Chapter 6. Low tech hacking for the penetration tester
Information in this chapter
• The Human Condition
• Technology Matters
• Staging the Effort
• Getting Things in Order
• A Useful Case Study
The chapters thus far have focused on physical security, social engineering, and surveillance, topics that are important to those who are working from the perspective of someone who is physically present at the location in question. This chapter takes a different approach and focuses on low-tech hacks for penetration testers, combining social engineering concepts with easy-to-use technology to create valid and effective attack techniques. To most penetration testers the end user is the weakest link in any information security chain; to organizations, this means their employees are vulnerable to compromise by creative and enterprising attackers. This chapter explains what aspects of human nature make employees vulnerable, and how a penetration tester can break the security chain by using these vulnerabilities against them. After covering these basics, the chapter walks through a case study that explains the techniques that have worked in the past, and why those techniques worked so well.
Key Words: Metasploit, Penetration test, Selective attention, USB thumb drive, Wrapper
Up to this point in the book, you've read a lot about physical security, social engineering, and surveillance (with a touch of Wi-Fi thrown in for good measure!). And these are all great topics, especially if you're working from the perspective of someone who is physically present at the location in question. But what about low tech hacks for penetration testers or those of us who work in the world of red teams? There really are no limits to what you can achieve in a penetration test if you use a bit of creativity. Everything you've read about, up to this point, can play an integral role in your work as a penetration tester; all you need is your own imagination and the ability to consider how “normal people” react to your actions.
There are literally dozens of books about penetration testing and red team operations. They all go into the use of software tools, usually within a Linux platform, to conduct the standard steps; information gathering, exploitation, escalation, migration, and exfiltration. But what most of these books fail to cover are the low tech activities that not only benefit your normal penetration testing but also can often stand on their own when working these types of projects. As you'll see as you progress through this chapter, we're taking the concepts of social engineering and combining them with easy-to-use technology to create valid and effective attack techniques.
Penetration testers tend to agree that the end user is the weakest link in any information security chain. This is mostly due to the fact that we've gotten better at using security tools and appliances. They're tangible; you can reach out and touch them. They come with an owner's manual and support groups in online forums to help you troubleshoot. But humans are social animals, and we've trained ourselves over the generations to help people and to trust people. It's always been a mechanism for the survival of our race. More individuals prefer to believe the best in others and their intentions. At the very least, we don't want to be the person who slows down the organization or stops progress altogether. But that aspect of being human also makes our employees vulnerable to compromise by creative and enterprising attackers. As we've mentioned in the previous chapters, everyone could use a healthy dose of suspicion.
Additionally, humans tend to have physical, emotional, and mental limitations that impact how we process information. Our brains tend to take shortcuts, which makes reading a book more of an exercise of understanding the key concepts in the book versus one of reading every single word in the book. That same ability to generalize data from our surroundings makes us vulnerable to specially crafted attack methods. A great penetration tester can achieve high success rates by introducing slight variations in a target's environment without arousing suspicion. As an example, we can introduce a new person into an environment and play that person off as an employee if we can create a feeling of confidence and trust in the target. This could be as simple as ensuring our new employee wears similar clothing to other employees in the organization, like a uniform used in a hospital or hotel chain.
This chapter will cover some of those aspects of our human employees and how they can be used against the end user to provide access to the penetration tester. We'll also provide a case study example of techniques that have worked in the past and describe why those techniques worked so well. There are as many possibilities as there are creative thinkers in the security business, so this chapter doesn't pretend to cover every possibility. But you should still walk away with a better understanding of what's really possibly, what really works, and why it works. We'll cover the basics in the first part of the chapter and then walk through our case study to demonstrate how effective these techniques really are in the real world. Let's start with why these techniques work.
The human condition
Despite the natural urge we may have to disagree, the human being and the human mind are not perfect. We're normally born with a plethora of tools intended to help us survive and live long and happy lives. From our base senses, such as sight, smell, touch, and hearing, to our ability to solve problems, it looks as if we're prepared for almost anything. But although we use the resources available to us efficiently, we have basic flaws that are built in and can be taken advantage of by an attacker. Before we delve into the penetration testing aspects of this chapter, let's examine some of the flaws that make us vulnerable. This is analogous to complex computer systems that can perform extremely difficult tasks but, due to their sheer complexity, introduce any number of other flaws as well.
