Chapter 2. Low tech vulnerabilities
Physical security
Information in this chapter
• A Mini Risk Assessment
• Outsider–Insider Threats
• Some Things to Consider for the Security of Your Buildings
• Bomb Threats in Chicago
• Check Those Phone Closets
• Remove a Few Door Signs
• Review Video Security Logs
• Consider Adding Motion-Sensing Lights
• Subterranean Vulnerabilities
• Clean out Your Elephant Burial Ground
• Spot Check Those Drop Ceilings
• Internal Auditors Are Your Friends
• BONUS: Home Security Tips
When it comes to security—whether pertaining to a large corporation or a small home network—physical security can be just as important as technical security. And similar to technical security, with physical security a short-term solution simply will not suffice. Risks, threats, and vulnerabilities abound today, and both their number and their impact have increased steadily over the past several years and will continue to increase, at least for the foreseeable future. That is why it is critical for organizations and homeowners alike to do everything in their power to institute countermeasures designed to improve their physical security posture, not just for today but for the long term. This chapter focuses on long-term approaches to attaining physical security. With an eye toward organizations, everything from building security, to phone lines, to video security logs, to motion-sensing lights is discussed. The chapter concludes with important security tips for homeowners.
Key Words: Biometrics, Countermeasure, Outsider–insider threat, Physical security, Risk, Tailgating, Threat, Vulnerability
Physical security has been a subject I have been very interested in ever since becoming a bonded locksmith in 1971. My full-time job was very technical and began to lead me into the world of computer security. It was the ability to experience both worlds at the same time that taught me how critical physical security is. It seemed to me, while working as a locksmith, that a lot of people really never gave the vulnerabilities of physical security much thought until there was some problem. I don't think things have changed much in the past 40 years, but it is encouraging to see people now begin to really look closely at the risks, threats, vulnerabilities, and countermeasures associated with physical security.
There was something else I noticed while staying closely associated with both the physical and technical worlds of security. While things are constantly changing in the technical security world, in the physical security world, things don't seem to change quite as quickly. As I said in Chapter 1, where we address social engineering, these first three chapters will closely relate in many ways. For the past 20 years, I have thoroughly enjoyed presenting on the subjects of physical security, computer security, and social engineering. More than 10,000 people have seen one or more of my presentations. The reason that I mentioned these presentations is that I get the opportunity to speak with people before, during, and after the sessions. It gives me an opportunity to see what they are doing about security and to hear about the things that concern them. In most cases, I can quickly tell whether or not someone has been a victim. Unfortunately, many of the people with whom I speak have been a victim of some form of physical or technical security threats.
While this is not a book about risk management, in many ways it really is. I heard a senior security director make a statement many years ago at a conference. He stated that their company had now come to the conclusion that all security issues really are risk management issues. Organizations (and homeowners) need to determine what they have at risk, what are the threats possibly targeting what they have at risk, how vulnerable are they to those threats, and what are the countermeasures (what can they do about the threats). Without some form of risk management, there really isn't any way to know what you have at risk or what you can do to help reduce the risk. Current threats are frequently in the news, and vulnerabilities to these threats are also frequently discussed. Understanding risk management is especially critical for small to midsize businesses that may not have a dedicated risk manager.
While I was working on my first book, Techno Security's Guide to Managing Risks for IT Managers, Auditors, and Investigators (ISBN: 978-1-59749-138-9, Syngress), I was spending a fair amount of time working from my boat out on the nearby lake. Even though this lake is technically a flowing river, it is still designated as a lake in name and on maps. As a part of a chapter in that book, I gave an example of a risk assessment by looking at my floating office on the boat. Realizing that most of you who will read this book probably did not read that one, I think it's worthwhile to share that risk assessment again.
A mini risk assessment
I had recently purchased my first boat. It wasn't huge, but it was just big enough for me to use as a floating office a couple of days a week when the weather is nice. Just for fun, I conducted a mini risk assessment of some of the risks, threats, vulnerabilities, and countermeasures associated with my floating office. The risk assessment wasn't intended to be extensive, but it will give you a simple example of the things to consider when conducting any risk assessment.
What did I have at risk?
The first and most important thing at risk while working on a floating office is my life. I also had the boat itself at risk even though I had passed some of the financial risk along to an insurance company, which is what we do with a lot of risks where it makes sense. There was also equipment on the boat that was at risk of not only sinking but of possibly being dropped overboard or being splashed with water from the wake from a passing boat. A sudden thunderstorm could cause problems as well. Depending on lake conditions, too many other boats could cause a problem. The battery in the boat could die, causing me to lose all power and even strand me on the lake. As you can see, whenever you consider what you have a risk, you will immediately start to consider some of the threats that could increase your risks. What I had at risk out there on the boat was everything that I could lose if something really bad happened. Let's call all the bad things that could happen possible threats.
