Chapter 8. Information security awareness training
Your most valuable countermeasure to employee risk
Information in this chapter
• An Introduction to Information Security Awareness
• Designing an Effective Information Security Awareness Program
• Implementing an Information Security Awareness Program
• Making Security Part of the Company Mindset
• Measuring Your Program's Success
As the previous chapters stated, social engineering attacks are a very real security threat that individuals as well as companies of all sizes must contend with on a daily basis. One way a company can minimize the risk of falling victim to such an attack is to design and implement an effective Information Security Awareness Program. This chapter explains why such a program is the best low-cost countermeasure for safeguarding sensitive information properly at any company, regardless of size. After highlighting the role of an Information Security Awareness Specialist, the chapter explains in detail the critical steps to implementing a successful Information Security Awareness Program. Among these is the creation and presentation of a business plan, a topic on which the text provides several guidelines. The chapter also delves into the components of an awareness program, and then discusses how to implement the program once the business plan is approved.
Key Words: Classification of Data Matrix, Information Security Awareness Program, Information Security Awareness Specialist, Quick Reference Guide, Touch point
On May 24, 1844, the first telegraph message was sent from Baltimore, Maryland, to Washington, DC. The message, from Samuel Morse, was a simple, but prophetic one: “What hath God wrought?”1
Fast-forward almost 170 years and we find ourselves living in a very different time, but facing many of the same risks. Back then Indians and “unknowns” cut wires to disrupt the flow of information or patched into telegraph lines to steal information. Today “unknowns” disrupt business communications, steal sensitive information at a magnitude that costs billions of dollars annually to the world's economy. The Internet, as wonderful as it is, is “What hath God wrought?”2
Suppose there comes a day when the entire world goes silent at exactly the same time. Governments around the world, television networks, stock exchanges, banking systems, communications, transportation, electrical grids, cell phones, anything that relies on the Internet and electricity would go silent at exactly noon Eastern Standard Time around the world. We would be catastrophically pushed back to a time just prior to “What hath God wrought?”3
If you think this is a farfetched scenario, think again. The world has become so reliant on the Internet that it has become its own worst nightmare. Business continuity plans would be useless as the last ounce of fuel and batteries died. The world would fall silent except for the chaos and fears that would take hold.
Could this actually happen? Yes! Is it more likely to happen at your company? Depends! Is there anything you can do to avoid such a calamity? No! There is no safe haven unless you can get in front of the risk. Unfortunately, as in Morse's time, the risks existed, albeit not as severe as we face today. The “unknowns” only need to get it right once. Your company needs to get it right 100% of the time. The question is: “How do you stop the ‘unknowns’ from getting it right once and to what degree?”
“Is it luck?”
They do it through excellent understanding of systems, networks, applications, and they do it the old-fashion low tech way. They simply walk into your business and steal information—sensitive information left lying around, the password taped under the keyboard, the printed data left at the copier, the sensitive information in the trash basket, the cupboard left unsecured, the laptop left unattended. Yes, they do it the old-fashion way by making a call and simply asking for sensitive information. These are the “unknowns” who look or sound like they belong, make themselves appear to be credible with a valid need to know. These “unknowns” are often referred to as social engineers. Adept, smart, they use the employee's desire to provide good customer/client service to gather sensitive information.
Kind of a bleak outlook, wouldn't you say? But there are ways to minimize the risks posed by the “unknowns” and what the potential “wrought”4 would be to your company. You must pay attention to your weakest link, and that is your people. It is your own employees' unintentional actions that are the greatest risk to sensitive information assets at your company whether customer, employee, business clients and that of the company.
An introduction to Information Security Awareness
This chapter is an overview on how to design and implement an effective information security awareness program. One chapter will not cover all you need to know, but it can serve as the foundation for starting a program or making an existing program better. In this chapter you will learn why an information security awareness program presents the best benefit, low-cost countermeasure for safeguarding sensitive information properly at any company, regardless of size. You will learn the critical steps and components to implementing a successful program.
The people and personalities of information security awareness
There are many essential characteristics needed for those involved in designing and implementing a successful information security awareness program. The following sections detail these attributes.
The information security awareness specialist
The need for an information security awareness specialist is emerging. This person has a good handle on marketing, communications, media, design, and project management. This individual doesn't necessarily need to be a subject-matter expert, and though having CISSP credentials would be helpful, it is not a requirement. A lot of what they must have is common sense and the ability to put into people-speak information outlined in the company's information security policy, standards, and other sources of guidance. An information security awareness specialist needs the creative ability and license to design a robust program and the maturity to implement it successfully.
What additional skill sets should you look for when hiring someone to design and implement an information security awareness program?
• Previous experience in implementing such a program is certainly an asset.
• Good writing skills.
• Someone with good people and presentation skills who is comfortable interfacing with all levels within the company. Often he or she will directly support the corporate information security officer (CISO) and other senior leaders in their presentation needs and craft emergency awareness messages too.
• Good project management skills.
• An entrepreneurial spirit.
The intrapreneur
An intrapreneur5 is someone who embraces the principles of an entrepreneur when working for a company. In other words, the intrapreneurs works within the confines of a company as if they are running their own business, willing to be a risk-taker as they advance the awareness program through the company's political environment. During the 7 years I was with Bank of America designing and implementing the information security awareness program, I had seven bosses. If each of those managers had decided to change the direction of the awareness program, my position and responsibility to implement the program would have been futile. Awareness programs must follow a consistent path that leads to greater employee awareness on how to safeguard sensitive information properly at the company.
This is not to say my managers did not give me input and valued suggestions. They were great team players. What I appreciated more than anything was their willingness to be enablers versus hands-on managers. I have never worked with a more wonderful group of people in all my life. To implement a successful information security awareness program, especially in a large corporation, you must “own the program,” be responsible for it and have the authority to implement it. The risk is not taking the responsibility and running with it. Never underestimate your capabilities to do so. If your manager is more of a hands-on person, you may feel less in control. You may not be able to create and implement the program you envision. However, you will still benefit from this chapter. The tools and techniques I will share with you will help anyone, and any company, start or improve an existing information security awareness program.
There is a tendency for management to redirect those who are responsible for designing and implementing the company's information security awareness program toward other projects. This often can become the death knell for your program. That's why it's important to have a business plan in place. You can point out to your manager where you are in the process of implementing the business plan, and why your efforts should not be redirected to other projects that do not support your plan. Of course, if your manager still wants to redirect your efforts, that's their call.
Data theft and employee awareness
If data theft is as important as everyone seems to think it is, then why aren't all companies providing information security awareness training to their employees?
The answer is simple. They do not understand the risks. Here is a simple analogy you can use when someone asks why an Information Security Awareness Program is so important to have at the company: When driving to work, everyone knows the rules of the road, but there are those who feel it's alright to run a red light or endanger others by multitasking while behind the wheel. When “driving” information through your company, the expectation is that employees will follow all the rules of the road you put in place. When they don't, the company's exposure to risk increases.
Using a cell phone, checking Facebook, or tweeting as you drive down the road are just not acceptable behaviors. I know you've seen people talking on cell phones, eating a hamburger, putting on lipstick, even reading a newspaper or book while driving. Somehow, these behaviors have become pervasive in our society, and they put all of us at risk.