Selective attention
In 1999, two psychology professors from different universities performed an experiment called the “Invisible Gorilla.” Their names are Christopher Chabris and Daniel Simons, and the premise behind their experiment was that human beings are naturally quite selective in what they pay attention to during a normal day. That selectivity can actually be tuned so targets will see what you what them to see and, with a high degree of success, not see what you'd like them to ignore. This is called selective attention.
In the experiment, you, as the observer, are watching six college-aged kids passing basketballs in front of some elevators. Three of the players are wearing white shirts and three are wearing black shirts. You're asked to count how many times the players in white shirts pass the basketball. And while the task sounds simple enough, and you're likely to get the correct answer to the question asked of you, you're also likely to miss the fact that a person in a gorilla suit walks right through the group of students, pounding its chest before moving off the opposite side of the screen.
You can find out more about the experiment, and watch some of the videos at www.theinvisiblegorilla.com. But since you, the reader, are already aware of the outcome, it might prove more fun to have one of your friends watch the video without telling them the punch line.
In reality, selective attention is a great way to engineer people's reactions and motivations. As a more practical example, consider for a moment why casinos in Las Vegas make you walk through the gambling areas and high priced shopping to get to your hotel room after check-in. Additionally, when you're bored, standing in line at the grocery store, how many times did you buy the candy bar? Or how many times (if you can count that high) did your children desperately want that toy on the bottom shelf at the checkout line? These are methods for keeping your attention elsewhere, to increase the chance that you'll spend more money and forget your wait in line.
Generally speaking, great hackers can use this to their advantage as well. If I can draw your attention to one thing, it means you're not paying attention to something else. This can also be referred to as distraction.
Magic is distraction
One of the core concepts of magic is to distract your audience so you can do something else while they're not paying attention. We've discussed magic in this book previously because it ties in well with what we're trying to test for in the security world. When was the last time you watched a magician perform a trick live? Can you recall the reaction of the audience? Was it surprise? Shock? The great part about this example is that the audience knew this was going to be a magic trick, and it still took them by surprise.
Let's take this one step further and not tell the audience about the trick or the magic. In fact, let's not even tell them they're an audience or we're a magician. At this point, the trick, when performed correctly with distraction and practice, should go completely unnoticed. Remember, our goal is to get the user to do something (help us install malicious software and bypass security mechanisms) while ignoring something else (the threat we could pose to the organization as an unknown person with unknown motives).
Building trust and influencing behavior
In a 2004, Robert Cialdini wrote an article for Scientific American entitled “The Science of Persuasion.” In his work, the author discusses the underlying interactions between human beings that can be manipulated in such a manner to increase the chance of a positive response from a target. As a penetration tester, we can use these same concepts to ensure our efforts are rewarded with success.
In the article, Mr. Cialdini states, “Six basic tendencies of human behavior come into play in generating a positive response: reciprocation, consistency, social validation, liking, authority, and scarcity.”1 So, from our perspective, in order to best penetrate an organization, we'll want to utilize these human tendencies when interacting with the employees of an organization in ways they'll understand instinctually. This touches on the social engineering concepts we've covered previously in this book. As you'll see in the case study later in this chapter, we use this concept to limit the chances we'll be confronted during our work. For example, actions as simple as looking and acting as though we have the appropriate level of authority to conduct an action, giving the target something tangible (such as a USB drive or CD), and being polite by offering the target a compliment help build trust and allow us to influence the behavior of the target. You'll see a demonstration of how a team can use these methods when we cover the case study later in this chapter.
Technology matters
Since this book is all about low tech methods for penetration testing and red teaming, we'll keep the technology to items and software that are easily and readily available to the layperson. These are typically items that won't require too much heavy lifting by the reader but will still provide useful results as well as a decent learning experience.
When we discuss technology in this chapter, we're discussing delivery and communication methods. Delivery methods allow us to get users to install our communication methods for us, simplifying the process of bypassing the security mechanisms in place at the target. In the most basic sense, delivery methods can be normal, off-the-shelf technology, such as USB thumb drives or a CD-ROM. In a more complex attack we might also utilize techniques involving drive-by web attacks or email phishing attacks. But let's start with the basics concerning our possible delivery methods.