Risk management, and especially security risk management, needs to be much more than a listing of best practices for managing risks. Throughout my years of security training and penetration testing, I always ensured that the client corporation's risk managers were a part of our evaluation process. The best book on this subject that I have seen to date is a book published in 2011 titled Security Risk Management: Building an Information Security Risk Management Program from the Ground Up by Evan Wheeler (ISBN: 978-1-59749-615-5, Syngress).
What were some possible threats while out on the lake?
I've already mentioned a few as I discussed some of the risks. The possible threats were a little different than they would be if I did a risk assessment of my home office. Weather could certainly be a threat, and so could simply hitting something as I was moving from one place to another on the lake. There was always the threat of a sudden thunderstorm as well as the threat of being hit by another boat. I wouldn't have had much of a threat of being hit by a car (hopefully) or suffering from a commercial power outage while I was out there. The possible threat of theft was small as long as I kept an eye on my equipment while I was launching the boat. Overall, the threats that could hinder my ability to conduct business from the boat would be lower than those from most places.
What were some of the possible vulnerabilities?
I would have been much more vulnerable to severe or any weather changes out there on the lake than I would be in my home office. This is a large lake about 20 miles long. For a few days following a heavy rain, there are hundreds of semi-submerged items floating downstream (remember, this lake was actually a river). If I didn't know the depth of the water that I was in, I would have been vulnerable to running aground or hitting something in water that was shallower than I thought it was. It would most likely just be inconvenient, but just like in any vehicle, I would be vulnerable to running out of fuel. I mentioned not being vulnerable to commercial power failures, but I could easily have been vulnerable to quickly running my only battery down to a point where I couldn't start the engine to get back to the marina. Although I am very careful, I would certainly have been vulnerable to falling overboard. That could be a difficult problem when you're on the water alone.
And finally, what about my countermeasures?
I really enjoy talking about countermeasures. The word even sounds cool. I had a lot of valuable equipment with me that would be at risk while I was out there on the boat. The countermeasures are the things that help me lower my vulnerability to any of the threats that I might encounter that could cause me to lose what I have.
I've learned a lot during the couple of years that I had my floating mini-office. Some of the countermeasures that made me feel comfortable out there were as follows:
• I tried to be on the lake only when I know that most other boaters weren't out there.
• I checked the weather forecast every time before I headed to the lake.
• I always wore a self-inflating life jacket in case I fell overboard.
• I used special waterproof cases for my computer and cell phone.
• A small inverter was onboard to provide me with 110 volts AC from the boat battery.
• The marina and my family were always notified of where I planned to be and when I expected to return.
• A small marina radio was always on board.
• The boat was constantly maintained.
• My weather radio warned me of any pending storms.
I'm sure there are many more issues that could be addressed in this mini-assessment. We all need to at least be familiar with and understand our risks at home and at work.
Just about every area of concern with security today is a risk management issue. This chapter, and most of the other chapters in this book, are chock full of what I like to call techno tidbits of useful risk management countermeasures. Many of them will be topics you might not have considered in the past as you put together your security plan. I hope this will help external, internal, and information system auditors to recognize several gaps in their audit processes.
Outsider–insider threats
For my definition here, let's consider the outside threats as those coming at you from the Internet or dial-up modem (you do know where all of your dial-up modems are, don't you?) or a simple phone call from a total stranger. The reason that I mentioned dial-up modems is that there are still a lot of them out there. Many maintenance ports on older PBXs, building environmental controls, air handling systems, and access control systems still use modems for maintenance access from off-site, and probably will continue to rely on them well into the future.
I'm not considering insider (current employee) activity in this chapter. For this discussion, let's consider outsider–insider threats as people who never were employees and didn't belong in your building.
This would be the category that my inside penetration team would fit into. When we roamed through the clients' buildings unchallenged, our team definitely didn't belong there (other than being hired to try to get there). A bad guy checking out your building for espionage or future terrorist activities would also fit in this category. In theory, some employee inside the building should eventually figure out that there is a Trojan Horse in the camp. Here's why I keep preaching about the subject of physical security and the subject of knowing who is in your buildings at all times. For more than three decades now, I have observed what I believe is a lack of awareness of this concern. Over the years, I have seen comparatively few articles that address this silent but formidable threat. Remember, when I spent those years doing this for a living, our penetration teams entered the clients' buildings expecting to get caught in an inside penetration attack that was designed to become more bold the longer I had the team in a building. Toward the end of just about every inside pen test, we were openly walking around like we worked in the target building, almost hoping to get caught by someone. We never did!
We were good, but I suspect that there are many bad guys out there who are much better at it than we were, and they won't try to get caught in the end like we did. We were also working under a few self-imposed rules that the real bad guys could care less about. Using forced entry, like a crowbar to get through doors or windows, was a no-no for us. Our main tools were a cool head and our social engineering skills whenever it made sense to use them.
