus on any one piece of code, but it also underscores the importance of developers, site owners, and security professionals to be more vigilant in their countermeasures.
Some other potential security risks that can be problematic for security professionals and users of Java are as follows:
![]() Following questionable or suspect links to sites that may themselves be of less than reputable nature. It is best to avoid following links to sites of a suspicious nature.
Following questionable or suspect links to sites that may themselves be of less than reputable nature. It is best to avoid following links to sites of a suspicious nature.
![]() Opening files that are from unknown or questionable sources. Users should be educated to avoid any content that is supplied to them from a source they do not recognize.
Opening files that are from unknown or questionable sources. Users should be educated to avoid any content that is supplied to them from a source they do not recognize.
![]() Apply necessary patches and fixes to prevent the exploitation of known vulnerabilities.
Apply necessary patches and fixes to prevent the exploitation of known vulnerabilities.
![]() Running with more privileges than are necessary such as when using the system while logged in as an administrator. Least privilege should always be exercised in these and other cases.
Running with more privileges than are necessary such as when using the system while logged in as an administrator. Least privilege should always be exercised in these and other cases.
Note
Regarding running with higher privileges than necessary, this is not just a problem with Java it is also more than possible to have the same problem with other active content. Running with higher privileges than absolutely necessary, such as when users run as an administrator, is very common in the computing world especially for home or small businesses where trained or knowledgeable IT staff may not be present. Users running with higher privileges impart the same unrestricted access and privileges to unscrupulous content as the user do to themselves. Exercising least privilege, or running a system with only the privileges necessary to do their required duties, is a principle in security that should always be exercised to avoid harm to a client system and mitigate client-side attacks.
Next, one of the biggest issues that cause Java to be a very attractive target is the platform and browser independence that is part of the fabric of Java. Java is designed to be a technology that can be written once and run anywhere (on any supporting system), which is in fact a big reason why the technology has become popular with the academic and open-source communities alike. Attackers wishing to make the biggest “splash” need only exploit the large amount of systems out there that support and use Java to provide rich content and applications. Of course making these exploits even more dangerous and disconcerting is the fact that vulnerabilities can be platform independent meaning that an exploit can move across operating systems and environments easily. Attacks that leverage the power of Java can easily move across platforms due to the same reason that Java itself is popular, platform independence and the ability for developers to write once and run anywhere. All things considered exploits are relatively simple to implement and are able to run with little or no limitations. Consider the fact that most modern browsers supports Java without through bundled plug-ins or technologies and you have an incredibly dangerous situation.
Did You Know?
Java exploits are easy to implement for developers or those who are knowledgeable regarding the language and do their homework. Considering the fact that most schools teach Java as part of their undergraduate computer science programs and such combined with the existing developer base and you have a large number of individuals that can make problems if they so choose.
Finally, it is definitely worth noting that due to the way Java executes; detection of security problems can be difficult by client-side security mechanisms to mitigate. In the Java model code is downloaded to a system and run on a Java Virtual Machine as we mentioned earlier in this section. This code (known as bytecode) is only partially compiled and is only further compiled by the system’s own JVM into machine specific code which is then executed on the system. When this code is compiled or parsed the actual process itself is something that cannot be observed by most, if not all, security software meaning that the possibility for malicious code to thwart security is higher. Further compounding the problem is the fact that malicious Java applets need not display any abnormal behavior which makes detection difficult, in fact tasks running within Java may run with higher privileges in the event they are digitally signed. On this last point, if an applet is signed it does not mean that it comes from a legitimate source so the danger is high, not to mention hard to detect.
Did You Know?
Java code can be fully compiled into machine specific code instead of leaving it as machine inspecific bytecode. If code is fully compiled into machine specific code it loses the ability to be easily ported to another system without being compiled for that system, but the need for a JVM is eliminated. In the case of bytecode, code can be written once and then compiled by the JVM into something specific for that system, but execution of the code may be slower due to the execution being run by a JVM.