USB thumb drives
At this point, if you've been around the security industry for any amount of time at all, you've likely heard the tale of “the guy who knows a guy that scattered USB thumb drives through a target parking lot, only to have the users pick up the drives and plug them into their computers.” It's a consistent story, and it's been around for a while, even if no one is actually certain who started it.
This technique has worked fairly consistently in the past. Your team buys some inexpensive thumb drives, installs some nefarious software on the drives, and places the drives in conspicuous places in the parking lot. USB drives have value to users because they're small, they hold data, and, frankly, they're cool. Over time, however, as this story has spread and been introduced into security awareness discussions and training, users have grown suspicious of random, unknown USB drives. As a penetration tester, that means we need to adjust our attacks to appear trustworthy to the users again, and we'll cover more about this later in the chapter.
First, let's look at some basic USB storage devices that might be useful to us during our testing. The first is the normal USB thumb drive. They range in size from about an inch to an inch and a half long, as shown in Figure 6.1. The storage capacities of these devices is sufficient for small payloads (such as a self-loading Trojan or key logger), or they can accommodate entire bootable Linux distributions. The payload you use should be determined by your end goal and your rules of engagement. And since these devices are so popular, most operating systems will auto-mount, auto-load, and/or auto-run content from them without much in the way of user interaction. This will be important later, when we're considering our strategic options for compromising the organization.
The next type of USB device is much smaller, and in my opinion, much more dangerous for users. If you recall from Chapter 1, we discussed the use of key logger devices that attach to the keyboard plug on the back of the computer. These devices look as if they belong there and don't draw attention to themselves. But, from my perspective, they're still larger than I'm comfortable with during a penetration test.
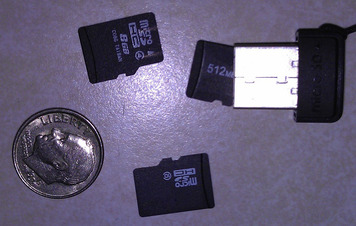
Looking at Figure 6.2, we see another version of the USB drive that is significantly smaller and can actually utilize a variety of storage chip sizes. This means we can create an 8 GB, a 16 GB, or even a 32 GB USB device without ever changing the actual hardware. And the storage cards we use in the device can be preloaded with specific types of deliverables, based on our needs.
In Figure 6.2 you'll see an image of the small USB device (it looks like those small USB dongles used for wireless mice and keyboards). Next to the device, I've placed several different micro SD cards, which are used as the memory for the device. One of the micro SD cards is shown sticking out of the slot, so you can get a better idea of how the memory slides into the device. And finally, I've included a dime so you get a better perspective of the size of the device.
I'm sure you've already guessed, but the two different USB devices we've discussed here will likely be used in two entirely different ways. For example, a full-size USB device dropped in a parking lot will still be seen by people walking to and from the office building each day. The smaller device is probably too difficult to see if it's lying on the ground, based on its size and color. And since the goal of this exercise is to ensure people see the device, pick it up, and use it, we'll have to consider a different attack method.
Also, bear in mind the USB devices themselves aren't the dangerous part of this setup. They just happen to be a convenient medium for delivering our actual content to the user's computer. We'll discuss more about how we can use these devices later in the chapter.
CDs and DVDs
CD-ROMs and DVDs are a popular medium for users. They can store music, documents, pictures, or other digital media, and they're fairly inexpensive. Most modern computers can utilize these discs without any extra software, and most operating systems can auto-run these types of devices.
For comparison purposes, CDs can hold up to 700 MB of data. This would be a great size for storing data with embedded Trojans or other malware, even with a fully bootable Linux operating system. On the other hand, DVDs have a capacity of roughly 4.4 GB, once all is said and done. In this instance, you can create the same bootable Linux operating system and include a much larger store of software that allows you to bypass any operating system—level restrictions or to compromise the data on the hard disk itself.
Again, which one of these options we end up utilizing depends entirely on the mission goal. If we're looking for a quick, user-level compromise, then we're probably better off using the less expensive CD-ROMs. If we're going for a full system compromise, where we intend to exfiltrate or modify data on the hard disk and need the larger collection of tools, we'll probably want to use the DVDs.