Some things to consider for the security of your buildings
Having worked for decades in the worlds of both physical and technical security, I find frequently that the people who manage these groups don't communicate with each other as well as they should. What we have at risk in the information security world can be considerably different from the things that we have at risk with pure physical security. What I mean by that is that certain locations should be looked at more closely when the risks of compromised or stolen intellectual property need to be more strongly protected against. It's always a good idea for the management team responsible for computer and information security to work closely with the management team responsible for overall building security. Following are a few of the areas where special emphasis is recommended.
Check all locks for proper operation
On every one of my team's penetration tests, we found at least one lock (either interior or exterior) in the building that wasn't functioning properly. This provided us with easy access to buildings and rooms that we shouldn't have been able to get into so easily. If employees are trained for just a few minutes on how to check to see if the locks on the doors that they use every day are working properly, this vulnerability can be all but eliminated. Building maintenance teams should also take a close look at all locks at least twice each year. Slightly misaligned strikes on the doorframes are the most common problem that we find. This is a serious problem, in that it defeats the purpose of the dead bolt feature of the lock. It takes me less than a second with my trusty fingernail file to see if a particular lock (bolt) has this problem. If it does, I'll know (and have the door opened) in a few seconds.
Use employee badges
I know these can be faked, but I still think that it is much better to have some form of visible identification worn by every employee at all times. Most of the companies that hired us did not have a policy requiring employees to wear their corporate ID badges all of the time. This made our social engineering attempts much easier. Once we were inside the buildings, it was as if everyone just took it for granted that we belonged there. Not only were we inside their buildings, but were also inside their firewalls and intrusion detection systems.
Employees can be somewhat trained to even detect fake ID badges. I was working for a large company that did require employees to always wear their ID badges when they were on company property. This was back in the days when color printers were just starting to show up in homes and offices. I created a fake ID that was intentionally made without any thought of quality control. The first time I wore it into the building instead of my real ID, I suspected that I would be stopped immediately and questioned about it. This was a security project, so I was prepared to explain myself. To my amazement, I never had to explain anything because it was never questioned. For the next three months, I wore it everywhere and not one person noticed it. During one of our security meetings, I told everyone in our group about my little experiment and most people were quite surprised that it was never detected.
Part two of my experiment had the most interesting results. I created a picture showing my two personal employee badges side by side. The fake one was quite obvious when seen next to the real one. We began to teach people how to take a slightly closer look at the badges that people were wearing as they walked through our buildings. From that time forward, I only wore my fake ID when I was conducting security awareness training for a group of employees. I was amazed at the number of my friends who had been through a version of the training and would spot the fake ID as I was walking past them on the way to another training class. Some would spot it from 10 feet away. These are the same people who didn't even notice it when they sat in my office just 3 feet away prior to being made aware of the threat. AWARENESS TRAINING WORKS!
Shredder technology keeps changing as well
As with everything else, these past few high tech years, shredder technology has changed considerably. Our team had gotten really good at putting strip-cut papers back together again years ago. We used to take bags of strip-cut documents that we found at the clients site back to our office during the test. Frequently, the bags of shredded documents were sitting outside in or near a dumpster where we simply picked them up and put them in our vehicle. Most of the time, documents that were strip-cut shredded all fell neatly into place in the bag or box where they were stored waiting to be disposed of. Our team was able to reassemble many of these documents within a few minutes. We would even take a document and paste the strips on a piece of cardboard in the shape of a Christmas tree, spreading the strips out as they were glued to the cardboard. Even with up to an inch between strips, the documents were easily readable once reassembled. We never even attempted to reconstruct a document that had been sent through a cross-cut shredder.
Today's small cross-cut shredders are very inexpensive and durable if you keep them oiled with the special oil available for shredders. I have a small one at home that cost only $39 and it creates a very small particle that would be next to impossible to reassemble. I have tried to wear it out for about 6 months and it just keeps on working. I'd also recommend encouraging all employees to get one for home use. I believe that it is a good policy to shred everything that comes to your home with any family member's name on it. Once you start doing this, it will become second nature and you will never need to wonder who might see your personal information once it leaves your home. Identity theft is on the rise.
Outdated but still sensitive documents should also be disposed of securely. When I worked at the Pentagon for the final 7 years of my military career, we were required to place certain sensitive (not classified, simply sensitive) documents into a safe containing a burn bag. To this day, I still use a burn bag at home for documents that I need to destroy that are too bulky for my shredder. It's a great way to clean out the barbeque grill on a cold sunny day. I feel good every time that I destroy sensitive personal documents rather than simply throwing them in a trashcan.