Some people simply believe their actions are acceptable because they do not believe their behavior will cause an accident. Go figure. The same is true in your company. Recently I was with a group of lawyers at a deposition. During the lunch break, every lawyer left their laptop computers and iPads in the conference room. Not one lawyer stayed behind to insure that they were not stolen. These are intentional behaviors without a clear understanding of the risks. If each lawyer's company had an Information Security Awareness Program that focused on this simple risk, an unintentional behavior (risk) could have been easily avoided. I have seen the exact same risk lead to a lost laptop in a secure area within a company's facility.
A common example of unintended risk is a laptop with unencrypted sensitive data left behind in a cab, at an airport, unattended and stolen. The employee who fails to secure sensitive information or properly destroy that information has put the company and its customers in jeopardy. Many companies today simply state in their standard that if your laptop is stolen, regardless of reason, it is grounds for termination. It is a serious problem that rivals that of tweeting while driving and other nonsensical behaviors.
IT specialists know the biggest risk every company faces is employee failure to safeguard sensitive information properly. All the security applications in the world will not stop unintentional employee security mishaps or premeditated events by a disgruntled employee. I sometimes wonder whether an Information Security Awareness Program should be called an information security risk avoidance program. That way, more senior leaders will better understand the importance and support the program. For some specific examples of these vulnerabilities, read Chapter 6.
The cost of noncompliance
The Ponemon Institute's 2010 “Cost of a Data Breach” report said: “The average organizational cost of a data breach increased to $7.2 million and cost companies an average of $214 per compromised record.”6 That is up from $192.50 per record in 2007. How much of this lost information was attributed to employees? We don't really know, but the data suggests that employees represent 80% to 85% of all data breaches. I stress this is not documented data, and, of course, not all data breaches are reported. Suffice it to say, unintentional incidents by employees due to a lack of awareness or improper behavior is a big issue.
A look at cost risk benefit
So, why don't companies look closer at the cost risk benefit ratio when it comes to training their employees in safeguarding sensitive information properly?
The following observations will give you insight to some of the prevailing thought patterns.
Not all senior leaders and managers understand the risk. Unfortunately, it isn't until an incident occurs that management becomes fully engaged in the need for a viable program. When the loss is staggering, the risk becomes reality. Often, the perceived cost to implement a program becomes a barrier. It only takes one data breach incident, costing $7.2 million, 7 as indicated by the Ponomen Institute, to get senior leadership's attention. Almost immediately, management wants to know what the company is doing to educate employees on the risks. Then the cost of implementing a program is no longer a factor. An investment of $1.00 to $2.00 per employee into a program each year that reinforces employee awareness on how to safeguarding sensitive information properly is far less costly than an incident caused by unintentional actions.
Risks come in many forms, and the process of litigation and eDiscovery is a major risk. I have seen depositions wherein emails that were written 10 years previously are entered as exhibits. If your company does not have a document retention and destruction policy in place, it should consider one to ensure incriminating documents are not forgotten in the system only to raise their ugly head down the road.
Another reason companies do not implement an information security awareness program is that management may have the impression that employees are adequately reviewed and vetted during the hiring process. The prevailing thinking is, “We have good people. They have a vested interest in the company. They are loyal, honest, and law-abiding citizens of the enterprise. So why do we need to train them in safeguarding sensitive information properly?” Sounds a little stupid, I know, but, employees are also human, and humans make mistakes. Never assume that new employees understand how to safeguard sensitive information properly. It is the unintentional mishaps due to a lack of knowledge that present the threat. A solid Information Security Awareness Program assures all employees, new hires, and existing employees clearly understand and exhibit the right behaviors to protect customer, employee, business, and company sensitive information. These information assets, when in the wrong hands, generate a significant risk to the company. Thus, a good Information Security Awareness Program is not only a risk avoidance program but also a significant countermeasure to low tech hacking activity that every company faces today from inside and outside the company's walls.
Designing an effective information security awareness program
An awareness program incorporates the company's defined behaviors regarding its policies, standards, and other guidance into easy to understand, commonsense protocols on how to safeguard sensitive information properly at the company. Components of the program should include, but not be limited to:
• Information classifications at the company (confidential, proprietary, etc.)
• Examples of each classification
• Classification marking and labeling
• Proper transmission of information
• Proper storage and retention of information
• Proper destruction of information
• Use of security tools (user IDs, passwords, password guidelines, and how to change a password)
• General guidelines (privacy, document protection, physical security, laptop security, workstation security, remote computing, social engineering, downloading software, use of USBs and other storage devices, cell phones, use of Internet applications such as Facebook and Twitter, etc.)
• Internet/intranet/email usage (general Internet/Intranet practices, electronic mail practices, email monitoring policy, eDiscovery)
• Incident reporting process
• Information security resources at the company (where to find specific information security guidance)
Information Security Awareness Programs will vary according to a company's resources and the level of risks it faces. There is no one solution to fit all situations, and each program needs to be customized to the organization.
Repetition is the aide to memory
When you give a presentation, there is an old adage attributed to Aristotle that says “Tell them what you are going to tell them. Tell them, and then tell them what you told them.” In other words, repetition is the aide to memory. When implementing an Information Security Awareness Program, that same adage holds true. An effective awareness program is not a one-time event. It is a program designed to change a culture from one of noncompliance to compliance in exhibiting the right safeguarding sensitive information behaviors. The program repeats the same message seven different times and seven different ways through a logical progression of touch points. Our goal is to enhance employees' awareness so that information security will become a cultural value exhibited throughout the company.
Touch points
When designing your program you MUST take into consideration all the existing and potential touch points available to you. Touch points are other resources within the company that you can utilize to support or deliver your awareness program. Some good examples are in-house periodicals, training platforms, media development capabilities, and other such communication avenues. As you look around your company, you will find many groups, such as personnel, supply, compliance, training and development, and communications, who will want to support the implementation of your program. Other divisions or groups within the company may not be as supportive. Too often, divisions or groups silo themselves, thinking that their operation is the most important, and thereby do not communicate effectively with other groups in the company. Your people skills in expressing your willingness to partner with others for the good of the company and its stakeholders will be of huge benefit to you in this process.
Never underestimate the needs of other group(s) within your company to support your awareness program. And never underestimate your ability to interact with those groups to provide services. Often, they need you just as much as you need them. You just need to help them see it. For example, if your company has a privacy group, they would be a great resource to partner with and support your awareness program. An in-house video production facility is always looking for ways to support internal clients, and so is training and development.
The first product I released in my program was a quick reference guide (QRG). I initially had a QRG sent directly to each employee in the company. For new hires, I partnered with the people in personnel who handled the new hire post-acceptance package. Each time the company hired a new employee, the employee received a package of materials such as a welcome letter, benefits information, corporate mission statement, etc., prior to their start date. The group that managed that process was excited to include the information security awareness QRG in the package.
As your program develops, you will discover that there is an administration component. The more you can relieve yourself of these responsibilities the more time you will have to concentrate on and move your program forward. For example, if you manually survey employees on an annual basis, who within the company can help with an electronic solution? Are they willing to run the survey for you? When I was creating our survey, I looked for individuals within the company who knew how to write good survey questions. There was no one. But, 2 years later, the need for surveys throughout the company had grown to such an extent that the resources became available as a new service from training and development. From that point forward, I had them design, implement, and manage our awareness survey. Training and development provided me with the data.