Staging the effort
Up to this point in the chapter we've focused on why humans are vulnerable to our efforts and on the medium we can use to finalize the compromise. The reason we haven't touched much on the actual penetration/red team portion yet is that I needed to set the stage. In this section, I'll talk a bit about how we can stage our effort, depending on the target organization, and then, in the case study, we'll cover more specifics.
Remember, this is a low tech approach to penetrating a target organization, and we'll cover this stuff in more detail later in the chapter in our case study. We're not using specially crafted exploits that we've written ourselves. Our goal is to keep this process as simple as possible and use suitable tactics for the job. So let's consider the information we need to know, generally speaking, to make this happen.
Target organization
One of the first things to think about is the target organization itself. What type of organization is it? Where is the organization located? What are the primary organizational mission goals? Where will the team move in on the target? Will it be at the office building itself? Is it at a conference location? What types of employees will we likely encounter during the work?
Location considerations
If we're hitting the organization on its own soil, then we need to know where the building is located and what the physical security is like. We won't cover that here since we've already covered it in Chapters 2 and 3. But it's an important consideration that we can't skip.
What if the organization is larger in size and has an annual conference, perhaps in Las Vegas (that is the convention capital of the world, right?)? This presents us with similar issues but with a few advantages. For example, if we were working from the target site itself, we would be more likely to encounter physical security mechanisms. But from a conference site, there is so much foot traffic that we can better blend in with the other folks in the area.
As noted previously in the book, we need to look the part. And that look depends entirely on the site we're working from during the initial compromise. Consider a corporate wide conference being held at a hotel. We have multiple options for how we dress and act. We can pretend to work for the organization itself, the hotel staff, the conference planning staff, or even a third-party vendor that has come in to provide discounts on local attractions to the employees. In many cases, we'll find that a mix of these will be useful. Regardless of how your team decides to deploy that initial compromise, never underestimate the value of looking the part.
Organizational culture
Another consideration for your penetration team is the culture of the target organization. Working within a medical environment, for example, is going to be entirely different from working in a conservative, non profit environment. Your attitude, personality, clothing options, and more should conform to the expectations of the target. If you recall from earlier in the chapter, people naturally want and need to trust other individuals. All you have to do is fit into the confines of their expectations.
Let's look at a quick comparison of two disparate organizations, so we can get a clearer picture of what might be necessary. Our first organization is a financial and investing firm based in a large urban setting. The employees dress professionally, with business casual attire for the worker bees, and suits and dresses for the executive staff. If we're looking to fit into their normal, everyday expectations, it would behoove us to avoid dressing in blue jeans and a t-shirt. Briefcases are more common than backpacks. Looking the part is critical here.
The second organization is a tech company that believes creativity is based on providing as few limits to the employees as possible. Workers are allowed to wear shorts, t-shirts, and flip-flops to work. The company is a green organization, stressing the recycling and reuse of as many materials as possible. In this instance, not only will we need to consider how we look and act within the organization but we'll also need to take into account how we deliver the media to our target. Over-the-top plastic or cardboard packaging could be detrimental to our cause.
Getting things in order
Once we've collected this basic information about the organization and where/when we should attack, we can put our project together. This part is where we get to use our imagination and decide what will work best. Will we initiate the project at the organizational headquarters? Or will we interface with the users directly in a more informal setting, such as a conference or public location?
Based on this decision, we'll decide what technology we'll use and how to launch our attacks. I use the plural term because we're likely to encounter more than a single user when implementing these techniques, and each one will require an attack. And location, time, and technology aren't the only decisions. There's always room for a wardrobe change as well. If you'll be working in a hotel environment, where all the hotel staff wears a green casual shirt with black slacks and black shoes, it should be easy to imitate the wardrobe. Name badges are also easy enough to mimic, since most are white or gold plastic with printing on them. The right clothing and accessories can create a sense of trust within your target because you blend in with their expectations.
Deciding on location
Users tend to be more relaxed and less on their guard when they're off-site than when they're at work. Now, that doesn't mean users are going to be alert and reliable when a stranger is in their work area; it just means they're likely to care more than they will when working off-site. So the best location to target users will normally be outside their normal working environment. Conditions are different and new. And most users won't know what's normal for those environments, making them less suspicious.