Keep an eye on corporate or agency phone books
When conducting a physical penetration test, the company's phone books were the first things that we went for. Once we got our hands on a corporate directory, the social engineering began. Most corporate phone books are laid out in a way that conveniently shows the entire corporate structure as well as chain of command, building addresses, and department titles. That kind of information also let us know the order in which to try entering the various buildings if there were several. Wherever the human resources department was located was usually where we went last. Here's why. As we tried to enter all of the other buildings by simply walking in the door like we belonged there, we were frequently challenged by a receptionist and asked where we were going. Our social engineering answer was always the same: “We were told that this is where human resources is located and we're here to fill out a job application.” In every case, the receptionist simply sent us in the right direction. We thanked her or him and walked out the door and directly into the building next door to try the same con. The phone book even gave us the human resources manager's name to drop if we needed to be a little more convincing that we belonged there but were simply lost. It also gave us the rest of the important people in the organization whose names and titles we could drop if we needed to when challenged. In addition to the names in the directories, most contained the physical location and chain-of-command ranking for the most important person in each department. It was often their offices, file cabinets, and trashcans that we spent the most time in during our nightly visits.
Employee awareness of the importance of a corporate directory will help ensure employees know how to safeguard this valuable corporate property. Old directories are still quite accurate, especially regarding buildings and department locations. They should be burned or shredded rather than simply thrown into the dumpster (we might even get hit if you throw them in while we're in there looking for goodies).
If paper directories can be eliminated altogether that would make our job a little tougher. Everything that you do to make it a little harder for the bad guys will make you a less likely target—they're looking for an easy mark. Online directories are better only if you don't let the social engineers get into your building. Once we were inside, we began looking for a monitor with the infamous sticky pad note on the side with the person's login id and password written on it. Once we logged onto the network as them, we could usually get to an online company directory if there was one.
Let me address one additional countermeasure while I'm on the subject of the login ID and password being written down and attached to the monitor or under your keyboard. Maybe that doesn't happen where you work, but we found at least one person who had done this on every job that we were hired to do. There is another reason we like to use someone else's login ID and password to get onto their networks. If we are able to do that, not only are we on their network on the inside of any firewall, but everything that we do will show up in some log as being done by the person who let us log in as them. Many larger companies now use at least some form of two-part authentication using either biometrics or a handheld authenticating device of some type to attain two-part authentication. Fortunately, some forms of biometric access control are getting to be very reasonable in price. Everything you do in the way of authentication will greatly reduce your vulnerability in this form of instant identity theft.
Unsecured areas are targets for tailgating
This was one of our most successful entry techniques regardless of the security procedures at the building. For some reason, people in the outside smoking areas didn't ever question our being there, and we were able to eventually walk in right behind them as they went back to work. We found that many corporations had good security at their main entrance points but were lacking at other entry and exit points. Members of our pen testing team were able to gain access on several occasions through parking deck or garage entry points that required card access. We would simply follow someone who was headed to the door and walk in behind him or her as we were pretending to search for our access cards that didn't exist.
Tailgating, frequently called piggybacking, is simply following someone into a building after they open the door with an access card or by entering a door code. The bad guy will often pretend to be searching for his or her access card while waiting for someone to enter with a legitimate card. If there is no guard at the entrance, the bad guy will probably go unchallenged and unnoticed. You really need to think about this one before you decide how you want to solve it. You can't place the legitimate employee in the position of having to challenge the bad guy to ask for identification.
The legitimate employee probably didn't come to work for you to be a security guard. On the other hand, you don't want bad guys just walking into your building. This problem is as old as dirt, but the solutions just keep getting more complex and expensive. Some companies employ cameras that photograph everyone who enters the building. Others are now employing biometrics scanners and other high tech devices. As with everything else in the security field, you need to get a system that is appropriate in cost for what you are trying to protect.
At a minimum, you can make your employees aware of this threat and have them notify their immediate superior that someone followed them in and note the time and date of the incident. This same employee awareness session should instruct all employees to display an ID so that fellow employees, who may not know them, don't think that they are tailgating as they walk in behind them.
I have found it very interesting to learn things about people, in general, from the very people I have trained over the past three decades. I think about this often as I write about, or present on, topics relating to security. One very encouraging aspect I notice is that employees really do want to do whatever they can to help with overall security. It's amazing to watch their awareness level rise as I describe certain scenarios. There is something else that I have been saying for decades: “By far, the least expensive and most effective countermeasure for the overall security of any organization is the employees of that organization.” If the employees of an organization are trained and taught to be aware of anyone not wearing proper identification where identification badges are used, the corporate security posture can be greatly increased.
The countermeasures for this vulnerability really aren't as simple as we might think. Most employees who work at and are entering a building aren't security people. They are simply trying to get back to work. Even though someone trying to enter a building using the tailgating or piggybacking method should be challenged, challenging them is an uncomfortable situation for most people. Unless there is a strong corporate policy requiring all employees to challenge anyone they can't identify, this is a difficult problem to deal with. As an absolute minimum, employees should be trained on when and how to notify security if they suspect an unauthorized person has followed them in.