The concept of relieving yourself of responsibilities allows you to do more. You cannot be all things to all people, nor will you have the time to manage every aspect of your program if you keep it too close to the vest. My suggestion is to find others in the company who can take on the responsibility of distribution and even implementation of certain aspects of your program. Again, this gives you more time to work on developing the next component of your program versus administrating what is already in place.
There was another side-benefit to adopting this process. When would a new employee be most interested in reviewing material and have the time to do it? Prior to starting the job with a new company! By receiving the QRG in the new hire package, there was not only a better chance of their reading the QRG, but it also told the new employee that the company believed that safeguarding sensitive information properly at the company was very important.
To team or not to team, that is the question
The very first step in creating your information security program is putting a business plan in place. Your manager may want you to team with others in your division to accomplish this task and that can become a challenge. In large companies there are so many opinions on what a program should look like that it can be confusing. Of course, there is safety in numbers, but well-meaning efforts can be wasted in teams. There is a paradox called the Abilene Paradox, 8 which basically states that a group of people will make a decision to do something that no one wants to do. The result is the project goes nowhere. If you are responsible, then you MUST have the authority to make it happen. Again, as an intrapreneur9 you take permission to do this; don't ask for it. I offer the following suggestions that worked for me:
• Independently design the program without the input of a team.
• Review weekly progress with your manager.
• Create a presentation of the program for your Chief Information Security Officer's approval.
• Once you have the CISO's approval, you are free to move the program forward.
Let's go back to the team concept for a minute. Did I ever use teams? You bet I did! As the program became reality, I would create teams according to what was in my business plan. In many cases I partnered with other departments within the company to get the resources I needed to move the program forward. For example, I partnered with the privacy department to create the platform for our online information security awareness web-based training program. I created a team to design the information security content for that web-based training program.
There were many reasons why I partnered with privacy, none less than the Gramm-Leach-Bliley Act (GLBA) that required employee training. If I could partner with privacy to deliver an online information security / privacy awareness training program under the GLBA mandate for privacy, I could add a significant touch point to my program. It did not hurt that employees did not recognize the difference between information security and privacy. Since information security was better known throughout the company because of our marketing efforts, privacy saw the advantage in exposure as well as sharing costs.
Our online information security/privacy web-based training program was created in the early 2000s prior to emerging web-based training and learning management systems emerging technologies. Timing is everything, and embracing new technology to deliver a program was, and is, a smart way to move your program forward. We shared the costs and were able to use many resources of other groups too. Don't underestimate your abilities. Our combined effort to create the first web-based training program at the company was very successful and an important component of the Information Security Awareness Program. I'll talk more about this later on in the chapter.
Creating a business plan for your Information Security Awareness Program
Your objective is to create and implement an Information Security Awareness Program that will cover the next 5-year business period. And it must be created in the next 90 days. That sounds great, but, where do you start? What should it include? I'd suggest everything, including the kitchen sink! Well, that might be going a little too far, but the point is to create a 5-year comprehensive plan. Create a vision of what your program will look like over time. Do not worry that you are including too much. This is your time to be creative. My vision was simple: that every employee clearly understood their responsibility to safeguard sensitive information properly at the company and exhibited the right behaviors. Pretty scary, but by the time I left the company we had statistically achieved the vision with over 230,000 employees worldwide.
Don't second-guess what will work and what will not. Remember, your objective in the first 90 days or less is to put your business plan together. This is the time to be a visionary and be creative. Don't worry about budget and how things will be funded. Too often we constrain our creativity by worrying about things that actually do not exist. Start being creative by putting all your ideas down on paper or note cards so that you can see the components in front of you. This will help you determine the directions you want to take the program and the products, tools, and resources you will need to accomplish this. Do not underestimate your abilities.
The presentation
I titled my presentation, “A Marketing Campaign for Information Security at Bank of America.” The presentation had four sections:
• Overview
• Product Fact Sheets
• Product Roll-Out with Audit Compliance
• Budget Projection
Audit Compliance was included because the information security awareness program was an audit issue. That would be one of my CISO's biggest questions. So, I actually sat down with audit prior to making the presentation to my CISO to ensure that what I was presenting would meet with their approval. I will elaborate later in this chapter, under “Let's Talk More about Alliances,” how important partnering with audit and other departments within the company can help you implement your awareness program.
The Overview section of the presentation was modeled on the best presentation I have ever heard. A salesperson was trying to sell a satellite phone system to an Arab sheik back in the 1980s. Rather than present facts, figures, and technical jargon, the salesperson went out and hired a graphic artist. His presentation would be a one-pager. The picture he had the artist draw was of the sheik in his tent, in the desert, sitting in his comfortable chair, speaking on his satellite phone to someone who was on another continent. The picture also showed the phone communicating with a satellite. On the backside of the presentation sheet was the price tag to make this picture come to life. I think it all came to about $3 million back then. According to the salesman, the presentation lasted less than one minute. The sheik looked at the picture and knew it was clearly what he wanted. When the salesman flipped the presentation page over to reveal the price, the sheik signed his approval on the page. Deal done! This is exactly how I approached presenting my business plan to my CISO. I wanted to show the components of the marketing concept and how they would support a successful information security awareness program. The same principle of the sheik's one-pager applied. Keep your presentation simple. Each component had a title page that included a picture or graphic and a bullet point or two.
The other three segments of the presentation, Product Fact Sheets, Rollout of the Program, and Budget Projection, supported the Overview. For example, Product Fact Sheets indicated:
• The product name
• Description of the product
• Dimensions, if applicable
• Audience
• Distribution
• Criteria, if applicable, such as awards, etc.
• Process, if applicable
• Internal support/vendor
• Unit cost
These segments of the presentation were loaded with detail and indicated the cost of each item to implement. I knew that my CISO was not interested in the cost of each item but rather the bottom line. My challenge was for her to buy into the marketing concept, the products, the vision, and the cost. As you go through the Overview section of your presentation, you will get a sense of your CISO's acceptance of the program. If your CISO is not showing interest, you probably will never get to the fact sheets, roll-out (calendar), or budget sections. Fortunately, my presentation went well. Little time was spent on the fact sheets or product roll-out. Why? She was already sold on the program, and all that really interested her was the cost. It also indicated that the numbers I was coming up with were not just pulled out of a cloud but the result of a lot of research. It said I had done my homework.
Presentation is everything!
When my CISO asked the key question, “How much is this going to cost?,” I laid out the final budget this way:
• Product release
Product by title
• Audit item
What audit item the product was addressing?
• Release month
What month it would be released?
• Quantity
In what quantities would it be released?
• Unit cost
What was the per item cost?
• Extension
What would it cost to print and release the product, and then what would be the total cost now and over time to implement the program?
When it came to the budget section of the presentation, it was easy for my CISO to see how I had come to the dollar amounts I was requesting. I painted the picture, showed how it all connected, and indicated what it would cost. It was the plan that would solve her audit issue. Her final question was, “Have you checked with Audit to see if this meets their needs?” If I had not then I would have not gotten her approval to implement the plan.
When putting your presentation together, take the time to anticipate questions that you may get. Some will be obvious, but others will randomly pop into your head. Do not ignore these thoughts. Write them down and craft an answer to them. You'll be surprised how better prepared you are when these questions are asked during the presentation.