If you're forced to conduct the project at the customer organization, your team will need to be more detailed in planning stages and conform more to the cultural norms of the organization. Your language, manner, and approach will have to be tailored to match the environment. When done correctly, on-site penetration projects shouldn't be much more difficult for a seasoned professional.
Another alternative is an off-site meeting or gathering of employees. Good examples are fund-raising carnival days, team-building exercises, and even charity work performed by employees as a group. They still work for the organization, but they're out of the office and less likely to be security conscious.
Choosing the strategy
The strategy is our game plan. It's how we'll approach the users, gain their trust, and get our software installed on their computers. The strategy has to take the location and the mood of the users into account. A good example of this would be a product convention in Las Vegas versus an executive meeting at an Atlanta hotel. The product convention is likely to include employees from all ranks of the organization, whereas the executive meeting is more likely to be attended by folks in formal business attire. Also, Las Vegas tends to foster that “what happens here, stays here” mentality, where employees are more likely to let their guard down and enjoy themselves. An executive meeting held at a nice hotel in Atlanta is less likely to foster this type of attitude.
When we use the term approach to describe our initial interface with the users, it doesn't necessarily entail walking up and having a conversation with them. There are a number of methods for introducing our payload in formats that will be trusted by employees. Printed flyers, gift bags, special offers, and other approaches can be utilized to gain the user's trust. And each one of these has benefits and disadvantages that you'll need to weigh as you create your strategy. Just don't make the mistake of assuming you need to interact with the employees face-to-face for your penetration test to be successful. You might find the employees are more trusting of a printed flyer presented with a benign-looking CD to the random stranger handing them something they never asked for.
The strategy we choose needs to fit with the location, target audience, time, and wariness of our targets. We can snail mail our payload to the target in custom packaging that makes it look more official (thus more likely to be opened and trusted). Another option to get the payload into our target's hands is to present it as a perk of a conference or convention. In some instances, we can use our newly developed social engineering skills to get third-party individuals to pass along our surprise for us (hotel staff, conference staff, human resources, etc.).
Since our penetration projects will be different, each of our approaches will be customized to the organization we're targeting. Your team will need to be flexible and creative. Consider all possible alternatives, because you can be fairly certain the target organization hasn't.
Many people have issues with approaching strangers, and their lack of confidence shows when they're forced to carry on a polite, friendly conversation with someone they've never met. To compound those anxieties, the individuals we'll be approaching are actually targets of our project. And while the end goal of our project is to educate the organization and its employees, there may still be an uncomfortable sense of anxiety that impacts the way we interact with the individuals with whom we're communicating.
I'm pointing this out because it's incredibly important to be relaxed in your interactions. Most people haven't studied body language, but they do have instincts that react to body language and can alert them to situations that could be dangerous or misleading. In our case, we're not actually a danger to them, but we want to reinforce that safe feeling in our target with friendly smiles, free-flowing and casual banter, eye contact, and a sense of professionalism. All these cues will be picked up by the target and will reassure them of our intentions, even if they don't actually stop to think about it (which is technically the point of this exercise).
Choosing the technology
The technology should fit together with whatever plan you've decided on. They're like pieces of the same puzzle. If you try to use technology that doesn't fit into the story you've created and that you're walking your target through, it will stand out and is more likely to look suspicious. CDs may be more useful in situations where it's a public venue and needs to appear mass produced, such as coupons, tourist information, or home business opportunities.
USB thumb drives cost more, and people will know that, so trying to hand someone a USB drive with “Atlantic City Tourist Information” on it will appear suspicious. We want to save the high-cost deliverables for those instances when we're working with a smaller target audience, and we want the impression to be personal, as if we're trying to earn that person's business.
In those cases where we have physical access to the target organization's building, we can use the micro USB drives, CDs, or something similar. These allow us to plug into the USB port on target systems and either automatically install our own software or reboot the computer into a customized operating system that will allow us to mine data from the resident hard disk.
Automated attacks vary
When we look at our technology, we need to consider our attack method. Are we looking to perform a one-time data mining effort and have that data exfiltrated to an external system on the Internet? Or are we hoping to compromise a target host with a Trojan or backdoor that calls back to a server, providing us with a tunnel into the target network? It really doesn't matter which of these you decide to pursue, but you need to take into account the hardware and networking requirements of your attack.