Special training for off-shift staff
I can't emphasize enough the need to train all of your second and third shift employees, and especially your janitorial services people, about the threats of social engineering. Obviously, pre-employment screening and possibly bonding are essential for any outside firm that you allow inside your buildings at any time. This is especially true for building access outside the normal 8 to 5 Monday through Friday standard work schedule. Frequently, these people have access to the master keys for a large section of the building and sometimes the entire building. They need awareness training to better prevent them from becoming victims of bad-guy social engineers who would like to borrow their keys for a minute or who get them to open a certain room.
This team should also immediately know whom to contact should they see anything suspicious that should be reported. If there is no immediate supervisor on duty during the evening or night shifts, everyone on that shift should know how to quickly contact the security forces. It can be very dangerous for them to approach a stranger themselves in an attempt to get them to leave.
This suggestion may not seem to fit in the context of this book, but let me mention it anyway. There is another very good reason to train your janitorial team (at least the team supervisors) to be extra watchful during the evening and night shift work hours. I have been teaching bomb recognition classes for the past 20 years. These same social engineering skills and physical building penetration methods could apply in any situation where the collective bad guys are trying to get into your building. The eyes and ears of the people who work in your building every day are critical when it comes to detecting anything or anyone unusual in the vicinity of the building. Bomb recognition training for key individuals and having an effective bomb incident plan are countermeasures that can be employed with considerable effect.
Bomb threats in Chicago
This is a good time for a little side story that will let you see how the many risks, threats, vulnerabilities, and countermeasures overlap in the worlds of physical and technical security.
Several years ago, I received a call from a friend from the Chicago area asking for some help. He said his company has office locations in several cities throughout the country and one office out of the country. A series of bomb threats called into their corporate headquarters were causing them to lose a little sleep. They just wanted our team's suggestions for what they should do about it. This meant a trip to Chicago for us in February. (For the warm-blooded person from the sunny south that I am, that was a bit like a trip to Greenland in mid-winter.) We went anyway.
Prior to going, I decided to look on the Internet to see if I could find anything out about this company. This could also provide a hint as to why someone would call in these bomb threats that fortunately were only threats, so far!
The company flew in their senior managers from around the country and we suggested that their corporate attorneys and risk managers attend the training as well. They were going to learn everything they wanted to know but were afraid to ask about bombs and bomb threats.
We arrived a day early, and we asked if they would like for us to take a look around their corporate headquarters building to see if we saw any glaring physical vulnerabilities that could allow someone to easily place a bomb in or close to the outside of their building. The outside perimeter was about as close to perfect as I had ever seen in a building of that size. As we were looking at the various locations from the inside, my eyes kept being drawn to their newly installed access control system. Each employee had been issued an ID card that would allow him or her to enter certain doors at specific times of the day. The system also kept track of the times that they entered and left the building.
My fellow team member gave me a strange “you've done it now” kind of look when I said that a simple metal coat hanger might be able to compromise the entire system. I was about to be put to the test as we approached the next set of outside access doors in that part of the building. The person who had hired us was standing there with a metal coat hanger and he handed it to me.
Keep in mind that we were walking around inside the nicely heated building without our coats. I was asked to go outside and attempt to open the doors with the coat hanger. On the other side of those doors it was still Greenland in February. I politely said I would go outside (without my coat) and try for a few minutes. All that I asked is if I started to turn blue, please “open the door from the inside and let me back in.”
That was never necessary. I was back inside in less than 30 seconds and everyone was standing there with a deer in the headlights look as I calmly walked through the quarter-of-a-million-dollar security system with no indication that I had ever been there. This was not the first time I had seen this issue with an improperly adjusted access control system. The system detected motion from the inside that automatically unlocked the door when someone was moving toward the door. I noticed that it detected us walking past the door from a considerable distance away. It was just too sensitive. I also noticed that the locking mechanism opened only one of a pair of double doors and that the motion sensor was mounted dead center between the double doors. The only thing protecting the opening between the double doors was a thin piece of weather-stripping. While I was standing outside briefly freezing to death, it was a simple matter of taking my thin metal coat hanger and sliding it between the two doors while rapidly moving it up and down. Within seconds, I heard the familiar click that I was hoping to hear. The security system thought I was inside because that's where it saw the motion of my coat hanger.
All of the senior managers, attorneys, risk managers and security team members were in a training room the following morning for their day of bomb threat training. I opened the meeting by letting them know that this was most likely a low probability threat but that they were smart to decide ahead of time to learn as much as they could about what they should do about these threats. We were going to spend the rest of the day learning about bombs, bomb threats, bombs in buildings, bombs outside of buildings, and all kinds of other scary things. It was going to be a fun day.
As I was finishing up my introduction, I walked around the room and placed a small packet of one to three pages in front of four of their most important people. As the four targeted people started to look through the papers placed in front of them, I simply stated that this is your high probability threat and something you need to address immediately in our opinion. The papers contained just about everything we would ever need to know about these people. Where they lived, how they most likely traveled to work, in some cases, where they went to college, where their children went to school, and much more. All of it was gained from a few social engineering phone calls and about an hour searching the Internet for information about them. Much of the information about these people (and possibly about you) was out on the Internet. It's not easy, but these people-finding search engines all have an opt-out option to have your name and contact information removed from their databases. Just type the words “people search engines” into www.google.com for the most recent list of these services. You should put your name in some of them to see what information is out there about you. You will most likely be surprised at how many places your name pops up.