Components of an awareness program
It's time to take out your creative brush and fill your canvas with ideas. Here are a few of the ideas I came up with:
• Using a slogan.
• Creating a character associated with information security. I have used cartoon characters in the past and think they are a great way to get messages across, but it is a matter of choice and what is acceptable in your corporate culture.
• Creating an all-purpose Quick Reference Guide that would be sent to each employee.
• Producing a video for new hires. This is not as costly as you might think. You can visit my website, www.stealthawareness.com, to view “The Ten Keys to Safeguarding Sensitive Information Properly” for an example. If your company has an in-house video production studio, partner with them. That's why they are there. My CISO was convinced that a video would cost $50,000 to produce. I did it for less than $3,000 using the company's in-house resources. What my CISO did not know at the time was that I was a video producer, director, writer, actor, and editor. So, it was easy for me to partner with our in-house resources to produce the video at a reduced cost. This is an example of using your skills. You may have expertise in graphic arts. Use that in your program design of materials to save costs. It's a value added that you can bring to the program. Another key concept.
• Creating a sticker employees can affix to their computer. This will provide them with your division's contact information such as telephone number, email address, and website for information security.
• Writing articles for existing in-house publications. I liked this better than creating my own newsletter. I did not have to feed the beast every month or worry about distribution, printing costs, etc. because I worked with another in-house newsletter.
• Creating an awareness section on your division's intranet website. Don't have a website? What would it take to create one that employees could access? Does someone in your organization have the skills and ability to create one for you? Think of the intrapreneur9 in you. If this was your own company and you needed this resource to move your business forward, what would you do?
Next steps
Once you are finished getting your ideas down on paper, design what the products would look like.
For example, if your business plan indicated creating a Quick Reference Guide, the key topics might be:
• Information and how to classify it
• Keeping your work area clean of sensitive information
• Creating a good password
• Using password-protected screen savers
• Remote computing
• Safeguarding the transmission of sensitive information
• Destruction of sensitive information
• Social engineering risks
• Insider threats
• Incident response
I would also include information and guidance on the use of smartphones, social media, and the risks of eDiscovery.
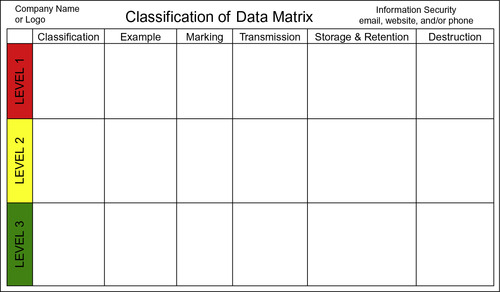
The Classification of Data Matrix
The Classification of Data Matrix was a one-pager stitched into the QRG that could be pulled out and posted in an employee's workspace. This matrix outlined how information is classified at the company and included:
• Definition of each classification
• Naming of each classification, such as Confidential or Proprietary. The matrix will explain the difference
• Appropriate marking of each classification on printed or electronic information
• Appropriate transmission of electronic and nonelectronic information
• Appropriate storage and retention of electronic and nonelectronic information
• Destruction policies for information
The above should be displayed in a one-page printed document that can serve as a deskside resource for employees to follow. Additional clarification should always be available and referenced in a standard or other guidance. As shown in Figure 8.1, each classification your company uses to define a level of sensitivity can be coded to visually indicate importance on the Classification of Data Matrix. You can't see in black and white print, but in this example Red = Confidential (Level 1), or your highest level of sensitivity; Yellow = Proprietary information (Level 2) that is internal to the company and not defined at a higher level of risk; Green = information that is available to the general public (Level 3).
Manager's Quick Reference Guide
Creating an information security Quick Reference Guide for managers is also an important step in your program. You want managers to ensure that employees are safeguarding sensitive information properly. Topics that may be included in this guide are:
• Information security as a team effort
• Application development and working with IT
• Knowing your employees are properly safeguarding sensitive information
• The importance of encryption and properly transmitting electronic and non-electronic information
• The downloading of unlicensed software
• The importance of being an enabler
• Consultant or vendor guidelines
• Updating or deleting an employee's system access immediately when transferred or terminated
• Social engineering risks
• The risk of insider threats
Finding materials for your program
Where can you find the content for the products and materials you're putting together for an Information Security Awareness Program?
The content of your deliverables, as shown in your awareness program's business plan, will come from:
• The standards and other guidance already in place at the company.
• The subject matter experts you can work with in information security to ensure continuity to published guidance. Realize that, if there is no published guidance, you will in effect be creating it when you release a guide, brochure, video, etc. Thus, there needs to be an approval process that includes your CISO because they are responsible for the implementation of the information security program at the company.
• Your review process. Obviously, your SMEs (Subject Matter Experts) will want their input. Here is where you begin to partner with others within the company.
The importance of a good editor
Always use a good editor. The credibility of your program hinges on this person. A few spelling or grammar errors can hurt the perception of your program. Be professional. I started out with an editor in corporate communications assigned to support our division. She helped us get off the ground. As our needs grew we were able to bring on a full-time editor to support the division. Look around you, and hopefully you can find some resources to help you.
Implementing an information security awareness program
Before you implement your program, you may want to send out a survey to a cross-section of employees to determine a uniform level of awareness in the company. This will provide you with a benchmark as the program progresses. This survey will determine your starting point by creating an awareness quotient for each question you ask. Do this each year, and you will see how effective your program becomes over time. Remember, as awareness rises, incidents should fall.
So, now your business plan has been approved. It is time to create the products and the distribution process to your employees. There are three key points that need to be considered:
1. If the program is going to be successful, you will need the support of the CEO.
The one question I hear most often is, “How do you get the CEO to endorse the program?” You could ask your manager to go to the CISO, who in turn, can go to their manager, who in turn, can go to their manager, who ultimately reports to the CEO and ask for their support. If your manager believes this the politically correct path, then you have to follow that process. I found a simpler way of doing this. I found out the name of the CEO's secretary. I called her and told her I was with information security and that we would be releasing a Quick Reference Guide. This guide would include information for associates on how to safeguard sensitive information properly at the company. I told her I wanted to put a picture of our CEO on the inside cover of the QRG along with his personal message to all our associates. We wanted his message to explain the importance of safeguarding sensitive information. He would explain how vital their knowledge is to the security of our company and it was his expectation that all our associates would fully follow the program. I told her I had already written the message and she asked me to send it to her. Within a week, I received approval and had my copy back with a few minor edits. I was also given the CEO's electronic signature. Most CEOs do not write their own messages. Their communications people craft those documents. I simply took the same approach. Craft it and ask for approval.
2. If the company does not have a corporate information security policy, then you should consider having one drafted.
The corporate information security policy, not to be confused with an information security policy, is a document approved by the company's board of directors. This policy states that the company has an information security program in place, who is responsible for implementing it (usually the CISO), and that all employees are required to follow it and what could happen to them if they didn't.
This policy may be required if your company is in the financial services or other heavily regulated industries. Your regulators can advise you. The policy places the onus on the board to be responsible overseers of the program by having in fact approved the policy, and it defines the person responsible for the development and implementation of the information security program. The policy is very generic, and one that would see little or no change over the years.
The reference to an information security policy means any standards put in place that states corporate information security's criteria for safeguarding information properly—i.e., information classification, access, etc. Sometimes these are referred to as policies too.