In addition to these problems is something else that makes vulnerability and exploitation worse is vendor update processes. Specifically software vendors are known to create their own Java Runtime Environment (JRE) and update and maintain them on their own on a less than rigorous schedule. In these situations vulnerabilities in the JRE may exist for a substantially long time and lead to weaknesses being present for a long while. Still not enough of a concern? Consider the fact that users are less than diligent about updating their systems with the latest patches and service packs meaning vulnerabilities may never be eliminated even though a fix exists.
JavaScript
JavaScript is one of the oldest types of dynamic or active content and is by far the most widely supported and recognized. JavaScript is used on just about every web site you may visit to perform various tasks of all types. This scripting language is so widely used mainly due to its simplicity (relative to other technologies) and its incredibly wide support among browsers and platforms. Furthermore this scripting language is popular because of its ability to be easily integrated with other types of content and applications making it useful to developers and web designers alike. The success of JavaScript however is also the reason why attackers have targeted and leveraged the technology as a means to compromise systems and cause untold grief for clients. JavaScript has been used to perform attacks that involve redirects, downloading of content, or even revealing details about a victim’s system.
JavaScript is a dynamic scripting language that was originally developed by Netscape to support richer client interaction in web browsers. The technology was originally implemented publically in the beta version Netscape Navigator 2 in 1995 under the name LiveScript, but renamed later to JavaScript.
Did You Know?
When Sun and Netscape announced the name change from LiveScript to JavaScript some confusion resulted, namely from users thinking that JavaScript and Java were related. While the name does suggest a relationship between Java and JavaScript the link is tenuous at best, but it nonetheless has been used by some in the industry so suggest a link in order to draw more attention to JavaScript.
When JavaScript was announced it was quick to gain attention and widespread use as a client-side language and quickly cropped up on webpages en masse. The scripting language which originally started on the Netscape Navigator platform has had some growing pains, but has since been adopted by every major browser and is now essentially ubiquitous. JavaScript today is used on most about every web site in some capacity and more than likely will remain a staple on web pages for a long time coming.
Warning
Microsoft did develop a reasonably compatible dialect of the language and named it JScript. Microsoft’s JScript added some enhancement to the JavaScript language such as improved handling for date to address the non-Y2K compliant methods in JavaScript Today the scripting language is included in every version of Internet Explorer that has been released since Internet Explorer 3 up through the current version (which is at version 9 as of this writing).
Do not make the mistake that JavaScript and JScript are the same language as they are not, something which Microsoft also makes sure that developers understand.
JavaScript, as originally intended, is a rich dynamic scripting language designed to enable site owners and web designers to create more attractive and rich web pages. While one can make a case that JavaScript is similar to Java in the sense that some structures look the same, however the similarities end there. Java is downloaded and run in a JVM, but JavaScript is downloaded, interpreted and run by the browser itself directly. This ability to run JavaScript code is inherent in most browsers and therefore the ability to write code once and have it run anywhere is in the system by design.
JavaScript as a technology is one of the older types of dynamic content available to site designers, but there’s something else about this age that is not readily apparent. JavaScript is 15 years old at the time of this writing and its security model has not been updated substantially since it was released. At the time the JavaScript language was released there were two security issues that were seen as being the biggest threats namely malicious code and scripts gaining access to the local computer’s file systems. As we’ll see it has somewhat, but not entirely accomplished these goals.
First, one of the biggest concerns with JavaScript when it debuted was the idea that it could allow access to content on the local computer. The idea was that a script running in a web browser could easily take the next step and grant access to the local file system on behalf of an attacker letting them view and alter local stored content such as the “My Documents” folder. To address this concern the creators of JavaScript specifically designed the language with the idea that local system access was prohibited by the technology. In fact JavaScript cannot get files from the hard disk unless the user or someone on the client side browses to and selects the files specifically.