Check those phone closets
If your building is in rented space, or in a multi-tenant building, it's a good idea to have someone perform a thorough check of your hard wiring for the phone lines. You don't know who was in there before you were, and old wiring is sometimes not removed when new tenants move in. On more than one occasion, our teams found old phone cable wiring still in place and being used in an inappropriate manner by inside employees. While we are on the subject, the need for physical security also comes into play when considering the corporate PBX (Private Branch Exchange), which is the internal phone company for larger corporations. The PBX may still have a modem for remote maintenance needs, and the phone number for that modem may be written on the wall right near the modem. Our pen testing teams frequently found access to many of the rooms where PBXs were located by using our social engineering skills to get someone to open the door for us.
Remove a few door signs
It always amazed us to see rooms that had a sign over them saying Computer Room or Phone Closet. Obviously, the people who work there know where it is, and there is no reason for anyone else to know what's in there. It's all right for the room to have a number on the door that building maintenance would understand, but there is little reason to make it so easy for the bad guys to find their best target. This may sound like I am getting a little too picky, but I'm not. The more difficult you make it for people who don't have a need to know about these critical rooms, the more secure you will be.
Review video security logs
Normally, after we have completed our mission and have taken all of the evidence that we have been there out to our vehicle, we would re-enter the building and try to be seen by the building security cameras that we knew were there. Hopefully, there were some we didn't know about. We would even jump up and down waving our arms just to see if anyone would eventually report us. As far as we know, we were never reported as being seen on the tapes recorded by those cameras. One of three things must have happened: the cameras weren't working (unlikely), the people looking at the playback of the video missed seeing us on the tape (probably unlikely), or they were never looked at (most likely). I'd recommend that someone in the company periodically test this process. If there were internal auditors in the company, this would be a good audit step. That entire expensive surveillance system is worthless if whatever is captured on tape isn't ever seen by a human who can do something about it.
This is another area where I believe that the people responsible for the techno security of the systems need to talk to the people responsible for physical security. Cameras and lights have always been countermeasures I like to see in and around buildings and personal homes. They can scream “go find an easier target” to the bad guys of the world. There may be areas where additional cameras could be recommended to help improve the security of critical areas or rooms. The team responsible for overall physical security might not know about these areas unless you tell them. They may already be monitoring areas that you aren't aware of, which could help you if you have an incident.
The reason I mentioned personal homes several times throughout this chapter is that your home can be another area of vulnerability for physical penetrations or social engineering attempts to gain specific information. Many people now do much of their work from home on workstations connected to the Internet at high speed. I employ as much physical security at my home office as I have at every other office where I have worked. The technology associated with home security products has increased significantly while the prices for that security have dropped along with the cost of the latest computers.
I recently installed a number of digitally controlled security cameras around the perimeter of my home as well as motion-activated security lights in all approach areas. This may sound a little paranoid, but I know I am much more protected than most of my neighbors and my family feels very safe knowing it would be difficult to attempt anything around our home without someone knowing about it. The security cameras are also motion activated, so the only thing I see is recorded activity when there is movement detected by the camera monitoring software. With the rapid advances in technology, these kinds of sophisticated security systems are very affordable and powerful.
Consider adding motion-sensing lights
Most of our social engineering-based inside penetration tests would have been much less successful if the companies that hired us had motion-sensing light controls installed in every office throughout their buildings. These are not the same kinds of light controls that I installed around my home. Those would help on the outside of any building. What I am talking about here are the motion sensors that turn on the lights inside an office or room when someone walks in. These same sensors turn the lights off after a preset time once the final person leaves the room.
Every penetration test we were hired to conduct had several buildings of opportunity for us to attempt to enter, and every one of them had at least a few lights on all night long. While we were conducting our initial surveillance of the buildings, that was one of the first things that we noted. Are there lights left on at night, and if so, are they the same lights every night? In most cases with a building having about 15 floors there would be six or eight lights left on. Our assumption was that whoever was assigned to that office was either still there or forgot to turn the light off when they left. Either way, it created a good situation for us. If a random number of lights were left on each night, the security forces would not have any easy way to decide if everything was normal at any given time.
As they patrolled from the outside (we were watching them do this from the outside and from the inside once we got into the building), they really had no reference for what would be a normal building profile. As we became bolder toward the end of a penetration test, we would even turn certain lights on just to see if security would become suspicious of this activity. No one ever did.
Several of the buildings we penetrated didn't have anyone working in them at night. If motion-sensing lights had been used throughout these buildings, we would have looked for softer targets. If we had entered a room in a completely dark building, the light coming on would have been very abnormal for any security team member who saw it.