Users are able to skirt most of the security technology that protects the organization. This is due to the legacy belief that all attacks will come from outside the network, from the Internet, and users are allowed free reign to come and go from their own network. But one of the most annoying technologies for penetration testers is the proxy server. Proxy servers force users through a single tunnel for their traffic, restricting the ports with which they can communicate. Trojan software tends to utilize set port numbers for communication, and a proxy server can break that connection, making all your effort up to this point fruitless.
Since this book is about low tech hacking, your best bet for pre compiled, ready-to-go Trojans and exploits is Metasploit and some of the other software on the Internet, such as Beast or Theef. Metasploit is your safer bet and provides mechanisms for wrapping the malicious software around executables, Internet documents, etc. As a bonus, the source codes for these payloads are normally available to the capable penetration tester, for free. Many Trojans, outside of consolidated tools like Metasploit, are written and released on the Internet, and the source code likely isn't available for you to review before using. If you pick a bad one, you could actually be doing much more harm than good for your client.
I should point out that using off-the-shelf payloads increases your chance of detection by security software on the user's end. Because these tools are so readily available, antivirus and security software vendors have created signatures that detect the tools and quarantine them almost immediately. They'll still work in many cases, but your chances of failure are increased. In some cases, you can find wrappers that will help obfuscate the code structure from detection systems on the user's side. But since we're limited in scope to low tech hacking, start out by practicing with the more readily available tools.
A wrapper is used by many hackers to obfuscate the code signature of a piece of malware so that it won't be detected by anti virus software once it's been installed on a user's computer. Most wrappers have an extremely short life span, since anti virus vendors search the Internet for them and adjust their tools to detect the artifacts/signatures left behind by the wrappers themselves. You can test your attack payloads against the various anti virus software products to find a wrapper that works, or, if you're a programmer, you can simply write your own.
A useful case study
Now that we've covered many of the basics of putting together a great low tech penetration test, it's time to put it all together. This case study will show how a possible low tech hack can be used to gain access to target computer systems. As you read through this example, it's important to remember that all of details in this penetration test can be changed and manipulated to fit your needs. This is less a step-by-step recipe than a demonstration of what's really possible.
The target in question is a large organization, with various offices in different cities around the country. The organization is large enough that it's difficult to tie together employees from different offices, who work in the same field, to communicate and strategize. Because of this, it was determined that an annual conference of human resource workers from all the offices would be held in Las Vegas, Nevada.
The goal of the conference was to get human resource employees from different offices to share solutions to common problems, to reinforce corporate human resource policies, and to foster relationships across the organization so employees have people to call when confronted with a difficult situation. The venue was chosen based on costs, proximity to the Strip, and the willingness of the hotel staff to help coordinate the effort. The HR manager at the corporate headquarters was the lead for the planning of the conference.
To aid in the planning of the conference, a list of potential attendees (numbering roughly 75 employees) was posted to the corporate website on a page linked from the corporate human resource page. While the link was not specifically advertised, it was still accessible from the Internet. The information on the page included name, phone number, email address, position, and location of each HR employee attending the conference. The page was updated automatically as each individual registered for the conference.
Based on all this information, it was decided that the best way to approach the employees would be through deception of the hotel and conference staff. Our team would stage two levels of attack, one against the hotel and one against the conference itself, but both aimed at the HR employees. Each of these two strategies required separate planning, but the two would dovetail into the same outcome.
The goal of the penetration effort was to get HR employees to install Trojan software onto corporate resources, allowing the team internal access to the corporate network. Two different approaches would be used, one via USB drive, and the other via CD-ROM. Where one medium might fail, the other might be successful.
Approaching hotel staff
The penetration team members decided that they would attempt to look like employees of the company holding the conference and approach front desk personnel with gift bags for employees checking into the hotel for the conference. It was easy enough to provide a list of employees who would be checking in, since this information had been provided on the corporate website. Each gift bag would contain a welcome letter from the conference organizers, valid corporate flyers (also downloaded from the corporate website and printed out), and gum, mints, candy bars, and a custom USB thumb drive that would have the corporate logo printed on it.