The information security awareness training program falls under “programs” as noted in the corporate information security policy and thus can be supported with a standard.
Do you need a corporate information security policy? It depends on your industry.
3. An information security awareness standard.
This standard becomes part of the corporate information security program as cited in the corporate information security policy. It gives you the authority to implement the information security awareness program. The standard states the employee responsibilities for safeguarding sensitive information properly as well as who should take training, whether it be new hires, all employees completing an online training program, and so on. And then comes when. What are the expectations to complete specific awareness training? Should it be done prior to system access or within 30 days of hire? This standard is just like any other standard and should be housed where other standards, such as classification of information, access, encryption, roles and responsibilities, etc., are kept.
Be sensible about the standard you create to ensure the processes can be followed in a timely manner. You don't want to create a mandate that's unreasonable and thereby cause non-compliance. You could create your own nightmare. An example of a bad requirement: All employees must complete information security awareness training prior to system access. I know we would all like to see that, but it's not going to happen, especially in a large organization. If you can have all new employees complete information security awareness training prior to system access, terrific!
After your proposed awareness standard has been reviewed with your manager, have audit review. Audit's approval is not necessary, but your CISO is always concerned about audit's approval. If he or she knows your program has already been approved by audit, you're in a much better position to have it approved. Of course, if your CISO makes changes in the standard, take it back to audit. This is more courtesy than asking for approval. The final decision rests with the CISO. You do not want your program to burden the company. You simply want to enhance awareness and validate that all employees are receiving awareness training on a timely basis and that each employee understands and acknowledges the responsibility to safeguard sensitive information properly.
Who writes the awareness standard?
If there isn't an awareness standard in place, don't wait for someone else to write it. You do it. Vet it with your manager and your CISO, and then walk it through your company's internal approval process.
It really doesn't matter if you are part of a large organization or a small one. It is critical to have an awareness standard. Someone is sure to ask, “Why do we have to do this?” It's so easy to answer with the following:
• The CEO mandates it (your message from the CEO).
• The board of directors mandates it (the corporate information security policy approved by the board of directors).
• The awareness standard mandates it (the information security awareness standard).
Finding win-win solutions
Because you have been given approval to implement an information security awareness program, do not let the “power” go to your head. The “Do it my way or else” is an old attitude to getting things done in the corporate environment. You can get more done with a kind word than you can with a gun! Always look for win-win solutions when implementing your program, even though you have the benefit of a mandate. Be an enabler!
One of the best illustrations regarding the ability to enable people is called “The String Analogy.” Begin by placing a piece of string on a flat surface. The string represents how people are motivated. If you try and push the string, you'll find it will crumble. If you push people, like the string, you will encounter push back or resistance and the string goes nowhere. Let's try pulling the string from one end. The string will stay straight and will follow, no matter where you pull it. People like to be pulled along and not pushed. That is what I hoped to accomplish with my awareness program. The goal was for employees to embrace the principle of safeguarding sensitive information properly, and thereby change the company's culture to one that says: “We value safeguarding sensitive information properly”. So, the program was designed to pull people along over time by providing consistent and ongoing messaging and tools. It worked!
Building a perpetual awareness program
What do you do when management in other divisions, departments, etc., is not supportive of the Information Security Awareness Program?
Sometimes management may object to implementing a new training program due to time constraints rather than the necessity of the program. Managers and senior executives recognize that employees are busy people and they do not want to take employees away from servicing customers, meeting deadlines, etc. If your program interferes with their expectations or bottom line, then you will receive push back. So, your program needs to be nonintrusive and at the same time provide awareness training in a concise, understandable format. You need to pull the string and find a way to fit required training into their schedule. A win/win solution.
An awareness program is not a one-time event. It should be a marketing approach with specific touch points and requirements, such as QRG and viewing a video. This softens the process and achieves the outcomes you are looking for. The most important benefit to your program is the acknowledgment that the employee has received awareness training.
Who should take the training?
Everyone! Each employee is an ambassador for the company. Imagine being at a party and someone says to you, “I'm concerned about what your company does with my personal information. “What happens to my social security number or driver's license number after I give them to you”? Well, “I don't know” is not a good answer. The reply must be, “Our company really takes your confidential information seriously. No one has access to your information unless he or she is acting on your behalf or has a valid need to know. Everyone in our company is tested annually on their knowledge of safeguarding sensitive information properly, and they receive safeguarding tips on a regular basis. We are constantly looking for new and better ways to take safeguard all your sensitive information through technology and employee awareness.” That type of reply is the result of an employee's familiarity with the information security message you are promoting on a continuing basis. You want the employee to be trained to the extent that safeguarding sensitive information becomes an automatic behavior and a mindset. Over time, safeguarding sensitive information properly will become a universal behavior in your company and the risk to an unintentional incident will be significantly reduced. So, the answer to the question “Who should take the training?” EVERYONE!
If your company has the resources to implement an online information security awareness training program you should be aware of a potential risk: That it is treated as a requirement of compliance, such as sexual harassment, code of ethics training, and other topics as defined by regulations. The reason I say this is that most compliance training is a once-a-year program (that's O.K.), but in your case it should only be one component of your program and not the whole program! “Oh yes, I passed the training” should not become the mantra of your program. It is an ongoing process of making employees aware. Remember, repetition is the aide to memory. Creating an Information Security Awareness Program that evolves into a cultural change in your company to safeguard sensitive information properly cannot be achieved in a one-time awareness course. It should be considered as one of many touch points in your program, albeit an important one.
The most important advantage of having an online Information Security Awareness Training Program is the ability to document the acknowledgment by each employee as they successfully complete the program. By employees passing, it validates the other components in your awareness program.
So that you do not blind-side employees to changes in standards or other guidances, it is recommended that you place a preview page of changes at the beginning of the annual training session and prior to the option to test out.
Getting the program off the ground
My first product release was the Information Security Quick Reference Guide. It's nice to think that everyone receiving the QRG will be excited to receive it, read it, believe it, and follow it. However, the reality is that the guide will get thrown on a desk, in a drawer, and not looked at by most employees. That is why management is the key to a successful response to the QRG. With their support and endorsement, the QRG will be received by employees with enthusiasm and utilized often once they understand the content and its importance. This is a good way to engage managers into the process of information security. Practicing good physical security and information security is not an employee option. It is a company imperative.
Making information security accessible
I think the most important thing about an information security awareness program is that people know how to contact information security when they have a question or concern.
I discovered that our division had an 800 number for managers to set up new employee access (add/change/delete) and for employees to have their access reset. There were several extensions on this number. Why not add an information security awareness extension? This idea of utilizing our 800 number transformed into a sticker that simply had our name, Corporate Information Security, the bank's color banner, the 800 number and extension, and our info@ email address on it. I had the sticker stitched into the Quick Reference Guide, with a note to associates to remove the sticker and place it on their monitor. We did not have a website developed at that time, but if we had, it would have been included on the sticker too. Today, affixing a sticker to a flat screen may not be ideal, but the idea is to get your division's contact information in front of your employees. So, do not be afraid to be creative.