There is another good reason to install these sensors. Over time, the energy saved by having the lights automatically turn off when there was no human around needing light could eventually pay for the additional cost of the sensor.
Subterranean vulnerabilities
This is certainly not a new topic, but it is one that I suspect that most people don't ever think about. Those of us who work in major cities, and even in small cities, walk over manholes every day. That's certainly nothing to be concerned about, but do we ever consider what's under those small circles of metal? While most companies don't own the manhole covers (and what's under them) surrounding their building, it's still a good idea to check on their security. The extent of the infrastructure that exists below the streets of most cities is incredible. Figure 2.1 a boring picture of a boring manhole on a boring street. Pretty neat huh?
If you enter the words “manhole security” in Google, you will find a few interesting articles about how manholes can be protected as well as a few stories that discuss the problem with manhole cover theft in some cities.
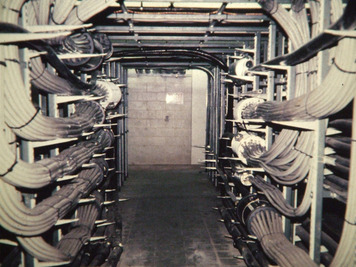
One of my fondest memories of a manhole in the movies was seeing Mother (Dan Aykroyd) working away in a nearby manhole at the beginning of the movie Sneakers in 1992. His penetration team was hired to test the security of a bank. The story was pure fiction, but the vulnerability of what could be accessed from within certain manholes was real. Here's a manhole cable vault that Mother would have been proud to work in. The picture in Figure 2.2 was taken on the other side of a typical manhole cover that you would see as you walked over it.
Most manholes like this have long since been secured, especially since 9/11. That doesn't mean that you shouldn't become aware of any manhole that could be used to access your building. This is even truer for multi-tenant (that's most of them) buildings in large cities.
Clean out your elephant burial ground
What happens when that computer (and elephant in this analogy) that you purchased a few years ago finally dies or becomes too old to do any work for you? I'll bet that it gets moved to your elephant burial ground with the rest of the electronic equipment that still looks new and valuable but isn't fast enough to keep up anymore. You can't simply put it out for the trash collectors to pick up, so there it sits, sometimes for years.
This burial ground was a prime target for our penetration teams as we conducted our vulnerability tests from inside our clients' buildings. We frequently used our social engineering skills to find out where the old computers were stored. If it was in a locked room, we would find a way to either get someone to open the door for us, or we would use our lock picks or pick gun to open the door.
Old disk drives will be an area of concern for years to come. Terabyte drives are now readily available (and cheap) at stores like Office Depot for anyone to purchase. Less than 15 years ago, I was thrilled to be able to purchase a 200-megabyte disk drive for $200. I was the first person that I'm aware of in my circle of friends to own a drive of this size for a mere $1 per megabyte. Now I'm seeing 500-gigabyte disk drives on sale for around $50 after rebates. This growth in technology is now happening so fast that most of us just take it for granted. The bad guys don't!
The tip here is to be careful with those old disk drives. This applies to the computers at home as well as at the office. There is much valuable data on them, and the risk is climbing as the storage capacity of every drive climbs rapidly each year. Be certain to remove all disk drives from computers that you plan to donate, give away, or simply throw away. I smash mine up with a hammer before disposing of the drives at my local electronic recycling center.
Old habits die hard, and this one will probably be no exception. As a country, we have been throwing away just about everything since the end of World War II. During the war, security was on everybody's mind, and each person encouraged friends and neighbors to be careful what they said and what they threw away. (I wasn't around during World War II, but I was the product of a happy homecoming after the war.) As individuals and companies, we need to bring back just a little bit of that way of thinking. We need to become aware of this problem and encourage each other to be more careful with assets by being more careful with our trash.
Many of the topics presented for thought in this chapter and throughout the entire book are just as appropriate in our homes as they are in our offices. This is especially true of our home office computers, networks, and trash!
Most of us are inundated with snail mail at home as well as at work. I have a policy in our home that nothing leaves in our trash can that clearly has any family member's name on it. This requires a little extra effort to destroy a single page of a credit card offer each time I receive one. If it has a name and address on it (obviously everything that arrives at my home does), I destroy that part of the document. Every small thing that I can do to protect my family from things like identity theft or credit card fraud helps me to sleep better each night.
Spot check those drop ceilings
On several occasions, we used our social engineering skills to get into buildings and then install a sniffer in the telecommunications hub for that floor. I recommend that all companies have their building maintenance teams perform a spot check above all suspended ceilings at least twice each year. We have been amazed at some of the things that we found up there while we were conducting the penetration test. You may even stumble into a security vulnerability you weren't even aware of.