In order to approach the hotel staff, the penetration team members needed to look the part of employees from the company. A high resolution image of the corporate logo was found on the website and used to embroider corporate-colored polo shirts. Team members donned these shirts, along with slacks and nice shoes, and approached the front desk. A few minutes later, the hotel registration manager had gladly agreed to hand out the bags to incoming conference attendees.
Each USB thumb drive had been loaded with Trojan software that would install itself on the employee's computer, hiding behind the actual driver installation process that normally pops up when a new drive is plugged in. The Trojan would then attempt to call back to a specific server address on the Internet, alerting the penetration team that a new connection had been created. The information transmitted by the Trojan included the computer's IP address, machine name, and date/time of its installation.
This type of activity is considered illegal, unless you've been granted specific permission by the organization to target their employees in this manner. And in many cases, you could still run into legal issues if the Trojans are installed on personal computers. Much of the legality of these activities depends heavily on what policies are in place at the organization itself, what the employees have been notified and trained on policies and expectations of the organization, and the state and federal laws that may apply.
In ALL circumstances, be sure to consult with appropriate legal experts to determine where your boundaries are and how best to proceed. Don't take a chance with this type of work. While in some organizations it may seem cut and dried, in others you may find yourself in hot water if you don't do your homework first!
Approaching conference staff
The second method of approach would put the penetration team in direct contact with the conference staff. This time the attack would come in the form of custom-printed CDs that contained information on tourist activities in Las Vegas, including brochures, flyers, and coupons. Included on the CD would be the Trojan, which would auto-load when the CD was put into a computer.
This time, the penetration team would need to emulate hotel staff. The goal was to deliver the CDs to the conference staff while pretending to be from the hotel and state that the hotel likes to provide these CDs to conference attendees as a way to help them enjoy their stay in Las Vegas. Emulating the clothing of the hotel staff was simple, since most employees wore a black polo shirt with tan slacks. Generic gold-colored name badges (that were similar to the ones worn by hotel staff, just without the logo) were created with fake names for each member of the penetration team.
In the morning, on the day registration was supposed to begin, penetration team members donned their uniforms and went downstairs to meet the registration staff. The plan was carried off without problem. The conference staff was immediately drawn into the story provided by the pen test team members and put the CDs on the registration table next to their own handouts. This way, when employees registered for the conference on-site, they could simply pick up all the conference materials and the tourist CD at the same time.
Conclusion
This particular penetration test worked out quite well. And while the scenario itself has been fictionalized to a degree to protect the innocent, it's still valid. The penetration team in this case had set identifiers into each of the two Trojan delivery mechanisms so we could discern how each computer was compromised, by the USB drive or the CD-ROM. The success rate for this attack was around 12 to 13 percent. That means that roughly 10 people installed the Trojan on their computer system so that it reached back across to the Internet to our custom server. That's 10 separate footholds on computers that process, store, or transmit that organization's sensitive information.
Now, what I haven't told you yet is that this particular organization was very security friendly. When I use the term security friendly, I mean to say the organization has a robust security program with annual security awareness training for all employees. This particular target should have been a tougher nut to crack. But as I mentioned earlier in the chapter, a successful low tech hack depends heavily on where and when you approach your targets and how the payloads are delivered. We created a false sense of security using social engineering tactics and delivered our payloads in a manner that was trusted, allowing us to gain access to the target network in all the organization's various geographic locations. Imagine the success rate for an organization that was less prepared and poorly trained.
Summary
Conducting penetration tests doesn't always have to rely on a great deal of technology. This chapter presented a methodology for using the concepts we've learned in this book to conduct such a penetration test. And while more technical payloads may help improve your success rate, it doesn't imply that your test will be entirely unsuccessful. Off-the-shelf software products, including some highly regarded free products, can often provide all the tools you need (along with your imagination) to do some low tech penetration testing. Also, keep in mind as you plan your test and start working through the steps, that you'll need to ensure you're playing by the rules. There are legal constraints that need to be addressed and managed.
Endnote
1.
Cialdini, R. The Science of Persuasion. Scientific American [Internet]. 2004 Jan [cited 2011 Sept 12]. Available from: http://www.scientificamerican.com/article.cfm?id=the-science-of-persuasion
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.