When you plant the seeds for success in your program, one simple product can make a big difference. Associates had a universal way to communicate with us, ask questions and receive guidance. Over time, we created an index of the most frequently asked questions so that the 800 number operators could answer the question or direct the caller to the answer, which most often was answered in the Quick Reference Guide. If the question was not answered in the QRG and the operator could not answer the question, it was sent to me. You might think that you would become overwhelmed with many calls, but we didn't find that to be the case. This simple process opened additional doors to implementing the information security awareness program several years later when privacy became a group within the company. When privacy started their awareness program, guess who started receiving their calls from the employees? You got it, we did. Privacy did not have an 800 number. What we learned was that the employee saw information security and privacy as one. That event opened the door for information security and privacy to partner in developing the first web-based training program at the company. We also provided privacy with an extension on our 800 line.
A lesson learned
You will learn many lessons along the road to designing and implementing your information security awareness program. Sometimes, the lesson comes from a very unexpected source. I, along with my boss and CISO, thought we had a terrific marketing campaign with a slogan that was catchy and would support the program. My boss and I went to corporate marketing to make sure the idea would be acceptable. It simply said: “Just PIP it!” “PIP” stood for “Protect Information Properly.” I wanted our slogan to be a key component to the marketing approach. Could you imagine employees saying: “Hey, Just PIP It!” Marketing thought the idea was terrific too. With their approval in place, “Just PIP It!” became a key element in the marketing of our program. We were pretty excited, until we talked to corporate communications. A resounding “No” could be heard across the enterprise. “No acronyms are allowed at the company!” it was exclaimed. “We like the idea, think it is very creative, but NO acronyms are allowed.”
“Is that your final answer?” I said.
“If we make an exception for you, we need to make an exception for everyone.” So, I was forced to change the slogan to: “Protect Information Properly—it is your responsibility!” Notice that I didn't say: “everyone's responsibility” but “your responsibility!” That is where the emphasis needs to be placed. Each employee needs to value the principle of safeguarding sensitive information properly. The word everyone takes employees off the mental hook of responsibility. The lesson learned is to remain flexible when designing your program. There is always someone else, in some position of authority, somewhere, who does not like what you are doing or who wants to exercise their authority over you, right, wrong, or indifferent. Incidentally, the acronym rule was rescinded a year later. Unfortunately, the campaign was in full gear by then.
The dollars and cents of your program
A common reason awareness programs are not supported is because your CISO has decided not to fund it. It's not the CEO's responsibility to fund your program. It is your CISO who holds the purse strings. Here are some ideas on how to fund your program:
1. Earlier, as you'll recall, we discussed the importance of creating a good business plan and to include a budget. At the time of presentation, all you are looking for in your presentation is formal approval of the budget to get the first year of the program off the ground and establish an expectation of what it will cost to move the program forward in subsequent years. You might be surprised to know that I did not have a line item budget.
2. Ask for the money. If you need additional dollars above and beyond what you requested in your presentation or that has been allocated to your program, simply ask for it. Present your ideas and why they are important to the overall program, and ask for the money to fund it. If funds are not available, ask that it be put in the budget process for next year. There may be other sources available to you. Take a look at these ideas:
• If your company acquires another company, normally transition dollars are available. This is good because those dollars do not come out of your budget, but rather a special fund (bucket) set up by the company. Often, you can kill two birds with one stone by using these additional dollars for the transition as well as other items you want to add to your enterprise-wide program.
• Another source is the division's supply budget. If there is going to be money left over at the end of the year, put your request in for it. Don't ask for money out of this fund at the last minute. Let your boss know you are looking for additional money before the end of the year for a specific project. Most of my life I have been fond of saying, when the mind is ready, the money is ready. You experience the truth of that statement when you purchase an item that you are excited about. Like buying a new car. If you can justify it in your mind, you will find a way to afford it. And, if you do not have the money, often others will find the money for you in the manner of creative financing. This is no different. If your boss sees the value in the product or idea that you are selling to them, they will go and find the money for you.
• It's always nice to use other people's money. Go back to your alliances, and see where you can partner to share the expense of your program. Online training is an example where information security and privacy can partner and share expenses. This brings value added to the company.
• What budget dollars are available in other departments within your division? There can be internal products they want to distribute to a specific division(s). This product(s) becomes another touch point for your program and makes sure the image the division is portraying is consistent throughout information security and thereby the company.
• Finding the money can be as simple as asking for it. Budgets do run in cycles, and there are times when nothing can be spent. Most important, if you are budgeted, make sure you spend it. And last, a severe incident almost always raises the need for greater awareness. There is nothing like an emergency to loosen the purse strings. It is why I encourage anticipating issues and how you will handle them. There is no greater advantage than being prepared in advance for the next question or need from your CISO.
Above and beyond
Be creative. You are your own best resource. I never took a concept or idea to my manager for approval other than my business plan. I always took what appeared to be a finished product. Do not be concerned about the perception of “Why did you put this together and waste time?” You are the manager of the awareness program and are presenting the product to your manager to keep your manager advised. Some of these items might be dummy mockups of a brochure, poster, a QRG, a short video. It's one thing for your boss to say: “That's a good idea,” and another when they say, “That's a good idea and the product concept looks great!” A picture is worth a thousand words. Conversely, if your manager is a control freak, then it is better to follow his direction, as much as it hurts me to say that.
When I create presentations, I always assume that the person I am presenting it to is not the decision maker. So I create the presentation in a manner that is easy for someone else to present and explain. Remember the sheik? This is why I use pictures and graphics as much as possible in a presentation. The same holds true when presenting a concept. There was a time when the budget was tight and an opportunity showed itself. It would require producing some infomercials. This was a short promotional video that I was able to produce myself that we aired on our in-house video channel and, later, on our in-house website when it was developed. Because I had the skills to produce these infomercials myself, that is what I did. When I suggested the concept to my boss, he told me we did not have the budget but thought it was a good idea. I said, “That is fine, but take a look at this.” I showed him the infomercial I'd already created and he approved it immediately. I know this is not the norm, but I was vested in my program and it was a way to keep it going during a time when there were budget restraints. Remember, risk taking and innovation can help you move your program forward. Ah, the intrapreneur. 10
If you have a company intranet, this is a great place to support information security services. If you are a small company, having your policies, standards, procedures, baselines, and other guidance housed on your information security website makes it easier for those with a need to know to find the information they are looking for. Usually your company will have a standard layout they want website developers to follow. Figure 8.2 provides a general template for what a website could look like.
Making security part of the company mind-set
Each department in CIS will probably want to have their own section on the website. If you institute a CIS website at your company, I guarantee that over time it will become the second largest at the company. Usually the company's main employee website is the largest in respect to content. You should have a web master, which is one other opportunity for you, if you are so inclined and skilled. This skill may bring value to you and your job within the company. If your company is large and has these capabilities in place, the group that manages the intranet will provide training and templates for you to follow. This is another touch point and another resource for your program. Do not underestimate your abilities. List the service tasks that information security provides, including your awareness program. This is where you can house and archive articles you have written, as well as other products used in your awareness program. The Employee Quick Reference Guide, the manager's guide, and even an orientation video are some of the materials you want to make easily available on your website. You'll be amazed at how many employees will utilize the materials you've put in place. Some of those materials are:
• CIS policy, standards and guidelines
• Awareness program
• Change access
• Request access
• Transmitting and storing data
• Consulting
You may want to include a “How to …” page on the website:
• How do I check for a virus on my computer?