There is one thing we learned about telecommunications and wiring throughout buildings. Wires just never seem to go away! This was especially true in multi-tenant buildings. In many cases, the office space was in use by another company or organization that had different needs from the current company occupying the same space. There was only one occasion where I can remember finding something in the drop ceiling that we believed was placed there for covert reasons. On another occasion, we found undocumented phone line extensions that were apparently used by a former tenant. They were not disconnected, and one of those lines was connected to a phone in a secure conference room. The people who had hired us to conduct this test were very surprised to learn that. It was our opinion at the conclusion of our penetration test that these extension lines were not added maliciously. They were simply left over from when the office was used by the prior tenant. I also suspect that our team was the first to have looked into the space above the drop ceiling in that building. There is simply no way to know what is up there unless someone looks!
This suggestion of checking out the space above the ceiling tiles would also be a suggestion I would make if considering places to hide things like bombs. We walk under drop ceilings day after day and normally have no reason to think about what might be up there. Usually, there is a least a foot of clearance between the grid work holding the drop ceiling in place and the ceiling itself. I have seen as much as 3 feet of clearance. You may be amazed at what you find hidden up there (hopefully it's not ticking).
Internal auditors are your friends
I have a lot of personal friends who were internal auditors for a variety of different sized companies. I suspect most of them would be very happy to hear me say that they are friends of the people who work in their respective companies. For most people, it isn't any fun being audited.
Just about everything I have mentioned in this chapter would make a good spot check audit point for an internal auditor. Someone on the good-guy side of the fence needs to check for these possible vulnerabilities and insure that the proper countermeasures are employed before they are exploited and become security incidents.
My experience with auditors over the years has been that things usually happen once they have made a suggestion for improving in a certain area of concern. Many of the larger corporations have information system auditors who have a primary responsibility for looking after the technical world within a corporation. That's a lot to keep up with. Most mid-sized corporations have internal auditors who have the information system responsibility in addition to the audit responsibility for everything else that needs to be audited. I believe that much of what I talk about in the following chapter regarding locks should also be something that is audited from time to time. This is especially true knowing that much of what I discuss in Chapter 3 has been well known to the good guys as well as the bad guys for years now (thanks to YouTube and security-related websites).
Bonus: home security tips
I probably spend more time considering home security than any other topic. Maybe it's because I now spend most of my time there. I also like the feeling of having a well-defended home for my family any time that I'm away. I watch the local news and keep up with the current threats in the vicinity of our city. If there ever was a place that needed security in depth, it's your home. Your job as the owner of a home or the head of your family is to make your home a tougher target than the rest of the homes in your neighborhood. You certainly don't want anything to happen to any of your neighbors, but if the bad guys are cruising the neighborhood looking for a place to hit, you want that place to be any place but yours.
In preparation for writing this chapter I looked up a number of different web links but I decided not to use those. By the time any book goes to print, things change on the Internet. What I had decided to do is to give you a list of topics to enter in the search field for http://www.YouTube.com. For several years now, I have been making a statement while speaking at security meetings that “if it's on YouTube, you had better know about it”. I can't think of a single thing that I have tried to find more information about where I haven't found that information with a quick YouTube search. It's absolutely amazing! So many of the things in the physical security world, and especially the things that deal with locks and bypass methods, used to be known only to a select number of people. Now they have become common knowledge for everyone in the world.
I have used several of the digital security cameras sold at stores like Sam's and Costco, and for the money they are excellent. The quality of the cameras that are available in a system costing about $1500 is pretty amazing. I spent another $1500 having someone wire mine, and I'm very happy I did. It's very comforting to know that when my driveway motion sensor activates with a mild beep, I can go to my security camera logs and see what caused the driveway alarm to activate. The current systems that come with the standalone computer and a good size hard drive can record for about 4 weeks before overwriting the logs. Even though my cameras have infrared sensors for nighttime use, the motion-sensing lights around our home are what really bring the camera's lens to life. Light is paint for video and still photography. The more light, the better. Most systems even have the ability to produce a file with any given camera in the system and create a runtime version of the viewer that could be given to police if necessary.
The combined system with motion-sensing cameras, motion-sensing driveway devices, and motion-sensing lights provide a peace of mind for my family that I really can't put a value on.
Summary
—Low Tech Jack
I've thrown a lot at you in this combination of risks, threats, vulnerabilities, and countermeasures associated with improving your physical security posture. What I have tried to address in this chapter is what I consider the low-hanging fruit that the bad guys of the world are very aware of. Most of the vulnerabilities mentioned are fairly easy to fix once you know about them. Many of you who read this book won't even be responsible for correcting your corporate vulnerabilities, but you might be able to get this book to someone in your organization who can correct them.
Security will always be a long-term team effort. This is true for every size company as well as every size family at home. If you have a computer in your home and you access the Internet to pay your bills or check your bank statement, you need to consider security every time you do. Even though we are in a very technical world that will do nothing but get technically more complex, we can't ever forget about physical security at home and at work. If you become a victim of identity theft, you will spend about 2 years getting your financial life back in order. Prevention is your absolute best countermeasure for most, if not all, of these possible threats.
Stay safe out there!
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.