Warning
There are some researchers and security professionals that believe the dangers associated with getting access to information on a system are irrelevant due to the way people work nowadays. Essentially the reasoning behind this way of this thinking is that more and more individuals are storing information that they access regularly in places not on their local system, namely on the web itself. Consider the rising use of services such as Google Mail, Docs and Calendaring where users store ever increasing amounts of information. Also factor in that not only individuals but entire businesses are now relying on hosted services to store their important information, a trend that will only increase as vendors like Microsoft offer the ability to store Office documents on the web. As more individuals and business move their important documents and info to web based environments that they do not control nor own less is stored on local systems meaning that attackers may only seek to steal credentials off the local system and not actual data.
The second security issue with JavaScript? Attacks initiated by malicious websites via JavaScript which has become an all too common occurrence unfortunately. By using JavaScript it is more than possible for an attacker to steal information from a client system within the limitations placed upon the scripting language.
Did You Know?
Researchers have found that JavaScript is capable of carrying out actions on the client-side that most probably never thought possible such as mapping out local networks. Security professionals have discovered that using specialized commands and code it is possible to map out and locate all web enabled devices on a network and issue commands to those devices. How serious a problem is this? Well in the past it was thought that stealing information such as credentials and history was the biggest problems, but now it has been shown to be more than possible issue commands to web enabled devices which includes devices such as wireless routers, printers and similar equipment.
A third type of attack exists that is closely related to the malicious code attacks mentioned previously in this section, these are cross-domain attacks. Cross-domain attacks occur when scripts are run from a location different than the web page or content being accessed, just like some forms of XSS. An example would be a website where several embedded advertisements or other similar types of content exist. In this scenario the content is embedded in the page, but does not exist in the same domain as the web page itself meaning they are being called from another site. Such is the case in the following example:
<SCRIPT SRC=“http://oriyano.com/script.js”></SCRIPT>
<SCRIPT SRC=“http://zelda.com/java.js”></SCRIPT>
In this example a web page with the embedded tags would actually be obtaining script from a third-party website and running it in the client’s browser. The danger here becomes one of trust and accessibility. First, because the user is more than likely accessing a website they already know and trust they will not think twice about the danger of running scripts from a third party as, after all, it did come from a site they trusted. In fact in this example the user will more than likely not even be prompted as to there even being a security concern. Second, when multiple scripts are called by one page an executed together they have access to each other’s global functions, objects, and variables. The effect of such access is that scripts can interact in unknown and unexpected ways potentially revealing information about the client and their environment.
What can happen if scripts can access each other? Well take a look at the following list:
![]() Different scripts can access with each other’s variables.
Different scripts can access with each other’s variables.
![]() Different scripts can redefine each other’s functions.
Different scripts can redefine each other’s functions.
Note
This combination and use of scripts is far from being uncommon, in fact it is the exact opposite. Most sites such as those that offer up news, articles, videos, or anything similar combine scripts in this manner to deliver ads and other content from partner sites. For example, a common technology that uses scripting is known as Google Analytics, which is used to deliver advertising and such to a web page, is in use by over 40% of the websites currently online. Another similar technology is used by the advertising giant Doubleclick also can be used to embed scripts in a web page, this service is in use by over 70% of websites currently online.
Another danger with JavaScript is the fact that it is widely used and supported by other technologies to make them work properly. JavaScript is in fact used by other technologies such as Adobe Flash and others to make them work as designed. Accentuating this situation even further is the reality that JavaScript is used in other technologies such as the AJAX suite of web development technologies which themselves are gaining more traction in the marketplace.
Did You Know?
Some security professionals and researchers have advocated the disuse of JavaScript as they see the technology as essentially “broken.” Upon closer analysis it is possible to see just exactly where this line of reasoning comes from as these researchers note that the technology has not had its fundamental security model updated since its inception—meaning that the security model is 16 years old at the time of this writing. Obviously this security model cannot and did not take into account the increasingly ingenuity of today’s attackers nor the environment it was eventually going to be deployed into.
These same researchers advocate turning off the JavaScript capabilities in the web browser to effectively prevent attacks from becoming an issue. Of course, like anything in life there are downsides and this is no different as turning off JavaScript will make most websites unusable by clients (or at least unpleasant to use).