• What is spyware?
• What is phishing?
• Remote computing and you
• When to use encryption
• Laptop security
• Tips for working remotely
Place your website's link on other division intranet websites. The company's main intranet website for employee information is a key place to have a link to your website.
To make it easier for employee access, materials, such as shown in Figure 8.3, were made available on our website (www.stealthawareness.com) for download.
The importance of communication with other lines-of-businesses
When implementing components of your Information Security Awareness Program, it is important that you have established a good communications matrix.
Though your CISO, and his or her direct reports, will or should be well connected, you need to develop your own contacts. Though your program includes manager responsibilities, you cannot always guarantee that managers will follow guidance. They are busy people, and busy people often forget to do things, especially when they do not see it related to their job function. Contact those who handle new hire orientation within a division and other contacts who provide services corporatewide or to a specific division or group. Recruit them to help you implement your program within their division. For example, you are about to send a document to every employee in the company. You can send the document out to everyone using employee distribution lists, and assuredly, every employee will receive your document whether it is hard copy or electronic. However, if you notify your contacts and managers that the document is coming, and what your expectations are, you may find that they have a different distribution process that they would prefer to follow. Failing to communicate properly can reduce the trust relationship you want and need to develop with management to effectively implement your awareness program.
Let's talk more about alliances
What are the various departments, divisions, etc., within your company that you can build alliances with?
Audit department
Yes, Audit is your friend! You'll find life easier for you, and any products and programs you create, if you run things by Audit on a continuing basis. Build the relationship and make them part of your team. I know this is not normal for Audit to have a close relationship with those they are auditing, but it made life a lot easier for me and them too once they realized we were all on the same team.
Legal department
Submitting materials to your legal department is the right thing to do. Rarely will you ever get a “you can't do this” statement from your legal counsel. It is managing the perception and protecting your program that counts. So, when implementing portions of your awareness program, such as an online training component, you want your legal department's input for obvious reasons and to make sure you have not overlooked something, such as how contractors are treated in reference to taking online awareness training.
Privacy division
Your company's privacy division can be your best partner. If your company is mandated by a federal regulation such as the Gramm-Leach-Bliley Act to implement an awareness program, then I highly suggest you partner with Privacy. One of the things we found was that employees did not know the difference between Information Security and Privacy. You want to eliminate that confusion. It benefits everyone in the company and also provides an additional shared resource to fund your program. In essence, by partnering with Privacy in implementing a corporatewide awareness online training program, we brought the awareness program to full exposure in the company. All other materials and delivery channels used were reinforced by the corporation's mandate by Compliance to take the information security and privacy training.
Compliance department
When I partnered with Privacy, we actually built the first web-based training platform at the company through the assistance of Training and Development and others. The company was working on a Learning Management System (LMS), but it would not be available for a couple of years. The first year Information Security and Privacy rolled out the online awareness training program, we had pockets of employees throughout the world who did not have system connectivity. Bandwidth, computers in the field for employees to take the training, etc., were not available in some markets. So we instituted a paper-based version at the same time. Our program was so successful in the second year of implementation that Compliance wanted to take over our program and add it to the new LMS platform they were ramping up. When instituting any new program, such as an online awareness training program, you will run into implementation issues. It takes time to make everyone (managers and employees) comfortable with the process.
It's very important to understand that when you place the implementation of your program in the hands of another group, such as Compliance or Training and Development, you will lose control of the product, but not the content. You MUST be willing to do that and understand why you should do it. The reasons are simple. Compliance would take over the ongoing development and cost of the course. In other words, you become a subject matter expert. This does not mean you do not have control of content, just the manner in which it is being presented. You also lose control of implementation, which is not a bad thing to lose control of. It is very time consuming and takes you away from other opportunities to explore with the awareness program. So, if you get the chance to build an information security online awareness program, don't allow it to bog you down once it has been implemented and is running effectively. The more responsibility you can give away to others for implementing your program, the less cost and time is required to support it. This allows you to go on to creating other touch points for your program unencumbered. Again, you will always remain the subject matter expert.
Training and communications division
If your company has a training and/or communications division, embrace their services. In some cases, you will have no alternative. For example, if your company has an LMS, it would be counterproductive to not use an established training platform. In addition, you want to make sure your materials are written in “corporate speak.” Coordinating your division's internal messages to the enterprise style is important. You are not the only one in your division communicating to the enterprise. You want to ensure that conflicting messages are not being sent out and that what is being communicated is in “people speak,” not “technical speak,” unless that is your audience.
Additionally, if your company has an employee website, nurture a relationship with the individual who updates the site. When an emergency occurs and you have an alert you need posted, you can save a lot of time getting it posted because a relationship has been created. I even went as far as sending my contact gift certificates for dinner for him and his wife to enjoy. Whenever I needed an alert communication to go out, Communication's review process was waived because we were able to establish a separate process and had developed a good working relationship.
Personnel department
Personnel can help you in many ways. For example, if you have a survey you want to send out to a demographic of the company, Personnel can slice and dice the distribution profile and provide you with lists—i.e., the SVPS, VPS, and the corporate officers, by hierarchy, so you have a good representation across the enterprise.
Personnel is probably the group in your company that sends out postacceptance materials to new hires. This is the team you want to coordinate with to distribute your QRG, manager's guide, or other information. This eliminates distribution costs from your budget. This is an example of getting more done for less.
Information security consultants
If your company is large enough to have internal information security technical consultants working with the various departments, then get to know these people. One of the dangers of implementing an Information Security Awareness Program is releasing a product or requirement that is in conflict with another division's calendar. Your internal information security consultants can help you with this issue. Your division contacts are also helpful.
Here are some final thoughts around alliances. Do not forget the importance of other direct reports in your division. When building your Information Security Awareness Program, ask those who report directly to the CISO to designate someone on their team you can interact with in the development and/or review of the program you are putting together. Everyone in Information Security should be an advocate of the awareness program. Many of your coworkers support other employees in the company. Make sure everyone knows that information security awareness materials are available, where to find standards and other guidance, and how to contact Information Security for clarification of questions, to voice concerns, or to report an incident.
Keeping your program viable
The answer lies in a simple concept to grow is to progress and to progress is to change. If you continue to change the look and feel of your program you keep the interest of employees. As an example, I produced video quick tips that were aired on the company's in-house television network and were also posted to our intranet website. The website provided tracking capabilities, and the number of people who watched those videos was amazing. Those statistics served as one measurement in the program.
The one product that I never used was a poster. Not that I have anything against them, because I don't. But, in my circumstance, we were not allowed to put posters on walls, only corkboards, which meant they had to be reduced in size, which reduced their effectiveness. If you are a small company, posters are a great idea if you are allowed to place them on the walls. For example, having a poster on an easel in the company's entrance foyer or elevator landings is an unobtrusive reminder to employees of right behaviors or an event you want to promote.
Other resources
If you have a university in your area or a school of the arts, you might consider sponsoring a contest for students to create an awareness poster or a short video that supports the information security messages at your company. This is an inexpensive way to get product created for your program and be involved in the community too. If you have an idea but not the creative ability to bring it to life, who inside your company can help you create the product? Never underestimate your own ability to create. Now, let's move on to the final portion of this chapter where I describe the most difficult thing you'll need to do: measure an information security awareness program.
Measuring your program's success
“What gets tracked and measured gets done.” This quote appears in many forms throughout the years, and is an adaptation of a longer quote by Lord Kelvin. It is always nice to have statistics in your favor when the viability of your program is questioned. And, be assured, sometime, someplace, somewhere, the need for an information security awareness program will be questioned or challenged by someone outside of your group.
Historically, it is difficult to measure the effectiveness of an information security awareness program. If you can connect your training to specific behaviors and have a way of monitoring those behaviors to see if compliance has improved, then that is what you are looking for. It validates the training. However, I caution that awareness is not training in the sense of learning how to operate a widget or a process. For example, knowing why and when sensitive information should be encrypted is awareness. Knowing how to encrypt sensitive information is training. The difference is in the understanding of and exhibiting the correct safeguarding sensitive information properly behaviors. What can you measure that will justify the effectiveness of your program? Here are a few ideas:
• How many employees have received training in any form (the acknowledgment process)?
• How many employees have received the Quick Reference Guide or other key materials you have distributed?
• How many “awareness” calls have you received and what categories are they in?
• If you do some marketing on creating easy-to-remember yet hard-to-crack passwords and your password resets go down, this is a good indicator that your program is working.
You want to capture before and after information to show improvement. It is not always easy to find applications or programs that can give you timely and accurate information that you can measure against your program. Think about processes in your company that can be tracked. If you can track it, you can measure improvement over time. For example, how many sensitive customer documents that include social security numbers, account numbers, and so on are not truncated as they are emailed outside the company without encryption? If this is tracked, request the data so that you can measure it against your efforts to enhance employee awareness on the importance of encrypting sensitive information when transmitted electronically outside of the company.
In my experience, I relied heavily on subjective measurements that ultimately validated the effectiveness of our program. It showed steady improvement over time. It also provided critical objectives to the program so that we complied with the Six Sigma quality management process already in place at the company.
Here's what I did initially. I created a paper mailer, because we did not have an online survey resource. To maximize the return of the survey, it was sent out with a way for the employee to respond anonymously. I actually had two surveys. One survey was for new hires and the other was for all other employees. The new hire survey was done on a monthly basis, while the employee survey was done once a year. I needed 600 responses on the annual survey to have valid statistical information. The easiest way to figure this out was to go on the Internet and search “sample size calculator.” I can tell you that when I went from a paper to an online survey, the number of respondents went up. I can also tell you that offering a trinket or other incentive to respond to the survey did not increase the number of responses. It's important to have a valid cross section of your organization. So distribute the survey to a good cross-section of the company's employees, up to and including the CEO. If you work for a large company, your personnel department should be able to provide a report that provides this information for you. If not, ask your personnel department how you can get the information you need. Obviously, you want the employee's full name, mail code and hierarchy, and position (CEO, SVP VP, officer, or designate by bands). If your survey was delivered via an online channel, then you would want the employee's email address, too. My response ratio was always high.
I asked questions in six basic categories:
• Passwords
• Viruses
• PC security
• Information security standards
• Data classification
• Other threats, such as remote computing, social engineering, and social media
I also asked questions that pertained to the level of service our division was providing. Even though this had nothing to do with the awareness program, it was in support of our division and a way to get that input while minimizing the intrusion of employee time from filling out another survey. I tracked all the questions CTQ (Critical to Quality). I only used ten questions in what I called our “awareness quotient,” for lack of a better term. It showed, over time, how the program was working and where there was a need for improvement. According to our regulators, over a 5-year period of time, our awareness quotient was highest in the industry. The chart in Figure 8.4 reflects one question but gives you an idea of what improvement looks like over time.
Identifying key components and cumulative results
Is it possible to define one product or component that made all the improvements? I don't believe so. It was a cumulative effect of the total program over time. As long as the program is constantly updated, it will show improvement and a behavioral difference in your company. When the company came out with an online survey application we could use, the administrative nightmare was over, and surveying became a lot easier. Keeping in line with respecting employee time, I surveyed existing employees once a year. Our response rate was very high and statistically validated the success of the program.
The survey gave us some important data. We began to identify who understood the training, what levels of management most often complied, and what areas within the company were being most impacted. This allowed us to understand what areas in the company needed more attention and where opportunities lay.
Depending on the number of data points you measure in your survey, you want to be able to show them and present statistics over time as depicted in Figure 8.5. I had this posted in my workspace so that when anyone walked in they could see how our program was being measured as well as our progress.
Summary
The design and implementation of an effective information security awareness program is far more complicated than what can be included in a single chapter. An additional source of information is the Internet. But be cautious. Not everything you read is good, solid information. There are individuals, associations, and companies available to help you design and implement your program. Fortunately, I had the opportunity to design and implement an Information Security Awareness Program at one of the largest companies in America and, for that matter, the world. So, I bring you real world experience and not theory. Nothing, however, is better than your own spirit, enthusiasm, and desire to create a viable awareness program for your company. Again, do not underestimate yourself!
Keep in mind that AWARENESS IS UNDERSTANDING RISK. Awareness is being proactive to those risks with sensible solutions, right behaviors. Each employee can significantly reduce the exposure of sensitive information by following simple behaviors and raising their hand with conviction when they see a potential or real risk. It is the same concept adopted by Homeland Security's “If You See Something, Say SomethingTM” campaign. It's your responsibility to create a program that effectively embraces employee attention with guidance on how to safeguard sensitive information properly. Over time, your program will change the culture to one that not only understands the importance of but also exhibits the right safeguarding sensitive information properly behaviors at your company. Let every employee at your company become a security officer because your employees are your most valuable countermeasure.
If employees are not made aware of their responsibilities, they cannot be held accountable. Each company in America can significantly reduce the loss of sensitive information, and thereby the exposure to the financial risks, through an effective employee awareness program. Make it happen at yours!
And finally, thank you for reading this chapter, as it is one more touch point in my mission to help others become more today than they were yesterday through presentation and awareness.
We fully acknowledge use ofChapter 4, “Developing an Effective Security Awareness Program,” from Techno Security's™ Guide to Securing SCADA: A Comprehensive Handbook on Protecting the Critical Infrastructure (ISBN: 978-1-59749-282-9, Syngress).
Endnotes
1.
Brier S, Clark C, Hewitt N, et al. Who Built America? Working People and the Nation's Economy, Politics, Culture, and Society, Vol. 1, 2nd Edition. New York: Bedford/St. Martin's, 2000
2.
Ibid
3.
Ibid
4.
Ibid
5.
Pinchot G, Pellman R. Intrapreneuring in Action: A Handbook for Business Innovation. San Francisco: Berrett-Koehler Publishers, Inc., 2000
6.
Report – Ponemon Cost of a Data Breach. 2010 http://www.symantec.com/about/news/resources/press_kits/detail.jsp?pkid=ponemon In Defense of Data, http://www.indefenseofdata.com/data-breach-trends-stats/
7.
Ibid
8.
The Abilene Paradox and Other Meditations on Management © 1988 by Jerry B. Harvey, ISBN 978-0669191790 (paper). Jossey-Bass Publishers, San Francisco
9.
Pinchot G, Pellman R. Intrapreneuring in Action: A Handbook for Business Innovation. San Francisco: Berrett-Koehler Publishers, Inc., 2000
10
Ibid
11
Ibid
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.