VBScript
VBScript or VBS is a programming language originally launched in 1996 by Microsoft as part of their Windows Script Technologies suite. This technology is specifically designed for the Microsoft platform and was originally designed to automate commands and as such replace the older batch languages that were in use by network administrators and developers up to that point.
While VBScript can be used to do simple batch processing and such on the client it can also be used as a web scripting and development tool like JavaScript. Using VBScript it is possible to access what is known as the Object Model in Internet Explorer and manipulate the application in ways not possible in other browsers or languages.
Web Application Obfuscation is one client-side method of attack that should be covered, especially when discussing scripting languages. Obfuscation of code has allowed hackers to take one attack and create hundreds-if not millions-of variants that can evade your security measures. Web Application Obfuscation takes a look at common Web infrastructure and security controls from an attacker’s perspective, allowing the reader to understand the shortcomings of their security systems. An attacker could bypass different types of security controls, as well, these same security controls can introduce new types of vulnerabilities.
Security tools such as IDS/IPS are often the only defense in protecting sensitive data and assets besides for being educated when it comes to mitigating attack.
Your best method of defense aside from trying to avoid attack is to secure your data, make sure its backed up and highly available. More of these protection methods will be covered in Chapter 10.
Note
VBScript is almost guaranteed to work on every current version of Internet Explorer, but not on other browsers. Other browsers such as FireFox, Opera, Chrome and others are more likely to support JavaScript than VBScript and as such it is chosen as the scripting language of choice for developers.
VBScript has been responsible for a number of security threats over the years, but some of the more well-known ones are discussed here in this section.
One of the most common issues with VBScript is its power to access different parts of the client system (usually if the client is Windows). Some well-known attacks include the accessing of objects such as address books in email, history in the browser, and other items. In fact worms such as Melissa were successful because the two main users of VBScript, Outlook and Internet Explorer were right in the crosshairs of the attack.
VBScript also is known to have a number of security holes that are periodically patched as the situation merits. The problem, as was seen with other technologies, is that users may and generally do fail to install the required patches and fixes to their systems and leave themselves vulnerable to attack. Even though VBScript has been folded into the .NET technology suite and doesn’t exist in the same form it used to enough older environments exist that are not being patched or maintained properly and they become targets.
HTML 5
This is the “new kid” on the block for websites and designs. HTML5 published as a Working Draft by the W3C, is designed to enhance and eventually replace what is currently known as HTML4 which first debuted in 1999. The new version is designed to introduce new features such as dynamic content, flexibility and security features. While HTML5 is not a standard yet, but rather a work in progress at this point, it is not widely used as of this writing however, is something you should be aware of due to its active content nature.
Note
HTML 5 is supported by a number of browsers currently on the market; in fact most of the browsers seen in Chapter 4 support HTML 5 in some capacity even though the support may not be as robust as it will be in the future.
Warning
There are also many other active content technologies, scripting languages and applets available to display in your browser and also cause your system harm if used maliciously. PHP (covered earlier in this book) is one such technology. Ajax is another. Be aware that there are many technologies available and security professionals should investigate as many as possible using the same methods of protection you would use for the ones mentioned in this book. Knowledge is power and the more you arm yourself with, the better your defenses will be.
Summary
In this chapter we examined the technologies and security threats associated with them. As we explored each technology we learned that a large number of vulnerabilities exist that make dynamic, active web pages, but at the same time each has security risks. Users have come to expect the rich and dynamic environment when using the web today and as security professionals we must become fully aware of any and all security risks to avoid problems wherever possible.
Technologies such as ActiveX, Flash, Silverlight, JavaScript, Java and VBScript all offer a tremendous amount of interactive capability and dynamic content to the web, but do so at a price. As with any technology, the ones in this chapter create risk, but also offer reward. In the wrong hands any of the tools mentioned in this chapter can be a powerful weapon that can be used against an organization.
